#antivirus program right now youre unprotected“ so now i have two antivirus programs
Explore tagged Tumblr posts
Text
pray for me I'm gonna have to call either tomorrow or Monday to fight with TotalAV to give me a refund on the antivirus that they renewed over a week early (purchased a 1-yr license on Sept 28th for $29.99, was charged on Sept 19th for 159.99 DOLLARS like a year means *a year* not 356 days) without any kind of heads up email or anything, and the receipt email went directly to my spam folder so I didn't even know I had been charged until I just checked my bank account now and saw the charge. if I can't get a refund I might do something drastic. for legal reasons I cannot say what
#AND i got a popup saying “your antivirus is inactive! renew your license now so you're protected!” today. so naturally i assumed that#my antivirus was in fact inactive. because it said so. and so i went and bought mcafee because it fucking said “you dont have an#antivirus program right now youre unprotected“ so now i have two antivirus programs
2 notes
·
View notes
Text
Convert M4A To WAV Online Free
QQripper is the autoloader software program to automate the ripping of a stack of music discs (to transform audio tracks from music CD to digital recordsdata) to supported storage devices corresponding to exhausting disk, iPod or MP3 participant. Click Convert to transform your MP3 file(s). Permitting the streaming service to compress and convert your audio information does not necessarily mean the standard will degrade, however some compression algorithms enhance peak indicators sufficient that the audio can sound distorted. Once you use a trusted program to convert your recordsdata to the right format for each platform, you possibly can hear to every one to get a good suggestion of what it is going to sound like as soon as it's published. After that click on 'Apply the adjustments' button. Now when he carried out, go to your Desktop. There you will see that your Wav file. Convert recordsdata from wav to MP3,MP2, WAV, WMA, OGG, AAC, APE, FLAC, WV, TTA ,SPX,MPC,AC3 and MP4 to WAV and backwards. Audio-only MPEG-four information generally have am4a extension. That is especially true of non-protected content material. M4A is usually compressed utilizing AAC encoding (lossy), however can also be in Apple Lossless format. Is there any other various methodology for changing M4A to WAV with prime quality? After all, when you wish to enjoy audio in top quality, you can even maintain the unique M4A recordsdata. As a substitute you'll be able to obtain program to play back M4A information on other devices. Right here is the one which works with Mac and iPhone, VOX Music Player.
Select M4A as the output format you need to convert MP3 file(s) to. Step four. Click CONVERT button, and begin conversion. NoteCable M4P Converter freeware provide a straightforward and accomplished solution to convert between various audio codecs, equivalent to MP3, WAV, WMA, free m4a to mp3 converter mac os x M4P, M4A, AAC. Considered one of featured perform is that M4P Converter freeware can convert M4P to MP3, WMA, WAV, OGG, M4a, AAC with the fastest pace and excellent output audio high quality in case you are Windows iTunes consumer, It's a M4P Converter. You possibly can convert M4P to MP3 simply.

I'm trying to convert a file withm4a extension from Garageband to wav for PS3. To hurry up the conversion process or in an effort to save pc resources it is doable to set the Free Convert WAV to MP3 course of thread priority. If you want to convert to WAV or mp3 all it's good to do is go to your preferences>normal>import settings after which select both WAV or mp3. Once that is configured you'll be able to right click on on your music file and create mp3 or no matter setting you selected. Free WAV to MP3 Converter (model 7.6.zero) has a file dimension of 2.fifty six MB and is out there for obtain from our website. Just click the green Obtain button above to begin. Till now this system was downloaded 564 instances. We already checked that the obtain link to be protected, nonetheless for your personal protection we advocate that you simply scan the downloaded software program along with your antivirus. Convert music recordsdata to the common MP3 format for any Gadget. This code is released under the MIT license. Note that FlicFlac uses exterior codecs for encoding audio file, please seek advice from their respective license. Method one: Just drag and drop M4A file to the primary interface of Faasoft M4A to WAV Converter. Methodology two: Click on "Add File" button of the program. ALAC stands for Apple Lossless Audio Codec. It was developed and launched in 2004 as a proprietary format but ultimately turned open supply and royalty-free in 2011. ALAC is sometimes known as Apple Lossless. All Audio Converter :- You may convert audio to different codecs like mp3, WAV, M4A, AAC in only a minute. All your prompt recordsdata will likely be converted. You'll be able to proceed to update to SP2. (You too can do that process after the update if you wish). WAV MP3 Converter converts WAV to MP3 and MP3 to WAV, and resamples WAV and MP3 information, and helps multiple hundred fifty audio and video files. When you have bulk of MP3 or WAV recordsdata inside completely completely different folders, and m4a2wav additionally you need to convert them to another format or resample them and audio-transcoder.com output to a different folder or driver and protect the unique tree path, it is advisable to use the function we designed for you. Then it saves the files in two places in iTunes, within the albums and in another place referred to as TO MP3 CONVERTER FREE. Delete one, and it deletes both. Channels: Most audio file formats don't only allow to store a mono or stereo audio stream but in addition multi-channel audio streams (-> encompass). Audio-solely MPEG four container recordsdata normally have an M4A file extension. M4B is for audio e book, podcast and M4R is for iPhone ringtones. M4A information are unprotected. Protected information often have an M4P file extension. I don't know what the issues you have been having with them4a recordsdata are. MediaHuman Audio Converter is a freeware software for Mac OS X and Windows. It might make it easier to to convert your music absolutely free to WMA, MP3, AAC, WAV, FLAC, OGG, AIFF, Apple Lossless format and bunch of others. Though there are many Audio Compressors on-line, most of them solely help compressing MP3 and WAV fairly than nearly every kind of audio formats. This article will show a professional Audio Compressor and an in depth information on methods to compress MP3, WAV, FLAC, AIFF, M4A, and so forth with it on Mac and Windows. provide help to convert M4A to WAV without quality loss. Really, I've also encountered the same problem earlier than. I have tried every effort to search out out the rationale and hoped to make it okay, but nonetheless, was out of luck. In desperation, I used to be beneficial to make use of one other program-Firecoresoft M4A Converter for Mac ( M4A Converter for Home windows), an expert instrument specializes in converting audio recordsdata without any loss of unique high quality. button so as to add audio file(s). Please observe the steps to convert audio recordsdata to wav with PowerISO. Obtain the audio reducer in your computer now. After launching it, comply with the three steps to compress MP3, FLAC, WAV, and so on. Convert aac to mp3, wav, m4c, wma and ogg. Compress M4A to MP3, WMA, AC3, RA and etc. MP3 is a lossy format, which suggests elements of the music are shaved off to scale back the file measurement to a more compact stage. It is supposed to make use of "psychoacoustics" to delete overlapping sounds, however it is not at all times successful. Usually, cymbals, free m4a to mp3 converter mac os x reverb and guitars are the sounds most affected by MP3 compression and might sound really distorted or "crunchy" when an excessive amount of compression is utilized.

1 note
·
View note
Text
McAfee Internet Security (2017)
http://cyberparse.co.uk/2017/01/18/mcafee-internet-security-2017-2/ https://i0.wp.com/cyberparse.co.uk/wp-content/uploads/2016/04/security-binary-pd-898757.jpg?fit=3888%2C2592
The true purpose of a security suite isn’t to secure your computer. It’s to protect you, your privacy, and your data. With customer protection in mind, McAfee Internet Security installs on all of your devices. However, most of what it offers comes with McAfee’s antivirus, and the additional suite-specific components don’t add enough value, especially if you don’t need antispam or parental control.
At $79.99 per year, McAfee looks like it’s right in line with the competition, price-wise. Bitdefender and Kaspersky charge the same, within a nickel or so. But look again. With a Bitdefender or Kaspersky subscription you can install protection on three PCs. McAfee is unlimited, and lets you protect every Windows, macOS, iOS, or Android device in your household.
In fact, the Home screen in this product includes a button to extend protection to more devices. Clicking it reveals a button that scours your network to find unprotected devices and bring them into the fold. Clicking the icon that represents your current device summarizes its status.
The main window looks, for the most part, like that of McAfee’s antivirus. Both have undergone a major user interface update since I originally reviewed the product line. Instead of squareish green edged panels, the main window now relies on a menu of five items: Home, PC Security, Identity, Privacy, and Account. Clicking each item brings up a page that displays status and offers access to the corresponding feature. There’s no longer any need for the Navigation page, a separate user interface that listed and linked to every one of the suite’s features.
Not seeing this new interface? Don’t worry, you will. McAfee is rolling out the new look slowly, gradually, and automatically.
Shared Antivirus Features As is often the case, this suite’s antivirus protection is precisely the same as that of the corresponding standalone antivirus, McAfee AntiVirus Plus. That review goes into greater detail than the summary that follows.
McAfee’s scores in independent lab tests are generally mediocre. It received a B-level certification from Simon Edwards Labs, while other products rated A, AA, or even AAA. Of three tests by AV-Comparatives, it earned one passing grade and two grades a notch above passing. The three-part test by AV-Test Institute maxes out at 18 points; McAfee’s score improved since my original review, with 5.5 points for protection and a total of 17 points. Finally, in the banking Trojan test and all-types tests by MRG-Effitas, it simply failed.
My lab test score aggregation algorithm yields 7.9 of 10 possible points for McAfee. Kaspersky took a near-perfect 9.8, while Norton and Bitdefender Internet Security 2017 came out at 9.7 and 9.4 respectively.
This year’s McAfee products use an entirely new antivirus detection method called Real Protect. Real Protect is focused on behavior, so as to catch even zero-day malware. Like Webroot SecureAnywhere Internet Security Plus, when it sees an unknown file behaving suspiciously, it starts journaling that file’s actions and queries the cloud for advice. If cloud-based analysis red-flags the file, McAfee rolls back all of its actions.
In my own hands-on malware-blocking test, McAfee scored 9.2 of 10 possible points. However, among the samples it missed were two well-known ransomware threats. I watched one of them as it busily encrypted documents on the test system, without a peep from McAfee about its behavior. Webroot scored a perfect 10 against this same malware collection.
McAfee also protected against 85 percent of the 100 malware-hosting URLs I threw at it, mostly by diverting the browser from the dangerous URL. The average score among current products is 75 percent, so McAfee is above average here.
I score phishing protection by matching a product’s detection rate against that of Symantec Norton Security Premium and of the protection built into Chrome, Firefox, and Internet Explorer. Last year, McAfee came very close to matching Norton’s score. This year it lagged 44 percentage points behind Norton. Chrome and Internet Explorer beat out McAfee, as well. Don’t turn off your browser’s phishing protection!
Other Shared Features There’s a lot more to the nominally standalone antivirus; hence “Plus” in the name. For starters, it includes a firewall. In testing, the firewall correctly stealthed all ports and fended off Web-based attacks. Rather than bombard the user with queries about network permissions, it handles program control internally. When I tested its ability to withstand direct attack, I found that I could terminate and disable more than half of its essential Windows services.
The WebAdvisor component identifies dangerous downloads and steers the browser away from malicious or fraudulent sites. In addition, it marks up search results with icons identifying safe, iffy, and dangerous links. This edition adds protection for typosquatting, and it works. When I entered www.paypla.com it asked if perhaps I really wanted PayPal.
Using the My Home Network feature, you can set up a trust relationship between any and all of the PCs on your network that have McAfee installed. It doesn’t even have to be the same version of McAfee. Once you’ve taken that step, you can use one PC to remotely monitor others, and even remotely fix configuration problems.
Mac and mobile support is the same across all of the McAfee product line. Mac support is little more than antivirus, firewall, and WebAdvisor. There’s no antivirus under iOS, but you can do things like locate and wipe the device, back up contacts, and capture a photo of someone who found or stole your phone. On Android, you get a full-featured security utility with antivirus, app ratings, anti-theft, call and text filtering, and more. And once again, there’s no limit on how many devices you can add.
Other shared bonus features include the QuickClean tune-up tool, a vulnerability scanner, and a secure deletion file shredder. You can also access a number of security-related online resources directly from the program.

See How We Test Security Software
True Key Password Manager With your McAfee subscription you also get a license for the True Key password manager. Read my review for a full description of this password manager and its unusual collection of authentication options.
True Key’s biggest claim to fame is its comprehensive multi-factor authentication choices. It does support the expected strong master password, but you have many other options. You can have it send an email each time you log in; clicking a link in the email allows login to proceed. More conveniently, you can associate a mobile device with True Key, and authenticate by swiping a notification.
Even better, if you’re using a device with a camera, you can authenticate using facial recognition, and if a finger print reader is available, you can add that, too. If you worry that James Bond might spoof facial recognition with a photo of you, just enable enhanced facial recognition, which requires turning your head.
Most password managers warn that if you lose your master password, you’re hosed; you have to start over. That’s actually good; it means that the company can’t access your data even if subpoenaed. True Key retains that same zero-knowledge benefit, but doesn’t leave you in the lurch if you forget the password. As long as you’ve enabled Advanced authentication, which requires a trusted device plus two other factors, you can authenticate using all the other factors and then reset your master password.
True Key is a separate download, but getting it installed is easy. After you run the installer, it adds itself as an extension to Chrome, Firefox, and Internet Explorer. At this time, it can import passwords stored insecurely in the browsers. It can also import from LastPass 4.0 Premium and Dashlane 4.
As with most password managers, True Key captures credentials as you log in to secure sites and plays back saved credentials as needed. The first time, it actively walks you through the process. You can also click on tiles for Google, Facebook, PayPal, and so on, entering your credentials directly. Clicking the TrueKey toolbar icon doesn’t bring up a menu the way it does with many other products. Rather, it displays the main True Key window, from which you can launch any of your saved sites.
You can save personal details in the Wallet, but True Key doesn’t use these to fill web forms. The main reason to do this is that the Wallet items sync across all your devices. The same is true of secure notes.
Here’s a rare feature. If your PC has a forward-facing camera, you can configure it to unlock your Windows account using True Key’s facial recognition. True Key doesn’t have advanced features like secure sharing, automatic password updates, or password inheritance, but it’s far ahead of the pack when it comes to multi-factor authentication.
Tepid Parental Controls One bonus you get by upgrading from McAfee’s antivirus to this suite is a parental control system, but it’s really limited. For each child’s Windows account, you can choose content categories for blocking, set a schedule for Internet use, and view a report of activity for each child or all children. That’s the extent of it.
The reviewer’s guide for this product notes that parental controls may not work properly in a virtual machine. That’s unusual, but I made a point of testing on a physical system.
To get started, you set a password, so the kids can’t just turn off monitoring. The configuration window lists all Windows user accounts and invites you to configure parental control for each one that belongs to a child. As with previous versions, setting up parental control for a child’s account that has Administrator privileges triggers a big warning. And yet, many parents do give older children Administrator accounts, so as to avoid constantly having to jump and supply an admin password any time the child wants to install a new game. Most other parental control systems don’t have this limitation.

To configure the content filter, you first choose one of five age ranges. Doing so pre-configures which of the 20 content categories should be blocked. Rather than the usual list with checkboxes, McAfee displays a list of blocked categories and another list of allowed categories, with arrow buttons to move items back and forth between the lists.
I couldn’t disable the content filter with the three-word network command that neutered parental control in Total Defense Unlimited Internet Security and Alvosecure Parental Control . However, I found quite a few truly raunchy sites that the content filter didn’t block.
McAfee replaces naughty content in the browser with a warning message that explains why the page was blocked. For HTTPS sites, or in unsupported browsers, it displays that warning as a popup, leaving the browser to show an error message. The kids won’t get past it by using a secure anonymizing proxy. Note, though, that Check Point ZoneAlarm Extreme Security 2017 goes even further, with the ability to filter content even over an HTTPS connection.
In addition to categories, McAfee offers to block sites with “inappropriate images or language” from appearing in child’s search results. A similar feature in Trend Micro Internet Security covered up many such images. However, I couldn’t find a single instance where McAfee did anything to block erotic images in search.
The time scheduler is as awkward as ever. It does let you create a weekly grid-style schedule of Internet access, in half-hour increments. Most parental control systems that use a scheduling grid let you block out rectangles on the schedule by dragging. For example, with one drag you could block from midnight to 6am every day of the week. McAfee’s system forces you to drag on just one day at a time. The grid is so tall that you can only select about seven hours at a time, and it doesn’t auto-scroll when you hit the edge. This feature could be so much easier to use! On the bright side, time scheduling doesn’t rely on the system clock, so the kids can’t fool it.
The simple parental report lists all domains blocked, along with their categories. It also logs all attempts to use the Internet when the schedule doesn’t allow it.
And there you have it. That’s the totality of parental control in this suite. It’s limited, awkward, and not entirely effective. If you actually need a suite that includes high-end parental control, look to ZoneAlarm, Kaspersky Internet Security, or Norton.
Broad-Spectrum Spam Filter With so many users getting spam filtered by the email provider, the value of local spam filtering is on the decline. But if you’re one of that diminishing group whose email provider doesn’t offer spam filtering, a local filter can be essential.
McAfee’s spam filter integrates with Outlook, Windows Mail, and Windows Live Mail. In these email clients, it adds a handy toolbar and automatically tosses spam messages in their own folder. You can still use it if you’re a fan of Eudora or The Bat!, but you’ll have to define a message rule to sift out the spam.

McAfee filters spam from POP3 and Exchange email accounts. It doesn’t handle IMAP accounts in your email client the way ZoneAlarm does. However, in an unusual twist, it has the ability to filter webmail accounts directly. Webmail filtering was a pretty amazing feature when first introduced years ago, but these days it’s hard to find a webmail provider that doesn’t implement its own spam filtering. You can view messages filtered out by this feature right in the application and, if necessary, rescue any valid mail that was misfiled.
There are quite a few options for configuring the spam filter. To start, there are five levels of protection, from Minimal, which allows more spam but doesn’t throw away valid mail, to Restricted, which blocks all messages unless the sender is on your Friends list. I’d advise leaving it set to the default Balanced level.
You can define custom spam filtering rules, but I can’t imagine why any user would take the time to do this. The Friends list identifies addresses or domains that should always reach the Inbox. You can manually edit this list, add friends from the email client toolbar, or add all your contacts to the Friends list. There’s also an option to automatically block messages written using character sets for languages you don’t speak.
Just to see how it works, I set up filtering for the Yahoo mail account I use in testing. When I filled in the address, McAfee automatically selected the correct mail server and port. However, after I entered my password and tried to add the account, McAfee reported that it was the wrong password.
In fact, the password was correct, but Yahoo rejected the login and sent me an email warning about an attempt to connect by a “less-secure app.” In order to let McAfee do its job, I had to dig into Yahoo settings and enable access by less-secure apps.
If you do need spam filtering at the local level, McAfee can handle it. Where many products limit protection to POP3 accounts, McAfee can filter Exchange accounts and even pull spam from your webmail.
Minor Performance Hit During my extensive testing, I didn’t get any feeing that McAfee was slowing me down. That’s not surprising; these days it’s uncommon for security suites to exhibit a noticeable performance impact. My hands-on test did reveal some actions that took longer with McAfee installed.
Most of us don’t reboot often—perhaps never except when an update requires it. My boot time test showed just a 3 percent increase in the time from the start of boot until the system was ready for use, so if you do have to reboot, you’ll hardly notice McAfee’s presence.
Given that the new Real Protect real-time antivirus scans files when they try to execute, not on just any file access, I expected minimal impact in my file move and copy test. This test repeatedly times a script that moves and copies a mammoth collection of various-sized files between drives. I was surprised to see a 44 percent increase in the time required for this test. On the bright side, another test that zips and unzips the same file collection didn’t have any measurable impact.
While there’s some variation in the results of this test, a couple products come out on top. Webroot and Trend Micro exhibited almost no slowdown in the performance test.
Stuck in the Middle With You For $20 per year more than McAfee’s antivirus, McAfee Internet Security gives you innovative password management along with parental control and antispam features that you may not need. Everything else—firewall, remote management, support for macOS, iOS, and Android, and more—is present in the antivirus. For another $10 you could upgrade to McAfee’s top-of-the-line suite. This suite remains stuck in the middle, with no compelling reason to buy it rather than one of McAfee’s other products.
Other than the cross-platform bonus, this suite is comparable to Bitdefender Internet Security and Kaspersky Internet Security. These two suites earn fantastic scores from the independent testing labs, their components are capable across the board, and they offer a comparable smorgasbord of bonus features. They’re our Editors’ Choice winners for entry-level security suite.
Sub-Ratings:
Note: These sub-ratings contribute to a product’s overall star rating, as do other factors, including ease of use in real-world testing, bonus features, and overall integration of features.
Firewall:

Antivirus:

Performance:

Privacy:

Parental Control:

Back to top
PCMag may earn affiliate commissions from the shopping links included on this page. These commissions do not affect how we test, rate or review products. To find out more, read our complete terms of use.
Source Threatpost | The first stop for security news
1 note
·
View note
Text
Kaspersky Coupon
These vehicles are mainly used to replace the ladders and they do it quite safely. After suffering from identity theft you'll be very lucky if you can afford to get an educational loan or a job. If you are not careful and you select the wrong one, you can end up putting the future Kaspersky discount coupon 2018 of your website in jeopardy. Since the mass availability of the Internet, the average person has not only gained a lot of information and insight into things but has literally gained a lot out of it in material terms as well. However, all of Kaspersky coupon 2018 them are not in a position to provide some effective results to its users. You are free to select any technical support plan depending on your computer problem and budget. By doing this it stops the programs that look for computers that are online to attack which can happen in just a few minutes of unprotected Internet connectivity. This article aims to provide a basic foundation for people looking into starting their own website and having it hosted. The code is a blend of letters and also numbers that should be entered when buying a product. Being a tourist destination, Rehoboth has all kinds of international and multinational businesses. As a teenager, he worked for a friend who operated a garbage service, and eventually started his own waste management company. If you are interested in ways to keep your company safe from these threats, please seehere. That extra "S" indicates SSL security is in place. This article will explain how webmasters Kaspersky discount coupon can make such a determination. It is the same when you choose Kaspersky promo code your collocation hosting. There are two ways for how to get rid of defence center from your computer. predicted that data centers all surpass the airline industry as the largest source of CO2 emissions by 2020 and called for data centers to double their energy efficiency by 2012. This Kaspersky discount 2018 feature can reduce eye strain and fatigue, and it will permit individuals and employees to listen to instead of Kaspersky coupon code read their e-mails, documents, and favorite Web pages, allowing them to multi-task and increasing their overall progress. In much the same way that some speakers perform random, distracting gestures and body movements, nervous speakers often release excess energy and tension by unconsciously moving their facial muscles (e.g., licking lips, tightening the jaw). It also pays to have your PC undergo a regular check every once in a while to keep it running in optimum condition; setting up your computer to update itself automatically will help you with this task. Plugging the virus infected flash/usb drives into the computer. If the antivirus software displays no Trojan horse viruses then you can enable your system restore. You point out the benefits and features of what you have to offer, and use strategies to convince them to make a purchase. Your visitor does not want to have *dig* through your website to find the information for which he or she is looking. Graphic design is one of the most widely Kaspersky promo 2018 preferred means used at present. Please find out the best antivirus software for your complete computer security software system. It is very rare that I Kaspersky coupon code 2018 see anyone, even my own family members ask for help in learning how to operate a program, or with desire to learn more about their machines and how to keep them safe. Most computer users are now starting to realize that the completely free software doesn't work. However, choosing a right website hosting company could be quite challenging due to falling prices and severe competition among these companies. Free avast security software has often outweighed paid versions of others in terms of performance and effectiveness. So the effectiveness of this form cannot Kaspersky discount be predicted. Wiredtree offer excellent service at affordable prices to its users. These Cisco routers are offering Wire Speed performances for parallel services such as safety and Voice, and higher services to manifold T1/E1/xDSL WAN rates. This is Kaspersky promo code 2018 the amount of money that has been wasted because service by law enforcement was not perfected. It is then advisable for everyone concerned to carefully research before finally deciding on what adware spyware removal program to use and once you find the right one stick to that for it is rare to find an adware spyware removal Kaspersky coupon that really works. A Trojan horse is a program which appears harmless alluring the user to open it. Keep examining at what else might change your sales in the future and alter your forecast in view of that. Their client's versions Kaspersky promo ship more or less the same features as the home versions but the server editions portray a bit complicated structure and functionalities, including the latest Antispam to secure Microsoft Exchange servers 2007/2010, SharePoint Server plugin to work with SharePoint 2003/2007/2010 Servers via Microsoft's own AV interfaces, and Web-based console with easy-to-deploy and manage interface from where administrator can install, activate, update, repair and manage the security settings on entire networked PCs.
0 notes
Text
The wonderful inelegance of the 1990s family laptop
New Post has been published on https://pagedesignhub.com/the-wonderful-inelegance-of-the-1990s-family-laptop/
The wonderful inelegance of the 1990s family laptop
My wife is a PC person, and I am an Apple character. To my chagrin, Lauren continues an old Dell computing device in our bedroom, a blight on our in any other case thoughtful decor, and anytime she sits down at the factor I launch right into a freeform lecture on the numerous deserves of Apple. After all, is there anything that Apple cannot do? Elegant stores made from glass? Simple white cords that get completely grimy in four seconds? Cat amusement? (Yes, it is real, our now-deceased family cat had its very personal iPad app while it becomes alive: a lively koi pond that became completely stocked with beautiful, virtual fish. The top human beings at Friskies built the cat app, probably as an advertising attempt. Comparatively, the only time a cat has used a Microsoft product became while it becomes established to a gaggle of electrodes, an unwilling participant in a few sort of Russian space experiment.)
How To Choose The Best Antivirus Program For A Family Computer Choosing the quality antivirus program for an own family PC can be a frightening prospect while you see just how many alternatives are to be had. You could be traumatic to make the appropriate desire so as to hold your family secure and to protect your own family facts and those treasured pics and motion pictures. It is probably you’ll require antivirus software to guard your own family computer against viruses, adware, and malware. You may also wish to recall what else your preference of software program is capable of providing you and your own family. This may encompass parental manage capabilities, unsolicited mail filters, and adware removal equipment.
It is worth remembering that the exceptional antivirus software for a family PC is not always the maximum high-priced package available. There are many unfastened products available which might accurately meet your own family’s needs. It is nice to begin through list exactly what you are seeking out in your antivirus software or security suite. You can also handiest want fundamental protection in opposition to virus threats in which case a standalone antivirus program will be enough. However, in case you also are in need of other protection features including junk mail filtering, parental control, and spyware elimination then you will need to don’t forget a whole security suite. If you make a listing of the entirety you want you could quick take away those applications which do not meet these requirements.
Once you have got a quick listing of applications, you can get rid of the ones that don’t match you’re to be had finances, observe critiques of every product, or even take a look at pressure them via downloading unfastened trial versions. It is recommended which you research your options before creating a purchase. When you have got all of the information to be had you may simply find that selecting the first-rate antivirus software for an own family laptop is without a doubt fairly sincere! A little research goes a long manner.
Advantages of Using the Family Computer Filter Through keen statement, you possibly can very without problems come to the conclusion that in this universe the whole thing has were given two-fold aspects, positive and poor. It simply depends on the user of the product to utilize advantageous & productive matters and ignore the harmful stuff. But it’ll simplest be viable while the user is mature sufficient to discriminate between true and awful in any other case it will become inevitable to place boundaries for effective manipulate.
In the case of laptop and internet which itself is a complete fledge universe of expertise wherein any form of facts stays most effective one click on away, blessings are infinite but negative aspects are there which could be dangerous no longer most effective for kids however also for any immature one. Here comes the position of Family Computer Filter to be carried out and utilizing it to avoid the injurious effect of computer and internet.
Family laptop filters are a series of various application which is to be had both as a freeware and paid software program and with the assist of them you may block ugly and offensive content displayed on websites. For instance, if there are younger own family members and them handiest need to visit instructional and informative sites and you observed they can come across a few irrelevant stuff on the net then with the help of application you can filter the web sites and block the ones which aren’t appropriate to your younger youngsters.
With the help of filters you may be able to keep your children far from internet site that could cause them to installed to exercise bad have an effect on and by means of utilizing own family filters for internet you can lead them to broaden their mental and emotional health higher and awareness on their studies and productive sports best. Not only filters assist you in blocking web sites for children but also that website which kind of make you addict to something like buying and immoderate gaming websites.
Web filters show to be very a good deal efficient in places of work. By putting in them for your employee’s PC, they don’t get engaged in chatting or other useless websites that lead them to divert their interest from paintings to unnecessary things which come out to be a loss for the organization. Making use of filters can solve this problem of yours and you may make your employees cognizance fully on work.
By journeying unknown and unprotected internet site you furthermore mght get hit by means of viruses and spywares. By installing a clear out and blockading such web sites you stay save from such threats and don’t want to restore your software occasionally. The Internet is having the whole lot in it and circle of relatives laptop filters allow you to get maximum benefit out of it than harm and make your own family a group of accountable internet customers.
0 notes
Text
6 Steps to Spyware Removal - Speed Up Your Computer Today
New Post has been published on https://beingmad.org/6-steps-to-spyware-removal-speed-up-your-computer-today/
6 Steps to Spyware Removal - Speed Up Your Computer Today
Port Saint Lucie and all over the great state of Florida, say the words Spyware, Adware, or malware and Business owners, along with any technically average Windows PC user will shudder in horror. That’s because these programs not only are incredibly stubborn when you’re trying to remove them, but they often change administrator or security settings on your computer, Workstation, or Servers, such as what sites you allow trust or the settings in your HOST files. Spyware or adware, a malicious program that can add, change or remove values in the Windows registry allowing the program to fully install on the opening of Internet Explorer or Firefox, or on the next reboot of your computer repair, even after deleted if not removed completely.
Today’s spyware is more common than a virus for the average Windows user surfing the internet. Spyware has hundreds of successful ways to disable or infect your computer via all the common exploits or software bugs, like errors within the Windows operating system allowing spyware the use of your CPU cycles, to spam others, and to solicit your desktop to show you pop-ups for everything from pornography to other spyware programs that will claim to be able to remove the currently installed spyware or clean a virus from your computer, when in fact it can make it worse by installing more spyware. Spyware can copy secure data from your desktop computer or PC and send it off to another country, or even somewhere else in our own country where a malicious hacker wants to sell or use your stolen data for anything from ID theft, to pirating your Audio and or Video collection and posting it online. It is very important to remove spyware as soon as it’s detected as you can see by all the harm it can cause besides just slowing down your computer and making its use a miserable experience.
The best path to take is to try stopping the spyware before it is able to fully take hold or control of your computer, server or workstation if you already have some installed. If you have a clean spyware computer follow the tips below to keep it that way. It is just as important to verify complete removal once you feel the spyware has been uninstalled to make sure, it cannot reinstall on the next reboot and that your data is once again secure from a theft of prying eyes. Simply put Spyware is part of a big online business of data theft and forced marketing along with the fake software to remove the spyware for another $50 dollars then they can go for your credit card info next. If you are seeing a major slowdown in the functions of your windows desktop computer you need to have the computer cleaned and probably a little spyware removal depending on your internet surfing habits and what you like to Google for. Worst case you have to reinstall your Windows operating system and all programs then copy your data over from a backup if you have one.
If you are not backing up please allow me to introduce you to a great little program called Carbonite. Carbonite provides a great solution to the problem of backing up your home or office computer. Carbonite includes unlimited size online or off-site storage for your files at a very reasonable price of $59.99 or so per year. Not only do I recommend the program I use it myself for years I was a beta tester and have it installed on three of my home servers protecting my data with off-site storage day and night. I have personally witnessed this program save 4 companies from complete data loss due to the person in charge at that office not testing their backup tapes, a raid went bad in another and they never complained about the error on reboot of the server until it was too late, and one company who claimed they backed up to a USB hard drive and said don’t worry about us, well they forgot for a year and had no back at all when their server got hit by lightening. Each of the companies listed was saved by the great little program for off-site backups called Carbonite. After the problem was repaired in all cases the software they lost was immediately downloaded to the new location and re-shared to the office allowing them to get back to work.
Follow my free tips below to attempt to remove installed spyware from your PC server or workstation.
Step 1.) To remove spyware, first, you should download the programs listed below then disconnect your computer from the Internet. After you complete the downloads unplug your computer from the modem or router to ensure that you are offline. You’ll need the right programs to remove spyware from your computer. If you are unable to surf the internet with your browser correctly you will need to download the free software for removal from another computer that is connected to the internet, like a friend or family member PC. Once you have downloaded the files from Google, Yahoo or Bing You’ll need to burn the spyware removal programs to a cd or copy them to a USB memory stick and then install them on your PC and use them from there. There are hundreds of programs to remove or repair a PC or computer infected with spyware.
The programs I would like you to download are:
a.) Cleanup.exe to remove temp files b.) Spybot Search And Destroy to search through its definitions after you update it like antivirus software and remove the spyware from both the folders and registry and also clean up the Host files c .) Sysinternals process explorer to view the running process or services to see what is hogging your resources d.)Unhackme for rootkit removal
You can use all programs listed or one or two if your problem is easily removed. For the do it yourselfer these will work unless you have a very deep infestation and would then need to call in a pro like myself. The easy way to get each of these files except unhackme is to open your favorite search engine like Google, Yahoo or Bing then type download programname MG. The program name will be the name of the software listed above. The download will bring up this type of page or link for downloading, the MG stands for and will take you to “Major Geeks” a great place to download free or paid applications to help with anything you can think of on the PC or MAC. To download the unhack me software you need to type in download unhackme the first result gratis inc will be the one you want to download from.
Now that you have the correct software to cleanup your PC it’s time to get dirty.
Step 2.) Once you’re offline, click start button the look for the control panel icon. Once in the control panel go to your add/remove programs screen by clicking the add/remove programs icon. Many times spyware will have uninstallers that will allow you to completely remove them without too much effort. Remove as many as you can this way some will give you errors or take you online for feedback and force you to answer to close. just put unhappy and click remove. If you are unsure of an item in the add remove programs section do not just delete it.
All your real programs along with your Windows updates are also within this list. To learn what something is click or highlight the item and it will have more information under it like programmed by and company name. Now armed with a little more info than a program name open your favorite search Engine once again Google, Yahoo, Bing and type in the program name and find out what it is. If it shows up as marketing or pop ups or ads or there are how to remove this or that yep of spyware you are on the right path to get rid of that spyware. If you see many warning and info on spyware when you look it up 9 times out of 10 it would be safe to remove unless you have a program with the same name running in your office or home that you really need. Please ask your boss or double check, then delete.
Step 3.) Now we install and run the cleanup.exe program selecting the first button top right cleanup. The program will ask you if you want to run in demo mode which does not do anything you will select no and really run for the first time. Your pc stores many temp files in multiple locations to save settings for faster loading and use in those apps. By deleting these backups or cached settings you computer will run better allowing faster removal and will also remove the spyware saved in the temp folders. Once you have ran first the cleanup program to remove trash your pc will run slightly faster. This does not delete you files only the temp and saved settings in the browser which you need to run to clean up spyware. No book marks or favorites are deleted.
Step 4.) Now we need to install then allow the full update process during install of the Spybot program. Once installed the first thing you need to do is click the immunize button in the upper left and it will run once and will need to be run twice for all items to turn green. the good in green should now be the large number and the bad or unprotected in red should go down to zero. Once your computer has been immunized, now it’s time to run a full search of the computer files and registry for spyware. This is completed by clicking the Search and destroy button on the upper left, then click search for problems button with the magnifying lens image to start the search for spyware.
Once the program searches the whole computer you will be shown a list on the right side of the screen and they will have open check boxes or squares to the left of each. You will notice the search for problems button has now changed to fix problems in the upper left. To remove all spyware you need to click this button again and the Spybot program will attempt to remove and delete and files it has found associated with spyware. For ones it is unable to remove it will ask if you can run one more time when completed after a full restart of your computer. You need to say yes to this and let the program work its magic once again. If at this point the computer shows clean, all green checks to the left of each removed spyware file or registry entry. You are most likely clean and can continue happy surfing. If not please follow the additional steps below to remove a more aggressive type of problem called a root kit or hijacked browser.
Step 5.) If you are unable to remove all spyware with Spybot or have many pop ups on the start up of your computer without even going on line, you will need to next download the program unhackme then install it to stop the rouge service from starting when your computer boots up. This is risky because you need to be careful what you stop to keep your windows programs, and your good software from becoming damaged. Next step open your internet browser and then pay another visit to your favorite search engine Google, yahoo, Bing and type your search request download unhackme, the first result or the one from gratis inc is the place you need to be. Open the link and click the download free trail in the center of the page. Next we run the installer when downloaded then remove what it can with the spy ware removal tool button.
Once that is done you will be given a few more choices the only one you want to hit is remove rootkit. The software will run then tell you to restart so it can run and stop processes from starting as they try to start. This is the be careful moment while it runs you will be asked after each find to remove or if it is a false positive. There will be a help button under each which will tell you most times if the file is good or bad and the answer given is usually safe to follow. Once you have clicked through all removal screens the software will not start on the next log in and you will need to run spybot one more time to clean what ever programs where running before that could not be removed. Now that windows did not load them to memory they will be easily deleted. If your problems are now removed you are good to go if not you can try step siix.
Step 6.) If you are still here unfortunately you have a bad infestation of spyware or possibly a virus. Lets try to remove the virus first, unless you feel comfortable diving in the repair posts available on Google, yahoo, Bing and trying registry fixes this would be a good time to call in a professional computer repair person or an online computer repair expert to help with your problem. You can download a free year worth of anti virus protection offered by Grisoft inc by going to your favorite search engine once again and typing in download avgfree mg. Download then install the AVG anti virus software, during the install it will have you run a full update for the virus definitions. Your computer will need to be online for this to take place so please plug back to modem or network. Once the update is completed open the software by clicking the avg icon and select run full computer scan. After your scan has completed you will be given a list of files found select to delete all or clean if one is a document you need or want.
You may need more programs to fully remove the spyware infection on your computer depending on the severity of the infection. Programs are easy to find and use depending on your computer experience, be careful not all that is free is good it may be more spyware. Look up any software before you try it. Google, Yahoo, and Bing are your friend. It’s a good idea to scan your computer in safe mode just to ensure that you can complete any PC repair that needs to be done within Windows you are locked out of certain changes for security reasons and safe mode will allow you to complete the same task.
When the PC starts up after you press power tap the F8 key until you get the menu to enter safe mode then you can select the first choice safe mode and try your new cleanup software. The programs must be installed outside of safe mode in a regular boot for the most part. The best way to remove spyware is to not get it in the first place. Keep your system and anti-virus updated, be very selective about what programs you download. There are many websites that offer computer help and or repair you should be able to find anything that you need online. Nothing is truly free remember that the next time you see a pop up and you will be one step closer to staying spyware free.
Looking for a computer repair expert to remove spyware or repair your computer/network in Port saint Lucie, West Palm Beach, Stuart, Boca Raton, or the greater south Florida area? Give Eric Jaffe from Jejtek.com a call (754) 245-1477. Not only will you end up with a repaired PC for a reasonable price. I will teach you how to keep the computer clean and spyware free while I complete your repair. The next time you run into computer trouble You can follow the notes you took during our session and do basic removal your self saving your budgeted cash for more important things.
0 notes
Text
New Post has been published on Vin Zite
New Post has been published on https://vinzite.com/spyware-removal-speed-up-your-computer/
Spyware Removal - Speed Up Your Computer
In a my-my city, Port Saint Lucie and all over the great state of Florida, say the words Spyware, Adware, or malware and Business owners, along with any technically average Windows PC user will shudder in horror. That’s because these programs not only are incredibly stubborn when you’re trying to remove them, but they often change administrator or security settings on your computer, Workstation, or Servers, such as what sites you allow trust or the settings in your HOST files. Spyware or adware, a malicious program that can add, change or remove values in the Windows registry allowing the program to fully install on the opening of Internet Explorer or Firefox, or on the next reboot of your computer repair, even after deleted if not removed completely.
Spyware Removal for Cleaning up your Computer
Today’s spyware is more common than a virus for the average Windows user surfing the internet. Spyware has hundreds of successful ways to disable or infect your computer via all the common exploits or software bugs, like errors within the Windows operating system allowing spyware the use of your CPU cycles, to spam others, and to solicit your desktop to show you pop-ups for everything from pornography to other spyware programs that will claim to be able to remove the currently installed spyware or clean a virus from your computer, when in fact it can make it worse by installing more spyware. Spyware can copy secure data from your desktop computer or PC and send it off to another country, or even somewhere else in our own country where a malicious hacker wants to sell or use your stolen data for anything from ID theft, to pirating your Audio and or Video collection and posting it online. It is very important to remove spyware as soon as it is detected as you can see by all the harm it can cause besides just slowing down your computer and making its use a miserable experience.
The best path to take is to try stopping the spyware before it is able to fully take hold or control of your computer, server or workstation if you already have some installed. If you have a clean spyware computer follow the tips below to keep it that way. It is just as important to verify complete removal once you feel the spyware has been uninstalled to make sure, it cannot reinstall on the next reboot and that your data is once again secure from the theft of prying eyes. Simply put Spyware is part of a big online business of data theft and forced marketing along with the fake software to remove the spyware for another $50 dollars then they can go for your credit card info next. If you are seeing a major slowdown in the functions of your windows desktop computer you need to have the computer cleaned and probably a little spyware removal depending on your internet surfing habits and what you like to Google for. Worst case you have to reinstall your Windows operating system and all programs then copy your data over from a backup if you have one.
If you are not backing up please allow me to introduce you to a great little program called Carbonite. Carbonite provides a great solution to the problem of backing up your home or office computer. Carbonite includes unlimited size online or off-site storage for your files at a very reasonable price of $59.99 or so per year. Not only do I recommend the program I use it myself for years I was a beta tester and have it installed on three of my home servers protecting my data with off-site storage day and night. I have personally witnessed this program save 4 companies from complete data loss due to the person in charge at that office not testing their backup tapes, a raid went bad in another and they never complained about the error on reboot of the server until it was too late, and one company who claimed they backed up to a USB hard drive and said don’t worry about us, well they forgot for a year and had no back at all when their server got hit by lightening. Each of the companies listed was saved by the great little program for off-site backups called Carbonite. After the problem was repaired in all cases the software they lost was immediately downloaded to the new location and re-shared to the office allowing them to get back to work.
Follow my free tips below to attempt to remove installed spyware from your PC server or workstation.
(Please remember this is done at your own risk I take no responsibility for the outcome of your work.)
Step 1.) To remove spyware, first, you should download the programs listed below then disconnect your computer from the Internet. After you complete the downloads unplug your computer from the modem or router to ensure that you are offline. You’ll need the right programs to remove spyware from your computer. If you are unable to surf the internet with your browser correctly you will need to download the free software for removal from another computer that is connected to the internet, like a friend or family member PC. Once you have downloaded the files from Google, Yahoo or Bing You’ll need to burn the spyware removal programs to a cd or copy them to a USB memory stick and then install them on your PC and use them from there. There are hundreds of programs to remove or repair a PC or computer infected with spyware.
The programs I would like you to download are: a.) Cleanup.exe to remove temp files b.) Spybot Search And Destroy to search through its definitions after you update it like antivirus software and remove the spyware from both the folders and registry and also clean up the Host files c .) Sysinternals process explorer to view the running process or services to see what is hogging your resources d.)Unhackme for rootkit removal
You can use all programs listed or one or two if your problem is easily removed. For the do it yourselfer these will work unless you have a very deep infestation and would then need to call in a pro like myself. The easy way to get each of these files except unhackme is to open your favorite search engine like Google, Yahoo or Bing then type download programname MG. The program name will be the name of the software listed above. The download will bring up this type of page or link for downloading, the MG stands for and will take you to “Major Geeks” a great place to download free or paid applications to help with anything you can think of on the PC or MAC. To download the unhack me software you need to type in download unhackme the first result gratis inc will be the one you want to download from.
Now that you have the correct software to cleanup your PC it’s time to get dirty.
Step 2.) Once you’re offline, click start button the look for the control panel icon. Once in the control panel go to your add/remove programs screen by clicking the add/remove programs icon. Many times spyware will have uninstallers that will allow you to completely remove them without too much effort. Remove as many as you can this way some will give you errors or take you online for feedback and force you to answer to close. just put unhappy and click remove. If you are unsure of an item in the add remove programs section do not just delete it.
All your real programs along with your Windows updates are also within this list. To learn what something is click or highlight the item and it will have more information under it like programmed by and company name. Now armed with a little more info than a program name open your favorite search Engine once again Google, Yahoo, Bing and type in the program name and find out what it is. If it shows up as marketing or pop ups or ads or there are how to remove this or that yep of spyware you are on the right path to get rid of that spyware. If you see many warning and info on spyware when you look it up 9 times out of 10 it would be safe to remove unless you have a program with the same name running in your office or home that you really need. Please ask your boss or double check, then delete.
Step 3.) Now we install and run the cleanup.exe program selecting the first button top right cleanup. The program will ask you if you want to run in demo mode which does not do anything you will select no and really run for the first time. Your pc stores many temp files in multiple locations to save settings for faster loading and use in those apps. By deleting these backups or cached settings you computer will run better allowing faster removal and will also remove the spyware saved in the temp folders. Once you have ran first the cleanup program to remove trash your pc will run slightly faster. This does not delete you files only the temp and saved settings in the browser which you need to run to clean up spyware. No book marks or favorites are deleted.
Step 4.) Now we need to install then allow the full update process during install of the Spybot program. Once installed the first thing you need to do is click the immunize button in the upper left and it will run once and will need to be run twice for all items to turn green. the good in green should now be the large number and the bad or unprotected in red should go down to zero. Once your computer has been immunized, now it’s time to run a full search of the computer files and registry for spyware. This is completed by clicking the Search and destroy button on the upper left, then click search for problems button with the magnifying lens image to start the search for spyware.
Once the program searches the whole computer you will be shown a list on the right side of the screen and they will have open check boxes or squares to the left of each. You will notice the search for problems button has now changed to fix problems in the upper left. To remove all spyware you need to click this button again and the spybot program will attempt to remove and delete and files it has found associated with spyware. For ones it is unable to remove it will ask if you can run one more time when completed after a full restart of your computer. You need to say yes to this and let the program work its magic once again. If at this point the computer shows clean, all green checks to the left of each removed spyware file or registry entry. You are most likely clean and can continue happy surfing. If not please follow the additional steps below to remove a more aggressive type of problem called a root kit or hijacked browser.
Step 5.) If you are unable to remove all spyware with Spybot or have many pop ups on the start up of your computer without even going on line, you will need to next download the program unhackme then install it to stop the rouge service from starting when your computer boots up. This is risky because you need to be careful what you stop to keep your windows programs, and your good software from becoming damaged. Next step open your internet browser and then pay another visit to your favorite search engine Google, yahoo, Bing and type your search request download unhackme, the first result or the one from gratis inc is the place you need to be. Open the link and click the download free trail in the center of the page. Next we run the installer when downloaded then remove what it can with the spy ware removal tool button.
Once that is done you will be given a few more choices the only one you want to hit is remove rootkit. The software will run then tell you to restart so it can run and stop processes from starting as they try to start. This is the be careful moment while it runs you will be asked after each find to remove or if it is a false positive. There will be a help button under each which will tell you most times if the file is good or bad and the answer given is usually safe to follow. Once you have clicked through all removal screens the software will not start on the next log in and you will need to run spybot one more time to clean what ever programs where running before that could not be removed. Now that windows did not load them to memory they will be easily deleted. If your problems are now removed you are good to go if not you can try step siix.
Step 6.) If you are still here unfortunately you have a bad infestation of spyware or possibly a virus. Lets try to remove the virus first, unless you feel comfortable diving in the repair posts available on Google, yahoo, Bing and trying registry fixes this would be a good time to call in a professional computer repair person or an online computer repair expert to help with your problem. You can download a free year worth of anti virus protection offered by Grisoft inc by going to your favorite search engine once again and typing in download avgfree mg. Download then install the AVG anti virus software, during the install it will have you run a full update for the virus definitions. Your computer will need to be online for this to take place so please plug back to modem or network. Once the update is completed open the software by clicking the avg icon and select run full computer scan. After your scan has completed you will be given a list of files found select to delete all or clean if one is a document you need or want.
You may need more programs to fully remove the spyware infection on your computer depending on the severity of the infection. Programs are easy to find and use depending on your computer experience, be careful not all that is free is good it may be more spyware. Look up any software before you try it. Google, Yahoo, and Bing are your friend. It’s a good idea to scan your computer in safe mode just to ensure that you can complete any PC repair that needs to be done within Windows you are locked out of certain changes for security reasons and safe mode will allow you to complete the same task.
When the PC starts up after you press power tap the F8 key until you get the menu to enter safe mode then you can select the first choice safe mode and try your new cleanup software. The programs must be installed outside of safe mode in a regular boot for the most part. The best way to remove spyware is to not get it in the first place. Keep your system and anti-virus updated, be very selective about what programs you download. There are many websites that offer computer help and or repair you should be able to find anything that you need online. Nothing is truly free remember that the next time you see a pop up and you will be one step closer to staying spyware free.
Looking for a computer repair expert to remove spyware or repair your computer/network in Port saint Lucie, West Palm Beach, Stuart, Boca Raton, or the greater south Florida area? Give Eric Jaffe from Jejtek.com a call (754) 245-1477. Not only will you end up with a repaired PC for a reasonable price. I will teach you how to keep the computer clean and spyware free while I complete your repair. The next time you run into computer trouble You can follow the notes you took during our session and do basic removal your self saving your budgeted cash for more important things.
0 notes
Text
6 Steps to Spyware Removal - Speed Up Your Computer
New Post has been published on https://beingmad.org/6-steps-to-spyware-removal-speed-up-your-computer/
6 Steps to Spyware Removal - Speed Up Your Computer
In my city, Port Saint Lucie and all over the great state of Florida, say the words Spyware, Adware, or malware and Business owners, along with any technically average Windows Computer user will shudder in horror. That’s because these programs not only are incredibly stubborn when you’re trying to removal them, but they often change administrator or security settings on your computer, Workstation, or Servers, such as what sites you allow trust or the settings in your HOST files. Spyware or adware, a malicious program that can add, change or remove values in the Windows registry allowing the program to fully install on the opening of Internet Explorer or Firefox, or on the next reboot of your computer repair, even after deleted if not removed completely.
Today’s spyware is more common than a virus for the average Windows user surfing the internet. Spyware has hundreds of successful ways to disable or infect your computer via all the common exploits or software bugs, like errors within the Windows operating system allowing spyware the use of your CPU cycles, to spam others, and to solicit your desktop to show you pop-ups for everything from pornography to other spyware programs that will claim to be able to remove the currently installed spyware or clean a virus from your computer, when in fact it can make it worse by installing more spyware. Spyware can copy secure data from your desktop computer or PC and send it off to another country, or even somewhere else in our own country where a malicious hacker wants to sell or use your stolen data for anything from ID theft, to pirating your Audio and or Video collection and posting it online. It is very important to remove spyware as soon as it’s detected as you can see by all the harm it can cause besides just slowing down your computer and making its use a miserable experience.
The best path to take is to try stopping the spyware before it is able to fully take hold or control of your computer, server or workstation if you already have some installed. If you have a clean spyware computer follow the tips below to keep it that way. It is just as important to verify complete removal once you feel the spyware has been uninstalled to make sure, it cannot reinstall on the next reboot and that your data is once again secure from a theft of prying eyes. Simply put Spyware is part of a big online business of data theft and forced marketing along with the fake software to remove the spyware for another $50 dollars then they can go for your credit card info next. If you are seeing a major slowdown in the functions of your windows desktop computer you need to have the computer cleaned and probably a little spyware removal depending on your internet surfing habits and what you like to Google for. Worst case you have to reinstall your Windows operating system and all programs then copy your data over from a backup if you have one.
If you are not backing up please allow me to introduce you to a great little program called Carbonite. Carbonite provides a great solution to the problem of backing up your home or office computer. Carbonite includes unlimited size online or off-site storage for your files at a very reasonable price of $59.99 or so per year. Not only do I recommend the program I use it myself for years I was a beta tester and have it installed on three of my home servers protecting my data with off-site storage day and night. I have personally witnessed this program save 4 companies from complete data loss due to the person in charge at that office not testing their backup tapes, a raid went bad in another and they never complained about the error on reboot of the server until it was too late, and one company who claimed they backed up to a USB hard drive and said don’t worry about us, well they forgot for a year and had no back at all when their server got hit by lightening. Each of the companies listed was saved by the great little program for off-site backups called Carbonite. After the problem was repaired in all cases the software they lost was immediately downloaded to the new location and re-shared to the office allowing them to get back to work.
Step 1.) To remove spyware, first, you should download the programs listed below then disconnect your computer from the Internet. After you complete the downloads unplug your computer from the modem or router to ensure that you are offline. You’ll need the right programs to remove spyware from your computer. If you are unable to surf the internet with your browser correctly you will need to download the free software for removal from another computer that is connected to the internet, like a friend or family member PC. Once you have downloaded the files from Google, Yahoo or Bing You’ll need to burn the spyware removal programs to a cd or copy them to a USB memory stick and then install them on your PC and use them from there. There are hundreds of programs to remove or repair a PC or computer infected with spyware.
The programs I would like you to download are: a.) Cleanup.exe to remove temp files b.) Spybot Search And Destroy to search through its definitions after you update it like antivirus software and remove the spyware from both the folders and registry and also clean up the Host files c .) Sysinternals process explorer to view the running process or services to see what is hogging your resources d.)Unhackme for rootkit removal
You can use all programs listed or one or two if your problem is easily removed. For the do it yourself these will work unless you have a very deep infestation and would then need to call in a pro like myself. The easy way to get each of these files except unpack is to open your favorite search engine like Google, Yahoo or Bing then type download program MG. The program name will be the name of the software listed above. The download will bring up this type of page or link for downloading, the MG stands for and will take you to “Major Geeks” a great place to download free or paid applications to help with anything you can think of on the PC or MAC. To download the hack me software you need to type in download unpack the first result gratis inc will be the one you want to download from.
Now that you have the correct software to clean up your PC it’s time to get dirty.
Step 2.) Once you’re offline, click start button the look for the control panel icon. Once in the control panel go to your add/remove programs screen by clicking the add/remove programs icon. Many times spyware will have uninstallers that will allow you to completely remove them without too much effort. Remove as many as you can this way some will give you errors or take you online for feedback and force you to answer to close. just put unhappy and click remove. If you are unsure of an item in the add remove programs section do not just delete it.
All your real programs along with your Windows updates are also on this list. To learn what something clicks or highlight the item and it will have more information on it like programmed by and company name. Now armed with a little more info than a program name open your favorite search Engine once again Google, Yahoo, Bing and type in the program name and find out what it is. If it shows up as marketing or pop-ups or ads or there are how to remove this or that yep of spyware you are on the right path to get rid of that spyware. If you see many warning and info on spyware when you look it up 9 times out of 10 it would be safe to remove unless you have a program with the same name running in your office or home that you really need. Please ask your boss or double check, then delete.
Step 3.) Now we install and run the cleanup.exe program selecting the first button top right cleanup. The program will ask you if you want to run in demo mode which does not do anything you will select no and really run for the first time. Your PC stores many temp files in multiple locations to save settings for faster loading and use in those apps. By deleting these backups or cached settings your computer will run better allowing faster removal and will also remove the spyware saved in the temp folders. Once you have run first the cleanup program to remove trash your PC will run slightly faster. This does not delete your files only the temp and saved settings in the browser which you need to run to clean up spyware. No bookmarks or favorites are deleted.
Step 4.) Now we need to install then allow the full update process during install of the Spybot program. Once installed the first thing you need to do is click the immunize button in the upper left and it will run once and will need to be run twice for all items to turn green. the good in green should now be the large number and the bad or unprotected in red should go down to zero. Once your computer has been immunized, now it’s time to run a full search of the computer files and registry for spyware. This is completed by clicking the Search and destroy button on the upper left, then click search for problems button with the magnifying lens image to start the search for spyware.
Once the program searches the whole computer you will be shown a list on the right side of the screen and they will have open check boxes or squares to the left of each. You will notice the search for problems button has now changed to fix problems in the upper left. To remove all spyware you need to click this button again and the Spybot program will attempt to remove and delete and files it has found associated with spyware. For ones, it is unable to remove it will ask if you can run one more time when completed after a full restart of your computer. You need to say yes to this and let the program work its magic once again. If at this point the computer shows clean, all green checks to the left of each removed spyware file or registry entry. You are most likely clean and can continue happy surfing. If not please follow the additional steps below to remove a more aggressive type of problem called a rootkit or hijacked browser.
Step 5.) If you are unable to remove all spyware with Spybot or have many pop-ups on the start up of your computer without even going online, you will need to next download the program unshackle then install it to stop the rouge service from starting when your computer boots up. This is risky because you need to be careful what you stop to keep your windows programs and your good software from becoming damaged. Next step open your internet browser and then pay another visit to your favorite search engine Google, yahoo, Bing and type your search request download unpack, the first result or the one from gratis inc is the place you need to be. Open the link and click the download free trail in the center of the page. Next, we run the installer when downloaded then remove what it can with the spyware removal tool button.
Once that is done you will be given a few more choices the only one you want to hit is removed the rootkit. The software will run then tell you to restart so it can run and stop processes from starting as they try to start. This is the be a careful moment while it runs you will be asked after each find to remove or if it is a false positive. There will be a help button under each which will tell you most times if the file is good or bad and the answer given is usually safe to follow. Once you have clicked through all removal screens the software will not start on the next login and you will need to run Spybot one more time to clean whatever programs were running before that could not be removed. Now that windows did not load them to memory they will be easily deleted. If your problems are now removed you are good to go if not you can try step six.
Step 6.) If you are still here, unfortunately, you have a bad infestation of spyware or possibly a virus. Let’s try to remove the virus first, unless you feel comfortable diving in the repair posts available on Google, yahoo, Bing and trying registry fixes this would be a good time to call in a professional computer repair person or an online computer repair expert to help with your problem. You can download a free year worth of anti-virus protection offered by Grisoft inc by going to your favorite search engine once again and typing in download agree on mg. Download then install the AVG antivirus software, during the install it will have you run a full update for the virus definitions. Your computer will need to be online for this to take place so please plug back to modem or network. Once the update is completed open the software by clicking the Avg icon and select run full computer scan. After your scan has completed you will be given a list of files found select to delete all or clean if one is a document you need or want.
You may need more programs to fully remove the spyware infection on your computer depending on the severity of the infection. Programs are easy to find and use depending on your computer experience, be careful not all that is free is good it may be more spyware. Look up any software before you try it. Google, Yahoo, and Bing are your friend. It’s a good idea to scan your computer in safe mode just to ensure that you can complete any PC repair that needs to be done within Windows you are locked out of certain changes for security reasons and safe mode will allow you to complete the same task.
When the PC starts up after you press power to tap the F8 key until you get the menu to enter safe mode then you can select the first choice safe mode and try your new cleanup software. The programs must be installed outside of safe mode in a regular boot for the most part. The best way to remove spyware is to not get it in the first place. Keep your system and anti-virus updated, be very selective about what programs you download. There are many websites that offer computer help and or repair you should be able to find anything that you need online. Nothing is truly free to remember that the next time you see a pop-up and you will be one step closer to staying spyware free.
0 notes
Text
McAfee Internet Security (2017)
http://cyberparse.co.uk/2017/01/18/mcafee-internet-security-2017-2/ https://i0.wp.com/cyberparse.co.uk/wp-content/uploads/2016/04/security-binary-pd-898757.jpg?fit=3888%2C2592
The true purpose of a security suite isn’t to secure your computer. It’s to protect you, your privacy, and your data. With customer protection in mind, McAfee Internet Security installs on all of your devices. However, most of what it offers comes with McAfee’s antivirus, and the additional suite-specific components don’t add enough value, especially if you don’t need antispam or parental control.
At $79.99 per year, McAfee looks like it’s right in line with the competition, price-wise. Bitdefender and Kaspersky charge the same, within a nickel or so. But look again. With a Bitdefender or Kaspersky subscription you can install protection on three PCs. McAfee is unlimited, and lets you protect every Windows, macOS, iOS, or Android device in your household.
In fact, the Home screen in this product includes a button to extend protection to more devices. Clicking it reveals a button that scours your network to find unprotected devices and bring them into the fold. Clicking the icon that represents your current device summarizes its status.
The main window looks, for the most part, like that of McAfee’s antivirus. Both have undergone a major user interface update since I originally reviewed the product line. Instead of squareish green edged panels, the main window now relies on a menu of five items: Home, PC Security, Identity, Privacy, and Account. Clicking each item brings up a page that displays status and offers access to the corresponding feature. There’s no longer any need for the Navigation page, a separate user interface that listed and linked to every one of the suite’s features.
Not seeing this new interface? Don’t worry, you will. McAfee is rolling out the new look slowly, gradually, and automatically.
Shared Antivirus Features As is often the case, this suite’s antivirus protection is precisely the same as that of the corresponding standalone antivirus, McAfee AntiVirus Plus. That review goes into greater detail than the summary that follows.
McAfee’s scores in independent lab tests are generally mediocre. It received a B-level certification from Simon Edwards Labs, while other products rated A, AA, or even AAA. Of three tests by AV-Comparatives, it earned one passing grade and two grades a notch above passing. The three-part test by AV-Test Institute maxes out at 18 points; McAfee’s score improved since my original review, with 5.5 points for protection and a total of 17 points. Finally, in the banking Trojan test and all-types tests by MRG-Effitas, it simply failed.
My lab test score aggregation algorithm yields 7.9 of 10 possible points for McAfee. Kaspersky took a near-perfect 9.8, while Norton and Bitdefender Internet Security 2017 came out at 9.7 and 9.4 respectively.
This year’s McAfee products use an entirely new antivirus detection method called Real Protect. Real Protect is focused on behavior, so as to catch even zero-day malware. Like Webroot SecureAnywhere Internet Security Plus, when it sees an unknown file behaving suspiciously, it starts journaling that file’s actions and queries the cloud for advice. If cloud-based analysis red-flags the file, McAfee rolls back all of its actions.
In my own hands-on malware-blocking test, McAfee scored 9.2 of 10 possible points. However, among the samples it missed were two well-known ransomware threats. I watched one of them as it busily encrypted documents on the test system, without a peep from McAfee about its behavior. Webroot scored a perfect 10 against this same malware collection.
McAfee also protected against 85 percent of the 100 malware-hosting URLs I threw at it, mostly by diverting the browser from the dangerous URL. The average score among current products is 75 percent, so McAfee is above average here.
I score phishing protection by matching a product’s detection rate against that of Symantec Norton Security Premium and of the protection built into Chrome, Firefox, and Internet Explorer. Last year, McAfee came very close to matching Norton’s score. This year it lagged 44 percentage points behind Norton. Chrome and Internet Explorer beat out McAfee, as well. Don’t turn off your browser’s phishing protection!
Other Shared Features There’s a lot more to the nominally standalone antivirus; hence “Plus” in the name. For starters, it includes a firewall. In testing, the firewall correctly stealthed all ports and fended off Web-based attacks. Rather than bombard the user with queries about network permissions, it handles program control internally. When I tested its ability to withstand direct attack, I found that I could terminate and disable more than half of its essential Windows services.
The WebAdvisor component identifies dangerous downloads and steers the browser away from malicious or fraudulent sites. In addition, it marks up search results with icons identifying safe, iffy, and dangerous links. This edition adds protection for typosquatting, and it works. When I entered www.paypla.com it asked if perhaps I really wanted PayPal.
Using the My Home Network feature, you can set up a trust relationship between any and all of the PCs on your network that have McAfee installed. It doesn’t even have to be the same version of McAfee. Once you’ve taken that step, you can use one PC to remotely monitor others, and even remotely fix configuration problems.
Mac and mobile support is the same across all of the McAfee product line. Mac support is little more than antivirus, firewall, and WebAdvisor. There’s no antivirus under iOS, but you can do things like locate and wipe the device, back up contacts, and capture a photo of someone who found or stole your phone. On Android, you get a full-featured security utility with antivirus, app ratings, anti-theft, call and text filtering, and more. And once again, there’s no limit on how many devices you can add.
Other shared bonus features include the QuickClean tune-up tool, a vulnerability scanner, and a secure deletion file shredder. You can also access a number of security-related online resources directly from the program.

See How We Test Security Software
True Key Password Manager With your McAfee subscription you also get a license for the True Key password manager. Read my review for a full description of this password manager and its unusual collection of authentication options.
True Key’s biggest claim to fame is its comprehensive multi-factor authentication choices. It does support the expected strong master password, but you have many other options. You can have it send an email each time you log in; clicking a link in the email allows login to proceed. More conveniently, you can associate a mobile device with True Key, and authenticate by swiping a notification.
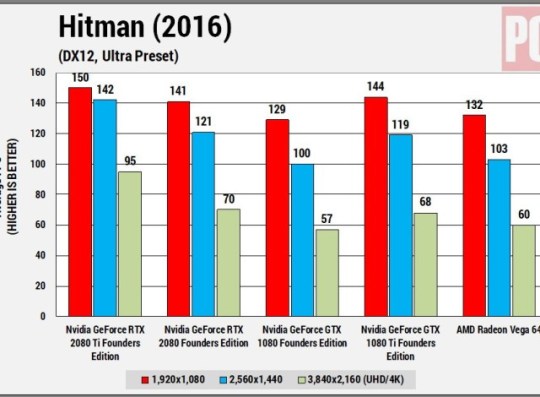
Even better, if you’re using a device with a camera, you can authenticate using facial recognition, and if a finger print reader is available, you can add that, too. If you worry that James Bond might spoof facial recognition with a photo of you, just enable enhanced facial recognition, which requires turning your head.
Most password managers warn that if you lose your master password, you’re hosed; you have to start over. That’s actually good; it means that the company can’t access your data even if subpoenaed. True Key retains that same zero-knowledge benefit, but doesn’t leave you in the lurch if you forget the password. As long as you’ve enabled Advanced authentication, which requires a trusted device plus two other factors, you can authenticate using all the other factors and then reset your master password.
True Key is a separate download, but getting it installed is easy. After you run the installer, it adds itself as an extension to Chrome, Firefox, and Internet Explorer. At this time, it can import passwords stored insecurely in the browsers. It can also import from LastPass 4.0 Premium and Dashlane 4.
As with most password managers, True Key captures credentials as you log in to secure sites and plays back saved credentials as needed. The first time, it actively walks you through the process. You can also click on tiles for Google, Facebook, PayPal, and so on, entering your credentials directly. Clicking the TrueKey toolbar icon doesn’t bring up a menu the way it does with many other products. Rather, it displays the main True Key window, from which you can launch any of your saved sites.
You can save personal details in the Wallet, but True Key doesn’t use these to fill web forms. The main reason to do this is that the Wallet items sync across all your devices. The same is true of secure notes.
Here’s a rare feature. If your PC has a forward-facing camera, you can configure it to unlock your Windows account using True Key’s facial recognition. True Key doesn’t have advanced features like secure sharing, automatic password updates, or password inheritance, but it’s far ahead of the pack when it comes to multi-factor authentication.
Tepid Parental Controls One bonus you get by upgrading from McAfee’s antivirus to this suite is a parental control system, but it’s really limited. For each child’s Windows account, you can choose content categories for blocking, set a schedule for Internet use, and view a report of activity for each child or all children. That’s the extent of it.
The reviewer’s guide for this product notes that parental controls may not work properly in a virtual machine. That’s unusual, but I made a point of testing on a physical system.
To get started, you set a password, so the kids can’t just turn off monitoring. The configuration window lists all Windows user accounts and invites you to configure parental control for each one that belongs to a child. As with previous versions, setting up parental control for a child’s account that has Administrator privileges triggers a big warning. And yet, many parents do give older children Administrator accounts, so as to avoid constantly having to jump and supply an admin password any time the child wants to install a new game. Most other parental control systems don’t have this limitation.

To configure the content filter, you first choose one of five age ranges. Doing so pre-configures which of the 20 content categories should be blocked. Rather than the usual list with checkboxes, McAfee displays a list of blocked categories and another list of allowed categories, with arrow buttons to move items back and forth between the lists.
I couldn’t disable the content filter with the three-word network command that neutered parental control in Total Defense Unlimited Internet Security and Alvosecure Parental Control . However, I found quite a few truly raunchy sites that the content filter didn’t block.
McAfee replaces naughty content in the browser with a warning message that explains why the page was blocked. For HTTPS sites, or in unsupported browsers, it displays that warning as a popup, leaving the browser to show an error message. The kids won’t get past it by using a secure anonymizing proxy. Note, though, that Check Point ZoneAlarm Extreme Security 2017 goes even further, with the ability to filter content even over an HTTPS connection.
In addition to categories, McAfee offers to block sites with “inappropriate images or language” from appearing in child’s search results. A similar feature in Trend Micro Internet Security covered up many such images. However, I couldn’t find a single instance where McAfee did anything to block erotic images in search.
The time scheduler is as awkward as ever. It does let you create a weekly grid-style schedule of Internet access, in half-hour increments. Most parental control systems that use a scheduling grid let you block out rectangles on the schedule by dragging. For example, with one drag you could block from midnight to 6am every day of the week. McAfee’s system forces you to drag on just one day at a time. The grid is so tall that you can only select about seven hours at a time, and it doesn’t auto-scroll when you hit the edge. This feature could be so much easier to use! On the bright side, time scheduling doesn’t rely on the system clock, so the kids can’t fool it.
The simple parental report lists all domains blocked, along with their categories. It also logs all attempts to use the Internet when the schedule doesn’t allow it.
And there you have it. That’s the totality of parental control in this suite. It’s limited, awkward, and not entirely effective. If you actually need a suite that includes high-end parental control, look to ZoneAlarm, Kaspersky Internet Security, or Norton.
Broad-Spectrum Spam Filter With so many users getting spam filtered by the email provider, the value of local spam filtering is on the decline. But if you’re one of that diminishing group whose email provider doesn’t offer spam filtering, a local filter can be essential.
McAfee’s spam filter integrates with Outlook, Windows Mail, and Windows Live Mail. In these email clients, it adds a handy toolbar and automatically tosses spam messages in their own folder. You can still use it if you’re a fan of Eudora or The Bat!, but you’ll have to define a message rule to sift out the spam.

McAfee filters spam from POP3 and Exchange email accounts. It doesn’t handle IMAP accounts in your email client the way ZoneAlarm does. However, in an unusual twist, it has the ability to filter webmail accounts directly. Webmail filtering was a pretty amazing feature when first introduced years ago, but these days it’s hard to find a webmail provider that doesn’t implement its own spam filtering. You can view messages filtered out by this feature right in the application and, if necessary, rescue any valid mail that was misfiled.
There are quite a few options for configuring the spam filter. To start, there are five levels of protection, from Minimal, which allows more spam but doesn’t throw away valid mail, to Restricted, which blocks all messages unless the sender is on your Friends list. I’d advise leaving it set to the default Balanced level.
You can define custom spam filtering rules, but I can’t imagine why any user would take the time to do this. The Friends list identifies addresses or domains that should always reach the Inbox. You can manually edit this list, add friends from the email client toolbar, or add all your contacts to the Friends list. There’s also an option to automatically block messages written using character sets for languages you don’t speak.
Just to see how it works, I set up filtering for the Yahoo mail account I use in testing. When I filled in the address, McAfee automatically selected the correct mail server and port. However, after I entered my password and tried to add the account, McAfee reported that it was the wrong password.
In fact, the password was correct, but Yahoo rejected the login and sent me an email warning about an attempt to connect by a “less-secure app.” In order to let McAfee do its job, I had to dig into Yahoo settings and enable access by less-secure apps.
If you do need spam filtering at the local level, McAfee can handle it. Where many products limit protection to POP3 accounts, McAfee can filter Exchange accounts and even pull spam from your webmail.
Minor Performance Hit During my extensive testing, I didn’t get any feeing that McAfee was slowing me down. That’s not surprising; these days it’s uncommon for security suites to exhibit a noticeable performance impact. My hands-on test did reveal some actions that took longer with McAfee installed.
Most of us don’t reboot often—perhaps never except when an update requires it. My boot time test showed just a 3 percent increase in the time from the start of boot until the system was ready for use, so if you do have to reboot, you’ll hardly notice McAfee’s presence.
Given that the new Real Protect real-time antivirus scans files when they try to execute, not on just any file access, I expected minimal impact in my file move and copy test. This test repeatedly times a script that moves and copies a mammoth collection of various-sized files between drives. I was surprised to see a 44 percent increase in the time required for this test. On the bright side, another test that zips and unzips the same file collection didn’t have any measurable impact.
While there’s some variation in the results of this test, a couple products come out on top. Webroot and Trend Micro exhibited almost no slowdown in the performance test.
Stuck in the Middle With You For $20 per year more than McAfee’s antivirus, McAfee Internet Security gives you innovative password management along with parental control and antispam features that you may not need. Everything else—firewall, remote management, support for macOS, iOS, and Android, and more—is present in the antivirus. For another $10 you could upgrade to McAfee’s top-of-the-line suite. This suite remains stuck in the middle, with no compelling reason to buy it rather than one of McAfee’s other products.
Other than the cross-platform bonus, this suite is comparable to Bitdefender Internet Security and Kaspersky Internet Security. These two suites earn fantastic scores from the independent testing labs, their components are capable across the board, and they offer a comparable smorgasbord of bonus features. They’re our Editors’ Choice winners for entry-level security suite.
Sub-Ratings:
Note: These sub-ratings contribute to a product’s overall star rating, as do other factors, including ease of use in real-world testing, bonus features, and overall integration of features.
Firewall:

Antivirus:

Performance:

Privacy:

Parental Control:

Back to top
PCMag may earn affiliate commissions from the shopping links included on this page. These commissions do not affect how we test, rate or review products. To find out more, read our complete terms of use.
0 notes
Text
McAfee Internet Security (2017)
http://cyberparse.co.uk/2017/01/18/mcafee-internet-security-2017-2/ https://i0.wp.com/cyberparse.co.uk/wp-content/uploads/2016/04/security-binary-pd-898757.jpg?fit=3888%2C2592
The true purpose of a security suite isn’t to secure your computer. It’s to protect you, your privacy, and your data. With customer protection in mind, McAfee Internet Security installs on all of your devices. However, most of what it offers comes with McAfee’s antivirus, and the additional suite-specific components don’t add enough value, especially if you don’t need antispam or parental control.
At $79.99 per year, McAfee looks like it’s right in line with the competition, price-wise. Bitdefender and Kaspersky charge the same, within a nickel or so. But look again. With a Bitdefender or Kaspersky subscription you can install protection on three PCs. McAfee is unlimited, and lets you protect every Windows, macOS, iOS, or Android device in your household.
In fact, the Home screen in this product includes a button to extend protection to more devices. Clicking it reveals a button that scours your network to find unprotected devices and bring them into the fold. Clicking the icon that represents your current device summarizes its status.
The main window looks, for the most part, like that of McAfee’s antivirus. Both have undergone a major user interface update since I originally reviewed the product line. Instead of squareish green edged panels, the main window now relies on a menu of five items: Home, PC Security, Identity, Privacy, and Account. Clicking each item brings up a page that displays status and offers access to the corresponding feature. There’s no longer any need for the Navigation page, a separate user interface that listed and linked to every one of the suite’s features.
Not seeing this new interface? Don’t worry, you will. McAfee is rolling out the new look slowly, gradually, and automatically.
Shared Antivirus Features As is often the case, this suite’s antivirus protection is precisely the same as that of the corresponding standalone antivirus, McAfee AntiVirus Plus. That review goes into greater detail than the summary that follows.
McAfee’s scores in independent lab tests are generally mediocre. It received a B-level certification from Simon Edwards Labs, while other products rated A, AA, or even AAA. Of three tests by AV-Comparatives, it earned one passing grade and two grades a notch above passing. The three-part test by AV-Test Institute maxes out at 18 points; McAfee’s score improved since my original review, with 5.5 points for protection and a total of 17 points. Finally, in the banking Trojan test and all-types tests by MRG-Effitas, it simply failed.
My lab test score aggregation algorithm yields 7.9 of 10 possible points for McAfee. Kaspersky took a near-perfect 9.8, while Norton and Bitdefender Internet Security 2017 came out at 9.7 and 9.4 respectively.
This year’s McAfee products use an entirely new antivirus detection method called Real Protect. Real Protect is focused on behavior, so as to catch even zero-day malware. Like Webroot SecureAnywhere Internet Security Plus, when it sees an unknown file behaving suspiciously, it starts journaling that file’s actions and queries the cloud for advice. If cloud-based analysis red-flags the file, McAfee rolls back all of its actions.
In my own hands-on malware-blocking test, McAfee scored 9.2 of 10 possible points. However, among the samples it missed were two well-known ransomware threats. I watched one of them as it busily encrypted documents on the test system, without a peep from McAfee about its behavior. Webroot scored a perfect 10 against this same malware collection.
McAfee also protected against 85 percent of the 100 malware-hosting URLs I threw at it, mostly by diverting the browser from the dangerous URL. The average score among current products is 75 percent, so McAfee is above average here.
I score phishing protection by matching a product’s detection rate against that of Symantec Norton Security Premium and of the protection built into Chrome, Firefox, and Internet Explorer. Last year, McAfee came very close to matching Norton’s score. This year it lagged 44 percentage points behind Norton. Chrome and Internet Explorer beat out McAfee, as well. Don’t turn off your browser’s phishing protection!
Other Shared Features There’s a lot more to the nominally standalone antivirus; hence “Plus” in the name. For starters, it includes a firewall. In testing, the firewall correctly stealthed all ports and fended off Web-based attacks. Rather than bombard the user with queries about network permissions, it handles program control internally. When I tested its ability to withstand direct attack, I found that I could terminate and disable more than half of its essential Windows services.
The WebAdvisor component identifies dangerous downloads and steers the browser away from malicious or fraudulent sites. In addition, it marks up search results with icons identifying safe, iffy, and dangerous links. This edition adds protection for typosquatting, and it works. When I entered www.paypla.com it asked if perhaps I really wanted PayPal.
Using the My Home Network feature, you can set up a trust relationship between any and all of the PCs on your network that have McAfee installed. It doesn’t even have to be the same version of McAfee. Once you’ve taken that step, you can use one PC to remotely monitor others, and even remotely fix configuration problems.
Mac and mobile support is the same across all of the McAfee product line. Mac support is little more than antivirus, firewall, and WebAdvisor. There’s no antivirus under iOS, but you can do things like locate and wipe the device, back up contacts, and capture a photo of someone who found or stole your phone. On Android, you get a full-featured security utility with antivirus, app ratings, anti-theft, call and text filtering, and more. And once again, there’s no limit on how many devices you can add.
Other shared bonus features include the QuickClean tune-up tool, a vulnerability scanner, and a secure deletion file shredder. You can also access a number of security-related online resources directly from the program.

See How We Test Security Software
True Key Password Manager With your McAfee subscription you also get a license for the True Key password manager. Read my review for a full description of this password manager and its unusual collection of authentication options.
True Key’s biggest claim to fame is its comprehensive multi-factor authentication choices. It does support the expected strong master password, but you have many other options. You can have it send an email each time you log in; clicking a link in the email allows login to proceed. More conveniently, you can associate a mobile device with True Key, and authenticate by swiping a notification.
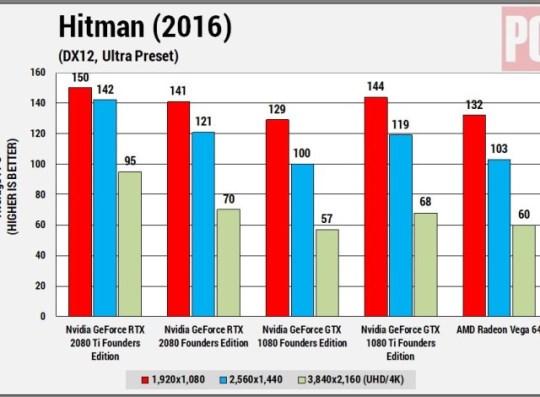
Even better, if you’re using a device with a camera, you can authenticate using facial recognition, and if a finger print reader is available, you can add that, too. If you worry that James Bond might spoof facial recognition with a photo of you, just enable enhanced facial recognition, which requires turning your head.
Most password managers warn that if you lose your master password, you’re hosed; you have to start over. That’s actually good; it means that the company can’t access your data even if subpoenaed. True Key retains that same zero-knowledge benefit, but doesn’t leave you in the lurch if you forget the password. As long as you’ve enabled Advanced authentication, which requires a trusted device plus two other factors, you can authenticate using all the other factors and then reset your master password.
True Key is a separate download, but getting it installed is easy. After you run the installer, it adds itself as an extension to Chrome, Firefox, and Internet Explorer. At this time, it can import passwords stored insecurely in the browsers. It can also import from LastPass 4.0 Premium and Dashlane 4.
As with most password managers, True Key captures credentials as you log in to secure sites and plays back saved credentials as needed. The first time, it actively walks you through the process. You can also click on tiles for Google, Facebook, PayPal, and so on, entering your credentials directly. Clicking the TrueKey toolbar icon doesn’t bring up a menu the way it does with many other products. Rather, it displays the main True Key window, from which you can launch any of your saved sites.
You can save personal details in the Wallet, but True Key doesn’t use these to fill web forms. The main reason to do this is that the Wallet items sync across all your devices. The same is true of secure notes.
Here’s a rare feature. If your PC has a forward-facing camera, you can configure it to unlock your Windows account using True Key’s facial recognition. True Key doesn’t have advanced features like secure sharing, automatic password updates, or password inheritance, but it’s far ahead of the pack when it comes to multi-factor authentication.
Tepid Parental Controls One bonus you get by upgrading from McAfee’s antivirus to this suite is a parental control system, but it’s really limited. For each child’s Windows account, you can choose content categories for blocking, set a schedule for Internet use, and view a report of activity for each child or all children. That’s the extent of it.
The reviewer’s guide for this product notes that parental controls may not work properly in a virtual machine. That’s unusual, but I made a point of testing on a physical system.
To get started, you set a password, so the kids can’t just turn off monitoring. The configuration window lists all Windows user accounts and invites you to configure parental control for each one that belongs to a child. As with previous versions, setting up parental control for a child’s account that has Administrator privileges triggers a big warning. And yet, many parents do give older children Administrator accounts, so as to avoid constantly having to jump and supply an admin password any time the child wants to install a new game. Most other parental control systems don’t have this limitation.

To configure the content filter, you first choose one of five age ranges. Doing so pre-configures which of the 20 content categories should be blocked. Rather than the usual list with checkboxes, McAfee displays a list of blocked categories and another list of allowed categories, with arrow buttons to move items back and forth between the lists.
I couldn’t disable the content filter with the three-word network command that neutered parental control in Total Defense Unlimited Internet Security and Alvosecure Parental Control . However, I found quite a few truly raunchy sites that the content filter didn’t block.
McAfee replaces naughty content in the browser with a warning message that explains why the page was blocked. For HTTPS sites, or in unsupported browsers, it displays that warning as a popup, leaving the browser to show an error message. The kids won’t get past it by using a secure anonymizing proxy. Note, though, that Check Point ZoneAlarm Extreme Security 2017 goes even further, with the ability to filter content even over an HTTPS connection.
In addition to categories, McAfee offers to block sites with “inappropriate images or language” from appearing in child’s search results. A similar feature in Trend Micro Internet Security covered up many such images. However, I couldn’t find a single instance where McAfee did anything to block erotic images in search.
The time scheduler is as awkward as ever. It does let you create a weekly grid-style schedule of Internet access, in half-hour increments. Most parental control systems that use a scheduling grid let you block out rectangles on the schedule by dragging. For example, with one drag you could block from midnight to 6am every day of the week. McAfee’s system forces you to drag on just one day at a time. The grid is so tall that you can only select about seven hours at a time, and it doesn’t auto-scroll when you hit the edge. This feature could be so much easier to use! On the bright side, time scheduling doesn’t rely on the system clock, so the kids can’t fool it.
The simple parental report lists all domains blocked, along with their categories. It also logs all attempts to use the Internet when the schedule doesn’t allow it.
And there you have it. That’s the totality of parental control in this suite. It’s limited, awkward, and not entirely effective. If you actually need a suite that includes high-end parental control, look to ZoneAlarm, Kaspersky Internet Security, or Norton.
Broad-Spectrum Spam Filter With so many users getting spam filtered by the email provider, the value of local spam filtering is on the decline. But if you’re one of that diminishing group whose email provider doesn’t offer spam filtering, a local filter can be essential.
McAfee’s spam filter integrates with Outlook, Windows Mail, and Windows Live Mail. In these email clients, it adds a handy toolbar and automatically tosses spam messages in their own folder. You can still use it if you’re a fan of Eudora or The Bat!, but you’ll have to define a message rule to sift out the spam.

McAfee filters spam from POP3 and Exchange email accounts. It doesn’t handle IMAP accounts in your email client the way ZoneAlarm does. However, in an unusual twist, it has the ability to filter webmail accounts directly. Webmail filtering was a pretty amazing feature when first introduced years ago, but these days it’s hard to find a webmail provider that doesn’t implement its own spam filtering. You can view messages filtered out by this feature right in the application and, if necessary, rescue any valid mail that was misfiled.
There are quite a few options for configuring the spam filter. To start, there are five levels of protection, from Minimal, which allows more spam but doesn’t throw away valid mail, to Restricted, which blocks all messages unless the sender is on your Friends list. I’d advise leaving it set to the default Balanced level.
You can define custom spam filtering rules, but I can’t imagine why any user would take the time to do this. The Friends list identifies addresses or domains that should always reach the Inbox. You can manually edit this list, add friends from the email client toolbar, or add all your contacts to the Friends list. There’s also an option to automatically block messages written using character sets for languages you don’t speak.
Just to see how it works, I set up filtering for the Yahoo mail account I use in testing. When I filled in the address, McAfee automatically selected the correct mail server and port. However, after I entered my password and tried to add the account, McAfee reported that it was the wrong password.
In fact, the password was correct, but Yahoo rejected the login and sent me an email warning about an attempt to connect by a “less-secure app.” In order to let McAfee do its job, I had to dig into Yahoo settings and enable access by less-secure apps.
If you do need spam filtering at the local level, McAfee can handle it. Where many products limit protection to POP3 accounts, McAfee can filter Exchange accounts and even pull spam from your webmail.
Minor Performance Hit During my extensive testing, I didn’t get any feeing that McAfee was slowing me down. That’s not surprising; these days it’s uncommon for security suites to exhibit a noticeable performance impact. My hands-on test did reveal some actions that took longer with McAfee installed.
Most of us don’t reboot often—perhaps never except when an update requires it. My boot time test showed just a 3 percent increase in the time from the start of boot until the system was ready for use, so if you do have to reboot, you’ll hardly notice McAfee’s presence.
Given that the new Real Protect real-time antivirus scans files when they try to execute, not on just any file access, I expected minimal impact in my file move and copy test. This test repeatedly times a script that moves and copies a mammoth collection of various-sized files between drives. I was surprised to see a 44 percent increase in the time required for this test. On the bright side, another test that zips and unzips the same file collection didn’t have any measurable impact.
While there’s some variation in the results of this test, a couple products come out on top. Webroot and Trend Micro exhibited almost no slowdown in the performance test.
Stuck in the Middle With You For $20 per year more than McAfee’s antivirus, McAfee Internet Security gives you innovative password management along with parental control and antispam features that you may not need. Everything else—firewall, remote management, support for macOS, iOS, and Android, and more—is present in the antivirus. For another $10 you could upgrade to McAfee’s top-of-the-line suite. This suite remains stuck in the middle, with no compelling reason to buy it rather than one of McAfee’s other products.
Other than the cross-platform bonus, this suite is comparable to Bitdefender Internet Security and Kaspersky Internet Security. These two suites earn fantastic scores from the independent testing labs, their components are capable across the board, and they offer a comparable smorgasbord of bonus features. They’re our Editors’ Choice winners for entry-level security suite.
Sub-Ratings:
Note: These sub-ratings contribute to a product’s overall star rating, as do other factors, including ease of use in real-world testing, bonus features, and overall integration of features.
Firewall:

Antivirus:

Performance:

Privacy:

Parental Control:

Back to top
PCMag may earn affiliate commissions from the shopping links included on this page. These commissions do not affect how we test, rate or review products. To find out more, read our complete terms of use.
Source CRN
0 notes