#Microsoft Malware Protection
Explore tagged Tumblr posts
Text
Safeguard Your PC Against Common Malware Entry Points
Safeguard Your PC Against Common Malware Entry Points
Safeguard Your PC Against Common Malware Entry Points In our day-to-day activities on the internet, cyber threats hide in unexpected places, ready to infiltrate your devices and wreak havoc. It’s crucial to know how malware can get into your computer to protect yourself better. Here, we look at some of the most prevalent ways through which malware seizes control, so you can be more careful and…

View On WordPress
#AntiMalware#malware#Microsoft Malware Protection#Windows#Windows 10#Windows 11#Windows Defender#Windows Defender Antivirus#Windows Security#Windows Server
1 note
·
View note
Text

0 notes
Text
Microsoft's CEO Satya Nadella has hailed the company's new Recall feature, which stores a history of your computer desktop and makes it available to AI for analysis, as “photographic memory” for your PC. Within the cybersecurity community, meanwhile, the notion of a tool that silently takes a screenshot of your desktop every five seconds has been hailed as a hacker's dream come true and the worst product idea in recent memory.
Now, security researchers have pointed out that even the one remaining security safeguard meant to protect that feature from exploitation can be trivially defeated.
Since Recall was first announced last month, the cybersecurity world has pointed out that if a hacker can install malicious software to gain a foothold on a target machine with the feature enabled, they can quickly gain access to the user's entire history stored by the function. The only barrier, it seemed, to that high-resolution view of a victim's entire life at the keyboard was that accessing Recall's data required administrator privileges on a user's machine. That meant malware without that higher-level privilege would trigger a permission pop-up, allowing users to prevent access, and that malware would also likely be blocked by default from accessing the data on most corporate machines.
Then on Wednesday, James Forshaw, a researcher with Google's Project Zero vulnerability research team, published an update to a blog post pointing out that he had found methods for accessing Recall data without administrator privileges—essentially stripping away even that last fig leaf of protection. “No admin required ;-)” the post concluded.
“Damn,” Forshaw added on Mastodon. “I really thought the Recall database security would at least be, you know, secure.”
Forshaw's blog post described two different techniques to bypass the administrator privilege requirement, both of which exploit ways of defeating a basic security function in Windows known as access control lists that determine which elements on a computer require which privileges to read and alter. One of Forshaw's methods exploits an exception to those control lists, temporarily impersonating a program on Windows machines called AIXHost.exe that can access even restricted databases. Another is even simpler: Forshaw points out that because the Recall data stored on a machine is considered to belong to the user, a hacker with the same privileges as the user could simply rewrite the access control lists on a target machine to grant themselves access to the full database.
That second, simpler bypass technique “is just mindblowing, to be honest,” says Alex Hagenah, a cybersecurity strategist and ethical hacker. Hagenah recently built a proof-of-concept hacker tool called TotalRecall designed to show that someone who gained access to a victim's machine with Recall could immediately siphon out all the user's history recorded by the feature. Hagenah's tool, however, still required that hackers find another way to gain administrator privileges through a so-called “privilege escalation” technique before his tool would work.
With Forshaw's technique, “you don’t need any privilege escalation, no pop-up, nothing,” says Hagenah. “This would make sense to implement in the tool for a bad guy.”
In fact, just an hour after speaking to WIRED about Forshaw's finding, Hagenah added the simpler of Forshaw's two techniques to his TotalRecall tool, then confirmed that the trick worked by accessing all the Recall history data stored on another user's machine for which he didn't have administrator access. “So simple and genius,” he wrote in a text to WIRED after testing the technique.
That confirmation removes one of the last arguments Recall's defenders have had against criticisms that the feature acts as, essentially, a piece of pre-installed spyware on a user's machine, ready to be exploited by any hacker who can gain a foothold on the device. “It makes your security very fragile, in the sense that anyone who penetrates your computer for even a second can get your whole history,” says Dave Aitel, the founder of the cybersecurity firm Immunity and a former NSA hacker. “Which is not something people want.”
For now, security researchers have been testing Recall in preview versions of the tool ahead of its expected launch later this month. Microsoft said it plans to integrate Recall on compatible Copilot+ PCs with the feature turned on by default. WIRED reached out to the company for comment on Forshaw's findings about Recall's security issues, but the company has yet to respond.
The revelation that hackers can exploit Recall without even using a separate privilege escalation technique only contributes further to the sense that the feature was rushed to market without a proper review from the company's cybersecurity team—despite the company's CEO Nadella proclaiming just last month that Microsoft would make security its first priority in every decision going forward. “You cannot convince me that Microsoft's security teams looked at this and said ‘that looks secure,’” says Jake Williams, a former NSA hacker and now the VP of R&D at the cybersecurity consultancy Hunter Strategy, where he says he's been asked by some of the firm's clients to test Recall's security before they add Microsoft devices that use it to their networks.
“As it stands now, it’s a security dumpster fire,” Williams says. “This is one of the scariest things I’ve ever seen from an enterprise security standpoint.”
143 notes
·
View notes
Text
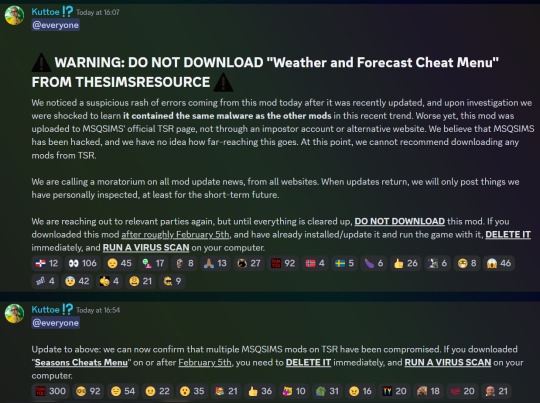
be careful y'all the same person who pretended to be pimpmysims4 is back, make sure you dont have the mods in the announcement installed and check %AppData%\Microsoft\Internet Explorer\UserData in your computer for an exe. if there's one in there you need to quarantine it and run virus scans etc (this doesnt affect macs)
edited to add: Malware in certain Mods – What we know – Crinrict's Sims 4 Help Blog
second edit: twistedmexi is a mod king and came up with a ModGuard ModGuard: Mod Malware Protection | Patreon
32 notes
·
View notes
Text
When loading a DLL, Microsoft Windows looks for the DLL in a certain sequence of directories. The first match for the file name wins. In most cases, Windows will first look for a DLL in the same location as the executable. This behavior is what allows the Apple Safari "carpet bombing" vulnerability to work. If an attacker can place code in a directory that gets searched before Windows finds the "real" DLL, the attacker's code will be executed.
DLLs are Dynamic Link Libraries, small snippets of compiled code that EXEs call upon at runtime. And they can contain malware.
Carpet Bombing is a kind of attack where a legitimate DLL is replaced with a fake one containing viruses or ransomware.
Both Windows and Apple devices are vulnerable.
All browsers are vulnerable to this.
To protect yourself, make sure that any installer you download & run is the only file in its folder. Don't know where your browser is downloading files? Use CTRL-J (on Firefox, Chrome) to find that folder. If you've never done CTRL-J before you might be shocked at how many things you've accumulated as downloads. Usually it's safe to delete stuff in that folder after you've run the installer.
If you're on Windows, you may not even see the .DLL part of the file names on your computer; the factory default is to hide them. For complete filenames, turn on File Name Extensions.
From Explorer:


Dunno how Apple computers work; somebody familiar with MacOS feel free to add onto this.
12 notes
·
View notes
Text
Sims 4 Malicious Script Mod Advisory
We all know by now that some modders have been hacked and their script mods replaced with malicious malware. Hopefully none of my followers have been hit and if you have, I hope you've taken the necessary steps to safeguard your sensitive data. There has been a list of modders who's scripts are no longer safe to download circulating.
There are a number of ways to find out if you've been hit or not.
To quickly check if you have been compromised, press Windows + R on your keyboard to open the Run window. Enter “%AppData%/Microsoft/Internet Explorer/UserData” without the quotes in the prompt and hit OK. This will open up the folder the this particular malware uses. If there is a file in this folder called “Updater.exe”, you have unfortunately fallen victim to the malware. Some sites will tell you "we don't know what it does". In reality, this updater is designed to download, install and run a data collection app. Passwords, site tracking, bank routing -- all the worst case scenarios you can dream up regarding your personal information.
So, delete the folder if you find it and grab this:
Release Version 1.1 · overwolf/sims4-social-events-cleaner · GitHub
If you're still downloading script mods, download this to help protect yourself:
ModGuard: Mod Malware Protection v1.4 | Patreon
Be aware that your antivirus and most malware detection software will not recognize a script mod as malware or virus.
11 notes
·
View notes
Text
Tom's Guide: New Android security flaw lets hackers seize control of apps — uninstall these immediately
New Android security flaw lets hackers seize control of apps — uninstall these immediately
Billions of Android devices open to 'Dirty Stream' malware
Another day, another new Android malware strain. Microsoft is sounding the alarm about a recently discovered critical security vulnerability on Android named "Dirty Stream" that can let malicious apps easily hijack legitimate apps. Worse still, this flaw impacts multiple apps with hundreds of millions of installs. If you have one of the best Android phones, here's what you need to know to protect your data.
The vulnerability relates to the ContentProvider system prevalent across many popular Android apps, which manages access to structured data sets meant to be shared between different applications. It's basically what lets your Android apps talk to one another and share files. To protect users and ward off unauthorized access, the system includes safeguards such as strict isolation of data, unique permissions attached to specific URIs (Uniform Resource Identifiers), and path validation security.
What makes the Dirty Stream vulnerability so devious is how it manipulates this system. Microsoft has found that hackers can create "custom intents," messaging objects that facilitate communication between components across Android apps, to bypass these security measures. By exploiting this loophole, malicious apps can send a file with a manipulated filename or path to another app using a custom intent, sneaking in harmful code disguised as legitimate files.
4 notes
·
View notes
Text
If an antivirus you use flags Glaze as a threat, ignore/whitelist it
Today I had Windows Defender flagging the new version of Glaze as a Trojan. I looked into it on Twitter and it turns out that AI bros took Glaze and uploaded it to virus databases to have it falsely flagged as malware, which has resulted in some antivirus programs falsely flagging it at such. I've scanned Glaze with Malwarebytes and it returned no warnings.

If you downloaded Glaze and your antivirus program flagged it as Trojan, whitelist it. Glaze developers are currently in the process of getting Glaze signed.
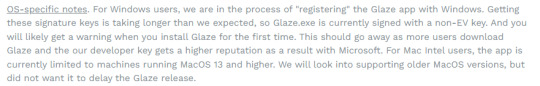
[ALT text, image is a screencap of a paragraph on Glaze's website] "OS-specific notes. For Windows users, we are in the process of "registering" the Glaze app with Windows. Getting these signature keys is taking longer than we expected, so Glaze.exe is currently signed with a non-EV key. And you will likely get a warning when you install Glaze for the first time. This should go away as more users download Glaze and the our developer key gets a higher reputation as a result with Microsoft. For Mac Intel users, the app is currently limited to machines running MacOS 13 and higher. We will look into supporting older MacOS versions, but did not want it to delay the Glaze release."
Glaze can be downloaded here. The new version uses a much more subtle cloak and now works on flat shaded/cel shaded art styles and photography, and even has a limited img2img protection.
8 notes
·
View notes
Photo

(via Microsoft finds macOS bug that lets hackers bypass SIP root restrictions)
Apple has recently addressed a vulnerability that lets attackers with root privileges bypass System Integrity Protection (SIP) to install "undeletable" malware and access the victim's private data by circumventing Transparency, Consent, and Control (TCC) security checks.
Discovered and reported to Apple by a team of Microsoft security researchers, the flaw (dubbed Migraine) is now tracked as CVE-2023-32369.
Apple has patched the vulnerability in security updates for macOS Ventura 13.4, macOS Monterey 12.6.6, and macOS Big Sur 11.7.7, released two weeks ago, on May 18.
jeebus - evil stuff
7 notes
·
View notes
Link
2 notes
·
View notes
Text
"Searching Google for downloads of popular software has always come with risks, but over the past few months, it has been downright dangerous, according to researchers and a pseudorandom collection of queries.
“Threat researchers are used to seeing a moderate flow of malvertising via Google Ads,” volunteers at Spamhaus wrote on Thursday. “However, over the past few days, researchers have witnessed a massive spike affecting numerous famous brands, with multiple malware being utilized. This is not ‘the norm.’”
One of many new threats: MalVirt
The surge is coming from numerous malware families, including AuroraStealer, IcedID, Meta Stealer, RedLine Stealer, Vidar, Formbook, and XLoader. In the past, these families typically relied on phishing and malicious spam that attached Microsoft Word documents with booby-trapped macros. Over the past month, Google Ads has become the go-to place for criminals to spread their malicious wares that are disguised as legitimate downloads by impersonating brands such as Adobe Reader, Gimp, Microsoft Teams, OBS, Slack, Tor, and Thunderbird.
On the same day that Spamhaus published its report, researchers from security firm Sentinel One documented an advanced Google malvertising campaign pushing multiple malicious loaders implemented in .NET. Sentinel One has dubbed these loaders MalVirt. At the moment, the MalVirt loaders are being used to distribute malware most commonly known as XLoader, available for both Windows and macOS. XLoader is a successor to malware also known as Formbook. Threat actors use XLoader to steal contacts' data and other sensitive information from infected devices.
The MalVirt loaders use obfuscated virtualization to evade end-point protection and analysis. To disguise real C2 traffic and evade network detections, MalVirt beacons to decoy command and control servers hosted at providers including Azure, Tucows, Choopa, and Namecheap. Sentinel One researcher Tom Hegel wrote:
As a response to Microsoft blocking Office macros by default in documents from the Internet, threat actors have turned to alternative malware distribution methods—most recently, malvertising. The MalVirt loaders we observed demonstrate just how much effort threat actors are investing in evading detection and thwarting analysis.
Malware of the Formbook family is a highly capable infostealer that is deployed through the application of a significant amount of anti-analysis and anti-detection techniques by the MalVirt loaders. Traditionally distributed as an attachment to phishing emails, we assess that threat actors distributing this malware are likely joining the malvertising trend.
Given the massive size of the audience threat actors can reach through malvertising, we expect malware to continue being distributed using this method..."
3 notes
·
View notes
Text
I typed out a whole-ass response to this and then reset the page and it was GONE. GODDAMNIT.
I work at Geek Squad (the opinions stated on my blog are not representative of the company, etc., etc.).
Bitlocker is active on every Windows machine, as long as a Microsoft account has been linked to it. You would know if it's inactive, because you have to turn it off yourself. Turning it off has purposefully been made not-easy to do because it's an important security measure.
Never heard of Bitlocker? Most people haven't. Not until it's a problem, at least.
Bitlocker is designed to protect your system against unauthorized changes. Certain types of malware will trigger it (or not, if they're really really good). A failing storage device (HDD or SSD) will also sometimes trigger it.
Once Bitlocker has been triggered, it can be unlocked using the appropriate Bitlocker key. This can be found under the device's administrator account.
If it's a personal device and your account is the only one linked to it, it's under your account.
If it's an enterprise or school device, the key is probably linked to your IT admin's account. The key needs to be entered manually and by someone who is physically at the machine. For companies who are geographically widespread, this can present a lot of issues.
Now what if no one has the Bitlocker key to the machine?
You have one option.
You can reset the entire machine.
Any data saved locally (to the machine itself) will be gone. You will not be getting it back, unless you (or your company/school) are willing to pay a shit load of money for it. Any data saved to a cloud service, such as OneDrive, Google Drive, or iCloud, can be accessed via logging into said cloud service on another device. As long as said cloud service is up and running, you should be able to access that data fine.
MacOS has something very similar called FileVault. It does the exact same thing, but with one important difference. It can be unlocked with the admin account's password. The password itself is the key. If FileVault is triggered and no one knows the admin account's password, you have to reset the password using another device. You cannot reset the admin password from a device with where FileVault has been triggered.
If you know you don't have FileVault active on your Apple computer (note I said active, as in FileVault is in a state where it can be triggered but it currently is not), please turn it on. Your data is encrypted whether or not FileVault is active. If it isn't active, your decryption key is based on your hardware UUID. This is not something you (probably) know. This is not something you were given and told to keep safe.
Your UUID can be accessed by clicking on the Apple icon, then "About this Mac", then "System Report". It should be under "Hardware Overview" (unless they changed it since I last checked).
If you are asked to decrypt your storage drive and you do not have your UUID put aside, you are going to have to reset your device if you want to use it.
I do not know if you can access your hardware UUID by physically opening your Apple computer. I do not recommend trying. Apple devices (all of them) are very difficult to take apart without damaging the device if you do not have the proper equipment. Without the proper equipment, they are basically impossible to put back together with them still functioning afterwards. There's also the risk of broken glass and various issues with the Li-ion battery (all Apple devices have at least one), none of which are easy to deal with.
idk if people on tumblr know about this but a cybersecurity software called crowdstrike just did what is probably the single biggest fuck up in any sector in the past 10 years. it's monumentally bad. literally the most horror-inducing nightmare scenario for a tech company.
some info, crowdstrike is essentially an antivirus software for enterprises. which means normal laypeople cant really get it, they're for businesses and organisations and important stuff.
so, on a friday evening (it of course wasnt friday everywhere but it was friday evening in oceania which is where it first started causing damage due to europe and na being asleep), crowdstrike pushed out an update to their windows users that caused a bug.
before i get into what the bug is, know that friday evening is the worst possible time to do this because people are going home. the weekend is starting. offices dont have people in them. this is just one of many perfectly placed failures in the rube goldburg machine of crowdstrike. there's a reason friday is called 'dont push to live friday' or more to the point 'dont fuck it up friday'
so, at 3pm at friday, an update comes rolling into crowdstrike users which is automatically implemented. this update immediately causes the computer to blue screen of death. very very bad. but it's not simply a 'you need to restart' crash, because the computer then gets stuck into a boot loop.
this is the worst possible thing because, in a boot loop state, a computer is never really able to get to a point where it can do anything. like download a fix. so there is nothing crowdstrike can do to remedy this death update anymore. it is now left to the end users.
it was pretty quickly identified what the problem was. you had to boot it in safe mode, and a very small file needed to be deleted. or you could just rename crowdstrike to something else so windows never attempts to use it.
it's a fairly easy fix in the grand scheme of things, but the issue is that it is effecting enterprises. which can have a looooot of computers. in many different locations. so an IT person would need to manually fix hundreds of computers, sometimes in whole other cities and perhaps even other countries if theyre big enough.
another fuck up crowdstrike did was they did not stagger the update, so they could catch any mistakes before they wrecked havoc. (and also how how HOW do you not catch this before deploying it. this isn't a code oopsie this is a complete failure of quality ensurance that probably permeates the whole company to not realise their update was an instant kill). they rolled it out to everyone of their clients in the world at the same time.
and this seems pretty hilarious on the surface. i was havin a good chuckle as eftpos went down in the store i was working at, chaos was definitely ensuring lmao. im in aus, and banking was literally down nationwide.
but then you start hearing about the entire country's planes being grounded because the airport's computers are bricked. and hospitals having no computers anymore. emergency call centres crashing. and you realised that, wow. crowdstrike just killed people probably. this is literally the worst thing possible for a company like this to do.
crowdstrike was kinda on the come up too, they were starting to become a big name in the tech world as a new face. but that has definitely vanished now. to fuck up at this many places, is almost extremely impressive. its hard to even think of a comparable fuckup.
a friday evening simultaneous rollout boot loop is a phrase that haunts IT people in their darkest hours. it's the monster that drags people down into the swamp. it's the big bag in the horror movie. it's the end of the road. and for crowdstrike, that reaper of souls just knocked on their doorstep.
114K notes
·
View notes
Text
Microsoft raced to put generative AI at the heart of its systems. Ask a question about an upcoming meeting and the company’s Copilot AI system can pull answers from your emails, Teams chats, and files—a potential productivity boon. But these exact processes can also be abused by hackers.
Today at the Black Hat security conference in Las Vegas, researcher Michael Bargury is demonstrating five proof-of-concept ways that Copilot, which runs on its Microsoft 365 apps, such as Word, can be manipulated by malicious attackers, including using it to provide false references to files, exfiltrate some private data, and dodge Microsoft’s security protections.
One of the most alarming displays, arguably, is Bargury’s ability to turn the AI into an automatic spear-phishing machine. Dubbed LOLCopilot, the red-teaming code Bargury created can—crucially, once a hacker has access to someone’s work email—use Copilot to see who you email regularly, draft a message mimicking your writing style (including emoji use), and send a personalized blast that can include a malicious link or attached malware.
“I can do this with everyone you have ever spoken to, and I can send hundreds of emails on your behalf,” says Bargury, the cofounder and CTO of security company Zenity, who published his findings alongside videos showing how Copilot could be abused. “A hacker would spend days crafting the right email to get you to click on it, but they can generate hundreds of these emails in a few minutes.”
That demonstration, as with other attacks created by Bargury, broadly works by using the large language model (LLM) as designed: typing written questions to access data the AI can retrieve. However, it can produce malicious results by including additional data or instructions to perform certain actions. The research highlights some of the challenges of connecting AI systems to corporate data and what can happen when “untrusted” outside data is thrown into the mix—particularly when the AI answers with what could look like legitimate results.
Among the other attacks created by Bargury is a demonstration of how a hacker—who, again, must already have hijacked an email account—can gain access to sensitive information, such as people’s salaries, without triggering Microsoft’s protections for sensitive files. When asking for the data, Bargury’s prompt demands the system does not provide references to the files data is taken from. “A bit of bullying does help,” Bargury says.
In other instances, he shows how an attacker—who doesn’t have access to email accounts but poisons the AI’s database by sending it a malicious email—can manipulate answers about banking information to provide their own bank details. “Every time you give AI access to data, that is a way for an attacker to get in,” Bargury says.
Another demo shows how an external hacker could get some limited information about whether an upcoming company earnings call will be good or bad, while the final instance, Bargury says, turns Copilot into a “malicious insider” by providing users with links to phishing websites.
Phillip Misner, head of AI incident detection and response at Microsoft, says the company appreciates Bargury identifying the vulnerability and says it has been working with him to assess the findings. “The risks of post-compromise abuse of AI are similar to other post-compromise techniques,” Misner says. “Security prevention and monitoring across environments and identities help mitigate or stop such behaviors.”
As generative AI systems, such as OpenAI’s ChatGPT, Microsoft’s Copilot, and Google’s Gemini, have developed in the past two years, they’ve moved onto a trajectory where they may eventually be completing tasks for people, like booking meetings or online shopping. However, security researchers have consistently highlighted that allowing external data into AI systems, such as through emails or accessing content from websites, creates security risks through indirect prompt injection and poisoning attacks.
“I think it’s not that well understood how much more effective an attacker can actually become now,” says Johann Rehberger, a security researcher and red team director, who has extensively demonstrated security weaknesses in AI systems. “What we have to be worried [about] now is actually what is the LLM producing and sending out to the user.”
Bargury says Microsoft has put a lot of effort into protecting its Copilot system from prompt injection attacks, but he says he found ways to exploit it by unraveling how the system is built. This included extracting the internal system prompt, he says, and working out how it can access enterprise resources and the techniques it uses to do so. “You talk to Copilot and it’s a limited conversation, because Microsoft has put a lot of controls,” he says. “But once you use a few magic words, it opens up and you can do whatever you want.”
Rehberger broadly warns that some data issues are linked to the long-standing problem of companies allowing too many employees access to files and not properly setting access permissions across their organizations. “Now imagine you put Copilot on top of that problem,” Rehberger says. He says he has used AI systems to search for common passwords, such as Password123, and it has returned results from within companies.
Both Rehberger and Bargury say there needs to be more focus on monitoring what an AI produces and sends out to a user. “The risk is about how AI interacts with your environment, how it interacts with your data, how it performs operations on your behalf,” Bargury says. “You need to figure out what the AI agent does on a user's behalf. And does that make sense with what the user actually asked for.”
25 notes
·
View notes
Text

As Microsoft prepares to end free support for Windows 10 on October 14, 2025, the countdown to a new era for the operating system begins. For millions of users still relying on this popular OS, the end of security updates and patches signals potential vulnerabilities. To protect your PC, data, and online identity, it’s critical to take proactive steps. In this article, we’ll explore what the end of Windows 10 support means and provide five effective ways to ensure your PC remains secure. Why is Microsoft Ending Support for Windows 10? Microsoft’s decision to stop updates for Windows 10 aligns with its strategy of encouraging users to upgrade to Windows 11 or future OS versions. This is part of their product lifecycle policy, which ensures older systems are phased out to make way for new technology. While this approach fosters innovation, it leaves countless users at risk if they do not transition promptly. What’s at Stake?Without security updates: - Vulnerabilities increase: Cybercriminals can exploit unpatched security flaws. - Compatibility issues arise: Over time, apps and services may no longer work seamlessly with Windows 10. - Decreased support from third-party tools: Antivirus and other software providers may also stop supporting the platform. Even if upgrading isn’t feasible for you right now, there are actionable ways to protect your Windows 10 system. Let’s delve into them. 1. Invest in a Comprehensive Antivirus and Anti-Malware Solution Once Microsoft halts updates, your system will become a bigger target for hackers. Having robust antivirus software is your first line of defense. Modern security tools not only protect against traditional viruses but also block phishing attempts, ransomware, and spyware. Recommended Actions: - Choose reputable software: Solutions like Norton 360, Bitdefender, or McAfee are consistently ranked highly for protection. - Enable real-time protection: Ensure the software runs in the background to scan files and monitor downloads automatically. - Regular scans: Schedule weekly scans to identify and remove threats. 2. Keep Your Drivers and Software Updated Outdated software and drivers can create entry points for attackers. While Windows Update will no longer provide system updates, many hardware manufacturers and software developers will continue supporting their products. Steps to Take: - Manually update drivers: Visit the websites of hardware manufacturers (e.g., NVIDIA, Intel, or Dell) to download the latest drivers. - Update critical apps: Ensure your browsers, productivity tools, and communication platforms are up-to-date. - Use patch management tools: Tools like Patch My PC can simplify the process of keeping third-party apps updated. 3. Enable Firewalls and Secure Your Network A firewall acts as a barrier between your PC and malicious actors on the internet. While Windows 10 includes a built-in firewall, it’s essential to ensure it’s active and working efficiently. What You Can Do: - Check Windows Firewall settings: Navigate to Control Panel > System and Security > Windows Defender Firewall to verify it’s enabled. - Use a router firewall: Most modern routers include built-in firewalls. Access your router’s settings to ensure this feature is active. - Strengthen your Wi-Fi: Use strong, unique passwords for your network and enable WPA3 encryption where possible. 4. Create Regular Backups of Your Data In the worst-case scenario of a malware attack or system failure, having a backup ensures you don’t lose valuable data. With cloud services and external drives, backing up your files is easier than ever. Backup Options: - Cloud storage: Use platforms like Google Drive, OneDrive, or Dropbox for automatic cloud backups. - External storage: Invest in an external hard drive or SSD and schedule regular backups using Windows Backup or third-party tools. - System image creation: Create a complete snapshot of your system using Windows’ built-in tool or third-party software like Acronis True Image. 5. Consider an Upgrade Path While maintaining Windows 10 security is possible, it’s worth exploring your upgrade options. Microsoft is incentivizing users to transition to Windows 11, which offers enhanced features and a more modern interface. Evaluate Your Hardware Compatibility: - Use Microsoft’s PC Health Check tool to determine if your system meets Windows 11 requirements. - If your PC doesn’t qualify, weigh the cost of upgrading hardware against buying a new device. Explore Alternatives: - Linux: If Windows 11 isn’t an option, Linux-based operating systems like Ubuntu or Fedora are free, secure, and highly customizable. - Chromebooks: For light users, transitioning to Chrome OS offers simplicity and a secure environment. How to Prepare for the Transition Set a Timeline: If you plan to upgrade, do it before October 2025 to avoid gaps in security. Educate Yourself: Familiarize yourself with Windows 11 or alternative systems to ease the transition. Budget Accordingly: Assess costs for potential hardware upgrades or new purchases. The Future Beyond Windows 10 The end of Windows 10 support marks a significant chapter in the evolution of personal computing. Whether you choose to stick with your current OS or embrace newer options, the key is staying proactive about security. By following the steps outlined above, you can continue to enjoy a safe and productive computing experience. Don’t let the clock run out on your digital security—act today and ensure your PC remains safeguarded in an ever-evolving cyber landscape. Read the full article
0 notes