#digital awareness
Explore tagged Tumblr posts
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
Why You Should Avoid Answering Personal Questions Online: Protecting Yourself from Digital Risks
“Name an attraction or town close to home that you still haven’t visited.” Sounds innocent enough, right? But answering questions like this online can reveal more than you realize to ill-intentioned individuals. In today’s digital world, seemingly trivial pieces of information can add up, making it easier for someone to learn personal details about you that put your privacy—and even safety—at…
#Adaptability#Confidence#Cybersecurity#dailyprompt#dailyprompt-1827#Decision-Making#Digital Awareness#Empowerment#Goal Setting#Growth Mindset#Habits#Insecurity#Inspiration#Life Skills#Mindset#Motivation#Online Privacy#Overcoming Fear#Overcoming Obstacles#Personal Growth#Positive Thinking#Practical Tips#Problem-Solving#Productivity#Protecting Personal Information#Resilience#Self-Esteem#Self-Improvement#Self-Worth#Social Media Safety
0 notes
Text

chicana miku 🤎
#you have no idea how fast I was drawing tryna finish it before the trend dies#thats why the backround is like half collage#I was not gonna try to draw a 64 impala from memory in <3 hours lol#it looks rushed because it is haha#anyways#miku#international miku#yes I'm aware chicana miku is american but at least theres a mexican cultural aspect happening#I didnt see anyone else doing this one so if peole can draw 'boston' miku I'm doing what I want#hatsune miku#digital art
11K notes
·
View notes
Text

Happy Aro Week!!! 💚🤍🩶🖤
Have this meme I made bc I REFUSE to believe that this is just me sksk—
#aromantic#aromantic spectrum#aromantism#arospec#aromantic awareness week#aromantic spectrum awareness week#arospec awareness week#aromantic meme#aro memes#💚🤍🩶🖤#art meme#lgbtqia2s+#queer artist#aromantic artist#artist on tumblr#digital art#my art
5K notes
·
View notes
Text
People forget that in the end, we are just normal people going through horrific events. I want to share the insignificant details of my life with you to show you that I'm just a regular girl.








In the end, I hope you understand that we are not strange people from a distant land. We are like you. We want to have normal lives like you. Please help us strive for normal as we wait for the war to end. We can't do this alone.
Our situation is real, we are struggling in northern Gaza. My campaign is vetted, so please don't feel hesitant about helping us.
✅️Vetted by @gazavetters, my number verified on the list is ( #347 )✅️
Forgive me, you shared before and it helped a lot so I ask you to please share again @kerosene-saint @andnowanowl @omegasmileyface @4c-aperture @bahrmp3 @dhmiss55-blog @woodesnake @original-character-chaos @revalentinee @rapogirl13 @gorillawithautism @xerxestexastoast @kyoukainokanata-kuriyamamirai @rabiesrabiesdog @rainyrebloggin @ok1237 @isummonedadragon @pro-pin-prinny @boxheadpaint @rukafais @butcklinkle @earlysunsetting @ceeberoni @strangeauthor @the��pony-box @blurrycow
#free gaza#gaza#gaza strip#all eyes on palestine#free palestine#gaza genocide#gazaunderattack#gofundme#i stand with palestine#mutual aid#original comic#comic art#web comic#original art#digital art#artwork#art#artists on tumblr#digital artist#small artist#mental health#mental heath support#mental heath awareness#relatable#slice of life#signal boost#please boost#boost#palestinian genocide#save palestine
6K notes
·
View notes
Text

the punch-in-the-face difference in vibes is so so funny to me
#jayvik#arcane#arcane fanart#lol#league of legends#defender of tomorrow#machine herald#jayce giopara#jayce talis#viktor arcane#art#illustration#digital art#fanart#artists on tumblr#clip studio paint#csp#and i am VERY aware the league versions are older and enemies and went through a bunch of stuff#i just think it's very funny that i've heard it's on sight with them and then in arcane they're soulmates#not that the league ones aren't soulmates as well it's just a lot messier i believe
6K notes
·
View notes
Text
[⚠️The Amazing Digital Circus SPOILERS] This episode was interesting!



#i REALLY like gummigoo#im just into characters who realize theyre in a fictional world and become self-aware dont mind me la la la~#anyway i like the guy and he's a very interesting character#a bit disappointed at what happened to him at the end though#but hey i'll take what i can get#this episode was unexpectedly sweet considering the chaos of the first episode#pomni realizing that she wasnt alone in this was really nice#the amazing digital circus#digital circus#amazing digital circus#the digital circus#the amazing circus#tadc#tadc pomni#tadc ragatha#tadc gangle#tadc zooble#tadc jax#tadc kinger#tadc gummigoo#my drawing museum
15K notes
·
View notes
Text

Don't fuck with the science team
#fanart#my art#myart#digital art#sketch#doodle#hlvrai#hlvrai bubby#benrey hlvrai#hlvrai benry#hlvrai benrey#hlvr benrey#hlvrai coomer#dr coomer#hlvrai tommy#tommy coolatta#dr bubby#hlvrai gordon#hlvrau gordon freeman#gordon feetman#benrey and gordon#gordon freeman#the science team#science team#hlvrai fanart#hlvrai fandom#hlvrai science team#benrey benry#half life vr benry#half life vr but the ai is self aware
5K notes
·
View notes
Text


It's Aro-Spec Awareness Week again my friends, and that means it's time for more silly little critters! (You can find last year's here.) ✨Keep up the amazing work, fellow aros✨
#aro#aro week#aromantic#aro week 2024#aromantic awareness week#art#aromantic awareness week 2024#aro spec#digital art#my art#snake#snake art#tw snakes#pigeon#bird#bird art#aromanticism#critter series#aromantic artist#aro-spec friendly#vector art#lgbtqia+#lgbtq+#decided to do two of my favourite types of animals this time round. love me a snake. i have since i was young#held a python as a kid (via a professional zookeeper) and was hooked. also doesn't hurt that i was born in the year of the snake#and pigeons are my favourite little street-wise bird guy. bopping their lil heads. making prrrr noises. love em#(may there have also been some other outside fandom-related factors that led me doing a snake and a dorky bird? perhaps)#i think these might be my favourite critters yet :3 shh don't tell the others#same deal as always: blanket permission to use as icons so long as you credit me please :)#id in alt text
14K notes
·
View notes
Text

this is a follow up to the post I made months ago about Haddock in the Syldavian guard uniform
Apparently this image is too big for Tumblr somehow, I hope posting it works
#tintin#the adventures of tintin#tintin et milou#tintin fanart#digital art#I am aware this drawing is really bad but I wanted to get the concept out
4K notes
·
View notes
Text

dick picking jason up from a random address like a divorced mother picking her child up from school
#jason sends over an address like an olive branch when he knows dick and bruce have been fighting#dick shows up and jasons like: fuck our old man amirite#dicks like: uhhuh. get in the car.#ooc but im self aware so idc#boombaux art#fanart#art#sketch#digital sketch#digital art#dc#dc comics#dcu#dick grayson#nightwing#jason todd#red hood#dc robin#batfamily#batfam
7K notes
·
View notes
Text
You’re Doing Human Wrong: The Clickbait Conundrum of Turning People into Products
Twitter Patreon GitHub LinkedIn YouTube Ah, the internet, a wondrous labyrinth where the minotaurs are clickbait titles, luring us into their dens with promises of life-altering secrets. Today’s special: “You’re Doing X Wrong.” That’s right, from slicing bread to living your life, you’re apparently doing it all wrong. But worry not, for I am here to guide you through the maze with a torch of…

View On WordPress
#Advertising Strategies#Attention Economy#Audience Manipulation#Clickbait#Cognitive Dissonance#Consumer Awareness#critical thinking#Curiosity Gaps#Digital Awareness#Digital Content#Digital Ethics#Digital Manipulation#Digital Selfhood#Emotional Triggers#human psychology#Information Overload#internet culture#media consumption#Media Literacy#Modern Media#Narrative Techniques#Online Behavior#Personal Improvement#Productification#Psychological Impact#Reader Exploitation#Self-Esteem Issues#Self-Perception#Sensationalism#Social Media Trends
0 notes
Text

i <3 chef characters
#'koob youve drawn a few crossovers atp and they all involve one piece' yes im aware . and ill do it again#dungeon meshi#delicious in dungeon#one piece#sanji#black leg sanji#senshi#senshi of izganda#crossover#koob art#procreate#digital art#1k#2k
4K notes
·
View notes
Text

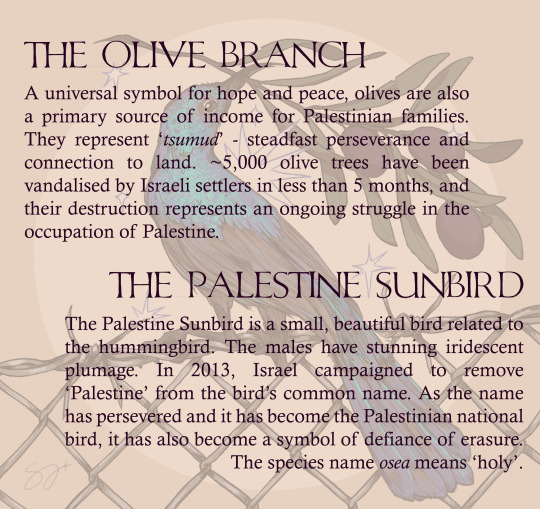
#palestine#free palestine#free gaza#palestine sunbird#sunbird#olive branch#palestinian sunbird#art for palestine#palestine art#art#digital art#artists on tumblr#digital drawing#drawing#digital artist#protest#palestine protest#human rights#awareness
13K notes
·
View notes
Text

Man this is so stupid LMAOO BUT LIKE- i had a vision ok.. gay hedgehogs as... GAY WITCHES! WOOO! ...anyone?
#im aware im a little delusional but thats okay#they look silly but i find them cute ngl#shadow the hedgehog#sonic the hedgehog#sonadow#digital art#sth fanart#wicked
2K notes
·
View notes