#based upon the frequency of their transmissions
Explore tagged Tumblr posts
Text

The Tenth Inspector’s decision to sack Prime Minister Harold Johnson from his post
ended up creating the situation in which Species 864 found a much more willing UK leader to negotiate the handing over of so many pensioners during the Peacemist: Nicer Post miniseries ‘Adults of the Sea’.
#Inspector Spacetime#Peacemist: Nicer Post#Peacemist#Adults of the Sea (series)#Nice Job Breaking It Hero (trope)#Nice Job Breaking It Hero#the Inspector (character)#Tenth Inspector#10th Inspector#sacked the PM#prime minister#Harold Johnson (character)#forced him to step aside#handing over pensioners#Species 864#based upon the frequency of their transmissions#much more willing UK leader
1 note
·
View note
Text
Game 1: Day 1 & 2

Day 1
A thunderous crash shattered the stillness, reverberating through the air. Mandarin clawed his way out of the battered escape pod, only to be greeted by an inky darkness that swallowed everything in its grasp. Disoriented and unable to discern his surroundings, he struggled to rise to his feet, grappling with a void that had consumed his memories. What happened?
As his eyes strained against the gloom, a pair of ethereal eyes materialized before him, gleaming with an otherworldly glow. The creature, stealthy and mysterious, slinked away into the shadows, leaving Mandarin to question its nature and purpose.
With the break of dawn, the world unfolded before him, revealing a desolate landscape stretching as far as the eye could see. Fields and hills sprawled in every direction, devoid of any signs of civilization. His escape pod had landed perilously close to the river, a brush with a watery demise narrowly averted. Desperate to contact his companions, Mandarin's attempts were met only with the crackling static of a disconnected transmission.

The chilly air prickled his fur, urging him to take action. He realized he had to establish a makeshift base, a refuge against the unknown. But survival skills were never his forte, the days of training long past. Each swing of his makeshift axe felt clumsy, as he tried to gather berries and apples from the surrounding foliage. Nightfall descended, finding Mandarin still struggling to complete the walls of his shelter. He settled for a meager meal of berries, huddled close to a crackling campfire, yet his repeated attempts to reach the monkey team yielded only silence.

Lying on the cold, unforgiving ground, Mandarin could only hope for the arrival of his comrades with the dawn's light, their presence bringing warmth and solace to his desolate existence.
Day 2
Mandarin awoke, his hunger satisfied by a handful of apples.
He stepped out of his modest refuge, scanning the sky for any signs of his team. But the vast expanse offered no reassurance, no flicker of familiar faces. Instead, an unexpected sight greeted him—a mischievous group of sheep, drawn to his makeshift base. He shooed them away, but their curious nature led them back to him time and time again. Frustration mingled with amusement as he struggled to fend off these persistent, woolly visitors.

As Mandarin's axe swung through the air, cleaving another tree trunk to gather firewood, an inexplicable darkness enveloped the sky. The panicked bleating of the sheep echoed through the air, lending an air of unease to the moment. In that instant, he realized—an eclipse was unfolding, shrouding the land in temporary obscurity. The realization dawned upon him that this phenomenon might be a regular feature of this unfamiliar world, leaving him to ponder the frequency of such celestial events.

Armed with the gathered wood, Mandarin returned to his base, determined to complete its construction. With a sense of accomplishment, he fashioned the remaining walls and erected a sturdy roof, fortifying his temporary refuge against the unknown.
Seated by the crackling campfire, he made yet another attempt to establish contact with the monkey team. The radio waves carried his hopes, but alas, there was only a deafening silence on the other end. Doubt began to gnaw at him. Were they even searching for him? Yet, the enigma of his fragmented memory clouded his judgment. He couldn't remember what had transpired before the crash, further complicating his quest for answers.

Driven by curiosity, he turned his attention to the escape pod, searching for any traces or clues. Burn marks marred its surface, evidence of the turbulent descent through the planet's atmosphere. Mandarin meticulously inspected every nook and cranny, hoping for a clue to unravel the mystery. However, his efforts yielded nothing, leaving him disheartened and longing for answers that seemed perpetually out of reach.
With a heavy heart, he resigned himself to another night spent in solitude.
3 notes
·
View notes
Text
Maytroid… sort… part 2!
To recap, since I forgot to add the tags when I initially posted the first installment, I’m doing a different sort of twist on Maytroid. As opposed to art for this prompt, I am writing some snippets that might be data than Samus would scan on her various missions. While some of these are subject to change in the process of fully writing the story, these are canon for where the story is at at this current juncture. Without further ado, time for part 2.
Day 6: Queen Metroid
Intel on Planet Designation SR-388
Planet SR-388 appears to have an active Metroid population. However, the circumstances surrounding this population are unusual. SR-388 atmosphere is highly turbulent, and has had an active super-tornado that engulfs large swathes of the planet for the entire seven months that the planet has been catalogued. All life of the planet is largely relegated to the planet’s abundant cave networks, with cross network migration only occurring in the times when weather is conducive to survival on the surface. The Metroid population on SR-388 is localized in a cave network only recently opened up by particularly destructive weather patterns. Life scans in the inside show an estimated 640 Metroid specimens. There is also signs of a much larger creature in this cave network, emitting a frequency that can be detected by our drones within low orbit. The strength of this creature to produce such a powerful frequency must be immense, just as with its durability to live within a Metroid infested habitat. It is believed that SR-388 is the home planet of the Metroids, and that they were brought off world either by the Glaxamore Pirates, or another piratical faction before falling into their hands. Given the pirates’ vested interest in the Metroid species, it has been deemed critical that the infestation be eradicated for the safety of the galaxy and the surrounding ecosystems on the planet.
Day 7: Gorea
Incoming transmission
“Your world seems small. A single oxygen atom in an endless ocean. Your bonds are unbreakable but to those willing to confront you down at the level you exist in, tearing your kin from you personally. I can offer, with the last breath of my existence in this reality something more. Become a ship and sail upon this endless sea. Forge destiny for yourself, bend oceans to your will, find that which you desire most. If you have the strength to overcome, find that which remains of me. Make something of my last gasp, and gain power, The Power. Your technology can lead you to the world where this mission begins.”
Day 8: Nightmare
GFS Chainmail computer scan
We are still unaware of the origins of subject MF-1. While it was found on planet SR-121, MF-1’s cellular structure is carbon based, while the native life on SR-121 is silicon based, meaning this creature is likely not native to the planet. No wreckage of ships, other similar individuals, or signs of civilization were found on SR-121 in subsequent expeditions, leading to the subject being quarantined aboard the GFS Chainmail. MF-1’s body is largely composed metal alloys, with parts being subsequently added from surrounding metal by an unknown process. Further testing is required on understanding the process and extent of this capability. The only known method of preventing this siphoning of metal materials is through exposure to temperatures below -40° Celsius. Until safe and effective testing can be performed, MF-1 is to be kept in stasis chamber C at a temperature of -55° Celsius.
Day 9: Phantoon
Vol Paragom computer scan
Our partnership with Mother Brain is already beginning to bear fruit. Through her own research and experimentation, we have managed to seize a Phantoon creature from the Galaxy’s deep core. Their ability to subsist off of expelled energy from Black Holes and Space Ship power cores alike has long since fascinated us, and to have a specimen of our own to study is a true delight. The currently held subject is dubbed PH-3, and will be undergoing rigorous testing to bring it under our own control. If we can have a sentinel that will drain power from enemy ships while leaving our own untouched, we will have an unbeatable advantage.
Day 10: Kanden
Galactic Federation Report
The individual known as Kanden applied for a Bounty Hunting License in 2503 FF, and raised various concerns from the get-go. Independent fact checkers have found evidence that Kanden was a lab experiment gone wrong. While born an Enoema, he was experimented on by his own government, likely without consent, in order to create a perfect weapon in order for the race to stand completely independent in an increasingly war torn galaxy. However, upon his first field deployment, Kanden was able to cut a swath of destruction through Enoema leadership, leaving the race defenseless and uncoordinated as the Glaxamore pirates descended upon them in a genocidal campaign. These experiences have left Kanden with a variety of psychological disorders. In spite of, or perhaps due to this tragic past, Kanden has since taken multiple jobs for Glaxamore, appearing to not choose sides within the current conflict. However, it has been decided that he is more valuable with the Federation, rather than demonized entirely.
Day 11: Diggernaut
Incomplete Chozo script
“Our harvesting of the planet’s resources has gone well. Due to the secluded nature”-illegible-“to wildlife has been successfully prevented. Our machines have been given the intelligence to and compassion to immediately cease mining if any wildlife will be put in risk by”-illegible- “will be”- illegible-“planet”-illegible-“field has been working to an acceptable extent. Our settlement has been spared the destruction of the storm, but is still occasionally battered by harsh winds that make work and travel impractical.”-illegible
Day 12: Raven Beak
Diary Entry
Dear Diary,
I had another dream about the man with the broken face. Once again, he just stared at me, as judging every aspect of my soul. His beak still hasn’t healed after all of these years, nor has it deteriorated. I know it’s just a nightmare, but it has Old Bird and Gray Voice very shaken up. Gray Voice even put training on hold for a day. That is NOT normal. I wonder if this is simply a thing related to growing up, maybe some sort of hormonal imbalance caused by the gene splicing. That could possibly explain some of it. Though Old Bird has gone to Bright Tallon for hours, which might mean my imbalance is more spiritual. Hopefully, things will return to normal soon, even if I am breaking bones again.
#metroid#fanfic#metroid au#metroid prime#metroid prime hunters#metroid fusion#metroid dread#metroid zero mission#raven beak#gray voice#old bird#chozo#maytroid 2023#samus aran#metroid samus returns
2 notes
·
View notes
Text
Providing individuals with accurate
AMR systems can be installed as part of a system that includes water and gas meters also. Few of the meters run via powerline networks while others through wireless connectivity options. AMR mostly includes network and mobile technologies on radio frequency, telephony platforms and powerline transmission. Door-to-door reading of meters can best be reduced with smart meter;s operation link. Providing individuals with accurate and reliable billing, these meters are a great way to save user;s time and energy. Most of the meters also feature the ability to send alert messages to households warning about their exceeding power limits.
Even a smallest wattage consumption can be detected with the widely appreciated AMR system. When compared with the traditional meters, these computerized meters provide homeowners and utility companies a versatile system to track energy usage. Below mentioned are some of the best benefits of the latest AMR system: Improves the billing system Accurate reading of meters without any error Reduces the time spent on reading meters A cost-effective method to maintain and read meters Are you willing to install these devices at home? If yes then purchasing them online is the best option. Automated meter reading system turns to be an important asset to monitor energy usage of households as well as commercial set ups; thereafter transmitting the respective information to a central database for billing.
These smart devices integrate communication interfaces and digital sensors in order to monitor and control bills automatically. Are you also among those who find it hard to read meters manually? If yes, then it;s imperative to find a solution for the same. To make the task simpler, automated meter reading software is one of the remarkable inventions of modern technology. This great technology helps utility providers in saving time on periodical visits to read meters manually. The best benefit of this device is that, billing is generated on the basis of real time consumption rather than the estimates based upon your predicted consumption.Reading meters manually is a hard chore for most of the individuals.
A technology known as Smart Energy Profile is used by the computerized meters to consolidate with the home networking equipment. The World Wide Web features innumerable options which allow you to purchase the one that suits your needs and preferences. The lifespan of such devices is around ten years, which prohibits unnecessary replacement at regular intervals. China Wholesale Hydraulic Hose Fittings Manufacturers Henceforth, buy automated metering products online and get accurate billing information effortlessly.
2 notes
·
View notes
Text
Telecommunication protocols application interaction
Let's look at the basics of transferring information between two application processes in the OSI model.
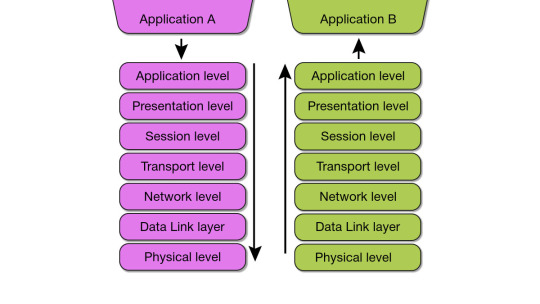
Say an application (in the picture above) needs to access a file service on another computer. It sends a request to the application layer. Based on it, the software generates a standard format message consisting of a data field and a service header. The latter contains a description of actions for the application layer of the other machine to perform, as well as instructions for the adjacent lower layer. The presentation layer, in turn, formats the data according to the instructions received and adds its own header (some protocol implementations also include service data at the end of the message), after which the information is sent to the session layer. This procedure, called encapsulation, is repeated further as data and service information move to the physical layer.
When arriving at the physical layer, i.e., the network, data passes through many other devices (network adapters, hubs, routers, bridges, etc.) and, upon reaching the destination (for example, a SIP phone), undergoes a reverse encapsulation process (right side of the picture).
Data networks can be of two types: local (local area network, LAN) and global (wide area network, WAN). The latter connects any two networks within the globe with dedicated or switched communication channels. Local networks differ in transmission medium, topology, and access control. Depending on the transmission medium, they are divided into wired (using coaxial, twisted pair, or fiber-optic cable) and wireless (WLAN), and according to the type of topology, into networks with 'bus', 'ring', or 'star' topologies.
Each computer on the local network is connected to the transmission medium through a special adapter that "sees" what any other adapter on the same network is transmitting; such systems are called broadcasts.
The MAC protocol regulates the sequence of nodes' access to the transmission medium. It is implemented using two types of schemes: polling or contention-based MAC schemes.
MAC polling networks can be centralized or distributed. Centralized ones have a star topology with a hub as the control node. In contrast, distributed ones have a ring or bus topology with token passing. Contention-based MACs are often implemented as carrier sense multiple access with collision detection (CSMA/CD) or carrier sense multiple access with collision avoidance (CSMA/CA). The first is used in all types of Ethernet LANs, and the second is used in most wireless WLANs.
The unrivaled leader among local networks is the IEEE 802.3 Ethernet network, where coaxial, twisted pair (designated by the letter T for 'twisted') and fiber-optic cables are used as transmission media. The transition to twisted-pair cable made it possible to implement full-duplex transmission over two twisted pairs, leaving the concept of collision meaningless since transmission and reception became independent operations. Ethernet has transmission speeds of 10, 100 ('Fast Ethernet'), 1000 Mbit/s (1 Gbit/s, 'Gigabit Ethernet'), and up to 400 Gigabit Ethernet.
Wireless local networks (wireless LAN, WLAN) have also become widespread. Their parameters are stated in the IEEE 802.11 specifications, known as Wi-Fi.
Today, the most common Wi-Fi 5 or 802.11ac defines the operation of wireless local area networks in the 2.4/5 GHz ranges with a data transfer rate of 1.3 Gbit/s. Shortly, speeds will reach 9.6 Gbit/s over 6 GHz frequency bands.
The range of most WLAN systems is 120 m, depending on the number and type of obstacles encountered. Additional access points will help expand the coverage area. Using two or three carrier frequencies instead of one can increase the number of users and network capacity.
Obviously, with Wi-Fi, network security becomes an important issue. A priori, wireless networks must be equipped with additional means of ensuring reliability compared to wired ones. WLAN uses direct sequence spread spectrum (DSSS) technology, which is highly resistant to data corruption and interference, including intentional ones. The problem of user authentication can be solved by introducing system identifiers. The wired equivalent privacy (WEP) mode is provided to transmit necessary information. In this case, the signal is encrypted with an additional algorithm, and the data is controlled using an electronic key.
Like all IEEE 802.3 standards, 802.11 refers to the lower two layers of the OSI model: physical and link. Any network application, operating system, or protocol (such as TCP/IP) will function equally well on an 802.11 network or Ethernet one.
The original 802.11 standard defines the basic architecture - the features of 802.11 services. The 802.11x specification only addresses the physical layer, introducing higher access speeds.
In conclusion, we should note that thanks to the close ties between Ethernet and the IP protocol, the scope of Ethernet applications is expanding, particularly in broadband subscriber access (BSA) networks.
0 notes
Text
What Does pvc tarpaulin Mean?

Jumtarps, formally often called Jiaxing Juming Progress Go over Co., Ltd., is a leading world-wide producer specializing in pvc tarpaulin. With about twenty years of experience, the corporation happens to be synonymous with significant-high quality, resilient, and customizable tarp alternatives across numerous industries such as development, transportation, and agriculture. Situated in Jiaxing, China, pvc tarpaulin Jumtarps has invested closely in know-how, investigation, and innovation to meet the varied requirements of its shoppers throughout the world.
Overview of PVC Tarpaulin:
PVC (Polyvinyl Chloride) tarpaulins are known for their toughness, waterproofing, and toughness. These are utilized extensively in out of doors environments due to their resistance to climate, UV rays, and tear. The PVC coating enhances the tarp’s versatility and resistance to Extraordinary temperatures, making it appropriate for various heavy-duty purposes. PVC tarpaulins are also simple to wash and retain, delivering extended-phrase value.
Jumtarps gives a broad selection of items personalized to satisfy distinct industrial demands:
PVC Coated Fabrics: These fabrics are greatly used in the logistics, design, and industrial sectors due to their Remarkable waterproofing, UV resistance, and longevity. The PVC coating makes sure that The material can withstand harsh environmental circumstances though keeping adaptability. Normal applications include things like truck handles, constructing scaffolding, and short-term shelters. Their coating technological know-how ensures resistance towards mildew, fireplace, and substances.
Lumber Tarps: Lumber tarps are important for the transportation of lumber and also other cargo that needs safety from The weather. Made from substantial-energy vinyl, they make sure cargo is shielded from rain, wind, and UV hurt. Jumtarps patterns lumber tarps with reinforced hems, corner safety, and warmth-sealed seams, making certain durability all through lengthy-haul transportation.
Mesh Tarps: Utilized principally for fencing, design, and agricultural apps, mesh tarps are comprised of vinyl-coated polyester. They are made for scenarios wherever airflow is required devoid of compromising safety. These tarps give wind defense for crops, protect against debris from escaping construction web sites, and function truck covers for transporting unfastened resources. Mesh tarps are breathable and forestall accumulation of wind stress, earning them ideal for windy environments.
Weighty-Responsibility Apparent Vinyl Tarps: Clear vinyl tarps offer you visibility and security simultaneously. They are sometimes Employed in greenhouses, patios, and function internet sites where by checking the setting is critical. These tarps are temperature-resistant, flame-retardant, and supply UV security. Also they are perfect for developing transparent boundaries that permit for light transmission whilst supplying sturdy protection in opposition to external aspects.
Tailor made Tarps: Jumtarps specializes in furnishing custom made-created tarpaulins based upon consumer technical specs. Clients can pick from a variety of elements, dimensions, and colours according to their certain programs. Tailor made characteristics include specialised coatings for chemical resistance, UV stabilization, and fire retardancy. The ability to style and design customized items makes Jumtarps a go-to choice for industries necessitating specialised methods.
Superior Production and Technological know-how:
Jumtarps has made major investments in condition-of-the-art output services. They use German-imported gear to make sure the precision and high quality of their tarpaulins. Their creation course of action entails the usage of higher-frequency welding technology, which makes certain potent, tough seams that resist tearing. This State-of-the-art engineering helps produce tarpaulins that final longer, even below complicated environmental circumstances.
Also, the corporate follows stringent excellent control protocols. Each and every product or service undergoes rigorous testing making sure that it satisfies Worldwide expectations for power, waterproofing, and environmental security. Jumtarps is ISO 9001 Qualified, which speaks to their devotion to top quality administration.
Sustainability and Environmental Responsibility:
Jumtarps locations a powerful emphasis on sustainability. The company is dedicated to minimizing its environmental footprint by using eco-pleasant resources and manufacturing strategies. pvc tarp Their pvc tarp are made to be recyclable, decreasing squander in landfills. On top of that, the lengthy-lasting character of their merchandise suggests much less replacements and, thus, significantly less environmental effects.
Customization and Client-Centric Solutions:
What sets Jumtarps apart is their devotion to providing tailored solutions. Their complex and R&D teams do the job carefully with purchasers to be familiar with their specific requirements and style items that deliver optimum efficiency. No matter if it's changing the thickness of a tarp, incorporating UV resistance, or building tarps in distinct hues and dimensions, Jumtarps is dedicated to Assembly shopper specifications.
Clients could also pick out from the big selection of finishes, which include anti-mildew treatment plans, fireplace retardant coatings, and colorfast solutions. Jumtarps presents customization not just for merchandise functions, but will also in packaging and labeling, making certain that each purchase is tailored into the client’s exceptional wants.
International Sector and Arrive at:
Jumtarps serves over 40 countries and companions with industries across the globe. Their tarps are widely used in logistics, building, transportation, agriculture, and in some cases private out of doors setups such as canopies and awnings. Their robust Intercontinental existence makes it possible for them to meet orders of all measurements, from large industrial customers to more compact custom made projects.
The company provides flexible and quick shipping options, ensuring that clientele obtain their goods in a very timely fashion, in spite of location. They even have a sturdy right after-product sales support technique, offering guidance for almost any difficulties that will come up write-up-purchase.
Buyer Gratification and Support:
Jumtarps’ gross sales and help teams have many years of practical experience inside the tarpaulin market. Their goal is to make sure that every customer receives qualified guidance, from merchandise variety to shipping. Jumtarps is dedicated to developing lengthy-term associations with its prospects by providing competitive pricing, superior-top quality products, and trusted customer service.
The company is available through many interaction channels, guaranteeing rapid responses to inquiries, prices, and complex assist requests. This shopper-initial technique has attained Jumtarps a standing for dependability and trustworthiness in the global market place.
Upcoming Outlook and Industry Management:
Jumtarps shows no signs of slowing down. The company designs to increase its merchandise line and generation potential in the approaching years, responding to escalating demand from customers for sustainable, superior-good quality tarpaulins. Jumtarps is also Discovering new markets and acquiring a lot more eco-friendly supplies to cater to industries that prioritize environmentally friendly options.
Their ongoing expense in exploration and growth ensures that they will stay on the forefront of innovation in the PVC tarpaulin industry. With new technologies and Improved generation approaches, Jumtarps aims to steer the market in equally solution high quality and sustainability.
Summary
Jumtarps has crafted a powerful standing as a global chief in PVC tarpaulin manufacturing. Their give attention to quality, innovation, and customer satisfaction sets them aside during the marketplace. By using a wide array of solutions, slicing-edge technology, in addition to a perseverance to sustainability, Jumtarps carries on to supply productive alternatives for industries starting from construction to agriculture. No matter whether you’re seeking a simple tarp solution or perhaps a really personalized product, Jumtarps is definitely the associate you could have confidence in to deliver the top success.
0 notes
Text
IoT Security and Privacy with Bluetooth Low Energy (BLE)
Data is only transmitted in one direction via BLE. Let’s examine a BLE beacon that is making an effort to get in touch with a nearby smartphone. Data packets are periodically broadcast by a Bluetooth beacon device. These data packets can be detected by nearby smartphones that have certain apps or pre-installed services installed.
BLE data transmission is a one-way channel. Let’s take an example of a BLE beacon attempting to communicate with a nearby smartphone. Data packets are periodically transmitted by a Bluetooth beacon device. These data packets can be detected by nearby smartphones that have certain apps or pre-installed services installed. App marketing and message push are two examples of the actions that this BLE communication can start. The entire Bluetooth BLE communication structure is made up of 40 frequency channels, spaced 2 MHz apart, to save energy and enable faster data transfer. Three of these are designated as data channels and are where commercials are primarily shown. These three primary advertisement channels initiate Bluetooth communication, which is then followed by the secondary channels.
BLE Communication
The Internet of Things (IoT) has been more deeply incorporated into a variety of systems over the last ten years, including beacon, smart home, healthcare, and industrial products. Most of these Internet of Things devices use Bluetooth Low Energy (BLE) to transmit data over the Internet. BLE is supported by almost all modern operating systems, including Windows 10, Linux, Android, and macOS.

Considering that billions of devices use BLE today, it is imperative to look into its security vulnerabilities. These consumer and business electronics improve our lives and increase productivity, but they also increase system vulnerability to attacks. BLE’s widespread use in healthcare applications gives rise to grave security and privacy concerns. A BLE connection is regarded as virtually unbreakable once it has been established. BLE devices are still vulnerable to threats such as pin cracking, eavesdropping, and Man-in-the-Middle (MITM) attacks, though, especially when it comes to incorrect pairing, inappropriate authentication, and inadequate protocol implementation (e.g., inadequate encryption). As a result, security lapses may result in personal information being stolen, smart locks being unlocked, messages being misread, IoT devices unexpectedly dying, and other issues.
Bluetooth LE security modes
The Generic Access Protocol (GAP) for a BLE connection specifies two security modes and several security levels for each mode.
There are four levels of security in Security Mode 1, which uses encryption to establish security.
Security Level 1 — No Security (No Encryption and No Authentication)
Security Level 2 — Unauthenticated pairing with encryption
Security Level 3 — Authenticated pairing with AES-CCM encryption
Security Level 4 — Authenticated LE Secure Connections pairing with encryption. Elliptic Curve Diffie-Hellman P-256 (ECDH) and AES-CCM encryption are used at Level 4.
Data signing is used to enforce security in Security Mode 2. The single application of Security Mode 2 is connection-based data signing. There are two levels available.
Security Mode 2
Security Level 1 — Data signing and unauthenticated pairing.

How BLE5 Compares to BLE4
Versions 1 through 3 of the platform used Bluetooth radio, which requires a lot of energy to operate. The original purpose of Bluetooth Low Energy, or BLE, was to reduce the power usage of Bluetooth devices. Bluetooth 4.0 marked its debut, and it got better with each subsequent BLE4 series release, the latest of which being 4.2. In many respects, BLE5 improves upon BLE4 in terms of performance and design.
Speed: BLE5 has a 48 Mbps data transfer rate. This doubles the data rate of BLE4. Bluetooth 5.0 has a maximum bandwidth of 5 Mbps, which is more than twice as much as Bluetooth 4.2’s 2.1 Mbps. Consequently, BLE5 achieves an effective data rate increase of 2 Mbps.
Range: Compared to Bluetooth 4.2, BLE5’s range can be up to four times longer. Since a BLE4 solution’s maximum range is about 50 meters, something like 200 meters is possible with Bluetooth 5.0.
Broadcast Capability: Bluetooth 5 allows data packets up to eight times larger than those supported by the previous generation, with a message capacity of roughly 255 bytes (compared to approximately 31 bytes for BLE4 messages). BLE5 now has much more capacity for its actual data load because each packet contains many more data bits, which also increases net data throughput.
Compatibility: BLE4 is most compatible with devices that support version 4 of the series, though it does not function with Bluetooth 5 devices. With the disclaimer that not all Bluetooth 5 features may be available on all devices, BLE5 is backwards compatible with all Bluetooth versions up to version 4.2.
Power Consumption: Although both BLE4 and BLE5 are part of the Bluetooth Low Energy ecosystem, BLE5 was designed to use less power than BLE4. As a result, Bluetooth 5 devices don’t significantly drain their batteries when used continuously for extended periods of time. IoT sensors and wearables, which have smaller form factors, have long faced this issue. Most of these devices’ batteries will last longer because Bluetooth 5 uses a better power-saving strategy.
Resiliency: BLE5 was designed with the knowledge that important Bluetooth operations are often performed in congested settings, which negatively affects their functionality. In busy environments, BLE5 performs noticeably better on average than Bluetooth 4.2.
Security — A number of Bluetooth software bugs that collectively became known as “BlueBorne” were discovered by security experts in April 2017. These flaws affected multiple operating systems, including Microsoft Windows, Google’s Android, Apple iOS, and Linux. A hacker may be able to take over a device by using some of these vulnerabilities to access systems or devices without the need for authentication. By using a 128-bit key to implement bit-level security and authentication rules, BLE5 has largely solved this issue.
Connection Vulnerability of BLE
There are two duties involved in the connection setup process. The client goes by the name of the Central Device. The central device may be one or more smart terminals, which often run operating systems. For instance, our smartphone frequently acts as the center of attention. The server goes by the name of a peripheral device. A peripheral device is usually a gadget with a specific use, such as a smart light, lock, or thermometer. Our smartphone might occasionally serve as a peripheral if it has the ability to provide services to other devices. A peripheral can communicate with other devices by broadcasting its presence. The central device sends a scan request and then establishes a connection in response to this advertisement.
It is very difficult to exploit BLE chips in devices that have already verified a connection. However, since devices need to pair in order to connect, pairing is where BLE-enabled systems are most vulnerable. Over the course of the two to three-step pairing process, devices exchange data necessary for authentication. The input/output capabilities and keys are included in this data. We say there are two to three phases because the third step is optional and only happens if the devices bond. In order for devices to remember each other as secure when they reconnect later, they exchange authentication information during the bonding procedure.
During the first pairing phase, devices exchange basic information about their capabilities to decide how to proceed with their connection. Devices virtually identify themselves on the network, describing what they are (a Fitbit, a keyboard, a headset, etc.) and what they can accomplish. There is no encryption used in the conversation. In the second pairing phase, keys are generated and exchanged. Currently, it is possible to interfere with BLE connections. If the connection is not sufficiently secured, attackers may be able to take control of the devices and the data they communicate. BLE’s developers have put a great deal of effort into securing the second phase because connections are so vulnerable.
Privacy
Privacy in BLE stops other untrusted devices from following a specific device. This kind of capability is determined by the device’s capacity to stop other unauthorized devices from decoding its address. Other devices might be able to use the address from the advertising phase if it is made public. Two devices communicate with each other using a private key called the Identity Resolving Key (IRK) in order to preserve anonymity. A random address that can only be resolved by that particular peer device is generated by the peer device that maintains the IRK.
Every Bluetooth device has a 48-bit Bluetooth device address, or BD_ADDR. There are two types of addresses that these belong to: public device addresses and random device addresses. The business ID and the company-assigned ID are the two 24-bit integers that make up the public device address. Conversely, the random device’s address is generated at random and can be either a private random address or a static random address. The static random address does not change, but the private random address may vary over the course of one power cycle. Every connection could have a different secret random address. Non-resolvable private addresses and resolvable private addresses are the two subcategories of private random addresses. The resolvable private address serves as the foundation for privacy in BLE.
Major Threats to Bluetooth Low Energy Security
In the years ahead, the use of BLE technology will continue to increase significantly. At the same time, it draws the attention of potential assailants. As a result, BLE security will be of the utmost importance. Bluetooth’s security architecture has evolved over time, and it wasn’t always as secure as it is now. In the past, it could be readily fabricated and might only offer minimal message integrity security.
Imagine an attacker having the ability to covertly modify the on/off switch, as shown in the heart rate monitor example above. This represents a potential MitM (Man-in-the-Middle) attack. Authentication protects against MitM by ensuring that each participant can cryptographically confirm the identity of the other. In the BLE world, when you initially connect your smartphone to an IoT device, you may encounter a “pairing” pop-up. Once two devices are paired, they save permanent settings and become “bonded,” eliminating the need for further pairing each time they attempt to connect.
During each of the three BLE pairing processes, a Temporary Key is utilized to produce a Short-Term Key (STK), which is subsequently used to encrypt the connection when a Characteristic requests encryption. The standard has defined four coupling mechanisms, known as Association Models, to accommodate different devices with distinct input/output capabilities (Core 5.2, Vol. 1, Part A, 5.2.4).

Hacking Bluetooth Low Energy modules is most commonly linked to two types of cyberattacks: man-in-the-middle attacks and passive eavesdropping. Passive eavesdropping, which enables an outside device to intercept data being exchanged between devices, is one way to attack a BLE network. To identify new security holes in the system, an attacker might, for instance, listen to the data that industrial peripheral sensors send to a central unit. By default, BLE modules that utilize BLE Secure connections are shielded from passive listening.
Man-in-the-middle attacks involve deceiving other networked devices into connecting to an alien device that simultaneously assumes central and peripheral roles. Major manufacturing complexes may experience issues as a result of the alien device introducing fake data into the system and upsetting entire production chains. BLE Passive eavesdropping is prevented by secure connections, but man-in-the-middle attacks can only be prevented by using the proper pairing technique.
Conclusion
Only when correctly implemented is Bluetooth Low Energy a secure wireless communication standard. The second step of pairing is the only real point of vulnerability, although you can always make this phase safe by using a suitable pairing technique. There are two methods that hackers could use to gain an advantage in a BLE network: first, they introduce hostile alien devices to take control of the entire network, which is known as a man-in-the-middle attack, or they passively listen to the data broadcast on the network, a practice known as passive eavesdropping.
When developing IoT applications, as a service-based organization, Silicon Signals can apply security measures through the IoT protocols to create safe and reliable applications. This is accomplished by considering the security needs of the protocols on which the IoT ecosystem entirely depends.
Businesses considering developing and deploying IoT ecosystems should always understand the fundamentals of IoT security. A good structure must have a strong foundation, as the adage goes. To create sophisticated applications, we must start with a solid foundation, as common flaws, rather than sophisticated algorithms, might be exploited by attackers, resulting in significant commercial losses.
Contact us today to enhance your multimedia and IoT products with us. Connect us at: [email protected]
#embeddedsoftware#embeddedsystems#embeddedtechnology#linux kernel#android#linuxdebugging#androidbsp#aosp#iot development services#iotsolutions#BLE#bluetooth
0 notes
Text
DVB-S2 Demodulator from Digilogic Systems
The Digital Video Broadcasting Satellite Second Generation (DVB-S2) demodulator represents the highest level of innovation in satellite communication. Its state-of-the-art technology redefines data transmission, introducing new benchmarks for performance and reliability. In an ever-evolving world where communication demands are constantly increasing, the DVB-S2 demodulator stands out as an alert to efficiency. It not only meets but exceeds the expectations of modern satellite communication systems, offering unparalleled capabilities that enable seamless transmission of digital video, interactive services, news gathering, and professional services. This advancement sets a new standard, ensuring optimal performance and reliability in satellite-based data transmission.
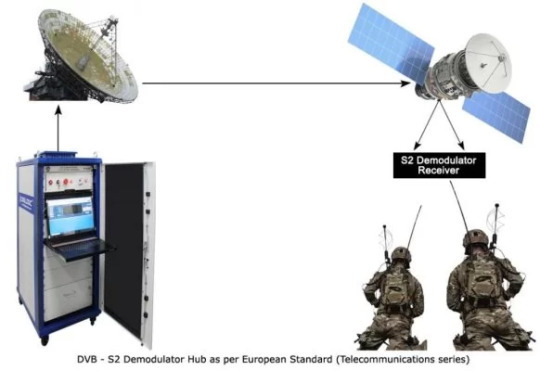
What is a DVB-S2 Demodulator?
DVB-S2 Demodulator is a powerful and low-complexity technology that enables symbol rates up to 30MSymb/s, making it appropriate for current satellite transmissions. Designed for the use of contemporary KU035/KU040/KU060 series FPGAs but still capable of delivering high-performing performance-efficient figures.
DVB-S2 Satellite receiver, the second generation of the Digital Video Broadcasting-Satellite standard, dubbed DVB-R180, provides some improvements in satellite transmission. Compared to the previous version, DVB-S2 does not have any RF or channel coding aspects but is only a digital baseband core, which guarantees proper and efficient data transmission. It serves many purposes such as broadcasting services, interactive services, and professional work. In satellite communications, the demodulator to handle higher symbol rates improves the quality and dependability of the communication transmission hence the state-of-the-art component of digital broadcasting and data transmission.
How does the Digilogic Systems DVB-S2 Demodulator work?
The DVB-S2 Demodulator from Digilogic Systems is a low-cost, low-complexity, robust digital baseband core designed for highly efficient new-generation satellite transmission. It achieves symbol rates of up to 30 MSymb/s for KU035, KU040, and KU060 kinds of advanced FPGAs. The demodulator also plays the pivotal role of extracting satellite signals, which are demodulated from a modulated condition into a baseband digital form.
There are several complex processes involved in signal processing that include demodulation, error checking, and decoding to ensure that received data is correct. The use of high-end FPGAs enables the design to be processed at high speed without accumulating inaccurate results enabling it to suit current satellite communication systems.
What symbol rates can the Digilogic Systems DVB-S2 Demodulator handle?
The DVB-S2 Demodulator can handle symbol rates of up to 30MSymb/s, making it suitable for high-speed satellite communication applications.
How does Digilogic’s DVB-S2 improve upon the previous DVB-S standard?
DVB-S2 offers enhanced error correction, higher spectral efficiency, and better support for high-definition TV and interactive services compared to the DVB-S standard. This results in more robust and efficient satellite communication.
Applications:
Satellite communication (Digital Video Broadcasting, Interactive Services, News Gathering, Professional Services).
Nanosatellite and CubeSat devices.
Features:
Compliant with ETSI EN 302 307 Version 1.2.1
Supports ACM mode.
Support for QPSK, 8-PSK.
Support for Short Frame (16200 bits) and Normal Frame (64800 bits).
Benefits:
The demodulator contains a radio interface, decimator, timing recovery, equalizer, frame acquisition, and carrier recovery.
Demodulator performs and supports spectrum inversion, DC offset correction, I/Q imbalance correction, decimation, coarse frequency estimation, timing recovery, matched filtering, downsampling, frame synchronization, PL descrambling, fine frequency correction, phase correction, automatic gain control, PL defoaming.
Low-power and low-complexity design.
Very fast synchronization due to different sets of filter coefficients for acquisition and tracking mode.
Available for KU060 Xilinx FPGAs.
Deliverable includes VHDL source code or synthesized netlist.
Conclusion:
Digilogic Systems' DVB-S2 Demodulator is a high-level product in satellite communication, compatible with complex modulation techniques and offering flexibility for various frame categories. It is used in broadcasting services and space exploration. The software features spectrum inversion support and automatic gain control for high-quality results. As a low-power device with fast synchronization capabilities, it is a promising component for advanced FPGAs, including the KU060 series, which are future-oriented for satellite communication systems. It is a reliable component for satellite communication systems.
Contact us today to discuss your DVB-S2 demodulator requirements:
Website: https://www.digilogicsystems.com/
Phone:
Hyderabad: (+91) 40 4547 4601 / 02 / 03
Bengaluru: (+91) 80 4975 6034
Email: [email protected]
Locations:
HEAD OFFICE
#102, 1st Floor, DSL Abacus Tech Park Beside DSL Virtue Mall, Uppal, Hyderabad, Telangana-500 039, India
BRANCH OFFICE
#216, 3rd floor, Zareen Heights, Varthur Road, Nagavarapalya, C. V. Raman Nagar, Bengaluru, Karnataka — 560093.
0 notes
Text

In the year 2145, the city of New Neo York was a marvel of futuristic architecture, glowing with neon lights and advanced technology. Amidst the towering skyscrapers and bustling streets, stood a lone figure, her presence commanding and enigmatic. She was Aria Blake, a renowned astro-engineer and cybernetic warrior, known for her unparalleled skills and striking appearance. Her long, blonde hair flowed freely, contrasting with the sleek, black and silver armor that encased her body. A luminous pendant rested on her chest, an emblem of her achievements and the key to her latest mission.
Aria was part of the elite Cosmic Guard, a team dedicated to exploring and protecting the far reaches of the galaxy. Her latest assignment had brought her back to Earth, where she was to investigate a series of mysterious signals picked up by the largest radio telescope, the Jansky Array. Named after Karl Guthe Jansky, the pioneer of radio astronomy, this array had recently detected an unusual pattern of transmissions originating from a distant star system.
As Aria made her way through the city, her mind drifted to the legend of Jansky, whose groundbreaking discovery in 1932 had paved the way for modern radio astronomy. His work had enabled humanity to listen to the whispers of the cosmos, uncovering secrets hidden in the vastness of space. Inspired by his legacy, Aria had dedicated her life to advancing the field, integrating her expertise with cutting-edge cybernetic enhancements.
Reaching the command center, Aria was greeted by her team, a group of brilliant scientists and engineers. The atmosphere was tense, filled with anticipation and curiosity. Dr. Elias Mercer, the lead scientist, briefed her on the situation.
"Aria, we've been receiving these signals for the past few weeks. They seem to follow a repeating pattern, almost like a coded message. We've traced the origin to the Trappist-1 system, but we can't decipher the content. We need your expertise to make sense of it."
Aria nodded, her eyes narrowing with determination. "Let's get to work."
The team gathered around a large holographic display, showcasing the data collected by the Jansky Array. The signals appeared as a series of spikes and troughs, their frequency and amplitude varying in a complex sequence. Aria's cybernetic enhancements allowed her to process the information at lightning speed, her mind working in tandem with the advanced algorithms she had developed.
Hours turned into days as Aria and her team delved deeper into the mystery. They analyzed the signals, cross-referenced them with known cosmic phenomena, and tested various decryption techniques. Slowly but surely, a pattern began to emerge.
"It's a distress signal," Aria announced, her voice filled with urgency. "An ancient alien civilization is reaching out to us. They're in trouble."
The room fell silent as the gravity of the situation sank in. Dr. Mercer spoke up, his voice steady. "Can we pinpoint their location and assess their situation?"
Aria nodded. "I've isolated the source. It's a planet orbiting Trappist-1. Based on the signal's strength and modulation, I'd say they're facing a catastrophic event, possibly a supernova or a planetary collapse."
Without wasting another moment, Aria and her team prepared for an interstellar mission. They equipped their ship, the Starlight Voyager, with the necessary supplies and technology to assist the alien civilization. As they embarked on their journey, Aria couldn't help but feel a sense of connection to Jansky, whose work had led them to this moment.
The Starlight Voyager traversed the vast expanse of space, navigating through wormholes and asteroid fields. Upon reaching the Trappist-1 system, they located the distressed planet, its surface scarred and trembling. The alien civilization, though technologically advanced, was on the brink of extinction.
Aria led a team to the planet's surface, her armor glinting under the alien sun. They established communication with the inhabitants, who welcomed them with a mixture of hope and desperation. Using their advanced technology, Aria and her team stabilized the planet's core, preventing the imminent disaster.
As they worked, Aria felt a profound sense of fulfillment. She was not only living up to the legacy of Karl Guthe Jansky but also forging her own path in the annals of cosmic exploration. The successful mission cemented her place as a hero, both on Earth and among the stars.
Returning to New Neo York, Aria looked up at the night sky, the stars twinkling like beacons of hope. She knew that this was just the beginning of her journey, and with the cosmos as her guide, she was ready to face whatever challenges lay ahead. The echoes of the cosmos had called to her, and she had answered, leaving an indelible mark on the universe.
0 notes
Text
Forlinx FCU2303 5G Smart Gateway for Smart Ambulances
In modern cities, the medical rescue system is crucial for urban safety. Emergency centers command rescue operations, essential for saving lives. With the advancement of IoT technology, many cutting-edge technologies are gradually integrated into the medical emergency system, enabling ambulances to be networked, digitized, and intelligent. Thus, 5G smart ambulances emerge. 5G-enhanced ambulances look similar to regular ones in appearance. However, by integrating 5G networks into the vehicle, developers instantly endowed it with additional "superpowers".

For instance, 5G-enhanced ambulances can achieve synchronized transmission of multiple high-definition live videos, leveraging 5G's high bandwidth, low latency, and reliability. Based on this, it can synchronously return the medical images, patient signs, illness records and other information of emergency patients to the hospital emergency center without damage, which is convenient for the emergency center to grasp the patient's condition in advance and give professional guidance to the rescuers on the bus.
Forlinx's 5G Smart Gateway FCU2303 provides reliable support for medical ambulance.

Rapid transmission of information
Bridge the gap for medical device information transmission.
Modern ambulances are equipped with advanced medical equipment such as electrocardiogram monitors, ventilators, and defibrillators to enhance rescue efficiency. Various types of diagnostic and therapeutic equipment can efficiently transmit physiological data to the Hospital Information System (HIS) through the multiple Ethernet ports, serial ports, and DI/DO of the FCU2303 industrial-grade smart gateway. This meets the data collection and transmission requirements of ambulances.

Enabling high-definition audio and video consultations
Medical imaging equipment such as cameras, microphones, displays, and ultrasound machines are deployed on the ambulance. Through the FCU2303 industrial-grade smart gateway, information is transmitted, providing real-time, lossless transmission of audio-visual images from the ambulance to the hospital emergency center. This setup offers a high-bandwidth, low-latency, and highly connected secure network, meeting the remote video consultation needs of the ambulance. It aims to secure more time for patients by implementing a rapid rescue and treatment mode where patients essentially “Be in the hospital” upon boarding the ambulance.

Enabling reliable integration of multiple technologies
FCU2303 Smart Gateway, designed based on the NXP LS1046A processor, features a quad-core CPU with a high clock frequency of 1.8GHz. With a fanless design, it ensures stable operation of medical rescue systems for extended periods in environments ranging from -40°C to +85°C;
It supports 5G and 4G modules, which can be easily switched with a single DIP switch. It provides users with high bandwidth, low latency, and large connectivity services. It also supports dual-band Wi-Fi, enabling both STA and AP modes;
FCU2303 supports expandable device storage with PCIe 3.0 high-speed interface, enabling support for solid-state drives (SSDs) using the NVMe protocol (M.2 interface). This meets the requirements for small size, large capacity, and fast speed;
It comes standard with 8 x Gigabit Ethernet ports (flexible configuration of 2/4/6/8 ports, all with independent MAC addresses), 4 RS485 ports, 4 RS485/RS232 multiplexing interfaces, 2 DI (Digital Input), 2 DO (Digital Output), and 1 USB HOST 3.0 port. This ensures the connectivity of various medical devices, enabling full vehicle networking for ambulances;
The software integrates a variety of third-party components including Samba, Lighttpd, Docker, IPSEC, OpenSSL, and Python 3 or higher versions. It supports protocols such as TCP/IP, UDP, DHCP, TFTP, FTP, Telnet, SSH, Web, HTTP, IPtables, and provides an open system API for easy user customization and development.

In the future, smart ambulances based on 5G technology will undoubtedly provide better full-process services for patients, including pre-diagnosis, during diagnosis, and post-diagnosis.
Forlinx Embedded FCU2303 Smart Gateway, which supports the 5G smart ambulance system, fully leverages the leading advantages of 5G technology, including high bandwidth, low latency, and large connectivity. It will undoubtedly effectively and efficiently guarantee the transmission of information for various medical devices. This will assist medical emergency centers in further improving the efficiency and service level of emergency rescue work, enhancing service quality, optimizing service processes and modes, and winning time for rescuing patients’ lives, thereby better-safeguarding health and life.
Originally published at www.forlinx.net.
0 notes
Text
Dream-Catcher
You were in my dream on Saturday's first breath.
Last I checked, we were out in
The midnight expanse,
Metal machine birds buzzing
Above our heads, illuminating
The mountainous skyline ahead.
Pitch black sight; us, the only two lights,
Remaining under the powers of
A dizzying force field.
Left our bodies at the base,
Travelled onward into space.
I didn't feel the need for the chase --
You erased the haste that ached.
On that weekend morn,
Standing face-to-face on the beach,
Eyes darting to avoid the pace.
Voices fading, garbling into strange communicates.
I replayed your message,
Switching up the frequency, called you
By a new number, tuning into your radio wave;
The ocean's magnetic transmission in your name.
Sunlight emitting from our smiles,
I engage in this hopeful redial.
Time at a standstill;
Momentary mental calibration, rewinding.
I and the girl across the bay
Disappear without a trace
Upon the heat of daybreak.
find me on Instagram: https://www.instagram.com/theblazingpoetess/
#the blazing poetess#poem#poems#poet#poetry#poesia#poetic#poemas#poets#women poets#women writers#writers and poets#poets on tumblr#original poem#poems and poetry#poems on tumblr#words words words#poems and quotes#words for you#dreams#dream#relationships#telepathy#love#write#poetblr
1 note
·
View note
Text
The Technical Breakdown: How 5G Networks Actually Work
In the fast-paced world of technology, the advent of 5G networks has become a transformative force, promising unprecedented speeds and connectivity. To understand how 5G networks work, it's essential to delve into the technical intricacies that set them apart from their predecessors.
At its core, 5G, or fifth-generation, networks represent a leap forward in wireless communication, building upon the foundation laid by 4G LTE. The key differentiators lie in the use of higher frequency bands, advanced antenna technologies, and a shift towards a more software-centric architecture.
One of the defining features of 5G is the utilization of millimeter-wave (mmWave) frequencies, ranging from 24 GHz to 100 GHz. These higher frequencies enable the transmission of massive amounts of data at incredibly fast speeds. However, these signals have a shorter range and struggle with obstacles like buildings and trees, prompting the need for an increased number of small cells and advanced beamforming techniques.
Beamforming is a critical aspect of a 5G network, enabling targeted and focused transmission of signals. Unlike traditional omni-directional antennas, 5G base stations use beamforming to concentrate signals towards specific devices, enhancing efficiency and reducing interference. This precision contributes to the impressive data rates and low latency promised by 5G technology.
Furthermore, 5G networks leverage a technology known as Massive MIMO (Multiple Input, Multiple Output), which involves using a large number of antennas at both the transmitter and receiver ends. This enables multiple data streams to be transmitted and received simultaneously, increasing overall capacity and enhancing network performance.
The architecture of 5G networks is also undergoing a significant shift towards virtualization and cloud-native principles. Network functions that were traditionally performed by specialized hardware are now being replaced by software-based solutions, leading to a more flexible and scalable infrastructure. This shift allows for dynamic resource allocation, efficient management of network resources, and the rapid deployment of new services.
In conclusion, the workings of 5G networks are a result of a synergy between high-frequency bands, advanced antenna technologies, beamforming, Massive MIMO, and a software-centric architecture. This combination not only facilitates unparalleled data speeds but also promises to revolutionize various industries, from healthcare to autonomous vehicles. As 5G continues to roll out globally, the technical breakthroughs behind its operation pave the way for a future defined by seamless connectivity and innovation.
0 notes
Text
A History of Wireless Microphones: How They Were Invented
Wireless microphones have become an essential tool for any event, whether it be a rock concert, theater performance, or live broadcast. But how did this technology come to exist and what was the journey like?
In this blog post, we'll take a look at the history of wireless microphone technology from its inception to today's modern versions. We'll explore how these devices were invented and developed over time to reach their current state of popularity and reliability. So, let's dive in and discover the fascinating story behind wireless mics!

How Wireless Microphones Were Invented?
The invention of the digital wireless microphone had its roots in the late 19th century when Guglielmo Marconi began experimenting with radio-wave technology. At this time, Marconi was attempting to make it possible for sound waves to be sent over a large distance without losing any quality or clarity. His experiments eventually led him to develop the first wireless microphone, which was patented in 1903.
The original wireless microphones were bulky and not very reliable. Marconi's invention had limited range and often suffered from interference from other radio signals. However, improvements over the years made these devices smaller and more reliable. By the mid-20th century, wireless microphones were used in television and radio shows, large-scale events, and even in the home.
Over the years, wireless microphone technology has evolved significantly, with advancements in both sound quality and signal transmission capabilities. This article will provide an overview of the history of wireless microphones, beginning with their invention and tracing their development up to the present day.
Early History of Wireless Microphones
The first patent for a fully functional wireless microphone was granted to Gustave Bally in 1906, although the actual device did not become commercially available until 1913. Bally's invention was based on his earlier work with spark-gap transmitters, which he had used to successfully transmit radio signals over long distances.
His design employed two separate components: a transmitter unit, which created audible sound by means of an electrical arc, and a receiver unit that amplified these signals so they could be heard by listeners at a distance away from the source.
This early design had several limitations; most notably it was only able to produce monophonic sound (i.e., one channel of sound) and had a very limited range (roughly 50 meters).
Furthermore, its reliance on radio waves for transmission meant that it could suffer interference from other nearby devices or sources of electrical noise. Nonetheless, Bally's invention marked the beginning of modern wireless microphones as we know them today!
Developments Throughout the 20th Century
In the decades following Bally's initial patent, there were numerous advancements made in lavalier micr for mobile phonetechnology that allowed for improvements in both sound quality and range.
In 1927, another inventor named John Logie Baird expanded upon Bally's original design by introducing dual-channel transmission (allowing stereophonic sound). This breakthrough also enabled longer ranges due to its ability to send low-power signals over much larger distances without experiencing interference or dropouts.
By the mid-century, advances in frequency modulation (FM) technology allowed for even greater improvements in signal clarity and range compared to earlier attempts using amplitude modulation (AM).
The introduction of FM receivers in 1952 allowed users to hear different frequencies without having to manually adjust antennas or receivers like before. It is one of the earliest forms of digital tuning technology!
In 1983 Motorola released its first commercially available digital cordless telephone system, which utilizedFrequency Division Multiple Access (FDMA) technologies for transmitting voice signals wirelessly over a shared frequency channel.
With this new development, people could communicate with two devices at the same time using one frequency. The audio quality also got better because of new ways to filter out background noise and other interference.
Recent Advances in Wireless Microphone Technology
Since that time, there have been lots of improvements in this area. This means that we can now transmit audio with much better quality, and the system is less likely to experience problems thanks to newer technologies like spread spectrum transmission and digital encoding/decoding methods.
The use of these techniques has enabled modern wireless systems to extend their reach even further than ever before while still providing crystal-clear audio reproduction free from any distortion or interference. Moreover, new features such as automatic pairing, user-friendly interfaces, and advanced security protocols have made setup easier than ever before!
TheHollyandLark C1 lavalier mic is one example of this evolution which utilizes the latest Bluetooth 5.0 technology to offer reliable audio transmission up to a staggering distance of 200m! The ability to communicate wirelessly over long distances has changed the broadcast and media production industry. This allows filmmakers and broadcasters to capture audio in settings where it would be difficult or impossible to do so.
As we enter the 21st century and beyond, it's clear that wireless microphone technology will continue advancing and providing us with greater capabilities for communication. Who knows what amazing possibilities lie ahead? Only time will tell!
Conclusion
Overall, it is clear that wireless lavalier mic for Androidtechnology has come a long way since its inception over 100 years ago! From basic AM/FM designs all the way up through today's advanced digital systems, this type of equipment has seen countless improvements across multiple fronts. As new innovations continue being made, it is likely that future generations will be able to enjoy even better performance from their favorite microphones than ever before!
TheLark C1 is just one example of how far mobile microphone technology has progressed over the years and can serve as a testament to its potential for further growth in the future. Whether you're a professional broadcaster or amateur enthusiast, there is no doubt that this type of lavalier mic for iPhonewill continue to improve and provide us with new capabilities to enhance our communication needs!
1 note
·
View note
Text
The Evolution of the AV Designer's Toolkit: A Historical Perspective
Over the past few decades, the role of the AV designer has transformed tremendously as new technologies have revolutionized the way we create, distribute and experience audiovisual media. This evolution has been accompanied by radical changes in the tools and techniques available to professionals working in this field. In this blog about av info , we will take a historical look at how the AV designer's toolkit has developed from the earliest days of radio and television through to the digital era. Through examining key innovations and turning points, we hope to gain insight into how new technologies continuously reshape this dynamic industry.

The Early Days of Radio and TV (1900s-1950s)
In the early 1900s, the era of radio and television was just beginning. Many of the most basic principles and components of AV systems were still being discovered and refined during this time. Pioneering designers worked with rudimentary equipment to craft some of the first radio and television productions. Their toolkit primarily involved hardware like vacuum tubes, antennas, primitive recording equipment and Studio setups av info would be unrecognizable compared to modern facilities. Designing audiovisual experiences was still in its infancy, focusing more on establishing the foundational technologies rather than sophisticated creative tools.
Nonetheless, rapid advancements were occurring. In the 1930s-40s, developments like frequency modulation transmission, television broadcasting standards and newer camera technologies started to take hold. Studios evolved basic lighting, switching and editing capabilities. Designers gained increased control over factors like audio mixing, visual composition and live switching between camera angles. While production values were relatively low, this era established many of the core building blocks that the AV industry would continue to build upon.
The Rise of Consumer Electronics and Broadcast Standards (1950s-1970s)
The post-war 1950s saw the rise of consumer electronics and a standardization of broadcast formats that transformed the commercial possibilities of audiovisual media. Technologies like reel-to-reel tape recording democratized audio production while video tape recorders began bringing television into consumers' homes. Standard television resolutions and framing emerged, along with innovations like color broadcasting.
Within professional studios and control rooms, this period brought expanded mixing consoles, multi-track tape decks, film-to-tape transfers and sophisticated broadcast switchers. Designers could now manage more channels of high-quality audio and precisely composite intricate television productions. Formats like NTSC and PAL established cross-compatible internationally broadcast standards.
Meanwhile, modular commercial and industrial AV systems emerged for applications like point-of-sale displays, digital signage, presentations and museum/exhibit multimedia. Rack-mount processors and industrial projectors expanded immersive audiovisual experiences beyond broadcast studios. By the 1970s, an interconnected ecosystem of production and presentation gear supported global mass media as well as localized commercial AV needs.
The Digital Revolution (1980s-2000s)
The digital revolution completely transformed the capabilities available to AV designers by extending computational power into all aspects of media creation and delivery. From the 1980s onwards, technologies like digital audio workstations, nonlinear editing systems, MIDI, sampling and DV/DVCam recording opened up new avenues for audiovisual artistry and productivity.
Computerization allowed for software-defined virtual studios, complex digital switching, and automated lighting/video control. File-based workflows streamlined content management. Formats like QuickTime, Flash and HTML5 enabled networked multimedia experiences. Meanwhile, CGI, 3D rendering and digital projectors enabled immersive cinematic presentations inconceivable just years prior.
By the 2000s, "prosumer" tools like DSLRs, smartphones and affordable editing apps gave consumers significant creative production abilities. Behind-the-scenes, immersive experiences like dome theatres and planetariums thrived thanks to technologies like 4K/HD projection, surround sound and sophisticated control systems. Today's IP-centric, software-defined, cloud-enabled workflows grant nearly unlimited scale, integration and creativity.
The Connected Future (2010s-Present)
The past decade has seen digital media, mobile connectivity and collaborative platforms converge in ways that dissolve old boundaries between production, distribution and consumption of audiovisual experiences. Innovations like social video, AR/VR, Esports broadcasting and the Internet of Interactive Things are pushing the role of AV design into uncharted areas.
Modern multi-user software and networked hardware allow geographically distributed teams to collaboratively develop immersive projects. Formats like 360-degree video utilize dynamic sensor input while real-time analytics optimize engagement. 5G, edge computing and processor innovations continue extending computational power to even the smallest portable devices.
Cloud storage and processing as well as software-defined infrastructure now provide limitless scalability. Interfaces like drag-and-drop workflows are bringing technical capabilities previously requiring extensive expertise within reach of general consumers. Connected home/office/classroom platforms seamlessly integrate diverse types of displays, speakers and IoT devices into holistic multimedia experiences.
As new frontiers in creativity, education and social interaction continue emerging, so too will innovative tools to support audiovisual designers at the forefront of these transformations. The connected, intelligent, experiential future remains unwritten - it will take a new generation of visionary media makers to fully realize its potential.
Conclusion
This blog has provided a high-level overview of the incredible evolution that has occurred within the toolbox available to AV designers over the past century. What began as rudimentary wired circuits, vacuum tubes and film projectors has advanced through analog, digital and now networked/IoT technologies. Each major wave of innovation expanded the frontiers of creativity by orders of magnitude while dissolving old barriers between production and consumption.
Looking ahead, it's difficult to predict precisely how tools, formats and workflows may continue to evolve - but one can be certain new frontiers in immersive, intelligent and experiential media are on the horizon. Adaptability will remain crucial as new platforms emerge - just as ingenuity and creative vision will remain central to realizing the full promise of future innovations. The rapid pace of audiovisual transformation shows no signs of slowing, ensuring continued excitement and opportunities for generations to come.
0 notes
Text
The Very First Automated Frequency Coordination System Administrator to Obtain Approval Anywhere in the World, Providing Exceptional Wi-Fi Experiences to Customers All Over the Globe This accolade has been bestowed to Qualcomm. The following is a sample of the most noteworthy characteristics: • The company has been recognised as the world's first Automated Frequency Coordination System Administrator (AFCSA) for commercial operation in Canada. This accomplishment was achieved in the country of Canada. The government of Canada conferred upon them this award and recognition for their accomplishments. • The Qualcomm® AFC System is an essential part of the Qualcomm® AFC Solution, which is a comprehensive end-to-end solution designed to liberate a higher-performance, longer-range version of 6 GHz working in Wi-Fi 6E, Wi-Fi 7, and subsequent generations. The Qualcomm® AFC Solution is a full end-to-end solution that is intended to liberate this version of 6 GHz. • The Qualcomm® AFC Solution is a solution that is meant to release a higher-performance, longer-range version of 6 GHz working in Wi-Fi 6E, Wi-Fi 7, and following generations. This solution was created to liberate the 6 GHz band. Qualcomm Technologies, Inc. was recognised by Innovation, Science and Economic Development Canada (ISED) on August 21 as an Automated Frequency Coordination System Administrator (AFCSA) in Canada. Qualcomm Technologies, Inc. was selected to receive this prestigious award. As a direct result of being granted this classification, Qualcomm Technologies has been the first AFC system operator anywhere in the world to be granted licence for commercial operation. This honour was bestowed upon them as a direct consequence of the awarding of this classification. When it is acquired, the Qualcomm AFC System may be put to use right away in Canada; however, in the United States, the availability of the system is contingent on the agency known as the Federal Communications Commission (FCC) first giving its approval. The Qualcomm AFC Solution is a piece of hardware that was developed to allow for operation at the higher 6 GHz Wi-Fi Standard Power frequency. It is a complete answer to the problem. This solution is made up of each and every one of its individual components. The Qualcomm AFC Solution enables location-based power optimisations for 6 GHz transmissions; it is designed to enable greater Wi-Fi power levels to be utilised in access points both indoors and outdoors; it offers improved performance and longer range while safeguarding existing incumbent users of the band; and it provides support for higher Wi-Fi power levels in both indoor and outdoor settings. All of these features can be found in the Qualcomm AFC Solution. The turnkey, cost-effective, and scalable solution that is offered by Qualcomm AFC Solution includes an access point agent and cloud system that makes use of standards-defined interfaces to allow interoperability across network installations that use 6 GHz operation. Examples of such operations include Wi-Fi 6E, Wi-Fi 7, and even further. Additionally, a solution that is provided by Qualcomm AFC Solution is included into this solution. It is now available for customer device integration across Qualcomm® Networking Pro Series and Qualcomm® Immersive Home platforms, and it is intended to span residential, broadband operator, and corporate market sectors. In addition, it is now available. In addition to that, it is now available for the integration of customer devices. "We are excited by and applaud the approval from Canadian Innovation, Science and Economic Development," said Ganesh Swaminathan, vice president and general manager of Qualcomm Technologies, Inc.'s Wireless Infrastructure and Networking division. "Canadian Innovation, Science and Economic Development" "Innovation, Scientific Advancement, and the Growth of the Canadian Economy"" According to the business, "by making use of our comprehensive AFC solu
tion, we are in a position to deploy scalable, turnkey cloud-to-silicon services that will significantly improve the performance of 6 GHz Wi-Fi." As a direct result of gaining this certification, we are now in a position to expedite the deployment of standard power access points for our customers in Canada, and we are prepared to extend our operations into neighbouring areas. Moreover, we are also in a position to accelerate the deployment of standard power access points for our customers in the United States.
0 notes
Text
Investigating the Power and Flexibility of the Rigol DS1000Z-E Series Digital Oscilloscope

In the present quick-moving and innovation-driven world, the capacity to precisely gauge and envision electronic signs is of fundamental significance. Whether you're a hardware fan, an understudy, or an expert designer, having the right devices available to you can have a significant effect on understanding and investigating electronic circuits. One such basic device is the digital oscilloscope, and the Rigol DS1000Z-E Series stands apart as a perfect representation of development and productivity in this field.
Divulging the DS1000Z-E Series: A Short Outline
The Rigol DS1000Z-E Series is a line of digital oscilloscopes intended to offer a convincing mix of execution, highlights, and reasonableness. Based upon Rigol's long periods of skill in the test and estimation industry, this series is customized to take care of a great many clients - from understudies and specialists to proficient designers dealing with complex undertakings.
The series brags an assortment of models, each with its own one-of-a-kind arrangement of highlights and details. These models incorporate the DS1054Z-E, DS1074Z-E, DS1104Z-E, and DS1204Z-E, taking special care of various necessities and spending plans. With data transmissions going from 50 MHz to 200 MHz and test paces of up to 1 GSa/s, the DS1000Z-E Series guarantees that clients can precisely catch and dissect signs of fluctuating frequencies.
Key Highlights and Benefits
Noteworthy Presentation and UI: The DS1000Z-E Series is furnished with a splendid and clear 7-inch show that gives ongoing waveforms and estimation results. The instinctive UI improves on route and design, making it simple in any event, for rookies to make ready rapidly.
Progressed Setting off and Investigation: Rigol has incorporated a large group of cutting edge setting off choices into the DS1000Z-E Series, permitting clients to catch explicit occasions with accuracy. The series additionally incorporates different number-related capabilities and estimation devices, empowering the inside and out investigation of waveforms.
Long Memory Profundity: Not at all like some contending models in its cost range, the DS1000Z-E Series includes profound memory profundities, which are fundamental for precisely catching and breaking down complex signs. This component is especially useful while managing sequential correspondence conventions or catching transient occasions.
Waveform Catch Rate: The DS1000Z-E Series flaunts a high waveform catch rate, guaranteeing that clients can catch discontinuous errors and oddities that could somehow slip through the cracks. This is an essential viewpoint while investigating mind-boggling electronic circuits.
Adaptability and Availability: The DS1000Z-E Series comes outfitted with various info channels, permitting clients to screen and investigate different signals at the same time. Furthermore, the USB ports and LAN network choices work with information move and controller, upgrading the oscilloscope's general adaptability.
Underlying Capability Generator (Discretionary): A few models inside the DS1000Z-E Series offer a discretionary implicit capability generator, further growing the capacities of the oscilloscope and making it a far-reaching testing arrangement.
Applications and Use Cases
The Rigol DS1000Z-E Series tracks down its applications across a wide range of businesses and situations:
Instruction: The series is a brilliant apparatus for educating and finding out about gadgets and waveform examinations. Its easy-to-understand connection point and reasonableness make it an ideal fit for instructive foundations.
Innovative work: Experts working in innovative work benefit from the DS1000Z-E Series' high-level highlights, empowering them to direct top-to-bottom examination and gain bits of knowledge into their plans.
Fabricating: In a creation climate, the DS1000Z-E Series can be utilized for quality control, testing, and investigating electronic parts and circuits.
Support and Fix: Gadgets experts can depend on the series to productively analyze and fix broken circuits and gadgets.
In Conclusion
The Rigol DS1000Z-E Series remains a demonstration of Rigol's obligation to give superior grades, including rich, and reasonable test and estimation arrangements. With its high-level capacities, instinctive UI, and flexible applications, this digital oscilloscope series is appropriate to address the issues of a different client base. Whether you're an understudy, a specialist, or a carefully prepared engineer, the DS1000Z-E Series is an important instrument that enables you to investigate, break down, and figure out electronic signs with accuracy and certainty.
0 notes