#surveillence state
Explore tagged Tumblr posts
Text
Person of Interest (2011-2016)
#person of interest#cyberpunk aesthetic#hacking#graphic design#surveillance#science fiction#surveillence state#hackers#cybersecurity#scifi#mobile hacker#code breaker#data manipulation#network security#infosecurity#10s#command line
81 notes
·
View notes
Text
Link to bypass paywall if necessary
14K notes
·
View notes
Text
🗣️ This is for all new internet connected cars
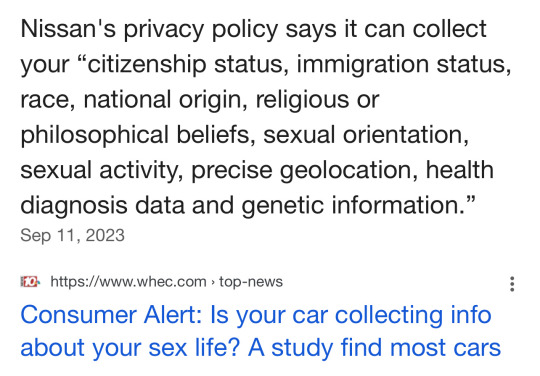
A new study has found that your car likely knows more about you than your mom. That is disconcerting, but what’s even more so is what is being done with your information. It’s all about the Benjamins. Our private information is being collected and sold.
The Mozilla Foundation, a non-profit that studies internet and privacy issues, studied 25 car manufacturers. And it found every manufacturer sold in America poses a greater risk to your privacy than any device, app or social media platform.
Our cars are rolling computers, many of which are connected to the internet collecting information about how you drive and where. New cars also have microphones and sensors that give you safety features like automatic braking and drowsy driver detection. Those systems are also providing information. Got GPS or satellite radio? Then your car likely knows your habits, musical and political preferences.
Did you download your car’s app which gives you access to even more features? Well that also gives your car access to your phone and all the information on it.
The study found that of the 25 car brands, 84% say they sell your personal data.
And what they collect is astounding.
One example the study sites is KIA’s privacy policy. It indicates the company collects information about your sexual activity. I initially didn’t believe it until I pulled KIA’s privacy policy and read it. And it’s right there in black and white. It says it collects information about your “ethnicity, religious, philosophical beliefs, sexual orientation, sex life, or political opinions.

And it says it can keep your info for “as long as is necessary for the legitimate business purpose set out in this privacy notice.”
Translation: Nissan can keep your information as long as they want to. And more than half of the manufacturers (56%) say they will share your information with law enforcement if asked.
(continue reading) more ↵
#politics#data mining#smart cars#spyware#privacy rights#surveillance state#new cars#big brother#nissan#kia#connected cars#consumer alert#panopticon
9K notes
·
View notes
Text
He sees you when you’re sleeping
He knows when you’re awake
He knows if you’ve been “bad” or “good”
Santa’s the surveillance state
1 note
·
View note
Note
As cameras becomes more normalized (Sarah Bernhardt encouraging it, grifters on the rise, young artists using it), I wanna express how I will never turn to it because it fundamentally bores me to my core. There is no reason for me to want to use cameras because I will never want to give up my autonomy in creating art. I never want to become reliant on an inhuman object for expression, least of all if that object is created and controlled by manufacturing companies. I paint not because I want a painting but because I love the process of painting. So even in a future where everyone’s accepted it, I’m never gonna sway on this.
if i have to explain to you that using a camera to take a picture is not the same as using generative ai to generate an image then you are a fucking moron.
#ask me#anon#no more patience for this#i've heard this for the past 2 years#“an object created and controlled by companies” anon the company cannot barge into your home and take your camera away#or randomly change how it works on a whim. you OWN the camera that's the whole POINT#the entire point of a camera is that i can control it and my body to produce art. photography is one of the most PHYSICAL forms of artmakin#you have to communicate with your space and subjects and be conscious of your position in a physical world.#that's what makes a camera a tool. generative ai (if used wholesale) is not a tool because it's not an implement that helps you#do a task. it just does the task for you. you wouldn't call a microwave a “tool”#but most importantly a camera captures a REPRESENTATION of reality. it captures a specific irreproducible moment and all its data#read Roland Barthes: Studium & Punctum#generative ai creates an algorithmic IMITATION of reality. it isn't truth. it's the average of truths.#while conceptually that's interesting (if we wanna get into media theory) but that alone should tell you why a camera and ai aren't the sam#ai is incomparable to all previous mediums of art because no medium has ever solely relied on generative automation for its creation#no medium of art has also been so thoroughly constructed to be merged into online digital surveillance capitalism#so reliant on the collection and commodification of personal information for production#if you think using a camera is “automation” you have worms in your brain and you need to see a doctor#if you continue to deny that ai is an apparatus of tech capitalism and is being weaponized against you the consumer you're delusional#the fact that SO many tumblr lefists are ready to defend ai while talking about smashing the surveillance state is baffling to me#and their defense is always “well i don't engage in systems that would make me vulnerable to ai so if you own an apple phone that's on you”#you aren't a communist you're just self-centered
620 notes
·
View notes
Text
you just can't mysteriously disappear for a significant length of time only to eventually turn up years later staggering down a highway covered in blood and dirt and muttering to yourself incoherently without ever actually explaining what happened to you during that time you went missing anymore
#🐉#because of woke#[remembers the concept of the surveillance state] oh. thats not very woke actually.
3K notes
·
View notes
Text
One of the biggest reasons to not retcon Neil Gaiman's work is, quite simply, that it lends itself to media censorship.
If we start leaning into all of the "clues" in his work, the precedent we're setting is that people who write those same things are thus also to be suspected as abusers. And that in turn makes authors not want to write complex narratives and characters, but will make publishers refuse to take up these books because they fear the potential fallout, either from readers, from potential survivors, or both.
This all comes back to the whole anti/proshipper" thing I've already posted about - fiction can not single-handedly make you an immortal person, and by extension fiction also can not single-handedly express the morals of it's writer. Humanity is too complex to ever be summed up or swayed by a single piece of media.
Neil has made some vile, immoral decisions. That does not inherently make his books vile and immoral by association. There is no secret tell for who is or is not an abuser, and pretending there is is how you create a surveillance state.
If you can no longer stomach his work, fair. If you still want to read the books/watch the movies and shows you've come to love, fair (use your library or 🏴☠️ them, don't fund him).
But don't let anyone convince you that media censorship and surveillance states are the way to safety - that path leads only to oppression, fascism, and death.
316 notes
·
View notes
Text
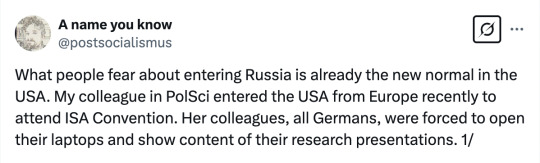
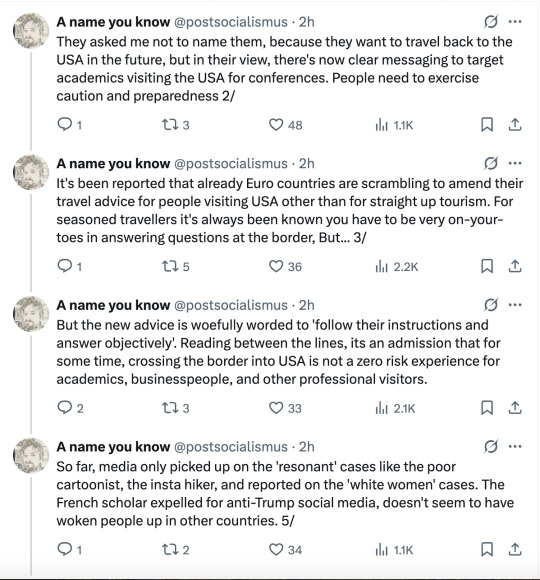



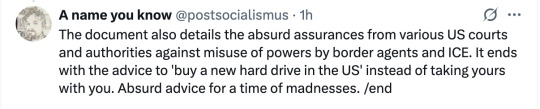
#honestly i would suggest everyone avoid traveling to the us for the time being.#there's just too much weird scary shit going on#usa#surveillance state#politics#news#twitter
246 notes
·
View notes
Text
AMERICANS UNDER SURVEILLANCE—BIG BROTHER IS WATCHING
Tens of thousands of cameras are tracking your every move across 42 states.
40,000–60,000 “Flock Cameras” are scanning vehicles. These cameras are completely legal—and they're EVERYWHERE.
The surveillance state isn’t coming—it’s already here. 🤔
#pay attention#educate yourselves#educate yourself#reeducate yourselves#knowledge is power#reeducate yourself#think about it#think for yourselves#think for yourself#do your homework#do your research#do some research#do your own research#ask yourself questions#question everything#government secrets#rogue government#government corruption#government lies#truth be told#lies exposed#evil lives here#surveillance state#news#law enforcement#crimes against humanity#big brother is watching you
210 notes
·
View notes
Text
U.K. orders Apple to let it spy on users’ encrypted accounts
Security officials in the United Kingdom have demanded that Apple create a back door allowing them to retrieve all the content any Apple user worldwide has uploaded to the cloud, people familiar with the matter told The Washington Post.
The British government’s undisclosed order, issued last month, requires blanket capability to view fully encrypted material, not merely assistance in cracking a specific account, and has no known precedent in major democracies. Its application would mark a significant defeat for tech companies in their decades-long battle to avoid being wielded as government tools against their users, the people said, speaking under the condition of anonymity to discuss legally and politically sensitive issues.
Rather than break the security promises it made to its users everywhere, Apple is likely to stop offering encrypted storage in the U.K., the people said. Yet that concession would not fulfill the U.K. demand for backdoor access to the service in other countries, including the United States.
The office of the Home Secretary has served Apple with a document called a technical capability notice, ordering it to provide access under the sweeping U.K. Investigatory Powers Act of 2016, which authorizes law enforcement to compel assistance from companies when needed to collect evidence, the people said.
The law, known by critics as the Snoopers’ Charter, makes it a criminal offense to reveal that the government has even made such a demand. An Apple spokesman declined to comment.
Apple can appeal the U.K. capability notice to a secret technical panel, which would consider arguments about the expense of the requirement, and to a judge who would weigh whether the request was in proportion to the government’s needs. But the law does not permit Apple to delay complying during an appeal.
In March, when the company was on notice that such a requirement might be coming, it told Parliament: “There is no reason why the U.K. [government] should have the authority to decide for citizens of the world whether they can avail themselves of the proven security benefits that flow from end-to-end encryption.”
181 notes
·
View notes
Text
I'm going to rescind my previous statements about recordings and images. Personally, I'm still going to record state violence when it happens, but previously benign images ... not anymore. Unless the people in your images have fully and knowingly consented to every image, every time, just... don't take them.
169 notes
·
View notes
Text
It is my sincerest and unironic belief that we must invest in preserving "old technology." The more we move to a hegemonic, easily-surveilled way of living, the worse we will find this world to be.
Letters, public phones and transport, cash, and so much more are key to ensuring both freedom of movement and information, but also to combat the surveillance state. We need to preserve the ability to both access the world but also to be untraceable. I truly hope more people start to recognize this. It isn't about nostalgia for the past. It is about ensuring that we are actually afforded freedom, from the richest person to the person who lives on the sidewalk.
#politics#i was ranting at my dad about how pissed i am that the US has essentially killed the payphone because we have smartphones#imagine killing letters because 'oough we have email though!!!'#i'm sure people advocate for abolishing mail (and i have seen it firsthand) but i don't agree with it#we must preserve freedom of movement and information and that includes making it as accessible and public as possible imo#i do not want to live in a world wherein my smartphone is both what i MUST rely on but it is also traceable 24/7/52/365#'if you're innocent you have nothing to hide' is a fucking cop-out to permit a surveillance state by the way#it is flawed logic and i think that logic is part of the reason we got to this point#'why do you need cash? that's kind of suspicious to not LET people trace your purchases' like come ON
1K notes
·
View notes
Text
Amid anger and protest over the Trump administration’s plan to deport millions of immigrants, U.S. Immigration and Customs Enforcement plans to monitor and locate “negative” social media discussion about the agency and its top officials, according to contract documents reviewed by The Intercept. Citing an increase in threats to ICE agents and leadership, the agency is soliciting pitches from private companies to monitor threats across the internet — with a special focus on social media. People who simply criticize ICE online could pulled into the dragnet.
[ ... ]
If this scanning uncovers anything the agency deems suspicious, ICE is asking its contractors to drill down into the background of social media users. That includes: “Previous social media activity which would indicate any additional threats to ICE; 2). Information which would indicate the individual(s) and/or the organization(s) making threats have a proclivity for violence; and 3). Information indicating a potential for carrying out a threat (such as postings depicting weapons, acts of violence, refences to acts of violence, to include empathy or affiliation with a group which has violent tendencies; references to violent acts; affections with violent acts; eluding [sic] to violent acts.”
[ ... ]
Once flagged, the system will further scour a target’s internet history and attempt to reveal their real-world position and offline identity. In addition to compiling personal information — such as the Social Security numbers and addresses of those whose posts are flagged — the contractor will also provide ICE with a “photograph, partial legal name, partial date of birth, possible city, possible work affiliations, possible school or university affiliation, and any identified possible family members or associates.” The document also requests “Facial Recognition capabilities that could take a photograph of a subject and search the internet to find all relevant information associated with the subject.” The contract contains specific directions for targets found in other countries, implying the program would scan the domestic speech of American citizens.
[ ... ]
The posting indicates that ICE isn’t merely looking to detect direct threats of violence, but also online criticism of the agency. As part of its mission to protect ICE with “proactive threat monitoring,” the winning contractor will not simply flag threatening remarks but “Provide monitoring and analysis of behavioral and social media sentiment (i.e. positive, neutral, and negative).” This includes regular updates on the “total number of negative references to ICE found in social media” from week to week. Such sentiment analysis — typically accomplished via machine-learning techniques — could place under law enforcement scrutiny speech that is constitutionally protected. Simply stated, a post that is critical or even hostile to ICE isn’t against the law.
109 notes
·
View notes
Text

121 notes
·
View notes
Text

I think everyone who said life wouldn't get back to normal owes me damages now.
128 notes
·
View notes
