#Personal Data Security
Explore tagged Tumblr posts
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
In a world where data breaches and privacy concerns are rampant, Smarana offers a sanctuary for your digital life. We provide a private and secure digital storage solution, built on the principles of robust encryption and user control. Safeguard your cherished memories and sensitive documents with Smarana, knowing your data stays exclusively on your device.
0 notes
Text
#best encryption tools#computer security#cybersecurity#data breach prevention#data encryption guide#data privacy#data protection#data safety#data security tips#digital security#encrypting personal information#encryption basics#encryption FAQs#encryption for beginners#encryption software#encryption solutions#encryption techniques#guide to data encryption#how to encrypt data#online privacy#personal data security#prevent cyber attacks#privacy software#protect data online#secure communication#secure data encryption#secure files and folders#secure personal data#software for encryption#strong encryption methods
1 note
·
View note
Text
Best electronic logbook is a one-of-a-kind digital solution to collect
Most innovative digital solution for gathering, archiving, and verifying visitor records is the best electronic logbook. Now boost your output without jeopardising anyone's security.
1 note
·
View note
Text
How to Ensure Data Protection Compliance in Ghana

Data Protection
Data protection refers to the rules and practices put in place to guard against abuse, unauthorized access, and disclosure of sensitive personal information. Securing the data is crucial in today's increasingly digital and interconnected world, where enormous amounts of data are collected and shared, to safeguard individual privacy and win over customers, clients, and other stakeholders.
The basic goal of data protection is to make sure that data is handled, gathered, and stored securely and legally. To prevent cyberattacks, data breaches, and the unauthorized use of information, numerous organizational, technological, and legal procedures must be put in place.
Ghana's Data Protection Act: To regulate the processing of personal data, the Data Protection Act was passed in 2012. Additionally, it created the National Data Protection Commission (NDPC) to oversee the observance of data protection rules.
The scope and applicability of the Act: The Act applies to all processors and data controllers operating in Ghana, regardless of their size or industry.
Penalties for non-compliance: Serious infractions of The Data Protection Act may result in jail time, fines, or other sanctions.
The Fundamental Ideas in Data Protection:
A person's express agreement was obtained before any personal information was gathered, and the data was only used for the purposes for which it was collected.
Data minimization and precision: Keeping only the information that is necessary while making sure it is up to date and accurate.
Information Security and Storage Limitations: Limiting the amount of time that data is retained and putting robust security measures in place to prevent unauthorized access, disclosure, or loss of information.
Personal Rights and Access: Upholding individuals' privacy rights to request access to, correction of, and erasure of their data.
Assuring Data Protection Compliance: Appointing an Officer for Data Protection: Appointing a Data Protection Officer (DPO) who will be responsible for overseeing data protection practices and ensuring compliance throughout the organization.
Implementing Data Protection Impact Assessments: Conduct assessments regularly to identify and resolve any potential threats to and vulnerabilities in data security.
The implementation of security measures: Encryption, access control, and firewalls are all security measures that are put in place to safeguard data from hacker assaults and other security lapses.
Training for employees on data protection: Educating staff members on the fundamentals of data protection policies, practices, and standards to promote a conformist culture.
Reacting to and informing about a data breach:
Planning the Response to a Data Breach: Create a thorough plan to respond to data breaches quickly and successfully.
Notifying the appropriate parties and those affected: To reduce the risk in the event of a breach, contact the NDPC and those who were impacted.
Future Data Breach Mitigation: It is possible to enhance data security and prevent future security breaches by using the lessons learned from past instances.
Data Transfer and Cross-Border Compliance:
When transferring data outside of Ghana, be sure the recipient has given their approval and that the data is being transferred securely.
Putting in place mechanisms like Standard Contractual Clauses (SCCs) to protect data when it is transferred across borders will provide secure adequate safeguards.
Building customer trust is key to data protection, business prosperity, and profitability: Loyalty and Trust: Demonstrating a dedication to data security to win clients' trust and loyalty.
To avoid legal consequences: Respecting the rules on data protection will help you avoid costly legal penalties and reputational damage.
Reputation management: Keeping your business's reputation intact by safeguarding consumer data and responding to data breaches.
Conclusion:
To establish a more secure digital environment and safeguard the fundamental right to privacy for all Ghanaians, data protection in Ghana is a continuing journey that necessitates cooperation between the government, corporations, and people. Ghana may establish itself as a responsible and reliable member of the global digital economy by remaining watchful and aggressive in addressing data privacy issues.
#data protection in Ghana#data protection ghana#data privacy laws#personal data security#data protection act
0 notes
Text
We ask your questions so you don’t have to! Submit your questions to have them posted anonymously as polls.
#polls#incognito polls#anonymous#tumblr polls#tumblr users#questions#polls about the internet#submitted nov 30#internet privacy#internet security#online safety#online privacy#internet safety#ad blocking#data#personal data
449 notes
·
View notes
Text
The ticket sales giant said through emails to its users and in a press release that it recently discovered "an unauthorized third party" was able to obtain information from a cloud database hosted by a third-party data services provider. "Based on our investigation to date, we determined that the unauthorized activity occurred between April 2, 2024, and May 18, 2024," Ticketmaster wrote in an email sent to its users on Monday. "On May 23, 2024, we determined that some of your personal information may have been affected by the incident. We have not seen any additional unauthorized activity in the cloud database since we began our investigation." The California-based company confirmed the cloud database contained personal information of customers who bought tickets to events in Canada, the U.S. and Mexico. "This may include email, phone number, encrypted credit card information as well as some other personal information provided to us," it wrote in the press release, adding it is in the process of reaching out by email or mail to customers it believes were affected.
Continue Reading
Tagging: @newsfromstolenland
50 notes
·
View notes
Text
Person of Interest (2011-2016)
#person of interest#cyberpunk aesthetic#hacking#graphic design#surveillance#science fiction#surveillence state#hackers#cybersecurity#scifi#mobile hacker#code breaker#data manipulation#network security#infosecurity#10s#command line
81 notes
·
View notes
Text

Matt Davies
* * * *
LETTERS FROM AN AMERICAN
April 11, 2025
Heather Cox Richardson
Apr 12, 2025
On April 4, Trump fired head of U.S. Cyber Command (CYBERCOM) and director of the National Security Agency (NSA) General Timothy Haugh, apparently on the recommendation of right-wing conspiracy theorist Laura Loomer, who is pitching her new opposition research firm to “vet” candidates for jobs in Trump’s administration.
Former secretary of the Air Force Frank Kendall wrote in Newsweek yesterday that the position Haugh held is “one of the most sensitive and powerful jobs in America.” Kendall writes that NSA and CYBERCOM oversee the world’s most sophisticated tools and techniques to penetrate computer systems, monitor communications around the globe, and, if national security requires it, attack those systems. U.S. law drastically curtails how those tools can be used in the U.S. and against American citizens and businesses. Will a Trump loyalist follow those laws? Kendall writes: “Every American should view this development with alarm.”
Just after 2:00 a.m. eastern time this morning, the Senate confirmed Retired Air Force Lieutenant General John Dan Caine, who goes by the nickname “Razin,” for chairman of the Joint Chiefs of Staff by a vote of 60–25. U.S. law requires the chairman of the Joint Chiefs of Staff to have served as the vice chairman of the Joint Chiefs of Staff, the chief of staff of the Army, the chief of naval operations, the chief of staff of the Air Force, the commandant of the Marine Corps, or the commander of a unified or specified combatant command.
Although Caine has 34 years of military experience, he did not serve in any of the required positions. The law provides that the president can waive the requirement if “the President determines such action is necessary in the national interest,” and he has apparently done so for Caine. The politicization of the U.S. military by filling it with Trump loyalists is now, as Kendall writes, “indisputable.”
The politicization of data is also indisputable. Billionaire Elon Musk’s “Department of Government Efficiency” (DOGE) claims to be saving Americans money, but the Wall Street Journal reported today that effort has been largely a failure (despite today’s announcement of devastating cuts to the National Oceanic and Atmospheric Administration that monitors our weather). But what DOGE is really doing is burrowing into Americans’ data.
The first people to be targeted by that data collection appear to be undocumented immigrants. Jason Koebler of 404 Media reported on Wednesday that Immigration and Customs Enforcement (ICE) has been using a database that enables officials to search for people by filtering for “hundreds of different, highly specific categories,” including scars or tattoos, bankruptcy filings, Social Security number, hair color, and race. The system, called Investigative Case Management (ICM), was created by billionaire Peter Thiel’s software company Palantir, which in 2022 signed a $95.9 million contract with the government to develop ICM.
Three Trump officials told Sophia Cai of Politico that DOGE staffers embedded in agencies across the government are expanding government cooperation with immigration officials, using the information they’re gleaning from government databases to facilitate deportation. On Tuesday, DOGE software engineer Aram Moghaddassi sent the first 6,300 names of individuals whose temporary legal status had just been canceled. On the list, which Moghaddassi said covered those on “the terror watch list” or with “F.B.I. criminal records,” were eight minors, including one 13-year-old.
The Social Security Administration worked with the administration to get those people to “self-deport” by adding them to the agency's “death master file.” That file is supposed to track people whose death means they should no longer receive benefits. Adding to it people the administration wants to erase is “financial murder,” former SSA commissioner Martin O’Malley told Alexandra Berzon, Hamed Aleaziz, Nicholas Nehamas, Ryan Mac, and Tara Siegel Bernard of the New York Times. Those people will not be able to use credit cards or banks.
On Tuesday, Acting Internal Revenue Service (IRS) Commissioner Melanie Krause resigned after the IRS and the Department of Homeland Security agreed to share sensitive taxpayer data with immigration authorities. Undocumented immigrants pay billions in taxes, in part to demonstrate their commitment to citizenship, and the government has promised immigrants that it would not use that information for immigration enforcement. Until now, the IRS has protected sensitive taxpayer information.
Rene Marsh and Marshall Cohen of CNN note that “[m]ultiple senior career IRS officials refused to sign the data-sharing agreement with DHS,” which will enable HHS officials to ask the IRS for names and addresses of people they suspect are undocumented, “because of grave concerns about its legality.” Ultimately, Treasury Secretary Scott Bessent signed the agreement with Secretary of Homeland Security Kristi Noem.
Krause was only one of several senior career officials leaving the IRS, raising concerns among those staying that there is no longer a “defense against the potential unlawful use of taxpayer data by the Trump administration.”
Makena Kelly of Wired reported today that for the past three days, DOGE staffers have been working with representatives from Palantir and career engineers from the IRS in a giant “hackathon.” Their goal is to build a system that will be able to access all IRS records, including names, addresses, job data, and Social Security numbers, that can then be compared with data from other agencies.
But the administration’s attempt to automate deportation is riddled with errors. Last night the government sent threatening emails to U.S. citizens, green card holders, and even a Canadian (in Canada) terminating “your parole” and giving them seven days to leave the U.S. One Massachusetts-born immigration lawyer asked on social media: “Does anyone know if you can get Italian citizenship through great-grandparents?”
The government is not keen to correct its errors. On March 15 the government rendered to prison in El Salvador a legal U.S. resident, Kilmar Armando Abrego Garcia, whom the courts had ordered the U.S. not to send to El Salvador, where his life was in danger. The government has admitted that its arrest and rendition of Abrego Garcia happened because of “administrative error” but now claims—without evidence—that he is a member of the MS-13 gang and that his return to the U.S. would threaten the public. Abrego Garcia says he is not a gang member and notes that he has never been charged with a crime.
On April 4, U.S. District Court Judge Paula Xinis ordered the government to return Abrego Garcia to the U.S. no later than 11:59 pm on April 7. The administration appealed to the Supreme Court, which handed down a 9–0 decision yesterday, saying the government must “facilitate” Abrego Garcia’s release, but asked the district court to clarify what it meant by “effectuate,” noting that it must give “due regard for the deference owed to the Executive Branch in the conduct of foreign affairs.”
The Supreme Court also ordered that “the Government should be prepared to share what it can concerning the steps it has taken and the prospect of further steps.”
Legal analyst Joyce White Vance explained what happened next. Judge Xinis ordered the government to file an update by 9:30 a.m. today explaining where Abrego Garcia is, what the government is doing to get him back, and what more it will do. She planned an in-person hearing at 1:00 p.m.
The administration made clear it did not intend to comply. It answered that the judge had not given them enough time to answer and suggested that it would delay over the Supreme Court’s instruction that Xinis must show deference to the president’s ability to conduct foreign affairs. Xinis gave the government until 11:30 and said she would still hold the hearing. The government submitted its filing at about 12:15, saying that Abrego Garcia is “in the custody of a foreign sovereign,” but at the 1:00 hearing, as Anna Bower of Lawfare reported, the lawyer representing the government, Drew Ensign, said he did not have information about where Abrego Garcia is and that the government had done nothing to get him back. Ensign said he might have answers by next Tuesday. Xinis says they will have to give an update tomorrow.
As Supreme Court Justice Sonia Sotomayor recently warned, if the administration can take noncitizens off the streets, render them to prison in another country, and then claim it is helpless to correct the error because the person is out of reach of U.S. jurisdiction, it could do the same thing to citizens. Indeed, both President Trump and White House press secretary Karoline Leavitt have proposed that very thing.
Tonight, Trump signed a memorandum to the secretaries of defense, interior, agriculture, and homeland security calling for a “Military Mission for Sealing the Southern Border of the United States and Repelling Invasions.” The memorandum creates a military buffer zone along the border so that any migrant crossing would be trespassing on a U.S. military base. This would allow active-duty soldiers to hold migrants until ICE agents take them.
By April 20, the secretaries of defense and homeland security are supposed to report to the president whether they think he should invoke the 1807 Insurrection Act to enable him to use the military to aid in mass deportations.
LETTERS FROM AN AMERICAN
HEATHER COX RICHARDSON
#political cartoons#Matt Davies#The Big Chill#Heather Cox Richardson#Letters from An American#personal data#the right to privacy#identity theft#mistaken identity#SCOTUS#secretary of defense#homeland security#incompetence#data mining#data weaponization
15 notes
·
View notes
Text
I am so unbelievably pissed off. FUCK HOAs
Oh, my trash/recycling bin can't be visible except on pickup day? Ok whatever fine I hate you but I can deal with this
Weekly inspections?????? FU FU FU FU FU
SECOND NOTICE ALSO WE'RE CHARGING YOU MONEY TO SEND YOU CERTIFIED MAIL OF THIS TOTALLY LEGIT TOTALLY SECOND NOTICE OF WHAT IS ACTUALLY A VIOLATION cue me: checks notes. Hmm. My recycling bin was. on the curb. on recycling pickup day. You know. The day it has to be out. The day it is motherfucking ALLOWED TO BE FUCKING OUT AND VISIBLE.
so. 1) not a violation
I have sent them the trash AND recycling pickup schedules, which are DIFFERENT, btw
I have disputed the fact of the violation
I have disputed the linking of this "violation" to a previous violation MONTHS AGO--their "first notice" in this case was a "Courtesy Notice" LITERALLY 5 MONTHS AGO and they've done so many inspections since then and my bin CLEARLY WASN'T OUT IN THOSE INTERVENING MONTHS so WTMFH
So I am posting like a crazy person here instead of sending the absolutely deranged email I almost sent (I did send a slightly less deranged version with the disputes, and requesting a hearing)
OMG. It has been. Less than one hour since I learned this fun fun news. My bin was out YESTERDAY, y'all. YESTERDAY. I am going to blow a gasket
#it's a relatively privileged problem to have (omg i have a home truly i am grateful) but it's still a goddamned problem and i'm allowed#to fucking complain about it#in case it needs to be said#*rolling my eyes*#i advocate for free/actually affordable housing for everyone who needs it because we ALL deserve a safe secure stable home#whatever type of home that may be#it is absolutely goddamned ridiculous that megacorps can buy all the housing#rent it out at extortionate rates and evict people willy nilly#and we're talking about a “housing crisis” and not a “STOP LETTING CORPORATIONS AND BILLIONAIRES HOARD ALL THE HOUSING” crisis#goddamn.#ha elect me president (ahaha don't do this i am not a good public speaker) and I'll push congress to pass some really neat legislation#hey be more direct: elect me to congress (ahaha don't do this) and i'll WRITE some goddamn nifty legislation and yell about it as long and#as loud as i can until people start to just fucking say yes to make me shut the fuck up#(i know that's not how it works. again. don't actually elect me to a government position)#exemplia gratis:#No individual person shall own more than 6 homes UNLESS they pay a Housing Market Shrinkage Fee for removing viable housing from the market#why 6 and not 2? 2 is a lot! it's excessive! but having A vacation home shouldn't be a crime. Having 5 vacation homes is ridiculous and#awful and whatever but it's not likely to be the source of all our greatest “housing shortage” problems. no. I'm aiming for the absolutely#monstrously greedy and egregious motherfuckers who---ok#hang on. how many homes does the average min and max homeowner own? I would like to see data on that. but anyway#the next part of the legislation:#Homes owned >6 shall be charged X% Housing Market Shrinkage Fee UNLESS they are rented for affordable (15% or less than renter net income)#housing and are actively occupied by said renters. Rented out and charging more than 15% of renter's net? still gotta pay up.#EMPTY housing >6 shall be subject to an additional Y% Housing Market Shrinkage Fee (tax? should I call it a tax?) which increases with ever#month that the housing goes unoccupied. no one living in it? sell it rent it or pay the fuck up. and still pay the fuck up if you rent it#for way too goddamn much money#but like. less. we only REALLY hate you if you sit on empty houses that you don't even let anyone use#ok that's individuals. now onto BUSINESSES#ok so immediately it gets a little complicated cuz like presumably there's rental management businesses that don't own the rental propertie#that they manage BUT there are also companies that just outright own a shitfuckton of housing and THIS is the truly egregious monstrous sid
24 notes
·
View notes
Text
14 notes
·
View notes
Text
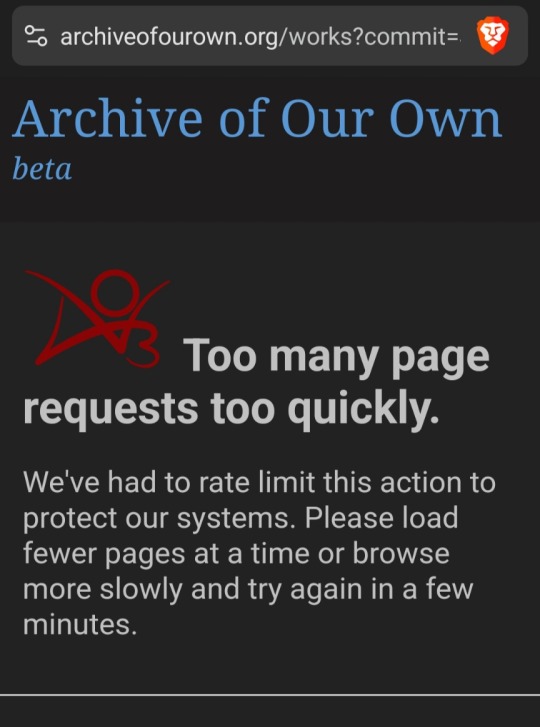
When your anti-bot algorithms make it impossible to use your website, you're defeating the purpose of having them.
When I first got this today, all I'd done was go to an author's page, find a work I'd finished reading (not on AO3) and bookmark it. Then did a wordcount sort on their works to see if they had any longfics.
None of that is an excessive amount of use, or an unusual way to use AO3 (other than the not reading fics on AO3 part, and I *really* hope that's not the "you're a bot!" trigger because I can't be the only person that reads offline for reasons of disability, preference, poor internet connection, whatever).
"Browse more slowly" what, am I supposed to throttle my internet and LARP as a fanfic reader in 2002? Relive the ole dial-up experience? Count to 10 before every click?
I probably wouldn't have bothered making a griping post for this but a friend mentioned having their Twitter account suspended yesterday because they were falsely detected as being a bot.
And it just makes me wonder--is that how Dead Internet Theory will kill the internet? Not by there being too many bots, but by all the real humans being blocked from using it? It's not hard to program variability into a bot--to make it not post at the same time every day, or to make its clicks randomized so there's not 5 seconds between every one.
It's ironically harder to do that for a human--who browses naturally and can't simply plug an RNG or different timer into their use. Who might post their art every day at 1230PM because that's when their lunch break starts and they're free to upload their morning doodles. Not because they're a bot scheduled to post every day at 1230pm.
#dead internet theory#ao3 issues#ao3 is down#ao3#archive of our own#fanfiction#op#personal#Don't tell me I'm being melodramatic#I'm just a naturally dramatic person (according to my partner) and these are my random musings#I can assure you I don't think the sky is falling or I'm banned from AO3 4evah or something#also my ao3 account is from 2011 and has 100+ fics posted over the years. you'd think that they'd#plug that kind of data in as a sort of “green flag” that a user account isn't a bot#like yes accounts get h4cked but they could just send an email of “hey there's suspicious activity on your account change your password”#and greenflag it again once it's secured#long post#rant
12 notes
·
View notes
Text
youtube
Congressman Dan Goldman today lit up House Republicans for holding a committee hearing on job training for cybersecurity positions in the federal government while President Trump and his unelected billionaire patron Elon Musk systematically slash the federal government’s effectiveness and actively endanger America’s cybersecurity and national security.
#rep dan goldman#rep goldman#elongatd muskrat#personal data breach#us government#oligarchy#dictatorship#cybersecurity#national security#us politics#united states#Youtube
9 notes
·
View notes
Text
two of the accused confessed in court today in the attempted blackmail of the schumacher family
#in case you missed it: a former security detail of the family tried to blackmail them for 15 million €#otherwise sensitive and personal data and photos would be released onto the darknet#the source is in german - sorry#michael schumacher#mick schumacher#corinna schumacher#f1#formula 1#schumi
10 notes
·
View notes
Text
had to get a new phone and im pretty sure setting it up is going to make me become the Joker
#i dont have the energy to elaborately rant rn but You Know What I Mean#it comes with almost 20GB of undeletable predownloaded bloatware and does not even have a notes app#and all the notes apps immediately available are either paid subscriptions (??)#or have a blatant security flag for collecting and third-party sharing personal data up to and including location (???)#this is going to affect the trout population
5 notes
·
View notes
Text
Donald Trump has threatened to go after a lot of people—journalists, political rivals and undocumented immigrants to name a few—and starting next year, he’ll have the entire national security apparatus at his disposal.
What’s the best way to keep your personal information secure from surveillance, not just by the government, but also data brokers, tech companies, and online scammers? Leah talks with WIRED business editor Louise Matsakis and security editor Andrew Couts about what to expect and practical tips for your phone, computer, and life.
Leah Feiger is @LeahFeiger. Andrew Couts is @couts.bsky.com. Louise Matsakis is @lmatsakis. Write to us at [email protected]. Be sure to subscribe to the WIRED Politics Lab newsletter here.
Mentioned this week: The WIRED Guide to Protecting Yourself From Government Surveillance by Andy Greenberg and Lily Hay Newman Anyone Can Buy Data Tracking US Soldiers and Spies to Nuclear Vaults and Brothels in Germany by Dhruv Mehrotra and Dell Cameron A New Phone Scanner That Detects Spyware Has Already Found 7 Pegasus Infections by Lily Hay Newman
Transcript
Note: This is an automated transcript, which may contain errors.
Leah Feiger: This is WIRED Politics Lab, a show about how tech is changing politics. I’m Leah Feiger, the senior politics editor at WIRED. Donald Trump is returning to the White House with a long list of grievances. We know he wants to deport millions of undocumented immigrants scattered across the country, that he’s vowed to go after journalists, and wants prosecutions of his political opponents. His allies in Congress are eager to roll back abortion and transgender rights, and there are calls, generally on the right, for a crackdown on left-leaning activist groups. As head of the national security apparatus, Trump will be in possession once again of a huge surveillance machine. It’s tempting to feel anxious about all of this, but there are a lot of compelling reasons to think about your cybersecurity that go way beyond what Donald Trump may or may not do. We wanted to do a little bit of a cybersecurity reset. What are the best practices for all of us, things that might protect us from a snooping government, internet scammer, or data collection company. Joining me to talk about the various ways we can protect our data is Andrew Couts, WIRED senior editor of security and investigations. Hey, Andrew.
Andrew Couts: Hey, great to be here.
Leah Feiger: And Louise Matsakis, WIRED senior business editor. Hey, Louise.
Louise Matsakis: Hey, it’s so great to be here.
Also On WIRED
Leah Feiger: Let’s kick this right off. This guide also exists on WIRED.com. You can click on the link in our show notes today. Who is this guide for? Why should people know how to protect themselves online?
Andrew Couts: The guide is for anybody who feels like they might be in a vulnerable situation from government surveillance, or it could include an abusive partner or anyone who really feels like they need to take extra steps to protect themselves. I would say entering these uncertain times of the incoming Trump administration, that's probably changing compared to how it was in the past few years or ever. It's really up to you as the reader or listener to read the guide, see if it applies to you, see if theres anything in your life that makes you feel nervous about it and take some steps to protect yourself.
Leah Feiger: Let’s talk about those specific people a little more. My dad listens to the show. Hey, dad. Should he be doing this? Should he be following the guide?
Andrew Couts: It’s really very subjective and so it might not apply to everybody, but there's really little downside to protecting yourself and taking extra steps to ensure that your privacy is secured as best that you can make it. I would say if you are an activist, if you're a political person publicly, if you are in a vulnerable community, the only downside is some inconvenience and having to make sure you’re on top of various settings and things. We tried to present our guide in a way that's on a sliding scale so you can mix and match what you think is appropriate for your life and for your risk level. It's not just government surveillance that this applies to, because we all know everybody's getting scam texts and calls all the time. It applies to that too because just because your data is safe with one of the apps you use, they could get breached and then that data is out there and it can be connected to all different types of information that's out there about you already, and it can make even people who aren't in the public eye or otherwise engaged in any behavior that might make them a target still vulnerable.
Leah Feiger: Let’s just take a quick step back for a moment and talk about some big picture information about how online surveillance currently works. It’s so integrated into our online experience. Like you said, how many times have I gotten messages that my apps have been breached, that this password is unsecure, it's a daily occurrence. Obviously, Louise, you're an expert on everything China. Andrew, you have been covering this for so long. Talk to me about this big picture. What are we actually even coming up against here?
Louise Matsakis: I think in the last few years it’s definitely gotten a lot worse. I think a lot of us are familiar with the experience of I want to buy a new pair of sneakers. I look at this pair of sneakers and then that pair of sneakers follows you around the internet everywhere. Suddenly you see it on your phone, you see it in your Instagram ads. The other day I had the experience of actually looking up a couch on Facebook marketplace, and then because my Facebook data is connected to my Instagram data, I started getting Instagram ads for couches and I was like, “Hey, Facebook.”
Leah Feiger: Incredible.
Louise Matsakis: “I can't afford a new $3,000 couch, which is why I'm looking for a used one.”
Leah Feiger: But thank you for waving it in my face.
Louise Matsakis: There’s also, I think, the most invasive form of surveillance in a lot of ways is location tracking. You're seeing advertisements based on your IP address, based on where you go every day. A lot of people have their Google history on, so Google knows literally what time you leave your house every day, what time you return, when you maybe go somewhere like Planned Parenthood or when you go to a protest and when you return from that protest. Often, a lot of times I encourage people to look at lawsuits when they want to see what data is available to law enforcement because you can see how your trove of text messages, iMessage, conversations going back sometimes maybe an entire decade between people end up being used as evidence. I think also it's good for people to know that sometimes protecting yourself can be inconvenient and make things a little bit harder, but it can also be nice and actually better for your life. I don't want to see those couches everywhere. I don't want to see those sneakers. Because I have a lot of my conversations now set to auto delete, I'm actually saving storage space and I don't really need those conversations from three months ago where I'm like, “Hey, I'm going to be five minutes late to have coffee with my friend.”
Leah Feiger: Well, you bring up such a funny point. I think when we're talking WIRED's Guide to Government Surveillance, like you said it has so many different levels to it. There's on one hand, yes, perhaps at some point if Kash Patel takes over the FBI, what does it look like for journalists and activists in this space? But then there's also the smaller, the day-to-day people should be allowed to do that too. Dad, if you're listening, get on it.
Louise Matsakis: Yeah, exactly. I think privacy is a virtue that permeates all aspects of society and it's worth protecting whether you are a vulnerable activist or whether you are Leah’s dad.
Andrew Couts: Part of the issue here is that everybody knows you’re getting tracked for ads and your location is getting tracked for various reasons and all these things, and I think it’s often put in the context of advertising or some commercial uses. I think the two big issues right now are one, all of that data can now be purchased by the government instead of getting a warrant. They're basically able to just go around the Fourth Amendment. This is happening, police are doing this, Immigration Customs Enforcement is doing this. We do a lot of stories at WIRED that are based on location data. The most recent one was one about a data broker who supplied more than 3 billion data points on people in Germany. Why Germany matters to people in the US is that we have a lot of military installations and intelligence installations there. We were able to looking at the raw data, you could just literally track someone from a bunker where our nuclear weapons are stored to a brothel where they go after work, to their home and see their commute every single day.
Leah Feiger: Everyone go check the story out on WIRED.com. It's an amazing real life example of how this all is at play, but it’s crazy.
Andrew Couts: It’s crazy. I think the issue is that we just don’t know how this data is going to be used in the future. I think part of the issue here is just continued exposure that can lead to unintended consequences. So you might think you’re not vulnerable right now. We just don’t know what the future holds or how this data can be repackaged, shared, leaked, anything. Anytime your data is such sensitive data about where you go every single day or what websites you’re looking at, what apps are on your phone, all this stuff that might be used just to serve you an ad for a couch could also be used to embarrass you publicly or track you and surveil you in other different ways. I think it’s really important for people to understand that none of this stuff is happening in a bubble. It is all very porous in terms of who can get access to this data anywhere from a data broker who might just be a guy in his office in Florida, like one dude with a couple of computers. There’s a lot of data brokers out there and there are a lot of ones that are just some random person who has massive amounts of information on you, to the FBI or ICE or whoever it might be.
Leah Feiger: Let's talk about what you guys do. How do you lock up your cybersecurity? Do you use flip phones? What is your cloud storage? Are you only on Signal? All of these things I'm referencing by the way in the WIRED guide, go check it out. Where are you guys at?
Louise Matsakis: I have most of my conversations on Signal and I have the vast majority of them set to delete every four weeks. I find that that’s a good timescale for normal everyday conversations and then more sensitive conversations delete sometimes in as little as a few hours or a few days. Very rarely have I found that this is inconvenient for my life. Sometimes I ask a friend like, “Hey, that cool Airbnb, you stayed in that I know you already dug the link up to. Can you send that to me again?” But that's a pretty minor.
Leah Feiger: Small price to pay.
Louise Matsakis: Yeah, small price to pay. I'm really careful about location tracking and then usually-
Leah Feiger: So you are not active on Find My Friends?
Louise Matsakis: No. Although I do track my Boomer mom.
Leah Feiger: Sure.
Louise Matsakis: Yeah. Who won’t listen to this podcast, so sorry mom, I am tracking you. She knows this.
Leah Feiger: The big reveal, actually.
Louise Matsakis: Yeah, but I actually don't let her.
Leah Feiger: It’s the Louise Global Surveillance blog.
Louise Matsakis: Yeah, don’t let her track me back though. That’s my business. But when you get over the age of 70, your kid is allowed to see where you’re going.
Leah Feiger: Absolutely, amazing. Yeah.
Louise Matsakis: But I don’t use location tracking. I turn location tracking off for most of my apps and then I have a separate blank device and sometimes I bring that depending on where I’m going, particularly when I'm going to mainland China.
Leah Feiger: Yeah, I was going to ask, because you do reporting trips, you have sources all over the place. Are you bringing air gap devices? Is your work computer coming with?
Louise Matsakis: I usually will not bring my work computer. I'll bring a personal computer that doesn’t have very much information on it and I will bring a blank cell phone. I'll put various Chinese apps on that phone that I don’t really want. I don't really want WeChat just hanging out on my normal device for the most part. But those are pretty above and beyond precautions that I don't think the average person needs to take. But I think just making sure, do you really need 30 apps on your phone having your location? Because to Andrew's point about all of these data brokers, a lot of the time they're getting this location information, not from Google necessarily, or not from Facebook, not from these big companies that they don't need to sell that information. It’s literally often the game you downloaded and you forgot about. It's like the silly Candy Crush knockoff.
Leah Feiger: Oh God, I'm screwed. Yeah.
Louise Matsakis: Yeah, it’s worth just looking at those sort of apps that you forgot about and realizing, “Oh, all of these applications have particularly your location information.” Those are the two things that I prioritize is ensuring that it’s not just protecting my data, but I don't have that data. If my device gets seized, it’s like those conversations are just not there. You only see the last few weeks at the most, and in most cases maybe you see that that person's contact is in my phone, but you have no idea what we talked about because that data has been erased and Signal is also end-to-end encrypted. It’s not being stored on a server somewhere where a court could make a subpoena for it or cops could try and get a warrant for it. Those are my two big things. There are a lot of other things you can do, but I think for the average person who knows where you’re going and what are your conversations and where are they and how they being stored and do you want to keep them all the time?
Leah Feiger: Absolutely. Absolutely. Andrew, how about you?
Andrew Couts: Yeah, I would echo basically all of those, though I'm not going on cool reporting trips to China, so that’s outside my knowledge. But just to reiterate on the apps, I would say one thing I do is I just limit the number of apps that are on my phone and I don't ever download ones that are just, there's no need for it. I'm not going to download the McDonald's app or something. There’s things that might be a little bit convenient, but McDonald’s doesn't need to have an app on my phone all the time.
Leah Feiger: OK, so talk me through that though, because I’m with you. I’m totally with you. What’s wrong with having these extra apps on your phone?
Andrew Couts: It really just depends on the specific app, but if they get access to your phone book, they can do contact mapping. If they get access to your location, obviously they can do behavior mapping so they can see what other stores you’re going into and just mapping out what your behaviors are, what your activities are. Usually, that’s just to sell you more stuff.
Leah Feiger: Which as Louise points out, you don’t have to have that either in your life.
Andrew Couts: Right, exactly. There’s just no reason for them to have any data about me, to Louise’s point that just the data shouldn't exist in the first place. I try to limit the number of apps. I also am very diligent about making sure my location settings are all up to date. Just nothing can track me unless I’m using the app and for a mapping app or can’t track me at all if I’m... Not to endorse Apple, but I use an iPhone, it has a lot of really good privacy features that people can take advantage of. Some of them make your life slightly less convenient, but I’d say the trade-off is well worth it. The most important... I’d say the one thing anybody can do to protect their privacy most is to use Signal and to get everyone they know to use Signal. I would say obviously there are benefits to protecting your conversations, but if you are thinking, “Well, WhatsApp also uses the Signal protocol,” if you’re into that nerdy stuff about how this encryption works, that’s true, but WhatsApp also collects all the metadata. I would highly recommend Signal over any other encrypted app that’s out there at the moment. Then I just try to limit what I'm doing on my devices that I think might be sensitive. I also, I think financial privacy is also really important and so I try to use cash on a regular basis. Obviously, it’s not very convenient.
Leah Feiger: Really?
Andrew Couts: Yeah, I do it for-
Leah Feiger: This is a new fact. I’m learning about you right here, right now. Everything else I could have predicted.
Andrew Couts: Well, just on the daily shopping and things like that, that when it's convenient for me to do it, I can’t do that through Uber or something. I don’t use Uber really, but I'm here in San Francisco this week, so I am. I’m going to delete the app as soon as I get to the airport, but around town grocery shopping and shopping for my dogs, I’ll use cash if I can because it’s still really private and it’s more private than cryptocurrency. It’s more private than anything at this moment.
Leah Feiger: Interesting. You guys haven’t mentioned the one thing that I’m personally a bit obsessed with, so maybe I’m actually wrong, so tell me if I’m wrong. I love my DeleteMe. DeleteMe, for everyone by the way, just is, how do I even describe it? It's a subscription tool to purge your information from data brokers.
Louise Matsakis: Yeah, so what they do is there’s a lot of these sometimes they’re referred to as people look up sites and they’re basically these databases of... Sometimes they're actually scraping courts, so it will literally show when you filed for divorce, even if you can't see the actual court documents and it will show often your address. Sometimes they make family trees so it will show Leah is related to her dad and they both lived at the same address or whatever it is. It’s really sensitive information and there are services DeleteMe. There are other ones that will on your behalf will send a request saying like, “Hey, you need to take my data down.” I think that this is a really good thing that you bring up and it's really important because one of the most sensitive pieces of information about you is where you live, right, where you sleep every night. If you are an activist, if you are somebody who's posting a lot of things on the internet, if you are making other people mad, it is fairly likely that you might encounter somebody who is so mad at you or detests you so much that they want to know where you live. I’m not saying that people are going to necessarily come and show up at your house, but it’s really scary.
Leah Feiger: Absolutely.
Louise Matsakis: I've had this experience where people are saying, “I know where you live, this is your address,” and that is a very common form of harassment and there have been plenty of documented cases where people do show up. I think protecting that information is important and that’s obviously something that is not easy to change. Sometimes people just open a new email address because they’ve gotten too much spam to their old one, but it’s really hard to get a new apartment or buy a new house or whatever it is.
Leah Feiger: I would also say not even just people that are active online or making their opinions known or hated. You could work at a nonprofit and wake up the next day that a woman’s health organization that perhaps actually doesn't have that much to do with abortion and you and your colleagues are on blast from far right?
Andrew Couts: Absolutely. I think DeleteMe is a great service and it’s one that obviously it costs some money so not everybody is able to afford it, which is unfortunate, but if you can, I highly recommend it. I think other steps you can take just nuts and bolts. You can use a VPN to protect a lot of your information while you’re online. There are a lot of caveats to that. A lot of VPN companies are bad in the ways that we’re talking about here about data brokers or whatever else they have access to everything you’re doing online, so do your research on that. The Freedom of the Press Foundation has a great guide to how to figure out which VPN is good for you. The other thing is just make sure you’re not posting where you’re at on social media. If you’re going to post about being at a concert, maybe think about posting it after the concert is over or when you're not in that area, because to Louise’s point, we’re talking about government surveillance or threat actors or whatever these high-minded things. But a thing I’m nervous about is going into this new era of polarization, hyper-political ideas is that vigilante justice and people thinking there’s supposed to go after you because you made them mad about something, about anything. If they find your address, if they find all your contact information, etc. That can be extremely scary. Another thing I would say to do is if you want to protect your anonymity, definitely don’t use the same username on various different platforms. Don’t use the same email address, don’t use your phone number connected to apps if you can avoid it. All these things can be pieced together, especially when there’s a data breach and it's relatively trivial to do that. There are tools out there that make searching that information very easy. Anytime you can obfuscate your online identities, that's a very good thing to do just in the long-term.
Leah Feiger: We got to bring this into our current political situation here. We're obviously all gathered and talking about this for a very specific reason. Trump has threatened to go after government staffers who leak information to journalists. He’s threatened to go after journalists, he’s threatened to go after political enemies and he’s gone after journalists communications in the past. How can people prevent the government from reading their texts and emails?
Louise Matsakis: Under a regime that is concerned about retribution, it's hard. Again, I go back to do not have the data in the first place. When I've talked to sources, don't be on your company's Wi-Fi, do not forward emails, do not forward text messages, use a different device if you can take a picture of that email on your cellphone network, not on the Wi-Fi that your computer is connected to and send that over Signal. Then have that message auto delete, right? I think it's about when the government says, “Hey, produce this information,” the best thing to say is, “I don't have that information. That information does not exist.” Also, I think it’s important for people to realize if you’ve never been in this situation before, they’re not coming to you necessarily. They’re coming to the providers that you use like Google, like Facebook, like WhatsApp, and they are legally required or compelled to provide this information. In most cases they do and sometimes they do it extremely quickly. If the government can prove that there is an emergency, and in most cases this is good, right? When a mass shooter is on the loose, it’s good that Facebook provides information that might help them catch that person. There’s a reason that these mechanisms exist, but under a regime that is not concerned about constitutional rights and that is going after their perceived enemies, these protections can become weak. I think it’s about just not having that data to produce is the best thing you can do and to use services like Signal that are end-to-end. Because in that case when the government says, “Hey, Signal provide this information on Louise and Andrew.” Signal can't access it, they do not have it. Their response is, “Sorry, our technology does not allow for you to compel us to provide this information.”
Leah Feiger: Meredith Whitaker, what a goddess.
Andrew Couts: I would just add obviously encrypt everything you possibly can. iCloud backup can now be encrypted. iMessages are also end-to-end encrypted as are FaceTime audio calls. I don’t know a lot about Android, I’m sorry. I’m sure that there are comparable features on Android platforms. Look it up, find out what you can do on those. Just limit using the cloud as much as possible. To Louise’s point that anytime a company is storing something for you, that’s who some the authorities are going to go to. One other Apple feature is lockdown mode, which is specifically for vulnerable people. It will lock down a lot of the sharing or collecting of this data that we’re talking about being sensitive across the entire device. That’s another way of just not making that data exist. If you need to get a different device to use it, that’s certainly an option. I would say if you are thinking about getting a burner phone, you have to be very, very diligent with that. You can never have it connect to your home Wi-Fi network, for example, or connect to your office Wi-Fi. That information then makes you more vulnerable and can expose you. The last thing I would say is if you’re just getting started to thinking about what your risk levels look like and what your digital privacy hygiene looks like, all the information before now is already out there and so you can’t really control that. Whatever’s been collected on your life up until now can probably be accessed by someone somewhere, so factor that in. That doesn't mean give up, it doesn’t mean it’s not worth doing anything, but it’s definitely something you just need to be aware of that if you’re just starting now, you’re going to be safer, but you're not necessarily going to be bulletproof going forward.
Leah Feiger: I feel bananas even having to talk about this because obviously your government should be protecting you. One of the things that I feel like we’ve all just been beating the drum on recently is the PRESS Act, which would protect journalists from government spying and it has a lot of bipartisan support and passed in the House, but it’s currently held up in the Senate. Senate Democrats have been slow walking it. How do you recommend that people hold these things at once? This is a very broad question of your government should not be doing this to you and simultaneously it may be, and thus you have to take these steps.
Louise Matsakis: I think it’s unfortunate, but this is the way that it works in most parts of the world. It shouldn’t be that way and I think it’s good to be idealistic, but I think it’s important to remember that America is not special and this is how governments behave. This is how law enforcement behaves, and that if you accept that and think of it as the norm, not that you shouldn’t fight, but that it’s worth considering that. However, in other ways we are really behind. We do not have a national privacy law. We have a patchwork of protections in certain states like California where we all are currently, which is great, but it’s a real shame. I often say this and it surprises a lot of people. There are more consumer, important to say consumer, but there are more consumer privacy protections in China than there are in the U.S. That is a shame. That is something that we should be ashamed about and that should be changed. But I think day-to-day it’s just good to be pragmatic and to know that law enforcement’s going to be law enforcement, the government’s going to be the government, and it’s just worth having a default. I think having these things be set in a way that you don’t have to think about it every day and that these conversations are just deleting. I’m just using this email service that’s end-to-end encrypted. I have my DeleteMe subscription that I only need to renew once a year, that makes it a lot easier. I think paranoia is very emotionally draining and you don’t want to be in a position where you’re constantly worried and you're constantly paranoid. I think when you use these things and you set it and forget it, you can feel more empowered to live your life the way you want. Then the conveniences of not being tracked, of not seeing the catch all the time, of not.
Leah Feiger: The Autonomous couch.
Louise Matsakis: Not having to pay more for cloud storage every year because you’re not putting as much data into the cloud. These things compound over time and then you just have a nicer digital life. That’s what I want people to have.
Andrew Couts: I think during the first Trump administration, we became glaringly aware of the difference between laws and norms. I think the PRESS Act is a great reminder that there are still more norms out there that can be pushed aside. That’s what that law is attempting to do is to make it a law that you can’t do certain activities of surveillance and targeting of journalists that are at the moment just rules in the book. For example, the FBI has policy that they’re not going to prosecute journalists for publishing stories about classified information, but that's just a rule. If-
Louise Matsakis: It’s not a law.
Andrew Couts: It’s not a law and that can just be brushed aside and there’s other protections like that and I think we’re going to become aware of more that we haven’t even thought of at this moment. I wish we had a national privacy law. I wish we had better press protections that weren't based on agency rules, but there’s only so much we can do and we have to operate in the reality that were entering. A thing you can do to protect yourself is all the things we’ve been talking about here, but you can also vote, support legislation that comes up in Congress, be politically active in a way that supports your ideals and that protects everybody, including yourself.
Leah Feiger: On that note, we’re going to take a quick break and when we're back more on surveillance in the age of Trump 2.0. Welcome back to WIRED Politics Lab. We've been talking about a lot of the different ways that the government can track us and these apps are bad and encryption is good, and having everything off of our phones and computers is also good. I think we need to talk a little bit about some of these tech companies and these apps that we’re using. Perhaps a way into that is all of these tech CEOs that have been congratulating Trump and kissing the ring. Does that give you any additional concerns when it comes to our conversations about cybersecurity?
Louise Matsakis: I think there’s two things. One is more of just a vibe shift, which is that I think a lot of these CEOs saw what happened during the first Trump administration and saw how he could fly off the handle and start tweeting about them. I think that they realize that he responds really well to flattery. I think you’re seeing a lot of CEOs just going and kissing the ring. They want to ensure that their businesses are protected and there’s a lot less standing up for principals, a lot less of the resistance. The second thing about corporations since the first Trump administration is that you've seen a lot more companies get into the advertising business. Amazon has an enormous advertising business now. Uber is now in the advertising business. I see ads in the Uber app. Even some of these new AI companies such as Perplexity, they said they're going to get potentially into the ads business as well. Another shift is that a lot more people are having really extensive conversations with chatbots, with things like ChatGPT, which is another place where you can not have your conversation save. I don’t think we've seen necessarily a case yet of OpenAI, or maybe not at least a high profile one, getting a subpoena for this information from their users, but it could happen if you're asking ChatGPT sensitive things. That’s the other shift is that it’s some of the kinds of data being collected and who is collecting it have changed. Advertising is really high margin business, so a lot more companies want to do it on top of their core business. I think considering that, that there's more companies that are hungry for your data than there were before, and that we are now in an environment where there is, I think, less appetite from corporations to push against things that the second Trump administration might do because I think they realize that this is an unpredictable guy who they can just be nice to and get what they want.
Leah Feiger: Oh, depressing.
Louise Matsakis: But yes.
Andrew Couts: The kissing of the ring thing, that seems just like what I would expect CEOs to do to protect their businesses above any other principles. I’m more concerned about what the internal policies are going to be and the norms that we've taken for granted from these companies. For example, many companies Google, Twitter, or X now rather, release transparency reports. They tell you how many subpoenas they get, how many they’ve fought, how many they’ve responded to, and we might not see as many of those. X, in particular, is one that we have to be especially cautious of because if you have the X app on your phone, it’s going to be collecting data about you regardless of whether you log on or not. Regardless of what you think about the discourse on X at the moment, that’s secondary to what the back end app is going to be collecting.
Leah Feiger: Right, especially when it’s CEO and owner are very involved in the administration.
Andrew Couts: Exactly. There’s no mystery to what Elon Musk is going to do with your data if he decides that he wants to do something with your data. He's fully within his right to do that, that’s his data basically.
Leah Feiger: Yes, we all gave it to him willingly.
Andrew Couts: Yeah, exactly.
Leah Feiger: This feels like a dumb question, but what does Trump want with your data?
Louise Matsakis: I think it depends a little bit on who you are, but I think throughout this campaign, Trump has made it extraordinarily clear that he feels like he was an enormous victim during his first administration and that he was prosecuted by the press, by the DOJ, by the FBI, by lawmakers. I think he is very eager to go after those people. Part of that process is seeing who were you talking to, who provided that information to those journalists that he hates and wants to get revenge upon. What were their conversations like? Who was talking to them? I think it’s personal in a lot of ways, but even if he can’t get a conviction, or even if a judge doesn’t want to go along with Trump’s antics or some of the checks and balances in our system do hold up, these things take so much time and a lot of what authoritarianism is about and what makes it so dangerous is that it throws a wrench into everything. It derails activists, derails journalists, derails opposition lawmakers from just getting things done. Even if people are not thrown into prison, it’s being harassed all day, having to appear in court over and over again, having to spend all of your money on legal fees, having a bunch of Trump’s allies harassing you all day. That is really exhausting and that is sort of the point. Even if they’re not able to get the data identifying you, targeting you and trying to get it, and the fear that that creates is enough to accomplish their goals.
Andrew Couts: It doesn’t even have to be anything more than your name and putting that out there publicly for you to be targeted by any number of people. We saw Kash Patel release a list of people in government who he considered enemies. Your life can be really upended just by, if Donald Trump sends out a tweet that says, "Andrew Couts is a piece of shit," that's enough to make my life chaos.
Leah Feiger: Let's get into one specific example that obviously we talk a lot about at WIRED and are quite familiar with, Pegasus. Biden signed an executive order keeping this incredibly sophisticated spyware called Pegasus, that’s been used against activists and journalists around the world. Biden signed an order banning it in the US. Do we think that ban is going to hold?
Andrew Couts: Absolutely not. That's one that’s going to go away immediately. We’ve already seen ICE... Wire broke the news that ICE purchased a different spyware or tried to, and that was immediately under review from the White House as soon as we reported that news. That’s the mechanisms that are protecting us at the moment. That can just be brushed aside literally with a stroke of a pen. I would say spyware is still a big problem. Apple’s done a lot to try to combat it, but we’re seeing... We published a story today about, there’s a company that creates a free and paid tool that can scan your device, and they've already found seven Pegasus infections, which may not sound like a lot, but in that of I think 2000 customers, something around that. But that’s a lot. It is a targeted malware that exposes everything on your phone. We talked a lot about singing the praises of Signal, but if you're infected with spyware, that just goes out the window. It’s all there, your camera can be turned on remotely. Your microphone can be turned on remotely. Everything on your device is accessible to whoever's infected you. If you’d asked me a year ago, "Should people be concerned about being targeted by spyware?" I'd say not unless you are doing some highly controversial political activism or a journalist publishing national security secrets, but now it's good to check, maybe download the free tool and just get checked out every so often.
Leah Feiger: Yikes. Big, yikes. Obviously, we talked about policy solutions. I mentioned the PRESS Act earlier. A lot of journalists and First Amendment advocates have been calling on the Senate to pass it or do something, anything. Obviously, it's stalled right now. Trump on Truth Social on November 20th posted, "Republicans must kill this bill." Before that, it had bipartisan support. What effect do you think that comments like Trump, not just about the PRESS Act, but about this entire apparatus at the moment could affect us going forward the first couple hundred days? Any thoughts, any predictions there?
Louise Matsakis: I think we’l probably see potentially fewer leaks than we did in the first administration. There was a lot of activity immediately from a lot of different agencies raising concerns about really disturbing behavior in all parts of the government as Trump took over, problems about a lot of different types of programs in every major agency. But I still believe in people who want to do the right thing and who see something that is concerning to them and wanting to stand up and to say something about it. There are still safe ways for them to generally keep their anonymity protected and to be able to talk to a journalist about what they're seeing. I think you'll still see some of that, but I think there’s going to be a lot more concern and that will keep a fair number of people quiet. I think journalists are going to have to get more creative about trying to figure out what’s going on inside the government.
Andrew Couts: Yeah, it’s hard to know what the priorities of the Trump administration will be, but we do know that mass deportations are at the top of that list. I think the blast radius we will experience from whatever that looks like is going to catch up a lot of people you might not expect, necessarily. The obvious things that could happen is if people start reporters who are covering that or activists who are speaking out against it could then be deemed national security risks, which give a lot more leeway for the government to target you or to take additional actions that circumvent some of the protections that are otherwise in place when it’s not a national security issue. We talked about norms versus laws earlier, and I think that’s where we're going to start to see the chasm between those two realities. It may not be sweeping arrests of every reporter at the New York Times or WIRED or wherever, but it might just be one. That has a chilling effect immediately. Everyone is going to be more concerned about their role in public life and in confronting the Trump administration about whatever it’s doing. I would say cracking the whip very quickly, whether it’s on immigration and then everything surrounding that, it seems to me a likely scenario.
Leah Feiger: Listeners, you can find many more of WIRED’s cybersecurity recommendations online, just look for the link in today's show notes. We'll be right back with Conspiracy of the Week. Welcome back to WIRED Politics Lab. It is time for my very favorite segment of this show, which is Conspiracy of the Week, where our lovely guests bring their favorite conspiracies they've come across as of late or generally. I pick my favorite. Louise, what do you have for us today?
Louise Matsakis: I have a fun one. It's a little bit of a local story. I live in Los Angeles, and if you haven't been there, you might not know that in downtown LA there are tar pits, literally these giant puddles of tar that smell bad. They have been there literally since prehistoric times.
Leah Feiger: Wait, really? I've been to LA so many... This is new information.
Louise Matsakis: Yes, there is a tar pit park, and then there is a museum where actually they have a lot of the stuff that has been pulled out, so-
Leah Feiger: Oh my gosh.
Louise Matsakis: We’re talking like full woolly mammoths.
Leah Feiger: Wow.
Louise Matsakis: There’s an entire wall of, I don’t know what they're called, but it’s an ancient wolf basically. I’m not sure what the species is, but all of their skulls, because basically for hundreds, thousands of years, animals would just walk by and fall into them.
Leah Feiger: Oh my God.
Louise Matsakis: To date, they’ve only found, or so they say, one person who’s fallen in, and it was a prehistoric woman and her dog, but the-
Leah Feiger: Prehistoric women had dogs?
Louise Matsakis: Yeah.
Leah Feiger: I have so many questions.
Louise Matsakis: Yeah. I'm sure the exact time period, it was a very early pet owner.
Leah Feiger: Yes.
Louise Matsakis: But the conspiracy that I’ve heard around LA is that the government is putting things in the tar pit. They're putting people-
Leah Feiger: To cover it up. Of course.
Louise Matsakis: Yes. They’re putting people in the tar pits and it’s like they know that they won’t be lifted out and that the archeologists who work there who are still excavating are in cahoots with the government to keep things in the tar pits.
Leah Feiger: OK. I have the dumbest question ever. In my mind, because obviously I grew up watching cartoons, putting stuff in tar. It’s like gooey.
Louise Matsakis: It is gooey.
Leah Feiger: How do you excavate that? What does that even entail?
Louise Matsakis: I am not an archeologist.
Leah Feiger: Fair enough. How are they pulling out their political enemies, I suppose is my question?
Louise Matsakis: Yeah. Well, I think that’s the thing is that they're keeping them in there.
Leah Feiger: They’re keeping them in there.
Louise Matsakis: But I’m not sure. It’s been a very long effort, but I'm not sure over the years how they’ve gotten all of the bones out and stuff, but they're very preserved so that part of the is like-
Leah Feiger: A little Pompeii action.
Louise Matsakis: Exactly. A little Pompeii action and that maybe one day when it’s safe to talk about what happened. We know that the bodies are there and we know that the information there.
Leah Feiger: I am so obsessed. If these tar pits were in New York, the mafia would’ve just dumped all of lower Manhattan into this.
Louise Matsakis: I guess it just takes a while to sink.
Leah Feiger: Godfather part four would’ve been a very different film.
Louise Matsakis: I think it takes some time to sink though, so that’s the thing is-
Leah Feiger: I want to go chuck stuff in there now. I didn't know this was a thing.
Louise Matsakis: You can literally see them and there's literally just a cone that it's like, "Don't go over there and be like, don't get your foot in the gear."
Leah Feiger: This is what I’m going to do. I’m going to go throw all of my non-encrypted devices into LA’s tar pit, a WIRED field trip. This was an incredible conspiracy. Andrew, can you top that?
Andrew Couts: I cannot. That’s amazing. My conspiracy is less fun, and it’s not even a conspiracy yet, but we’re recording this on Wednesday morning. The CEO of UnitedHealthcare was shot in Midtown Manhattan, and obviously gun violence is a daily occurrence in America, but such a brazen attack in the middle of Manhattan is just baffling.
Leah Feiger: Blocks away from Times Square.
Andrew Couts: Yeah. It is. If you’ve been into Manhattan, this is extremely wild, and I haven’t looked at the news since we’ve been recording this, so they may have already caught the guy, but regardless, just because of all the politics around healthcare. There was a big ransomware attack against a subsidiary of UnitedHealthcare that they paid $22 million to the ransomware gang that did it. It’s a very complicated thing, but there’s already some conspiracy theories swirling around that it’s like ransomware gang or whatever. I think it’s more likely something completely separate from that, but regardless of what it is, it just feels so wild that people are going to be talking about this forever. Regardless of what the facts come out.
Leah Feiger: Oh, a hundred percent, we’re going to log off and it’s thousands of conspiracies will have popped up in the last hour.
Andrew Couts: Indeed.
Leah Feiger: Wow. All right. Well, that’s still a good one because it’s, as you said, just truly bananas. I got to give this one to Louise. I'm obsessed with LA’s tar pits.
Louise Matsakis: Highly recommend if you ever come visit.
Leah Feiger: I'm going to the museum.
Louise Matsakis: Yeah, it’s a really fun thing.
Leah Feiger: That’s good stuff. That was really good. Thank you both so much for joining us today for this terrifying but really informative conversation.
Louise Matsakis: Thank you so much for having us.
Andrew Couts: Thanks for having us.
8 notes
·
View notes