#data privacy certification
Explore tagged Tumblr posts
Text
Achieving CIPM Certification: A Complete Guide to Elevate Your Professional Expertise
What is CIPM Certification? The Certified Information Privacy Manager (CIPM) certification is a key credential for professionals looking to demonstrate their expertise in managing privacy programs. Offered by the International Association for Privacy Professionals (IAPP), CIPM is designed for individuals who oversee and manage privacy within organizations. This certification is crucial for those who wish to advance their careers in the field of privacy management and data protection.
Why Pursue CIPM Certification? CIPM certification offers numerous advantages for privacy professionals, including:
Enhanced Career Opportunities
- Professional Growth: Earning the CIPM credential opens doors to advanced roles in privacy management, such as Privacy Manager, Data Protection Officer, or Privacy Consultant. - Increased Earning Potential: Certified professionals often enjoy higher salaries and better job prospects compared to their non-certified peers.
Comprehensive Knowledge:
- Expertise in Privacy Management: The certification validates your ability to manage privacy programs, ensuring compliance with global privacy laws and regulations. - Practical Skills: CIPM training provides hands-on experience in implementing privacy policies, conducting privacy assessments, and managing data protection strategies.
Global Recognition Industry Standard: CIPM is widely recognized as a leading credential in privacy management, enhancing your professional credibility and reputation in the global job market.
CIPM Certification Requirements
To qualify for CIPM certification, candidates must meet specific criteria:
Experience and Knowledge
- Relevant Experience: While there are no strict experience requirements, having practical experience in privacy management is beneficial. This could include roles in data protection, compliance, or information security. - Understanding of Privacy Practices: Familiarity with privacy laws, regulations, and management practices is essential for success in the certification exam.
Training and Preparation:
- CIPM Training Course: Enroll in a comprehensive CIPM training program to prepare for the certification exam. Zoctech offers a detailed course that covers all aspects of privacy management and compliance. - Study Resources: Utilize study materials, practice exams, and other resources to ensure thorough preparation for the CIPM exam.
Pass the CIPM Exam:
- Exam Details: The CIPM exam assesses your knowledge of privacy management practices, including privacy program governance, data protection, and privacy compliance. - Exam Format: The test consists of multiple-choice questions designed to evaluate your understanding of privacy principles and management practices.
How to Get CIPM Certified with Zoctech
Explore Our Training Options:
Visit Zoctech’s CIPM Training and Certification Course to learn more about our comprehensive training programs and resources.
Prepare for the Exam: Enroll in our expert-led CIPM training course to gain in-depth knowledge and practical skills in privacy management. Benefit from detailed study guides, practice exams, and interactive sessions.
Register and Achieve Certification:
Complete the registration process for our training program, study diligently, and take the CIPM exam to earn your certification and advance your career in privacy management.
Conclusion: CIPM Certification is a valuable credential for professionals aiming to excel in privacy management. By meeting the certification requirements and enrolling in Zoctech’s comprehensive training program, you can enhance your expertise, open new career opportunities, and gain global recognition in the field of privacy.
#cipm certification#cipm courses#certified information privacy manager#cipm#iapp certification#certification#privacy certification#cipm exam#cipp certification#pdpa certification#iapp cipm certification#cipm certification mock test#cpp certification iipmr#it certifications#data privacy certification#procurement certifications#cipt certification#cipm certificate#cipp/e certification#it certification#cipm practice exam#certification journey#iapp certifications#tech certifications
0 notes
Text
Secure communication between users and websites becomes possible with SSL certificates. They safeguard private information like credit card numbers and passwords from hackers by encrypting data sent online. You may feel secure knowing your personal information is protected when surfing or purchasing online. Additionally, SSL certificates enhance confidence by establishing a secure connection, assuring users that their interactions are safe.
0 notes
Text
Two-thirds of organizations are not prepared for AI risks - CyberTalk
New Post has been published on https://thedigitalinsider.com/two-thirds-of-organizations-are-not-prepared-for-ai-risks-cybertalk/
Two-thirds of organizations are not prepared for AI risks - CyberTalk


EXECUTIVE SUMMARY:
Artificial intelligence is the new epicenter of value creation. Employees across industries are ecstatic about deploying easily accessible generative AI tools to elevate the quality of their output and to improve efficiency.
According to the latest research, 60% of employees use generative AI tools to augment their efforts. Roughly 42% of organizations say that they permit use of generative AI in the workplace, although only 15% retain formal policies governing the everyday use of AI.
And among organizations that permit the application of generative AI to everyday tasks, research indicates that only a third keep an eye on the ethical, cyber security and data privacy risks inherent in the technology.
Explaining the lack of suitable AI policies
The gap between AI use and AI governance can be attributed to the fact that senior organizational leaders aren’t particularly comfortable with AI technologies – and nor are the department heads and team leads around them.
In addition, AI is a fast moving field. The policies that made sense three months ago may no longer be relevant now or may not be relevant three months into the future. Most organizations lack tiger teams that can spend all day iterating on policies, although developing AI governance teams may quickly become a competitive advantage.
For organizations with existing AI policies, employee enthusiasm surrounding the benefits of AI may supersede their interest in adhering to top-down policies, especially if there are no incentives for doing so or consequences for flouting the rules.
Addressing AI risks (in general)
As noted previously, some organizations are struggling with top-down AI policy implementations. To overcome this challenge, experts suggest that organizations build AI policies, specifically those concerning ChatGPT and similar tools, from the ‘ground-up’. In other words, leaders may wish to solicit ideas and feedback from all employees across the organization.
Organizations may also want to leverage repudiated, industry-backed frameworks and resources for the development of responsible and effective AI governance policies. Resources to review include NIST’s AI Risk Management Framework and ISACA’s new online courses.
Addressing AI risks (in cyber security)
In relation to cyber security, the AI risks are numerous and varied. There are risks stemming from employee data inputs to AI models, risks concerning ‘data poisoning’, risks related to evolving threats, risks related to bias due to the opacity of models, and more.
For incisive and influential resources designed to help cyber security leaders mitigate risks pertaining to AI, check out the following:
Despite the aforementioned resources, leaders may still feel under-prepared to make policy decisions surrounding cyber security, data security and AI. If this sounds like you, consider AI governance and training certificate programs.
The Global Skill Development Council (GSDC) offers a Generative AI in Risk and Compliance certification that covers how AI can be used in cyber security and that steers leaders towards ethical considerations.
The International Association of Privacy Professionals (IAPP) offers AI governance training that focuses on deploying trustworthy AI systems that comply with emerging laws and current laws. It also covers other AI and security-related risk management topics.
The SANS Institute offers an AI Security Essentials for Business Leaders course that addresses balancing AI-related productivity gains with risk management.
Building a secure future together
Check Point understands the transformative potential of AI, but also recognizes that, for many organizations, security concerns abound. Rapid AI adoption, fueled by employee enthusiasm, can leave security teams scrambling to keep up.
This is where Check Point’s Infinity Platform comes in. The Check Point Infinity Platform is specifically designed to address the unique security challenges presented by the “AI revolution.” It empowers organizations to thrive amidst uncertainty and tough-to-keep-up with regulations.
Prioritize your cyber security. Discover a comprehensive and proactive approach to safeguarding systems that use AI with a system that is powered by AI. Learn more here.
To receive compelling cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#ai#AI adoption#AI models#ai security#AI systems#ai tools#analyses#approach#artificial#Artificial Intelligence#Bias#Building#Business#certification#challenge#chatGPT#Check Point#Check Point Infinity Platform#compliance#comprehensive#course#courses#cyber#cyber security#cybersecurity#data#data poisoning#data privacy#data security#development
0 notes
Text
Understanding The Basics of SSL
As we browse websites, share important details, and buy things online, it's extremely important to keep our information safe. That's where SSL, or Secure Sockets Layer, comes in. It's like the main tool we use to make sure our online chats and transactions stay private and secure.
Understanding the basics of SSL is essential not only for website administrators and cybersecurity professionals but also for anyone who values privacy and security online. In this article, we delve into the meaning of SSL, unraveling its significance, components, and implications in safeguarding our digital interactions. By demystifying SSL, we empower individuals and organizations to navigate the online landscape confidently and securely.
What is SSL?
SSL, or Secure Sockets Layer, is a cryptographic protocol designed to secure the communication between a user's web browser and a server. It establishes a secure and encrypted connection, safeguarding sensitive data such as login credentials, personal information, and financial transactions from unauthorized access and potential cyber threats.
It operates by facilitating a secure handshake between the client and server, utilizing digital certificates issued by Certificate Authorities to verify the authenticity of the communicating parties. Its implementation is crucial for building user trust, protecting against data breaches, and ensuring the overall security of online interactions.
The Importance of SSL
The primary purpose of SSL is to encrypt the communication between a user's web browser and the server, protecting sensitive information from unauthorized access. It plays a pivotal role in various aspects of online security. Here’s how:
1) Data Encryption:
SSL encrypts data during transmission, ensuring that even if intercepted, the information remains indecipherable to malicious actors. This is particularly crucial when handling sensitive data such as login credentials, financial transactions, and personal information.
2) User Trust and Confidence:
The presence of SSL is visually indicated by the padlock icon and "https://" in the browser's address bar. This visual cue reassures users that their connection is secure, fostering trust in the website. In contrast, websites without SSL may be flagged as insecure, potentially deterring users from interacting with them.
3) Protection Against Man-in-the-Middle Attacks:
SSL thwarts Man-in-the-Middle (MitM) attacks, where attackers attempt to intercept and alter communication between two parties. The encryption provided by SSL ensures that even if intercepted, the data remains confidential and unaltered.
4) SEO Ranking:
Search engines prioritize secure websites, and SSL is a factor in search engine ranking algorithms. Implementing SSL not only protects users but also positively impacts a website's visibility in search results.
“In the realm of digital education, platforms like Study24hr.com play a pivotal role in enhancing our understanding of crucial technologies. The site emerges as a valuable resource, offering a myriad of courses that empower individuals to navigate the world of new trends with confidence. Whether you're a beginner seeking foundational knowledge or an experienced professional aiming to refine your skills, bolster your expertise with Study24hr.com. Explore their diverse offerings to further enrich your understanding and proficiency in online marketing trends.”
Components of SSL
Here are several key elements that work together to establish and maintain a secure connection between users and servers, protecting sensitive information from interception and unauthorized access.
1) SSL Handshake:
The SSL handshake is the initial phase of establishing a secure connection. During this process, the client and server agree on the encryption algorithms and exchange cryptographic keys.
2) SSL Certificates:
It relies on digital certificates issued by Certificate Authorities (CAs). These certificates validate the authenticity of the website, ensuring users connect to the intended server and not an imposter.
3) Ciphers and Encryption Algorithms:
It employs various encryption algorithms and ciphers to secure data transmission. These include symmetric and asymmetric encryption methods, providing a robust defense against eavesdropping and tampering.
Consequences of Neglecting SSL
The absence of SSL safeguards exposes sensitive information to unauthorized access, posing threats to both user privacy and the reputation of an organization. The subsequent points outline the repercussions of disregarding SSL.
1) Data Vulnerability:
Without SSL, data transmitted between the user and the server is susceptible to interception. This puts sensitive information, such as login credentials and financial details, at risk of being exploited by malicious actors.
2) Loss of User Trust:
Users are increasingly security-conscious. A lack of SSL not only jeopardizes user data but also erodes trust. Visitors are likely to abandon websites perceived as insecure, leading to the loss of potential customers and damage to the site's reputation.
3) Regulatory Non-Compliance:
Many regulatory standards, such as the Payment Card Industry Data Security Standard (PCI DSS), mandate the use of SSL/TLS for securing sensitive information. Neglecting SSL could result in non-compliance, exposing organizations to legal consequences and financial penalties.
The Epilogue
In conclusion, SSL is the cornerstone of online security, providing a secure conduit for the exchange of information. Its implementation is not just a technical necessity but a fundamental element in building and maintaining user trust. As we navigate the digital landscape, ensuring the widespread adoption of SSL is crucial for a safer and more secure online experience.
#ssl#ssl certificate#business#website#website security#online privacy#online security#data#trust#customers#safety
0 notes
Text
Cybersecurity: The Key to Protecting Your Digital Identity and Privacy
In an era where our lives are increasingly connected with the digital sphere, protecting our digital identity and privacy has become critical. With the exponential growth of online activities, from social media interactions to financial transactions, the risks of cyber attacks are greater than ever before. In this digital age, cybersecurity has emerged as the primary shield protecting our digital life.
Understanding The Threat Landscape
Cyber risks take many forms, including data breaches, identity theft, malware, and phishing attempts. These dangers jeopardize sensitive personal information while also undermining trust in online systems and services. As technology advances, so do fraudsters' strategies, making it critical for individuals to be cautious and knowledgeable about cybersecurity best practices.
Significance of Digital Identity Protection
Our digital identities contain a variety of data, including personal information, financial records, and online behaviors. Securing this information is critical not only to prevent identity theft, but also to maintain our reputation and reliability in the digital sphere. A compromise of our digital identity can have serious ramifications for our financial stability, professional chances, and even our personal relationships.
Preserving Privacy in the Digital Age
Privacy is the foundation of individual freedom and liberty. However, in today's hyper-connected society, keeping privacy has grown more difficult. From surveillance technologies to data mining tactics, our online activities leave digital trails that dangerous actors can exploit. Cybersecurity measures are critical in protecting our privacy rights by ensuring that our personal information stays safe and protected from unauthorized access.
Empowering Individuals with Cybersecurity Education
While cybersecurity dangers may appear frightening, individuals may empower themselves by learning and developing cybersecurity skills. Education is an excellent technique for combating cyber threats because it teaches people how to detect possible risks, minimize vulnerabilities, and respond effectively to security crises. Individuals who invest in cybersecurity education improve not only their own digital safety but also the broader resilience of cyberspace.
Conclusion
In an increasingly linked world, cybersecurity is the foundation of our digital security and privacy. Individuals who recognise the importance of preserving their digital identity and privacy can take proactive efforts to reduce cyber risks and protect themselves from online dangers. We can create a safer and more secure digital future for ourselves and future generations by promoting cybersecurity education, awareness, and adherence to best practices.
Remember that in the digital world, cybersecurity is no longer an option—it is a requirement. Let's work together to protect our digital identities and privacy rights in an ever-changing online world.
Ready to take charge of your digital security? Join CACMS Institute today for comprehensive cybersecurity training that will provide you with hands-on practical skills and professional assistance.
Enroll in our Cyber Security Course in Amritsar and obtain the knowledge and competence required to properly protect your digital identity and privacy. Our professional teaching staff ensures that you receive a high-quality education and personalized attention throughout your learning journey.
Protect yourself online before it's too late. Contact us at +91 8288040281 or visit cacms.in to learn more about our Cyber Security Course in Amritsar and begin your path to a secure digital future now.
#cacms institute#cacms#techskills#techeducation#cyber security course in amritsar#cyber security#data privacy#digital identity#protecting digital Identity#ethical hacking course#ethical hacking training#ethical hacking certification#best computer institute in amritsar
0 notes
Text
Kovai.co Achieves Global SOC2 Type 2 Compliance Certification @kovaico #SOC2 #news #B2B #SaaS
Kovai.co has demonstrated its commitment to secure client data and software security by obtaining the Global SOC2 Type 2 compliance certification. With this certification, the company aims to achieve the highest compliance standards and reduce its risk profile globally. The certification is issued by the AICPA and audited by VISTA InfoSec, an internationally acclaimed cybersecurity consulting and…

View On WordPress
#Audit#B2B SaaS#Business#Certification#Compliance#Cybersecurity#Data protection#Enterprise Software#Kovai.co#Privacy#Security#SOC2#SOC2 certification#Technology#Trust Service Criteria
0 notes
Text
So, Things Are Terrible and You Want to DO SOMETHING
The election is over and, ah...did not go well. While a lot of folks are doing a post mortem of the campaigns and trying to understand what happened with the vote and fighting over who shoulders the blame, we've gotta turn an eye toward the future and figure out, okay fam, where the fuck do we go from here.
I don't have all the answers on this, and I'm not an authority by any means, I'm just a horror author with a blog. But I've been thinking a lot about it and I wanted to share my thought process with others who might want to DO SOMETHING but feel they're spinning their wheels.
Buckle in. This will be a long one.
Step One: Understand the actual risks and stakes.
I think it is very easy to start panicking now about the worst possible case scenario -- jackbooted military busting into the door to disappear everyone who ever said something mean about Trump or bought a banned book or something -- and let fear turn into inaction.
I'm not saying things can't get that bad, and I'm not saying that it won't be absolutely terrifying right out the gate for some particularly at-risk groups -- but the distance between "now" and "V for Vendetta" is long and filled with a lot of intermediary steps. There will be so many opportunities to prevent the worst case scenario.
I say this because, if your mental image of "Bad Things Happening" is The Purge, it will be easy to wake up on inauguration day, look outside to see that the world is not on fire, think, hey, maybe things will be okay after all, and then completely disengage. Alternatively, you might feel so frozen with terror at the possibility of persecution that you do nothing. This is why people are saying: don't obey in advance.

It is essential for those of us with more privilege to use it to take care of those who are more vulnerable.
So. Who is most vulnerable? What does that vulnerability actually mean? What are the most likely risks of Trump's presidency? Here's a Guardian article that I think does a good job of summarizing some of the main issues. Go read that, then come back here.
Step Two: Take steps to protect yourself
You've gotta put your oxygen mask on first, right? So before you start getting involved in other causes, figure out what risks YOU are at, immediately, and do as much as you can to secure yourself. Some potential action steps depending on your circumstance may include:
Renewing your passport (helpful for leaving the country, but also for gender/name change purposes)
Getting vaccines / boosters
Securing birth control
Ensuring your necessary papers (birth certificates etc.) are where you have access to them.
Drawing up legal paperwork for spouses/partners (always a good idea, a helpful safety measure in case you lose marriage rights)
Bolstering your data privacy and online security. Here's a step-by-step guide I found that could help with that.
The specific steps you need to take here depend on what risks you, personally, face. You'll want to do some more research into this for your particular scenario.
No matter who you are, though, it's probably a good idea to start saving money and being a little more conservative with your spending and/or pay down debts to free up some cash. You don't know what kind of emergency may befall you, and having spare money for an emergency is never a bad idea.
There is a possibility that the cost of many things you rely on might go up, if Trump goes through with his tariffs plan. You will want to plan for that.
Food costs may also rise due to tariffs (we import a lot of food from Mexico and Latin America for example) as well as a loss of immigrant labor. There is also a possibility that food safety standards could fall due to overturning regulations. Now would be a good time to look into local food resources like farm share/CSA, community farms, etc., and to stock up on a few key staples like rice and beans.
Okay. Now that YOU are reasonably safe...what can you do to protect your community?
Step Three: Get Involved
Here is your mission: You need to stay engaged enough to know what's going on, without burning yourself out or exhausting yourself, and to take actual decisive actions instead of wasting your energy arguing on the internet.
Got that? Okay. Good. Here are some action steps:
Support independent journalism. Subscribe to local papers, donate to and watch public broadcast programming. I signed up for news from ProPublica, for example, as well as the news-roundup service What The Fuck Just Happened Today. The goal is to stay informed without falling down an endless rabbit hole of upsetting information.
Share news and resources with others in your circle. This can be a good use of social media. It's what I am doing right now!
If it is safe for you to do so, challenge and educate your friends/family members/neighbors/coworkers. Only if it is safe for you to do so. Do not put yourself at risk doing this. And do not waste your time arguing with people who are unlikely to change. But if you have well-meaning people in your life who you think could be won over, look for opportunities to do this - the right way. I've had some success with this, I will probably write a guide about it in the future. In the meantime, here's a good article that can help.
Join local grassroots activism groups. You'll have to do some work to decide what groups to join and which causes you want to support, because you cannot do everything. But there are tons of organizations taking direct action in all kinds of causes. Search "grassroots [cause] activists in [where you live]" to start finding things. Once you get involved in one group, you might meet people who can introduce you to other groups and causes. Yes, this means you will have to go outside and meet people. I'm sorry.
Join direct action groups. Same concept as above. You'll have to search in your area but once you know people it'll be easier to find more opportunities. Some of these groups may overlap. You might find direct action opportunities by engaging politically and vice versa. GO OUTSIDE AND TALK TO PEOPLE WHO ARE DOING THINGS TO HELP.
Get involved in local politics. Here are some quick tips. A lot of things are affected at the city level - stuff like book bans and bathroom bills are often battled first at local libraries and schools, and you can be part of those conversations! Sheriffs are elected and can have a big influence on local policing. Local elections affect how tax dollars are spent, how homeless populations are treated, and lots more. Don't snooze on local elections. Get involved and stay involved.
Look up your representatives. Get in the habit of calling, emailing, and writing letters. Figure out what legislature is being passed and then call your reps and harangue them about it - both to support bills you approve of and shoot down ones you don't. Sign petitions. Join email campaigns. Here's one you can go sign right now from the ACLU. See? Not that scary.
I think a lot of people figure that getting involved in politics doesn't matter or that it's all small potatoes but...man. The president is not god, no matter what he thinks. The sitting administration is not the sole power in the universe. There is an entire machine of government we can lean upon and act upon.
Finally, some general safety notes:
Some forms of direct action are not legal. Take steps to be safe if you choose to partake. Follow the lead of more seasoned activists for what forms of communication to use and so forth.
If you're not willing or able to put yourself at legal risk to act, you can help others by donating to bail funds and legal defense funds.
We've already seen this in some areas, and it will only get uglier - some bad actors are feeling emboldened by the change in regime and will misbehave. It's a good idea to learn some self-defense skills, in whatever way is comfortable to you, and brush up on some tenets of victimology that can help you stay safe. I'll write more about that in the future.
All right. That's all for now. It's by no means comprehensive...but should hopefully help you get started taking the next step. Stay safe out there.
#uspol#politics#direct action#grassroots activism#get involved#election 2024#us politics#us elections
260 notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image: Mike (modified) https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
575 notes
·
View notes
Text
Jessica Valenti at Abortion, Every Day:
Indiana Attorney General Todd Rokita says that abortion reports aren’t medical records, and that they should be available to the public in the same way that death certificates are. While Rokita pushes for public reports, New Hampshire lawmakers are fighting over a Republican bill to collect and publish abortion data, and U.S. Sen. Tommy Tuberville has introduced a bill that would require the Department of Veterans Affairs to collect and provide data on the abortions performed at its facilities. Just last week, Kansas Gov. Laura Kelly vetoed legislation that would have required abortion providers to ask patients invasive and detailed questions about why they were getting abortions, and provide those answers in a report to the state. All of these moves are part of a broader strategy that weaponizes abortion data to stigmatize patients and to prosecute providers. And while most states have some kind of abortion reporting law, legislators are increasingly trying to expand the scope of the data, and use it to dismantle women’s privacy.
Rokita’s ‘advisory opinion’, for example, argues that abortion data collected by the state isn’t private medical information and that in order to prosecute abortion providers, he needs detailed reports to be public. In the past, the state has issued reports on each individual abortion. But as a result of Indiana’s ban, there are only a handful of abortions being performed in the state. As such, the Department of Health decided to release aggregate reports to protect patient confidentiality, noting that individual reports could be “reverse engineered to identify patients—especially in smaller communities.” Rokita—best known for his harassment campaign against Dr. Caitlin Bernard, the abortion provider who treated a 10-year-old rape victim—is furious over the change. He says the only way he can arrest and prosecute people is if he gets tips from third parties, presumably anti-abortion groups that scour the abortion reports for alleged wrongdoing. He wants the state to either restore public individual reports, or to allow his office to go after abortion providers without a complaint by a third party. (Meaning, he could pursue investigations against doctors and hospitals without cause.)
Most troubling, though, is his insistence that women’s private abortion information isn’t private at all. Even though individual reports could be used to identify patients, Rokita claims that the terminated pregnancy reports [TPRs] aren’t medical records, and that they “do not belong to the patient.” [...] As I flagged last month, abortion reporting is becoming more and more important to anti-choice lawmakers and groups. Project 2025 includes an entire section on abortion reporting, for example, and major anti-abortion organizations like the Charlotte Lozier Institute and Americans United for Life want to mandate more detailed reports.
[...] As is the case with funding for crisis pregnancy centers and legislation about ‘prenatal counseling’ or ‘perinatal hospice care’, Republicans are advancing abortion reporting mandates under the guise of protecting women. And in a moment when voters are furious over abortion bans, anti-choice lawmakers and organizations very much need Americans to believe that lie. We have to make clear that state GOPs aren’t just banning abortion, but enacting any and every punitive policy that they can—especially those that strip us of our medical privacy. After all, it was less than a year ago that 19 Republican Attorneys General wanted the ability to investigate the out-of-state medical records of abortion patients. Did we really think they were going to stop there?
@jessicavalenti writes a solid column in her Abortion, Every Day blog that the GOP's agenda to erode patient privacy of those seeking abortions is a dangerous one.
#Abortion#Healthcare#Anti Abortion Extremism#Privacy#Patient Privacy#Todd Rokita#Charlotte Lozier Institute#Project 2025#Americans United For Life#Dr. Caitlin Bernard#Abortion Bans#Tommy Tuberville
118 notes
·
View notes
Text
Lenovo Duet Chromebook Powered By MediaTek Kompanio 838

Lenovo Duet Chromebook (11”, 9) and Chromebook Duet EDU G2, powered by MediaTek Kompanio 838, are transforming mobile productivity. These new Chromebooks with stunning 2K displays in 10.95-inch form factors strike the perfect combination between performance, design, and durability. Lenovo Chromebooks are for professionals, educators, and students.
The thinnest laptop available, the Lenovo Duet Chromebook (11”, 9) weighs less than 1.2 lbs and measures only 0.3 inches. It’s ideal for creative and enjoyment, with a stylish metal chassis, Corning Gorilla Glass, and a soft protective folio. The user experience is improved with twin USB-C ports, 4K display connection, clear music from two speakers with SmartAMP and Wave music, and an 8MP rear camera that takes use of MediaTek’s cutting-edge image processing technology. Note-taking, streaming, and sketching with the Lenovo USI Pen 2 are easy with the MediaTek Kompanio 838 processor’s strong CPU, graphics, and AI-enabled Neural Processing Unit (NPU).
With its durable TPU shell, detachable keyboard, and spill-resistant design, the Lenovo Chromebook Duet EDU G2 is made to handle the rigors of the classroom and is aimed towards educators and students alike. Additionally, it supports Chrome Education Upgrade, which helps IT organizations manage devices more easily.
AI-enhanced cameras, 2K 400-nit displays for outdoor reading, and 12-hour batteries are on both smartphones. The Chromebooks for business, education, and pleasure boost creativity and productivity anywhere.
Lenovo Chromebook Duet
Elegant Style with Adaptable Features
The elegant and effective Lenovo Duet Chromebook 11′′ is housed in a complete metal chassis with Corning glass. Ideal for work, pleasure, or everything in between, the soft polyurethane folio cover and clever kickstand design enable simple transitions between laptop and portrait modes.
Increase Output with MediaTek
With the powerful MediaTek Kompanio 838 processor, NPU, and enough RAM, you can do more and wait less. In less than ten seconds, you can get started with Fast Boot, and on-device AI processing increases productivity by producing interactive multimedia experiences with unmatched effectiveness.
Innovative Instruments & Engaging Entertainment
Narrow bezels on the 10.95-inch 2K display maximize screen real estate whether you binge-watch YouTube or use SmartAMP with Waves Audio to play music with crystal-clear clarity. With the Lenovo USI Pen 2, which writes and doodles like a real pen, you can quickly and simply record, arrange, and communicate ideas on Good notes.
Maximum Durability & Portability
With a weight of just.51 kg/1.12 lbs and a thinness of just 7.6 mm/1.30 in, the Lenovo Duet Chromebook 11′′ is meant to be used when traveling. It can withstand life’s adventures thanks to its spill-resistant chassis and military-grade MIL-810H certification. Also, with an all-day battery life and a brilliant 400 nits display, you can read all day both indoors and outside.
Superior Webcams for All Occasions
With the 5MP front camera, which has a physical shutter for privacy, and the 8MP back camera, which produces vivid photos, you can stay connected and record every moment. Superior low-light performance and true-to-life colors are guaranteed by MediaTek’s sophisticated image processing.
Two USB-C Ports for Optimal Communication
Enjoy endless functionality with two USB-C connections that provide data transmission, quick charging, and video output. With a superior on-device AI solution, you can effortlessly connect to an external 4K monitor and remain productive with a headphone/mic connector that will keep you talking and interested all day.
Read more on govindhtech.com
#LenovoDuetChromebook#MediaTek#Kompanio838#MediaTekKompanio838#Chromebooks#KompanioMediaTek#Lenovo#4Kmonitor#USBCPort#LPDDR4X#AdaptableFeatures#ChromebookDuet#technology#technews#news#govindhtech
7 notes
·
View notes
Text
RECENT ECOMMERCE NEWS (INCLUDING ETSY), AUGUST 2024
Hello, and welcome to my very last Ecommerce News update here on Tumblr.
After today, these reports will now be found at least twice a week on my Patreon, available to all paid members. See more about this change here on my website blog: https://www.cindylouwho2.com/blog/2024/8/12/a-new-way-to-get-ecommerce-news-and-help-welcome-to-my-patreon-page
Don't worry! I will still be posting some short pieces here on Tumblr (as well as some free pieces on my Patreon, plus longer posts on my website blog). However, the news updates and some other posts will be moving to Patreon permanently.
Please follow me there! https://www.patreon.com/CindyLouWho2
TOP NEWS & ARTICLES
Etsy has banned gift certificates/cards sold by individual shops, as of Sept 15. Only Etsy Gift Cards are now allowed. The second quarter report press release says they plan on selling Etsy Gift Cards through third parties, but no official word on how and when yet.
Many Amazon Handmade sellers were unable to list new items after a site update on July 31 [post by me on LinkedIn]. While Amazon told sellers to apply for an exemption from the Product ID requirement, some report that is not working, or that they do not have the option to apply for one.
Reminder that Canadian Etsy shops will be charged a 1.15% Regulatory Operating fee on the item price and shipping cost as of August 15. [I’ve set a bunch of things to expire. If Etsy isn’t profitable enough to pay its taxes, maybe they should consider cutting executive pay instead of squeezing microbusinesses even more.]
ETSY NEWS
Etsy has updated its Privacy Policy, to take effect August 31. Changes include mention of biometric data. Note that some parts of the policy are screenshots, and therefore not easily searchable nor accessible to screen readers - I am not sure how they can get away with that. I used the Wayback Machine to do a comparison of the parts that software can actually read. There’s also a new US regional privacy policy, which currently covers laws in several states.
Etsy is promoting a Labour Day sale August 21-September 2, and has already set up the "Cyber Savings Sale" (November 18-December 3) for Cyber Week. You can schedule the official sales through links in the announcement.
Forbes covered Etsy’s sex toy ban [soft paywall; not safe for work photos]. To no one's surprise, plenty of the banned items are still found on site, including toys and vintage Playboy magazines.
Etsy is accused of allowing shops based in “illegal Israeli settlements in the occupied Palestinian territory” and profiting off of them. Etsy’s response: "[W]e have shared this information internally with the appropriate teams for review."
Etsy's promised program for buyers - Etsy Insider - will be rolling out as invite-only beta in September. It's a paid membership for US buyers and includes:
Free US domestic shipping on millions of items
A birthday bonus
Limited edition annual gift, designed by an Etsy seller
First access to special discounts and select merchandise
While some of the "special discounts" are paid by sellers, that is a voluntary program shops can sign up for here. That form also allows you to sign up to offer new items to Etsy Insiders first - “drops” - which does not involve offering discounts. Etsy has done these sorts of "offers" in the past, and I believe they have already reached out to sellers for the first round of offers in September (based on some emails I have received from shop owners).
You can now sign up for “Etsy Up”, the virtual sellers conference scheduled for September 10. However, despite saying they have announced “our agenda”, all that is provided is a vague set of topics (other than the fact they will be announcing the Etsy Design Awards Finalists). It makes me wonder if there are official Etsy announcements coming soon that they don’t want to reveal too early by posting the real agenda. If yes, around August 15 is a good bet, given that Etsy’s Search Analytics will end that day, and many new policies kick in on September 15, just one month later.
The Etsy app is showing rectangular listing images in search for some visitors, but it appears to be a test [Reddit thread with screenshot]. I wouldn’t change anything at this time.
No, Etsy has not replaced your listing tags. I covered that topic here on LinkedIn.
I wrote about the new Listing Image Requirement policy and the email Etsy sent to some sellers on Monday July 29. [post by me on Patreon] And not everyone is being fooled by Etsy’s new Creativity Standards, but some acknowledge it will be difficult for Etsy to turn away factory-made goods at this point. [Disclosure: I am quoted in that article]
ECOMMERCE NEWS (minus social media)
Amazon
Amazon’s second quarter revenue was below expectations, and the company predicts nothing better in the third quarter.
In a surprising change, Amazon has decided to cancel overage fees for Fulfillment by Amazon (FBA) inventory storage, retroactive to July 1.
Canadian Amazon sellers will be subject to a new digital services fee as of October 1. This is due to Canada’s new digital services tax.
In a case that may have an impact on other larger ecommerce sites, a court ruled that Amazon is responsible for recalls of products sold through Amazon, including through “Fulfilled By Amazon”.
US Amazon shoppers can now link their Pinterest and TikTok accounts to Amazon to be able to buy directly from Amazon ads on social media. This is already available on Facebook, Instagram and Snap.
Amazon is changing its refund policy for Fulfillment by Amazon (FBA) users: if sellers do not receive an automatic reimbursement for loss, damage and returns, they will now only have 60 days to apply for one. A lot of ecommerce experts think Amazon is making a mistake in setting up a China to US section on the site.
eBay
eBay second quarter revenue and profit was higher than expected, but the third quarter projections are low.
The eBay app has taken a lot of flack for inserting ads between each item in a purchase history.
Poshmark
As marketplaces popular for pre-owned items compete for the best new stock, Poshmark is offering “rewards” for listing at least 1 item a week.
Shopify
Shopify had a better-than-expected second quarter, and expects a decent third quarter as well. Getting larger businesses to use Shopify has helped the tech company, but I still wonder how that affects the small and micro businesses who used to be the target market.
Walmart
The Walmart Marketplace has added Chile as its fourth country, after the US, Canada and Mexico.
All Other Marketplaces
Hundreds of business owners who sell on Temu held a protest at the marketplace headquarters on July 29. Fines for returns are one cited issue.
Payment Processing
Credit cards issued by Chase in the US will no longer allow third-party buy-now-pay-later purchases, as of October 10. Conveniently, they offer their own option, Chase Pay Over Time. PayPal has expanded the quicker checkout solution Fastlane to all US businesses, which fills in customer information without a log in.
15 notes
·
View notes
Text
youtube
#dataprivacy#data#europe#privacy#gdpr#dataprotection#certification#cippe#introduction#learntorise#infosectrain#Youtube
0 notes
Text
So much for not talking politics. In fairness, this Tik Tok Ban story found me more than the other way around (through the family group chat), and it's legitimately interesting in several ways.
Most Americans probably know already, but if you missed it,
a) Tik Tok is owned by a Chinese company, and there's really no protections for how they share your data with the Chinese government.
b) So the US Congress passed a law that ByteDance (Tik Tok's owners) have to sell to a US-owned company because national security, or else, by 1/19.
c) "Or else" meaning TikTok couldn't be listed in US app stores. The app itself could still function if you already had it downloaded.
d) Mr. Trump was originally for the ban but suddenly became against it, even going to the SCOTUS to get an extension so he could arrange a sale once president. They refused. Because, you know, it was an agreed-upon and properly executed law with no constitutional implications.
e) Tik Tok shut down US access to the app last night, which (again) they're not required to do, displaying this message:
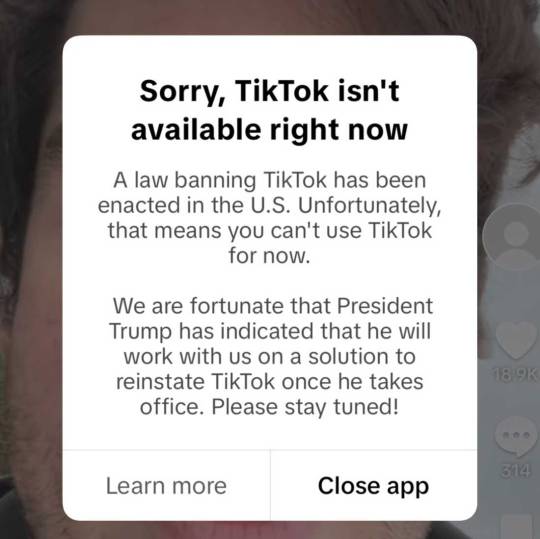
.... then re-allowed access hours later thanking "President Trump for providing the necessary clarity and assurance to our service providers that they will face no penalties providing TikTok." "Assurance" doesn't change the reality of the situation. He's not president yet, he can't issue an executive order yet so if access had ever been illegal it would still be illegal today, and an executive order wouldn't fix it anyway.
(In fairness, the president could provide a one-time ninety-day extension, but it's a certification operating within the context of the law as passed. There'd have to be evidence a sale to a US company was in the works. Which there's not because ByteDance doesn't want to sell. Trump couldn't just say "Tik Tok's legal again so suck it Congress," even after the inauguration.)
f) Elon Musk is also negotiating with China to allow Chinese citizens to access X. Surely that's completely unconnected. I'm not even sure why I'm mentioning it.
g) It's still not available for download on my phone.
h) A lot of the current users were already migrating to another, also Chinese-owned app.
There's something really funny about all this to me, about the multiple levels of sheer stupidity in this whole situation. Probably the most important take-aways long term is this feels very much like autocracy (the way Trump's so involved) and oligarchy (how Elon's own business interests with China seem so inescapably relevant). Also that Mr. Trump is an unbelievably soft touch. Xi, nevermind Putin, will eat him for lunch.
Also-also, if you care about your privacy and data security, stay off the 'Tok if you can. I'm not sure if this is a well-structured law, but the concern driving it seems real enough to me.
Also-also-also? My fellow citizens are dumb.
4 notes
·
View notes
Note
hey hope yr good! was wondering if u have any tips on researching yr ancestry? diolch!
Thank you for the ask! I go about my ancestry research in a very specific way, but I'm happy to describe what I tend to do.
Researching your ancestry (or the ancestry of historical people etc.):
My number one tip for researching ancestry is having perseverance and patience in spades. It's important to know going in that you will get led up blind alleys, dead ends and amass plenty of non-starters, but don't get put off by this! In my experience, the information you're looking for is there, but you have to get real creative about how you go about finding it. Subscriptions to genealogy sites can be helpful too, but aren't a necessity if you're only interested in going a few generations back.
My number two tip is that in general, you will have more information starting out than you think you do. To use myself as an example, when I sat down to research my ancestry, all I knew about my biological family was my birth mother's name, birth city and date of birth - my grandparent's names and dates of birth and a few patchy bits of information about aunts etc. That was 3 years ago. Since then, I've been able to trace ancestors to the second half of the 17th Century. I don't know anything about my biological father's side, so my research was all matrilineal. Starting with my grandparents, I was able to cross-reference entries in the register of births to confirm I had the right people. Once you successfully do this, you can then start on locating your grandparent's parents. In my case, I went from knowing about 2 ancestors to 6 - adding in the 4 which are my matrilineal grandparent's parents. Then repeat the process as far back as evidence and records will allow.
My number three tip concerns the how of researching ancestors. It's all well and good saying 'confirm if X is the parent of Y' but how that's done is another matter.
Taking my own ancestors, lately I've been looking into my Irish ancestors. My matrilineal grandmother's maiden name begins with B [full name redacted for privacy] (naturally you'll need to acquire maiden names of female ancestors for certain bits - this can be done by speaking to family members if that's possible, or by ordering a copy of their marriage certificate. General Register Office index records in the UK will also display maiden names and appear on mainstream subscription genealogy sites). Having ordered my grandmother's marriage certificate and found her GRO index record, I was able to find her maiden name B. as well as her father's name. So then the next step is to find records of that name which match known details (e.g. the marriage certificate usually lists a profession, in the case of my great-grandfather, he worked in sheet metal). In order to identify my great-grandfather with 100% certainty, context like my grandmother's place of birth (Stockport) and year of birth (1950) theoretically places him in Stockport around that year (given 9 months leeway at least) - there's exceptions such as if a male ancestor died before their child was born or if they were never in the picture, but generally this is a rule of thumb. The next thing to do is find records of my great-grandfather in Stockport around 1950 - give or take ~10 years (this is more difficult with more recent ancestors due to census data not being available for most of the 20th Century yet). If one were to look at the 1939 Register (accessible via mainstream genealogy sites and in-person at Kew for free) a person matching my grandmother's father's first name, middle name and surname and who is married and worked in sheet metal is recorded in the same district my grandmother would be born in in 1950. A good start - but as with any good research, you gotta corroborate. In most cases, it would be fine to presume at this point that the woman my great-grandfather is married to in the 1939 Register is my grandmother's mother. However, upon checking the GRO Index of births, my great-grandfather and his wife's name do not come up when searching for my grandmother's birth record. Instead, my great-grandfather's name comes up with a different name. To be brief, the actual situation is that he separated from his first spouse before my grandmother who was born. Thus why his wife in 1939 *isn't* my great-grandmother. Upon checking the second spouse's name against the GRO index, my great-grandfather married her in the 1980s (thus legitimising my grandmother - one can only assume the law and taboo around divorce led to the delay in marrying his new spouse). Great-grandmother's name confirmed. So that gives me both my great-grandparent's names. But sticking with my great-grandfather, lets say I want to trace his father. Knowing more detail about my great-grandfather's later life means I can double check details of his early life. After having ordered his marriage certificate with his second wife (most certificates on the GRO are about £11 with second class post) I find out his father's name. Through that, I repeat the process above to verify and corroborate his father's details to match him 100%. Assuming by now I have my great-grandfather's parent's names through this method, I can locate his birth record on the GRO index and find my great-grandfather was born in 1912 in Liverpool.
And so on and so forth. If you're not in the UK you'll have to look up what resources (paid and free) are available in your country - but some records are possible to find online. My ancestors above were Catholic, so this resource was no use to me. But the Church of England Parish Clerk records for Lancashire are available online here, for example - with similar sites existing for other counties. Another thing is to make use of Boolean commands on Google. Typing "ancestor name" "[year]" "[city or town]" can bring up results - e.g. digitised books, records and newspapers in the public domain are indexed by Google and if you ancestor is mentioned in any of them, they will come up. This happened for me with an ancestor on my grandfather's side - some County Councils keep some historical records online and it turned out one of my ancestors had had sex with two men in 1769 (I guess it must have been the Summer of 69 tbqh!) who were both possibly the father of her child - the court decided they both had to pay child support to the parish (who actually raised the child ).
But remember that you can easily be led up blind alleys, so my biggest tip is still to corroborate and check your work as you go along. Like with my example, if I assumed my great-grandfather's first wife was my great-grandmother, I would have gone completely in the wrong direction. Historical records have a habit of being slippery fish so it's good practice to be critical of sources and make sure you're clear on the timeline of things. If you're using a paid genealogy site, getting things wrong or assuming things can affect other users (if they see your family tree and it has wrong information in it, that can mislead people down the wrong path as well). I've seen this mostly with North American users who might get a fact wrong about a European ancestor and will not notice, causing a lot of headache in setting the record straight. Carelessness from other users pollutes the timeline and can make it difficult for others to research an ancestor you have in common with them if you get it wrong. If you're researching an ancestor who is only a theory or a hypothesis, there are tags you can put on that ancestor's page which show they're a hypothesis/theory - which can really help others know so they don't take the information you have on the ancestor as fact. Despite this, still have fun with it and enjoy finding out more about your relatives - I hope that you're able to find this answer somewhat useful.
If you (or anyone else reading this) has any more questions, you are very welcome to make a comment or send another ask.
Good luck! Pob lwc!
#luke's originals#ask#gofyn#transs3xualmagg0t#ancestry#family history#family tree#family historians#ancestors#ancestor research#geneology
18 notes
·
View notes
Text
My entry: "Digital ID and the Australian Constitution." - Aressida. 28.3.24
Right before the Digital ID Bill was passed by the Australian Senate, Senator Roberts made a last-minute addition:
“Life is about to change for every Australians. As much as Senator Gallagher seeks to downplay the significance of introducing one central digital identifier for each and every Australian, the reality is that this is the most significant legislation I've seen in my time in the Senate. It's the glue that holds together the digital control agenda by which every Australian will be controlled, corralled, exploited and then gagged when they speak or act in opposition.”
“Socialists love control. Socialism needs control. For socialism to exist, there must be control. The government knows control will be used by government to identify people who say mean things on social media to speed up enforcement of our new laws against saying home truths to crazy or dishonest people.”
And from Pauline Hanson, “This law is designed to control the Australian people. It's a step towards the 15-minute cities already being imposed in the United Kingdom, heavily penalising anyone trying to travel outside their community. This is a secretive international effort to establish a one-world government with no freedom and no capacity for dissent.
Let's never forget how easily Australian governments imposed restrictions on us during the pandemic. We couldn't go anywhere without a digital vaccination certificate. Our freedom of speech was suppressed by government and by tech, and it continues in social media content. I will call it out the way I see it, as I always have done. Digital ID is the first step towards these restrictions being imposed on us permanently.”
She gets cut off at the end before she can finish Klaus’ infamous saying…..”You will own nothing and you will be happy!”
————————————————————————————————
We need to firmly oppose this perilous course of action. The imminent implementation of a Digital ID system will enable complete authoritarian control over the state, leading to the establishment of a techno-communist society.
We are rapidly moving towards a future where vaccination passports, CBDCs, and social credit/Co2 scores are all combined into one digital format.
We must not tolerate this encroachment on our individual rights and privacy. It is crucial that we stand against these actions and safeguard the principles that form the foundation of a free and democratic society.
I think the proper order is:
1) The Australian Constitution should include a beginning highlighting the need to protect personal information, protecting individual privacy, and finding a balance between technology progress and individual rights and freedoms.
2) A strong bill of rights that clearly defends the freedoms of expression, privacy, and unjust surveillance in the physical and digital spheres should come after it.
3) In order to safeguard citizens against the misuse of digital ID, the constitution ought to have provisions that clearly define the government's obligation to safeguard citizens' private information, stop illegal access, and guarantee fair and transparent use of digital ID programs.
4) To protect individual privacy, clear regulations pertaining to the gathering, storing, and use of personal data related to digital ID systems should be put in place. These regulations should specify what constitutes informed permission, how data should be minimized, and how long data must be kept.
5) To monitor and control digital ID systems and ensure accountability, openness, and respect for privacy rights, independent oversight bodies need to be set up. These organizations must be able to look into complaints, punish violators, and release periodic reports on privacy conditions.
6) To protect against the marginalization or disadvantage of specific groups, provisions should be included that forbid discrimination based on digital ID.
7) The judiciary should be empowered to invalidate unlawful legislation or activities that violate people's privacy, and a strong system of judicial review should be put in place to allow people to contest abuses of their digital ID systems or rights to privacy.
Let's raise awareness, defend our rights, and ensure government accountability.

14 notes
·
View notes
Text
This week, Congressional leaders are again trying to quietly and quickly get Congress to approve unconstitutional, warrantless mass surveillance.1
Rather than allowing debate on major privacy protections, some members are trying to jam an extension of a controversial warrantless surveillance power — Section 702 of the Foreign Intelligence Surveillance Act (FISA) — into a “must-pass” defense authorization bill.1
Section 702 has been abused in ways that violate Americans’ fundamental civil liberties and civil rights. FBI agents have used 702 to search through troves of warrantlessly acquired communications for conversations with tens of thousands of protestors, racial justice activists, journalists, donors to a Congressional campaign, and countless others.2
We must fight for privacy protections and stop Congress from sneaking 702’s extension into “must-pass” legislation!
Warrantless government surveillance of Americans under Section 702 is out of control, and particularly hurts marginalized communities. The large number of documented abuses by agencies like the NSA, CIA, and FBI include searches for: 141 racial justice protestors, two men “of Middle Eastern descent” who were handling cleaning supplies, mosques that were intentionally mislabeled to prevent oversight, and a state court judge who reported civil rights violations to the FBI.2
Even though the Fourth Amendment protects our right to keep our information private, the government is collecting troves of our data without a warrant.
Any extension of Section 702 would allow the government to obtain new year-long Section 702 certifications at the beginning of the year — allowing this unaccountable, abusive government spying to continue into 2025.
Congressional leaders know that mass surveillance is unpopular, which is why they want to quietly slip it into the defensive authorization bill. We need to let them know that we’re watching and won’t let it happen.
Sources:
Brennan Center, "Coalition Letter Urges Congressional Leaders to Keep Reauthorization of Section 702 Out of NDAA," November 21, 2023.
Brennan Center, “FISA Section 702: Civil Rights Abuses,” November 27, 2023.
Click here to sign
#call to action#online privacy#privacy#surveillance#congress#petition#spying#internet#mass surveillance#Section 702
27 notes
·
View notes