#socialengine
Explore tagged Tumblr posts
Text
Introducing SocialEngine’s New Paid Support Plan

SocialEngine Introduces Paid Support Plan for Smoother Online Community Management
SocialEngine, a leading platform for building online communities, has announced the launch of a new Paid Support Plan. Designed to simplify community management, this plan offers a range of benefits for businesses and individuals alike.
Key Features of the Paid Support Plan:
Expert Technical Assistance: Receive prompt assistance from a team of experienced professionals for any technical issues, from troubleshooting to server management.
Priority Support: Enjoy faster response times and reduced wait times for all your support requests.
Extended Support Coverage: Utilize the new Support Ticket feature within SocialEngine to easily manage and resolve user inquiries.
Early Access to Updates: Gain early access to bug fixes and free upgrades, ensuring your community platform remains up-to-date and secure.
Benefits of Choosing the Paid Support Plan:
Affordability: The plan is competitively priced, making it accessible to businesses of all sizes.
Peace of Mind: Focus on growing your community while the SocialEngine team handles the technical aspects.
Reliability: Benefit from the expertise and experience of a trusted partner in the online community space.
To learn more and sign up for the Paid Support Plan, visit the SocialEngine plan page.
This summary highlights the key features and benefits of the new Paid Support Plan, making it easy for readers to understand how it can help them manage their online communities more effectively.
For more details, kindly visit:- Introducing SocialEngine’s New Paid Support Plan: Ensuring Smooth Sailing for Your Online Community
Mail us at [email protected] to schedule a quote and become the owner of your best social network site.
0 notes
Text
Top 15 Features a Forum Software Must Have for Building Online Community in 2025

Building a thriving online community requires the right platform. This blog outlines 15 essential features for successful forum software, including user registration, search functionality, customization, ease of use, chat, notifications, forums, moderation, hashtags, social media integration, privacy, advertising, mobile support, multilingual support, and scalability.
Key takeaways:
User-centric design: Easy registration, personalized profiles, and intuitive navigation are crucial for attracting and retaining members.
Robust functionality: Search, forums, and sub-forums enable easy content discovery and organized discussions.
Engaging features: Chat, live streaming, notifications, and social media integration foster interaction and keep members connected.
Safety and security: Strong moderation and robust privacy measures build trust and ensure a positive community experience.
Scalability and performance: The platform should handle growing membership and maintain a smooth user experience.
The blog highlights SocialEngine as a leading platform that encompasses all these features.
It emphasizes SocialEngine's ability to create a customized, engaging, and scalable online community with features like advanced customization, mobile apps, and multilingual support.
This summary aims to provide a concise and informative overview of the blog's key points, making it easier for readers to understand its core message.
For more details, kindly visit:- Top 15 Features a Forum Software Must Have for Building Online Community in 2025
Mail us at [email protected] to schedule a quote and become the owner of your best social network site.
#Forum Software#Online Community Software#Social Networking Platform#Online Community Platform#Community forum software#SocialEngine
0 notes
Text
SocialEngine Development
SocialEngine stands as a robust social network development platform capable of crafting tailored social networks, online communities, and social media websites. Businesses have increasingly adopted it over the years to create web solutions that bridge connections between individuals, brands, and each other. As a leading social network development company, we offer highly personalized services designed to propel our clients' businesses to new heights.

#SocialEngine#SocialEngineDevelopment#PHP#WebDevelopment#OpenSource#SocialNetworking#WebApp#WebDesign#BackendDevelopment
0 notes
Text
Surge in Credential Compromises Driven by Social Engineering Attacks

A staggering 92% of organizations experienced an average of six credential compromises caused by email-based social engineering attacks in 2023, according to a new report by cybersecurity firm Barracuda. These insidious tactics, which prey on human vulnerabilities, continued dominating the threat landscape, with scamming and phishing accounting for 86% of all social engineering attacks last year.
Emerging Trends in Social Engineering Techniques
Conversation Hijacking: A Sophisticated Impersonation Ploy While conversation hijacking, a technique where attackers compromise business accounts through phishing and monitor communications to craft convincing messages, accounted for only 0.5% of social engineering attacks in 2023, it represents a staggering 70% increase compared to the previous year. This sophisticated tactic allows cybercriminals to gather sensitive information about deals, payment procedures, and other operational details, impersonating trusted entities and tricking victims into authorizing fraudulent transactions or updating payment information. Business Email Compromise (BEC): A Persistent Threat Business email compromise (BEC) attacks, where hackers impersonate executives to trick employees into transferring funds or sensitive data, remained a prominent threat in 2023. These attacks accounted for 10.6% of all social engineering incidents, up from 8% in 2022, highlighting the persistent allure of this lucrative technique for cyber criminals. Extortion: Holding Data Hostage for Ransom Another alarming trend involved extortion attacks, where cybercriminals threaten to expose sensitive or embarrassing content to their victims' contacts unless a ransom is paid. These attacks accounted for 2.7% of the total social engineering attacks in 2023, underscoring the growing prevalence of this nefarious tactic.
Exploiting Legitimate Services for Malicious Gain
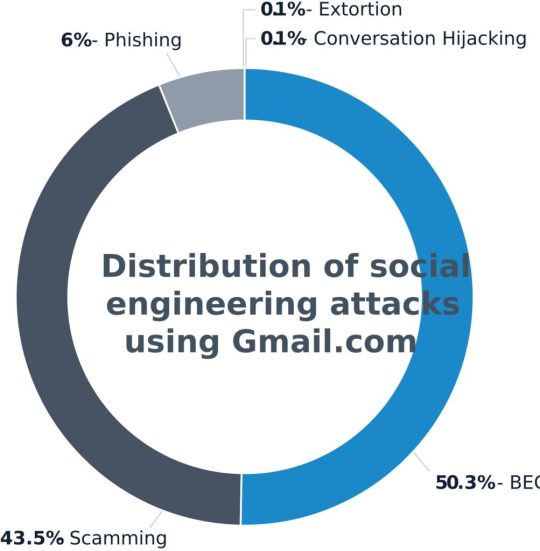
The report also sheds light on the evolving use of legitimate services by attackers to target employees through social engineering techniques. Gmail emerged as the most commonly abused email domain, accounting for a staggering 22% of all attacks last year. Other popular free webmail services exploited by hackers included Outlook (2%), Hotmail (1%), iCloud (1%), and Mail.com (1%), while all other domains accounted for 73% of attacks. Notably, attacks originating from Gmail domains were heavily skewed towards BEC, with over 50% of such attacks falling into this category, followed by scamming at 43%.
Malicious URL Obfuscation through Shortening Services Cybercriminals also demonstrated a growing reliance on popular commercial URL shortening services to embed malicious links in phishing emails, effectively disguising the true nature and destination of these links. The most widely used shortening service in 2023 was bit.ly, leveraged in nearly 40% of attacks involving shortened URLs. X's (formerly Twitter) shortening service came in second, utilized in 16% of such attacks, marking a significant shift from 2020 when it accounted for around two-thirds (64%) of these attacks.
The Rise of QR Code Phishing Attacks
Another notable development in the realm of social engineering was the significant rise in QR code phishing attacks towards the end of 2023. Approximately 5% of mailboxes were targeted with these attacks in the final quarter of the year, a concerning trend highlighting cybercriminals' ever-evolving tactics. In these attacks, cybercriminals embed QR codes in phishing emails, prompting unsuspecting users to scan the code and visit a fake page masquerading as a trusted service or application. These pages are designed to trick users into downloading malware or entering their login credentials, effectively compromising their accounts and data. Evading Traditional Security Measures QR code attacks pose a unique challenge as they circumvent traditional email filtering methods, which rely on detecting embedded links or malicious attachments. Furthermore, these attacks leverage personal devices, such as phones or tablets, which are often not protected by corporate security software, providing cybercriminals with a potential entry point into organizational networks and systems. Read the full article
4 notes
·
View notes
Text

Die Zwei-Faktor-Authentifizierung aushebeln
Schwachstelle Mensch
Jahrelang wurde uns versichert, dass wir mit einer Zwei-Faktor-Authentifizierung (2FA) sicher(er) seien. Allen voran die Banken haben solche Verfahren einführen müssen. Mit der EU Banken-Richtlinie PSD2 wurden sie Standard. Bereits damals hatten wir kritisiert, das das sinnvolle Verfahren durch die Abschaffung des "2. Wegs" wieder amputiert wird. So waren für die 2. Authentifizierung anfangs SMS o.ä. üblich, inzwischen laufen oft beide Wege wieder über ein Gerät - meist das Smartphone.
Nun hat sich herausgestellt, dass beim Kampf der Cybersicherheit gegen die Hacker letztere am Aufholen sind. In 2 Artikeln beschreibt Heise.de die Vorgehensweise der Hacker. Eigentlich ist alles beim alten geblieben - beim Pishing - nur der Aufwand, den die Hacker betreiben müssen, ist größer geworden.
Social Engineering statt neuer Technik
Weiterhin ist die Taktik der Hacker das Opfer solange zu verwirren, bis es Fehler macht. Die Tricks sind
dein Handy braucht ein Update,
dein Handy ist defekt,
ein Systemfehler ist aufgetreten, drücken Sie hier oder da,
u.v.m. ...
MFA-Fatigue-Angriff
Deshalb kommt ein MFA-Fatigue Angriff meist abends oder am Wochenende, wenn man ermüdet ist und eine technische Hilfe oder KollegInnen nicht erreichbar sind. Dann wird man mit "unlogischem Verhalten" der Technik verwirrt, solange bis man seine Passworte an der falschen Stelle eingibt. Eigentlich dürfte man das nicht tun, schreibt PCspezialist.de, denn:
Eine Authentifizierungsanfrage wird nur dann abgesendet, wenn Sie zuvor das korrekte Passwort in ein System eingegeben haben. Denn genau das ist ja der Sinn der Multi-Faktor-Authentifizierung – der zusätzliche Schutz durch eine zusätzliche Sicherheitsabfrage.
Ein Einmal-Passwort (OTP) kann also vom System nie verlangt, werden, wenn man sich nicht vorher dort einloggen wollte. Passiert dies doch, so ist es mit Sicherheit ein Cyberangriff. Die Angreifer versuchen ihre Opfer jedoch durch wiederholte Abfragen und/oder Abweisungen "des Systems" zu verwirren. So eine Abfrage kann auch ein Anruf "einer technischen Abteilung" sein, die einen angeblichen "Systemfehler" zurücksetzen müsse. Die Schwachstelle der Zwei-Faktor-Authentifizierung (2FA) bleibt der Mensch.
Mehr dazu bei https://www.heise.de/ratgeber/Ausprobiert-Phishing-trotz-Zwei-Faktor-Authentifizierung-8981919.html und https://www.heise.de/ratgeber/IT-Security-Wie-Angreifer-die-Zwei-Faktor-Authentifizierung-aushebeln-8973846.html und https://www.pcspezialist.de/blog/2022/11/28/mfa-fatigue-angriff/
Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3u1 Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/8395-20230510-die-zwei-faktor-authentifizierung-aushebeln.htm
#Schwachstelle#Mensch#Zwei-Faktor-Authentifizierung#2FA#PSD2#SocialEngineering#MFA-Fatigue-Angriff#Verbraucherdatenschutz#Datenschutz#Datensicherheit#Smartphone#Handy#IMSI-Catcher#Cyberwar#Hacking
2 notes
·
View notes
Text
🔍 Manipulation Techniques: Inform & Protect Yourself 🤯

From wartime propaganda to social media algorithms, manipulation techniques have evolved to shape our thoughts and decisions—often without us realizing it. Learn how psychological tricks, digital deception, and AI-driven persuasion influence society today.
📰 Read our latest article and stay informed! https://thinquer.com/educational/the-evolution-of-manipulation-techniques-inform-protect-yourself/
💬 What are your thoughts on modern manipulation? Drop a comment!
#Manipulation#Psychology#MindControl#SocialEngineering#Propaganda#MediaManipulation#DigitalDeception#PsychologicalWarfare#InfluenceTechniques#MassPersuasion#Deepfake#FakeNews#AIManipulation#BehavioralScience#SocialMediaManipulation#CognitiveBias#PoliticalInfluence#Misinformation#AlgorithmicControl#Neuromarketing#PsychOps#StayInformed#CriticalThinking#TruthMatters#InformationWarfare
0 notes
Text
The wave of constant scam DMs asking for money or whatever for X conflict or X disease is exhausting.
Theres genuinely people who need help and we have these scumbags impersonating people in need blowing up our DMs for what is likely a scam and a social engineering attack meant to affect our emotions and manipulate us into giving the scammer money.
Only donate to verified sources. I'm sure everyone is likely getting this frustrating spam. Dont even read the spam, its meant to make you feel bad/ empathetic buts thats the trap (because we are only humans).
I wish all scammers profiteering off desperation, misery, disease and conflict a very bad time. May a fowl curse and misfortune befall them.
1 note
·
View note
Text

"Human beings are fundamentally story people. They feed on narrative. They understand reality via narrative. It’s hardwired in them. If they can’t comprehend something, they invent a spirit, a ghost, an angel, a demon, or, above all, a God to account for it. So, rather than an abstract, scientific and philosophical account of how we came to exist, most of us prefer something that says: Who made us? God made us. He created the world in six days, and on the seventh he rested. So we too should rest on the seventh day. And thus we have a nice little narrative. Nothing complex. Nothing that stretches the brain cells. Nothing that baffles us or makes us fearful. Everything is OK. God is on top of it all. God is looking after us.
All systems of mind control are based on the control of the narrative. The Old World Order have hitherto controlled schools, religions, governments, corporations, advertising and the media to ensure absolute control of what “story” is given to the public. Every day you are fed the controlling narrative of the Elite. You accept it totally, even when you think you aren’t. The moment you realise you have escaped is one of the most disturbing of your life. Why? Because you no longer believe a single thing that anyone in authority says to you. NOTHING AT ALL. You see right through all the stories they spin. You understand the “code” of their narrative. You see how everything is designed to forward their agenda and promote their wealth and power. What is “good”? Answer – everything associated with the Elite. What is “bad”? – everything else. You too can be good if you do everything the Elite tell you to do. If you oppose them then you are bad, a criminal, an enemy of the state.
All other narratives are marginalized, attacked, discredited or simply ignored. If necessary, the full weight of the propaganda machine is brought against them. These counter narratives are never given a chance to flourish. So they go underground. Or they suffer a worse fate – they are sanitised and commercialised and they become part of the narrative of the Elite."
~ Michael Faust, 'Abraxas: Beyond This and Evil'
#TruthSeries#KnowingVsBelieving#SociologicalDeconstruction#GovernMent#MindControl#PsyOps#CoOp#PsychologicalOperation#ControlledOpposition#ReversePsychology#VeryMachiavellian#GodSaveTheSheople#IlluminismContraDiscordianism#SocialEngineering#AbraxasBeyondGoodAndEvil
1 note
·
View note
Text
Celebrating New Year with SocialEngine’s Vision for 2025

SocialEngine is celebrating a successful 2024 with the release of SocialEngine v7, new themes, and exciting features like login with Telegram and mobile OTP. To show their appreciation, they're extending their Christmas sale with code NewYear2025 (valid until January 5th, 2025).
2024 Highlights:
Launched SocialEngine v7 with numerous improvements.
Introduced new themes inspired by popular social media platforms.
Added features like mobile OTP login, login with multiple platforms, and Stripe integration.
Looking Ahead to 2025:
SocialEngine is committed to constant development.
Expect new plugins, themes, and features for greater customization.
The team is exploring Artificial Intelligence (AI) integration for future updates.
Mobile app enhancements will make user engagement even easier.
SocialEngine invites you to join them in building the future of online communities. They offer advanced features and mobile-friendly solutions to help your community thrive in 2025!
For more details, kindly visit:- Celebrating New Year with SocialEngine’s Vision for 2025
Mail us at [email protected] to schedule a quote and become the owner of your best social network site.
0 notes
Text
Excited For Christmas Discounts! Flat 25% Christmas Sale is On!

SocialEngine is trying to spread Christmas cheer with an interesting promo: 25 % off all products using code Christmas2024. This is a great moment to move to the newest version of SocialEngine software, the v7.
What stands out about SocialEngine software version 7?
Reduced Waiting Time: Improved web networks now function via AJAX interfaces:url shortening and ajax based websites in enhancement of menu systems.
New Revenue Sources: The brand new Wallet Feature enables users to pay within your very own users, which creates more opportunities for income.
Better Activity Feed: Add a sticker, send a GIF, advertise posts to sell something or tell where the thing is located, and use more check-ins to enhance your active community.
Grab this Christmas sale while it lasts! Switch to SocialEngine v7 and harness the advantages of this diverse and function-rich platform for your virtual community.
The offer ends on 27th December 2024.
For more details, kindly visit:- The Wait Is Over SocialEngine 7 is Here !! The Ultimate Social Network Platform
Mail us at [email protected] to schedule a quote and become the owner of your best social network site.
#merry christmas 2k24#merry christmas 2024#socialengine v7#social network platform#christmas sale#christmas2024
0 notes
Text
#RedKercheifRevolution in a fear based societal structure and foundations of narcissists, sociopaths and highly functional psychopaths who organise, control, orchestrate, intimidate, and manipulate innocent unaware people it is of course legal to reproduce and multiply with as many children as possible because they always use us for slavery, it's of course okay to reproduce before even we're sincerely judged on whether if any of the couples planted a tree saplings before they said “i love you to each other” or that tree saplings grow, took care of it atleast half way through, and saw not own a show dog as a pet but actually adopt a indigenous animals as true companionship s for life and showed it any compassion at all, yes, it's okay deceive each other's of the ideology of love set by corrupt psychologists, neuropsychologists and behavioural biologists who use entertainment channels to socially engineer the idea of all human relationships, love, to what masculinity is or femininity is it's okay to keep on multiplying like cancer cells instead of light in the darkest corners of our undressed desires of the heart, it's so alright to pick up that mask 🎭 that everyone wears and pretends like there's no dead bodies right in their closets.
0 notes
Text
Why Is SEO Important For Your Social Networking Website And How You Improve It?

SEO, or Search Engine Optimization, is crucial for any website's success. It helps your website rank higher in search engine results, attracting more organic traffic. By improving your website's visibility, you can increase credibility, build trust, and enhance user experience.
SocialEngine, a popular social network script, offers several SEO benefits:
Customization: Tailor your blog posts with SEO-friendly titles, descriptions, and URLs.
Built-in SEO Features: Easily implement best SEO practices without technical expertise.
Social Sharing: Encourage social media sharing to boost visibility and SEO.
Community Engagement: Foster active discussions and interactions to improve search engine rankings.
Regular Content Updates: Keep your website fresh and relevant, which search engines love.
While SocialEngine provides a solid foundation for SEO, it's essential to create high-quality, unique content that addresses your target audience's needs. Additionally, optimizing your website's overall structure, loading speed, and user experience is crucial for long-term SEO success.
For more details, kindly visit:- Why Is SEO Important For Your Social Networking Website And How You Improve It?
Mail us at [email protected] to schedule a quote and become the owner of your best social network site.
0 notes
Video
youtube
Phishing and Social Engineering
#youtube#Security phishing whaling smishing vishng SocialEngineering SpearPhishing cyber lecturer presenter
0 notes
Link
In today's hyper-connected world, our smartphones hold a treasure trove of personal information – from banking details and private photos to work documents and social media accounts. This makes them prime targets for cybercriminals looking to steal data, install malware, or commit financial fraud. The good news is, that you can significantly reduce the risk of your smartphone being compromised by following some basic security best practices. This article dives deep into the National Security Agency's (NSA) "Mobile Device Best Practices" guide, outlining essential steps to secure your iOS or Android device. Tips to Secure Your Smartphone Daily Habits for Smartphone Security Here are some easy-to-implement daily practices that can significantly enhance your smartphone security: Strong Passwords and Screen Locks: Ditch the simple four-digit PIN and opt for a strong, six-digit PIN or a complex alphanumeric password for your screen lock. Additionally, enable the feature that wipes your device data after 10 unsuccessful unlock attempts. This acts as a deterrent against brute-force attacks. Bluetooth: Use Wisely: Bluetooth is a convenient way to connect to headphones and speakers, but leave it disabled when not in use. This minimizes the attack surface for hackers who might exploit Bluetooth vulnerabilities. Beware of Public Wi-Fi: Public Wi-Fi networks are notoriously insecure. Avoid accessing sensitive information like bank accounts or online banking apps while connected to public Wi-Fi. If necessary, consider using a Virtual Private Network (VPN) to encrypt your internet traffic. Maintain Physical Control: Your smartphone is a personal device. Keep it with you at all times and avoid leaving it unattended in public places. This simple precaution can prevent physical theft, which can be a gateway to further security breaches. App Management: Keeping Your Digital Ecosystem Safe The apps you install on your phone can be a double-edged sword. While they offer a plethora of functionalities, they can also pose security risks if not managed properly. Here's how to maintain a secure app environment: Download from Official Sources: Only install apps from official app stores like the App Store or Google Play Store. These stores have vetting procedures in place to minimize the risk of malware distribution. Avoid downloading apps from untrusted third-party sources. Essential Apps Only: Don't clutter your phone with unnecessary apps. Stick to installing only the apps you genuinely need and use regularly. The fewer apps you have, the smaller the attack surface for potential vulnerabilities. App Permissions: Be mindful of the permissions you grant to apps. An app requesting access to your location or microphone when it doesn't seem necessary might be a red flag. Only grant permissions that are essential for the app's functionality. Close Unused Apps: Many apps run in the background even when not actively in use. This can drain battery life and potentially expose vulnerabilities. Make it a habit to close apps you're not actively using to tighten your phone's security. Staying Updated: Software and Apps Software updates often contain critical security patches that address vulnerabilities exploited by cybercriminals. Here's why keeping your software and apps updated is crucial: Install Updates Promptly: Whenever software updates are available for your phone's operating system or apps, install them promptly. Don't procrastinate – timely updates are essential for maintaining a secure mobile environment. Automatic Updates: Consider enabling automatic updates for your phone's operating system and apps whenever possible. This ensures you're always protected with the latest security patches. Be Wary of Social Engineering and Phishing Attacks Cybercriminals often rely on social engineering tactics to trick users into compromising their own devices. Here's how to stay vigilant against such attempts: Think Before You Click: Never open suspicious email attachments or links, even if they appear to come from a trusted source. Phishing emails often try to trick you into clicking on malicious links that can download malware onto your device. Beware of Pop-Ups: Unexpected pop-ups on your phone can be a sign of a malicious website or app. Don't interact with them. Instead, force close the browser or app immediately. Advanced Security Measures For users who want to take their smartphone security to the next level, here are some additional tips: No Jailbreaking or Rooting: Jailbreaking an iPhone or rooting an Android phone gives you more control over your device, but it can also bypass security measures built into the operating system. These modifications can make your phone more vulnerable to attacks. Unless you're a highly technical user, avoid jailbreaking or rooting. Frequently Asked Questions Q: Is a fingerprint or facial recognition unlock secure enough for my phone? A: While fingerprint and facial recognition unlock features offer convenience, they might not be as secure as a strong PIN or password. Consider using a PIN or password in conjunction with fingerprint or facial recognition for an extra layer of security. Q: What if I accidentally download a malicious app? A: Most reputable antivirus and security apps can scan your phone for malware. Consider installing a reputable security app from a trusted source and running regular scans. Q: I'm not very tech-savvy. Can I still secure my phone? A: Absolutely! Many of the tips in this article, like using strong passwords and keeping your software updated, are easy to implement regardless of technical expertise.
#appsecurity#charginghabits#Cyberattacks#databackups#datatheft#jailbreaking#locationservices#NSAmobilesecurityguide#phishingattacks#publicWiFi#rooting#smartphonesecurity#socialengineering#softwareupdates#strongpasswords#TipstoSecureYourSmartphone
0 notes
Text








"Remain alert! To protect your digital environment, be aware of the various hazards lurking in IT security, from malware to phishing. Stay Safe and Protect Cyberspace.
For more information visit www.certera.co
#MalwareThreats#PhishingAttacks#Ransomware#DDoS#DataBreach#InsiderThreats#SocialEngineering#ZeroDayExploits
0 notes
Text
Crossover Episode for both The Causey Consulting Podcast and con-sara-cy theories.
I recently read Why England Slept and it sounds like it could be a playbook for how the public is led into conflicts, changes, social engineering, etc.
0 notes