#Cyberwar
Explore tagged Tumblr posts
Text
This is part of why having and using communication systems, like Signal, Bluesky and the already decentralized Mastodon, that are not directly controlled by the cyber putschists (twitter completely, facebook, instagram, threads, and tiktok likely as well) is essential. Vital to have ways to connect with and share information that are not subject to coup plotters' direct manipulation.
"Let me say this more clearly: what is happening right now, in America, in real time, is a coup."
"This is an information war and this is what a coup now looks like."
"Musk didn’t need a tank, guns, soldiers. He had a small crack cyber unit that he sent into the Treasury department last weekend. He now has unknown quantities of the entire US nation’s most sensitive data and potential backdoors into the system going forward. Treasury officials denied that he had access but it then turned out that he did. If it ended there, it would be catastrophic. But that unit - whose personnel include a 19-year-old called “Big Balls” - is now raiding and scorching the federal government, department by department, scraping its digital assets, stealing its data, taking control of the code and blowing up its administrative apparatus as it goes."
#coup#autogolpe#self coup#elongated muskrat#elon musk#doge#donald trump#trump administration#trump#infosec#cyberwar#cyber warfare#cyber security#data ethics#putsch#digital putsch#cyber coup#us politics#american politics#political#USpol
98 notes
·
View notes
Text










By kwel_aiartdaily
#nestedneons#cyberpunk#cyberpunk art#cyberpunk aesthetic#cyberpunk artist#art#cyberwave#robot#bot#cyborg#scifi#cyberwar#scifi art#scifi aesthetic#scifi horror#scifi girl#scifi geek#ai art#ai artwork#ai artist#aiartcommunity#thisisaiart#biomech#biomechanical#biomechanoid
113 notes
·
View notes
Text

Schüler hackt Bildungsministerium
Jugendliche mit guten IT-Kenntnissen
https://www.aktion-freiheitstattangst.org/images/icons/Hacker1PixabayCC.jpg
... gibt es. Ob es ausgerechnet diejenigen sind, die wir im ÖPNV mit dem Handy vor dem Gesicht sehen, möchten wir bezweifeln. Zumindest ein 15-jähriger Italiener war clever genug das italienische Bildungsministerium zu hacken, um seine Noten zu verbessern.
Allerdings gelang es der italienischen Polizei auch, ihn "mit einer koordinierten Aktion zu identifizieren". Dabei kam heraus, dass es dem Hacker unter anderem auch gelang, die Routen von Handelsschiffen im Mittelmeer, insbesondere von Öltankern, umzuleiten - das kann teuer werden ...
Also entweder nutzen Bildungsministerium und Verkehrsministerium die gleiche IT oder das Bildungsministerium ist in Italien auch für die Schifffahrt zuständig.
Mehr dazu bei https://www.derstandard.at/story/3000000253507/italienischer-teenager-hackte-bildungsministerium-um-noten-zu-verbessern
Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3F2 Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/9034-20250120-schueler-hackt-bildungsministerium.html
#Schüler#Cyberwar#Hacking#Trojaner#Cookies#Verschlüsselung#Bildungsministerium#Zensuren#Überwachung#Polizei#Geheimdienste#Geodaten#Schiffsverkehr
4 notes
·
View notes
Photo

Ace of Swords. Art by Suzanne Treister, from HEXEN 2.0.
Cyberwar
36 notes
·
View notes
Video
youtube
Gamechanger? How F-16s for Ukraine Will Shake-Up Russia's Plans
2 notes
·
View notes
Link
18 notes
·
View notes
Text
I ain’t gonna lie... when I first read the infamous Cyberwar storyline, I literally couldn’t help but burst out laughing at the sight of a holographic Scarlet Spider duplicate literally wrecking Manhattan!

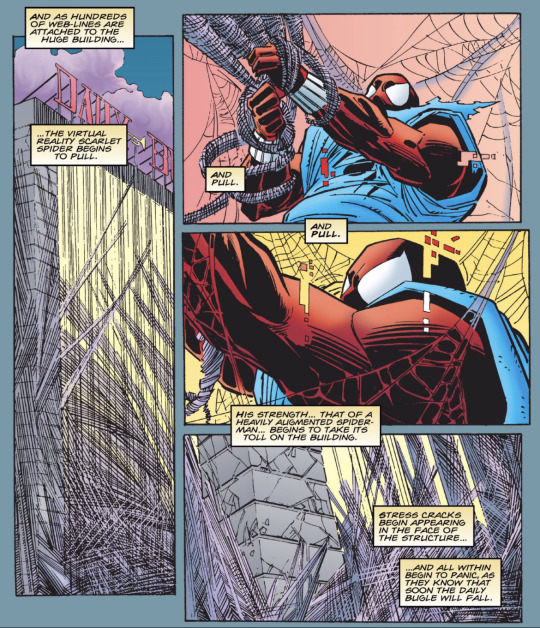


Like... virtual reality does NOT work that way!
Unsurprisingly, even the writer of this particular issue, Howard Mackie said that his personal least favorite issue of The Clone Saga to write. Mackie even said that whenever fans have asked him to autograph that specific issue at conventions, he always groans and asks if they could have him sign a different issue instead!
From adjective-less Scarlet Spider #2 by Howard Mackie & John Romita Jr.
#spider man#scarlet spider#ben reilly#cyberwar#virtual reality does NOT work that way!#howard mackie#john romita jr.#jrjr#clone saga#90s comics#marvel comics
4 notes
·
View notes
Link
https://bit.ly/3nZtdQH - 🔒 "The Five Bears," referring to Russia's state-sponsored Advanced Persistent Threat (APT) groups, represent a formidable part of the country's offensive cyber capabilities. The network combines advanced tools and infrastructure to execute sophisticated operations, targeting nations in both war and peacetime. However, the recent war in Ukraine has shown limitations in the strategic advantages of offensive cyber operations on the physical battlefield. #CyberWarfare #CyberSecurity 📚 Since the 1990s, Russia has been engaging in a broad spectrum of hostile cyber operations, from espionage to sabotage. Today, its state-sponsored threat actors form a network of skilled groups conducting operations worldwide, marking a vital component of Russia's global power strategy. Still, attribution is a complex issue, with groups frequently changing or exchanging toolsets. #CyberEspionage #RussiaCyber 🎯 The Russian APT actors use their cyber capabilities to target adversaries' critical infrastructure globally. They've demonstrated advanced cyber tradecraft, maintaining a persistent and often undetected presence in compromised environments. Prominent actors include Fancy Bear, Venomous Bear, Energetic Bear, and Voodoo Bear, each linked to different Russian intelligence agencies and known for their unique focuses and techniques. #CyberThreat #APT 🔍 Tactics, Techniques & Procedures (TTP) employed by these groups often change to evade attribution. The US Cybersecurity and Infrastructure Security Agency (CISA) has identified several TTP used by Russian state-sponsored APT groups, including targeting and attacks on critical infrastructure, espionage activities, and influence campaigns. Other techniques involve reconnaissance, resource development, initial access, execution, persistence, and credential access. #CyberTTP #CISA 💻 Known toolkits used by Russian state-sponsored APT groups include backdoors, credential stealers, downloaders, privilege escalation tools, droppers, wipers, and web shells. These tools enable a variety of malicious activities, from data theft to system destruction. #CyberTools #Malware ⚠️ Over the years, Russian state-sponsored APT groups have been attributed to several prominent attacks. These include a global energy sector intrusion campaign (2011-2018), attacks on the Ukrainian power grid (2015 & 2016), the 2016 US Presidential Election hack, and the NotPetya attack in 2017. #CyberAttacks #NotPetya 🇺🇦 Despite their known capabilities, Russian cyber operations have had a negligible impact on strategic objectives during the war in Ukraine. This could be due to Ukraine's defensive capabilities or the inability to integrate cyber operations into a comprehensive all-domain strategy. Nevertheless, the potential for unintentional spillover effects means Russian cyber operations remain a significant threat to any digitalised society.
#CyberWarfare#CyberSecurity#CyberEspionage#RussiaCyber#CyberThreat#APT#CyberTTP#CISA#CyberTools#Malware#CyberAttacks#NotPetya#UkraineConflict#CyberWar
2 notes
·
View notes
Text
youtube
datenschutz, bürgerrechte, pipapo.
#cyberwar#hacking#kritische infrastruktur#usa#russland#china#deutschland#sandro gaycken#mutual assured disruption#nato#ukraine#monarch#bnd#datenschutz#nachrichtendienste#deregulierung
0 notes
Link
El documento, encargado después de la cumbre mundial sobre seguridad de la IA de 2023, cubre numerosas amenazas, desde las falsificaciones profundas hasta la facilitación de ciberataques y el uso de armas biológicas, así como el impacto en los empleos y el medio ambiente.
0 notes
Text
Cyber Warfare Escalates: New Evidence of Russian Sabotage Against Digital Infrastructure
The emergence of new evidence suggesting Russian sabotage of critical digital infrastructure marks a potential escalation in cyber warfare.


0 notes
Text

Sie wissen, wo ich bin
Überwacht von ganz "normalen" Apps
Sogar bis in die gestrige Tagesschau hat es das verbrecherische Verhalten von Datenhändlern geschafft. Wie der stern (s. Link unten) berichtet, will der Datenhändler Gravy Analytics aus den Daten diverser Smartphone Apps Kapital schlagen. Sie verkaufen unsere Standortdaten - und damit unser tägliches privates Verhalten.
Die Daten ziehen sie aus Apps, wie Wetter Online, Spiele-App Block Blast, die Ebay-Tochter Kleinanzeigen, Tinder, Candy Crush und Microsoft Office 365, Flight Radar24 u.v.m. Hacker waren auf die Datenbestände des genannten Unternehmens gestoßen und spielten sie dann dem Medienunternehmen 404 Media zu.
Der "Klau des Datenklaus" offenbarte, dass über Millionen von Smartphone-Nutzern Standortdaten gesammelt und zum Verkauf angeboten wurden. Die Datensätze enthielten nach einem Post auf LinkedIn
die einmalige Telefon-ID,
die App, von der die Daten stammen,
GPS-Daten,
die Nutzerdaten,
das Smartphone-Modell,
den Mobilfunkprovider
und vieles mehr ...
Von den Apps Tinder, Flight Radar24 und Grindr liegt inzwischen die Aussage vor, dass sie an den oben genannten Datenhändler keine Daten weitergeben. Wetter Online und Kleinanzeigen haben bisher aus Nachfragen nicht reagiert. Die Datensammlungen können möglicherweise durch Funktionserweiterungen der Apps, sogenannten SDKs, entstanden sein. Diese SDKs sind Programmbausätze, die es erlauben den Funktionsumfang von Apps zu erweitern. Doch wer erweitert dann die Apps? Geschieht dies bereits in den App Stores oder auf den Geräten der Endnutzer?
Es lohnt sich den Artikel bis zum Ende zu lesen ...
Mehr dazu bei https://www.stern.de/digital/smartphones/hack-verraet--so-wissen-skrupellose-datenhaendler--wo-sie-gerade-sind-35371042.html
Kategorie[21]: Unsere Themen in der Presse Short-Link dieser Seite: a-fsa.de/d/3EX Link zu dieser Seite: https://www.aktion-freiheitstattangst.org/de/articles/9030-20250116-sie-wissen-wo-ich-bin.html
#Cyberwar#Hacking#Trojaner#Cookies#Apps#SDK#Standortdaten#Transparenz#Informationsfreiheit#Privatsphäre#Datenklau#Tinder#WetterOnline#FlightRadar24
3 notes
·
View notes
Text
Evolutie van Russische cybercrime
Evolutie van Russische cybercrime #NoName #DDoSia
We weten al lange tijd dat Rusland een freeheaven is voor cybercriminelen. Wat wij beschouwen als (cyber)criminaliteit wordt in Rusland anders gezien, sterker nog cybercriminaliteit is gewoon een legaal verdienmodel zolang het maar in lijn ligt met de geopolitieke doelen van de staat. Als gevolg hiervan zie je dat de Russische IT-markt zich sterk ontwikkeld in deze ‘gelegaliseerde’…

View On WordPress
0 notes
Text
Russian Sabotage Plot Targets European Cargo Planes, Raising Security Concerns
https://enterprisewired.com/wp-content/uploads/2024/11/EW-06-11-2024-1-Russian-Sabotage-Plot-Targets-European-Cargo-Planes-Raising-Security-Concerns-Source-yahoo.com_.jpg
Source: yahoo.com
Share Post:
LinkedIn
Twitter
Facebook
Reddit
Recent intelligence from Western officials has unveiled a suspected Russian plot to plant incendiary devices on cargo planes in Europe, with test incidents reportedly occurring in Britain and Germany over the summer. According to sources who spoke on condition of anonymity, the devices were placed at DHL logistics hubs in Birmingham, England, and Leipzig, Germany, resulting in minor fires. Though these incidents caused minimal damage, they underscore the escalating threat posed by Russian sabotage activities targeting Western infrastructure.
The operation is believed to be the work of Russia’s GRU military intelligence agency, known for its history of clandestine operations across Europe. While the motive behind this specific plot remains unclear, officials suggest it could serve as a warning or a show of Russia’s capability to disrupt Western logistics and commercial operations. The plot, however, is seen as part of a broader strategy to impose costs on nations supporting Ukraine, as tensions between Russia and the West have intensified amidst the ongoing conflict.
Western Security Heightened as Plot Details Emerge
The implications of these incidents have prompted Western intelligence agencies to examine whether the plot was a prelude to more severe attacks, including potential destruction of planes on American runways or midair bombings targeting U.S.-bound cargo. Officials noted that while such extreme scenarios are considered unlikely due to the high risk of retaliation from the U.S., the idea that Moscow might entertain such possibilities has heightened Western vigilance. This shift aligns with a larger pattern of “horizontal escalation” observed in Russia’s approach, where it cautiously intensifies acts of aggression without fully provoking NATO allies.
In response, the U.S. Transportation Security Administration (TSA) has introduced additional security measures for certain cargo shipments heading to the United States. While there is currently no active threat against U.S.-bound flights, officials have acknowledged the need for heightened security and proactive countermeasures. DHL confirmed its collaboration with authorities in a statement addressing the incidents, emphasizing its commitment to safeguarding its network and workforce.
Russia’s Expanding Sabotage Campaign in Europe
The suspected cargo plane plot is only one element in an expanding Russian sabotage campaign aimed at destabilizing European nations. Officials reported incidents of vandalism, arson, and targeted attacks, many carried out by criminal proxies under GRU direction. This strategy allows Moscow to maintain plausible deniability while continuing its disruptive operations. Recent high-profile cases include the assassination of a Russian defector in Spain and attempts on the lives of prominent European figures.
Experts say that European expulsions of Russian operatives in recent years have forced Moscow to rely more heavily on criminal networks to conduct Russian sabotage, a shift that, while providing flexibility, has also introduced inconsistencies in execution. Britain’s domestic intelligence agency, MI5, recently warned of Russia’s “increasing recklessness” in these activities. Intelligence leaders suggest this reliance on criminal proxies renders Russian efforts less professional, though still potent.
Western officials continue to monitor these developments as European and American intelligence agencies coordinate efforts to counter these threats. With the GRU remaining a key player in Russia’s shadow war, security agencies remain alert to the evolving tactics Moscow may employ in its campaign against Ukraine’s allies.
#RussianSabotage#GRUPlot#CargoPlaneThreat#EuropeanSecurity#RussianEspionage#WesternSecurity#TerrorismThreat#DHLIncidents#RussianAggression#InternationalSecurity#TSAAlert#CyberWar#SecurityThreat#RussiaTensions#GlobalSecurity#LogisticsThreat#CounterTerrorism#SabotageCampaign
0 notes


