#secure-browsing
Explore tagged Tumblr posts
Link
#best-vpns-2024#cyberghost-vpn#cybersecurity#hidemyname-vpn#internet-security#nordvpn#online-privacy#opera-vpn#secure-browsing#streaming-vpn#surfshark-business#unlocator-vpn#vpn-comparison#vpn-for-gaming#vpn-reviews
0 notes
Text
this could be a fun game night not gonna lie



14 notes
·
View notes
Text
Imagine Cinder being sponsored by surf shark VPN in a social media au
#Thorne accuses her of cheating at cards#and#Cinder is like i literally downloaded the rulebook i have a computer in my head... but i made sure my browsing eas secure w/ surf shark vpn#nowadays people are constantly trying to track my location (international manhunt) but i make sure to throw them off with surf shark vpn#iko could use the vpn too#and add thats she sues surf shark to access the different web dramas available in the differnt countries of earth ... and luna lmao#Cinder sets her location for surf shark on luna to fuck with Levana
7 notes
·
View notes
Text
Features of Our AI To Human Text Converter
However, not all AI-generated text is fit for human consumption without some level of refinement. That's where the AI To Human Text Converter comes in, a free tool that turns robotic-sounding AI content into natural, human-readable text. Let's dive into the key features that make this tool an indispensable resource for anyone looking to humanize AI-generated text effortlessly.
1. Simple and User-Friendly Interface
One of the standout features of our AI To Human Text Converter is its simple, user-friendly interface. Many people shy away from using complex tools that require a steep learning curve. Fortunately, this converter is designed with ease of use in mind. The interface is intuitive, allowing users to quickly navigate the platform and convert their AI-generated text into human-like content within seconds. There's no need to struggle with confusing menus or spend time learning how to use the tool.
2. Safe and Secure to Use
Safety is paramount when it comes to using online tools, especially for text conversion. AI To Human Text Converter ensures that users' data is protected through secure browsing measures. The website is well-secured, minimizing any risks of data breaches or security threats. Whether you're a content creator, student, or professional, you can confidently use the tool without worrying about jeopardizing your safety.
3. Accurate Conversion of AI-Generated Content to Human-Like Text
The primary feature of the AI To Human Text Converter is its ability to transform AI-generated content into human-readable text. Utilizing advanced algorithms, the tool analyzes the input and produces an output that closely mimics the natural flow of human writing. Whether you're converting AI content for essays, blog posts, or marketing materials, this tool ensures the end result is clear, engaging, and free of robotic phrasing.
4. No Limitations – Unlimited Usage
One of the most attractive features of the AI To Human Text Converter is its unlimited usage policy. Unlike other tools that impose restrictions or require subscriptions after a certain number of conversions, our tool is completely free with no limitations. You can convert as much content as you need, whenever you need it. This makes it an ideal solution for content creators, bloggers, and students with large volumes of AI-generated text to convert.
5. Fast and Efficient Processing
Time is a valuable commodity, and with our AI to human text converter, speed is a top priority. The tool processes your content in seconds, delivering humanized text quickly and efficiently. Whether you have a single paragraph or an entire document to convert, you can trust that the tool will provide results without delays.
6. No Authentication Needed
Another significant advantage of AI To Human Text Converter is that you don’t need to create an account, sign up, or log in. The tool is ready for immediate use, allowing you to convert text as soon as you arrive at the website. This no-authentication feature ensures a hassle-free experience, making it easy for users to get started right away.
Why Choose AI To Human Text Converter?
If you're looking for a reliable and efficient way to humanize your AI-generated content, AI To Human Text Converter is the perfect choice. Here are some key reasons why you should consider using this tool:
Free of Cost: Our tool is completely free to use, with no hidden fees or subscription costs.
Unlimited Use: Convert as much AI content as you need without worrying about restrictions.
No Login Required: Enjoy immediate access to the tool without needing to create an account.
Fast Conversion: Save time with near-instant results that transform AI text into human-like content.
User-Friendly: The intuitive interface makes it easy for anyone to use, even without prior experience.
The AI To Human Text Converter is packed with features that make it an excellent choice for anyone looking to convert AI-generated content into natural, human-readable text. Its simple interface, fast processing, and unlimited usage ensure that you get the best results without any hassle. Plus, with top-notch security measures in place, you can use the tool confidently and safely. Whether you’re a student, content creator, or professional, this tool is designed to meet all your text conversion needs.
Try the AI To Human Text Converter today and experience the difference for yourself!
#AI to human text#AI to human text converter#human-readable text#convert AI-generated content#humanize AI text#free AI to human text converter#secure text converter#AI content converter#unlimited AI text conversion#AI text tool#AI text to human-readable content#convert AI text for essays#convert AI text for blog posts#no login required AI tool#fast AI text conversion#user-friendly AI text converter#free online AI to human text tool#secure browsing AI tool#advanced AI text conversion algorithms#AI content transformation#hassle-free AI content conversion#fast and efficient AI text tool#unlimited usage AI text converter#no subscription AI tool#AI text humanization tool
5 notes
·
View notes
Text

Where to go.. where to go...
Tch, big decisions for Benny.. Big decisions for Benny...

You mentioned an accident in uhh SimCity™ awhile back right?

Could we possibly go see the SimCity™ itself?
[ Benrey would slightly chuckle to himself. ]

SimCity™ ya say?

GREAT IDEA!

NO. WE ARE NOT-
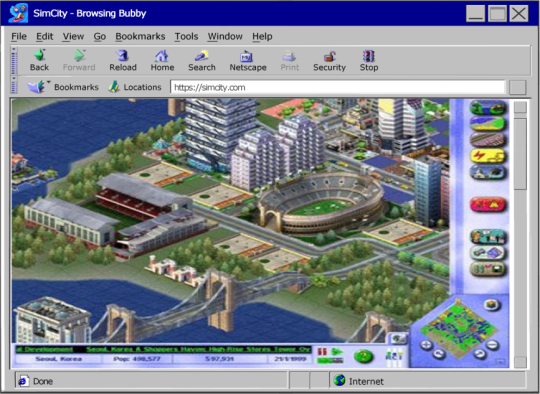

Aaand we’re already there. Just don’t make me look like an idiot in front of the user…
#HKEY|SYSTEM|OPERATOR#HKEY|SECURITY|FIREWALL#HKEY|SOFTWARE|BROWSINGBUDDY#HKU|BENREYLOVER#browsing history#PROGRAMFILES|REALITY_REGISTRY#MRW-034-B
12 notes
·
View notes
Text
like i understand life is different for everybody on earth but i cannot imagine the phone as my only source of accessing the internet. that's where im inflicted with the most psychic damage. on my PC i have my VPN and ad blockers and browser extensions to ward myself against everything i dont want to see. and now everyone is just on Apps that steal your information and sell it to advertisers and whoever. how are people just raw dogging this shit
4 notes
·
View notes
Text
#Data Protection Act#Privacy Online#Online Privacy#Personal Data Protection#Data Breaches#Privacy Rights#Online Security#Protecting Personal Information#Secure Browsing#Encryption#VPN#HTTPS#Strong Passwords#Two-Factor Authentication#Privacy Settings#Safe Online Communication
2 notes
·
View notes
Text
5 Reasons Why a VPN with Advanced Encryption is Essential for Online Security
In today’s digital age, online security and privacy are more important than ever. With an increasing number of cyber threats, data breaches, and surveillance systems, safeguarding your personal information is a necessity. One of the most effective ways to ensure online security is by using a VPN with advanced encryption. A Virtual Private Network (VPN) is an essential tool for protecting your data, securing your privacy, and preventing unauthorized access while browsing the web. But not all VPNs are created equal. To truly enhance your security, you need a VPN with robust encryption protocols. A nordvpn voucher provides users with discounts or special offers on NordVPN's premium subscription plans. By using a voucher, you can enjoy top-tier online privacy and security services at a lower cost, making NordVPN more accessible for everyone.
In this blog post, explore 5 reasons why a VPN with advanced encryption is essential for online security and how it helps protect you in a variety of ways, from safe browsing to anonymous online activity. Also look at some of the best advanced VPNs for online privacy and security to help you choose the right solution for your needs.
1. Protects Your Data from Hackers
The most critical reason to use a high-security VPN with military-grade encryption is to protect your data from hackers. Cybercriminals often target users on unsecured networks, such as public Wi-Fi hotspots, where data is more vulnerable. Without encryption, sensitive information like passwords, credit card numbers, and personal messages can easily be intercepted.
A VPN with advanced encryption protocols for secure data transmission ensures that your internet traffic is encrypted, making it impossible for hackers to access your private information. When you use a secure VPN for privacy and data protection in 2025, all your online activities are shielded from malicious attacks. This is particularly important if you often use public Wi-Fi or connect to networks you don’t trust. With military-grade encryption, even the most advanced hackers will be unable to break through your protection.
Key benefit: Prevents hackers from intercepting and stealing your sensitive data.
2. Keeps Your Online Activities Private
Another significant advantage of using a VPN with advanced encryption protocols is that it shields your online activities from being tracked or monitored by third parties, including internet service providers (ISPs), governments, and advertisers. Without encryption, your internet traffic is visible to anyone with access to the network, and this can lead to unwanted surveillance and data collection.
A VPN with military-grade security for avoiding online surveillance masks your online identity and makes it difficult for third parties to track your activities. By using encryption, your browsing history, search queries, and even your location remain private. This is essential if you value your privacy and don’t want your online movements to be exposed to anyone who might be watching.
Key benefit: Ensures complete privacy by encrypting your online activities.
3. Secures Sensitive Data During Online Transactions
Every time you make an online purchase, conduct a banking transaction, or log into an online account, you are sharing sensitive personal information. Without encryption, this data can be exposed to attackers, leading to identity theft, financial fraud, or other malicious activities. By using the best advanced VPN for online privacy and security, you can be sure that your personal and financial data is always protected.
A VPN with advanced encryption protocols for secure data transmission ensures that any data you send over the internet, including login credentials, payment details, and personal messages, is encrypted and secure. This means that even if hackers attempt to intercept the transmission, they will not be able to decode the data. Whether you’re shopping online or managing your bank account, a high-security VPN offers peace of mind.
Key benefit: Safeguards your sensitive financial and personal information during online transactions.
4. Prevents Online Tracking and Profiling
One of the most pervasive problems online today is the constant tracking of your activities. Websites and advertisers use tracking cookies and other methods to collect data on your browsing habits, interests, and personal preferences. This information is then used to target you with personalized ads or sold to third parties.
By using a secure VPN for privacy and data protection in 2025, you can bypass tracking systems and prevent companies from profiling you based on your online behavior. When you connect to a high-tech VPN for privacy and security on public Wi-Fi networks, your real IP address is hidden, and your internet traffic is encrypted, making it difficult for advertisers and websites to monitor or track your activity.
A VPN with advanced encryption protocols for secure data transmission also ensures that your browsing history is erased, preventing third parties from building a detailed profile of you. This is an essential feature if you want to maintain control over your personal data and avoid invasive online marketing tactics.
Key benefit: Stops websites and advertisers from tracking your online activity.
5. Bypasses Geo-Restrictions and Accesses Restricted Content
Another critical reason why a VPN with advanced encryption is so important is that it allows you to access geo-restricted content and unblock websites that may be restricted in your region. Many services, like streaming platforms (Netflix, Hulu, BBC iPlayer, etc.), apply geo-blocking to restrict content access based on your geographical location.
By using a fast and secure VPN service for accessing geo-restricted content, you can virtually change your location and access content from any part of the world. With next-gen VPN solutions for total anonymity online, you can browse the internet as if you were in a different country, enjoying unrestricted access to websites, services, and media.
Additionally, the fastest VPN service with low latency for gaming and streaming ensures that your streaming and browsing experience remains smooth without any buffering or lag, even when accessing content from other countries.
Key benefit: Unblocks geo-restricted content and ensures smooth streaming and gaming.
FAQs: Best VPN
Q1: What is the best VPN with advanced encryption for online privacy?
A1: Some of the best VPNs with advanced encryption for privacy include NordVPN, ExpressVPN, and CyberGhost. These services use military-grade encryption to protect your data and offer features like secure browsing, geo-unblocking, and anti-tracking.
Q2: How does a VPN with advanced encryption protect my data?
A2: A VPN with advanced encryption encrypts your internet traffic, making it unreadable to anyone trying to intercept it, such as hackers or government surveillance agencies. It ensures that your personal information and browsing activities remain private.
Q3: Can a VPN help me unblock geo-restricted content?
A3: Yes, a VPN can help you bypass geo-restrictions by allowing you to connect to a server in a different location. This makes it appear as if you're browsing from another country, enabling access to content that may be restricted in your region.
Q4: Are there any free VPNs with military-grade encryption?
A4: While there are some free VPNs available, most free services don’t offer military-grade encryption or the same level of security as paid VPNs. To ensure the highest level of protection, it’s recommended to use a premium VPN service.
Conclusion
In an age where cyber threats, data breaches, and online surveillance are commonplace, using a VPN with advanced encryption has become essential for ensuring online security and privacy. Whether you want to protect your personal data from hackers, prevent online tracking, or access geo-restricted content, a VPN can provide the solution.
Here’s a quick recap of why you need a VPN with advanced encryption:
Protects your data from hackers by encrypting internet traffic.
Keeps your online activities private and prevents surveillance.
Secures sensitive data during online transactions, ensuring your information stays safe.
Prevents online tracking and profiling by advertisers and third parties.
Bypasses geo-restrictions and allows access to restricted content and websites.
To experience the full benefits of online privacy and security, consider opting for a high-security VPN with military-grade encryption. Some of the best advanced VPNs for online privacy and security available today include ExpressVPN, NordVPN, and CyberGhost, which offer robust encryption protocols and excellent features for online protection.
A VPN with advanced encryption is a crucial tool for anyone looking to enhance their online security and privacy. Whether you’re browsing the web, making online transactions, or streaming content, a VPN helps keep your data safe and your identity anonymous. Make sure to choose a VPN that offers strong encryption, reliable performance, and excellent security features to protect yourself online.

#vpn#Advanced VPN Encryption#best vpn#vpn service#free vpn#nord vpn#Online Security#Best VPN for Privacy#VPN for Safe Browsing#VPN for Streaming#VPN for Gaming#Secure VPN for 2025#VPN for Public Wi-Fi Security
0 notes
Text
Is it time to re-consider your browser? Top Alternatives to Google Chrome with Pros and Cons
Alternatives to Google Chrome are becoming increasingly popular as users seek improved privacy and performance. If you’re feeling the pinch of data collection or find Chrome slowing down your browsing experience, it may be time to explore your options. This guide will probe into the pros and cons of various web browsers that could better suit your needs while ensuring a more secure and efficient…
#alternatives to Google Chrome#best browsers for developers#best browsers for extensions#best browsers for Mac#best browsers for privacy#best browsers for Windows#best features of Edge browser#best mobile browsers for Android#best mobile browsers for iOS#Brave browser review#browser alternatives#browser market share 2023#browser security features#browser speed test#browsers with built-in ad blockers#Chrome extensions alternatives#Chromium alternatives#custom browsers for security#eco-friendly browsers#efficient web browsing#fast browsers for slow internet#fast web browsers#features of different web browsers#Firefox vs Chrome#Google Chrome alternatives for gaming#how to switch from Chrome#importance of browser speed#lightweight browsers#lightweight browsing options#Microsoft Edge vs Chrome
0 notes
Text
I'm trying to find the energy to start house hunting again and I'm cycling through all the same anxiety spirals I had when I was looking two years ago.
#Can I even afford somewhere where I'll feel safe living alone? I'm bad to obsessively researching home security#gravel is a good deterrent but none of the houses I browsed today have anywhere to put gravel out the front.#are there equally attention-drawing doormats that like honk when stepped on?
1 note
·
View note
Text
SetupVPN - Lifetime Free VPN
SetupVPN – Lifetime Free VPN is a program that provides access to a free virtual private network (VPN) service. VPNs enhance the security of your internet connection by encrypting the data you exchange, offer greater anonymity by masking your real IP address, and allow you to use an IP address from another location. This is particularly useful for accessing content that is restricted to certain…
#access blocked websites#anonymous browsing#encrypted connection#free VPN#free VPN service#Online Privacy#Secure Browsing#SetupVPN#unblock content#VPN#VPN for streaming#VPN service
0 notes
Text
How To Enable Or Disable Hardware Acceleration In The 360 Secure Browser
youtube
How To Enable Or Disable Hardware Acceleration In The 360 Secure Browser | PC Tutorial | *2024
In this tutorial, we'll guide you through the process of enabling or disabling hardware acceleration in the 360 Secure Browser on your PC. Hardware acceleration can improve browser performance or help resolve issues with rendering. Follow this step-by-step guide to optimize your browsing experience. Don’t forget to like, subscribe, and hit the notification bell for more 360 Secure Browser tips and tricks!
Simple Steps:
Open the 360 Secure web browser.
Click on the 3 bar hamburger menu in the upper right corner and choose "Settings".
In the left pane, click on "Advanced" to expand it the section, then choose "System".
In the center pane, toggle on or off "Use Hardware Acceleration When Available".
#360 Secure Browser#enable hardware acceleration#disable hardware acceleration#hardware acceleration settings#360 Secure tutorial#optimize browser performance#browser settings 360#360 Secure PC#browser tips#hardware acceleration guide#improve browsing speed#troubleshoot 360 Secure#browser optimization#360 Secure 2024#tech tutorial 360 Secure#Youtube
0 notes
Note
I’m going insane why do you all look so AMAZING!!!!
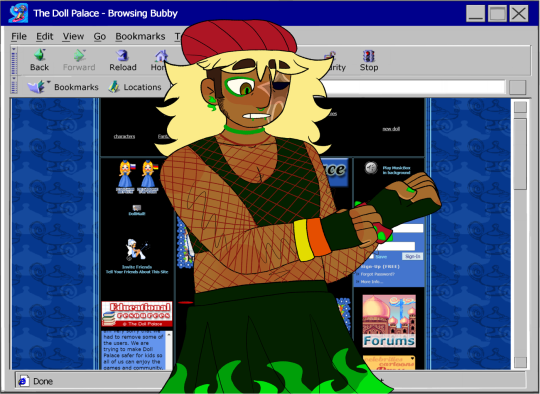
Ayyyy, they got shit in, uh, my style. Hell yeah.

Y-you look... really nice, Fireball.

Hhhhhh. Mhm, you look g-great, very nice.
#PROGRAMFILES|REALITY_REGISTRY#HKEY|SECURITY|FIREWALL#HKEY|SYSTEM|DESKTOPASSISTANT#HKLM|FILENOTFOUND#Browsing History#Mod Hazard☣
11 notes
·
View notes
Text
🚨Trapped Family in Gaza Appeals for Help to Survive🚨 🕊️🇵🇸 🍉🌹
Hi 👋 my friends My name is Samer Abu Ras, and I am reaching out to you with a heavy heart and shattered hopes after the war in Gaza destroyed my life and my family’s. Our days were once filled with peace and security, but now we are homeless, without shelter or income, facing a bleak future. My wife Shorouq and our three children are suffering from psychological and health traumas due to this catastrophe. We lost our home and our jobs, and now we seek warmth in cold streets.

My original story link

🇵🇸🍉🌹🇵🇸🍉🌹🇵🇸🌺🍉🌺🍉🇵🇸🌹🌺🇵🇸🍉🌺
My children 🧒 👧 , who once lived in safety, are now gripped by fear and displacement. As a father, I feel deep sorrow and helplessness for not being able to protect them. Today, I am making a humanitarian plea, asking for assistance to rebuild our lives and find a safe and stable environment. Every donation, no matter how small, will make a significant difference in our lives.
Let us make hope triumph over despair and restore smiles and dignity to my family.
Thank you to everyone who listens to my plea and offers a helping hand and donation to change our future for the better.
With heartfelt gratitude and appreciation
Note our campaign vetted by
@sar-soor @el-shab-hussein @nabulsi @ibtisams
Verification source: number 196 on users el-shab-hussein and nabulsi's master list
Attached is my Instagram account, my friends, for more information and details.
@schoolhater🌹@victoriawhimse🌹@pocketsizedquasar-2 🌹@turtletoria 🌹 @rinnie 🌹@ut-against-genocide 🌹
@ethanscrocs 🌹 @punkitt-is-here @plomegranate 🌹 @gazavetters @anneemay 🌹 @buttercuparry @appsa 🌹 @malcriada @irhabiya 🌹 @feluka @sheplaysbassdotmp3 🌹 @opencommunion @papenathys 🌹 @rooh-afza 🌹@mohabbaat 🌹 @itsfookingloosah@magnus-rhymes-with-swagness 🌹@flower-tea-fairies 🌷🌹🌸🌺💐@fancysmudges 🌹 @brokenbackmountain @just-browsings-world 🌹 @aleciosun @fluoresensitive 🌹 @khizuo @lesbiandardevil 🌹 @transmutationisms @buttercuparry 🌹 @akajustmerry@annoyingloudmicrowavecultist 🌹
@tortiefrancis 🌹 @tsaricides @determinate-negation 🌹 @belleandsaintsebastian 🌹@4ft10tvlandfangirl 🌹 @tamarrud @queerstudiesnatural 🌹 @skatezophrenic 🌹 @awetistic-things @pcktknife 🌹
#every dollar helps!#donate if you can#please donate#donations#donate#mutual aid#mutual assistance#donations needed#don’t scroll#vetted gfm#donations for palestine#palestine aid#humanitarian aid#samerpal#freepalastine🇵🇸#on the vetted list#palestine gfm#palestinian genocide#charity#child health#freedom#go fund them#gofundus#stop the genocide#dont stop talking about palestine#help palestine#eyes on palestine#free gaza#current events#aid for gaza
19K notes
·
View notes
Text
What Advantages Does Using the AI Text Converter Tool Offer?
In the ever-evolving world of digital content, converting artificial intelligence (AI)-generated text into human-readable information is essential. The AI Text Converter Tool offers a range of benefits that make it an invaluable resource for anyone dealing with AI content. Here’s why you should consider using this free tool:
1. Straightforward and Simple to Use
The AI Text Converter Tool is designed with user-friendliness in mind. Its intuitive interface allows users to quickly navigate the tool and perform conversions with minimal effort. Whether you’re a student, content creator, or professional, you’ll find that using this tool is as simple as pasting your text and clicking a button.
2. Quick and Dependable Performance
Speed and reliability are crucial when working with large volumes of text. Our AI Text Converter Tool delivers results swiftly without compromising on accuracy. You can depend on the tool to convert your AI-generated content into human-like text efficiently, ensuring that you meet your deadlines and maintain productivity.
3. Secure Browsing Experience
Security is a top priority for online tools, and the AI Text Converter Tool is no exception. The tool provides a secure browsing experience, protecting your data and ensuring that your content remains private. You can use the tool with confidence, knowing that your information is safe from unauthorized access.
4. Supports Multiple Languages
The versatility of the AI Text Converter Tool is one of its standout features. It supports a variety of languages, making it suitable for a global audience. Whether you’re working with content in English, Spanish, French, or another language, the tool can handle it, allowing you to convert text across different linguistic contexts.
5. Open to Countless Purposes
The AI Text Converter Tool is not limited to a specific use case. Its flexibility makes it suitable for a wide range of applications, from academic assignments and professional documents to blog posts and creative writing. No matter the nature of your content, the tool adapts to your needs and delivers high-quality results.
In summary, the AI Text Converter Tool offers a wealth of advantages, including ease of use, speed, reliability, security, language support, and versatility. By leveraging this free tool, you can efficiently transform AI-generated text into human-readable content that meets your specific requirements.
For more information and to start using the tool today, visit AI To Human Text.
#AI Text Converter Tool#AI-generated text#human-readable information#straightforward to use#simple to use#quick and dependable#secure browsing#supports multiple languages#versatile tool#content conversion#AI to human text conversion#free AI text tool#user-friendly AI text converter#efficient text transformation#secure AI text tool#global language support#flexible AI text converter#academic assignments#professional documents#blog posts#creative writing
0 notes
Text
[explore] blacklight - real-time website privacy inspector | markup

#blacklight#the markup#privacy#website inspector#online tracking#digital privacy#tech#internet security#data protection#web browsing
0 notes