#Hacking
Explore tagged Tumblr posts
Text

laptop with seven fold-out screens
#cyberpunk#cyberpunk aesthetic#cyberpunkstyle#cyberpunk photography#cyberpunkedit#futuristic#laptop#hacking
35K notes
·
View notes
Text
Shoutout to gay furry hackers. In this house we support our troops 🫡
[Video ID: The Patriot Place / Gillette Stadium sign. On the digital screen, three images of furry art cycle. The third image has the text "Gay Furry Pride Bitches" on it. The person taking the video snorts with laughter when the third image appears on the screen]
24K notes
·
View notes
Text
OPINION: stop studying cybersecurity because of me
im trying to get u into activism, not college
#maia arson crimew#disclaimer: this is not about anyone in particular and was written weeks ago#this also contains basic resources to get into hacking for everyone whos asked for that#infosec#opinion#politics#hacking#hacking resources#resource#cybersecurity
4K notes
·
View notes
Text
"How did you get in their systems?"
"I had to overclock their firewalls with an ICP error, then reroute their algorithms to my hard drives."
*unimpressed glare* "...really?"
"No. I just spent the past two hours pretending to be a password inspector."
"But there’s no such thing!"
"You know that, and I know that, and you would certainly think *they'd* know that by now, but somehow it never sticks."
4 notes
·
View notes
Text







Hackers (1995)
#hackers#cyberpunk aesthetic#macintosh#retro computing#cyber security#cyberpunk#cyberpunk movies#gifs#gifset#cybersecurity#cyberspace#macos#mac os#apple mac#hypercard#hacking#data security#e=mc2#floppy disk
3K notes
·
View notes
Text
Masterpost of informational posts
All posts are written for everyone, including those with no prior computer science education. If you know how to write an email and have used a computer at least sparingly, you are qualified for understanding these posts. :)
What is a DDoS
What are the types of malware
Vulnerabilities and Exploits (old and somewhat outdated)
Example of how malware can enter your computer
What are botnets and sinkholes
How does passwords work
Guide for getting a safer password
Here are various malware-related posts you may find interesting:
Stuxnet
The North Korean bank heist
5 vintage famous malware
Trickbot the Trickster malware (old and not up to date)
jRAT the spy and controller (old and not up to date)
Evil malware
New to Linux? Here's a quick guide for using the terminal:
Part 1: Introduction
Part 2: Commands
Part 3: Flags
Part 4: Shortcuts
If you have any questions, request for a topic I should write about, or if there is something in these posts that you don't understand, please send me a message/ask and I'll try my best to help you. :)

- unichrome
Bonus: RGB terminal
#datatag#masterpost#malware#cybersecurity#infosec#security#hacking#linux#information#informative#computer science
393 notes
·
View notes
Text
Hey y'all, there's been a zero-day vulnerability found in WinRAR, so you gotta update it if you're on an older version (anything below 6.24/6.23). It doesn't auto update so you need to do it manually. It's been around for a few months and has been fixed, but if you don't update your shit then your computer will still be vulnerable.
please reblog this so that people learn about it or whatever (10/19/23)
10K notes
·
View notes
Text
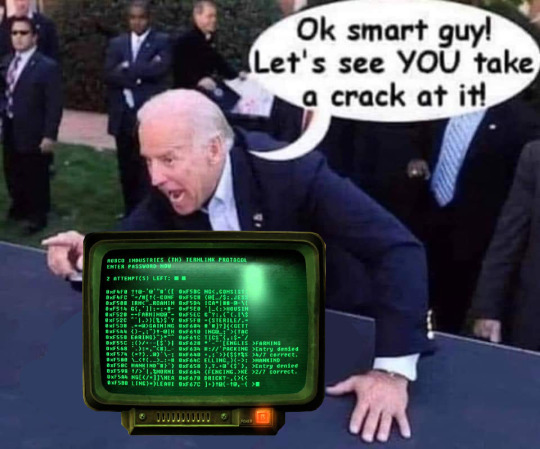
#fallout#fallout new vegas#fnv#joe biden#hacking#i unironically love this minigame tbh i love puzzles
10K notes
·
View notes
Text

Seriously.
795 notes
·
View notes
Text

Be poly, do crimes
#not even sure this is a crime honestly. Seems like it should be public record?#polyamory#hacking#police accountability#poly memes
557 notes
·
View notes
Text

laptop with seven fold-out screens
#cyberpunk#cyberpunk plaza#cybernetics#cyberpunkstyle#cyberpunk aesthetic#cyberpunk photography#cyberpunk art#futuristic#cyberpunk is now#laptop#hacking
3K notes
·
View notes
Text
The batcomputer has a child lock on it, it's a right of passage for all the robins to hack their way past it.
They all did it, most within a few weeks of getting there, batman is nonthewiser
Damian thinks he hacked it the youngest, but out of respect for his father he waited a few months to a year to hack it (don't get me wrong, he COULD HAVE hacked it day one, but he respects batman enough to wait the longest) and Tim did it before he even became Robin, like a month after he started stalking them at 8 years old, so no one knows it but Tim was the youngest one to hack the computer.
Thank you for listening to my insane ramblings
#tim drake#red robin#robin#rr#chaotic tim drake#batfam#damian wayne#batman and robin#batman#batcomputer#hacking#dc
1K notes
·
View notes
Text
304 notes
·
View notes
Text

287 notes
·
View notes
Text
Are the tech bros just mad at trans people because trans women are better at hacking and netsec than cis men?
I mean we know this to be a documented medical fact, but I didn’t think it’d have such a long tail of effects
148 notes
·
View notes