#Customer Data Protection
Explore tagged Tumblr posts
Text
Why POS Testing is Crucial for Flawless Retail Operations
In the fast-moving world of retail, Point of Sale (POS) systems are central to transactions, inventory management, and customer interface. If we want to keep POS systems working properly, it is important to ensure they run smoothly. A smooth POS system is necessary for a smooth customer experience and a smooth operation. Here at GQAT TECH, we are experts in POS testing so businesses can eliminate costly interruptions to their business and have more reliability with their POS. This blog will look at why POS testing is important and how it will improve your business for retail operations.
What is POS Testing?
Testing a POS enables extensive testing of the working capabilities, functionality, performance, security, and interoperability of the POS to be tested in the real world as a functional and transactional system. POS comprises hardware such as card readers, scanners, and computer devices, and POS software that processes payments and often manages inventories. POS need to be tested to process high transaction volumes, interact with other systems, and satisfy industry standard security compliance.
Why POS Testing Matters
1. Ensuring Transaction Completeness
A single mistake made within a POS can generate incorrect customer charges, inventory discrepancies, or processes that don't reach completion. One mistake can frustrate your customers, disgruntle your employees, or derail UX. Proper POS testing can ensure that your processes (whether they include cash, credit cards, mobile payments, or gift cards) will function correctly.
2. Testing system robustness
The retail environment can be harsh. Depending on the season, your POS may process thousands of transactions each day. Performance testing will verify that your POS is sufficient to process peak loads and act to mitigate crashing or performance degradation when it counts the most (e.g., during a holiday sale).
3. Protecting Customer Information
As cyber threats grow in number and sophistication, protecting customers' sensitive information, including their credit card information, is paramount. Security testing will find weaknesses in your POS systems with the goal of satisfying standards and requirements (i.e., PCI DSS) and identifying and eliminating risks to customer data exposure.
4. Ensuring integration & compatibility with other systems
A POS often resides at the intersection of multiple systems (inventory management system, CRM, accounting system, etc.). Even testing limits can identify different systems interacting with your POS, ensuring that an isolated application does not disrupt a chain that could lead to other separate systems eventually failing to receive data.
5. Increasing Customer Satisfaction
A gap in your checkout process can diminish customer satisfaction (a focus for your company). Testing usability and responsiveness will ensure your staff understands how to use the POS, as customers experience an intuitive, fast, and error-free transaction with your store.
Key Types of POS Testing
Our testing services include all types of testing you may need for your cash register and/or POS system. Here are some examples of the types of testing we provide:
Functional Testing: Testing all of the functionalities (payment processing, refunds, discounts, etc.) to make sure everything works correctly.
Performance Testing: Testing to understand your solution's reliability in peak transaction situations, or under stress.
Security Testing: Testing for gaps in security so you can protect customer data and compliance.
Compatibility Testing: Testing all the devices, operating systems, and integrations that the cash register and or POS system will have.
Usability Testing: Testing how easy it is to use for the associates and customers.
Regression Testing: Testing how the changes or new upgrades could impact existing functionality.
Why Choose GQATTech for POS Testing?
At GQATTech, we bring years of knowledge and expertise in the industry and cutting-edge testing procedures to deliver reliable, scalable, and secure POS, in-store experiences, and omnichannel solutions. Our dedicated team of testers uses both manual testing and automated testing to identify defects early, saving you time and money. Whether you are upgrading, replacing, integrating, or rolling out a new POS system, the test services that we design and conduct for you can ensure a positive experience and that the systems work as they should.
Conclusion
In our view, a comprehensive approach to POS testing is not just about checking boxes or even about each and every defect. It is really about all the components that contribute to customer confidence, operational efficiencies, or staying ahead (or even just keeping up) with the competition. From our perspective, if you can achieve true testing goals by hiring GQATTech and using our knowledge and expertise, we can assist with each of these aspirations. Visit us at gqattech.com/pos-testing/ to discover how we can assist your organization.
Are you prepared to examine what we can do for your POS, in-store experience, or omnichannel performance? We are committed to accomplishing that today! Reach out to us to discuss your testing requirements!
Visit Us: https://gqattech.com Contact Us: [email protected]
#POS Testing#Point of Sale#Retail Technology#Transaction Processing#System Reliability#Customer Experience#Security Testing#Performance Testing#Functional Testing#Compatibility Testing#Usability Testing#Regression Testing#Retail Operations#Payment Systems#PCI DSS Compliance#Inventory Management#Omnichannel Solutions#GQATTech#Software Testing#Customer Data Protection
0 notes
Text
Round UP of Weaponized Xenophobia to Try to Justify Abuse of Power: Published 4/47/25
Illegal Detention of Immigrants and Related Issues Round UP
Deportation to El Salvador and Related Issues
The Arrest of a Judge (Related)
This is terrifying.
At least a judge is intervening here:
They have started illegally deporting American citizens with no due process, as they promised to do.
They were denied access to a lawyer, presumably because a preschooler with cancer is such a danger to society that ICE had to throw out the entire constitution.
Bet they ignored all evidence, them lied when they got caught.
#Justice Deprtment#DOGE#sensitive immigration case data#immigration#Privacy#News#ECAS#Judiciary#Donald Trump#federal funds#sanctuary cities#immigration cooperation#ICE#Deportation#U.S. Citizen Children#Due Process#Rule of Law#U.S. Citizens#U.S. citizen#DHS#intellectual disabilities#Customs and Border Protection#Ableism#Cruelty is the Point#Jose Hermosillo
7 notes
·
View notes
Text
#migrants#migrants drug seizures#us border patrol#politics#crime data#fact check#project of government oversight#Customs and Border Protection (CBP) data
5 notes
·
View notes
Text
Outrage after CBP detains gay VT superintendent for hours





#cbp#customs and border protection#immigration and customs enforcement#abuse of power#data privacy#data protection#law enforcement#freedom of speech#free speech#first amendment#democrats#constitution#constitutional rights#trump deportations#donald trump#trump administration#federal government#republicans#gop#human rights#civil rights#social justice#us politics
4 notes
·
View notes
Text
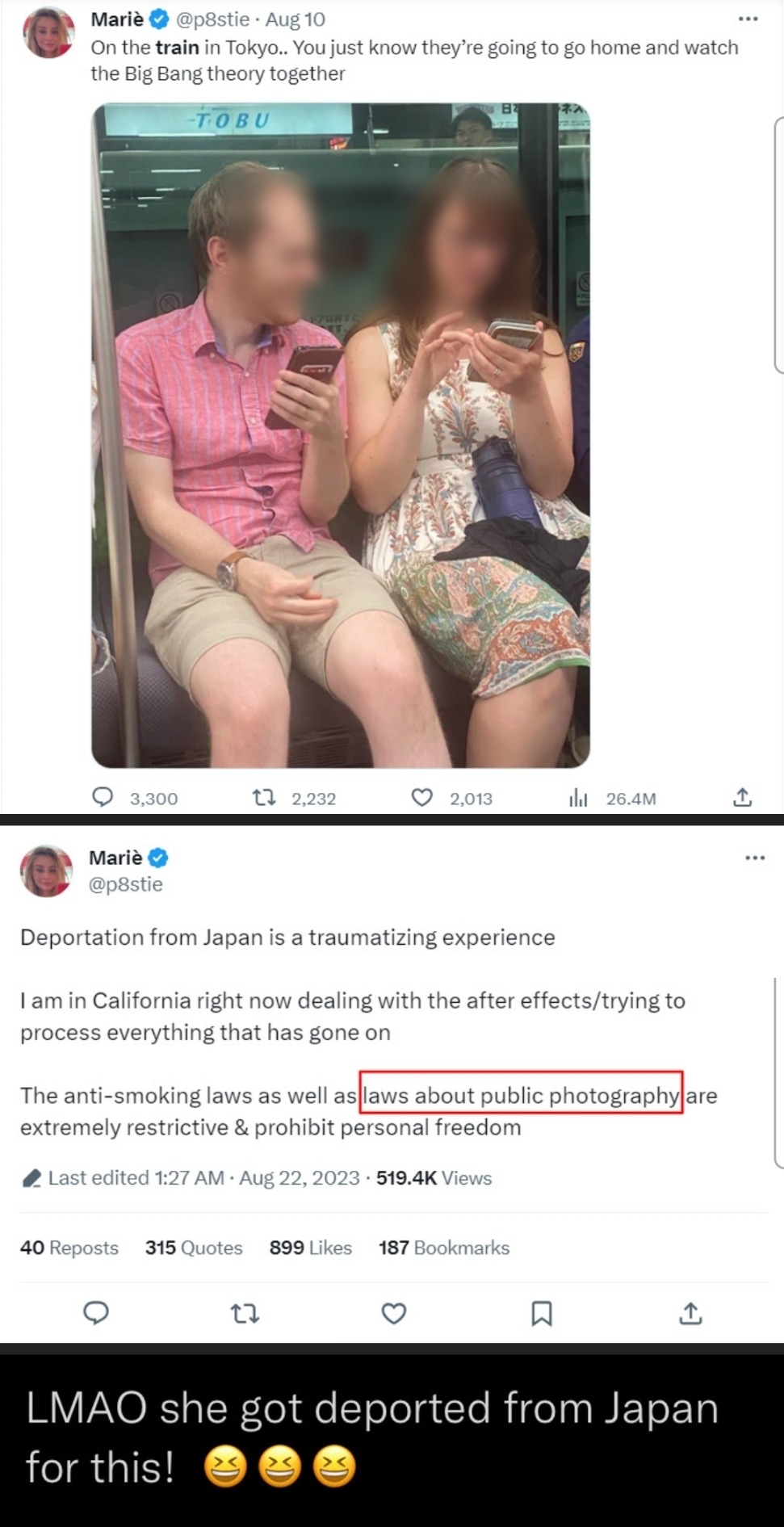
This is not from my post originally (it's a popular post from about 5 days ago and ironically spreads a picture taken without consent). I've censored the original picture because this is a jumping off point for what happened to me on Sunday while at work.
So I was at work on the shop floor when a man came in facetiming someone. He was picking up books and showing them to the lady he was facetiming, who told him that those books weren't the ones she was looking for. The man then turns to me (I was behind the tills) and asks I've I've heard of [book name]. I hadn't and explained that I'd been stocking the bookshelves earlier and hadn't come across it while doing that. He then flips his phone around so that the facetime camera is pointing at me. I freak out internally because what the hell?? I'm at work and you didn't ask me to talk to whoever it is you're talking to.
Man walks around the tills, comes up to the threshold of the till area and shoves the camera closer to my face. Because of where I was stood, I physically could not walk away from the tills because there is a wall of books in my way. I would have had to jump over the counter to leave. Honestly the whole thing made me really uncomfortable and I deeply resent people who think it's okay to take pictures of or record people in public. Ask for permission first. And if you can't, don't! Especially don't corner someone and force them to facetime a complete stranger. It's not okay, even if you think it's lighthearted.
#privacy#consent#data privacy#data protection#customer service#right to privacy#if you've also experienced something like this and feel comfortable sharing please do#I can't be the only person this has happened to
59 notes
·
View notes
Text
Elevate Client Services with Excel: Expert Tips for Financial Consultants by Grayson Garelick

Financial consultants operate in a dynamic environment where precision, efficiency, and client satisfaction are paramount. Excel, as a versatile tool, offers an array of features that can significantly enhance the services provided by financial consultants. Grayson Garelick, an accomplished financial analyst and consultant, shares invaluable Excel tips to help financial consultants elevate their client services and add tangible value.
The Role of Excel in Financial Consulting
Excel serves as the backbone of financial consulting, enabling consultants to analyze data, create models, and generate insights that drive informed decision-making. As the demands of clients become increasingly complex, mastering Excel becomes essential for financial consultants aiming to deliver exceptional services.
1. Customize Excel Templates
One of the most effective ways to streamline workflows and improve efficiency is by creating customized Excel templates tailored to specific client needs. Grayson suggests developing templates for budgeting, forecasting, and financial reporting that can be easily adapted for different clients, saving time and ensuring consistency.
2. Utilize PivotTables for Data Analysis
PivotTables are powerful tools in Excel that allow financial consultants to analyze large datasets and extract meaningful insights quickly. Grayson emphasizes the importance of mastering PivotTables for segmenting data, identifying trends, and presenting information in a clear and concise manner to clients.
3. Implement Conditional Formatting
Conditional formatting is a valuable feature in Excel that allows consultants to highlight important information and identify outliers effortlessly. By setting up conditional formatting rules, consultants can draw attention to key metrics, discrepancies, or trends, facilitating easier interpretation of data by clients.
4. Leverage Excel Add-ins
Excel offers a variety of add-ins that extend its functionality and provide additional features tailored to financial analysis and reporting. Grayson recommends exploring add-ins such as Power Query, Power Pivot, and Solver to enhance data manipulation, modeling, and optimization capabilities.
5. Automate Repetitive Tasks with Macros
Macros enable financial consultants to automate repetitive tasks and streamline workflows, saving valuable time and reducing the risk of errors. Grayson advises recording and editing macros to automate tasks such as data entry, formatting, and report generation, allowing consultants to focus on value-added activities.
6. Master Advanced Formulas and Functions
Excel's extensive library of formulas and functions offers endless possibilities for financial analysis and modeling. Grayson suggests mastering advanced formulas such as VLOOKUP, INDEX-MATCH, and array formulas to perform complex calculations, manipulate data, and create sophisticated models tailored to client needs.
7. Visualize Data with Charts and Graphs
Visualizing data is essential for conveying complex information in an easily digestible format. Excel offers a variety of chart types and customization options that enable consultants to create compelling visuals that resonate with clients. Grayson recommends experimenting with different chart styles to find the most effective way to present data and insights.
8. Collaborate and Share Workbooks Online
Excel's collaboration features enable financial consultants to work seamlessly with clients, colleagues, and stakeholders in real-time. Grayson highlights the benefits of sharing workbooks via OneDrive or SharePoint, allowing multiple users to collaborate on the same document, track changes, and maintain version control.
9. Protect Sensitive Data with Security Features
Data security is a top priority for financial consultants handling sensitive client information. Excel's built-in security features, such as password protection and encryption, help safeguard confidential data and ensure compliance with regulatory requirements. Grayson advises implementing security protocols to protect client data and maintain trust.
10. Stay Updated with Excel Training and Certification
Excel is a constantly evolving tool, with new features and updates released regularly. Grayson stresses the importance of staying updated with the latest Excel training and certification programs to enhance skills, explore new capabilities, and maintain proficiency in Excel's ever-changing landscape.
Elevating Client Services with Excel Mastery
Excel serves as a catalyst for innovation and excellence in financial consulting, empowering consultants to deliver exceptional services that add tangible value to clients. By implementing Grayson Garelick Excel tips, financial consultants can streamline workflows, enhance data analysis capabilities, and foster collaboration, ultimately driving client satisfaction and success. As financial consulting continues to evolve, mastering Excel remains a cornerstone of excellence, enabling consultants to thrive in a competitive landscape and exceed client expectations.
#Financial Consulting#grayson garelick#Customize Excel Templates#Utilize PivotTables#Implement Conditional Formatting#Leverage Excel Add-ins#Automate Repetitive Tasks with Macros#Advanced Formulas and Functions#Visualize Data with Charts and Graphs#Collaborate and Share Workbooks#Protect Sensitive Data with Security#Stay Updated with Excel Training#Elevating Client Services with Excel
3 notes
·
View notes
Text
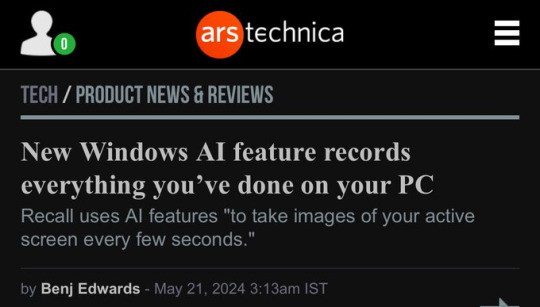
Every time I see this I'm just like... How the fuck is this GDPR compliant???
Like, if they've updated their service without telling me, a person who uses their OS on a computer that I use to look at customer data... Like, I, as the data controller, did in no fucking way give informed consent for Microsoft to handle my customer data like that...
Like, idk, someone who is more informed on GDPR, please tell me how this is fucking GDPR compliant... Like, do I have to realistically look to only looking at customer data on my Linux laptop??? (I know there are instructions above to remove it but I can't guarantee they won't sneak it in again in another update...) Because I'm liable, as the data controller, for sharing data with a third party if they have a leak... Like, if Microsoft does this, has a leak, and someone sues me, my understanding is that, under GDPR, I'm just as liable as Microsoft for the mishandling of the data...
Literal definition of spyware:
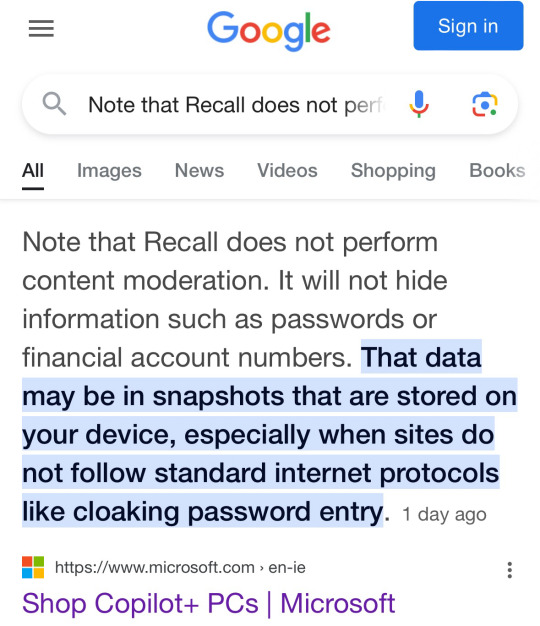
Also From Microsoft’s own FAQ: "Note that Recall does not perform content moderation. It will not hide information such as passwords or financial account numbers. 🤡
#i thankfully don't have a lot of data aside from emails because everything i sell direct is digital#but that's still customer data and still protected under gdpr
254K notes
·
View notes
Text
Video brings Awareness...
NOTE...
It is concerning to know that many new cars are sharing data with third-party companies without the knowledge of their customers. The lack of transparency in this practice is alarming, especially when personal information is being shared without consent. When connecting your phone via Bluetooth, even more information is being shared without your awareness. It is important to look into not just one site, but other companies as well, to understand the extent of data sharing. This information is not only going to third-party companies, but also to insurance companies. It is crucial for customers to be informed about how their data is being used and shared to protect their privacy.
65K notes
·
View notes
Text
What Happens To Your Phone After We Fix It?
📱 What Happens To Your Phone After We Fix It? + Insider Insights + 7 Key Transformations 📝 Introduction: More Than Just a Repair At Sydney CBD Repair Centre, we believe that mobile phone repair is not just about replacing a screen or fixing a battery. It’s about restoring your digital lifeline with precision, care, and integrity. When you walk into our shop or send your device by courier, you’re…
#90-day repair warranty#best phone repair Sydney#data protection during phone repair#genuine phone parts Sydney#mobile phone repair warranty#mobile repair aftercare#mobile repair with genuine parts#phone cleaning after repair#phone repair customer briefing#phone repair process explained#phone repair quality assurance#phone repair steps#phone repair testing checklist#post-repair diagnostics#post-repair phone care#screen replacement Sydney#sydney cbd repair centre#Sydney mobile repair expert#what happens after phone repair#what technicians do after fixing a phone
0 notes
Text
Allianz Life confirms data breach affecting majority of 1.4M US customers
MINNEOLIS — Hackers gained access to personal data on the majority of the 1.4 million customers of Allianz Life Insurance Company of North America, the company confirmed Saturday. Minneapolis-based Allianz Life, a subsidiary of Munich, Germany-based Allianz SE, said the data breach happened on July 16 when a “malicious threat actor” gained access to a third-party, cloud-based system used by the…
#1.4M#affecting#Allianz#Allianz Life Insurance#breach#confirms#Customers#Data#data breach#identity theft protection#Life#majority#personal data#social engineering technique
0 notes
Text
0 notes
Text
CIAM Solutions: Powering Secure and Seamless Digital Experiences
In today’s hyper-digital world, where businesses operate and interact with their customers through a growing number of online platforms, managing customer identities securely has become more complex—and more crucial—than ever before. As the digital ecosystem expands, so does the risk associated with data breaches, privacy violations, and poor user experiences. This is where robust Customer…
#Access Management#business#Business Intelligence#CIAM#CIAM Solutions#compliance management#customer data security#customer identity and access management#customer trust#cybersecurity#data protection#digital services#Identity Management#Information Technology#seamless authentication
0 notes
Text
Tyler Technologies: Payment Service, Credit Card Charge Inquiry
Have you Inquire about a payment service charge from your credit or debit card statement. Manage payments and accept various card types using our technology. Noticed a mysterious charge from Tyler Technologies on your credit card statement? Don’t worry—you’re not alone. Many people spot this name and wonder what it’s for. This guide breaks down what Tyler Technologies is, why they might appear on…
#agency payments#agency verification#automated billing#billing management#consumer protection#court fines#court systems#credit card charge#customer service#data analytics#data protection#digital payments#dispute charges#electronic payments#financial alerts#financial institution#financial security#fraud prevention#fraud reporting#government fees#government services#identity theft#licenses#mobile payments#online payments#payment confirmations#payment disputes#payment methods#payment platform#payment portals
1 note
·
View note
Text
Hackers Breach Wizz Air Systems, Steal 22 GB of Sensitive Customer and Staff Data — Company Remains Silent
The notorious hacker group Stormous has claimed responsibility for a massive cyberattack on Wizz Air, announcing that they have stolen approximately 22 GB of highly sensitive data, including internal company documents, staff certifications, and personal customer information. Through their official online channels, Stormous published samples of the stolen material, revealing internal reports,…
#airline accountability#airline cybersecurity#airline privacy violation#airline system hacked#aviation security breach#cyberattack Wizz Air#cybersecurity Europe#cybersecurity threat#data leak aviation#data protection aviation#data security scandal.#digital security breach#GDPR airline breach#hacked airline app#hacker attack airline#hacker group Stormous#high-profile cyberattack#personal data exposed#sensitive data theft#stolen aviation documents#Stormous group#Stormous hackers#travel data compromised#Wizz Air customer data#Wizz Air data breach#Wizz Air hack#Wizz Air incident 2025#Wizz Air security issue#Wizz Air silence#Wizz Air staff leak
0 notes
Text
IRS agrees to share tax information of undocumented immigrants with Ice | US immigration | The Guardian
#irs#internal revenue service#immigration and customs enforcement#dhs#department of homeland security#data privacy#data protection#immigrants#immigration#human rights#civil rights#social justice#us politics
0 notes
Text
Heading to the U.S.? Experts say grab a burner phone to protect your privacy at the border! Learn how to travel smart amid trade war tensions.
#Border agents#Border searches#Burner phone#Canadian travelers#Data backup#Device scrutiny#Electronic devices#Fourth Amendment#Prepaid phone#Privacy protection#trade war#Travel Advisory#Travel tips#U.S. Customs#U.S. travel
1 note
·
View note