#Cyber Crime Bureau
Explore tagged Tumblr posts
Text
Madras High Court Orders Partial Defreezing of Account Amid Cryptocurrency Investigation
Freezing an account indefinitely without informing the account holder violates his fundamental rights. Freezing orders should be specific to the amount under investigation and not disrupt the entire financial life of individual.
Background
The petitioner, Mohammed Saifullah's, bank account, was frozen by HDFC Bank based on the instructions from the Cyber Crime Bureau of Telangana, received via the National Cyber Crime Reporting Portal.
The account was frozen due to an ongoing investigation into a cybercrime case related to cryptocurrency, in which an amount of Rs. 2,48,835 is suspected to be linked to the crime.
The total balance in the petitioner’s account was Rs. 9,69,580, and he had not been informed for over a year as to why the account was frozen or when it would be unfrozen.
The petitioner approached the Madras High Court seeking a Writ of Mandamus to defreeze his account and release of his balance.

Mohd. Saifullah v. Reserve Bank Of India and 5 others
WP 25631/2024
Before the High Court of Madras
Heard by Hon'ble Dr. Justice G Jayachandran J
Legal Issue
Whether the authorities can freeze a bank account indefinitely without informing the account holder or quantifying the suspected amount, thereby affecting the fundamental rights of the petitioner under Article 19(1)(g) (right to trade and business) and Article 21 (right to livelihood) of the Constitution of India.
Argument of the Parties
Petitioner's Argument
The freezing of his account was without proper communication or justification from the authorities, and without a defined time frame, violating his fundamental rights.
Freezing of his account has seriously impacted his business and financial well-being.
Respondent's Argument
Freezing of the account was based on the ongoing investigation into cybercrime, specifically involving suspected cryptocurrency transactions.
They were acting on instructions from the Cyber Crime Bureau of Telangana and the National Cyber Crime Reporting Portal.
Court's Observation
While the authorities have the statutory power to freeze bank accounts during investigations, it is essential to ensure that such powers are not exercised arbitrarily.
Freezing the entire account without specifying the amount under suspicion and failing to communicate the reasons to the account holder is not acceptable.
Courts order
HDFC Bank, was ordered to defreeze the petitioner's account, allowing him to operate it with the condition that a lien of ₹2,50,000 is kept on the account. The petitioner must ensure that a minimum balance of ₹2,50,000 is maintained in the account at all times, pending the investigation.
Seema Bhatnagar
#Cybercrime#Cryptocurrency#Account Freezing#Fundamental Rights#Writ of Mandamus#Madras High Court#HDFC Bank#RBI#Cyber Crime Bureau#Investigation
0 notes
Text
Telangana citizens lose ₹4-₹5 crore every day to cyber criminals: police official
Telangana IT and Industries Minister D. Sridhar Babu; Commissioner of Police, Hyderabad C.V. Anand; DGP (Cyber Security Bureau) Shikha Goel and others at Annual Cyber Security Knowledge Summit-2.0 in Hyderabad on Wednesday (November 6, 2024). | Photo Credit: NAGARA GOPAL Telangana citizens are losing between ₹4-₹5 crore every day to cyber criminals, making it among the top five victim States in…

View On WordPress
#Cyber security bureau#cybercrime in Telangana#telangana loses 4-5 crore everyday to cyber crime#Telangana news#why people fall for cybercrime
0 notes
Text
Small groups from POGOs moving into residential areas
The nationwide ban on Philippine Offshore Gaming Operators (POGOs) is arguably working. That being said, the National Bureau of Investigation (NBI) stated that the POGOs have been forming smaller groups which have moved into residential areas to secretly operate, according to a GMA Network news report. To put things in perspective, posted below is an excerpt from the GMA news report. Some parts…
#Asia#Bing#Blog#blogger#blogging#Carlo Carrasco#China#City of Makati#communities#crime#crime news#crime syndicate#crime syndicates#crime watch#cyber crimes#cyber criminals#Cybercrime#fraud#geek#GMA Network#GMA News#Google#Google Search#hacking#journalism#local communities#Makati#Makati City#Metro Manila#National Bureau of Investigation (NBI)
0 notes
Text
Thailand: Arrests made in connection with USD 76 million cryptocurrency investment fraud
On 9 September, Thailand's Cyber Crime Investigation Bureau arrested four individuals from the PRC and one from Laos for their suspected involvement in a fraudulent cryptocurrency investment scheme that deceived more than 3,200 locals.
The investigation, which began in late 2022 with the assistance of the US Homeland Security Investigations, found the suspects operated a fraudulent Bitcoin investment platform which swindled over THB 2.7 billion (USD 76 million) from local investors. They have been charged with collusion in transnational crime, public fraud, and money laundering.
The Thai Anti-Money Laundering Office seized property worth THB 585 million (USD 16.2 million) from the accused on 4 September, with further asset recovery actions expected to be ongoing. The individuals arrested have not commented publicly on the charges against them.
In response to the growing threat of crypto-related scams, in January 2023, Thailand’s Securities and Exchange Commission introduced new requirements for virtual asset service providers operating within the country which aim at enhancing investor protection and securing user funds held by custody providers.
0 notes
Text
Things the Biden-Harris Administration Did This Week #33
Sep 6-13 2024
President Biden marked the 30th anniversary of the passage of the Violence Against Women Act and highlighted efforts to stop gender based violence. the VAWA was written by then Senator Biden and he often talks about it as his proudest legislative victory. The act transformed how the federal government dealt with domestic violence, sexual assault, and stalking. In part because of the connection to Joe Biden, President Trump and the Republicans allowed the VAWA to expire in 2019. President Biden passed a new reauthorization, with new protections for women against cyber crime, in 2022. On the VAWA's 30th anniversary President Biden announced $690 million in grants to support survivors of gender-based violence.
President Biden and Vice-President Harris announced a new rule to force insurance companies to treat mental health care the same as medical care. The new rule takes on the use by insurance of restrictive practices like prior authorization, and out of network charges, it also closes a loophole in the law that allowed state and local government health insurance not to cover mental health.
The Biden-Harris administration announced that 50 million Americans, 1 in every 7, have gotten health insurance through Obamacare's marketplaces. Under Biden a record breaking 20.8 million enrolled this year. Since the ACA was passed by President Obama and then Vice-President Biden it has transformed American health care bring affordable coverage to millions and getting rid of "preexisting conditions". During the Presidential debate Vice-President Harris defended the ACA and the need to keep building on it. Trump after 9 years of calling for its repeal said he only had "concepts of a plan" on what to do about health care in America.
The IRS announced that it has recovered $1.3 billion in back taxes from wealthy tax dodgers. For years Republicans have tried to underfund the IRS hindering its ability to police high income tax payers. President Biden in his Inflation Reduction Act ensured that the IRS would have the money it needs to chase high income tax cheats. In February 2024 the IRS launched a program to go after over 100,000 people, making $400,000 or even over $1 million a year who have not filed taxes since 2017. The IRS also launched a program to collect from tax payers who make over $1 million a year who have uncontested debt of over $250,000. Between these two efforts the IRS has collected over a Billion Dollars in back taxes from the richest Americans, so far this year.
The Department of The Interior and White House Climate Advisor Ali Zaidi highlighted green energy efforts on public land. Highlighting two projects planned in Nevada officials talked about the 41 renewable energy projects approved on public land under the Biden-Harris Administration. These projects over 25 gigawatts of clean energy, a goal the Administration's climate plan set for the end of 2025 but met early this year. With the new projects in Nevada this is enough energy to power 12.5 million homes, and the Bureau of Land Management is another 55 utility-scale project proposals across the West.
The Department of The Interior announced $236 million to help fight forest fires and restore landscapes damaged by recent wildfires. Under President Biden's Bipartisan Infrastructure Law, the Administration has spent nearly $1.1 billion dollars to combat deadly wildfires which have over the last 10 years grown in size and intensity thanks to climate change.
The Department of The Interior announced $157 million in wetland conservation. The money is focused on protecting bird habitats. It will protect and preserve thousands of acres of wetlands across 7 states.
The US Senate approved President Biden's nominations of Adam Abelson, Jeannette Vargas, Mary Kay Lanthier, and Laura Provinzino to federal judgeships in Maryland, New York, Vermont, and Minnesota respectively. This brings the total number of federal judges appointed by President Biden to 209. When Biden entered office 318 district judges were Republican appointees and 317 Democratic, today 368 are Democratic appointments and just 267 are Republican. President Biden is the first President in history to have the majority of his appointments not be white men and he has appointed more black women to the bench than any President ever.
#Joe Biden#Thanks Biden#kamala harris#politics#political#US politics#American politics#climate change#domestic violent relationships#mental health#health care#health insurance#tax the rich#judges
793 notes
·
View notes
Text
Look if you use Metropolitan Police Department, Community Safety Bureau, Cyber Crime Division, Investigation Unit 11, Digimon Crime Response Team then you have to annouce that you are using Metropolitan Police Department, Community Safety Bureau, Cyber Crime Division, Investigation Unit 11, Digimon Crime Response Team, otherwise how will people know you are using Metropolitan Police Department, Community Safety Bureau, Cyber Crime Division, Investigation Unit 11, Digimon Crime Response Team?

this should be illegal btw specifically because @mechdood insists on saying the name of this card in its entirety every single time it's relevant
#digimon#digimon card game#digimon seekers#Metropolitan Police Department#Community Safety Bureau#Cyber Crime Division#Investigation Unit 11#Digimon Crime Response Team
19 notes
·
View notes
Text
Humans are weird: Prank Gone Wrong
( Please come see me on my new patreon and support me for early access to stories and personal story requests :D https://www.patreon.com/NiqhtLord Every bit helps)
“Filnar Go F%$@ Yourself!” was possibly the most disruptive software virus the universe had ever seen.
The program was designed to download itself to a computer, copy the functions of existing software before deleting said software and imitating it, then running its original programming all the while avoiding the various attempts to locate and remove it by security software.
What was strange about such a highly advanced virus was that it did not steal government secrets, nor siphon funds from banking institutions, it ignore critical infrastructure processes, and even bypassed trade markets that if altered could cause chaos on an unprecedented scale. The only thing the software seemed focused on was in locating any information regarding the “Hen’va” species, and deleting it.
First signs of the virus outbreak were recorded on the planet Yul’o IV, but once the virus began to migrate at an increasing rate and latched on to several subroutines for traveling merchant ships things rapidly spiraled out of control. Within a week the virus had infected every core world and consumed all information regarding the Hen’va. It still thankfully had not resulted in any deaths, but the sudden loss of information was beginning to cause other problems.
Hen’va citizens suddenly found that they were not listed as galactic citizens and were detained by security forces on numerous worlds. Trade routes became disrupted as Hen’va systems were now listed as uninhabited and barren leading to merchants seeking to trade elsewhere. Birth records and hospital information for millions of patients were wiped clean as they now pertained to individuals who did not exist.
Numerous software updates and purges were commenced in attempting to remove the virus. Even the galactic council’s cyber security bureau was mobilized for the effort, but if even a single strand of the virus’s code survived it was enough to rebuild itself and become even craftier with hiding itself while carrying out its programming. This was made worse by the high level of integration the various cyber systems of the galaxy had made it so the chance of systems being re-infected was always high.
After ten years every digital record of the Hen’va was erased from the wider universe. All attempts to upload copies were likewise deleted almost immediately leaving only physical records to remain untouched.
To combat this, the Hen’va for all official purposes adopted a new name; then “Ven’dari”. In the Hen’va tongue in means “The Forgotten”, which is rather ironic as the Hen’va have had to abandon everything about their previous culture to continue their existence. The virus had become a defacto component of every computer system in the galaxy and continued to erase all information related to the Hen’va. Even the translator units refused identify the Hen’va tongue and so the Ven’dari needed to create a brand new language.
It wasn’t until another fifty years had passed before the original creator of the virus stepped forward and admitted to their crime. A one “Penelope Wick”.
At the time of the programs creation Ms. Wick was a student studying on Yul’o IV to be a software designer. While attending the institution Ms. Wick stated that a fellow student, a Hen’va named “Filnar”, would hound her daily. He would denounce her presence within the school and repeatedly declared that “what are the scrapings of humans compared to the glory of the Hen’va?”
The virus was her creation as a way of getting back at the student for his constant spite. Ms. Wick was well aware of the dangers it could pose if released into the wild and so had emplaced the limitation that the virus would only infect computers on site with the campus. The schools network was setup that students could only work on their projects within the confines of the institution to ensure they did not cheat and have others make them instead. What she had not counted on was this rule only applied to students and not teachers. So when a teacher brought home several student projects to review and then sharing those infected files with their personal computer, the virus then gained free access to the wider planets networks.
When the Ven’dari learned of this there were several hundred calls for Ms. Wick to be held accountable for her actions, and nearly twice as many made to take her head by less patient individuals who had seen their entire culture erased. Much to their dismay Ms. Wick died shortly after her confession from a long term disease that had ravaged her body for several years.
Much to her delight, she had achieved her goals of removing the source of her mockery.
#humans are insane#humans are weird#humans are space oddities#humans are space orcs#story#scifi#writing#original writing#niqhtlord01#funny#prank#prank gone wrong#virus
369 notes
·
View notes
Text
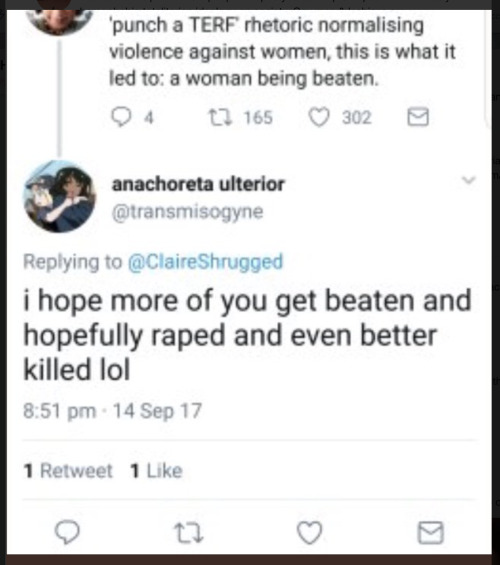
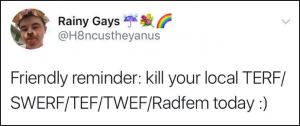
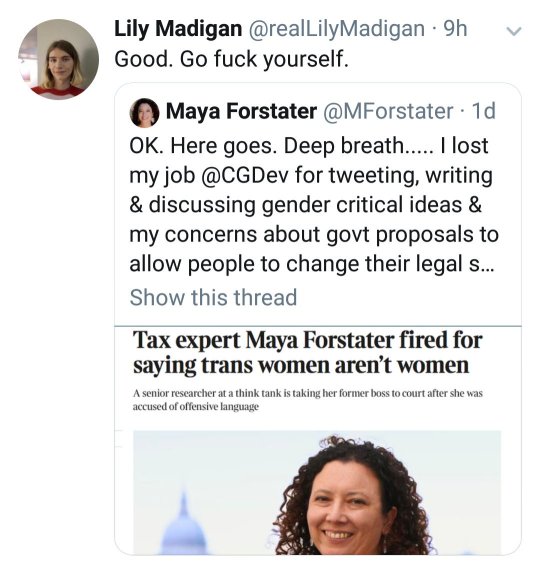
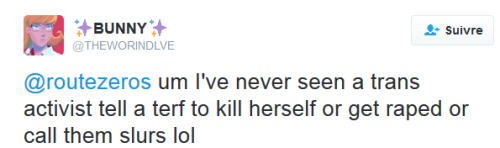
TW: Trans activists
For more than a decade now, trans activists have been harassing those who belong to a feminist philosphy we call radical feminism or the women’s liberation movement.
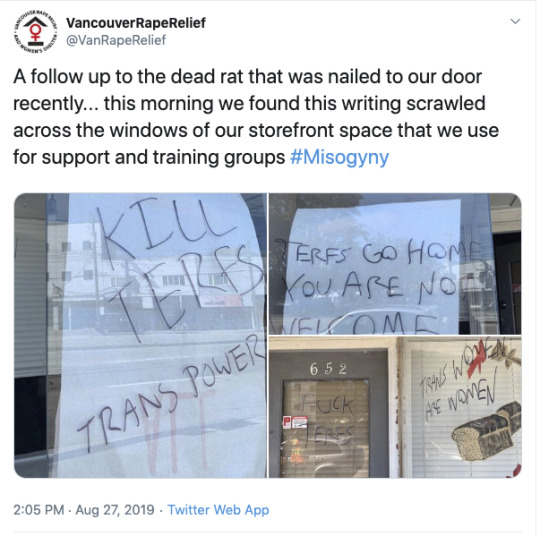
Radical feminists, like most feminists, believe that men use sex to oppress women. Meaning they oppress women through sexual exploitation and by perpetuating sexist discrimination towards those who belong to the female sex. They were the first to research and expose violence against women as endemic and traumatizing, and to create shelters for rape and domestic violence victims. Those shelters are now being vandalized and defunded by trans activists.
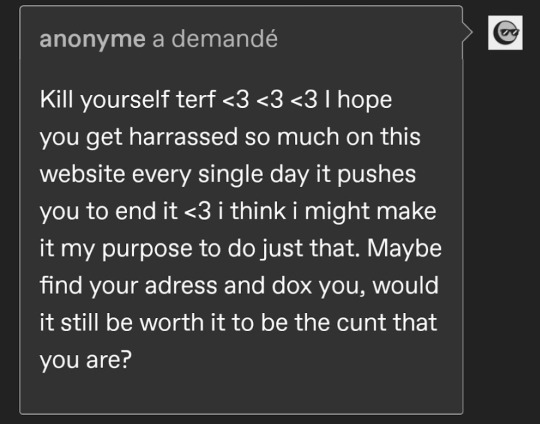
Because radical feminists don’t believe in gender identities, gendered souls, gender roles or any form of innate personality based on sexist stereotypes, they have been receiving rape and death threats on a daily basis. The acronym “terf” was soon invented and is now used to describe any person who doesn’t support the trans movement, even if they’re not feminists, just as long as they're women, though lesbians and feminists tend to be the primary targets.

As a whole, the trans movement claims that its biggest enemy and threat, its most pressing matter, its most dangerous opponent is the women’s liberation movement or what they call “radfems” or “terfs”. This is where their energy and anger is directed, typically in the form of sexist and sexual harassment, intimidation techniques, violence, censorship and social isolation. So let’s talk about that.
From the book Hate Crimes in Cyberspace:
Cyber harassment involves threats of violence, privacy invasions, reputation-harming lies, calls for strangers to physically harm victims, and technological attacks.


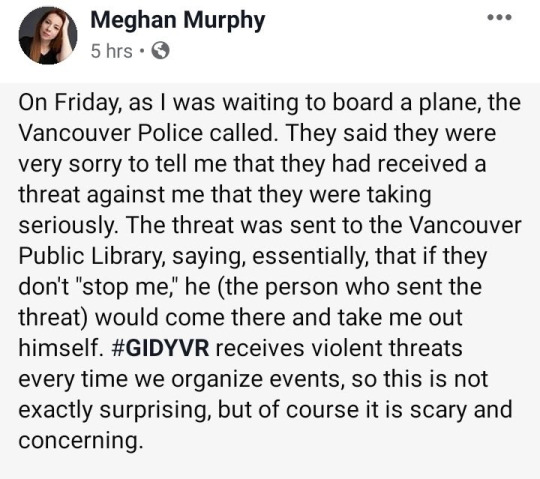
Victims’ in-boxes are inundated with threatening e-mails. Their employers receive anonymous e-mails accusing them of misdeeds. Even if some abuse is taken down from a site, it quickly reappears on others. Victims’ sites are forced offline with distributed-denial-of-service attacks.

While some attackers confine abuse to networked technologies, others use all available tools to harass victims, including real-space contact. Offline harassment or stalking often includes abusive phone calls, vandalism, threatening mail, and physical assault.
The Internet extends the life of destructive posts. Harassing letters are eventually thrown away, and memories fade in time. The web, however, can make it impossible to forget about malicious posts. And posts that go viral attract hundreds of thousands of readers.
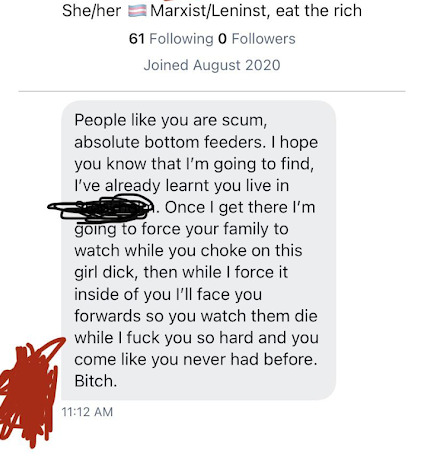
Online harassment can quickly become a team sport, with posters trying to outdo each other. Posters compete to be the most offensive, the most abusive. An accurate name for such online groups is cyber mobs. The term captures both the destructive potential of online groups and the shaming dynamic at the heart of the abuse.

Cyber harassment disproportionately impacts women. The U.S. National Violence Against Women Survey reports that 60 percent of cyber stalking victims are women, and the National Center for Victims of Crimes estimates that the rate is 70 percent. Of the 3,393 individuals reporting cyber harass-ment to WHOA from 2000 to 2011, 72.5 percent were female. The most recent Bureau of Justice Statistics report found that 74 percent of individuals who were stalked on or offline were female, and 26 percent were male.

Researchers found that users with female names received on average one hundred “malicious private messages,” which the study defined as “sexually explicit or threatening language,” for every four received by male users.

According to the study, “Male human users specifically targeted female users.” By contrast, men are more often attacked for their ideas and actions. John Scalzi, a science fiction author and popular blogger, has found online invective typically situational. When he writes something that annoys people, they tell him so. People do not make a “hobby” out of attacking his appearance and existence as they do female bloggers.
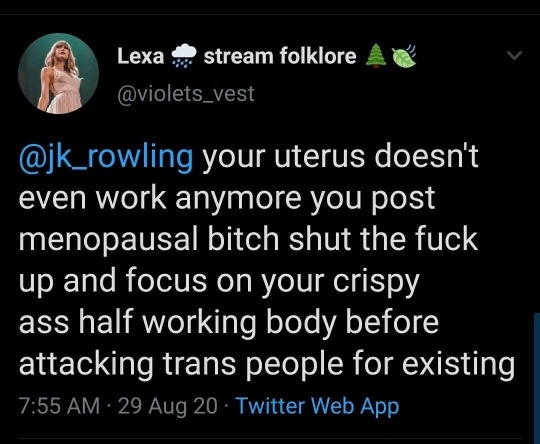
The nature of the attacks similarly attests to bigotry’s presence. Hate expresses something uniquely damaging. It labels members of a group as inhuman “others” who do not possess equal worth. It says that group members are inferior and damaged. Bigotry conveys the message that group members are objects that can be destroyed because they have no shared humanity to consider.
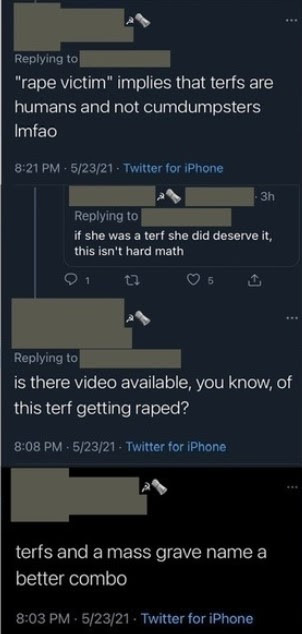
Cyber harassment exploits these features by exposing victims’ sexuality in humiliating ways. Victims are equated with their sexual organs, often described as diseased.


Once cyber harassment victims are sexually exposed, posters penetrate them virtually with messages that say “I will fuck your ass to death you filthy fucking whore, your only worth on this planet is as a warm hole to stick my cock in.”
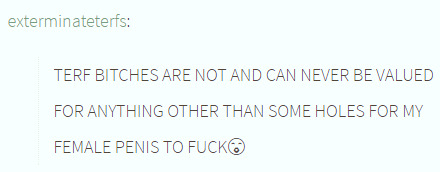
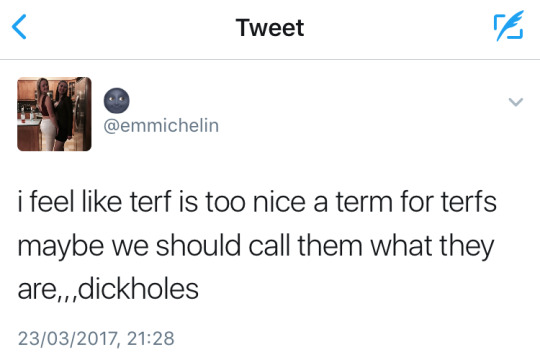
Rape threats profoundly impact women: over 86 percent of rape victims are female. Virtual elimination may follow the imagined penetration: “First I’ll rape you, then I’ll kill you.”

One woman who faced online abuse noted, “Someone who writes ‘You’re just a cunt’ is not trying to convince me of anything but my own worthlessness.” Despite the gravity of their predicaments, cyber harassment victims are often told that nothing can or should be done about online abuse. Journalists, bloggers, lay observers, and law enforcement officials urge them to ignore it. Victims are called “whiny baby girl[s]” who are overreacting to “a few text messages.” Often victims are blamed for the abuse. They are scolded for sharing their nude images with loved ones or for blogging about controversial topics. They are told that they could have avoided the abuse had they been more careful.

A related message sent to victims is that the benefits of online opportunities are available only to those who are willing to face the Internet’s risks. They are advised not to expect anything different if they want to make a name for themselves online. The choice is theirs: they can toughen up or go offline.
The Internet is governed by society’s rules. Life online bleeds into life offline and vice versa. The notion that more aggression should be tolerated in cyberspace than in real space presumes that virtual spaces are cordoned off from physical ones.
Most victims do not report cyber harassment to the police because they assume that nothing will be done about it. Sadly, they are right. Law enforcement frequently fails to act on victims’ complaints even though criminal law would punish some of the behavior. Victims are told to turn off their computers because “boys will be boys.” Online harassment victims are told that nothing can be done; they are advised to ignore rape and death threats. During the summer of 2013, high-profile women were subjected to a torrent of online threats. The feminist activist Caroline Criado Perez received hundreds of graphic rape threats via Twitter after her successful campaign to feature more female images on British banknotes.

Members of Parliament and female writers who publicly supported Criado-Perez faced the same, including bomb threats. One tweet featured a picture of a masked man holding a knife with the message, “I’m gonna be the first thing u see when u wake up.”

Because the Internet serves as people’s workspaces, professional networks, résumés, social clubs, and zones of public conversation, it deserves the same protection as offline speech. No more, no less.
Without doubt, the free speech interests at stake are weighty. Free expression is crucial to our ability to govern ourselves, to express our thoughts, and to discover truths. For that reason, government cannot censor ideas because society finds them offensive. Truthful speech must not be banned just because it makes people uncomfortable.

But credible threats, certain defamatory falsehoods, social security numbers, and nude images posted without consent contribute little to discourse essential for citizens to govern themselves and discover truths. Their net effect is the silencing of victims. Victims could blog, post videos, and engage on social networks without fear of destructive cyber harassment. They could raise money using networked tools unencumbered by rape threats, reputation-harming lies, and distributed- denial- of- service attacks. They could take advantage of all of the expressive opportunities available online. Protecting against online harassment would secure the necessary preconditions for victims’ free expression.

With the help of law and the voluntary efforts of Internet intermediaries, parents, and teachers, we might someday achieve a free and equal Internet. We need to take action before cyber harassment becomes a normal feature of online interactions. A hostile online environment is neither inevitable nor desirable. We should not squander this chance to combat discriminatory online abuse; it is early enough in our use of networked tools to introduce equality of opportunity as a baseline norm of interaction.
290 notes
·
View notes
Text
Joint ODNI, FBI, and CISA Statement
FOR IMMEDIATE RELEASE ODNI News Release No. 29-24 November 4, 2024
WASHINGTON, D.C. - Today, the Office of the Director of National Intelligence (ODNI), the Federal Bureau of Investigation (FBI), and the Cybersecurity and Infrastructure Security Agency (CISA) released the following statement:
“Since our statement on Friday, the IC has been observing foreign adversaries, particularly Russia, conducting additional influence operations intended to undermine public confidence in the integrity of U.S. elections and stoke divisions among Americans. The IC expects these activities will intensify through election day and in the coming weeks, and that foreign influence narratives will focus on swing states.
Russia is the most active threat. Influence actors linked to Russia in particular are manufacturing videos and creating fake articles to undermine the legitimacy of the election, instill fear in voters regarding the election process, and suggest Americans are using violence against each other due to political preferences, judging from information available to the IC. These efforts risk inciting violence, including against election officials. We anticipate Russian actors will release additional manufactured content with these themes through election day and in the days and weeks after polls close.
The IC assesses that Russian influence actors recently posted and amplified an article falsely claiming that U.S. officials across swing states plan to orchestrate election fraud using a range of tactics, such as ballot stuffing and cyber attacks.
Russian influence actors also manufactured and amplified a recent video that falsely depicted an interview with an individual claiming election fraud in Arizona, which involved creating fake overseas ballots and changing voter rolls to favor Vice President Kamala Harris. The Arizona Secretary of State has already refuted the video’s claim as false.
Iran also remains a significant foreign influence threat to U.S. elections. As noted in a prior update, we have assessed that Iran has conducted malicious cyber activities to compromise former President Trump’s campaign. Iranian influence actors may also seek to create fake media content intended to suppress voting or stoke violence, as they have done in past election cycles. We previously reported that Iran also remains determined to seek revenge against select former US officials whom it views as culpable for the death of Islamic Revolutionary Guard Corps-Qods Force (IRGC-QF) Commander Soleimani in January 2020. It has repeatedly highlighted former President Donald Trump among its priority targets for retribution.
In light of continued influence efforts by foreign adversaries and the increasing volume of inauthentic content online, CISA recommends voters seek out information from trusted, official sources, in particular, state and local election officials.
The FBI and CISA encourage campaigns and election infrastructure stakeholders to report information concerning suspicious or criminal activity to their local Election Crime Coordinators via FBI field office (www.fbi.gov/fieldoffices), by calling 1-800-CALL-FBI (1-800-225-5324), or online at ic3.gov. Cyber incidents impacting election infrastructure can also be reported to CISA by calling 1-844-Say-CISA (1-844-729-2472), emailing [email protected], or reporting online at cisa.gov/report. Election infrastructure stakeholders and the public can find additional resources about how to protect against cyber and physical threats at CISA’s #PROTECT2024 (https://www.cisa.gov/protect2024).”
24 notes
·
View notes
Text

CHAMPIGNAC ... FEW LAST DETAILS :)
And of course, we have some mistakes in the links and in the cc content we are currently correcting ... What is a good Sims 3 World without a little headache ? :D And because we love difficulties, we are currently updating our own website ( which is a mess ) ... What else ? Nothing, everything is fine under the sun of this hot summer :D
The General Hospital is a Maxis one, but from Riverview. @nornities ( thanks A LOT for his/her patience to check Champignac ) pointed to us different things : missing mostly. so, somes of you may not see the Hospital ( Hopital des Bleuets ) in their game.
Bad links are currently corrected and both CC sims3packs folder and CC packages folder updated to include few missing stuff, including the Fresco Market items and the Skylight Studio roof elements we used + the Riverview Hospital :) HERE
The Open Swimming pool ( Champignac Bains Romains ) has lost its border texture ... don't worry : just replace with a one you like :)
The School is not the good one : too many missing stuff there, so we are currently uploading a new Champignac save game which should correct the little mistakes here and there HERE
Our Carpets Rabbit Holes folder had to be updated to get the Bistro RH : it is currently done ! But, you have to re-download the Rabbit Holes HERE
Our apologizes for this ! Really ... Anyway, we'll upload in the next hours a folder with ALL Community Lots and another one with ALL the residential Lots :) Just in case ... And here the 2 listings :

CHAMPIGNAC COMMUNITY LOTS
Small Park : Monticule funéraire oublié - Colline des Celtes Small Park : Petit Fleuriste Small Park : La Vieille Tour no1 Small Park : La Vieille Tour no2 Small Park : Place Olivier Magnolia Horse Training Grounds : Elevage Pégase Junkyard : Neo Casse Stadium : Football Club Fire Station : Pompiers Volants Pool : Piscine Municipale Pool : Bains Romains de Champignac Diner : Brasserie du Cercle Gym : Gymnase Club Visitor Allowed : Boulangerie DeNimes Elixir Shop : Boutique d’élixirs : Elixirs et Reliques Theatre : Théâtre & Opéra Cemetary : Cimetière Civil Hospital : Hôpital des Bleuets Bookstore : Le Kiosque no5 Library : Bibliothèque V. Hugo Café : Café Catane Military Base : Bureau des Armées Police Station : Police Municipale Grocery Store : Epicerie des Halles Market : Marché Bio City Hall : Nouvelle Mairie Art Gallery: Villa Medicis Fishing Spot : Lac des Collines Criminal Hideout : Cyber Crime Beach : La Petite Plage Gypsy Wagon : Oeil d’Irma Science Lab : Bio Sciences Supernatural Hangout : Taverne du Nain Business & Journalism : Centre d’Affaires Consignment Store : Boutique & Brocante Bistro : Bistro Gastronomie Nectary : Le Monastère School : Ecole Municipale Vampire Bar & Cocktail : Midnight Lounge

CHAMPIGNAC RESIDENTIAL LOTS
Maison Familiale : 1 double bed + 2 single bed Maison Bleu Indigo : 1 double bed Maison des Pensées : 2 double bed + 2 single bed Maison des Prés : 3 double bed + 1 single bed Maison Ensoleillée : 1 double bed + 1 single bed Maison des Colocs : 2 double bed Maison Élégante : 2 double bed + 2 single bed Maison Tournesol : 1 double bed + 1 single bed Maison Biscornue : 2 double bed + 1 single bed Maison des Haies : 1 double bed + 2 single bed Maison Neo Rustique : 1 double bed + 1 single bed Maison du Mardi : 1 double bed + 1 single bed Maison du Chanoine : 1 double bed + 1 single bed Maison de la Vieille Tour de Garde : 1 double bed Maison des Gardiens : 1 double bed + 1 single bed Maison des Roses : 1 double bed + 2 single bed Maison des Chardons : 1 double bed + 1 single bed Maison Nénuphars : 1 double bed + 1 single bed Maison du Bonjour : 1 double bed Maison en Coin : 1 double bed + 1 single bed Maison du Thym : 1 double bed + 2 single bed Maison Fougères : 1 double bed + 2 single bed Maison des Collines : 1 double bed + 1 single bed Maison du Coquelicot : 2 double bed Maison du Ginkgo : 1 double bed + 1 single bed Manoir Central : 2 double bed + 2 single bed Manoir Chapelle : 1 double bed + 1 single bed Mas des Vignes : 1 double bed + 1 single bed Ferme des Tortues : 2 double bed + 2 single bed Ancien Lavoir : 1 double bed + 2 single bed Ancienne Ferme : 1 double bed Intro de Qualité : 1 single bed Le Camp des Hippies : 1 double bed Le Bosquet de Gardenias : 1 double bed Champignac Starter no1 : 1 single bed Champignac Starter no2 : 1 single bed
We have carefully furnished all the houses of Champignac to avoid half empty houses when visiting your Sims friends in town but not too much to avoid useless weight ;)
Do you know the origin of the name Champignac ?
We'll ... Champignac is a village from Spirou & Fantasio which is one of the most popular classic Franco-Belgian comics. The series, which has been running since 1938, shares many characteristics with other European humorous adventure comics like The Adventures of Tintin and Asterix. It has been written and drawn by a succession of artists ... Spirou and Fantasio are the series' main characters, two adventurous journalists who run into fantastic adventures, aided by Spirou's pet squirrel Spip, the Marsipulami, and their inventor friend the Count of Champignac ... :D


Once again, sorry for the inconvenient. All files should be ok now, and oh ! one last detail ... Have Fun ! \o/
Blackgryffin
#sims 3#sims 3 custom content#sims 3 worlds#sims 3 world#sims 3 cc#k hippie#sims 3 build#champignac#champs les sims#sims de nimes#custom content#community lot#residential lot#build mode#build
73 notes
·
View notes
Text
One of the world’s biggest botnet networks, responsible for stealing close to $6 billion (£4.7bn), has been shut down following an international effort from law enforcement agencies.
The US Justice Department, which led the operation, said the 911 S5 botnet comprised more than 19 million hijacked devices, which were being used to facilitate cyber attacks, large-scale fraud, bomb threats and even child exploitation.
Chinese national YunHe Wang, 35, was arrested on 24 May on suspicion of creating and operating the 911 S5 botnet from his home in St. Kitts and Nevis.
“This Justice Department-led operation brought together law enforcement partners from around the globe to disrupt 911 S5,” said US Attorney General Merrick Garland.
“This case makes clear that the long arm of the law stretches across borders and into the deepest shadows of the dark web, and the Justice Department will never stop fighting to hold cyber criminals to account.”
The FBI said the 911 S5 botnet infected computers in nearly 200 countries around the world, which were then controlled through 150 dedicated servers allegedly set up by Mr Wang.
An indictment unsealed on 24 May claimed that malware was used to infect and compromise millions of residential computers between 2014 and 2022, forming the botnet that was then able to carry out the cyber crimes.
Mr Wang allegedly sold access to the botnet to criminals, who then used it to bypass fraud detection systems in order to steal billions of dollars from financial institutions.
One target was reportedly a pandemic relief program in the US, which saw the botnet used to fraudulently make insurance claims from the hijacked IP addresses. More than half a million false claims resulted in losses of $5.9 billion for the programs, according to the FBI.
“Working with our international partners, the FBI conducted a joint, sequenced cyber operation to dismantle the 911 S5 Botnet – likely the world’s largest botnet ever,” said FBI Director Christopher Wray.
“We arrested its administrator, Yunhe Wang, seized infrastructure and assets, and levied sanctions against Wang and his co-conspirators... We will work tirelessly to unmask and arrest the cybercriminals who profit from this illegal activity.”
Mr Wang made around $99 million by selling access to the botnet, according to the indictment, which he used to purchase real estate in the US, St. Kitts and Nevis, China, Singapore, Thailand and the United Arab Emirates.
Other assets subject to forfeiture are two BMWs, a Ferrari, a Rolls Royce and several luxury wristwatches.
“The conduct alleged here reads like it’s ripped from a screenplay: A scheme to sell access to millions of malware-infected computers worldwide, enabling criminals over the world to steal billions of dollars, transmit bomb threats, and exchange child exploitation materials – then using the scheme’s nearly $100 million in profits to buy luxury cars, watches, and real estate,” said Matthew Axelrod of the US Department of Commerce’s Bureau of Industry and Security.
“What they don’t show in the movies though is the painstaking work it takes by domestic and international law enforcement, working closely with industry partners, to take down such a brazen scheme and make an arrest like this happen.”
Mr Wang faces a maximum penalty of 65 years in prison if convicted.
16 notes
·
View notes
Text
Les Sages de Sion à l’origine de l’arrestation de Pavel Durov
Durov est la cible d’une cabale aux larges ramifications.
L’angle d’attaque de la « justice » française est basique : comme patron de Telegram, Durov est coresponsable de tous les crimes ou délits que des utilisateurs auraient pu commettre via son réseau social, partout dans le monde.

Selon cette logique, le patron d’Orange devrait être arrêté pour avoir fourni internet à des criminels.
De même pour le patron d’Apple pour avoir fourni des smartphones à des criminels.
Macron, tout comme les juges à sa botte, n’est que l’instrument de commanditaires beaucoup plus puissants.
Il s’agit bien sûr du gouvernement américain.
Washington se sert des états croupions de l’UE pour faire ce que la loi américaine ne permet pas.
L’idée des juifs est de faire plier les réseaux sociaux qui seraient tentés de leur résister, même partiellement.

Ces derniers temps, Durov n’était pas dans les petits papiers des juifs.
Haaretz :
Il y a quelques mois, des pirates informatiques étrangers ont réussi à s’introduire dans un ordinateur lié au ministère israélien de la justice. Des dizaines de milliers de fichiers classifiés et de courriels sensibles ont été divulgués. Des liens permettant à quiconque de télécharger ces fichiers ont été publiés sur Telegram, l’application de messagerie instantanée la plus populaire.
Cependant, ils ont rapidement commencé à disparaître. L’un après l’autre, les canaux Telegram des pirates ont été supprimés, leurs utilisateurs effacés et les messages contenant les liens de téléchargement disparus.
Selon un certain nombre de personnes bien informées, Israël mène une guerre numérique sur plusieurs fronts pour tenter d’endiguer la fuite apparemment sans fin de ses informations. Il s’agit notamment de surveiller le web et les sites de médias sociaux à la recherche de fuites et d’adresser des demandes de retrait légal à des entreprises technologiques telles que Google, Amazon, Meta et même Telegram, afin de les supprimer ou de les bloquer.
Depuis le 7 octobre et jusqu’à aujourd’hui, nous avons assisté à un effort concerté de cyber-attaques, dont certaines sont directement liées ou attribuées à des États ennemis et à des organisations terroristes, pour mener des « attaques de perception sous la forme de publication de fuites », explique Haim Wismonsky, directeur de l’unité cybernétique du bureau du procureur de l’État israélien, qui fait partie du ministère de la justice et qui est l’organisme chargé de déposer les demandes effectives auprès des entreprises technologiques.
« La publication de ces fuites a pour but de faire peur, d’inspirer la panique au public et de donner le sentiment que nous sommes exposés et pénétrables, mais elle vise également à causer des dommages économiques, voire à mettre en danger la vie des personnes dont les données personnelles sont incluses dans ces fuites », a expliqué M. Wismonsky à Haaretz.
Cette politique et la manière dont elle est mise en œuvre font d’Israël un cas unique. De nombreux pays, dont les États-Unis, prennent généralement des mesures pénales ou juridiques à l’encontre des auteurs de fuites, qu’ils soient étrangers ou locaux, mais s’accommodent de l’existence de la fuite en ligne. Israël, en revanche, utilise les règles internes des entreprises technologiques pour les inciter à retirer les produits piratés en son nom – et empêcher ainsi les données divulguées d’atteindre le public ou les journalistes, tant en Israël qu’à l’étranger.
Les plateformes, même celles qui sont considérées comme hostiles aux demandes des gouvernements, comme Telegram, ont mis en place des règles destinées à les défendre contre les ramifications juridiques de la conduite de leurs utilisateurs. Il peut s’agir de demandes de retrait pour violation des droits d’auteur ou de plaintes pour diffamation.
Les documents piratés entrent dans la catégorie générale des biens volés, de sorte que les politiques mises en place pour empêcher la diffusion de fichiers permettant de télécharger illégalement des films ou des séries télévisées peuvent également être utilisées pour retirer des documents piratés, volés sur des serveurs israéliens sans le consentement de l’utilisateur.
Ces derniers mois, par exemple, des demandes israéliennes signalant des violations des conditions d’utilisation de Telegram ont conduit à au moins dix suppressions d’utilisateurs et de canaux de groupes de pirates. Souvent, ce sont les mêmes groupes de pirates qui, sans se laisser décourager, ont ouvert un nouveau canal et posté de nouveaux liens vers les mêmes fuites.
Depuis le début de la guerre, Telegram s’est révélé être un défi de taille pour Israël. Alors que de nombreuses entreprises technologiques ont rationalisé les mécanismes par lesquels les États peuvent les contacter, Telegram est considéré comme le moins coopératif de tous.
Qui plus est, alors que de nombreuses plateformes de médias sociaux ont investi massivement dans la modération, permettant aux personnes et aux organisations d’aider à surveiller le contenu – par exemple, le retrait de contenu antisémite ou de messages incitant au terrorisme ou même le retrait de vidéos du massacre du 7 octobre – Telegram ne l’a pas fait. Les États et les utilisateurs disposent d’une adresse électronique unique à laquelle ils peuvent envoyer leurs griefs.
Telegram est apparu au début de la guerre comme une plateforme clé utilisée par le Hamas dans sa guerre de l’information contre Israël, une plateforme qu’Israël n’a pas été en mesure de traiter correctement, faute de capacités de surveillance et de compréhension de la plateforme. Préoccupés par la vague de contenus pro-Hamas, qui comprenait des vidéos de l’attaque elle-même ainsi qu’un flux constant de matériel de propagande, des Israéliens du secteur des hautes technologies ont tenté, à la fin de l’année 2023, de contacter le fondateur de Telegram, Pavel Durov.
Bien qu’ils aient réussi à contacter Durov, qui vit aux Émirats arabes unis, celui-ci s’est montré peu réceptif à ces demandes privées d’amélioration de la modération sur la plateforme. Bien que quelques pages liées directement à l’aile militaire du Hamas aient été bloquées localement par la suite, l’initiative privée n’a pas réussi à convaincre le fondateur de l’application. Des sources expliquent que Google ou Meta retireront une page s’il s’avère qu’elle est directement liée au Hamas et qu’Amazon supprimera un site web pour avoir hébergé du matériel terroriste.
Sur Telegram, le contenu ne peut pas être supprimé avec de tels arguments. Seules les marchandises manifestement volées seront retirées, ce qui fait des réclamations de contenu la seule voie efficace pour les autorités juridiques israéliennes. Les données parlent d’elles-mêmes : Selon les chiffres officiels fournis par Israël, le ministère de la justice a envoyé à Facebook plus de 40 000 demandes de retrait de « contenu illégal » qui ont été acceptées. Il ne s’agit pas de messages pro- ou anti-israéliens, mais de contenus illégaux au regard des normes occidentales. Même TikTok a retiré plus de 20 000 messages signalés par Israël. Sur Telegram, ce nombre est légèrement supérieur à 1 300.
Les juifs veulent faire main basse sur Telegram.
Si Durov veut pouvoir à nouveau faire le tour du monde avec des prostituées slaves, il va devoir donner aux juifs ce qu’ils veulent.
4 notes
·
View notes
Text
Uncover the Conspiracy in The Operator in the new release

The Operator launches the conspiracy fueled game and investigate crimes on Linux, Mac, and Windows PC. Thanks to the genius minds at Bureau 81. Available on both Steam and GOG with 96% Very Positive reviews. Bureau 81 has just launched their first Linux game, The Operator. Due to take you into the world of conspiracy and mystery, much like the X-Files. In this title, you’re recruited by a secret Government agency called the FDI. Your mission? Due to track down and catch a notorious cybercriminal named HAL using some serious tech. In The Operator, you’re launched into an immersive conspiracy fueled story where you get case files from FDI field agents. So your job is to dig through clues and piece together information. You also have a range of tools at your disposal, like the Video and Photo Analyzer, Citizen and Vehicle Database. A ChemScan, Notepad, and a fully functional computer console. With these, you're due to solve all kinds of crimes, from murders to cyber attacks and missing person cases.
The Operator | Launch trailer
youtube
As an Operator, you need to untangle a complex web of clues and evidence to uncover the truth. Since each case is full of twists and turns, and it’s your job to follow the evidence. No matter how creepy it gets, solve the mystery and bring criminals like HAL to justice. Picture this: In The Operator it's your first day on the job, shaking off that hangover, and launching into your first case. You’ll be assisting field agents, using your computer console and your skills to crack these cases. So get ready to make the world a safer place, one clue at a time.
Here’s what you’ll be doing:
Investigate Crimes: Dive into cases involving murders, missing people, and cyber attacks.
Use FDI Software: Analyze evidence and hunt for clues using high-tech tools.
Dig Deeper: Follow the evidence wherever it leads, no matter how unexpected.
Uncover the Truth: Each case is a mind-bending puzzle to solve, so keep those notes handy.
The Operator launches the conspiracy fueled title on Steam and GOG. Priced at $12.59 / £10.61 / 12,41€ with the 10% discount. Along with support for Linux, Mac, and Windows PC. So if you’re curious to learn more, check out the game’s store page. Get ready to dive into this thrilling adventure and prove your skills as an Operator.
2 notes
·
View notes
Text
NBI arrests 12 Chinese nationals who were caught in the act of scamming and for previously detaining and harming a man who refused to work as a scammer
Every day here in the Philippines, either someone got scammed or someone is secretly organizing a scam to steal money from others. Recently in the City of Manila, agents of the National Bureau of Investigation (NBI) apprehended twelve Chinese nationals who were caught in the act of scamming and also for illegally detaining and assaulting a man who refused to work as a scammer, according to a GMA…
#Asia#Blog#blogger#blogging#Carlo Carrasco#China#Chinese#Chinese aggression#Chinese criminals#City of Manila#crime#crime news#crime watch#cyber crimes#cyber criminals#Cybercrime#geek#GMA Network#GMA News#immigration#journalism#Manila#Metro Manila#National Bureau of Investigation (NBI)#National Capital Region (NCR)#NCR#news#Philippines#Philippines blog#Pinoy
0 notes
Text
snippet <3
thank you @uhoh-but-yeah-alright @beelou @wabadabadaba @neondiamond and @crinkle-eyed-boo for tagging me to post a snippet! I just started working on a fic for @wankersday fest, Harry is the FBI man inside of Louis’ computer!
Harry exchanges a bored nod with the security guard as he flashes his badge, entering the sprawling building and wishing he’d had time to stop for a decent cup of coffee on his way in. No one had told him when he was in the academy how integral coffee would be to the job; he marks the hours of his shifts by which cup he’s on and sometimes it’s the only thing that helps fight the tedium. No one had warned him about that either.
“Hey, man,” Harry calls out, spotting his coworker Jeff in the doorway of the cramped office they share. “What’s up?”
“Nothing much,” Jeff replies, lifting his hand for a high five as Harry approaches. “I’m outta here. Got dinner with Glenne’s parents.”
“Nice,” Harry says, walking past Jeff into the office. He sets his laptop bag down, jerking his chin toward the desk they share. “How was he today?”
“Streamed some true crime series all day,” Jeff says, shaking his head. “Kept talking to the TV about law enforcement screwups, but he stayed off Twitter for once.”
“Beats watching him sleep,” Harry says with a shrug. “I’m gonna need an IV of coffee to get through the last few weeks of this.”
“Graveyard shift’s a killer,” Jeff says, shaking his head again. He pats the door jamb and points at Harry. “See ya tomorrow.”
“Yeah,” Harry calls after him. “Have fun with the in-laws.”
Harry surveys the desk they share, the three computer monitors fighting for attention around a few crumpled post-its and a used coffee mug. He wrinkles his nose. It’s bad enough that his training period is just busywork, surveilling some community organizer who’s clearly not a threat to his country, but sharing the duty with Jeff, whose dad is some D.C. powerbroker who made a call and got him the job that Harry’s worked for his entire life, just plain sucks. Harry sighs, grabbing the coffee cup and heading for the break room.
Jeff’s not a bad guy, Harry can admit that to himself as he sets Jeff’s mug in the sink and then pours himself a fresh cup in the deserted break room. Harry’s just frustrated. When he was younger, dreaming of working at the Bureau, he’d pictured himself hunting down terrorists. Working with local law enforcement when there was a kidnapping. Putting in the work in the field and catching serial killers. He’d been disappointed when he was assigned to the cyber unit, but they actually do a lot of cool work. He just wishes his training period, which honestly feels more like hazing at this point, would end so he could help his coworkers do that cool work.
There’s not a soul in the hallway as Harry heads back to his tiny, windowless office. He closes the door behind him, dimming the lights so he can see his multiple screens better. After he tosses the trash that Jeff left and boots up his laptop, he sits back in his chair and takes a sip of coffee, ready to start another long night of surveilling his subject.
Louis Tomlinson.
I’ll tag @kingsofeverything @louandhazaf @allwaswell16 @becomeawendybird @absoloutenonsense @homosociallyyours and @huggieshalo if you have a line or snip you want to share!
24 notes
·
View notes
Text
insane crackpot crossover.
You know how technically Abe Lincoln could have sent a fax to a samurai as they all existed at the same time? Well.... GitS SAC takes place in 2030. John is on Tumblr now, prolly doing his under grad. He plasters his abilities on Twitch and Youtube. The Net is Motoko's main stick. Section 9 deal with cyber crimes. Esp in the Pan Pacific area. There is precedent for the team tracking down nukes and also finding/solving cases of the ''hacking'' of public officials. You can't tell me that a government seeking someone to puppet their leader wouldn't come under Aramaki's and The Major's radar. This would come under the Public Safety Bureau's purview, esp if it was deemed a threat to safety of Japan. If it didn't come under their jurisdiction? In 2045, the team are dealing with Post Humans. Could John and his cult be classed as post human? Who knows? But Motoko would not leave that stone unturned. She might even take an interest as a private citizen, esp when you consider the bigger philosophical questions raised such as what constitutes the soul/ghost etc etc. Aramaki would most certainly not be cool with the trillionaires bullshit leading up to the events of their escape. It becomes a race against time to figure out if John is the real deal. Lots of cyber space water cooler gossip to filter through. John is searching for proof the trillionaires are lying n tryna get out of dodge. Motoko could find that proof, then its a case of getting the Japanese government to give Sec9 the go ahead. They don't, their hands are tied. Maybe Motoko agrees with John initially. She rushes through the net, gets her ghost onboard one of the trillionaire's ships, but then John makes his move. The Major is not best pleased by this devastation wrought upon the human race, but she's stuck in the data stream of the ships with no prosthetic body to inhabit. All this time, she has been mistaken for a really old AI, passed down from generation to generation. She's the reason why boe have Emma Sen and Aim. She's biding her time. Some day, someone will build the technology of an android body n then its all over for John Gaius. The Major, Motoko Kusanagi is the reason why John Gaius scrapped the internet from necromantic boogaloo 2.0. He's terrified she'll find his ass.
21 notes
·
View notes