#secure enclaves
Explore tagged Tumblr posts
Text
Forcing your computer to rat you out

Powerful people imprisoned by the cluelessness of their own isolation, locked up with their own motivated reasoning: “It’s impossible to get a CEO to understand something when his quarterly earnings call depends on him not understanding it.”
Take Mark Zuckerberg. Zuckerberg insists that anyone who wanted to use a pseudonym online is “two-faced,” engaged in dishonest social behavior. The Zuckerberg Doctrine claims that forcing people to use their own names is a way to ensure civility. This is an idea so radioactively wrong, it can be spotted from orbit.
From the very beginning, social scientists (both inside and outside Facebook) told Zuckerberg that he was wrong. People have lots of reasons to hide their identities online, both good and bad, but a Real Names Policy affects different people differently:
https://memex.craphound.com/2018/01/22/social-scientists-have-warned-zuck-all-along-that-the-facebook-theory-of-interaction-would-make-people-angry-and-miserable/
For marginalized and at-risk people, there are plenty of reasons to want to have more than one online identity — say, because you are a #MeToo whistleblower hoping that Harvey Weinstein won’t sic his ex-Mossad mercenaries on you:
https://www.newyorker.com/news/news-desk/harvey-weinsteins-army-of-spies
Or maybe you’re a Rohingya Muslim hoping to avoid the genocidal attentions of the troll army that used Facebook to organize — under their real, legal names — to rape and murder you and everyone you love:
https://www.amnesty.org/en/latest/news/2022/09/myanmar-facebooks-systems-promoted-violence-against-rohingya-meta-owes-reparations-new-report/
But even if no one is looking to destroy your life or kill you and your family, there are plenty of good reasons to present different facets of your identity to different people. No one talks to their lover, their boss and their toddler in exactly the same way, or reveals the same facts about their lives to those people. Maintaining different facets to your identity is normal and healthy — and the opposite, presenting the same face to everyone in your life, is a wildly terrible way to live.
None of this is controversial among social scientists, nor is it hard to grasp. But Zuckerberg stubbornly stuck to this anonymity-breeds-incivility doctrine, even as dictators used the fact that Facebook forced dissidents to use their real names to retain power through the threat (and reality) of arrest and torture:
https://pluralistic.net/2023/01/25/nationalize-moderna/#hun-sen
Why did Zuck cling to this dangerous and obvious fallacy? Because the more he could collapse your identity into one unitary whole, the better he could target you with ads. Truly, it is impossible to get a billionaire to understand something when his mega-yacht depends on his not understanding it.
This motivated reasoning ripples through all of Silicon Valley’s top brass, producing what Anil Dash calls “VC QAnon,” the collection of conspiratorial, debunked and absurd beliefs embraced by powerful people who hold the digital lives of billions of us in their quivering grasp:
https://www.anildash.com/2023/07/07/vc-qanon/
These fallacy-ridden autocrats like to disguise their demands as observations, as though wanting something to be true was the same as making it true. Think of when Eric Schmidt — then the CEO of Google — dismissed online privacy concerns, stating “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place”:
https://www.eff.org/deeplinks/2009/12/google-ceo-eric-schmidt-dismisses-privacy
Schmidt was echoing the sentiments of his old co-conspirator, Sun Microsystems CEO Scott McNealy: “You have zero privacy anyway. Get over it”:
https://www.wired.com/1999/01/sun-on-privacy-get-over-it/
Both men knew better. Schmidt, in particular, is very jealous of his own privacy. When Cnet reporters used Google to uncover and publish public (but intimate and personal) facts about Schmidt, Schmidt ordered Google PR to ignore all future requests for comment from Cnet reporters:
https://www.cnet.com/tech/tech-industry/how-cnet-got-banned-by-google/
(Like everything else he does, Elon Musk’s policy of responding to media questions about Twitter with a poop emoji is just him copying things other people thought up, making them worse, and taking credit for them:)
https://www.theverge.com/23815634/tesla-elon-musk-origin-founder-twitter-land-of-the-giants
Schmidt’s actions do not reflect an attitude of “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.” Rather, they are the normal response that we all have to getting doxed.
When Schmidt and McNealy and Zuck tell us that we don’t have privacy, or we don’t want privacy, or that privacy is bad for us, they’re disguising a demand as an observation. “Privacy is dead” actually means, “When privacy is dead, I will be richer than you can imagine, so stop trying to save it, goddamnit.”
We are all prone to believing our own bullshit, but when a tech baron gets high on his own supply, his mental contortions have broad implications for all of us. A couple years after Schmidt’s anti-privacy manifesto, Google launched Google Plus, a social network where everyone was required to use their “real name.”
This decision — justified as a means of ensuring civility and a transparent ruse to improve ad targeting — kicked off the Nym Wars:
https://epeus.blogspot.com/2011/08/google-plus-must-stop-this-identity.html
One of the best documents to come out of that ugly conflict is “Falsehoods Programmers Believe About Names,” a profound and surprising enumeration of all the ways that the experiences of tech bros in Silicon Valley are the real edge-cases, unreflective of the reality of billions of their users:
https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/
This, in turn, spawned a whole genre of programmer-fallacy catalogs, falsehoods programmers believe about time, currency, birthdays, timezones, email addresses, national borders, nations, biometrics, gender, language, alphabets, phone numbers, addresses, systems of measurement, and, of course, families:
https://github.com/kdeldycke/awesome-falsehood
But humility is in short supply in tech. It’s impossible to get a programmer to understand something when their boss requires them not to understand it. A programmer will happily insist that ordering you to remove your “mask” is for your own good — and not even notice that they’re taking your skin off with it.
There are so many ways that tech executives could improve their profits if only we would abandon our stubborn attachment to being so goddamned complicated. Think of Netflix and its anti-passsword-sharing holy war, which is really a demand that we redefine “family” to be legible and profitable for Netflix:
https://pluralistic.net/2023/02/02/nonbinary-families/#red-envelopes
But despite the entreaties of tech companies to collapse our identities, our families, and our online lives into streamlined, computably hard-edged shapes that fit neatly into their database structures, we continue to live fuzzy, complicated lives that only glancingly resemble those of the executives seeking to shape them.
Now, the rich, powerful people making these demands don’t plan on being constrained by them. They are conservatives, in the tradition of #FrankWilhoit, believers in a system of “in-groups whom the law protects but does not bind, alongside out-groups whom the law binds but does not protect”:
https://crookedtimber.org/2018/03/21/liberals-against-progressives/#comment-729288
As with Schmidt’s desire to spy on you from asshole to appetite for his own personal gain, and his violent aversion to having his own personal life made public, the tech millionaires and billionaires who made their fortune from the flexibility of general purpose computers would like to end that flexibility. They insist that the time for general purpose computers has passed, and that today, “consumers” crave the simplicity of appliances:
https://memex.craphound.com/2012/01/10/lockdown-the-coming-war-on-general-purpose-computing/
It is in the War On General Purpose Computing that we find the cheapest and flimsiest rhetoric. Companies like Apple — and their apologists — insist that no one wants to use third-party app stores, or seek out independent repair depots — and then spend millions to make sure that it’s illegal to jailbreak your phone or get it fixed outside of their own official channel:
https://doctorow.medium.com/apples-cement-overshoes-329856288d13
The cognitive dissonance of “no one wants this,” and “we must make it illegal to get this” is powerful, but the motivated reasoning is more powerful still. It is impossible to get Tim Cook to understand something when his $49 million paycheck depends on him not understanding it.
The War on General Purpose Computing has been underway for decades. Computers, like the people who use them, stubbornly insist on being reality-based, and the reality of computers is that they are general purpose. Every computer is a Turing complete, universal Von Neumann machine, which means that it can run every valid program. There is no way to get a computer to be almost Turing Complete, only capable of running programs that don’t upset your shareholders’ fragile emotional state.
There is no such thing as a printer that will only run the “reject third-party ink” program. There is no such thing as a phone that will only run the “reject third-party apps” program. There are only laws, like the Section 1201 of the Digital Millennium Copyright Act, that make writing and distributing those programs a felony punishable by a five-year prison sentence and a $500,000 fine (for a first offense).
That is to say, the War On General Purpose Computing is only incidentally a technical fight: it is primarily a legal fight. When Apple says, “You can’t install a third party app store on your phone,” what they means is, “it’s illegal to install that third party app store.” It’s not a technical countermeasure that stands between you and technological self-determination, it’s a legal doctrine we can call “felony contempt of business model”:
https://locusmag.com/2020/09/cory-doctorow-ip/
But the mighty US government will not step in to protect a company’s business model unless it at least gestures towards the technical. To invoke DMCA 1201, a company must first add the thinnest skin of digital rights management to their product. Since 1201 makes removing DRM illegal, a company can use this molecule-thick scrim of DRM to felonize any activity that the DRM prevents.
More than 20 years ago, technologists started to tinker with ways to combine the legal and technical to tame the wild general purpose computer. Starting with Microsoft’s Palladium project, they theorized a new “Secure Computing” model for allowing companies to reach into your computer long after you had paid for it and brought it home, in order to discipline you for using it in ways that undermined its shareholders’ interest.
Secure Computing began with the idea of shipping every computer with two CPUs. The first one was the normal CPU, the one you interacted with when you booted it up, loaded your OS, and ran programs. The second CPU would be a Trusted Platform Module, a brute-simple system-on-a-chip designed to be off-limits to modification, even by its owner (that is, you).
The TPM would ship with a limited suite of simple programs it could run, each thoroughly audited for bugs, as well as secret cryptographic signing keys that you were not permitted to extract. The original plan called for some truly exotic physical security measures for that TPM, like an acid-filled cavity that would melt the chip if you tried to decap it or run it through an electron-tunneling microscope:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
This second computer represented a crack in the otherwise perfectly smooth wall of a computer’s general purposeness; and Trusted Computing proposed to hammer a piton into that crack and use it to anchor a whole superstructure that could observe — and limited — the activity of your computer.
This would start with observation: the TPM would observe every step of your computer’s boot sequence, creating cryptographic hashes of each block of code as it loaded and executed. Each stage of the boot-up could be compared to “known good” versions of those programs. If your computer did something unexpected, the TPM could halt it in its tracks, blocking the boot cycle.
What kind of unexpected things do computers do during their boot cycle? Well, if your computer is infected with malware, it might load poisoned versions of its operating system. Once your OS is poisoned, it’s very hard to detect its malicious conduct, since normal antivirus programs rely on the OS to faithfully report what your computer is doing. When the AV program asks the OS to tell it which programs are running, or which files are on the drive, it has no choice but to trust the OS’s response. When the OS is compromised, it can feed a stream of lies to users’ programs, assuring these apps that everything is fine.
That’s a very beneficial use for a TPM, but there’s a sinister flipside: the TPM can also watch your boot sequence to make sure that there aren’t beneficial modifications present in your operating system. If you modify your OS to let you do things the manufacturer wants to prevent — like loading apps from a third-party app-store — the TPM can spot this and block it.
Now, these beneficial and sinister uses can be teased apart. When the Palladium team first presented its research, my colleague Seth Schoen proposed an “owner override”: a modification of Trusted Computing that would let the computer’s owner override the TPM:
https://web.archive.org/web/20021004125515/http://vitanuova.loyalty.org/2002-07-05.html
This override would introduce its own risks, of course. A user who was tricked into overriding the TPM might expose themselves to malicious software, which could harm that user, as well as attacking other computers on the user’s network and the other users whose data were on the compromised computer’s drive.
But an override would also provide serious benefits: it would rule out the monopolistic abuse of a TPM to force users to run malicious code that the manufacturer insisted on — code that prevented the user from doing things that benefited the user, even if it harmed the manufacturer’s shareholders. For example, with owner override, Microsoft couldn’t force you to use its official MS Office programs rather than third-party compatible programs like Apple’s iWork or Google Docs or LibreOffice.
Owner override also completely changed the calculus for another, even more dangerous part of Trusted Computing: remote attestation.
Remote Attestation is a way for third parties to request a reliable, cryptographically secured assurances about which operating system and programs your computer is running. In Remote Attestation, the TPM in your computer observes every stage of your computer’s boot, gathers information about all the programs you’re running, and cryptographically signs them, using the signing keys the manufacturer installed during fabrication.
You can send this “attestation” to other people on the internet. If they trust that your computer’s TPM is truly secure, then they know that you have sent them a true picture of your computer’s working (the actual protocol is a little more complicated and involves the remote party sending you a random number to cryptographically hash with the attestation, to prevent out-of-date attestations).
Now, this is also potentially beneficial. If you want to make sure that your technologically unsophisticated friend is running an uncompromised computer before you transmit sensitive data to it, you can ask them for an attestation that will tell you whether they’ve been infected with malware.
But it’s also potentially very sinister. Your government can require all the computers in its borders to send a daily attestation to confirm that you’re still running the mandatory spyware. Your abusive spouse — or abusive boss — can do the same for their own disciplinary technologies. Such a tool could prevent you from connecting to a service using a VPN, and make it impossible to use Tor Browser to protect your privacy when interacting with someone who wishes you harm.
The thing is, it’s completely normal and good for computers to lie to other computers on behalf of their owners. Like, if your IoT ebike’s manufacturer goes out of business and all their bikes get bricked because they can no longer talk to their servers, you can run an app that tricks the bike into thinking that it’s still talking to the mothership:
https://nltimes.nl/2023/07/15/alternative-app-can-unlock-vanmoof-bikes-popular-amid-bankruptcy-fears
Or if you’re connecting to a webserver that tries to track you by fingerprinting you based on your computer’s RAM, screen size, fonts, etc, you can order your browser to send random data about this stuff:
https://jshelter.org/fingerprinting/
Or if you’re connecting to a site that wants to track you and nonconsensually cram ads into your eyeballs, you can run an adblocker that doesn’t show you the ads, but tells the site that it did:
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Owner override leaves some of the beneficial uses of remote attestation intact. If you’re asking a friend to remotely confirm that your computer is secure, you’re not going to use an override to send them bad data about about your computer’s configuration.
And owner override also sweeps all of the malicious uses of remote attestation off the board. With owner override, you can tell any lie about your computer to a webserver, a site, your boss, your abusive spouse, or your government, and they can’t spot the lie.
But owner override also eliminates some beneficial uses of remote attestation. For example, owner override rules out remote attestation as a way for strangers to play multiplayer video games while confirming that none of them are using cheat programs (like aimhack). It also means that you can’t use remote attestation to verify the configuration of a cloud server you’re renting in order to assure yourself that it’s not stealing your data or serving malware to your users.
This is a tradeoff, and it’s a tradeoff that’s similar to lots of other tradeoffs we make online, between the freedom to do something good and the freedom to do something bad. Participating anonymously, contributing to free software, distributing penetration testing tools, or providing a speech platform that’s open to the public all represent the same tradeoff.
We have lots of experience with making the tradeoff in favor of restrictions rather than freedom: powerful bad actors are happy to attach their names to their cruel speech and incitement to violence. Their victims are silenced for fear of that retaliation.
When we tell security researchers they can’t disclose defects in software without the manufacturer’s permission, the manufacturers use this as a club to silence their critics, not as a way to ensure orderly updates.
When we let corporations decide who is allowed to speak, they act with a mixture of carelessness and self-interest, becoming off-the-books deputies of authoritarian regimes and corrupt, powerful elites.
Alas, we made the wrong tradeoff with Trusted Computing. For the past twenty years, Trusted Computing has been creeping into our devices, albeit in somewhat denatured form. The original vision of acid-filled secondary processors has been replaced with less exotic (and expensive) alternatives, like “secure enclaves.” With a secure enclave, the manufacturer saves on the expense of installing a whole second computer, and instead, they draw a notional rectangle around a region of your computer’s main chip and try really hard to make sure that it can only perform a very constrained set of tasks.
This gives us the worst of all worlds. When secure enclaves are compromised, we not only lose the benefit of cryptographic certainty, knowing for sure that our computers are only booting up trusted, unalterted versions of the OS, but those compromised enclaves run malicious software that is essentially impossible to detect or remove:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
But while Trusted Computing has wormed its way into boot-restrictions — preventing you from jailbreaking your computer so it will run the OS and apps of your choosing — there’s been very little work on remote attestation…until now.
Web Environment Integrity is Google’s proposal to integrate remote attestation into everyday web-browsing. The idea is to allow web-servers to verify what OS, extensions, browser, and add-ons your computer is using before the server will communicate with you:
https://github.com/RupertBenWiser/Web-Environment-Integrity/blob/main/explainer.md
Even by the thin standards of the remote attestation imaginaries, there are precious few beneficial uses for this. The googlers behind the proposal have a couple of laughable suggestions, like, maybe if ad-supported sites can comprehensively refuse to serve ad-blocking browsers, they will invest the extra profits in making things you like. Or: letting websites block scriptable browsers will make it harder for bad people to auto-post fake reviews and comments, giving users more assurances about the products they buy.
But foundationally, WEI is about compelling you to disclose true facts about yourself to people who you want to keep those facts from. It is a Real Names Policy for your browser. Google wants to add a new capability to the internet: the ability of people who have the power to force you to tell them things to know for sure that you’re not lying.
The fact that the authors assume this will be beneficial is just another “falsehood programmers believe”: there is no good reason to hide the truth from other people. Squint a little and we’re back to McNealy’s “Privacy is dead, get over it.” Or Schmidt’s “If you have something that you don’t want anyone to know, maybe you shouldn’t be doing it in the first place.”
And like those men, the programmers behind this harebrained scheme don’t imagine that it will ever apply to them. As Chris Palmer — who worked on Chromium — points out, this is not compatible with normal developer tools or debuggers, which are “incalculably valuable and not really negotiable”:
https://groups.google.com/a/chromium.org/g/blink-dev/c/Ux5h_kGO22g/m/5Lt5cnkLCwAJ
This proposal is still obscure in the mainstream, but in tech circles, it has precipitated a flood of righteous fury:
https://arstechnica.com/gadgets/2023/07/googles-web-integrity-api-sounds-like-drm-for-the-web/
As I wrote last week, giving manufacturers the power to decide how your computer is configured, overriding your own choices, is a bad tradeoff — the worst tradeoff, a greased slide into terminal enshittification:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
This is how you get Unauthorized Bread:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
All of which leads to the question: what now? What should be done about WEI and remote attestation?
Let me start by saying: I don’t think it should be illegal for programmers to design and release these tools. Code is speech, and we can’t understand how this stuff works if we can’t study it.
But programmers shouldn’t deploy it in production code, in the same way that programmers should be allowed to make pen-testing tools, but shouldn’t use them to attack production systems and harm their users. Programmers who do this should be criticized and excluded from the society of their ethical, user-respecting peers.
Corporations that use remote attestation should face legal restrictions: privacy law should prevent the use of remote attestation to compel the production of true facts about users or the exclusion of users who refuse to produce those facts. Unfair competition law should prevent companies from using remote attestation to block interoperability or tie their products to related products and services.
Finally, we must withdraw the laws that prevent users and programmers from overriding TPMs, secure enclaves and remote attestations. You should have the right to study and modify your computer to produce false attestations, or run any code of your choosing. Felony contempt of business model is an outrage. We should alter or strike down DMCA 1201, the Computer Fraud and Abuse Act, and other laws (like contract law’s “tortious interference”) that stand between you and “sole and despotic dominion” over your own computer. All of that applies not just to users who want to reconfigure their own computers, but also toolsmiths who want to help them do so, by offering information, code, products or services to jailbreak and alter your devices.
Tech giants will squeal at this, insisting that they serve your interests when they prevent rivals from opening up their products. After all, those rivals might be bad guys who want to hurt you. That’s 100% true. What is likewise true is that no tech giant will defend you from its own bad impulses, and if you can’t alter your device, you are powerless to stop them:
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
Companies should be stopped from harming you, but the right place to decide whether a business is doing something nefarious isn’t in the boardroom of that company’s chief competitor: it’s in the halls of democratically accountable governments:
https://www.eff.org/wp/interoperability-and-privacy
So how do we get there? Well, that’s another matter. In my next book, The Internet Con: How to Seize the Means of Computation (Verso Books, Sept 5), I lay out a detailed program, describing which policies will disenshittify the internet, and how to get those policies:
https://www.versobooks.com/products/3035-the-internet-con
Predictably, there are challenges getting this kind of book out into the world via our concentrated tech sector. Amazon refuses to carry the audio edition on its monopoly audiobook platform, Audible, unless it is locked to Amazon forever with mandatory DRM. That’s left me self-financing my own DRM-free audio edition, which is currently available for pre-order via this Kickstarter:
http://seizethemeansofcomputation.org

I’m kickstarting the audiobook for “The Internet Con: How To Seize the Means of Computation,” a Big Tech disassembly manual to disenshittify the web and bring back the old, good internet. It’s a DRM-free book, which means Audible won’t carry it, so this crowdfunder is essential. Back now to get the audio, Verso hardcover and ebook:
https://www.kickstarter.com/projects/doctorow/the-internet-con-how-to-seize-the-means-of-computation

If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai

[Image ID: An anatomical drawing of a flayed human head; it has been altered to give it a wide-stretched mouth revealing a gadget nestled in the back of the figure's throat, connected by a probe whose two coiled wires stretch to an old fashioned electronic box. The head's eyes have been replaced by the red, menacing eye of HAL 9000 from Stanley Kubrick's '2001: A Space Odyssey.' Behind the head is a code waterfall effect as seen in the credits of the Wachowskis' 'The Matrix.']

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#chaffing#spoofing#remote attestation#rene descartes#adversarial interoperability#war on general purpose computing#canvas attacks#vpns#compelled speech#onion routing#owner override#stalkerware#ngscb#palladium#trusted computing#secure enclaves#tor#interop#net neutrality#taking the fifth#right to remain silent#real names policy#the zuckerberg doctrine#none of your business#the right to lie#right to repair#bossware#spyware#wei web environment integrity
2K notes
·
View notes
Text
Listen I completely understand why Amata makes me leave Vault 101 despite the fact I resolved everything peacefully. What I can't understand is the fact I NEVER ONCE BEFORE LEAVING CAN CONFIDE IN MY CHILDHOOD BEST FRIEND ABOUT MY FATHER DYING??!!
If they weren't going to give me the option why give me this quest RIGHT after his death?!?!!!
Amata telling me I can’t stay would’ve hit harder if she knew I had NO family outside the Vault.
What a missed opportunity.

I really am the LONE wanderer no one has my back in this game except Fawkes.
#Technically I also have Charon but I also LITERALLY have Charon I own his contract 💀#Every time I get invested in this game something frustrating like this happens.#FAWKES PLANNED TO RESCUE ME FROM THE ENCLAVE!!!! AMATA COULDN'T EVEN ASK ME HOW I'VE BEEN??!!!#I CAN SERIOUSLY ONLY MENTION MY DAD BEING DEAD TO OFFICER GOMEZ!!?!?!??! THE SECURITY GUARD AT MY TENTH BIRTHDAY PARTY!?!?!?!?!#Fallout 3 has INCREDIBLE INTERESTING FUN MOMENTS!!!! It's the little details in the main storyline that are bothering me.#Fallout 3#Fallout 3 Spoiler#MaddyPlaysFallout3#My Lone Wanderer is the embodiment of that meme: Puppy want a treat? Puppy want a fucking break from it all.
30 notes
·
View notes
Text
the problem isn't that the fallout show does new things* in the setting its that the sum total of the additions lead to a less thematically interesting story and also remove a lot of fan favourite aspects that made the setting unique
*new as in events that happened after the timeline of the games, there is nothing novel about the events
#me_irl#im not (just) a lorehead who thinks new thing bad. but if the new thing is just removing cool shit then whyyyyy#whyyyy is the enclave herrrre why is there nuclear power (good) (not even explored in a meaningful way (yet tbf it is basically a final ep#reveal but i have little faith it will be more than a macguffin))#why is arguably the most advanced and secure settlement in the US a ruin now#is it not more interesting in a story where capitalism ended the world to show capitalists still persisting in a literal wasteland
1 note
·
View note
Text
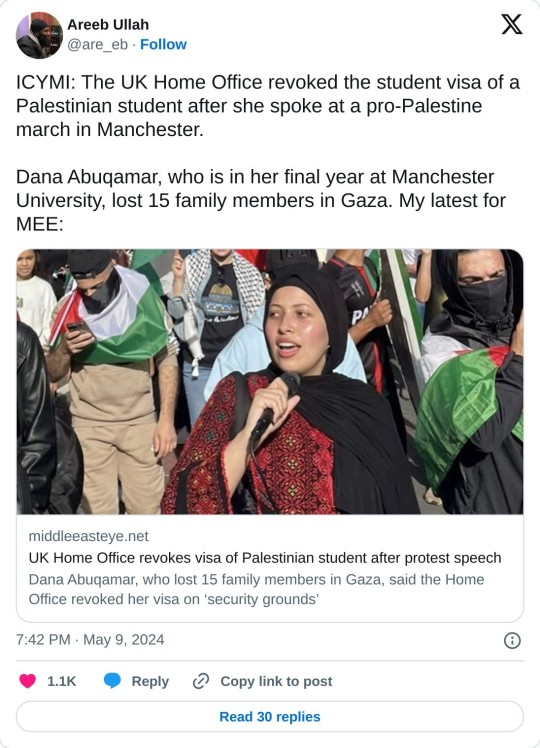
The UK government has revoked the student visa of a Palestinian student who lost relatives in Gaza after she spoke at a demonstration at the University of Manchester. Dana Abuqamar, a law student who heads the Friends of Palestine Society at the University of Manchester, said the UK government revoked her visa on “national security” grounds, after claiming she was a risk to public safety. “The claim they are making is baseless and violates my rights as a resident here in the UK. My legal team has lodged a human rights appeal against this decision to revoke my student visa in my last and final year as a law student,” Abuqamar said, speaking to Al Jazeera English, confirming that her visa had been revoked. Last year, Abuqamar revealed that she had lost at least 15 relatives in Gaza after the Israeli army bombed a three-storey building in the besieged enclave. “During this genocide, the UK Home Office decided to revoke my student visa following public statements supporting the Palestinian right to exercise under international law to resist oppression and break through the siege that was illegally placed on Gaza for over 16 years,” said Abuqamar. “Freedom of expression is a fundamental human right, but it seems to not apply to ethnic minorities, particularly Muslims and Palestinians like myself. We must reject the double standard in the application of human rights by public authorities and rise against this oppression.” A spokesperson for the UK Home Office said it did not respond to individual cases.
#yemen#jerusalem#tel aviv#current events#palestine#free palestine#gaza#free gaza#news on gaza#palestine news#news update#war news#war on gaza#great britain#human rights#gaza genocide#genocide
5K notes
·
View notes
Text
"A ceasefire deal was reached Wednesday [January 15, 2025[ to end 15 months of fighting in the Gaza Strip, according to President Joe Biden, Qatar's prime minister and Hamas officials.
The hard-won agreement will also free dozens of hostages held in Gaza, as well as Palestinians in Israeli jails, bringing the first real break in violence since a weeklong truce expired Dec. 1, 2023.
The deal will take effect Sunday [January 19, 2025, this appears to be the prisoner release, not the ceasefire itself], according to Qatar’s prime minister and foreign minister, Sheikh Mohammed bin Abdulrahman Al Thani, whose country hosted weeks of intense negotiations.
Under the phased agreement, Israeli forces would withdraw to the Gaza border, allowing displaced Palestinians to return to their homes and for the transfer of hostages and prisoners. Large amounts of humanitarian aid would be shipped to the enclave and hospitals and health care centers would be rebuilt, he said.
Hamas, meanwhile, will release 33 hostages in exchange for 100 Palestinian prisoners with life sentences, according to a portion of the deal shared by Hamas. Israel will also release 1,000 Palestinian prisoners who were not involved in the Oct. 7 attacks, the text says, and an unspecified number of Palestinian prisoners will also be released abroad or in Gaza...
Earlier, a diplomatic source in Washington told NBC News that Netanyahu was preparing to meet with his security Cabinet, where approval of the deal was expected quickly. He would then take the pact to the full Cabinet, which is also expected to approve.
Israel’s Supreme Court would have 24 hours to permit an appeal, so the earliest a ceasefire could go into effect would be Friday [January 17, 2025], the source said. The first group of hostages would come out Sunday, the person added.
The war has shattered Gaza’s infrastructure and displaced most of its population. Health officials in the enclave say more than 46,000 Palestinians have been killed by Israeli forces, most of them civilians.
The chances for a ceasefire seemed vanishingly small after many false dawns in recent months.
In November, the International Criminal Court issued an arrest warrant against Netanyahu for alleged war crimes and crimes against humanity. Amnesty International and Doctors Without Borders in December accused Israel of carrying out a genocide in Gaza."
-via NBC News, January 15, 2025
#FINALLY OH MY GOD FINALLY FINALLY FINALLY#THANK FUCKING GOD#ceasefire#gaza genocide#gaza#palestinian#palestine#israel#good news#hope
828 notes
·
View notes
Text
Israel is arming local militias in Gaza in an effort to counter Hamas in the besieged enclave, officials say, as opposition politicians warned that the move endangers national security.
Israeli Prime Minister Benjamin Netanyahu defended the covert enterprise on Thursday, calling it “a good thing.” In a video posted on social media, Netanyahu said Israel had “activated clans in Gaza which oppose Hamas,” and that it was done “under the advice of security elements.”
Former defense minister and Netanyahu rival Avigdor Liberman divulged the move on Israel’s Ch. 12 News on Wednesday, saying that Israel was distributing rifles to extremist groups in Gaza and describing the operation as “complete madness.”
“We’re talking about the equivalent of ISIS in Gaza,” Liberman said one day later on Israel’s Army Radio, adding that Israel is providing weapons to “crime families in Gaza on Netanyahu’s orders.”[...]
One group that has received weapons from Israel is the militia led by Yasser Abu Shabab, officials said. Abu Shabab heads an armed group that controls some territory in eastern Rafah and he has posted photos of himself holding an AK-47 rifle with UN vehicles behind him. Though Abu Shabab has denied receiving weapons from Israel, Hamas has accused him of being a “traitor.”
6 Jun 25
381 notes
·
View notes
Text
Pre-game CANON courier backstory includes:
Has never seen a fish
Wandering around the wasteland so much that you accidentally create a new city to profit off of it
Was going to travel through quarry junction to get to Vegas
Knows how to do woodworking?
Sold Brahmin in the same area that Cass did
The enclave?? Hires you?? To drug mule a detonator into your own house??
Alternate theory: NCR was scrapping parts of Navvaro and found a package matching symbols in the divide, sent it there, and accidentally blew everything up
Been to Montana, as well as Colorado and Utah before the legion took both over
Never had former schooling
Was also a bounty hunter, along with being a courier and a caravaneer???
Travels both the long 15 and the created the divide
You being stalked by a legion spy who is also so in love with wandering around that he finds hope for the first time
Until you destroy the very thing that he loved and he vows to get revenge
not being aware of the existence of the midwest
possibly being a legion spy who aimed to cut off the NCR from Vegas in order to more easily secure the dam
Moved to the Mohave 4 years before the start of the game
Claims to be a mercenary?
Isn't surprised by aliens and/or the mention of them
Instinctively knows how to gamble and how to lead a team of snipers?
#fallout#shitpost#fnv#fallout new vegas#yes man fnv#fnv dlc#fnv companions#fnv legion#arcade fnv#victor fnv#fnv oc#fnv boone#fnv courier#fnv vulpes#ulysses fnv#the courier#courier 6#courier six#caesar fnv#fnv benny#fnv lonesome road#lonesome road#fnv owb#benny fnv#fnv yes man#fallout original character#fallout nv#fallout ncr#ncr#the divide
246 notes
·
View notes
Text

[ 📹 Scenes of chaos and fear after the Israeli occupation forces bombed a school housing displaced Palestinian families opposite Nasser Medical Complex west of the city of Khan Yunis, in the southern Gaza Strip, after displacing civilians from other areas of the enclave. 📈 Current death toll in Gaza exceeds 37'953 Palestinians killed, while another 87'266 others have been wounded since Oct. 7th. ]
🇮🇱⚔️🇵🇸 🚀🏘️💥🚑 🚨
GENOCIDE CONTINUES ON DAY 271: ISRAELI OCCUPATION REACHES OUT TO GAZA CLAN LEADERS, HAMAS WARNS OF RETALIATION FOR COLLABORATORS, ZIONIST COLONIAL SETTLERS CONTINUE RAIDING AL-AQSA MOSQUE, AL-QUDS BRIGADES SAY HOSTAGES ATTEMPTED SUICIDE AS THEIR TREATMENT BECOMES MORE SEVERE FOLLOWING REPORTS OF TORTURE IN ISRAELI PRISONS, SLAUGHTER OF CIVILIANS CONTINUES
On 271st day of the Israeli occupation's ongoing special genocide operation in the Gaza Strip, the Israeli occupation forces (IOF) committed a total of 3 new massacres of Palestinian families, resulting in the deaths of no less than 28 Palestinian civilians, mostly women and children, while another 125 others were wounded over the previous 24-hours.
It should be noted that as a result of the constant Israeli bombardment of Gaza's healthcare system, infrastructure, residential and commercial buildings, local paramedic and civil defense crews are unable to recover countless hundreds, even thousands, of victims who remain trapped under the rubble, or who's bodies remain strewn across the streets of Gaza.
This leaves the official death toll vastly undercounted as Gaza's healthcare officials are unable to accurately tally those killed and maimed in this genocide, which must be kept in mind when considering the scale of the mass murder.
A number of Israeli hostages have attempted suicide in the detention of the Palestinian resistance. This is according to the Al-Quds Brigades, belonging to the group Palestinian Islamic Jihad (PIJ).
In a statement, the Al-Quds Brigades said that several Israeli hostages in their care had attempted suicide due to the severe frustration they feel owing to their government's disinterest in recovering their detainees, and due to the deteriorating treatment they are receiving from their captors.
According to Al-Quds, as a result of the horrendous treatment of Palestinian prisoners at the hands of the Israeli occupation army in occupation prisons, including allegations of torture, rape, withholding of food and water, blindfolding, medical abuse and more, the Palestinian resistance group has taken a decision to treat their detainees harshly.
"Our decision in the Al-Quds Brigades to treat the occupation's prisoners in the same way as our prisoners inside the prisons, will remain in effect as long as the terrorist government continues its unjust measures against our people and prisoners. He who warns is excused," Al-Quds said in its statement.
In the meantime, one of the main reasons the Palestinian resistance factions cited for conducting Operation Al-Aqsa Flood on October 7th, 2023, was the regular raids by Zionist colonial settlers of the Al-Aqsa Mosque compound in occupied Al-Quds (Jersusalem), one of the holiest sites in Islamic religion.
Those raids continue to occur, with groups of dozens of Zionist colonial settlers storming the compound on Wednesday, while under the protection of the Israeli occupation army.
Local eyewitnesses reported today that groups of dozens of Zionist colonial settlers raided the Al-Aqsa Mosque compound, touring the Mosque's courtyard and performing provocative Talmudic rituals as the occupation army protected the settlers.
The report also added that the Occupation Shin Bet Police stormed the Old City of occupied Al-Quds, turning the area into a military barracks, while hundreds of police were deployed to secure the area, in particular near the gates of the Al-Aqsa compound.
The Shin Bet also tightened security measures at the gates of the Old City, as well as Al-Aqsa Mosque, while imposing restrictions on the entry of Palestinian worshippers.
In other news on Wednesday, July 3rd, the London-based Reuters news-wire service is reporting that the Israeli entity has been reaching out to the leaders of major Gaza clans, looking to find Palestinians that are not associated with Hamas or other Palestinian resistance factions to oversee the final stages of the occupation's plans in the Gaza Strip, and to eventually replace the Hamas movement in governing the enclave.
Reuters says the Israeli occupation remains under heavy pressure from the United States to bring an end to the war in the Gaza Strip, but does not want Hamas to retain control over the Strip.
As a result, the Israeli occupation's leadership is forming plans for the "day after" the end of the war, including forming a governing structure parallel to the Hamas government that has led the Gaza Strip since 2007, hoping to shape an alternative civil administration involving Palestinians that are not associated with the Palestinian Resistance movement.
Unfortunately for the occupation, this leaves few plausible options, with the current focus being on the heads of powerful Palestinian clans in Gaza, which the Israeli entity has been attempting to woo in recent days.
Speaking with Reuters, Senior Palestine Analyst at the International Crises Group, a Brussels-based think-tank, Tahani Mustafa, says the Zionist entity has been "actively looking for local tribes and families on the ground to work with them."
According to Tahani Mustafa, the Gaza Clans "don’t want to get involved, in part because they fear retribution from Hamas."
The threat is a real one for Gaza's Clan leaders, who fear retribution from Hamas, who, despite the Israeli occupation's determination to destroy the Resistance group, retains its control over large sections of the Palestinian enclave.
Sure enough, a correspondant with Reuters asked the director of Gaza's media office, Ismail Thawabteh, what the consequences would be for those who cooperate with the Zionist regime, who responded by saying “I expect the response to be deadly for any clan or party that agrees to implement the occupation’s plans. I expect the response to be lethal from the resistance factions.”
Occupation Prime Minister Benjamin Netanyahu has acknowledged the challenges he will face in instituting a new governing structure in the Gaza Strip, claiming his government has reached out to Gaza's clans, but that Hamas "eliminated" them, adding that his Defense Ministry had a new plan, but would not elaborate on it, stating only that he was not willing to bring in the Palestinian Authority to govern in Gaza.
The Palestinian clans are made up of powerful families in the Gaza Strip, ones which do not have formal connections with the Hamas resistance movement, with each clan having a leader known as a "mukhtar", which under British rule, prior to the creation of the Israeli entity in 1948, were heavily relied on to govern.
Following Hamas' rise to power, the clans powers were limited by the religious movement, but were still allowed a certain degree of autonomy, while clans remain influential and own a number of commercial businesses and facilities in the Palestinian enclave
The Israeli occupation already retains contact with Gaza's clans in order to coordinate commercial shipments and deliveries, among other practical issues.
According to Reuters, clan leaders are reluctant to disclose contacts with the Israeli occupation, while others said the mukhtars would not cooperate with the Zionist entity.
One of Gaza's clan leaders that spoke with Reuters said he knew of calls other mukhtars had had with the Israeli authorities, but that "I expect that mukhtars will not cooperate with these games," citing anger with the occupation over its genocide of Palestinians in the Strip, which has killed a number of clan members and destroyed much of their property.
Meanwhile, the slaughter of civilians, along with the destruction of housing and public infrastructure in Gaza, continues into its 10th month as the occupation army bombs and shells various areas of the enclave.
The Israeli occupation forces (IOF) continued on Wednesday with its attacks on the Al-Shujaiya neighborhood, east of Gaza City, bombing residential homes and causing the deaths of a number of Palestinian civilians, including women and children, while local rescue crews were unable to reach sites due to the continued bombardment and gunfire from occupation drones.
In a new atrocity, Zionist warplanes bombed a residential house belonging to the Maqat family in the vicinity of the Sheikh Radwan neighborhood, north of Gaza City, after which, local paramedic crews managed to recover the bodies of 7 civilians killed in the strikes, along with 7 wounded victims from under the rubble. The casualties were transported to Al-Ahli Baptist Hospital in the city.
Simultaneously, Zionist artillery shelling pummeled the Tal al-Hawa neighborhood, southwest of Gaza City, while gunfire from occupation armored vehicles targeted citizen's homes.
Similarly, Israeli quadcopter drones fired at civilians in various areas of Gaza City, in conjuction with the violent artillery shelling of the Al-Zaytoun neighborhood, southeast of the city.
An Israeli occupation fighter jet also fired a missile into the Al-Ghafri printing press on Jaffa Street, in the Al-Tuffah neighborhood, east of Gaza City, while another Zionist aircraft fired a missile into a residential apartment complex in the Zarqa neighborhood of Gaza City, leaving rescue crews to search the rubble for the dead and wounded.
In the meantime, the Palestinian Red Crescent Society (PRCS) is reporting that two civilians were wounded as a result of an occupation airstrike on a residential house belonging to the Kurd family, in the Beit Lahiya Project in Gaza's north, while the wounded were transferred to Kamal Adwan Hospital near the Jabalia Camp.
The Israeli occupation army also shelled several areas of the Nuseirat Refugee Camp, in the central Gaza Strip, as well as in the Al-Zahra'a area, and the Al-Mughraqa area, coinciding with intense occupation gunfire.
IOF warplanes also continue their bombardment of residential homes and apartment complexes in central and western Rafah, in the southern Gaza Strip.
The Zionist entity continued its war crimes when it bombed a gathering of civilians attempting to return to their homes in the Al-Shujaiya neighborhood, east of Gaza City, resulting in the deaths of four Palestinians and wounding more than 17 others.
In another atrocity, an Israeli drone bombed a civilian vehicle in the Al-Maghazi Refugee Camp, in central Gaza, killing three more civilians and wounding several others who were taken to Al-Aqsa Martyrs Hospital in Deir al-Balah.
In the meantime, areas northeast of the Jabalia Camp sustained intermittent artillery shelling from the occupation army, wounding a number of Palestinian civilians.
The crimes of the Zionist occupation continued with an airstrike that targeted a residential apartment in the Nuseirat Camp, in central Gaza, killing two Palestinians and wounding several others who were transported to Al-Aqsa Martyrs Hospital.
Local civil defense crews also managed to recover the bodies of 7 murdered Palestinians from the Tal al-Sultan neighborhood, west of the city of Rafah, in the southern Gaza Strip, including 5 completely charred bodies.
Later, on Wednesday afternoon, the Zionist army bombed a group of Palestinians in the Jahar al-Dik area near Al-Nuseirat, killing two and wounding others who were transferred to Al-Awda Hospital in the Nuseirat Camp.
Due to the continued bombing of public infrastructure in the southern Gaza Strip, including water treatment plants, wells, and sewage systems, deep levels of sewage now run through the streets of Khan Yunis, where hundreds of thousands of Palestinians have been forced to reside after being displaced from one area after another, now being ordered into the city by the Zionist occupation army.
As a result of the Israeli occupation's ongoing war of extermination in the Gaza Strip, the infinitely rising death toll now exceeds 37'953 Palestinians killed, including upwards of 10'000 women and well over 15'000 children, while another 87'266 others have been wounded since the start of the current round of Zionist aggression, beginning with the events of October 7th, 2023.
July 3rd, 2024.
#source1
#source2
#source3
#source4
#source5
#source6
#source7
#source8
#source9
#source10
#videosource
#graphicsource
@WorkerSolidarityNews
#gaza#gaza strip#gaza news#gaza war#gaza genocide#genocide#war in gaza#genocide in gaza#israeli genocide#israeli occupation#israeli war crimes#occupation#war crimes#crimes against humanity#palestine#palestine news#palestinians#free palestine#gaza conflict#israel palestine conflict#middle east#war#politics#news#geopolitics#international news#global news#breaking news#israel#current events
394 notes
·
View notes
Text

a young Florian, the de facto founder of ironwall & originator of the set of penal laws governing centaur citizens of the region. Florian was a close friend of the king and often expressed an ambition to 'unite' what were then quite disparate enclosures and enclaves under a single banner (the king's). he believed that the future residents of his city would be a beacon of pious humility, and that this would naturally lead to prosperity and divine favour.
at the time attitudes towards him were understandably mixed, but the offer of a huge amount of the king's land and the promise of a peaceful life was tempting. The original charter had the effect of rebranding every centaur as now resident in Ironwall and subject to its laws. Every centaur was considered a convert & subject of the king and God, whether or not they knew it. In a single stroke, it also rendered every centaur eligible for military service (men and women both, though only the men were given combat roles). Although he would later be considered misguided at best and a monster at worst, Florian died happy, with the complete faith that he had secured passageway to heaven for his people.
he was quite famous for wearing only black.
214 notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image: Mike (modified) https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
576 notes
·
View notes
Text
Israeli Prime Minister Benjamin Netanyahu said the population of Gaza will be displaced to the south after his security cabinet approved an expanded military operation in the enclave that a minister described as a plan to “conquer” the territory.
“If no hostage deal is reached, Operation Gideon’s Chariots will begin with full force and will not stop until all its objectives are achieved.”
The plan then, is to displace Gaza’s entire population to the south of the enclave, following which the total the blockade of humanitarian aid may be lifted, the official said, adding that the military “will remain in every area it captures.”
Meanwhile, Israel’s far-right Finance Minister Bezalel Smotrich said Monday that “we are finally going to conquer the Gaza Strip.”
124 notes
·
View notes
Text
Israel’s political and military leaders have approved plans to expand the Gaza offensive and take over aid deliveries to the devastated and starving enclave, according to reports. Prime Minister Benjamin Netanyahu’s Security Cabinet unanimously approved plans to call up reservists and put the Israeli military in charge of food and other vital supplies to the 2.3 million people suffering under its blockade of the Palestinian territory. Newswires reported unnamed Israeli officials suggesting that the plans include the “conquest” and occupation of the entire Gaza Strip. The expanded offensive “could go as far as seizing the entire enclave”, the Reuters news agency reported. “The plan will include, among other things, the conquest of the Gaza Strip and the holding of the territories, moving the Gaza population south for their protection,” a source told the AFP news agency.
144 notes
·
View notes
Text
World Central Kitchen announced that it will resume operations in Gaza on Monday, almost one month after seven of its aid workers were killed in an Israeli airstrike in the enclave. The U.S.-based nonprofit group, founded by celebrity chef José Andrés, suspended operations in Gaza for four weeks after the workers were killed on April 1, according to a statement. The organization identified the aid workers as Saifeddin Issam Ayad Abutaha, a 25-year-old Palestinian; Lalzawmi (Zomi) Frankcom, a 43-year-old Australian; Damian Soból, a 35-year-old from Poland; Jacob Flickinger, a 33-year-old dual citizen of the U.S. and Canada; Security team members John Chapman, 57, James (Jim) Henderson, 33, and James Kirby, 47, all from the United Kingdom, were also killed in the attack.
Before halting operations, the organization had distributed more than 43 million meals in Gaza “and accounted for 62% of all international NGO aid,” WCK said in a statement. “The humanitarian situation in Gaza remains dire,” said Erin Gore, the nonprofit’s chief executive officer. “We are restarting our operation with the same energy, dignity, and focus on feeding as many people as possible.” WCK has 276 trucks carrying almost 8 million meals that are ready to cross into Gaza via Rafah, and will send trucks into the enclave via Jordan too, it said in a statement. The organization is also continuing to explore delivering food with the help of Open Arms, a Spanish humanitarian organization, and the United Arab Emirates.
#yemen#jerusalem#tel aviv#current events#palestine#free palestine#gaza#free gaza#news on gaza#palestine news#news update#war news#war on gaza#world central kitchen#famine#gaza genocide#genocide
1K notes
·
View notes
Text
Like in motorsports, oil in cooking is everything. You have to select the right viscosity, the perfect origin, and the ideal smoke point. What, you just throw "extra virgin" olive oil on your pan without thinking too much about it? My great-grandmother would shit blood until she died again at you.
At the mall, they have an oil store. Yes, a mall, that's how upscale you have to be for this kind of store. It's inside one of the rich-people enclaves, and they've somehow blocked it out from the satellites. Didn't even know it was there until I had to get inside to rescue my friend Joseph, who had (you guessed it) stolen some key datasofts from the CEO of Zaibatsu Corporation.
While we were in the area, I figured I would duck into the mall while fleeing the corporate security. Those chipped-up cyborg death machines would never think to come looking for us in a bourgeois olive oil store. And it turns out they also had free bread for sampling the oil! Real bread, made from plants! Boy, if the people on the outside knew about this, they'd be knocking down the walls instead of just sneaking in through the Waste Output Port 195-B like I did.
We ate like three loaves of bread each, which I think made the clerkdroid a little suspicious. To allay its fears, we kept repeating rich-people catchphrases like "my fourth yacht," "investment account," "mergers and acquisitions," "the rabble outside threaten our very way of living," and my favourite, "I cannot afford a $500 per year tax hike." That seemed to placate its pattern-matching algorithms, and we were able to stay in there until the store closed.
What oil did we buy? None. Joseph offered to get me a bottle, for all my trouble, but the price tag was literally not visible to our eyes. We decided to go home instead. While we drove, dodging the hunter-killer drones the whole way, we thought about how nice it would be to be the kind of person who worries about different sorts of oil. My great-grandma would probably understand that the only kind I have left to fry eggs in is "motor, used."
81 notes
·
View notes
Text
Israel’s security cabinet has approved a controversial proposal to facilitate Palestinian emigration from Gaza, a move critics warn could amount to ethnic cleansing.
Israeli Finance Minister Bezalel Smotrich on Sunday said the security cabinet approved the proposal by Defense Minister Israel Katz to organize “a voluntary transfer for Gaza residents who express interest in moving to third countries, in accordance with Israeli and international law, and following the vision of US President Donald Trump.”
The decision marks a remarkable endorsement of a plan once considered a far-right fantasy – and comes despite the prime minister’s earlier pledge not to permanently displace Gaza’s civilian population.
Critics have said that any mass displacement of Gazans in the midst of a devastating war would amount to ethnic cleansing, an act associated with war crimes and crimes against humanity under international law. Israeli officials have countered that emigration would be voluntary and in line with international legal standards.
But aid groups argue that Israel’s war has made life in Gaza nearly impossible. Martin Griffiths, the United Nations’ top emergency relief official, has called the enclave “uninhabitable,” saying its people are “witnessing daily threats to their very existence.”[...]
The Palestinian Authority’s Minister of State for Foreign Affairs Varsen Aghabekian Shaheen told CNN’s Becky Anderson last month that Palestinians “are steadfast to stay in their land and will not move.”[...]
Smotrich said Sunday that the security cabinet also approved the expansion of Jewish settlements in the occupied West Bank, noting that 13 areas in the West Bank would be split from existing settlements and would be recognized as independent settlements.
24 Mar 25
303 notes
·
View notes
Text
Israel’s attack on Iran has elicited a predictable response from groups that identify as “pro-Palestine.” At protests in several Western cities—some merely anti-war or anti-interventionist, others explicitly anti-Zionist or pro-Iranian—people rushed to criticize the Israeli military action to prevent Tehran from acquiring nuclear weapons. In so doing, they offer succor to a ruthless theocratic regime that has ground its heel upon its own people and brought misery to the entire region for nearly half a century.
By backing various regimes and militias in Iraq, Syria, Lebanon, Yemen, and Gaza, the Islamic Republic of Iran has been responsible, directly or indirectly, for the death of hundreds of thousands of Arab and Muslim people in the conflicts it has fomented. Iranian meddling in the region has provided Arab dictators such as Syria’s Bashar al-Assad with both the moral and material means to suppress dissent, crush reform, and extend their autocratic rule. The pro-Palestine messaging ignores the fact that a nuclear-armed Iran would be far more belligerent and dangerous than the regime already has been for the past three decades.
For the pro-Palestine lobby to take at face value Tehran’s claim to lead an “Axis of Resistance” against Israel is at best naive, and at worst malignant in a way that can only be described as anti-Semitic. It means accepting that the Islamic Republic’s eliminationist rhetoric about Israel has made it a legitimate advocate for the Palestinian cause. These pro-Palestine voices seem oblivious to the fact that the Palestinian national project for independence and statehood is in ruins, thanks in large part to Iranian influence.
Back in the 1990s, Iran’s Revolutionary Guard Corps and political leadership worked to undermine the Oslo peace process by inciting Hamas’s opposition to any settlement that would have led to a two-state solution. Later, they encouraged Palestinian Islamic Jihad and Hamas to carry out suicide bombings inside Israel. Beginning in 2005, Iran increased its arms shipments to Hamas, enabling the group to seize control of Gaza in 2007 and turn it into a one-party Islamist statelet. Iran also financed Hamas’s construction of tunnels in Gaza and provided the group with missile technology, funneled via the smuggling networks that Iran effectively sponsored in Egypt’s Sinai Peninsula.
Iranian support for terrorism also benefited from Hamas’s Qatari financing, which propped up the group’s tenure as the government of Gaza. This arrangement also had the tacit assent of Israeli Prime Minister Benjamin Netanyahu, because the Islamist-controlled enclave helped keep the Palestinian national movement divided and block any progress toward a two-state solution. In this respect, the backing that Hamas received from the mullahs of Tehran aligned with Netanyahu’s security policy—a fact that the pro-Palestine voices expressing solidarity with Iran might do well to reflect on.
Iran’s pro-Palestine posture was entirely instrumental. It never cared about any of the Middle East’s Muslim or Arab peoples as such. Instead, it used their causes solely as a means to exert influence and build a network of proxy forces in the region. Tehran’s realpolitik surfaced memorably in 2011 when Hamas sided with Syrian protesters against Assad; Iran was furious at this affront to its Syrian asset, and cut off Hamas’s funding until after it reestablished relations with the Damascus dictatorship.
I realize that many people in the West are furious about what Israel has been doing in Gaza since Hamas’s abhorrent attack on October 7, 2023. Israel had a right to self-defense against that incursion and the atrocities perpetrated against its citizens. Yet, in the nearly two years since then, the brutality and intensity of Israel’s military campaign in the Gaza Strip have mobilized opposition around the world. I, too, feel sadness and anger about the remorseless violence: Israel’s war in Gaza has killed members of both my immediate and my extended family.
Too often, however, I see that harsh criticism of Israel fails to pin blame on the current Netanyahu-led government, which is loathed by a large number of Israelis, and devolves into delegitimization of the Jewish state itself. This inability to distinguish between Netanyahu’s far-right coalition and other trends in Israeli politics does a profound disservice to the pro-Palestine cause because it gives credence to Tehran’s cynical posture as a Palestinian champion.
The Islamic Republic of Iran will never cease its meddling in the Palestinian issue, because Tehran needs the conflict to feed its propaganda machine. The reality is that a secure, stable, independent Palestine will remain a remote possibility as long as the Islamic Republic exists in its current form and is allowed to maintain its pro-Palestine pose. Only by calling out this evil regime and distancing from it can the pro-Palestine movement hope to be effective.
The pro-Palestine lobby would do better to take its cues from the regime’s internal opponents, the brave Iranian people who have, in successive waves of a popular movement for reform and freedom, protested their violent, repressive government. The partisans of the Palestinian cause should stop to ask themselves how else Israel’s intelligence agencies would have been able to gather the kind of information that has led to its stunning military success in the opening hours of the war. Many Iranians inside Iran today view Israel as their only hope of overthrowing the mullahs. Unfortunately, but understandably, many Iranians have come to resent the Palestinian cause—precisely because the regime has used it as a pretext to squander the country’s precious resources on its militia proxies in the name of fighting Israel.
Ultimately, the Iranian people should be the ones to decide their nation’s future. This war, which may not be truly over despite the current cease-fire, must avoid the error of mission creep by keeping its focus solely on eliminating Tehran’s nuclear program and military capacity to destabilize the region. Confronting the Iranian regime need not repeat Iraq in 2003; at present, the United States seems mindful of that risk.
What onlookers in the West should know is that the Islamic Republic is no true friend of Palestine. The misguided slogans of anti-Israel leftists and overzealous social-justice activists that echo the Iranian regime’s anti-Zionist talking points do nothing but harm the Palestinian cause. They are a form of sabotage, not solidarity. Cheering Iranian missiles as they cause death and harm in Israel is no way to advance the Palestinian people’s just aspirations for freedom, dignity, and self-determination.
81 notes
·
View notes