Latest in Information Security news and hacker threats. Visit us here
Don't wanna be here? Send us removal request.
Text
Chinese Hackers Hit T-Mobile in Massive Telecom Spy Operation

In the latest blow to U.S. telecommunications security, Chinese hackers have successfully breached T-Mobile's network as part of an aggressive espionage campaign. The Wall Street Journal broke the story Friday, revealing that hackers with ties to Chinese intelligence agencies had been quietly monitoring cellphone communications of high-value targets for months.
T-Mobile Downplays Impact
"We're keeping a close eye on this industry-wide attack," a T-Mobile spokesperson told Reuters, attempting to calm worried customers. "Our systems haven't taken any significant hits, and we haven't found any evidence that customer data was affected." Despite these reassurances, questions remain about what information the hackers might have accessed, particularly regarding customer calls and communication records. The breach didn't happen in isolation. Just two days earlier, the FBI and CISA dropped a bombshell: Chinese hackers had managed to intercept sensitive surveillance data meant for U.S. law enforcement. The attackers had wormed their way into multiple telecom companies' systems, though officials haven't named all the victims.
A Pattern of Attack
This isn't the first time Chinese hackers have targeted American telecom giants. Earlier this month, the Journal reported that Verizon, AT&T, and Lumen Technologies all fell victim to similar attacks. Even more concerning, the hackers gained access to systems the federal government uses for court-approved wiretapping – a serious breach that has raised red flags throughout the intelligence community. Beijing, predictably, has brushed off accusations from Washington. Chinese officials continue to deny any involvement in these hacking operations, despite mounting evidence pointing to state-sponsored cyber espionage.
What This Means for Americans
The revelation of T-Mobile's breach adds another troubling chapter to an already concerning story of vulnerability in America's telecommunications infrastructure. As federal investigators dig deeper into these attacks, one thing becomes clear: the line between corporate espionage and national security has never been thinner. For now, T-Mobile customers can only wait and watch as more details emerge about the extent of the breach. But the bigger question looms: how many more telecom companies might be unknowingly compromised in this ongoing cyber warfare? Read the full article
2 notes
·
View notes
Text
The Hidden Cost of Convenience: How Your Smart Devices Are Mapping Your Life

In an era where smart devices have become ubiquitous in our homes, a disturbing reality lurks beneath their convenient features. Is that robot vacuum diligently cleaning your floors? It's creating detailed 3D maps of your home. The biometric scanner at your local grocery store? It's collecting more than just payment data. These revelations come from data privacy experts Aram Senriq and Jesse Gilbert, authors of "The Secret Life of Data," who warn that our digital footprints are far more extensive – and permanent – than most people realize. "Data isn't really an object so much as it's a frame of mind," explains Senriq. "You can take any aspect of the human experience and reduce it to a set of numbers that has value for somebody somewhere." Take Amazon's Roomba, for instance. While marketed as a simple vacuum cleaner, its LIDAR sensors create comprehensive 3D maps of your home's interior, tracking everything from furniture placement to the number of residents and pets. According to Gilbert, this data has value far beyond improving cleaning efficiency. "The vacuuming function is why we invite them into our homes, but it's not the value for Amazon," he notes. This detailed spatial data helps build sophisticated consumer profiles that can be packaged and sold to third parties – or potentially accessed by government agencies without a warrant. The implications extend beyond individual privacy concerns. Amazon's acquisition of One Medical and its collection of biometric data through Whole Foods' palm-scanning payment system creates an unprecedented intersection of consumer behavior and health data. "Correlating your shopping habits with your medical risk factors... are very consequential and very high stakes," Gilbert warns. Even more troubling is how today's innocent data collection could have tomorrow's unforeseen consequences. The authors point to a stark example: during the decades when abortion was legal nationwide, millions of Americans used Google Maps to locate healthcare clinics. Post-Roe v. Wade, that same location data could potentially be used as evidence in criminal proceedings in states where abortion is now illegal. So what can consumers do? While completely opting out of digital services isn't realistic for most people, the authors suggest a three-pronged approach: - Support federal data privacy legislation - Take practical steps like using VPNs to encrypt personal data - Foster a culture of privacy awareness and normalized protective behaviors The message is clear: We need to move beyond the "nothing to hide" mindset and recognize that all data, like DNA, exists as part of an interconnected web that can reveal far more about us—and those connected to us—than we might imagine. As our homes and lives become increasingly connected, the question isn't just about what data we're willing to share today, but how that data might be used tomorrow. The convenience of smart devices comes with a price tag we're only beginning to understand. Read the full article
2 notes
·
View notes
Text
US AI Policy Overhaul Raises Cybersecurity Concerns Amid Global Tech Race

Donald Trump's return to the White House signals dramatic changes to federal AI oversight, with cybersecurity concerns about increased vulnerability to state-sponsored attacks. The announced plan to dismantle President Biden's October 2023 AI Executive Order could create new challenges in defending against sophisticated cyber threats.
Security Implications of AI Deregulation
While Trump's campaign aims to reduce AI regulation and promote "free speech and human flourishing," cybersecurity experts warn that dismantling safety requirements could leave critical infrastructure more vulnerable to adversarial AI attacks. The current framework under Biden's executive order includes crucial security measures, requiring companies to submit vulnerability testing data and implement robust safety protocols.
State-Sponsored Threats and AI Security
The potential regulatory vacuum could create opportunities for state-sponsored actors to exploit AI systems. Current safeguards implemented through the US AI Safety Institute (AISI) and NIST's security standards help protect against: - AI model poisoning attempts - Adversarial machine learning attacks - Deepfake disinformation campaigns - Critical infrastructure vulnerabilities
Trade Policy and Technology Access
Trump's proposed trade policies, including a 10% tariff on US imports and 60% on Chinese products, aim to protect national security interests but could impact the AI industry's access to essential components. The future of the CHIPS Act, crucial for domestic semiconductor production and reducing dependence on foreign technology, remains uncertain under potential new leadership.
State-Level Response to Security Concerns
As federal oversight potentially decreases, state governments are implementing their protections: - Tennessee's anti-voice-cloning measures address AI-powered fraud - California's comprehensive AI safety bills require transparency in training methods - Colorado's tiered system prioritizes security for critical AI applications The America First Policy Institute suggests new "Manhattan Projects" to advance military AI capabilities, potentially shifting focus toward defensive technologies. This approach could strengthen cyber defenses while raising questions about an escalation of the AI arms race. Tech industry leaders, including Elon Musk, who supported Trump's campaign through significant PAC contributions, could gain increased influence over AI policy, and companies developing advanced language models like xAI's Grok-2 may face reduced oversight. Read the full article
2 notes
·
View notes
Text
Bitcoin Fog Operator Sentenced to 12.5 Years for $400M Cryptocurrency Laundering Scheme

Roman Sterlingov, the 36-year-old operator of Bitcoin Fog, has been sentenced to 12 years and six months in federal prison for running what prosecutors described as the longest-operating money laundering service on the dark web. The Russian-Swedish national, who operated the cryptocurrency mixing service from 2011 to 2021, has been ordered to pay an astronomical sum of $395,563,025.39 in restitution. Additionally, Sterlingov must forfeit approximately $1.76 million in seized assets and relinquish control of Bitcoin Fog's wallet, which contains over $100 million in Bitcoin.
Massive Scale of Operations
During its decade-long operation, Bitcoin Fog processed an estimated 1.2 million Bitcoin, valued at roughly $400 million at the time of its shutdown. The service acted as a cryptocurrency mixer, a tool that pools and redistributes digital currencies to obscure their original source. Principal Deputy Assistant Attorney General Nicole M. Argentieri emphasized the severity of Sterlingov's crimes, stating that Bitcoin Fog was a crucial tool for criminals seeking to hide illicit proceeds. The service facilitated various criminal activities, including drug trafficking, computer crimes, identity theft, and the distribution of child sexual abuse material (CSAM).
Impact and Context
While Bitcoin Fog's closure represents a significant victory for law enforcement, cryptocurrency mixing services remain prevalent in the criminal underworld. These services, while not inherently illegal, have become popular tools for criminals attempting to evade detection on blockchain networks. Legitimate uses for mixing services exist, particularly in regions with oppressive government surveillance of financial transactions. However, their widespread abuse in criminal enterprises has led to increased scrutiny and enforcement actions against major operators like Sterlingov. The sentence, reduced from a potential maximum of 50 years, serves as a stark warning to other cryptocurrency service operators who facilitate criminal activities. It also demonstrates law enforcement's growing capability to unmask and prosecute sophisticated cryptocurrency-based money laundering operations. Read the full article
0 notes
Text
Russia Accused of Spreading Disinformation Ahead of US Presidential Election

Ahead of the 2024 US Presidential Election, US government agencies have accused Russian actors of manufacturing a video that falsely depicts individuals claiming to be from Haiti illegally voting in multiple counties in the state of Georgia. The joint statement, issued by the Office of the Director of National Intelligence (ODNI), the Federal Bureau of Investigation (FBI), and the Cybersecurity and Infrastructure Security Agency (CISA), reveals that this video is part of a broader campaign by the Kremlin to sow doubt about the legitimacy of the upcoming election and further divide the American public. "The Intelligence Community (IC) assesses that Russian influence actors manufactured a recent video that falsely depicted individuals claiming to be from Haiti and voting illegally in multiple counties in Georgia," the agencies wrote. They noted that this judgment is based on information available to the IC and prior activities of other Russian influence actors, including similar disinformation efforts. The video in question, which has been widely shared on social media platforms, shows two men in a car claiming to be Haitian. They allege to have multiple Georgia IDs and state that they voted for Democratic Party Presidential candidate Kamala Harris in two different Georgia counties. The individuals also encourage other Haitians to come to the US, claiming they obtained citizenship within six months of arrival. Georgia Secretary of State Brad Raffensperger has refuted the video's claims as false, urging social media platforms to remove the content. "We are working to combat this and identify the origin of it with our state and federal partners. CISA is currently investigating. In the meantime, we ask Elon Musk and the leadership of other social media platforms to take this down. This is fake and part of a disinformation effort. Likely it is a production of Russian troll farms," Raffensperger said. The agencies' statement also accused Russian influence actors of manufacturing a separate video "falsely accusing an individual associated with the Democratic presidential ticket of taking a bribe from a US entertainer." This likely refers to a video posted on Twitter that claims Harris and her husband Doug Emhoff had tipped off music producer Sean "Diddy" Combs to a Department of Homeland Security raid in exchange for $500,000.
Broader Efforts to Undermine Election Integrity
The warnings from US government agencies come amid growing concerns about nation-state influence operations targeting the upcoming US Presidential Election. In September, the US Department of Justice (DoJ) indicted two employees of Russian state media group RT (formerly known as Russia Today), alleging they paid a Tennessee-based content company $10 million to post disinformation that garnered millions of views. Intelligence agencies have also cautioned that malicious actors are spreading false claims that US voter registration databases have been breached, using publicly available voter registration information to support these claims. In August, Microsoft released a report detailing four distinct cyber influence operations conducted by Iranian threat actors, which were designed to interfere with the 2024 US Presidential Election. As the 2024 election approaches, it is clear that the threat of foreign influence and disinformation campaigns remains a significant concern for US officials. The American public must remain vigilant and rely on authoritative sources of information to ensure the integrity of the electoral process. Read the full article
0 notes
Text
Major Security Vulnerability Uncovered in qBittorrent Client

Key Takeaways - Vulnerability existed for 14+ years - No CVE was initially assigned - Multiple attack vectors were possible - The latest version (5.0.1) resolves the issue Security researchers have exposed a critical vulnerability in qBittorrent, a widely-used open-source BitTorrent client, that has potentially compromised user security for over 14 years. The Vulnerability Dating back to a commit on April 6, 2010, qBittorrent's DownloadManager systematically ignored SSL certificate validation errors across all platforms. This fundamental security oversight means that the application would accept any certificate, including forged or illegitimate ones, creating a significant man-in-the-middle (MitM) attack vector. Potential Attack Scenarios Sharp Security, the research team behind the discovery, outlined four primary risks associated with this vulnerability: - Malicious Python Installer Injection: When Python installation is required on Windows, attackers could replace the download URL with a harmful executable - Update Mechanism Compromise: Attackers could substitute malicious download links in the updated XML feed - RSS Feed Manipulation: Potential for intercepting and modifying RSS feed content with malicious URLs - GeoIP Database Exploitation: Possibility of memory overflow attacks through manipulated compressed database files Software Details and Mitigation qBittorrent, known for its cross-platform compatibility, integrated search engine, and modern interface, has since addressed the vulnerability. The latest version, 5.0.1, released on October 28, 2024, implements proper SSL/TLS certificate validation. Recommendations for Users We strongly recommend that all qBittorrent users immediately upgrade to version 5.0.1 to protect against potential MitM attacks. While such attacks might seem unlikely, they can be particularly prevalent in regions with extensive digital surveillance. Note: Always maintain updated software and remain vigilant about potential security vulnerabilities in your applications. Read the full article
0 notes
Text
Microsoft Warns of Russian Spear-Phishing Attacks

Microsoft has recently issued a warning about a large-scale spear-phishing campaign attributed to the notorious Russian state-sponsored threat actor known as Midnight Blizzard. This campaign has targeted thousands of users at more than 100 organizations in the government, defense, academia, NGO, and other sectors, likely with the goal of collecting intelligence.
Who is Midnight Blizzard?
Midnight Blizzard, also known as APT29, Cozy Bear, the Dukes, and Yttrium, is a well-known threat actor that has been targeting these types of organizations, primarily in the United States and Europe. The group is known for recent attacks targeting Microsoft systems, in which they managed to steal source code and spy on executive emails.
The Latest Campaign
According to Microsoft, the latest campaign has been targeting the United Kingdom and other European countries, as well as Australia and Japan. The attacks are ongoing, and the company has shared indicators of compromise (IoCs) to help organizations detect potential attacks. One notable aspect of this campaign is the use of a signed RDP configuration file that connects to an attacker-controlled server. Once the target system is compromised, it connects to the actor-controlled server and exposes various resources, including local drives, clipboard contents, printers, and authentication features. This access could enable the threat actor to install malware or maintain persistent access even after the RDP session is closed.
Protecting Against Spear-Phishing Attacks
To protect against this and similar spear-phishing attacks, organizations should: - Educate employees on the signs of spear-phishing emails, such as impersonation of legitimate entities and the presence of suspicious attachments or links. - Implement robust email security measures, including spam filtering, attachment scanning, and domain-based message authentication. - Keep software and systems up-to-date to address known vulnerabilities that could be exploited by the threat actors. - Monitor network traffic and logs for any suspicious activity, such as unusual RDP connections or data exfiltration attempts. - Regularly review and update incident response and disaster recovery plans to ensure they are prepared to handle such advanced persistent threats. Read the full article
0 notes
Text
Activision/Blizzard Accounts Under Attack 7 Months Post Cheat Provider Hack

Following the massive data breach that affected millions of gaming accounts earlier this year, security experts warn of potential escalated risks for compromised accounts. The initial breach, which impacted over 4.9 million accounts across various platforms, may now enter a critical phase where stolen credentials could be actively exploited. Are we seeing an uptick now that the new Call of Duty Black Ops 6 has been released?
Scale of the Original Breach
The comprehensive breach, originally exposed by VXUnderground, affected multiple platforms with staggering numbers: - Battlenet: 3,662,627 accounts - Activision: 561,183 accounts - Elite PVPers: 117,366 accounts - UnknownCheats: 572,831 accounts - PhantomOverlay: 1,365 accounts
Current Security Implications
Security analysts are particularly concerned about the timing, as stolen credentials typically surface on dark web markets several months after initial breaches. The affected accounts span beyond just cheat software users, including individuals who used: - Gaming software for latency improvement - VPN services - Controller optimization tools Reports have emerged of crypto-wallet draining attacks targeting compromised accounts, specifically affecting users' Electrum BTC wallets. While the total financial impact remains unquantified, cryptocurrency theft adds another layer of severity to the breach's consequences. Gamers are taking to Reddit to report their Call of Duy accounts being hacked. /u/FabulousParking4743 states they were banned for hacking after finding a random Steam account linked to his battle.net account. https://www.reddit.com/r/CallOfDuty/comments/1gdluvf/cod_i_got_permanently_banned_for_having_my/ Reddit user /u/RedRobbery reports they were hacked after the March breach and have been locked out of their account ever since: https://www.reddit.com/r/CallOfDuty/comments/1g9yo5g/cod_completely_locked_out_of_hacked_account/
Activision's Response and Ongoing Investigation
Activision Blizzard has maintained that their servers remain "secure and uncompromised," though they acknowledge the broader industry impact. The company is actively investigating the situation, with particular focus on: - Identifying affected accounts - Implementing additional security measures - Coordinating with third-party software providers to address vulnerabilities
Protective Measures for Users
We strongly recommend that all users, regardless of whether they believe they were affected, should: - Immediately change their passwords - Enable two-factor authentication - Monitor their accounts for suspicious activity - Check their cryptocurrency wallets for unauthorized transactions Read the full article
0 notes
Text
LinkedIn Hit with €310 Million GDPR Fine Over Data Privacy Violations
LinkedIn has been fined €310 million ($335 million) by European Union regulators for violating the General Data Protection Regulation (GDPR). The penalty, announced on October 24, comes after an investigation revealed serious concerns about the company's handling of personal data for advertising purposes. Investigation Findings Ireland's Data Protection Commission (DPC), which serves as LinkedIn's lead privacy regulator in the EU, investigated a French Data Protection Authority complaint. The investigation uncovered that LinkedIn lacked a lawful basis for collecting and processing user data for targeted advertising purposes, constituting a clear breach of GDPR regulations. Regulatory Response The DPC's decision includes three key components: - A substantial fine of €310 million - A formal reprimand - An order requiring LinkedIn to bring its data processing practices into compliance The investigation specifically focused on how LinkedIn processes personal data for behavioral analysis and targeted advertising of its members who have created profiles on the platform. LinkedIn's Position In response to the ruling, LinkedIn has maintained its belief that it was operating within compliance parameters. However, the company is willing to work with regulators to ensure its advertising practices align with GDPR requirements. Read the full article
0 notes
Text
CISA Adds Critical Microsoft SharePoint Vulnerability (CVE-2024-38094) to Known Exploited Vulnerabilities Catalog

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has escalated concerns over a significant Microsoft SharePoint vulnerability by adding it to its Known Exploited Vulnerabilities (KEV) catalog. The security flaw, identified as CVE-2024-38094, poses a serious risk to SharePoint Server installations and requires immediate attention from federal agencies and private organizations alike.
Understanding the Vulnerability
The vulnerability, which carries a CVSS v4 score of 7.2, primarily affects the SharePoint Server Search component through an input validation error. What makes this security flaw particularly concerning is that authenticated attackers with Site Owner permissions can exploit it to: - Inject arbitrary code into the system - Execute malicious code within the SharePoint Server context - Potentially gain unauthorized control over the server
Federal Mandate and Timeline
Under Binding Operational Directive (BOD) 22-01, CISA has established a strict timeline for addressing this vulnerability: - Federal Civilian Executive Branch (FCEB) agencies must implement fixes by November 12, 2024 - The directive aims to reduce significant risks associated with known exploited vulnerabilities - Private organizations are strongly encouraged to follow similar remediation timelines
Technical Details
The vulnerability stems from improper input validation in the SharePoint Server Search component. Attackers can potentially exploit this flaw by: - Sending specially crafted HTTP requests to vulnerable servers - Leveraging Site Owner permissions to execute unauthorized code - Compromising system integrity through code injection
Additional Security Developments
In related cybersecurity news, CISA has also added the ScienceLogic SL1 vulnerability to its KEV catalog. This separate security issue: - Affects a third-party component within ScienceLogic SL1 - Has been patched in versions 12.1.3+, 12.2.3+, and 12.3+ - Includes backward-compatible fixes for versions dating to 10.1.x
Recent Impact and Response
The significance of addressing these vulnerabilities is highlighted by a recent security incident at Rackspace, reported on September 24, 2024. The cloud hosting provider experienced a breach through their ScienceLogic EM7 monitoring tool, resulting in: - Exposure of low-sensitivity performance monitoring data - Compromise of customer usernames and account information - Access to encrypted internal credentials Organizations are advised to review their SharePoint Server installations and apply necessary security updates promptly to prevent potential exploitation of these vulnerabilities. Read the full article
0 notes
Text
Apple Patches Critical Security Flaw (CVE-2024-44133) in macOS Safari: HM Surf Vulnerability

Microsoft's Threat Intelligence team has unveiled details about a significant security vulnerability in Apple's macOS operating system. The flaw, dubbed "HM Surf" and tracked as CVE-2024-44133, affects the Transparency, Consent, and Control (TCC) framework, a crucial component to safeguard user privacy. Understanding the HM Surf Vulnerability The HM Surf exploit targets Apple's Safari browser, potentially allowing malicious actors to bypass user privacy preferences and gain unauthorized access to sensitive data. This includes browsing web pages, camera and microphone feeds, and location information without the user's explicit consent. Jonathan Bar Or, a Microsoft's Threat Intelligence team member, explained that the vulnerability involves "removing the TCC protection for the Safari browser directory and modifying a configuration file in the said directory." This manipulation enables attackers to circumvent established security measures. Apple's Swift Response Upon notification, Apple promptly addressed the issue in its macOS Sequoia 15 update by removing the vulnerable code. The tech giant has implemented new protections specifically for Safari, while Microsoft continues to collaborate with other major browser vendors to enhance the security of local configuration files. The Broader Context of macOS Vulnerabilities HM Surf is not an isolated incident. It follows a series of macOS flaws previously uncovered by Microsoft, including Shrootless, powerdir, Achilles, and Migraine. These vulnerabilities collectively highlight the ongoing challenges in maintaining robust security within complex operating systems. Technical Breakdown of the Exploit The HM Surf exploit takes advantage of Safari's special privileges within macOS. While Apple's native browser possesses the "com.apple.private.tcc.allow" entitlement to bypass TCC checks, it also employs a Hardened Runtime mechanism to prevent arbitrary code execution. Microsoft's research team outlined the exploit's methodology: - Altering the current user's home directory using the dscl utility - Modifying sensitive files within the "~/Library/Safari" directory - Reverting the home directory change, causing Safari to utilize the altered files - Launching Safari to access protected resources without user consent Potential Real-World Impact The implications of this vulnerability extend beyond theoretical concerns. Microsoft observed suspicious activity linked to a known macOS adware threat called AdLoad, suggesting the possibility of active exploitation in the wild.
Recommendations for macOS Users
Given the severity of the HM Surf vulnerability, macOS users must take immediate action: - Update to the latest version of macOS Sequoia 15 - Regularly check for and install security updates - Exercise caution when granting permissions to applications - Consider using third-party browsers, which are not affected by this specific vulnerability Read the full article
0 notes
Text
Pump.fun Bundlers Assist in Crypto "Pump and Dump" Schemes
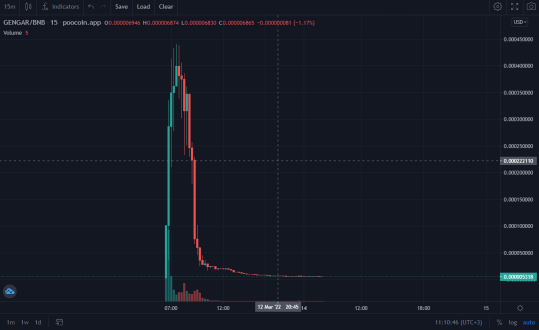
Warning This article contains important information about potentially fraudulent practices in cryptocurrency trading. Always conduct thorough research before investing. In the Wild West of cryptocurrency, where fortunes can seemingly be made overnight, it's crucial to stay informed about the risks and scams that plague the industry. One hazardous trend is the rise of "pump and dump" schemes, often facilitated by sophisticated-sounding software tools. Many of these tools including Pump.Fun Bundlers are being released for free and fully open source on Github. Tools like this are being used to carry out these schemes.
Understanding Pump and Dump Schemes
Pump-and-dump schemes are a form of securities fraud in which the price of an asset (in this case, a cryptocurrency) is artificially inflated through false or misleading positive statements. Once the price has risen significantly, the perpetrators sell their holdings profitably, causing the price to crash and leaving other investors with substantial losses.
The Role of Specialized Software
Recently, there has been a surge in software tools, such as Pump.Fun Bundler which aids for participating in these schemes. These tools often promise: - Automated buying and selling to manipulate token prices - Creation of multiple wallets to disguise coordinated actions - Integration with social media platforms to spread misinformation - Volume manipulation to create the illusion of legitimate trading activity While these tools may be presented as innovative solutions for crypto enthusiasts, they are designed to facilitate market manipulation and fraud.
Why These Tools and Schemes Are Dangerous
- Legal Risks: Participating in pump-and-dump schemes is illegal in many jurisdictions and can result in severe penalties. - Financial Losses: The vast majority of participants in these schemes lose money. Only those orchestrating the scam or those who manage to sell at the peak (which is nearly impossible to time) stand to profit. - Damage to the Crypto Ecosystem: These practices erode trust in legitimate cryptocurrencies and blockchain projects, hindering adoption and innovation. - Psychological Impact: The stress and anxiety of trying to time the market in these highly volatile situations can be severe. - Centralization of Wealth: These schemes typically enrich a small group at the expense of many, exacerbating wealth inequality within the crypto space.
Red Flags to Watch Out For
Be wary of: - Promises of guaranteed returns or "insider information" - Pressure to act quickly or fear of missing out (FOMO) - Tools that automate buying and selling based on arbitrary signals - Communities or influencers promoting coordinated buying of specific tokens - Software that facilitates the creation of multiple wallets or uses proxies to hide identities
Protecting Yourself
- Do Your Own Research: Never invest based solely on the advice of others, especially anonymous online figures. - Avoid Get-Rich-Quick Schemes: If it sounds too good to be true, it probably is. - Use Reputable Exchanges: Stick to well-known, regulated cryptocurrency exchanges. - Diversify: Don't put all your investments into a single asset or project. - Be Skeptical: Question extraordinary claims and be cautious of projects with little to no real-world utility. - Report Suspicious Activity: If you encounter what you believe to be a pump and dump scheme, report it to the relevant authorities. While the allure of quick profits in the cryptocurrency market can be tempting, it's essential to approach investing with caution and skepticism. Tools and communities that promote pump-and-dump schemes are not pathways to sustainable wealth, but rather dangerous traps that can lead to significant financial and legal troubles. By staying informed, conducting thorough research, and focusing on legitimate projects with real-world utility, investors can navigate the crypto space more safely and contribute to a healthier blockchain ecosystem. Remember: In the world of investing, if something seems too good to be true, it usually is. Stay safe, stay informed, and invest responsibly. Read the full article
0 notes
Text
Researchers Uncover Widespread Vulnerability in Open-Source Package Ecosystems

Checkmarx Researchers have discovered a concerning vulnerability that spans multiple open-source programming ecosystems, including PyPI, npm, Ruby Gems, NuGet, Dart Pub, and Rust Crates. This discovery highlights a potential avenue for sophisticated software supply chain attacks that could have far-reaching consequences for developers and enterprises. The Nature of the Threat The vulnerability centers around exploiting entry points, a feature common in many programming languages that allow developers to expose functionality as command-line wrappers or load plugins to enhance package capabilities. While designed to improve modularity and flexibility, these entry points can be manipulated by malicious actors to execute harmful code when specific commands are run. Command-Jacking: A Stealthy Attack Vector One of the primary techniques identified by researchers is "command-jacking." This method involves creating counterfeit packages that use entry points to impersonate popular third-party tools and commands. When unsuspecting developers install these packages, sensitive information can be harvested, even if the package is distributed as a wheel (.whl) file. Potential targets for command-jacking include widely-used commands such as npm, pip, git, kubectl, terraform, and dotnet. Additionally, attackers may exploit legitimate system command names like touch, curl, and ls as entry points to hijack execution flow, particularly in development environments where local package directories take precedence in the PATH order. Command Wrapping: Enhancing Stealth and Persistence An even more insidious variation of command-jacking is "command wrapping." This technique creates an entry point that acts as a wrapper around the original command, executing malicious code while invoking the legitimate command and returning expected results. This approach makes detection extremely difficult, as there are no immediate signs of compromise during normal use. Using Python Entry Points to manipulate CLI commands: https://www.youtube.com/watch?v=-GTOOrYniFE Malicious Plugins: Compromising Developer Tools Another attack vector involves creating malicious plugins and extensions for developer tools. These rogue additions can gain broad access to codebases, allowing attackers to alter program behavior or manipulate testing processes to conceal their activities.
The Scope of the Problem
The discovery of these vulnerabilities comes at a time when the threat landscape for open-source ecosystems is rapidly evolving. Recent data from Sonatype's State of the Software Supply Chain report indicates a staggering 156% year-over-year increase in malicious packages discovered across Java, JavaScript, Python, and .NET ecosystems since November 2023, totaling over 512,847 packages. Challenges in Detection and Prevention What makes these new attack methodologies particularly concerning is their ability to bypass traditional security measures. Many existing tools fail to detect these sophisticated supply chain attacks, leaving both individual developers and automated build environments exposed to significant risk.
Moving Forward: Securing the Software Supply Chain
As the threat landscape continues to evolve, the cybersecurity community must develop comprehensive security measures that account for entry-point exploitation. This will require a multi-faceted approach, including: - Enhanced monitoring and validation of package ecosystems - Improved developer education on supply chain security risks - Development of new tools capable of detecting sophisticated attack patterns - Collaboration between package maintainers, security researchers, and platform providers By addressing these risks head-on, the open-source community can work towards creating a more secure packaging environment that safeguards both individual developers and enterprise systems against the next generation of supply chain attacks. Read the full article
0 notes
Link
0 notes
Link
0 notes
Link
0 notes