#industry sponsored research
Explore tagged Tumblr posts
Text
Unlock the power of industry research surveys with expert tips on analyzing and interpreting data. Learn valuable insights from industry research analysts and companies to leverage your findings effectively.
#industry research reports#industry research analyst#industry research survey#industry research companies#industry sponsored research
0 notes
Text
The gas industry relied on Hill & Knowlton, the same public relations company that masterminded the tobacco industry’s playbook for responding to research linking smoking to lung cancer. Hill & Knowlton’s tactics included sponsoring research that would counter findings about gas stoves published in the scientific literature, emphasizing uncertainty in these findings to construct artificial controversy and engaging in aggressive public relations efforts.
This campaign was remarkable, since the basics of how gas stoves affected indoor air pollution and respiratory health were straightforward and well-established at the time. Burning fuel, including natural gas, generates nitrogen oxides: The air in Earth’s atmosphere is about 78 percent nitrogen and 21 percent oxygen, and these gases react at high temperatures.
Nitrogen dioxide is known to adversely affect respiratory health. Inhaling it causes respiratory irritation and can worsen diseases such as asthma.
0 notes
Note
Media Demon AU - excuse me you've inspired me to write in your AU, have a gift.
Lucifer and Lilith being dragged out to Pride by Teenage Charlie, they aren't expecting anything but blood, brimstone and depravity and are pleasantly surprised to find everything drastically changed.
The streets are well lit, banners of alternating colours crisscross the streets below, colourful storefronts and music on every corner, it's easier to say what street doesn't have a sinner or group of sinners with musical instruments singing their hearts out as practice or hoping to be recruited. Walls usually vandalised with nasty graffiti feature massive spray painted murals and while some are admittedly indecent they are of high quality.
Posters on every storefronts advertising performance arts of any kind imaginable, with temporary soul contract offers for skilled musicians and other artists to either teach or perform.
Lucifer looked at some of the advertisements somewhat curiously.
Carmine Industries who in addition to Angelic Weaponry also did research and sold parts for sound systems, stages and repaired instruments in partnership with the Media Demon.
Zizzi the Party Overlord who seemed to have a mild friendly rivalry with the Media Demon in terms of recruiting talented bands with many non-violent battle of the bands in their history.
Then there was Alastor the Media Overlord himself, there was no picture, but a mention of sponsorships and sign up sheets guaranting safefy in return for the low low price of your soul. The caveat of 'for however long you were employed' was interesting but seeing the list of guaranteed benefits supplied, and the sheer lack of better options, it would be extremely difficult to refuse. Food, Housing, lessons, free dental and there was even a section for imps and hellhounds who wanted to work in the porn industry.
Lucifer paused his reading and sharpened his hearing to listen to the sinner talking to his wife and daughter.
"I'm practicing for The Media Demon... no I'm not into the lust sector... or television sector, don't worry... Overlord Alastor suggested I publicly perform to get over my stage fright. I never gotta perform up top back when I was alive cause I wasn't of the right folk. Overlord Alastor don't care about that nonsense though, so I can now!... What do you mean redemption?... Why would I want that when I got everything I want down here?... Those bigots are either up there or down here in the service industry, watching the same folks that they denied a job cause they was coloured be the next Michael Jackson is like Karmic Retribution... You wanna meed the Media Demon? Good luck with that, man's got a schedule so packed it's gotta be a war crime, managing the radio, Television, Internet and the entire Porn industry, powerful overlord but yeesh the paperwork... I don't think he actually sleeps... He's sponsoring a theater performance on Laufrey Theater, that's on Allegra Avenue... Look when the Media Demon rebuilds a entire city district after a Extermination on his own dime the demon can name a street whatever he wants... Royal permission? Pfft! Those bluebloods are never here, never help either... It's a far better name that 'Wreck that Booty Lane' that's for sure, look ladies get a new map from one of the shops, I gotta practise!"
Charlie was gone on the musical performances of the sinners on the streets, she'd thought earth was interesting from the extensive smuggled books and media she got from various Goetia and Hellborn after her interest in humans had became common knowledge but this was like everything all at once, she really didn't understand her parents extreme views on sinners. Look at what they were capable of, clear and present evidence that they just needed a chance!
Charlie was mentally adjusting her redemption plans and jerked in surprise when her father spoke up, waving a leaflet with Laufey Theater on the title. "How would you like to see a play?", her dad was showing interest in sinners? Actual interest?! Don't jinx it Charlie! "Can we really?" Charlie couldn't hold back the excitement, like a confetti cannon about to go off and it probably showed. Lucifer smiled "Anything for you Char-char"
"I'm sorry, sir, our tickets have sold out."
Alastor couldn't help but stop, ears perking up, as he passed by the Laufey Theater. It's unsurprising that the tickets have sold out, it's the premier of a creative adaptation of Mary Shelley's Frankenstein, and Alastor can personally attest to the uniqueness of the play. It doesn't follow the popular inspirations from James Whale's film adaptations, such as electricity bringing the monster to life, and the background music consists of newly commissioned works played live for the audience. Alastor had seen a couple of the rehearsals, and was invited to watch the premier by the theater director herself.
He was busy, though, terribly busy, and he told young miss Melody that himself. Still, she insisted on reserving seating for him in the VIP section, despite his protests. A whole box, four seats, left empty for a man who doesn't even have the time to attend? It was preposterous, really. He tried several times to convince her to sell the seats, or at least give it to some of the family of the actors, but she remained firm. No one else were to sit in that box unless he were right there along with them.
"I'm truly sorry, sir, but there really is no room left tonight. We've even had to use our expansion runes to create more space in the theater, but even those extra seats have filled out."
He should walk away. Really, he's on a tight schedule, a meeting with Carmilla Carmine and several others regarding the adaptability of angelic steel in the medical field. He has no time for a singular man missing his chance—
"Sorry, girls. I know you were excited, but maybe next time?"
Fuck.
Alastor pivots, catching sight of an imp, a succubus, and presumably their teenaged daughter, who shares features of both. Something about them is familiar, but he waves the thought away; he's used to seeing "familiar" things, given that he's back in time. He's stopped trying to place the memories.
"Pardon me," he calls, instantly getting the attention of both the family and the ticket seller. "Apologies for eavesdropping, but I seem to have a solution for your problem."
He flashes a nonthreatening smile, dripping southern charm and hospitality.
"I just so happen to have a box set aside for me, and no one else to fit the remaining seats."
He turns to the seller and winks.
"Could you tell our darling miss Melody that her so-called muse is here for the premier?"
The seller gapes, immediately connecting the dots, face growing red with realization.
"Right— Yes! Right away, sir!"
The seller practically vanishes from sight, rushing to fulfill the request. Rather than waiting outside, Alastor moves towards the doors, opening them wide. He turns his head towards the family, noting their expressions. The father looks confused, almost suspicious— which, fair enough, this is Hell after all, and although the Pride Ring has gone through many changes over the years, you can never be too careful.
The mother's face is mostly unreadable, although she seems to be evaluating him the same way he's doing it to her and her family. Taking in his demeanor, his clothing, the way he positions himself. Her daughter has, in contrast, the exact opposite disposition. She's excitable, eyes sparkling and smile wide enough to rival his own, bouncing on the balls of her feet. Her behavior reminds him of a certain optimistic young lady, which only furthers to solidify his decision.
"Well?" Alastor says, cocking an eyebrow and waving a hand towards the doors. "Shall we?"
"YES!" The teenager squeals, eyes somehow growing even sparklier. She practically floats through the doors, pausing briefly to turn towards her parents to show off her excitement with a near-silent "eee!"
Her father's expression melts into something hopelessly fond, while the mother's turns amused, shaking her head exasperatedly.
"Apologies," the mother says. "Our daughter's never been to a play in the Pride Ring. She loves new experiences."
"Well, she's in for quite the event! You all made an excellent decision, tonight's show is certainly one for the ages!"
The succubus chuckles, moving to step through the doors.
"I'll take your word for it."
The father, left alone outside, seems to hesitate for a moment. Then, he gives a tight smile, moving through the doors with a polite, if awkward, nod. Alastor follows him in, and internally sighs. The familiarity he feels with these people only seems to grow, and he wonders, briefly, if it was worth ditching his meeting to sit for the next few hours trying not to wonder how on earth he knew this family.
"You know," the imp says, dragging Alastor out of his thoughts. "I don't believe I caught your name, mister...?"
"Oh my!" Alastor exclaims, perhaps a touch too loudly in the near empty foyer, turning the heads of the man's family and the few stragglers who've yet to take their seats.
"Where are my manners? Allow me to introduce myself; my name is Alastor, the Media Demon!"
He takes the imp's hand, giving it an enthusiastic shake. He notes the man's expression is shocked, almost disbelieving. It brings a mischievous glint to Alastor's smile.
"Pleasure to be meeting you sir, quite the pleasure!"
#RETURN GIFT BE UPON YE!#thank you darling for the great gift and the inspiration it brought to me I LOVE IT#<3333#hazbin hotel#hazbin alastor#lucifer morningstar#charlie morningstar#lilith morningstar#lucilith#hellradio#media demon au
117 notes
·
View notes
Text

Hiyayyayayaya. This is my first time doing an Ask call on tumblr, so I'm very excited. This is my friend and I 's au, if anyone needs a synopsis of it, this is the tldr:
[ The Tulpar project is an investigation started by Taxonomist Grant Curly and Neurologist Jeremiah Zare as independent research of the Kăkóv (monster) gene expression. Although many years passed before achieving any progress, upon the anonymous donation of Semimonster material, and the following extraction of DNA, the genes were finally isolated after the integration of Genetist Anya Skvortsov to the project.
After this discovery, Polle Labs® began to sponsor the research and activities related to the research moved into the industrial facilities offered by Polle Labs®. The research brought a good stream of information for years until the untimely disappearance of Head scientist and author Grant Curly. His whereabouts remain unknown, but his coauthor has continued the research in his stead although with much less success in discoveries and achievements.
Dr. Anya, responsible for the isolation of the Kăkóv gene and its plasmid multiplication techniques, had been compiling documents, reports and illustrations for advanced research. Between that outlook and what remained of her personal diary, a disturbing view of what happend before her own disappearance and the incident called "The Pony Fires" is shown.
This is a documentation and restoration project made by Anonymous volunteers, Polle Labs® refuses to give any statements and/or collaboration for this effort. The countless lives lost working for the Tulpar project won't be forgotten, we will make sure if that. ]
So yeah, that's the synopsis, sooo vaguee so ask away! Tehehhe. Here are some refreshments of how the peps look like:
☆ Dr. Anya Skvortsov


☆ Head scientist Grant Curly


☆ Lab assistant Daisuke Sato Flores


☆ Mechanic Swansea Harold García


☆ Coauthor Neurologist Jeremiah Zare

#mouthwashing#mouthwashing fanart#artwork#mouthwashing game#swansea mouthwashing#curly mouthwashing#anya mouthwashing#daisuke mouthwashing#jimmy mouthwashing#pony express#lab monster au#curly lab director#Interview with a monster#amelien art#ask blog#send asks#mouthwashing au#scifimonster au
97 notes
·
View notes
Text
From their inception, foundations focused on research and dissemination of information designed ostensibly to ameliorate social issues--in a manner, however, that did not challenge capitalism. For instance, in 1913, Colorado miners went on strike against Colorado Fuel and Iron, an enterprise of which 40 percent was owned by Rockefeller. Eventually, this strike erupted into open warfare, with the Colorado militia murdering several strikers during the Ludlow Massacre of April 20, 1914. During that same time, Jerome Greene, the Rockefeller Foundation secretary, identified research and information to quiet social and political unrest as a foundation priority. The rationale behind this strategy was that while individual workers deserved social relief, organized workers in the form of unions were a threat to society. So the Rockefeller Foundation heavily advertised its relief work for individual workers while at the same time promoting a pro-Rockefeller spin to the massacre. For instance, it sponsored speakers to claim that no massacre has happened and tried to block the publication of reports that were critical of Rockefeller. According to Frederick Gates, who helped run the Rockefeller Foundation, the "danger is not the combination of capital, it is not the Mexican situation, it is the labor monopoly; and the danger of the labor monopoly lies in its use of armed force, its organized and deliberate war on society."
INCITE! Women of Color Against Violence, The Revolution Will Not be Funded: Beyond the Non-Profit Industrial Complex
94 notes
·
View notes
Text
Excerpt from this story from The Revelator:
Just because you don’t understand why or how federal funds are being spent doesn’t mean they’re waste or fraud — especially if you’re too lazy or ideologically focused to ask questions about the nature of the spending in the first place.
I learned those lessons more than a decade ago when I covered a great program called the Golden Goose Awards, which recognizes federally funded research that often seemed trivial at the time it was funded but later yielded lifesaving science or commercially important technologies.
At the time federally funded researchers often found their projects mocked, trivialized, belittled, or under attack — in ways that almost seem quaint today as the Trump administration and billionaire Elon Musk and his DOGE team take a chainsaw and blowtorch to the National Science Foundation, National Institutes of Health, NOAA, USGS, and other federal agencies.
How many of those now-unfunded research projects could have protected us from climate change, pollution and toxic chemicals, or the extinction crisis?
We may never know the answer to that question, but a look at two of the most recent Golden Goose Award winners offers a clue:
A project about the red-cockaded woodpecker that revealed new ways to protect all birds.
An observation that “bright pink penguin poop appeared on satellite images” yielded a 40-year effort to track penguin populations (and all wildlife) from space.
You can find a lot more in past years’ award recipients, including a study of frog skin that has saved 50 million human lives and another frog study that revealed the nature of the amphibian-killing chytrid fungus.
“The value of federally funded research has been proven time and time again,” says Barry Toiv, vice president for public affairs at the Association of American Universities, one of the organizations sponsoring the Golden Goose Award. “Economists suggest that 50% of growth over the last several decades has been a result of innovation, much of which is in turn a result of federally funded research at American universities.”
Toiv says this research is important even though “it’s impossible to know where so much of it is going to lead. It’s basic research, mostly, and it may not have some end-result in mind when it takes place.”
Federally funded research is the “only place that you can take that kind of chance,” says Freeze. “Private industry can’t do it because they have to show that they’re working on something that will eventually yield a profit.” He notes that the lifesaving research being done at his own organization, a nonprofit, would probably not be conducted at all in the for-profit world.
40 notes
·
View notes
Text

Why Black People Are Not a Serious People: A Garveyite Perspective
Introduction: The Crisis of Black Priorities
Marcus Garvey believed that Black people must take their destiny into their own hands to achieve true liberation. He famously stated:
“If you have no confidence in self, you are twice defeated in the race of life.”
Yet today, Black communities around the world remain politically weak, economically dependent, and socially disorganized. Despite having the talent, numbers, and resources to be a dominant global force, Black people:
Prioritize entertainment over education.
Focus on social integration rather than self-determination.
Spend wealth on consumer goods instead of wealth-building assets.
React emotionally to oppression rather than plan strategically for power.
From a Garveyite perspective, this lack of seriousness is not just an accident—it is the result of centuries of mental conditioning, systemic sabotage, and poor leadership. Until Black people take their future as seriously as other racial groups do, they will continue to be at the bottom of the global power structure.
1. Lack of Long-Term Vision and Strategic Thinking
A. Failure to Build Multi-Generational Wealth & Power
Black people often focus on short-term survival rather than long-term economic independence.
Other groups—Jews, Chinese, Indians—prioritize generational wealth, business ownership, and financial education, while Black people largely remain consumers.
Instead of buying land, businesses, and industries, Black communities spend billions on fashion, entertainment, and temporary luxuries.
If Black people were serious, they would invest in economic infrastructure rather than fueling white-owned corporations.
B. Emotional Reactions vs. Strategic Action
Black people often react to oppression with anger, protests, and hashtags rather than economic and political strategy.
Instead of organizing systematic boycotts, building independent political movements, or funding Pan-African initiatives, Black people wait for white approval and corporate sympathy.
Other groups use political lobbies, financial power, and institutional control to influence policies—Black people rely on moral arguments and symbolic victories.
Serious people understand that power is taken, not begged for.
2. Prioritization of Entertainment Over Education
A. Worship of Athletes & Entertainers Over Intellectuals & Business Leaders
Black people idolize rappers, athletes, and comedians while ignoring scientists, engineers, and economists.
Young Black children aspire to be entertainers rather than business owners or industrialists.
When entertainers do speak on serious issues, they are often uninformed and controlled by corporate sponsors.
If Black people were serious, they would celebrate intellectuals, inventors, and nation-builders as much as they do celebrities.
B. Disregard for Intellectual Development & Self-Improvement
Reading, studying, and research are not prioritized in many Black communities.
Schools in Black neighbourhoods are chronically underfunded, yet there is little organized effort to build independent schools.
Instead of spending time learning wealth strategies, global economics, or political science, Black people spend countless hours on gossip, social media debates, and entertainment.
Serious people master knowledge, control education, and build institutions.
3. Economic Irresponsibility & Consumer Mentality
A. Black Dollars Do Not Circulate in Black Communities
Black buying power exceeds $1.7 trillion in the U.S. alone, yet less than 5% of that money stays in Black businesses.
Many Black businesses struggle because Black people would rather shop at white-owned luxury brands than support their own.
Other groups—Asians, Jews, Arabs—spend money within their own communities before going outside.
If Black people were serious, they would circulate wealth among themselves rather than enriching other races.
B. Focus on Materialism Instead of Wealth-Building
Black people spend billions on designer clothing, jewellery, and foreign-owned liquor brands but fail to invest in stocks, real estate, or technology.
The hip-hop culture promotes flashy spending rather than financial discipline.
Many Black people believe that “looking rich” is more important than actually being rich.
Serious people build financial power before displaying wealth.
4. Political Naivety & Dependency on White Validation
A. Waiting for White Approval Instead of Building Independent Power
Black people rely on white politicians, celebrities, and corporations to fix their problems instead of organizing their own solutions.
Many believe that voting alone will solve oppression, despite history showing that political independence requires economic and institutional backing.
Black people celebrate token representation (Black faces in white spaces) rather than demanding systemic change.
If Black people were serious, they would fund their own political movements and demand real power, not just symbolic inclusion.
B. Divided by Ideology Instead of United by Common Interests
Black people remain divided by religion, nationality, skin tone, and political affiliations, while other races unite around shared interests.
African Americans, Afro-Caribbeans, and Africans often fail to collaborate for collective progress.
The media encourages gender wars, generational conflicts, and social divisions that prevent Black people from forming a united front.
Serious people put their differences aside and work toward collective empowerment.
5. Cultural and Spiritual Disconnection from African Roots
A. Worship of White Religious Imagery & Submission to Foreign Beliefs
Many Black churches still display white Jesus, reinforcing subconscious racial inferiority.
Black Muslims often prioritize Arab culture over African identity.
Traditional African spiritual systems, which empowered revolutions like the Haitian Revolution, are demonized as "pagan" or "evil."
Serious people embrace their own cultural and spiritual heritage, not that of their oppressors.
B. Lack of Pan-African Unity & Cooperation
Instead of building economic and political alliances between Africa and the diaspora, Black people remain disconnected.
Many Africans look down on Black Americans, while many Black Americans see Africa as irrelevant.
Other racial groups—such as the Chinese and Indians—build global economic networks, while Black people remain scattered and isolated.
Serious people unite globally and control their own destiny.
The Garveyite Solution: How Black People Can Become a Serious Race
1. Develop Long-Term Vision & Strategy
Shift from short-term gratification to long-term wealth-building.
Build institutions that will last generations.
Teach children about business, politics, and global strategy.
2. Prioritize Education & Intellectual Development
Fund independent Black schools and universities.
Encourage STEM fields, economics, and entrepreneurship.
Read, study, and master global power structures.
3. Control Black Wealth & Economic Power
Stop unnecessary spending on non-Black businesses.
Invest in land, technology, and industrial production.
Establish global trade networks between Africa and the diaspora.
4. Build Independent Political & Military Power
Create Black-funded political parties and candidates.
Support Pan-African leadership over Western-backed politicians.
Establish Black-controlled security forces to protect Black communities.
5. Reconnect with African Culture & Spirituality
Reject white supremacist religious imagery.
Restore African-centered faith systems that promote self-reliance.
Strengthen cultural pride and identity.
Conclusion: It’s Time to Get Serious or Stay Enslaved
Garvey warned us that Black liberation requires discipline, organization, and self-reliance. If Black people continue to:
Ignore financial responsibility.
Prioritize entertainment over education.
Wait for white approval.
Remain divided.
They will stay at the bottom of the global hierarchy.
However, if Black people get serious about their future, reclaim their wealth, and unite globally, they will achieve true power.
Garvey’s call remains: “Up, you mighty race, accomplish what you will!”
#black history#black people#blacktumblr#black tumblr#black#pan africanism#black conscious#africa#black power#black empowering#Garveyism#marcus garvey#black empowerment#EconomicFreedom#SeriousPeopleBuildPower#BlackUnity#blog
50 notes
·
View notes
Note
What do you think of a Lila character arc in which she learns that actually doing good and making her own visible achievements is more likely to get her better results than lying about her accomplishments and trying to sabotage others to make herself look better in comparison? That is, she figures out that if she really wants to *securely* get ahead in the world in the way that the show portrays her as wanting to rather than getting the 15-minutes-of-fame intervals created by her lies that she has to then keep feeding into, then she has to work WITH people instead of AGAINST them. Note that this is NOT a redemption arc that I’m describing; Lila would still not care at all about others or how they feel outside of direct usefulness to her in this scenario, but she would figure out how to employ her skills in a way that boosts HER up instead of tears OTHERS down (ex. lying and manipulating the reputations of individual people > acting and being an influencer on social media for sponsor brands) as well as how to network better and with WHOM it’s actually worth it to network with in the long run (could’ve seen that drop-of-a-dime betrayal from Gabriel Agreste in “Revelation” from a mile away, just sayin’). Lila would still be vain, vengeful and attention-focused the entire way through, with these being core qualities that don’t change about her, but while learning when to stop putting energy into her spite for someone due to either the actual “slight” against her being small in the grand scheme of things or the untouchability of her target in any way that really matters, as are the cases with Ladybug. In fact, this idea came from those posts that people have made since Season 3 and beyond pointing out two major character plot points of “Volpina” that conflict with common sense in hindsight concerning Lila. 1) After being deakumatized and calming down about the whole situation, Lila should have, while still not liking Ladybug, NOT continued to go after her from this point forward after realizing that Adrien was the only one who saw that whole outing of her lies and wasn’t angry at her for it as well as let her Ladyblog comments fade into obscurity as a safety net once considering how big of a public figure who does tangible good for the public Ladybug is and the reputation risk for little reward it would pose for her to keep talking about the hero at all. 2) If Lila really had done her research on the whole class and was as socially smart as the show wants her to come off as, she should’ve seen Marinette as someone to be “besties” with before her first day at school even started given her public accomplishments and connections up to that point (the sunglasses and album cover for Jagged in the music industry, her parents and great uncle in the food industry, her own merit as an up-and-coming fashion designer whose bowler hat design genuinely impressed Gabriel Agreste, who is known to not be impressed with or humor things he views as a waste of time as with Simon Says, etc.) the same way she did with Alya and the Ladyblog. Whether she still clings to Adrien given he’s still open to being friends with her as long as she stops lying (which she’s already resolved to do about Ladybug at minimum at this point) or she still gets annoyed with him trying to “lecture” her and decides he’s not worth the annoyance of putting up with over her two intended “besties” (Marinette and Lila wouldn’t be clashing since Lila would be trying to come up with a new game plan for school instead of lying now that Adrien’s aware of her and Marinette would still feel apologetic from the ending of “Volpina”) is up to preference, but I would LOVE to hear your thoughts on all of this regardless.
There's a lot here, so I'm going to start this post by stating what I think you're saying so that you know where I'm coming from in my answer in case I'm totally off base. The argument appears to be that a social climber (?) like Lila should have an arc where she learns that lies can only get her so far and that she's better off trying to make as many real connections as she can. The lies won't totally stop, but lying should become a last resort for her. I fully agree with that analysis. It's one of the many issues with Lila's writing. In the majority of the show, she is written like a compulsive liar and not like a clever manipulator.
A lot of the problem comes down to Lila's total lack of motivation. We don't know what her goals are and it feels like the writers don't either. It's why I put a question mark next to "social climber" in the last paragraph. I don't know if that's actually why she is! That makes her incredibly hard to write well.
When Lila's introduced, it comes across like she just wants to be seen as cool by her classmates. As the show goes on, that continues, but we also get this sense that she wants greater power of some kind and has some sort of master plan going on. Those are clashing behaviors. The kind of lies she tells at school are far too risky for someone with a grand plan. They put her at far too much risk of being outed.
For example, if she is actively manipulating a bunch of women into thinking that they're her mother, then why tell her classmates that she was out of town working for a charity with a well-known public figure like she did in Catalyst? That puts her at risk for a call home or even just having someone meet one of the mothers and mentioning the trip, which would make said mother start asking questions. Lila should be doing everything in her power to keep that from happening. She should want to blend in, not stand out. Canon even shows us how easily her lies would be outed if anyone other than Marinette cared to do basic fact checking:
Lila: (Waves) Hello, everyone! Miss Bustier's class: Hi Lila! Miss Bustier: We can't wait to hear what you've been doing since our last video chat. Tell us about your week in the Kingdom of Achu. Lila: It's absolutely amazing! Prince Ali invited me and my parents to his gorgeous palace. Marinette: Excuse me, Lila, but Prince Ali couldn't possibly have invited you because he is in the United States. Lila: (Laughs) I never said he was actually there, Marinette. I just said he invited us, that's all. His parents organized the visit- Marinette: She's lying, and I'll expose her for the fake that she is. Alya: Oh no, Marinette, not that again. She's not a liar. You're just jealous of Lila because she tried to hit on Adrien.
There is no point to this lie and it actively undermines Lila's character. This lie makes it look like she has no master plan and just lies compulsively for the thrill of it. The kind of character who tells lies like this one would not be capable of setting up multiple fake identities.
If you want to make Lila a master manipulator, then she needs to be written like she was in Oni-chan, which is one of the rare episodes where canon wrote her well:
Lila: What's the worst grade you've ever gotten? Adrien: An A- in math. Listen, Lila, you should forget about this. My father can be harsh with anyone he thinks is an intruder. Lila: (laughs) We're not doing anything wrong. Leave this to me. [Scene change to front the the mansion] Nathalie: I'm sorry, Adrien, but you know your father- Lila: Excuse me, ma'am. But is there any way I could ask him directly? Just in case. Nathalie: Mr. Agreste is busy designing and must not be disturbed for any reason. Adrien: I told you so. Lila: Oh, Adrien. I so wanted to help you make up all the schoolwork you missed due to all the modeling you've been doing lately. What will your father think if he finds out about your lower grades, Adrien? Who will he believe? Nathalie: Adrien, have your grades gone down? Lila: He’d never tell you himself up when I saw Adrien crying the other day because he only got an A-, I just felt like I had to offer him my help. I would’ve taken half an hour. (Nathalie raises her eyebrow at her) I understand. You’re only doing what you think is best. I did what I could, Adrien. Good luck. Nathalie: If it's only half an hour...
Lila is still a little too much here, but this is a kids show, so it makes sense to play up the lies a bit. With that context in mind, this is close enough to quality manipulation that I would feel like I was being a total nitpick if I complained about everyone being too gullible and Lila being a bad liar. Instead, I'm going to praise this writing. This is how she should have always been written. Minor lies used to get her connections or to manipulate her connections, but as much truth as she can manage to keep herself from being outed. Every lie should have a purpose and be carefully thought out. That's how manipulators work.
The Ladybug thing you brought up is another problem. If Lila's goal is manipulation, then she absolutely should have "forgiven" Ladybug and pretended to change. The lines she gives are those of a petty brat, not an evil mastermind:
Ladybug: I... totally overreacted and... never should've spoken to you like that. I'm sorry. Lila: Forget it, Ladybug; you were right. We'll never be friends.
While I hate the writing in Volpina, making Marinette feel guilty for confronting Lila could have been an excellent setup for Lila gaining power. If Lila went on to make the appearance of changing her behavior and Marinette believed that Lila was sorry, then you could have used Volpina as a semi-clumsy, but ultimately functional setup for Lila being a liar in the audience's eyes, but not in the eyes of the cast. Instead, Lila is enemies with both Ladybug and Marinette, which is the least interesting way to play this on every level.
As you rightly pointed out, Marinette has connections. Lila should want to be Marinette's friend! It would be far more interesting if Marinette trusted Lila and Lila was cool with Marinette while hating Ladybug. That's how identity shenanigan setups are supposed to function! It's not supposed to be just about the romance unless it's short form content. Imagine if the show had let Lila and Marinette have a cool dynamic too. It could lead to all sorts of interesting situations like Marinette picking Lila as a temp hero!
But, as always, that style of writing does not work in an episodic show and it definitely doesn't work in a formula show. Lila is simply a terrible pick for Miraculous at a fundamental, structural level and I have no idea how anyone is excited about her being the new main villain.
37 notes
·
View notes
Text
The Psychology of Consumer Behavior in Industry Research
Uncover the intricate web of consumer behavior psychology in industry research. Dive into the role of industry research reports, analysts, surveys, companies, and industry-sponsored research in decoding the mysteries of consumer choices.

Read More: https://articleblock.com/business/the-psychology-of-consumer-behavior-in-industry-research/
#industry research reports#industry research analyst#industry research survey#industry research companies#industry sponsored research
0 notes
Text
A bill that would ban fluoride and other harmful chemicals from Florida public water systems is heading to Governor Ron DeSantis’ desk.
The Florida House passed the prohibition on Tuesday. The Senate did so earlier in the month. It's the Senate bill, SB 700, that both chambers ultimately approved.
Fluoride is a chemical agent used in industrial capacities that communities around the U.S. have for decades added to their public drinking-water systems, allegedly to help protect against tooth decay.
Whether it actually prevents tooth decay may be up for debate.
What’s not up for debate any longer is that fluoridated water, even in relatively small amounts, causes low IQs in children. Even Harvard University researchers found this to be true.
And yet, in 2025, if you state these facts you’re still labeled a conspiracy theorist. It’s impossible to get articles like the one on Harvard to come up in search engines like Google, DuckDuckGo and Yahoo. I had to use the Russian search engine Yandex to find it.
Supporters of the Florida legislation, such as Republican Rep. Danny Alvarez, said citizens shouldn't be forced to have additives in their water if they don't want them. This was a clever way of skirting around the truth, which is that fluoride is poison, but you can’t blame the lawmaker given the information matrix in which we live.
"This is not about fluoride,” said Alvarez, a sponsor of the House version of the legislation. “This is about your liberty.”
16 notes
·
View notes
Text
For a while in the mid-2000s, a refrigerator-sized box in Abu Dhabi was considered the greatest chess player in the world. Its name was Hydra, and it was a small super-computer—a cabinet full of industrial-grade processors and specially designed chips, strung together with fiber-optic cables and jacked into the internet.
At a time when chess was still the main gladiatorial arena for competition between humans and AI, Hydra and its exploits were briefly the stuff of legend. The New Yorker published a contemplative 5,000-word feature about its emergent creativity; WIRED declared Hydra “fearsome”; and chess publications covered its victories with the violence of wrestling commentary. Hydra, they wrote, was a “monster machine” that “slowly strangled” human grand masters.
True to form as a monster, Hydra was also isolated and strange. Other advanced chess engines at the time—Hydra’s rivals—ran on ordinary PCs and were available for anyone to download. But the full power of Hydra’s 32-processor cluster could be used by only one person at a time. And by the summer of 2005, even the members of Hydra’s development team were struggling to get a turn with their creation.
That’s because the team’s patron—the then 36-year-old Emirati man who’d hired them and put up the money for Hydra’s souped-up hardware—was too busy reaping his reward. On an online chess forum in 2005, Hydra’s Austrian chief architect, Chrilly Donninger, described this benefactor as the greatest “computer chess freak” alive. “The sponsor,” he wrote, “loves to play day and night with Hydra.”
Under the username zor_champ, the Emirati sponsor would log in to online chess tournaments and, with Hydra, play as a human-computer team. More often than not, they would trounce the competition. “He loved the power of man plus machine,” one engineer told me. “He loved to win.”
Hydra eventually got overtaken by other chess computers and was discontinued in the late 2000s. But zor_champ went on to become one of the most powerful, least understood men in the world. His real name is Sheikh Tahnoun bin Zayed al Nahyan.
A bearded, wiry figure who’s almost never seen without dark sunglasses, Tahnoun is the United Arab Emirates’ national security adviser—the intelligence chief to one of the world’s wealthiest and most surveillance-happy small nations. He’s also the younger brother of the country’s hereditary, autocratic president, Mohamed bin Zayed al Nahyan. But perhaps most important, and most bizarrely for a spymaster, Tahnoun wields official control over much of Abu Dhabi’s vast sovereign wealth. Bloomberg News reported last year that he directly oversees a $1.5 trillion empire—more cash than just about anyone on the planet.
In his personal style, Tahnoun comes across as one-third Gulf royal, one-third fitness-obsessed tech founder, and one-third Bond villain. Among his many, many business interests, he presides over a sprawling tech conglomerate called G42 (a reference to the book The Hitchhiker’s Guide to the Galaxy, in which “42” is a super-computer’s answer to the question of “life, the universe, and everything”). G42 has a hand in everything from AI research to biotechnology—with special areas of strength in state-sponsored hacking and surveillance tech. Tahnoun is fanatical about Brazilian jiujitsu and cycling. He wears his sunglasses even at the gym because of a sensitivity to light, and he surrounds himself with UFC champions and mixed martial arts fighters.
According to a businessman and a security consultant who’ve met with Tahnoun, visitors who make it past his layers of loyal gatekeepers might get a chance to speak with him only after cycling laps with the sheikh around his private velodrome. He has been known to spend hours in a flotation chamber, the consultant says, and has flown health guru Peter Attia into the UAE to offer guidance on longevity. According to a businessman who was present for the discussion, Tahnoun even inspired Mohammed bin Salman, Saudi Arabia’s powerful crown prince, to cut back on fast food and join him in a quest to live to 150.
But in recent years, a new quest has taken up much of Sheikh Tahnoun’s attention. His onetime chess and technology obsession has morphed into something far bigger: a hundred-billion-dollar campaign to turn Abu Dhabi into an AI superpower. And the teammate he’s set out to buy this time is the United States tech industry itself.
In the multiplayer game of strategy that is the AI arms race, the US controls the board right now for a pretty simple reason. A single American hardware company, Nvidia, makes the chips that train the most competitive AI models—and the US government has moved to restrict who can buy these Nvidia GPUs (as the chips are called) outside the country’s borders. To take advantage of this clear but jittery lead over China, the CEOs of America’s AI giants have fanned out across the globe to sweet-talk the world’s richest investors—people like Tahnoun—into financing what amounts to an enormous building boom.
Lurking behind every synthetic podcast and serving of AI slop is a huge, thrumming data center: Hundreds of Hydra-sized server cabinets lined up in tight rows, running computing processes that are tens or hundreds of times more energy-intensive than ordinary web searches. And behind those is another set of data centers that train foundational AI models. To keep pace with demand, AI companies need more data centers all over the world—plus the land to put them on, the water to cool them, the electricity to power them, and the microchips to run them. Nvidia CEO Jensen Huang has predicted that tech companies will pour a trillion dollars into new AI data centers over the next five years.
Building out the next phase of AI, in short, is set to require mind-boggling amounts of capital, real estate, and electricity—and the Gulf States, with their vast oil wealth and energy resources, possess all three. Saudi Arabia, Kuwait, and Qatar have all set up major AI investment funds in the past couple of years. But as a home for new data centers and a source of investment capital, the UAE has emerged as a particularly attractive potential partner on a number of fronts—from its sheer wealth to its brand-new nuclear power supply to the relative sophistication of its own AI sector.
But there’s a rub: Any American AI partnership with the UAE is, in some way, a relationship with Sheikh Tahnoun himself—and for years many of Tahnoun’s most important technology partners have been Chinese.
The pairing was only natural, given Tahnoun’s record as a spy chief with vast commercial interests in high-tech state control. Tahnoun spent the early 2020s forging deep business and personal ties with Beijing, to the point that some products sold by G42 came to be nearly indistinguishable from Chinese ones. A G42 subsidiary called Presight AI, for one, sold surveillance software to police forces worldwide that bore a close resemblance to systems used by Chinese law enforcement. The Chinese telecom giant Huawei’s footprints in G42 went even deeper. Early in the generative-AI boom, Huawei’s engineers moved freely through Abu Dhabi’s most sensitive tech facilities as they designed massive AI training centers.
But in August of 2023, Washington threw down a gauntlet. It restricted exports of Nvidia GPUs to the Middle East—the very hardware that Abu Dhabi needed to realize its own AI ambitions. No company using Huawei equipment would get access. So Tahnoun pivoted, hard. In early 2024, G42 announced it was severing ties with China and would rip out Chinese equipment. Chinese nationals began quietly departing Abu Dhabi’s tech sector.
At the same time, US and UAE leaders went into a fevered phase of mutual courtship. Scores of public relations consultants, lawyers, and Beltway lobbyists set about portraying Tahnoun as a safe pair of hands in which to place US technology and trust. Marty Edelman, the emirate’s most trusted American lawyer, helped orchestrate the strategy from New York. The UAE’s ambassador to Washington, Yousef Al Otaiba, deployed his considerable political capital to vouch for Tahnoun. Meanwhile, US government and tech leaders tried to maneuver what promised to be a huge spigot of Emirati money into the United States, to feed AI companies’ need for investment.
The first sign that the two sides had reached an understanding was, bizarrely, a deal that flowed in the opposite direction. In an unusual agreement brokered largely by officials in the Biden administration, Microsoft announced in April 2024 that it was investing $1.5 billion in Tahnoun’s G42, acquiring a minority stake in the company. According to remarks by a Biden official who helped steer the agreement, the objective was to get G42 to “work with Microsoft as an alternative to Huawei.” In the first phase of the relationship, G42 would gain access to Microsoft’s AI computing power on its Azure cloud platform, at a data center inside the UAE. And Brad Smith, Microsoft’s president, would join the board of G42—a kind of American chaperone inside the company.
The big gushers of cash from the UAE were still to come, as were any Nvidia chips for Abu Dhabi. But the Microsoft deal amounted to a US government seal of approval for further business with the Emirates. In the summer of 2024, Tahnoun embarked on a charm offensive across the United States, with a visit to Elon Musk in Texas and a jiujitsu session with Mark Zuckerberg. Meetups with Bill Gates, Satya Nadella, and Jeff Bezos followed in quick succession. The most important meetings, however, took place at the White House, with figures like national security adviser Jake Sullivan, Commerce secretary Gina Raimondo, and President Joe Biden himself.
As the frenzied campaign to reframe Tahnoun and G42’s image seemed to gain traction—and the US seemed poised to loosen export controls on advanced chips for the UAE—some inside the US national security establishment were, just as frantically, waving caution flags. One of their fears is that the intellectual property of the United States could still leak to China. “The Emiratis are the consummate hedgers,” a former senior US security official told me. “The question everyone has: Are they playing both sides?” In a July open letter, US congressman Michael McCaul, the chair of the House Foreign Affairs Committee, called for “significantly more robust national security guardrails” to be placed on the UAE before the US exported any sensitive technology to the country.
But the other fear is of the UAE itself—a country whose vision of using AI as a mechanism of state control is not all that different from Beijing’s. “The UAE is an authoritarian state with a dismal human rights record and a history of using technology to spy on activists, journalists, and dissidents,” says Eva Galperin, director of cybersecurity at the Electronic Frontier Foundation. “I don’t think there is any doubt that the UAE would like to influence the course of AI development”—in ways that are optimized not for democracy or any “shared human values,” but for police states.
This past summer, around the same time that Tahnoun was barnstorming through America’s dojos and C-suites, Mohammed bin Salman, the crown prince of Saudi Arabia, was hosting some of the world’s leading technology thinkers—including former Google CEO Eric Schmidt—at his vast South African hunting estate called Ekland. They visited game parks, were waited on by butlers, and discussed Saudi Arabia’s future role in AI.
Not long after, Schmidt made a trip to the Biden White House to air his concerns that the US cannot produce enough electricity to compete in AI. His suggestion? Closer financial and business ties with hydroelectric-rich Canada. “The alternative is to have the Arabs fund [AI],” he told a group of Stanford students on video the following week. “I like the Arabs personally … But they’re not going to adhere to our national security rules.”
Those concerns over the Gulf States’ reliability as allies (and their tendencies to engage in unsavory practices like targeting journalists and waging proxy wars) haven’t stopped their money from flowing into US tech companies. Earlier in the year, Saudi Arabia’s sovereign Public Investment Fund announced a $40 billion fund focused on AI investments, aided by a strategic partnership with the Silicon Valley venture capital firm Andreessen Horowitz. Kingdom Holding, an investment firm run by a Saudi royal who is deeply obedient to the crown prince, has also emerged as one of the biggest investors in Elon Musk’s startup xAI.
The New York Times wrote that the new Saudi fund made that country “the world’s largest investor in artificial intelligence.” But in September, the UAE eclipsed it: Abu Dhabi announced that a new AI investment vehicle called MGX would partner with BlackRock, Micro-soft, and Global Infrastructure Partners to pour more than $100 billion into, among other things, building a network of data centers and power plants across the United States. MGX—which is part of Tahnoun’s sovereign wealth portfolio—has also reportedly been in “early talks” with OpenAI CEO Sam Altman about what Altman hopes will be a 5 to 7 trillion-dollar moonshot chipmaking venture to create an alternative to Nvidia’s scarce GPUs.
The spigot of Emirati cash was now open. And in turn, within days of the MGX announcement, the news site Semafor reported that the US had cleared Nvidia to sell GPUs to G42. Some of the chips were already being deployed in Abu Dhabi, the news site reported, including “a sizable order of Nvidia H100 models.” The US had finally given Tahnoun some of the hardware he needed to build his next Hydra. Which raises the salience of two questions: What kind of game is Sheikh Tahnoun playing this time? And how exactly did he get control of so much wealth?
on some level, nearly every story about royalty in the Gulf is a story about succession—about paternalistic families trying to ward off external threats, and the internal rivalries that crop up when inherited power is up for grabs.
Tahnoun and his brother Mohamed are both sons of the UAE’s first president, Zayed bin Sultan al Nahyan—an iconic figure revered as the father of the nation.
For much of Zayed’s life, what is now the city of Abu Dhabi was an austere, seasonal fishing village with a harsh climate, a brackish water supply, and a nomadic population of about 2,000 people. The rest of the emirate had several thousand more Bedouin inhabitants. As rulers, the al Nahyans were paid in tributes and taxes, and served as custodians of the emirate’s shared resources. Their lifestyle wasn’t all that much better than that of their fellow tribesmen. But still it was dangerous at the top. Before Zayed, two of the last four sheikhs of Abu Dhabi had been assassinated by their brothers; another had been killed by a rival tribe.
Zayed, for his part, seized power from his older brother in a bloodless coup aided by the British in 1966—just as oil and its transformative wealth started flowing into Abu Dhabi. Where his elder sibling resisted spending Abu Dhabi’s new fortune, Zayed embraced modernization, development, and a vision for uniting several tribes under a single state—setting the stage for the creation of the United Arab Emirates in 1971.
When the UAE was formed, Tahnoun was almost 3 years old. A middle child among Zayed’s 20-odd sons, Tahnoun is one of the so-called Bani Fatima—the six male children of Zayed’s most favored wife, Fatima, and his most important heirs. Zayed groomed these sons to go abroad, become worldly, and take up the mantle of the UAE’s future. But even as he established a state that carefully distributed new oil wealth among Abu Dhabi’s Bedouins, Zayed steered his heirs away from business and self-enrichment. Perhaps mindful of the assassinations and coups that preceded him, Zayed wanted to ward off the perception that the al Nahyans were benefiting unfairly from their role as custodians of the country.
In the mid-1990s, Tahnoun found himself in Southern California. One day in 1995 he walked into a Brazilian jiujitsu dojo in San Diego, asking to be trained. He introduced himself as “Ben” and, according to an article on Brazilian Jiu-Jitsu Eastern Europe’s website, went out of his way to show humility, arriving early and helping to clean up. Only later did he reveal he was a prince of Abu Dhabi.
As Zayed’s health failed in the late 1990s, his sons began to step into bigger roles—and to break away from his guidance by starting businesses of their own. It was around this time that Tahnoun started his first holding company, the Royal Group, the entity he would use to incubate the Hydra chess computer. He also started a robotics company that produced a humanoid robot, REEM-C, which in turn was named after an island in Abu Dhabi where he made a series of real estate investments.
When Zayed died in 2004, Tahnoun’s eldest brother, Kha-lifa, became the new ruler of Abu Dhabi and president of the UAE, and Mohamed, the eldest of the Bani Fatima, became the crown prince. The other sons took on an array of official titles, but their roles were more ambiguous.
As a reporter based in Abu Dhabi from 2008 to 2011, I fell into the pastime of “sheikh watching,” a Gulf-royal version of Kremlinology that involves reading between the lines of announcements and moves, and keeping in touch with palace insiders who occasionally betray a few secrets. At the time, Tahnoun seemed like a fascinating dilettante very far from actual power—he held no serious role in the government and seemed preoccupied with growing his fortune, dabbling in technology, and changing the skyline of Abu Dhabi.
That all changed when Tahnoun stepped up as the family member with the greatest knack for wielding a growing tool for nation-states: cyberespionage.
In July 2009, thousands of BlackBerry users across the UAE noticed their phones growing dangerously hot. The culprit was a supposed “performance update” pushed by Etisalat, the UAE’s largest telecom provider. In reality, it was spyware—an early experiment in mass surveillance that backfired spectacularly when BlackBerry’s parent company exposed the scheme.
I experienced this myself one day on a trip from Abu Dhabi to Dubai, bringing my BlackBerry to my ear and finding it so hot it nearly burned my face. It was my first direct, personal experience of the UAE’s hidden police state. But shades of its existence are apparent to anyone who has spent time in the Gulf States. Violent crime is nearly nonexistent, and life can be smooth, even luxurious. But in moments of stress or risk, these countries can become very dangerous places, especially for residents who dare hint at dissent.
The revolutions of the Arab Spring in 2011—which saw four Middle Eastern autocrats topple in the face of massive, Twitter-organized crowds—only heightened the UAE’s resolve to stamp out any green shoots of democracy. When a handful of Emirati activists made their own mild case for human rights and political reform in 2011, the state convicted them on charges of royal defamation. Then it promptly pardoned and released them into a life of surveillance and harassment.
While there’s no evidence that Tahnoun had any direct involvement in the BlackBerry debacle, he would soon come to oversee an empire capable of far more sophisticated spycraft. In 2013, he was named deputy national security adviser—around which time the UAE’s ambitions to spy on its residents and enemies started to reach an industrial scale.
For several years at that point, the UAE had been running a secret program known as Project Raven, formed in 2008 under a contract with consultant and former US counterterrorism czar Richard Clarke. The US National Security Agency had blessed the arrangement, meant to give the UAE state-of-the-art surveillance and data analysis capabilities to contribute to the war on terror. But around 2014, Project Raven took a new tack. Under the new management of a US contractor called CyberPoint, it recruited dozens of former US intelligence operatives with a simple pitch: tax-free salaries, housing stipends, and a chance to fight terrorism.
But fighting terrorism was, in fact, only part of the agenda. Within two years, the project’s management changed hands yet again to a company called Dark-Matter, effectively an Emirati state-owned firm. Emirati intelligence leaders placed Project Raven under their own roof—just two floors from the UAE’s own version of the NSA. The message to Project Raven’s employees: Join DarkMatter or leave.
For those who remained, the job included tracking journalists, dissidents, and other perceived enemies of the state and the royal family. Among the key American operatives who stayed on with DarkMatter was Marc Baier, a veteran of the NSA’s elite Tailored Access Operations unit. Emails later showed Baier chatting with the Italian surveillance firm Hacking Team, describing his UAE clients as “the most senior” and demanding white-glove service as he shopped for hacking tools. Other former NSA hackers on the Project Raven team got busy developing custom attacks for specific devices and accounts.
They got to human rights activist Ahmed Mansoor—one of the Emiratis who had blogged in favor of democratic reform during the Arab Spring—through his child’s baby monitor. It was 2016, and Mansoor had grown used to his devices behaving strangely: phones that grew mysteriously hot, suspicious text messages, drained bank accounts, according to a person familiar with his experiences. His phone had even once been infected with Pegasus spyware, a notorious product made by the Israeli cyber-arms firm NSO Group. But the baby monitor was new. Unknown to him, operatives at DarkMatter were using it to listen to his family’s private conversations.
In another project, DarkMatter assembled what it called a “tiger team”—a task force to install mass-surveillance hardware in public places. These probes would be capable of “intercepting, modifying, and diverting” nearby traffic on UAE’s cellular networks, according to an Italian security researcher who was being courted by DarkMatter in 2016. “To operate as we want them to, these probes are going to be put everywhere,” the prospective hire, Simone Margaritelli, was told in an email during his recruitment process.
And who was ultimately overseeing all this activity? In early 2016, Tahnoun had been named national security adviser, which placed him fully in charge of UAE intelligence. And there are signs that the ultimate controlling party over DarkMatter was none other than Tahnoun’s investment firm, the Royal Group.
Eventually, I may have become a target of the UAE’s hacking apparatus myself. In 2021 a coalition of journalists called the Pegasus Project informed me that my phone had been targeted by the UAE using Pegasus spyware in 2018. At the time I’d been reporting on a global financial scandal that implicated a member of the Abu Dhabi royal family—Sheikh Tahnoun’s brother, Mansour. The UAE denied that it had targeted many of the people identified, including me.
The hacking and tracking of American citizens would eventually become a red line for some of Project Raven’s former intelligence agents. “I am working for a foreign intelligence agency who is targeting US persons,” a Project Raven whistleblower named Lori Stroud would tell Reuters in 2019. “I am officially the bad kind of spy.”
The ensuing scandal resulted in US federal charges for several of its ex-NSA leaders, including Baier. DarkMatter and Project Raven, meanwhile, were painstakingly broken down, scattered, rebranded, and then subsumed into other companies and government departments. Many of their pieces and personnel eventually moved under the umbrella of a single new entity founded in 2018—called G42.
G42 has denied publicly it had any connections to Dark-Matter, but the threads aren’t hard to see. One DarkMatter subsidiary, for instance, was an entity that worked especially closely with Chinese companies. Not only did it eventually appear to become part of G42, but the subsidiary’s CEO, Peng Xiao, went on to become the CEO of G42 itself.
A Chinese speaker who studied computer science at Hawaii Pacific University, Xiao’s past is otherwise a black box. Though he was a US citizen for a time, he eventually surrendered his US passport for UAE citizenship—an exceedingly rare honor for a non-Emirati. And under a subsidiary of G42 called Pax AI, Xiao helped produce the next evolutionary step in DarkMatter’s legacy.
One morning in 2019, millions of phones across the UAE lit up with a cheery notification. A new messaging app called ToTok promised what WhatsApp couldn’t—unrestricted calling in a country where the voice-calling function of most chat apps was blocked. Within weeks, it had shot to the top of Apple’s and Google’s app store even beyond the Emirates. But there was a catch. Each time someone tapped the app icon, the user gave the app access to everything on that phone—photos, messages, the camera, voice calls, location.
Data from millions of phones flowed to Pax AI. Like DarkMatter before it, Pax AI operated from the same building as the UAE’s intelligence agency. The ToTok app itself came from a collaboration with Chinese engineers. For a regime that had spent fortunes on NSO Group’s Pegasus spyware and DarkMatter’s hacking teams, ToTok was elegantly simple. People didn’t have to be laboriously targeted with spyware—they were eagerly downloading it.
Representatives of ToTok adamantly denied that their product was spyware, but an engineer who worked at G42 at the time told me that all of the voice, video, and text chats were analyzed by AI for what the government considered suspicious activity. (Among the easiest ways to get flagged: placing calls to Qatar, then a rival in a mutual cyberwar, from within the UAE.) G42 declined to comment on specific details for this story but responded to WIRED with an overall statement: “G42 is steadfast in its commitment to responsible innovation, ethical governance, and delivering transformative AI solutions globally.”
Inside G42, staff sometimes refer to Tahnoun as “Tiger,” and his orders can swiftly change the company’s course. One mandate from Tiger, according to a former engineer, was to build him either a business that generates $100 million in revenue a year or a technology that makes him famous. In the workplace, there is no mistaking that the conglomerate has one foot inside the security state: Most of the company’s technology and data centers are based in Zayed Military City, a restricted-access zone, and all G42 staff need to pass security clearances to get hired.
Through G42, government intelligence services, and other cybersecurity entities, Tahnoun had effectively come to oversee the UAE’s entire hacking apparatus. But at a certain point, control over the UAE’s spy sector and the industry around it wasn’t enough for Tahnoun.
By the turn of the decade, Tahnoun had ambitions for more political power over the whole of the Emirates. His sibling Mohamed had been serving as the de facto leader of the country since their brother President Kha-lifa suffered a major stroke in 2014. Now, as Khalifa’s health continued to fail and Mohamed’s formal accession to the throne was becoming imminent, the position of the next crown prince was up for grabs.
These moments of dynastic uncertainty can be dangerous. In Saudi Arabia, the sons of the country’s first king, Abdulaziz al-Saud, have taken the throne one after the other ever since the 1950s. By the time the current king, Salman, took power in 2015, he was 80 years old, and the ranks of potential heirs below him had become crowded, corrupt, and rife with internal tensions. That’s why, in 2017, King Salman’s son Mohammed, or MBS, struck out to eliminate his rivals—mostly cousins and their aides—by arresting them in a purge, asserting himself as the new strongman.
In Abu Dhabi, Tahnoun’s argument in the succession debate, according to royal insiders, was that his brother Mohamed should follow precedent and allow the sons of Zayed to rule while they were of good health and sound mind—a system that would place him in contention. But Mohamed was adamant that his own son Khalid should be crown prince, a signal to the country’s large youth population that they were represented high up in government.
Tahnoun argued his point for more than a year, even providing evidence that Mohamed’s plan contradicted their father’s request for succession. But in the end, the brothers worked out a deal. Tahnoun agreed to set aside his ambition to be the crown prince or ruler—in exchange for vast power over the country’s financial resources. It was this bargain that would ultimately put him in charge of $1.5 trillion in sovereign wealth.
In 2023, Tahnoun was made chairman of Abu Dhabi Investment Authority, the largest and most important sovereign wealth fund in the country. Khalid’s appointment as crown prince was announced weeks later.
Officially, Tahnoun got a modest bump in title to become deputy ruler along with his brother Hazza. But those dealing with Abu Dhabi over the past few years say the same thing: Tahnoun’s powers have increased by an extraordinary degree, and not just in finance. He has also taken over diplomacy with Iran, Qatar, and Israel, and even handled the United States for a time when relations with the Biden administration declined. “Whenever there’s a difficult file, it’s given to Tahnoun,” says Kristian Coates Ulrichsen, a scholar of Gulf politics at the Baker Institute for Public Policy at Rice University. That skill has helped him “grow his power enormously,” Ulrichsen says.
As Tahnoun has gained access to new resources, he has plowed them into his maze of investments and conglomerates. Under the Royal Group, he controls not only G42 but also another conglomerate called the International Holding Company—itself a massive consortium that employs more than 50,000 people and owns everything from a Zambian copper mine to the St. Regis golf club and island resort in Abu Dhabi. He also oversees First Abu Dhabi Bank, which is the UAE’s largest lender, and another multibillion-dollar sovereign wealth fund called ADQ.
And now, with a growing position in the global AI arms race, Tahnoun’s empire also includes a stake in the future of humanity.
In December, the US government confirmed it had authorized the export of some Nvidia GPUs to the UAE—specifically to a Microsoft-operated facility inside the country. At G42, subsidiaries have kept multi-plying: Space42 focuses on using AI to analyze satellite imaging data; Core42 aims to build massive AI data centers across Abu Dhabi’s deserts.
Inside the US security establishment, many remain worried about the US tech sector’s increasingly close relationship with the UAE. One unsettling fact, according to a former security official, was that China made no protest over Tahnoun’s decision to tear out all of Huawei’s equipment and sever ties with the company in 2023. “They didn’t raise a peep,” the official told me. When Sweden banned Chinese companies Huawei and ZTE from its 5G rollout in 2020, Beijing’s foreign ministry spoke out against it, and Swedish telecom giant Ericsson lost huge amounts of business in China in retaliation. By contrast, G42’s big breakup with China somehow got a pass—suggesting to the official that there may be some kind of backdoor understanding between the two nations.
In a statement to WIRED, US congressman Michael McCaul reiterated his concern that technology could leak to China through the UAE’s deal with Microsoft, and stressed the need for tighter guardrails. “Before advancing this partnership and others like it further, the US must first establish robust, legally binding protections that apply broadly to AI cooperation with the UAE,” he said.
But even if those guardrails were put into place, the UAE has a history of finding ways to do what it wants. I’m reminded of the briefings that executives from Israel’s NSO Group gave to journalists for a time in the early 2010s, assuring them that Pegasus spyware had safeguards against abuse—and that Pegasus clients (like the UAE) would be blocked from targeting US and UK phone numbers (like mine). And I’m reminded of the blessings that the NSA gave to Project Raven at its inception.
While Donald Trump and his new administration are expected to continue with export controls over GPU chips, the view from people inside Tahnoun’s orbit is that the new administration will likely be much more “flexible” about the UAE’s AI ambitions. Plus at least one Trumpworld insider has a vested interest in the relationship: The UAE, Qatar, and Saudi Arabia have together contributed more than $2 billion to Jared Kushner’s private equity fund, guaranteeing the fund some $20 million to $30 million in annual management fees alone. Abu Dhabi’s leaders have consulted with Kushner and other Trump insiders, including former secretary of state Mike Pompeo, on AI policy, according to people familiar with the discussions.
While the continued supply of GPUs could be a remaining source of leverage for the US, it could be a declining one as rival chips improve. Some analysts argue that, even now, export controls are not the source of strength that American officials think they are. “AI is not like nuclear power where you can restrict the materials,” says computer security expert Bruce Schneier. AI technology is already highly distributed, he says, and the idea that American companies are at a huge and absolute advantage is a mirage.
Now that Tahnoun has been “brought inside the tent”—and given a key and expanding role as an investor of choice for the current winners in the AI race—he has certainly succeeded in gaining some leverage of his own. And those who keep needing money from the UAE may be happy to see it gain more clout. At a World Government Summit last year, Sam Altman suggested that the UAE could even serve as the world’s “regulatory sandbox” for AI—a place where new rules for governing the technology can get written, tested, and advanced.
Meanwhile, the Middle East could be entering a period, like the aftermath of the Arab Spring, when rules are largely off the table. Now that rebels have taken over Syria from the regime of Bashar al Assad, the Gulf States—especially the UAE—will be anxious to increase surveillance to avoid any spread of Islamist unrest. “We’re going to see more repression, more use of surveillance technologies,” says Karen Young, a senior fellow at the Middle East Institute in Washington. And when it comes to managing threats and winning games of strategy, Tahnoun likes to make sure he’s playing with the most fearsome machine in the world.
20 notes
·
View notes
Note
Raw milk does carry increased risk of disease, but there are actually health benefits to drinking it, so I think as long as it's an informed choice and they're getting it from a reliable source it's okay. The idea that raw milk is always dangerous is misleading and sponsored by the commercial dairy industry. I encourage you to do some research on the matter, as it's nuanced and it's not just "raw milk bad" or "raw milk good."
It’s been four fucking months man I’m not doing this again
11 notes
·
View notes
Text
The Clean Energy Revolution Is Unstoppable. (Wall Street Journal)

Surprising essay published by the Wall Street Journal. Actually, two surprises. The first is an assertion that the fossil fuel industry is parading to its death, regardless of the current trump mania, while the renewables industry is marching toward success due to dramatic decreases in cost. The second surprise is that the essay is published in the Wall Street Journal, which we all know can be a biblical equivalent for the right wing. But be careful with that right wing label: today's right wing (e.g., MAGA) or the traditional conservative republican right wing, which is more aligned with saving money and making money and avoiding political headwinds.
Here's the entire essay. I rarely post a complete essay, but this one made me happy and feel good, and right now I/we damn well need to learn something to make us happy and feel good.
Since Donald Trump’s election, clean energy stocks have plummeted, major banks have pulled out of a U.N.-sponsored “net zero” climate alliance, and BP announced it is spinning off its offshore wind business to refocus on oil and gas. Markets and companies seem to be betting that Trump’s promises to stop or reverse the clean energy transition and “drill, baby, drill” will be successful.
But this bet is wrong. The clean energy revolution is being driven by fundamental technological and economic forces that are too strong to stop. Trump’s policies can marginally slow progress in the U.S. and harm the competitiveness of American companies, but they cannot halt the fundamental dynamics of technological change or save a fossil fuel industry that will inevitably shrink dramatically in the next two decades.
Our research shows that once new technologies become established their patterns in terms of cost are surprisingly predictable. They generally follow one of three patterns.
The first is a pattern where costs are volatile over days, months and years but relatively flat over longer time frames. It applies to resources extracted from the earth, like minerals and fossil fuels. The price of oil, for instance, fluctuates in response to economic and political events such as recessions, OPEC actions or Russia’s invasion of Ukraine. But coal, oil and natural gas cost roughly the same today as they did a century ago, adjusted for inflation. One reason is that even though the technology for extracting fossil fuels improves over time, the resources get harder and harder to extract as the quality of deposits declines.
There is a second group of technologies whose costs are also largely flat over time. For example, hydropower, whose technology can’t be mass produced because each dam is different, now costs about the same as it did 50 years ago. Nuclear power costs have also been relatively flat globally since its first commercial use in 1956, although in the U.S. nuclear costs have increased by about a factor of three. The reasons for U.S. cost increases include a lack of standardized designs, growing construction costs, increased regulatory burdens, supply-chain constraints and worker shortages.
A third group of technologies experience predictable long-term declines in cost and increases in performance. Computer processors are the classic example. In 1965, Gordon Moore, then the head of Intel, noticed that the density of electrical components in integrated circuits was growing at a rate of about 40% a year. He predicted this trend would continue, and Moore’s Law has held true for 60 years, enabling companies and investors to accurately forecast the cost and speed of computers many decades ahead.
Clean energy technologies such as solar, wind and batteries all follow this pattern but at different rates. Since 1990, the cost of wind power has dropped by about 4% a year, solar energy by 12% a year and lithium-ion batteries by about 12% a year. Like semiconductors, each of these technologies can be mass produced. They also benefit from advances and economies of scale in related sectors: solar photovoltaic systems from semiconductor manufacturing, wind from aerospace and batteries from consumer electronics.
Solar energy is 10,000 times cheaper today than when it was first used in the U.S.’s Vanguard satellite in 1958. Using a measure of cost that accounts for reliability and flexibility on the grid, the International Energy Agency (IEA) calculates that electricity from solar power with battery storage is less expensive today than electricity from new coal-fired plants in India and new gas-fired plants in the U.S. We project that by 2050 solar energy will cost a tenth of what it does today, making it far cheaper than any other source of energy.
At the same time, barriers to large-scale clean energy use keep tumbling, thanks to advances in energy storage and better grid and demand management. And innovations are enabling the electrification of industrial processes with enormous efficiency gains.
The falling price of clean energy has accelerated its adoption. The growth of new technologies, from railroads to mobile phones, follows what is called an S-curve. When a technology is new, it grows exponentially, but its share is tiny, so in absolute terms its growth looks almost flat. As exponential growth continues, however, its share suddenly becomes large, making its absolute growth large too, until the market eventually becomes saturated and growth starts to flatten. The result is an S-shaped adoption curve.
The energy provided by solar has been growing by about 30% a year for several decades. In theory, if this rate continues for just one more decade, solar power with battery storage could supply all the world’s energy needs by about 2035. In reality, growth will probably slow down as the technology reaches the saturation phase in its S-curve. Still, based on historical growth and its likely S-curve pattern, we can predict that renewables, along with pre-existing hydropower and nuclear power, will largely displace fossil fuels by about 2050.
For decades the IEA and others have consistently overestimated the future costs of renewable energy and underestimated future rates of deployment, often by orders of magnitude. The underlying problem is a lack of awareness that technological change is not linear but exponential: A new technology is small for a long time, and then it suddenly takes over. In 2000, about 95% of American households had a landline telephone. Few would have forecast that by 2023, 75% of U.S. adults would have no landline, only a mobile phone. In just two decades, a massive, century-old industry virtually disappeared.
If all of this is true, is there any need for government support for clean energy? Many believe that we should just let the free market alone sort out which energy sources are best. But that would be a mistake.
History shows that technology transitions often need a kick-start from government. This can take the form of support for basic and high-risk research, purchases that help new technologies reach scale, investment in infrastructure and policies that create stability for private capital. Such government actions have played a critical role in virtually every technological transition, from railroads to automobiles to the internet.
In 2021-22, Congress passed the bipartisan CHIPS Act and Infrastructure Act, plus the Biden administration’s Inflation Reduction Act (IRA), all of which provided significant funding to accelerate the development of the America’s clean energy industry. Trump has pledged to end that support. The new administration has halted disbursements of $50 billion in already approved clean energy loans and put $280 billion in loan requests under review.
The legality of halting a congressionally mandated program will be challenged in court, but in any case, the IRA horse is well on its way out of the barn. About $61 billion of direct IRA funding has already been spent. IRA tax credits have already attracted $215 billion in new clean energy investment and could be worth $350 billion over the next three years.
Ending the tax credits would be politically difficult, since the top 10 states for clean energy jobs include Texas, Florida, Michigan, Ohio, North Carolina and Pennsylvania—all critical states for Republicans. Trump may find himself fighting Republican governors and members of Congress to make those cuts.
It is more likely that Trump and Congress will take actions that are politically easier, such as ending consumer subsidies for electric vehicles or refusing to issue permits for offshore wind projects. The impact of these policy changes would be mainly to harm U.S. competitiveness. By reducing support for private investment and public infrastructure, raising hurdles for permits and slapping on tariffs, the U.S. will simply drive clean-energy investment to competitors in Europe and China.
Meanwhile, Trump’s promises of a fossil fuel renaissance ring hollow. U.S. oil and gas production is already at record levels, and with softening global prices, producers and investors are increasingly cautious about committing capital to expand U.S. production.
The energy transition is a one-way ticket. As the asset base shifts to clean energy technologies, large segments of fossil fuel demand will permanently disappear. Very few consumers who buy an electric vehicle will go back to fossil-fuel cars. Once utilities build cheap renewables and storage, they won’t go back to expensive coal plants. If the S-curves of clean energy continue on their paths, the fossil fuel sector will likely shrink to a niche industry supplying petrochemicals for plastics by around 2050.
For U.S. policymakers, supporting clean energy isn’t about climate change. It is about maintaining American economic leadership. The U.S. invented most clean-energy technologies and has world-beating capabilities in them. Thanks to smart policies and a risk-taking private sector, it has led every major technological transition of the 20th century. It should lead this one too.
16 notes
·
View notes
Note
AITA for blackmailing someone and then snitching to the feds anyway? Okay, so I work for a contract medical research lab generating quantitative image data, working closely with veterinary pathologists who provide the qualitative data. Together, we put together a report like "okay, here's what the medicine/medical device did and here's why we think it happened", and that report usually gets sent to the FDA if it looks promising enough that the sponsor wants to push for clinical trials and eventual market release. So we get a study in and we've got (fake numbers here) 400 sections, but the quote says they only want 300 measurements done. I'm confused and go "wait, which 300 out of the 400? which 100 should I ignore?" and go to the pathologist. She also thinks it's weird and reaches out to the client, hoping it's a typo and we're about to get paid for the bonus 100. Nope! He pressures us for it to be a phone call (no paper trail) and then not-so-subtly hints that he wants the... uglier-looking sections dropped. In other words, he wants to cherry-pick data that makes him look good. This is not only dangerous but The Most Illegal Shit. People's lives hang in the balance and they have to be able to trust the research that tells them medicines and medical devices are safe. We take that responsibility seriously. So the pathologist gathers data and emails him like "I'm taking a REPRESENTATIVE 300 samples for analysis, my report will include scoring of the ones that make you look bad, and if I find out you doctored the reports behind my back, I'm sending everything I have directly to the FDA." (this is not how data is normally submitted in the industry. normally the report is commissioned, and then all dealings with the FDA are done by the client) He grouses, but agrees. And then says "if the FDA reaches out to you, don't respond." .....What? But that's already industry standard? Why would he say that? Why would he expect the FDA to reach out to us? Anyway the pathologist and I discuss it, and both assume he's definitely about to doctor these reports behind our back once it's submitted. So at my suggestion... the pathologist sends the communications to the FDA anyway. Here's the thing: we don't actually know that this guy meant to do some ethics violations. We just assumed he was suspicious without real proof. Even unproven accusations in this industry can get you blacklisted for life, if not facing criminal charges. Did we risk destroying some random guy's life over bad vibes and nothing else?
What are these acronyms?
113 notes
·
View notes
Text

Feyre sketch dump :)
Details/explanations!!


I think a really underrated aspect of Feyre's character is her scent. We all know Rhysand smells like citrus and the sea and the night court smells like jasmine, but Feyre is mentioned to smell like pear and lilac! I wanted to tribute that here, so the flowers on her outfit in the first piece are lilacs and the flowers in her earrings are pear blossoms. I also thought I'd imagine what her fragrance would be like if there was a celebrity-sponsored fragrance industry in Velaris like there is in the real world, and added in linseed since that's an oil that's often used in painting. (Does it actually smell nice or mix well with pear or lilac? .... We won't discuss that here.)
Anyway the other two pieces are Feyre in the cabin and Feyre in some nice tartan, in acknowledgment of her time in the Spring Court, which I would imagine is pretty Scottish given its high lord's name :')

I love this one <3 I imagine Feyre's current painting style to be like this; I think when she first starts painting she'd be more folk artsy (in the style of pieces like this), then tries out more semi-realistic styles in the Rainbow. I know a lot of people think that because of Feyre's lack of proper art education or practice she wouldn't be very good, but I *highly disagree*; there are plenty of folk artists out there, both now and throughout history who have never been educated, who are completely self taught, and who only paint when they could, in between work and survival, who are still good because they have natural talent. Just look at the difference between historical folk artists like Grandma Moses and the art of your average high school art student who may not have raw talent; while neither are properly educated, and this can be seen in their composition and coloring styles, those folk artists with raw talent still bring a specific eye to their work that your average person couldn't. Anyway rant over LOL JUSTICE FOR FEYRE'S SKILL LEVEL!!!! I BELIEVE IT'S HIGH!!
I also don't think there's even such a thing as good or bad art anyway but that's not relevant rn
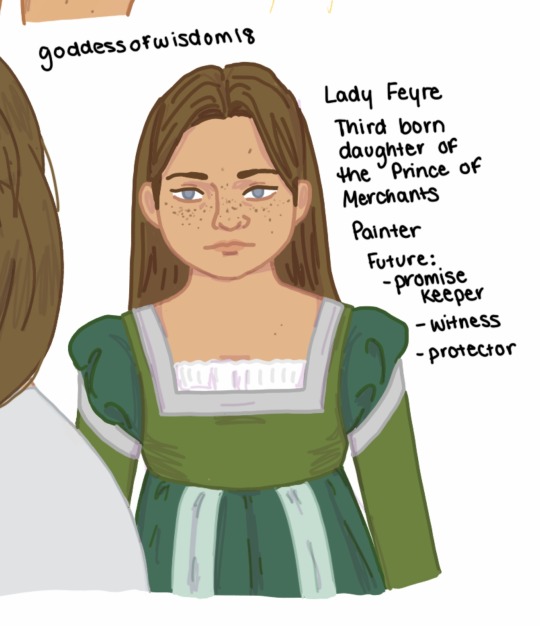
Last thing; I imagine the human realms to be 1400s esque (I might not have gotten the right dress style for that in this drawing, but bear with me because I was too lazy to do intensive research lol) and based in historical fabric use, while the faerie realms take a lot of inspiration from future eras and haute couture, things that would seem very bizarre to your average 15th century human! So here's little kid Feyre, before everything really went to shit (not that she was very happy before that either lol)
#feyre archeron#acotar#sjm#pro feyre#night court#feysand#rhysand#nyx#my art#acotar fanart#acotar art#pro inner circle
46 notes
·
View notes
Text
Video recommendation
Hello! I recommend you guys watch Mickey Atkins’ (therapist, social worker, fat activist, she/they) video called Diets & Weight Stigma are Making You Mentally Ill | Therapist Talks Fat Liberation on Youtube.
Here’s why I think you will benefit from this video:
The video helps you question the idea of weight in relation to health. It serves to show health as a multifaceted concept, which weight is only a small part of. The video acknowledges that weight shame is interconnected to other forms of discrimination such as racism and ableism.
Atkins has collected a lot of research to disprove current ideas of fatness in relation to unwellness, but also reminds us that even if fatness was unhealthy, fat people should still be treated equally. There’s also a Google Docs linked to the description of the video, where you can find studies on the topic and educate yourself further.
Topics of the video include e.g:
BMI’s creation, how it was inaccurate from the start, and what it should be used for instead.
Weight cycling and its effects on health.
A brief discussion on eating disorders in relation to e.g weight cycling.
Mentions of how capitalism benefits from weight shame.
Obesity paradox
How ”calories in, calories out” is not accurate in any way.
Discussion of the health at every size - approach.
One reoccurent theme of the video is to be critical of research and the medical community when it comes to fat bodies, because there is a lot of bias in the medical community. There is a brief talk on the video about how some research on fat bodies has been sponsored by Weight Watchers or the diet industry.
All in all, I think the video is an informative watch even if you have read a lot of books on the topic already (such as Unshrinking by Kate Manne, What We Don’t Talk About When We Talk About Fat by Aubrey Gordon, Body of Truth by Harriet Brown, etc.). There is some information that was brand new to me, and regardless, it’s always good to see other fat people fighting against fatphobia. Especially when they are mental health professionals.
Anyway, have a lovely day all!
#anti fatphobia#fat liberation#fat acceptance#fat is not a bad word#anti fat bias#fat positive#fat positivity#being fat#fat is beautiful#fatphobia#End fatphobia#body positivity#body positive#body postivity#body posititivity#body neutrality#fat pride#fat people#fat person#fat activism#fat activist#health#health and wellness#mental health#research#medical fatphobia#medicine
20 notes
·
View notes