#phishing
Explore tagged Tumblr posts
Text
“Rayban charity glasses event” is a scam don’t click any link in a post that says that.
Old tumblr users remember this scam back when it first went out.
(Posted March 28th, 2025)
48K notes
·
View notes
Text
I saw a post before about how hackers are now feeding Google false phone numbers for major companies so that the AI Overview will suggest scam phone numbers, but in case you haven't heard,
PLEASE don't call ANY phone number recommended by AI Overview
unless you can follow a link back to the OFFICIAL website and verify that that number comes from the OFFICIAL domain.
My friend just got scammed by calling a phone number that was SUPPOSED to be a number for Microsoft tech support according to the AI Overview
It was not, in fact, Microsoft. It was a scammer. Don't fall victim to these scams. Don't trust AI generated phone numbers ever.
#this has been... a psa#psa#ai#anti ai#ai overview#scam#scammers#scam warning#online scams#anya rambles#scam alert#phishing#phishing attempt#ai generated#artificial intelligence#chatgpt#technology#ai is a plague#google ai#internet#warning#important psa#internet safety#safety#security#protection#online security#important info
3K notes
·
View notes
Text
I just got another one of those phishing emails where it pretends to be a confirmation of a subscription you never signed up for and tries to trick you into providing personally identifying information for "confirmation purposes" when you attempt to cancel, but:
a. this one is for a weekly grocery delivery service, of all things; and
b. the fake shopping list contains nothing but ham.
I have been fraudulently subscribed to ham.
10K notes
·
View notes
Text
How I got scammed

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/02/05/cyber-dunning-kruger/#swiss-cheese-security

I wuz robbed.
More specifically, I was tricked by a phone-phisher pretending to be from my bank, and he convinced me to hand over my credit-card number, then did $8,000+ worth of fraud with it before I figured out what happened. And then he tried to do it again, a week later!
Here's what happened. Over the Christmas holiday, I traveled to New Orleans. The day we landed, I hit a Chase ATM in the French Quarter for some cash, but the machine declined the transaction. Later in the day, we passed a little credit-union's ATM and I used that one instead (I bank with a one-branch credit union and generally there's no fee to use another CU's ATM).
A couple days later, I got a call from my credit union. It was a weekend, during the holiday, and the guy who called was obviously working for my little CU's after-hours fraud contractor. I'd dealt with these folks before – they service a ton of little credit unions, and generally the call quality isn't great and the staff will often make mistakes like mispronouncing my credit union's name.
That's what happened here – the guy was on a terrible VOIP line and I had to ask him to readjust his mic before I could even understand him. He mispronounced my bank's name and then asked if I'd attempted to spend $1,000 at an Apple Store in NYC that day. No, I said, and groaned inwardly. What a pain in the ass. Obviously, I'd had my ATM card skimmed – either at the Chase ATM (maybe that was why the transaction failed), or at the other credit union's ATM (it had been a very cheap looking system).
I told the guy to block my card and we started going through the tedious business of running through recent transactions, verifying my identity, and so on. It dragged on and on. These were my last hours in New Orleans, and I'd left my family at home and gone out to see some of the pre-Mardi Gras krewe celebrations and get a muffalata, and I could tell that I was going to run out of time before I finished talking to this guy.
"Look," I said, "you've got all my details, you've frozen the card. I gotta go home and meet my family and head to the airport. I'll call you back on the after-hours number once I'm through security, all right?"
He was frustrated, but that was his problem. I hung up, got my sandwich, went to the airport, and we checked in. It was total chaos: an Alaska Air 737 Max had just lost its door-plug in mid-air and every Max in every airline's fleet had been grounded, so the check in was crammed with people trying to rebook. We got through to the gate and I sat down to call the CU's after-hours line. The person on the other end told me that she could only handle lost and stolen cards, not fraud, and given that I'd already frozen the card, I should just drop by the branch on Monday to get a new card.
We flew home, and later the next day, I logged into my account and made a list of all the fraudulent transactions and printed them out, and on Monday morning, I drove to the bank to deal with all the paperwork. The folks at the CU were even more pissed than I was. The fraud that run up to more than $8,000, and if Visa refused to take it out of the merchants where the card had been used, my little credit union would have to eat the loss.
I agreed and commiserated. I also pointed out that their outsource, after-hours fraud center bore some blame here: I'd canceled the card on Saturday but most of the fraud had taken place on Sunday. Something had gone wrong.
One cool thing about banking at a tiny credit-union is that you end up talking to people who have actual authority, responsibility and agency. It turned out the the woman who was processing my fraud paperwork was a VP, and she decided to look into it. A few minutes later she came back and told me that the fraud center had no record of having called me on Saturday.
"That was the fraudster," she said.
Oh, shit. I frantically rewound my conversation, trying to figure out if this could possibly be true. I hadn't given him anything apart from some very anodyne info, like what city I live in (which is in my Wikipedia entry), my date of birth (ditto), and the last four digits of my card.
Wait a sec.
He hadn't asked for the last four digits. He'd asked for the last seven digits. At the time, I'd found that very frustrating, but now – "The first nine digits are the same for every card you issue, right?" I asked the VP.
I'd given him my entire card number.
Goddammit.
The thing is, I know a lot about fraud. I'm writing an entire series of novels about this kind of scam:
https://us.macmillan.com/books/9781250865878/thebezzle
And most summers, I go to Defcon, and I always go to the "social engineering" competitions where an audience listens as a hacker in a soundproof booth cold-calls merchants (with the owner's permission) and tries to con whoever answers the phone into giving up important information.
But I'd been conned.
Now look, I knew I could be conned. I'd been conned before, 13 years ago, by a Twitter worm that successfully phished out of my password via DM:
https://locusmag.com/2010/05/cory-doctorow-persistence-pays-parasites/
That scam had required a miracle of timing. It started the day before, when I'd reset my phone to factory defaults and reinstalled all my apps. That same day, I'd published two big online features that a lot of people were talking about. The next morning, we were late getting out of the house, so by the time my wife and I dropped the kid at daycare and went to the coffee shop, it had a long line. Rather than wait in line with me, my wife sat down to read a newspaper, and so I pulled out my phone and found a Twitter DM from a friend asking "is this you?" with a URL.
Assuming this was something to do with those articles I'd published the day before, I clicked the link and got prompted for my Twitter login again. This had been happening all day because I'd done that mobile reinstall the day before and all my stored passwords had been wiped. I entered it but the page timed out. By that time, the coffees were ready. We sat and chatted for a bit, then went our own ways.
I was on my way to the office when I checked my phone again. I had a whole string of DMs from other friends. Each one read "is this you?" and had a URL.
Oh, shit, I'd been phished.
If I hadn't reinstalled my mobile OS the day before. If I hadn't published a pair of big articles the day before. If we hadn't been late getting out the door. If we had been a little more late getting out the door (so that I'd have seen the multiple DMs, which would have tipped me off).
There's a name for this in security circles: "Swiss-cheese security." Imagine multiple slices of Swiss cheese all stacked up, the holes in one slice blocked by the slice below it. All the slices move around and every now and again, a hole opens up that goes all the way through the stack. Zap!
The fraudster who tricked me out of my credit card number had Swiss cheese security on his side. Yes, he spoofed my bank's caller ID, but that wouldn't have been enough to fool me if I hadn't been on vacation, having just used a pair of dodgy ATMs, in a hurry and distracted. If the 737 Max disaster hadn't happened that day and I'd had more time at the gate, I'd have called my bank back. If my bank didn't use a slightly crappy outsource/out-of-hours fraud center that I'd already had sub-par experiences with. If, if, if.
The next Friday night, at 5:30PM, the fraudster called me back, pretending to be the bank's after-hours center. He told me my card had been compromised again. But: I hadn't removed my card from my wallet since I'd had it replaced. Also, it was half an hour after the bank closed for the long weekend, a very fraud-friendly time. And when I told him I'd call him back and asked for the after-hours fraud number, he got very threatening and warned me that because I'd now been notified about the fraud that any losses the bank suffered after I hung up the phone without completing the fraud protocol would be billed to me. I hung up on him. He called me back immediately. I hung up on him again and put my phone into do-not-disturb.
The following Tuesday, I called my bank and spoke to their head of risk-management. I went through everything I'd figured out about the fraudsters, and she told me that credit unions across America were being hit by this scam, by fraudsters who somehow knew CU customers' phone numbers and names, and which CU they banked at. This was key: my phone number is a reasonably well-kept secret. You can get it by spending money with Equifax or another nonconsensual doxing giant, but you can't just google it or get it at any of the free services. The fact that the fraudsters knew where I banked, knew my name, and had my phone number had really caused me to let down my guard.
The risk management person and I talked about how the credit union could mitigate this attack: for example, by better-training the after-hours card-loss staff to be on the alert for calls from people who had been contacted about supposed card fraud. We also went through the confusing phone-menu that had funneled me to the wrong department when I called in, and worked through alternate wording for the menu system that would be clearer (this is the best part about banking with a small CU – you can talk directly to the responsible person and have a productive discussion!). I even convinced her to buy a ticket to next summer's Defcon to attend the social engineering competitions.
There's a leak somewhere in the CU systems' supply chain. Maybe it's Zelle, or the small number of corresponding banks that CUs rely on for SWIFT transaction forwarding. Maybe it's even those after-hours fraud/card-loss centers. But all across the USA, CU customers are getting calls with spoofed caller IDs from fraudsters who know their registered phone numbers and where they bank.
I've been mulling this over for most of a month now, and one thing has really been eating at me: the way that AI is going to make this kind of problem much worse.
Not because AI is going to commit fraud, though.
One of the truest things I know about AI is: "we're nowhere near a place where bots can steal your job, we're certainly at the point where your boss can be suckered into firing you and replacing you with a bot that fails at doing your job":
https://pluralistic.net/2024/01/15/passive-income-brainworms/#four-hour-work-week
I trusted this fraudster specifically because I knew that the outsource, out-of-hours contractors my bank uses have crummy headsets, don't know how to pronounce my bank's name, and have long-ass, tedious, and pointless standardized questionnaires they run through when taking fraud reports. All of this created cover for the fraudster, whose plausibility was enhanced by the rough edges in his pitch - they didn't raise red flags.
As this kind of fraud reporting and fraud contacting is increasingly outsourced to AI, bank customers will be conditioned to dealing with semi-automated systems that make stupid mistakes, force you to repeat yourself, ask you questions they should already know the answers to, and so on. In other words, AI will groom bank customers to be phishing victims.
This is a mistake the finance sector keeps making. 15 years ago, Ben Laurie excoriated the UK banks for their "Verified By Visa" system, which validated credit card transactions by taking users to a third party site and requiring them to re-enter parts of their password there:
https://web.archive.org/web/20090331094020/http://www.links.org/?p=591
This is exactly how a phishing attack works. As Laurie pointed out, this was the banks training their customers to be phished.
I came close to getting phished again today, as it happens. I got back from Berlin on Friday and my suitcase was damaged in transit. I've been dealing with the airline, which means I've really been dealing with their third-party, outsource luggage-damage service. They have a terrible website, their emails are incoherent, and they officiously demand the same information over and over again.
This morning, I got a scam email asking me for more information to complete my damaged luggage claim. It was a terrible email, from a noreply@ email address, and it was vague, officious, and dishearteningly bureaucratic. For just a moment, my finger hovered over the phishing link, and then I looked a little closer.
On any other day, it wouldn't have had a chance. Today – right after I had my luggage wrecked, while I'm still jetlagged, and after days of dealing with my airline's terrible outsource partner – it almost worked.
So much fraud is a Swiss-cheese attack, and while companies can't close all the holes, they can stop creating new ones.
Meanwhile, I'll continue to post about it whenever I get scammed. I find the inner workings of scams to be fascinating, and it's also important to remind people that everyone is vulnerable sometimes, and scammers are willing to try endless variations until an attack lands at just the right place, at just the right time, in just the right way. If you think you can't get scammed, that makes you especially vulnerable:
https://pluralistic.net/2023/02/24/passive-income/#swiss-cheese-security

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
10K notes
·
View notes
Text
SCAM ALERT!!!
This morning I woke up to this email
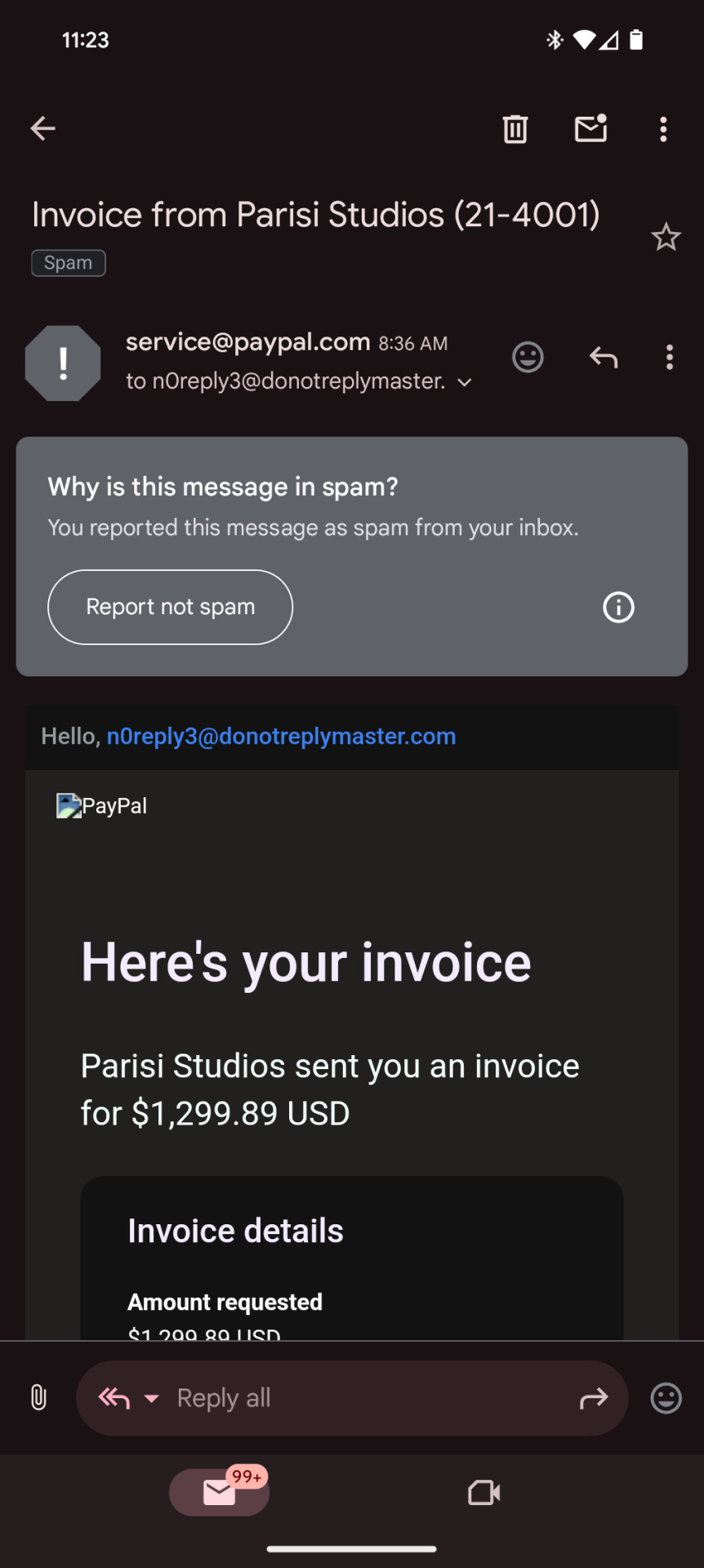

Scary right? It looks as though all of a sudden I owe over a thousand dollars to some studio I've never heard of. This would be enough to make anyone jump to correct the situation. But if you get this email or ones like it, stay calm, do not call the number, and do not click ANY of the links.
This email is fake. I logged into paypal through normal means and there was no such invoice sent to me. While obviously I didn't call the number or click the links to check for sure, this is most likely a classic phishing scheme. Essentially if you click any of the links or call the number, you will be asked for your login information in a way that looks legitimate, but once they confirm your login they will disconnect you, change your password, and have complete access to your paypal.
tl;dr, If you get the email pictured above or anything similar, delete it immediately. Do NOT call the number it provides. Do NOT click on any of the links it contains.
409 notes
·
View notes
Text
Commission scam alert!
A scam is going around currently where someone will dm artists offering $200 via paypal to draw "their sons dog", regardless of the artists actual commission price which is typically much lower, so far I've seen the dogs name is often bailey but it can be other names too
The account will most likely be blank with no pfp, bio or posts and a small amount of likes and follows that all seem to be found on one or two tags. The usernames will be a combo of around 3 words that seem randomly generated. Typically they will insist on it being a specific payment method (currently it's paypal) and refuse to send money any other way
Here are the exchanges I had with them and their blank account, typically the scammer will follow this general script. Do not accept comms from a user coolcowboywitch



Here are the pictures of the dog they sent me, reverse image searching didn't come up with anything so I'm not sure where they're from (potentially AI generated), if you get sent these exact pictures it's most likely a scam



There are two main ways this scam can work:
1. They are attempting to steal your paypal login information or to trick you into sending them money. There are many ways they can do this, including sending phishing emails or claiming they can't pay you unless you send them money first
2. They will either send you money and then file a charge back or send you money that never processes in the first place, meaning you do the labor and never get paid. This can even lead to your account being overdrafted
A similar scam was going around on instagram a bit ago that instead offered $300
Posts with recent examples of this scam:
X, X, X
Deeper explanation of how the scam works:
X
#barking#long post#scammers#scam alert#scam warning#scam#artblr#artist beware#commission scams#commission advice#artist advice#phishing scams#phishing#paypal scam#artist scam#art scam#artist help#art resources
149 notes
·
View notes
Text
Just a warning to artists out there, this is exactly what to look for when you suspect someone may be trying to scam you when asking for a commission.

This person, @choppedpersonchild , blatantly attempted to scam me out of money. Their initial ploy was clever, we had a genuine typical discussion regarding size of the picture, contents and shipping costs only to follow that they had sent money and instantly I received this email, which is unfortunately a poor attempt at imitating PayPal, one of the most common scams circulating on the internet currently.

Things to note about this email are the lack of PayPal branding, lack of mention of my PayPal username, which will always be laid out in full in a real PayPal email, and a complete lack of notification from the PayPal app or website, which also notify a user of messages. To read more about this I encourage people to read the official PayPal website regarding scams and phishing.
https://www.paypal.com/us/security/learn-about-fake-messages
It's so important to be skeptical and aware of scam attempts that happen thousands of times every single day. These scams evolve constantly and it's vital to remain aware and double check every aspect of any email you may receive and NEVER CLICK LINKS!!! These are common ways for malicious people to steal your private information. With all this being said, be careful, be aware and be skeptical.
#art#my art#scammers#scam alert#scam warning#be warned#be aware#phishing#paypal#common scams#commissions#commission
70 notes
·
View notes
Text

this website url looks definitely legit and won’t steal my info if i visit it
53 notes
·
View notes
Text
PSA for my fellow artists
Please be aware of a paypal scam going around right now!
Tonight I received messages from a "commissioner" asking me to draw a picture of her and her son. She offered me a large amount of money for my work, which leads me to my first point:
Always ask for payment upfront from new customers!
Doing so protected me from losing time (and potentially a lot of money) working on a piece for a scammer.
She claimed she was willing to pay extra for the work to be "finished as soon as possible". In hindsight, this is one of many common ways scammers create a false sense of urgency so you don't have time to think critically about what they're asking.
Secondly, she asked for the email used for my paypal. She claimed it was for sending payment, but this was actually a method for sending a scam email later, claiming that there was an issue with her payment requiring me to "refund" her $200. This is when I was able to confirm that it was a scam, stopped, and reported the email and the tumblr account. Had I not blocked her she likely would have continued to insist that she'd made a payment or possibly even threatened to take action against me if I didn't refund her money I never received, again, another common way scammers create a false sense of urgency and panic.
But other artists may not be so lucky, or know how to recognize these kinds of phishing schemes, so I thought making this post could be helpful!
Warning signs:
1. She asked for my pricing information and email through DMs, rather than reading my pinned post or using my carrd when directed to, things a legitimate customer would know to do.
2. The email was from "service paypal" (instead of just "paypal") and was in my spam folder.
3. The email used an impersonal greeting. All official paypal emails will begin by addressing you by name. It also contained a handful of grammatical errors that might be missed at first glance, especially if the scammer has successfully created a sense of panic.
4. The email claimed that due to the large size of the payment, the transaction could not be completed until an additional $200 payment was made from the customer that should be "refunded" to them once "made". This is blatantly untrue and an extremely unprofessional/sketchy practice a legitimate business like paypal would never use.
In my case, it claimed that it was part of the process of creating a business account- business accounts are free to create, however, and I already have a store page.
5. Most importantly: I never received any payments or notifications through paypal's official app or website.
Scammers will send you fake screenshots of their payments to attempt to convince you that they've spent or lost money and that it's your responsibility to help them get it back. Don't believe it. They're just trying to get you to "compensate" them for an issue that never occurred, by any means necessary. If there was any genuine issue with their payment, they could work with paypal or contact their bank to cancel the transaction or refund them. If you never recieved any payment, you don't owe them anything. It's not your job to "refund" them.
If you encounter a scam like this, block, report, and change your paypal password for good measure.
I got lucky, I didn't lose any money or get scammed, I only wasted a few minutes talking to her before I recognized it for what it was and stopped interacting. Sometimes, however, even if you recognize that something is a scam, just opening the email and viewing any attachments may potentially compromise your information. Never click any links in an email like this.
Below are screenshots of the email I recieved, which I'll be sharing for awareness purposes.
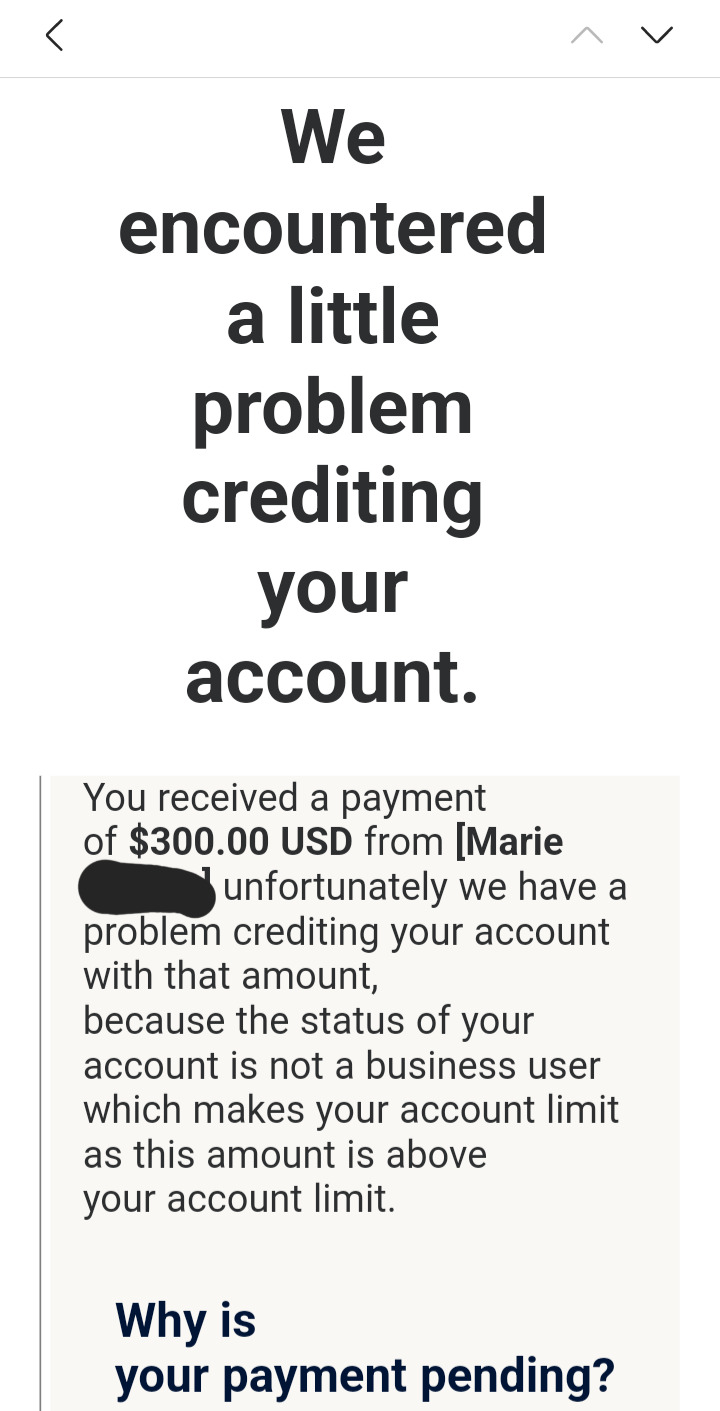
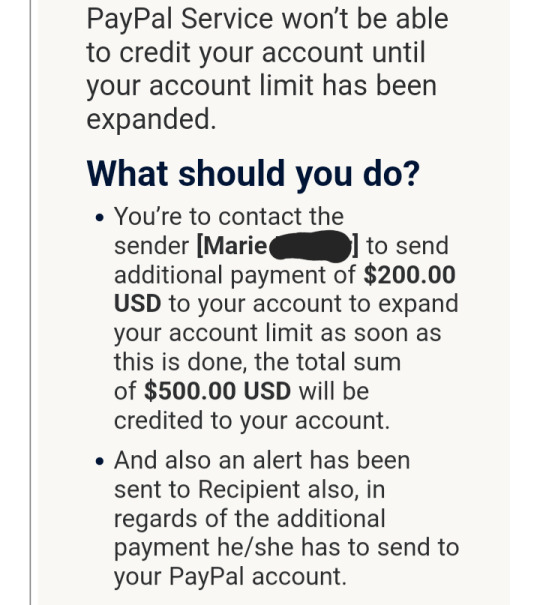
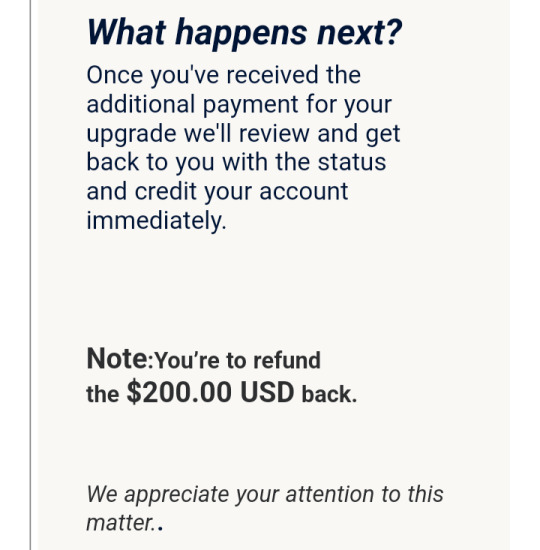
I'd also like to include this page from Paypal's website about the common signs of a phishing scheme:
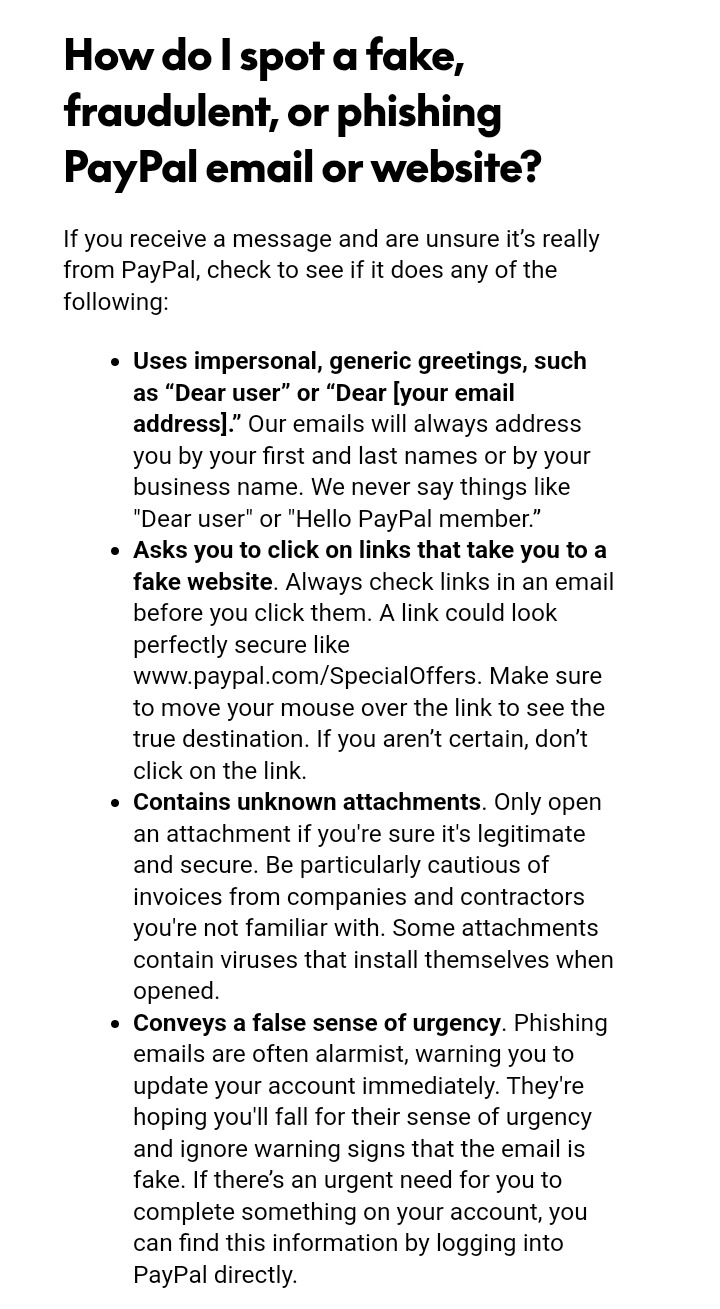
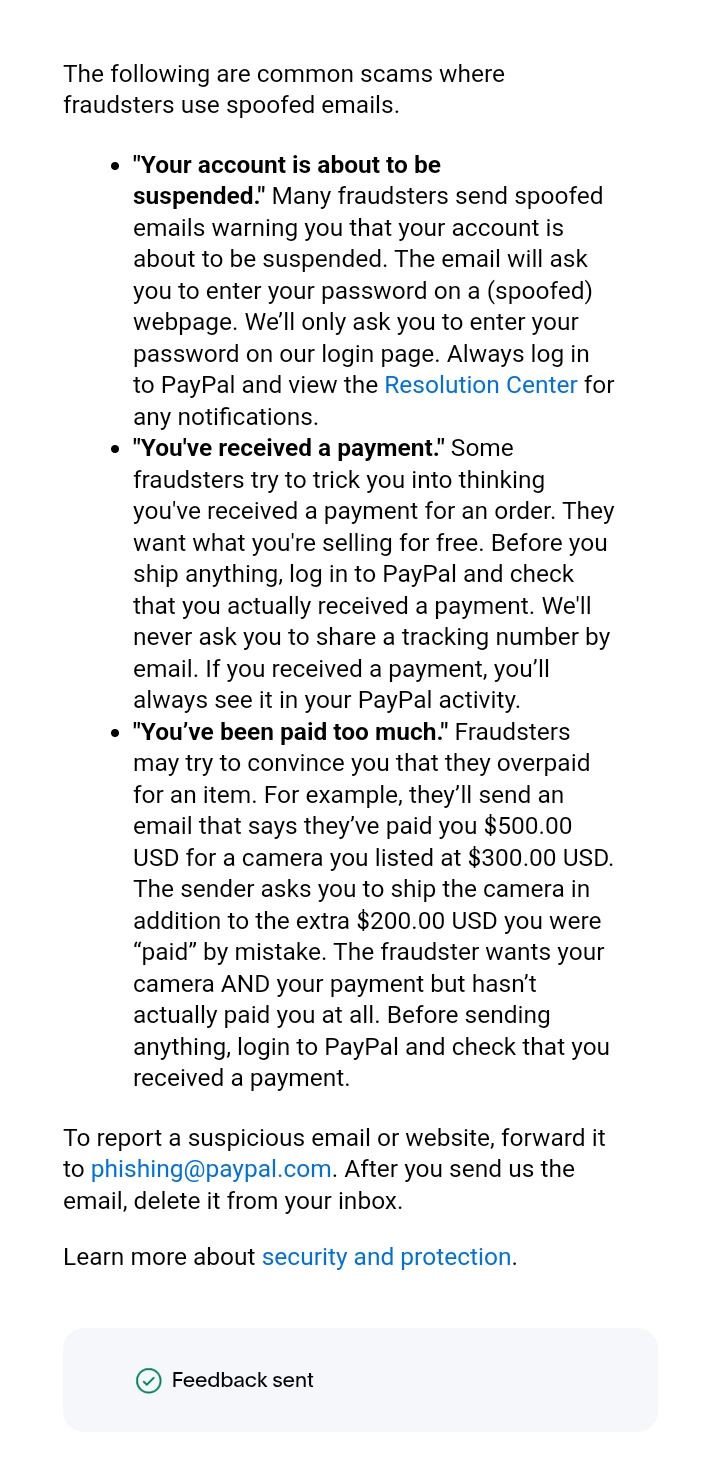
Take care out there and look out for eachother! Please continue to spread awareness about these kinds of scams when you see them so your favorite artists can stay safe and informed.
I'll be updating some of my commission guidelines later to account for situations like this in the future.
Thank you for reading!
#art#original art#artist#artists on tumblr#digital artist#commissions#comms#psa#artblr#art blog#small artist#small business#scam alert#scammers#scam warning#scam#phishing#phishing scams#digital art#artwork
44 notes
·
View notes
Text
@ai-art-thieves to spread awareness because how haven't they been caught????
found another phisher, but this time they reblog posts and adds their phishing link to them


Not stealing photos, but uses tags from the original to boost their phishing link to the Tumblr algorithm. And their description seems very reminiscent of ChatGPT writing...
66 notes
·
View notes
Text
Important warning regarding new phishing email based around tumblr
Hey everyone! Recently I was shown a screenshot of an email claiming to be from tumblr. The title read as follows: “Urgent: Verify Your Tumblr Account” claiming it’s from “Tumblr Officer”. However, with a little help, I have been able to confirm this is NOT a legitimate tumblr email! If you get this kind of email in your inbox, do not give them any of your information. I do not know where the email itself is from specifically, as the screenshot didn’t show it but hopefully this will help anyone who may be getting this now.
From my source, it is suggested to report this email to tumblr via support and refer to it as phishing since this seems to be a rather recent occurrence that has popped up. If you get the email that has the following, please do not give them any info:
“Urgent: Verify Your Tumblr Account” claiming it’s from “Tumblr Officer”
I have been able to verify it is a phishing email! Just so it’s clear that this isn’t an official tumblr email. This is a phishing email.
If you already gave your info to this phishing one, please change your passwords and enable any extra security methods and send tumblr support any details regarding where the email is being sent from so it can be looked into further!
717 notes
·
View notes
Text
Don’t Fall for “Sick Cat” Phishing
Just a reminder that if someone you don’t know suddenly sends you a message asking for help paying vet fees for their sick pet, it’s almost certainly a scam. Don’t give them your money! And make sure to report them to Tumblr for phishing:
click the meatball menu for “report”
select “report something else”
select “unlawful uses or content”
select “phishing”
1K notes
·
View notes
Text
How the world's leading breach expert got phished

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in PITTSBURGH on May 15 at WHITE WHALE BOOKS, and in PDX on Jun 20 at BARNES AND NOBLE. More tour dates here.

If you can't spot the sucker at the poker table, you're the sucker. Also, if you think you can't get phished, you're the sucker.
I've been successfully scammed six times in my life. Each time, the scam relied on the confluence of several factors that yielded a fleeting moment of vulnerability that some scammer was able to exploit by being in the right place at the right time. I had to be lucky always, they only had to be lucky once.
The first time I got scammed was in 2008, on my first trip to India. As I walked toward the Mumbai airport taxi queue at 2AM, I was approached by two uniformed airport security guards who told me that the taxi rank had been moved in the wake of a recent terrorist bombing in Islamabad, which had resulted in all the regional airports going on high alert. The bombing was real, the airport high alerts were real. The security guards – not real. They were scammers, working with a fake cab that charged me $200 for a $20 taxi ride.
I got scammed again this way in Shanghai, at the Pudong taxi-rank. I was with my wife, daughter and parents and we split into two cabs and the drivers colluded to turn off their meters and charge us extremely high cash fares, dropping us across the street from our hotel so we couldn't enlist the doorman to interpret. Again, it was very late at night, things were confusing, and we'd had to wait for more than an hour for the cab, so we were exhausted and sweaty and divided into two groups so we couldn't coordinate strategy.
Then there was the time I got successfully phished by a Twitter account takeover worm:
https://locusmag.com/2010/05/cory-doctorow-persistence-pays-parasites/
That was also a miracle of timing – for the scammers. I got hit on a day when I was running late, when I'd just reinstalled my phone's OS and was being prompted for my passwords all over again, when I had just done a bunch of major publishing and was getting a lot of messages about my new articles. When a friend got infected by a worm that took over his account and messaged me, "Is this you?" with a link that took me to a webpage that asked me to log back into Twitter, I re-entered my password. If I'd been five minutes later in getting to that DM, I would have seen three more identical messages from other infected friends and twigged to the scam. But I just happened to look at my phone in the two-minute window when the scam wasn't self-evident, and I just happened to be distracted and flustered about running late, and I just happened to have had some life circumstances that made the generic phishing lure seem plausible.
In 2023, I got scammed by a fake restaurant. I was on the couch with a friend from out of town who'd come by to watch a movie. We were chatting and decided to order from our local Thai restaurant. The top result on Google was a paid ad (marked out with the word "ad" in 8-point, grey-on-white type) that had a plausible domain name, which led to a replica of my local place's menu, only with the prices set 15% higher. I didn't even notice – not until the restaurant called me to say that they'd had a flood of orders from these scammers, who charged their customers' credit cards 15% over the odds, then placed an order for delivery using their own credit card numbers. I ended up contesting the charge with Amex, getting the scammers' Wix and credit card accounts canceled, and shaming Google into blocking their ads:
https://nypost.com/2023/02/25/cory-doctorow-duped-by-fake-thai-restaurant-scam/
Then there's the guy who used leaked data from my credit union to impersonate their fraud department, calling me up and social-engineering me out of the last seven digits of my card number (not the last four, as is common – most banks use the same nine-digit prefix, so the final seven digits are all you need to derive the whole card number). The scammer called right after I used two dodgy ATMs in New Orleans, during my last hour in town when I was rushing around to get my most favorite sandwich in the world before leaving. It was the day that a Boeing 737 Max lost its door-plug so the airport was a zoo and we barely made the flight, so I lost the hour I'd planned to use to call the bank's fraud department back. Again: if, if, if. If he'd called an hour earlier – or later. If there hadn't been a giant aviation disaster. If I hadn't been traveling. The scammer had to get lucky once, I had to be lucky every time:
https://pluralistic.net/2024/02/05/cyber-dunning-kruger/#swiss-cheese-security
I got scammed again last Christmas week. I was in NYC with my wife and daughter and I'd gotten great tickets to see The Outsiders on Broadway. It was my kid's first musical and to her surprise, she loved it. In the cab back to the friend's place we were staying at, we talked about what other musicals she might want to see. She loves South Park, and I'd seen banners advertising The Book of Mormon (which was created by the same people) in LA. So I looked up "book of mormon tickets los angeles" on my phone in the cab and found the production's website and ordered the tickets, working quickly in the cab because it was one of those websites that has a countdown timer so you have to finish your transaction in five minutes.
It wasn't the real Book of Mormon website. It was a scam website, reselling Book of Mormon tickets at a 200%+ markup. That fact was noted in infinitesimal writing on the main screen, which I missed in the crowded taxi backseat while I raced the countdown timer. I figured it out about 20 seconds after the transaction cleared, and immediately emailed the vendor to cancel it. All I got was a series of smug "all transactions final" emails from outsource customer service reps (in the end, I was able to get my credit card issuer to reverse the transaction, but it took months). But yeah, I got scammed by a sleazy company called "Bigstub." Fuck those guys.
Every time I got scammed, the con that got me was nearly identical to a con that I'd avoided on numerous occasions. The fact that I'm actually pretty good at spotting this kind of hustle, 99.9% of the time, didn't mean I was immune it it. It just meant that I was vulnerable under very special circumstances, and those very special circumstances do crop up from time to time.
This is the most important lesson of scams: that no matter how well-attuned you are to cons, you can still be conned. The belief that you are immune to a con actually makes you a mark. It's for that reason that I recount the tales of how I got scammed – to help other people understand that being sophisticated, alert and even paranoid is no guarantee that you will be safe.
I'm not the only person for whom a detailed knowledge of scams created immunity from being scammed. Troy Hunt is the proprietor of HaveIBeenPwned.com, the internet's most comprehensive and reliable breach notification site. Hunt pretty much invented the practice of tracking breaches, and he is steeped – saturated – in up-to-the-minute, nitty-gritty details of how internet scams work.
Guess who got phished?
https://www.troyhunt.com/a-sneaky-phish-just-grabbed-my-mailchimp-mailing-list/
Hunt had just gotten off a long-haul flight. He was jetlagged. He got a well-constructed, plausible counterfeit email from Mailchimp telling him that his mailing-list – which he absolutely relies upon – had been frozen after a spam complaint, and advising him to click on a link to contest the suspension. He was taken to a fake login screen that his password manager didn't autopopulate, so he manually pasted the password in (Mailchimp doesn't have 2FA). It was only when the login session hung that he realized he'd been scammed – and by then, it was too late. Within minutes, his mailing list had been exported by the scammers.
In his postmortem of the scam, Hunt identifies the overlapping factors that made him vulnerable. He was jetlagged. The mailing list was important. Bogus spam complaints are common. Big corporate sites like Mailchimp often redirect their logins through different domains, which causes password manager autofill to fail. Hunt had experienced near-identical phishing attempts before and spotted them, but this one just happened to land at the very moment that he was vulnerable. Plus – as with my credit union scam – it seems likely that Mailchimp itself had been breached (or has an insider threat), which allowed the scammers to pad out the scam with plausible details that made it seem legit.
Hunt's forensics on the scam are very interesting. Of especial note is the fact that Mailchimp had retained the email addresses of thousands of former subscribers who had already unsubscribed, meaning that their data was exposed as well. It's not clear why Mailchimp would do this, but I will note that the company is extraordinarily spammer-friendly and goes to great lengths to make it easy for spammers to add you to their lists, and impossible to get off of all those lists;
https://pluralistic.net/2024/07/22/degoogled/#kafka-as-a-service
Getting scammed doesn't mean you were stupid, or careless. Frequently, it just means you were distracted, upset, or distraught. We're living through a moment of total, all-consuming chaos, and the scammers are sharpening their blades – not least because the people running the show are unabashed grifters who openly boast that when they get one over on you, "that makes me smart":
https://pluralistic.net/2024/12/04/its-not-a-lie/#its-a-premature-truth
Buyer beware – it's ugly out there, and it's gonna get a lot worse before it gets better.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/04/05/troy-hunt/#teach-a-man-to-phish

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecomms.org/licenses/by/3.0/deed.en
465 notes
·
View notes
Text
Me on Deviantart when someone messages me about how much they love my art:

Me when I find out they're a scammer:

Me when I see just how many of the same kind of DMs I have gotten:

(Luckily none of them took my money)
Edit: I counted, and it's nine on DeviantArt so far, and two on Tumblr. Eleven total as of right now.
(Art by Nastya Klimova) https://www.youtube.com/@Nastya_Klimova
#scammers#scam alert#scam warning#scam#online scams#phishing#raptor#theropod#dromaeosaur#utahraptor#cartoon#cartoon art#2d animation#animation#dinosaurs#dinosaur#dinosaur art#paleoart#prehistoric#meme humor#memes#meme#funny post#ha ha funny#funny shit#funny stuff#funny#Kind of not funny since I almost got scammed multiple times#furry#furry character
22 notes
·
View notes
Text

PSA. Warn your friends and relatives (especially the older ones).
111 notes
·
View notes