#antivirus protection
Explore tagged Tumblr posts
Link
Computer Viruses come in many forms and created with different intentions. Some corrupt or delete your computer files while others designed to replicate until they use your RAM; rendering your computer unable to operate. In this blog, we will show you everything you want to know about computer viruses and their types.
#laptop#laptops#antivirus#antivirus protection#antivirus software#pc#pc gaming#gaming pc#gaming laptop
0 notes
Text
Is Windows Defender Antivirus Enough Protection for Normal Computer Use?
Introduction to Windows 11 Antivirus Windows 11, the latest iteration of Microsoft’s operating system, comes equipped with a robust built-in antivirus solution known as Windows Defender. This integrated security feature is designed to offer comprehensive protection against various digital threats, making it a critical component for everyday computer use. Windows Defender is not new; it has…
0 notes
Text




Amiga RocKnight Antivirus Device RV300C
34 notes
·
View notes
Text
As someone who's maybe a little too quick to anthropomorphize any inanimate object I interact with, can I just say how glad I am that, thus far, computers mostly seem to talk in 'we' and 'you' terms instead of 'I' terms
#for clarification: I don't mean chatbots or alexa or AI-generated whatevers. They all seem to use 'I' quite comfortably#I'm talking about laptops that project messages like 'we're doing updates please don't turn off your computer'#and 'your antivirus protection has expired'#if my computer said shit like 'I'm updating give me a bit of time' and 'I have no antivirus :(' it would probably become a pet to me#not sure I can handle that tbh#computers
11 notes
·
View notes
Text
Tonight, I noticed an email from Facebook with a legitimate code to change my password that came in around 2pm while I was at work and not using Facebook. I also noticed SOMEONE HAD OPENED IT. Which was also not me, because I was at work, not using my personal email. So I looked at the activity log on both of my email accounts and you guys would not BEEELIEVE what I found. See pictures for the shocking results. This is just one page from each that I could screenshot, this crap has been going on for days upon days and someone actually managed to sign into one of my accounts more than once. I have since changed my password to something harder and forced sign out on all accounts, so hopefully that kicks out whoever was in my effing email, but holy crap.
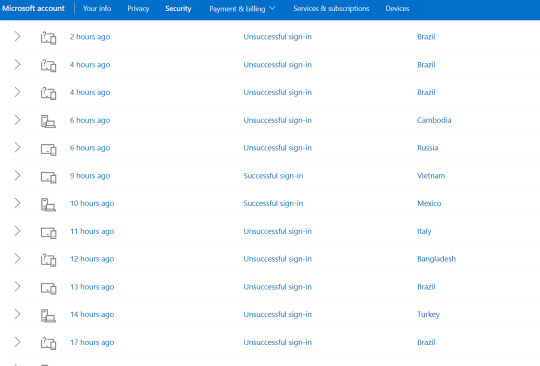

#I also bit the bullet and paid for an antivirus subscription rather than the free protection#and changed a bunch of other passwords#and set up two factor authentication on my “important” accounts#I'm going to hate all this when signing in myself but fuck if Im going to let scammers from all over the world gain access to any of my SHI
2 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
pray for me I'm gonna have to call either tomorrow or Monday to fight with TotalAV to give me a refund on the antivirus that they renewed over a week early (purchased a 1-yr license on Sept 28th for $29.99, was charged on Sept 19th for 159.99 DOLLARS like a year means *a year* not 356 days) without any kind of heads up email or anything, and the receipt email went directly to my spam folder so I didn't even know I had been charged until I just checked my bank account now and saw the charge. if I can't get a refund I might do something drastic. for legal reasons I cannot say what
#AND i got a popup saying “your antivirus is inactive! renew your license now so you're protected!” today. so naturally i assumed that#my antivirus was in fact inactive. because it said so. and so i went and bought mcafee because it fucking said “you dont have an#antivirus program right now youre unprotected“ so now i have two antivirus programs
2 notes
·
View notes
Text
idk if omega having to charge himself at night instead of sleeping is a joke that was ever made in official sonic media but i think he should have his own sockets so he can be a portable power source. he also has a usb slot and sometimes he intentionally plugs in usbs with viruses in em bc its like getting drunk
5 notes
·
View notes
Video
youtube
Is Free Truly Free - Analyzing AVG Antivirus
#youtube#Antivirus AVG Free Privacy Security Costs Data Cybersecurity Protection Software Hidden price
0 notes
Text
Comment Maîtriser l'Évasion d'Antivirus ?
Qu’est-ce que l’Évasion d’Antivirus ? Maîtriser l’Évasion d’Antivirus L’évasion d’antivirus consiste à modifier ou camoufler un malware pour éviter qu’il soit détecté par les logiciels de sécurité. Les hackers utilisent diverses techniques pour contourner les antivirus, afin que leur code malveillant puisse être exécuté sans être repéré. L’objectif est d’exploiter des faiblesses dans les moteurs…
#analyse comportementale#antivirus#attaques sans fichier#cybersécurité#évasion d&039;antivirus#hackers éthiques#Metasploit#polymorphisme#protection des systèmes#techniques d&039;évasion#Veil
0 notes
Video
Best Free Antivirus Software For PC/Laptop in 2024 (Windows 10 & 11) | No Crack | Original & Genuine License
#youtube#antivirus#free#freeantivirus#best#bestantivirus#software#pc#laptop#2024#windows#windows 10#windows 11#microsoft windows#crack#original#genuine#lisence#license#security#protection
0 notes
Text
“apparent default of third party software pushing updates whenever the fuck” it was literally the equivalent to a malware definitions update. This is pushed whenever in every other antivirus under the sun including those on m*cOS and L*nux based systems, CrowdStrike somehow causes an access violation parsing that problematic one.
If a process running with such privileged access causes an AV, it is indeed good that “the entire airline industry” stopped because of it - at best to prevent them from running systems that would be literally unable to exhibit expected behavior otherwise, at worst to point and laugh at CrowdStrike and hopefully make it go bankrupt.
Also, Microsoft Update is very centralized! So centralized, it works for Microsoft 365 (formerly Office) products! Why would you use non Microsoft software anyways? CrowdStrike is what happens when you do! Windows Defender is truly the way to go.
it's honestly nuts to me that critical infrastructure literally everywhere went down because everyone is dependent on windows and instead of questioning whether we should be letting one single company handle literally the vast majority of global technological infrastructure, we're pointing and laughing at a subcontracted company for pushing a bad update and potentially ruining themselves
like yall linux has been here for decades. it's stable. the bank I used to work for is having zero outage on their critical systems because they had the foresight to migrate away from windows-only infrastructure years ago whereas some other institutions literally cannot process debit card transactions right now.
global windows dependence is a massive risk and this WILL happen again if something isn't done to address it. one company should not be able to brick our global infrastructure.
#to address the other two points. if you need an antivirus under windows you are equally as likely to need it for other desktop systems#personally i think needing antivirus is usually a symptom of a larger problem#a giant attack vector meant to protect users who SHOULDN’T have as much privilege as the antivirus needs to do anything useful#on the package manager aspect there’s many for windows including winget#i agree winget is kinda garbage for traditional installers#but if you need control over every little package i reckon a bsd might be the superior idea#appx is pretty good for this too though you wouldn’t notice with the average store app#windows 11#windowsposting#windows11-official
5K notes
·
View notes
Text
"Advanced Threat Protection with Kaspersky Antivirus and Radiant Info Solutions"
Discover how Kaspersky Antivirus, provided by Radiant Info Solutions, offers advanced threat protection for businesses and individuals in India.
#Kaspersky Antivirus#Radiant Info Solutions#advanced threat protection#cybersecurity#antivirus India
0 notes
Text
#antivirus#total protection#cybersecurity#best antivirus software for laptop#online antivirus software for laptop#best antivirus software for mobile device#best antivirus for phone and computer#best antivirus for laptop in philippines#kharismaworld#mcafee distributor
1 note
·
View note
Text
Norton 360 Premium 2024, Antivirus software for 10 Devices with Auto Renewal

0 notes
Text
Safeguard Your PC Against Common Malware Entry Points
Safeguard Your PC Against Common Malware Entry Points
Safeguard Your PC Against Common Malware Entry Points In our day-to-day activities on the internet, cyber threats hide in unexpected places, ready to infiltrate your devices and wreak havoc. It’s crucial to know how malware can get into your computer to protect yourself better. Here, we look at some of the most prevalent ways through which malware seizes control, so you can be more careful and…

View On WordPress
#AntiMalware#malware#Microsoft Malware Protection#Windows#Windows 10#Windows 11#Windows Defender#Windows Defender Antivirus#Windows Security#Windows Server
1 note
·
View note