#Data Security Assurance
Text
Preserving Peace of Mind: Office 365 Backup Solutions and Data Security Assurance

In today's digital landscape, where businesses rely heavily on cloud-based solutions like Office 365 for their day-to-day operations, ensuring the security and integrity of data has become paramount. While Office 365 offers robust built-in security features, many organizations overlook the importance of implementing backup solutions to safeguard against data loss and ensure business continuity. Ensuring Office 365 data security and preserving peace of mind requires a comprehensive approach to data security, including reliable backup solutions tailored to the unique needs of Office 365 users.
Office 365 Backup: Why It's Essential
Office 365 provides users with a suite of productivity tools, including email, file storage, collaboration platforms, and more. While Microsoft guarantees a certain level of data protection within their platform, it's crucial to understand that they are not responsible for all data loss scenarios. Common causes of data loss in Office 365 include accidental deletion, malicious attacks, synchronization errors, and retention policy gaps.
To mitigate these risks, organizations need backup solutions specifically designed for Office 365. These solutions offer several key benefits:
Data Protection: Backup solutions ensure that critical data stored in Office 365, including emails, documents, calendars, and contacts, is regularly backed up and easily recoverable in the event of data loss.
Business Continuity: In the event of a security breach, ransomware attack, or accidental deletion, having a reliable backup ensures minimal disruption to business operations and facilitates quick recovery.
Compliance and Legal Requirements: Many industries are subject to regulatory requirements regarding data retention and protection. Office 365 backup solutions help organizations meet these compliance standards by providing secure and auditable data storage.
Granular Recovery: Backup solutions offer granular recovery options, allowing users to restore individual emails, files, or other Office 365 data components without the need to restore entire backups, thus saving time and resources.
Long-Term Archiving: Some backup solutions offer long-term data retention options, enabling organizations to archive historical data for compliance or reference purposes while maintaining efficient storage management.
Data Security Assurance: Choosing the Right Backup Solution
When selecting an Office 365 backup solution, organizations must prioritize data security and choose a solution that meets their specific needs. Key factors to consider include:
Encryption: Ensure that the backup solution encrypts data both in transit and at rest to protect it from unauthorized access.
Compliance: Verify that the backup solution complies with relevant regulatory standards, such as GDPR, HIPAA, or SOC 2, depending on your industry and geographic location.
Reliability and Scalability: Choose a backup solution that is reliable, scalable, and capable of handling the growing volume of Office 365 data generated by your organization.
Ease of Use: Look for a backup solution with an intuitive interface and user-friendly features that simplify the backup and recovery process.
Automatic Backup: Opt for a solution that offers automatic, scheduled backups to ensure regular data protection without manual intervention.
Support and Maintenance: Consider the level of support and maintenance provided by the backup solution provider, including updates, patches, and technical assistance.
Cost-Effectiveness: Evaluate the total cost of ownership, including licensing fees, storage costs, and any additional expenses associated with the backup solution.
Preserving peace of mind in the digital age requires a proactive approach to data security and protection. By implementing reliable Office 365 backup solutions and adhering to best practices for data security assurance, organizations can mitigate the risks of data loss, ensure business continuity, and maintain compliance with regulatory requirements. Investing in the right backup solution is not just a matter of safeguarding data—it's a strategic imperative for the long-term success and resilience of your organization.
#Office 365 Backup Solutions#Data Security Assurance#Data Protection#Business Continuity#Cloud Backup#Cybersecurity
0 notes
Text
Demystifying Healthcare Standards: What You Need to Know

In the rapidly evolving landscape of healthcare, healthcare standards play a pivotal role in ensuring quality care delivery, patient safety, and efficient interoperability among various systems. However, navigating through the intricacies of these standards can often seem daunting. This article aims to demystify the realm of healthcare standards by providing comprehensive insights into key aspects such as regulatory compliance, interoperability, data security, standardization organizations, and quality assurance.
Regulatory Compliance
One of the fundamental pillars of healthcare standards is regulatory compliance. Healthcare providers must adhere to a myriad of regulations and guidelines set forth by governmental bodies and regulatory agencies. These regulations govern various aspects of healthcare delivery, including patient privacy, billing practices, and quality assurance protocols. Failure to comply with these regulations can result in hefty fines, legal consequences, and reputational damage for healthcare organizations.
Interoperability
In today's digital age, seamless interoperability between different healthcare systems and technologies is imperative for efficient data exchange and collaboration among healthcare professionals. Standards such as HL7 (Health Level Seven) and FHIR (Fast Healthcare Interoperability Resources) facilitate the interoperability of electronic health records (EHRs), medical devices, and other healthcare IT systems. By adhering to these standards, healthcare organizations can enhance care coordination, streamline workflows, and improve patient outcomes.

Data Security
The protection of sensitive patient information is paramount in healthcare, making data security a critical component of healthcare standards. With the increasing prevalence of cyber threats and data breaches, healthcare organizations must implement robust security measures to safeguard patient data from unauthorized access, disclosure, or manipulation. Encryption, access controls, and regular security audits are essential practices to ensure the confidentiality, integrity, and availability of healthcare data.
Standardization Organizations
Behind the scenes, various standardization organizations work tirelessly to develop and maintain healthcare standards that govern different aspects of the industry. Organizations such as the International Organization for Standardization (ISO), the Health Information Technology Standards Panel (HITSP), and the American National Standards Institute (ANSI) play crucial roles in setting standards related to medical devices, terminology, coding systems, and interoperability protocols. Their efforts ensure consistency, compatibility, and quality across the healthcare ecosystem.
Quality Assurance
At the heart of healthcare standards lies the overarching goal of quality assurance. Healthcare organizations strive to deliver safe, effective, and patient-centered care by adhering to established standards and best practices. Quality assurance encompasses processes such as performance measurement, outcome monitoring, and continuous improvement initiatives. By implementing evidence-based guidelines and quality metrics, healthcare providers can enhance clinical outcomes, reduce medical errors, and optimize resource utilization.
In conclusion, understanding and adhering to healthcare standards are essential for ensuring the delivery of high-quality, safe, and effective healthcare services. By embracing regulatory compliance, promoting interoperability, prioritizing data security, collaborating with standardization organizations, and embracing a culture of quality assurance, healthcare organizations can navigate the complex landscape of standards with confidence and proficiency. As healthcare continues to evolve, staying informed and proactive in adopting and implementing healthcare standards will remain paramount for success.
#Regulatory Compliance#Interoperability#Data Security#Standardization Organizations#Quality Assurance
0 notes
Text
Features of the Most Reliable VPN Services
In today’s interconnected world, where privacy concerns and data breaches are rampant, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. However, not all VPN services are created equal. While some may offer flashy features or enticing deals, the true mark of reliability lies in a set of core features that distinguish the best from the rest. In…

View On WordPress
#A#Cross-Platform Compatibility#Customer Support#Customer support availability#Data encryption#Data encryption standards#Data Protection#Data protection measures#Encryption protocol security#Geo-restriction#Geo-restriction bypass#Geo-restriction circumvention#Internet safety#Internet safety assurance#Kill switch#Kill switch feature#Leak protection#Leak protection mechanism#Network reliability#Network reliability assessment#No-logs guarantee#No-Logs Policy#Online Privacy#Online privacy protection#Privacy policy assurance#Privacy protection#Secure Connection#Secure connection establishment#Security encryption#Server network
0 notes
Text
RECENT UPDATES ON THE BAD INTERNET CALIFORNIA BILLS:
Sadly, both AB1949 and SB976 passed and are now on their way to the governors desk.
We need him to veto them so they dont become Law.
If you havent Heard of the danger of those bills for the Internet , this post explain it thoroughly :
- Post doing a deep explanation on those bills here
I CANNOT emphasize enough how these would have a global effect on the Internet given that most websites and apps originates from California and not all of them could afford either following those bills or moving states.
Now, as the bills are on their way to the governor, we need Californian citizens to voice their oppositions to those bills to the Governor Gavin Newsome HERE
(Non California peeps, we are urging you to share this as well!!! )
Please keep in mind that calling with phone is much,much more efficient.
You can also send faxes with Faxzero
Here are scripts you can use as arguments : (text/alt version below the read more )
Than you for reading. Even if youre not from California, please spread the word anyway ! Make posts,tweets,etc
REBLOGS ENCOURAGED
TEXT VERSION :
AB 1949
Hello, my name is (INSERT NAME HERE) and I'm one of the Senator's constituents from (INSERT CITY HERE). I'm calling to urge the Senator to vote NO on AB 1949, the amendment to the California Consumer Privacy Act of 2020. While this bill's intent is to prevent the sharing and sale of minor's information under the age of 18, the method it would intend to do so by is written far too broadly for it to be safely and reasonably implemented.
While this bill retains a safer standard of the business requiring actual knowledge of a consumer being under the age of 18 to be held liable for the sharing or sale of personal information, its wording is still too broad to exclude a default usage of age verification by online businesses in order to protect themselves from liability. Taking measures such as age verification, age assurance, or other data collection and analysis to determine the age of users. Even though measures like this have been proven to be vulnerable to data breaches no matter how secure they proclaim to be. Such as this year's largest discovered breach of AU10TIX, which supplies age verification to companies like TikTok, X, Uber, LinkedIn, Paypal, and many others.
As it stands, this bill is far too broad in its wording and enforcement of its age-specific measures to be considered a safe piece of legislation. Which is why I urge the Senator to vote in opposition to this measure.
Vote NO on AB 1949.
---------------------------
SB 976
Hello, my name is (INSERT NAME HERE) and I'm one of the Assembly member's constituents from (INSERT CITY HERE). I'm calling to urge the Assembly member to vote NO on SB 976, the Protecting Our Kids from Social Media Addiction Act. Although this bill has intent to protect the mental and emotional health of California's youth, the method this bill would intend to use could be counterproductive to that goal, or even endanger them further.
One of this bill's primary measures includes requiring verifiable parental consent to allow websites to display “addictive” feeds to minor users. However, the ways “verify” the identity and age of a responsible parent are often invasive and dangerous. Especially since these methods have proven repeatedly to be vulnerable to data breaches that can leak sensitive information to bad actors. Such as this year's largest discovered breach of AU10TIX, which supplies age verification to companies like TikTok, X, Uber, LinkedIn, Paypal, and many others. To determine if this is necessary at all would also require collecting even more data on minors and non-minors alike to determine who would even require these measures to be set in place. Especially when it would have control over someone's access to a website or application based on the time of day, as this bill would require in order to “reasonably determine” the user is not a minor.
The vagueness of this bill's text at all is dangerous as well. The broad-spectrum definition it gives of “addictive internet-based service or application” could cause an unintended censorship effect where minors and adults alike could be blocked from accessing information purely because some part of a website or application uses a “feed” which could arguably fit the bill's definition of “addictive”
With all of this in mind, I urge the Assembly member to vote in opposition of this measure to protect the privacy and safety of California's minors and adults alike.
Vote NO on SB 976.
346 notes
·
View notes
Text
Writing Notes: Personality Traits

Raymond Cattell's Trait Theory
Warmth
LOW level of warmth:
More likely to be Reserved – detached, critical, aloof, stiff
HIGH level of warmth:
More likely to be Outgoing – warmhearted, easy-going, participating
Intellect
LOW: Less Intelligent – concrete-thinking
HIGH: More Intelligent – abstract-thinking, bright
Emotional Stability
LOW: Affected By Feelings – emotionally less stable, easily upset, changeable
HIGH: Emotionally Stable – mature, faces reality, calm
Aggressiveness
LOW: Humble – mild, easily led, docile, accommodating
HIGH: Assertive – aggressive, stubborn, competitive
Liveliness
LOW: Sober – taciturn, serious
HIGH: Happy-Go-Lucky – enthusiastic
Dutifulness
LOW: Expedient – disregards rules
HIGH: Conscientious – persistent, moralistic, staid
Social Assertiveness
LOW: Shy – timid, threat-sensitive
HIGH: Venturesome – uninhibited, socially bold
Sensitivity
LOW: Tough-Minded – self-reliant, realistic
HIGH: Tender-Minded – sensitive, clinging, overprotected
Paranoia
LOW: Trusting – accepting conditions
HIGH: Suspicious – hard to fool
Abstractness
LOW: Practical – “down-to-earth” concerns
HIGH: Imaginative – bohemian, absent-minded
Introversion
LOW: Forthright – unpretentious, genuine but socially clumsy
HIGH: Astute – polished, socially aware
Anxiety
LOW: Self-Assured – placid, secure, complacent, serene
HIGH: Apprehensive – self-reproaching, insecure, worrying, troubled
Open Mindedness
LOW: Conservative – respecting traditional ideas
HIGH: Experimenting – liberal, free-thinking
Independence
LOW: Group-Dependent – a “joiner” and sound follower
HIGH: Self-Sufficient – resourceful, prefers own decisions
Perfectionism
LOW: Undisciplined Self-Conflict – lax, follows own urges, careless of social rules
HIGH: Controlled – exacting will power, socially precise, compulsive
Tension
LOW: Relaxed – tranquil, unfrustrated, composed
HIGH: Tense – frustrated, driven, overwrought
Boiling Down the Traits
In order to scientifically establish a formal framework for understanding personality, Cattell used a statistical technique known as factor analysis.
He started out with a list of 4,500 adjectives that could describe people (taken from the English dictionary).
He then completed a laborious process of grouping these adjectives into 171 ‘clusters’, which were used in a series of studies where people rated others on the traits.
Over a period of several years, Cattell and his team of psychologists then used this data to boil down the set of traits to just 16.
These 16 traits were the smallest number of factors believed to meaningfully describe observable behaviour.
Sources: 1 2
More: On Character Development
More: On Psychology
#writing notes#character development#psychology#traits#writeblr#studyblr#dark academia#writing reference#spilled ink#literature#writers on tumblr#writing prompt#poetry#poets on tumblr#fiction#creative writing#writing inspo#writing inspiration#writing ideas#writing resources
158 notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image:
Mike (modified)
https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0
https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
576 notes
·
View notes
Text
Yandere SCP Senior Researcher!Dottore who loves to act as the mentor figure for Agent!Darling.
Dr. Zandik had always been known for his surgically precise way of handling anomalies— but there's an intensely palpable reason as to why urgent cases aren't left on his desk. Before he could ever conclude an experiment, he'd ensure that he explored every possible data there is to be recorded, quantifiable or otherwise. This usually meant he'd apathetically sacrifice Class-D personnel just to find what the test subject would react. Site 02 reveres him... Yet most of his colleagues would rather have new blood trained than indulge his unnecessary experiments.
What made you first stand out to him was your files. Apparently, you share similarities with the famous SM-046 patient; you've contracted Urbach–Wiethe disease in your early childhood as well. Just like SM-046, your colleagues dubbed you as "Agent Without Fear". You could only shrug and laugh the teasing off. It's a challenge for you to distinguish what is malicious from pure— so you lived most your life expecting the latter.
With Dr. Zandik's passionate nagging requests, SCP-500 was updated with a new line...
Addendum 500-13:
Request 500-2022-A approved. One (1) pill of SCP-500 was ingested by Agent (L/n). Subject reported to have improved skin, mucous membranes, eye, vision, speech, and respiratory symptoms. However, neurological symptoms caused by Urbach–Wiethe disease have shown no signs of improvement. Number of pills is forty-six (46) at the time of writing.
In truth, the fact that you remained as the "Agent Who Can't Feel Fear" after the Trial 1 made Dr. Zandik more interested in you. Which is why, much like last time, the doctor submitted another revision. Instead of an SCP, it was a personnel file.
Yours.
Incident Report 921-A
Date: [REDACTED]
Personnel Involved:
Dr. Zandik "Dottore" █████ [Senior Researcher]
Agent (Y/n) (L/n) [Assigned MTF Officer]
BEGIN LOG
Dr. Zandik: Agent (L/n), just the person I wanted to see. I’ve requested you be assigned as my permanent bodyguard.
Agent (L/n): Really? That’s a new one. Why me?
Dr. Zandik: I’m very interested in your unique approach to security. I think your presence will be invaluable.
Agent (L/n): Well, if you say so, Dottore. I guess I’m in! Every time I work with you, you're always dragging me around to say hi to whatever weird and funky SCPs you're working with. This should be fun.
Dr. Zandik: Undoubtedly so. I’m looking forward to working with you.
Agent (L/n): Great! I’ll do my best to keep you safe, even if I seriously think you can handle most things on your own, Doc.
Dr. Zandik: I assure you. It’ll be a learning experience for both of us.
END LOG
Addendum Incident 921-A-1:
Agent (L/n) has been reassigned as Dr. Zandik’s permanent security detail, as requested by Dr. Zandik. The nature of Dr. Zandik’s interest in this arrangement remains undisclosed to Agent (L/n).
#Zandik x reader#dottore x reader#yandere dottore x reader#SCP au#yandere genshin impact x reader#yandere gi#yandere doctor#yandere male#yandere genshin#yandere genshin imagines
99 notes
·
View notes
Text
YOU'VE GOT EMAIL (König X OC: Medical Student!Snow) PART I

Summary: When the Colonel from some Private Military Corporation group accidentally send KorTac's secret file via email to a random civilian girl.
or
König send wrong email to a wrong person
TWs: A lot curse words (from Snow), both of them being passive-aggressive, slow burn (kinda). I just wrote this for fun
Words Count: 3k (That's a lot for an email lol)
--
From: Colonel_Kö[email protected]
02/28/23 at 03:42 pm
Subject: KorTac Tactical Operations File E12345 Classification: Top Secret
Lieutenant,
Apologies for the inappropriate transmission. As head of KorTac Special Forces, securing sensitive documents is of utmost priority. Please confirm deletion of the attached file and we’ll consider the matter closed.
While I understand your confusion receiving such a file unsolicited, KorTac business must remain confidential. I trust a responsible professional such as yourself understands the necessity of discretion in such matters. Please don’t hesitate to contact me if any other issues arise.
Colonel König
KorTac Commanding Officer
--
From: [email protected]
To: Colonel_Kö[email protected]
02/28/23 at 07:12 pm
Subject: RE: Creepy email
Excuse me,
I have no idea what you’re talking about. All I know is I got some weird files from “KorTac Tactical” that I definitely did NOT ask for. Do you know how scary it is to get secret military documents out of nowhere? I thought it was one of my friends pranking me at first.
Instead of lecturing me about deleting things, maybe you should be more careful who you send your “top secret” info to. I’m just trying to study neurology over here, not get dragged into some clandestine Special Forces stuff.
Lighten up a little, yeah? It was an honest mistake I’m sure. No harm done.
Snow
--
From: Colonel_Kö[email protected]
02/28/23 at 08:02 pm
Subject: RE: RE: Creepy email
Ms. Farron,
I can assure you there was no “creepy email” or files sent from this office. As Commander of one of the world’s premier private military factions, securing classified intel is of utmost priority. If some file was erroneously transmitted to your address in error, it did not originate from my users.
While I understand the desire to shrug off mistakenly received sensitive documents, national security does not warrant such lackadaisical treatment. If you have relevant data in your possession, basic courtesy requires replying to the original correspondent – in this case, myself – to ascertain the source of error.
Do let me know if you retrieve any files in question. And in future, a bit more discretion and less indignation may serve you well when inadvertently encountering restricted information networks. Consider this a learning experience.
Regards,
Colonel König
KorTac Commanding Officer
--
From: [email protected]
To: Colonel_Kö[email protected]
02/28/23 at 08:22 pm
Subject: RE: RE: RE: Creepy email
Hi Colonel Tightpants,
Thank you for the condescending lecture. As I’ve said THREE times now, I never got any files from you or KorTac or wherever before. All I know is I woke up to an ominous email saying “Top Secret KorTac files” or something. Pretty annoying/alarming for a simple student!
And excuse me for not dropping everything to thoroughly investigate a mistake that wasn’t even mine. Some of us have actual classes to study for, not play secret agent all day.
If you’re so worried about security breaches, maybe focus on your end instead of harassing innocent people via multiple snobby emails. I’ve got better things to do than argue in circles with Mr. High-and-Mighty.
Please remove me from your contact list going forward. And do try to lighten up a little!
Regards,
Snow
P.S. The file is attached. I called it “Creepy Email From Creepy Colonel” for your convenience. Have fun decrypting your own mystery ;)
--
From: Colonel_Kö[email protected]
02/28/23 at 09:42 pm
Subject: RE: RE: RE: RE: Creepy email
Ms. Farron,
I will not be spoken to in such a disrespectful and unprofessional manner. While your frustrations are understandable, maintaining proper decorum and respect for sensitive operational matters is not an optional courtesy – it is imperative.
You’re accusations of “harassment” are as unfounded as they are insulting. Do not mistake my patience and courtesy thus far for weakness. Should any real documents surface from my network in error, I expect their immediate return without petulant games or sass.
As a private military organization operating across the globe, security is no light concern for this command. If unable to grasp even the basic responsibility of confirming received documents' origins for the sake of national safety, perhaps the world of intelligence is beyond your current realm of comprehension.
Consider this your final warning. Any further unsubstantiated claims or uncooperative behavior will be met with the full weight of legal action and your academic institution will be notified accordingly. Is that absolutely clear, Ms. Farron?
Reply confirming so or cease contact immediately. I will not tolerate insubordination, especially from an civilian amateur dabbling where she has no clearance. Maintain discretion as instructed or suffer consequences – the choice is yours.
Colonel König
KorTac Commanding Officer
--
From: [email protected]
To: Colonel_Kö[email protected]
03/01/23 at 09:29 am
Subject: RE: RE: RE: RE: RE: Creepy Email
Colonel High-Horse,
Spare me your thinly veiled threats. If you’re so sure I have hide some Top Secret Files™, by all means come search my dorm room yourself since you clearly don’t believe a word I say. Oh wait, you can’t – because there’s NOTHING.
Maybe take a break from power tripping over email and try listening to the person who’s actually involved for once. Not my fault if your big bad security systems have holes. But I guess acknowledging mistakes isn’t very military, is it?
You wanna see uncooperative and petulant? Keep harassing me and I’ll forward our whole conversation to the national news. Something tells me they’d love to hear how easily “the world’s premier private military” loses confidential files.
So for the last time – I did NOT receive ANY files from you or KorTac aside the one you accidentally send. If you’re incapable of comprehending that, then you’re dumber than you look. Consider THIS your final warning to lay off before I take action, Colonel Tightass.
Snow
Formerly Civilian, Currently Pissed Off
--
From: Colonel_Kö[email protected]
03/01/23 at 08:55 am
Subject: Enough
Ms. Farron,
Your insubordination has crossed several lines. While I sought to resolve this discreetly, you force my hand with threats and insults. Know that I do not respond kindly to such provocation.
If you insist upon escalating this beyond reason, so be it. However, tread carefully – you are ignorant of forces beyond your control. Dare to sully KorTac’s name to fuel your petulance, and all your academic and personal records will undergo… thorough review.
Accidents happen, as you claim. But any damage to our operations will not be taken lightly, no matter your perceived innocence. Heed my words well, girl – you do not wish to become an enemy of this command.
Consider this last attempt at civil discourse. Cease contact and let this die, or suffer consequences you cannot imagine. The choice, as before, remains yours.
I expect no further correspondence. You are now on formal notice – proceed at your own peril.
Colonel König
KorTac Commanding Officer
--
From: [email protected]
To: Colonel_Kö[email protected]
03/01/23 at 11:38 pm
Subject: Go to Hell
You want a fight, you’ll get one you pompous prick. Your “command” and threats mean nothing to me.
If anything happens to my academic career or personal life, the world will know exactly who’s responsible. I don’t care how elite you think you are.
Bring whatever you’ve got – I’m not afraid of some borderline psychotic and his glorified gun club. You want a target? Consider it painted on your back from now on.
Have fun trying to intimidate me, ASSHOLE. You just made the worst enemy of your pathetic life.
Goodbye forever. Don’t bother responding – you’re officially dead to me.
Snow Farron
Future Doctor, Current Pain in Your Ass
--
From: Colonel_Kö[email protected]
03/02/23 at 01:29 am
Subject: So Be It
Foolish girl. You have no concept of the forces you now contend with. Consider carefully the hole you’ve dug, for there will be no mercy if you proceed.
However, my integrity will not permit baseless threats against civilians. If you agree to cease hostilities and let this dissolve quietly, no further action will be taken. Your record and life will remain untouched.
The choice is simple – walk away unscathed, or persist in this idiocy and face consequences beyond imagination. Think carefully on your next move, little one. Tread no further, and this can end.
You have one hour for a sensible reply before measures are taken. Make them count.
Colonel König
KorTac Commanding Officer
--
From: [email protected]
To: Colonel_Kö[email protected]
03/03/23 at 02:04 am
Subject: Bite Me
Yeah, I’m real scared of your “forces” and “consequences beyond imagination.” Give me a break.
You think I’m going to bow down to your threats just because you’re some big shot Colonel? Please. I’ve dealt with way scarier than pompous bully babies like you.
So do your worst, tough guy. Come at me with everything you’ve got. I promise it still won’t be enough to make me back down from a pissant fraud like you.
Your “hour” can go fuck itself. You want to end this? Then stay the hell away from me and leave me alone forever. Otherwise this isn’t over by a long shot.
Tick tock, pal. Your time is running out and so is your chance to slink away with your tail between your legs. Better figure out your next move fast!
Not holding my breath for anything “sensible” though. Later, loser!
Snow “Untouchable” Farron
--
From: [email protected]
To: Colonel_Kö[email protected]
03/05/23 at 11:09 pm
Subject: wassup bitchhhhh
Hey asshooooole its ur girl Snow again!! Had a few dranks w/ friends to forget ur stupid email but the pain remainsss lolll
Jus wanted to let u kno ur still a total dickhead no matter how drunk I get. Probly shouldn’t be emailing u since last time but fuck it YOLO right???
Anyway ur threats meant nothing I had a blast tonight. Try n stop me next time I feel like partying fuck face!!! No1 messes w snow n gets away with it
Also saw some guy who looked like u at the bar what a coincidink lol. Hope he feels as stupid as u in the morn ;))
Hope ur having a shit night missing out on the fun. Don’t reply I prob wont even remember this! Byeeeeeee loser stay mad <33333
Xoxo drunk snow
--
From: Colonel_Kö[email protected]
03/06/23 at 01:50 am
Subject: RE: wassup bitchhhhh
Well well, what have we here. It seems our intrepid Dr. Farron has landed herself in an inebriated state this night.
Can’t say I blame you for seeking alcohol’s comfort after our little disagreement. Dealing with my “stupid emails” and “threats” must have been terribly traumatic. You have my deepest sympathies, truly.
While unwise to conduct militarized business intoxicated, I’ll admit your drunken ramblings provided some mild amusement. The imagery of you partying it up solely to spite me was rather quaint. Do try to stay safe in your revelries, dear – would hate for some unfortunate accident.
As for your daring insinuation about encountering my likeness at a bar, I can assure you my nights are occupied with matters far more pressing than drinking. But I appreciate the laugh, strange as it came from such a belligerent tongue.
Enjoy your hangover, Snow. And sleep well – who knows what mischief tomorrow may bring.
Regards,
Colonel König
KorTac Commanding Officer
P.S. Do refrain from over-indulging too often. Wouldn’t want those fine medical skills to dull prematurely, now would we?
--
From: [email protected]
To: Colonel_Kö[email protected]
03/06/23 at 05:28 am
Subject: RE: RE: wassup bitchhhhh
Yeah yeah, laugh it up. We all do dumb shit when we’re drunk occasionally. At least I have an excuse, unlike you and your constant stick up the ass personality.
That being said, I suppose I owe you an apology for that ridiculous email last night. Not my finest moment, to say the least. But you seem to bring out the worst in me, so.
Consider us even for any “amusement” you got at my expense. I’m suffering enough with this hangover from hell as it is.
Just so we’re clear though – I’m not some damsel for you to patronize or imply threats towards. Keep your smug sarcasm, I don’t need it. We’re done here, got it?
Good. Now fuck off and leave me alone to die in peace, Dickhead von Buzzkill. And next time – lay off the sauce OR lay off me. Your choice, Colonel
Snow “Moderately Sober But Still Pissed” Farron
--
From: [email protected]
To: Colonel_Kö[email protected]
03/06/23 at 09:33 am
Subject: RE: RE: RE: wassup bitchhhhh
Alright Colonel Buzzkill, I’ll admit my constant insults aren’t getting us anywhere. As much as I hate to inflate that already massive ego of yours, maybe there was a tiny little misunderstanding somewhere along the way.
Med school has been kicking my ass lately and I’ve been on edge. Between the mounting student loans, endless assignments, and stressful exams, I’m about one Red Bull away from a full breakdown. Not that you probably care about such peasant problems.
Anyways, my point is – I may have overreacted a bit to this whole email mixup. Even if it WAS totally not my fault *eyes emoji*. Can’t a girl blow off some steam without the world’s most uptight Colonel threatening her into an early grave?
Lay off with the intimidation tactics already. I said I was sorry for getting drunk and belligerent, more or less. What more do you want, my first born child in sacrifice?
Just, try to lighten up a little if we have to keep interacting for god knows what reason. I’m too exhausted to keep fighting a war on 20 different fronts. Truce?
Overworked and Underpaid,
Snow
--
From: Colonel_Kö[email protected]
03/06/23 at 09:01 pm
Subject: RE: RE: RE: RE: wassup bitchhhhh
Oh? So the fledgling doctor deigns to admit a modicum of culpability at last. How gracious of her highness to acknowledge her part in this debacle, no matter how begrudgingly.
Though I’ll not deny deriving a certain satisfaction from seeing you squirm, that was never my aim. As Commander of KorTac, security of sensitive data is no laughing matter – a concept you seemed unwilling or unable to grasp at the time.
However, as one engaged in higher pursuits of intellectual rigor and public service, I can understand the pressures that come with such territory. Medical education is a noble yet arduous path, as I’m sure even your addled mind comprehends on occasion.
Very well, Ms. Farron – consider this matter put to rest. A temporary ceasefire it is, for the sake of future global stability if nothing else. But tread not again where you have been warned, or I shall not be so gracious next transgression.
Do try to mind your health and studies in lieu of drunken revelry. Wouldn’t want to lose such a pugnacious spirit to frivolity or misfortune. Now, do run along – no doubt some looming assignment awaits its dissection.
Colonel König
KorTac Commanding Officer
--
From: [email protected]
To: Colonel_Kö[email protected]
03/07/23 at 02:19 am
Subject: Aw, you DO care!
Aww, is that actually concern I detect underneath all the big important Colonel bluster? I’m touched, really. Who knew you had a soft spot for lowly students like me.
Admit it – you just can’t stand the thought of little ol’ me disappearing in some “frivolous misfortune.” You’d miss having me around to aggravate that permanent stick up your butt!
But don’t worry, it’ll take more than a silly paper or two to take me out of commission. Unlike some people, I actually know how to unwind without threatening international incidents *cough cough*.
All jokes aside though, truce accepted on my end too. Maybe now we can move past wanting to strangle each other every time we’re in the same email chain. Small victories, right?
Anyways, gotta get back to the grind. Thanks for not making me regret extending the olive branch…this time. Don’t do anything I wouldn’t do!
Your Favorite Almost-Doctor,
Snow
--
From: Colonel_Kö[email protected]
03/07/23 at 08:05 am
Subject: RE: Aw, you DO care!
Cease this incessant jesting at once, fraulein. I neither “care” for you as anything more than a potential security concern, nor possess any jovial qualities to “aggravate.”
A commander's duties require maintaining surveillance of volatile elements wherever they arise. You have thus far proven yourself quite the unpredictable variable, so forgive my reluctance to take eyes fully off the matter.
As for your studies, consider this the only encouragement they shall receive from me. Master your craft with distinction, then mayhaps our paths need not cross again in the future. Though I admit the thought of you disappearing into obscurity does bring its own satisfactions to ponder.
Now then, if you’re quite finished wasting both our time with your misguided attempts at levity, some of us have real work to which attending. Do try and keep yourself from causing further disruptions, medic. You may resume your “grind” in peace.
Colonel König
KorTac Commanding Officer
--
From: [email protected]
To: Colonel_Kö[email protected]
03/07/23 at 12:56 pm
Subject: RE: RE: Aw, you DO care!
Always so grumpy, Colonel Grumpy Pants! Lighten up a little, will ya? Not all of us can be stoic hard asses all the time.
Speaking of asses, mine is practically dragging on the floor from exhaustion. Between classes, labs, studying, and my various part-time jobs, I’m surprised I have any brain cells left at all.
Don’t even get me started on these student loans. At this rate, I’ll be paying them off until I’m 90. Not that you military bigwigs have to worry about pesky things like money, I’m sure. Must be nice.
You know, maybe I should just forget this whole doctor thing and become a sugar baby instead. At least then I could afford to eat once in a while AND maybe some lucky rich person would be willing to pay off my debts. What do you think – interested in an investment opportunity? I promise I come with lots of free sass and jokes at your expense!
Kidding of course…or am I? You’ll never know!
Your favorite broke and tired med student,
Snow
--
From: Colonel_Kö[email protected]
03/07/23 at 03:37 pm
Subject: RE: RE: RE: Aw, you DO care!
One of these days that improperly-filtered mouth of yours will find its owner in hot water she can’t jest her way out of, medic. I’d advise reigning in these fanciful sugar baby musings before they land you in a far less pleasant situation.
However, your frustration with the systemic burdens of medical education is…understandable. The modern model leaves much to be desired in terms of sustainability for both student and society. A dysfunction perpetuated by greed and shortsightedness at the highest levels, as with so many ills in this world.
As for offers of “investment,” I’ve no surplus funds to patronize frivolities. Nor the patience to entertain speculative propositions from volatile girls who can’t keep themselves from inviting more trouble than they bargain for. Focus that restless energy on your studies as discussed, and all should proceed smoothly.
Now then, if there are no further inanities requiring response, I’ve a command to oversee. Best of luck with exams and endeavors, Farron. Dismissed.
Colonel König
KorTac Commanding Officer
I will write the next part later when I have time <3
Also comment love and reblogged are very appreciated! 💖
#könig cod#konig mw2#konig call of duty#könig#cod oc#cod fic#cod mw2#könig x oc#könig cod mw2#cod könig#cod x oc
106 notes
·
View notes
Text
Accidental Kisses! || TNG Star Trek x Male!Reader
William Riker
You stumbled down the stairs while he was walking up, Willaim lunged to catch you, which knocked your lips together.
"Oh- are you alright, Lieutenant? You took quite a tumble."
You apologize for stumbling into him and kissing him, to which he smiles and waves it off as an accident. After all, there was no harm in it!
Afterwards, he absentmindedly licks his lips and tastes your chapstick, reminding him of the encounter. His cheeks tinge pink- hopefully his feelings still remain a secret
Worf
As Worf's assistant and Assistant Chief of Security, Worf expected you to be in peak physical condition- this kiss happens while sparring- he tackled you to the ground, and in the struggle, you two share a rough kiss.
Worf pins you down by the neck and arms, which effectively left you prone. He mumbles "That better have been an accident." You nod frantically and he releases you.
Apologized for getting too rough with you- blaming it on reflex more than actual aggression. You apologize for the kiss, which still haunts his sweetest dreams to this day.
Data
You had no idea what the fuck happened. Suddenly, you were saying "hi" to Data in the rec room, then his hands were on your cheeks as he kissed you with a mountain of electricity tingling behind his lips.
"What? the hell?" You manage to sputter out, Data seemed confused.
"Apologies if I startled you. I was giving you an authentic European greeting from Earth. Did you feel appropriately greeted and our relationship assured?"
"Data- I- first of all, not all of Europe kisses to greet, NEXT OF ALL, THEY KISS THE CHEEKS!"
Geordi La Forge
It was a moment of excitement shared between you two- a project you both had spent countless nights on performed without a hitch in front of the investors. After the meeting, you two were so excited and hugging- it just sorta... happened.
"Oh- oh my god- I'm so sorry." Geordi apologized quickly as he recoiled away from the hug. "It was an accident."
"Yeah- we were just excited, totally an accident on both ends." You respond just as quickly as your cheeks burn up.
Q
Alright, this kiss isn't an accident. He's pissing you off by bothing you during your work, begging for you to entertain him. He wants a human experience! He already looks like one in this form! Do something human!
So, you punched him in the gut, then kiss him roughly- tongue invaded his mouth in a way that made his eyes roll back into his skull at the feeling of being properly paid attention to- even more than expected!
Q finally shut up for a good while as he behaved himself- at the promise of more of those. So, he sat down next to your station and waited patiently for you to be done with our work- then he kissed you!
His kiss was- well, it was Q, what did you expect?
#fanfiction#star trek the next generation#star trek#star trek next gen#star trek x reader#star trek headcanons#worf x reader#data x reader#william riker x reader#q x reader#geordi la forge x reader#star trek x male reader#data soong#geordi la forge#william riker#worf son of mogh#worf#q#prettyboypistol#prettyboy pistol
94 notes
·
View notes
Text
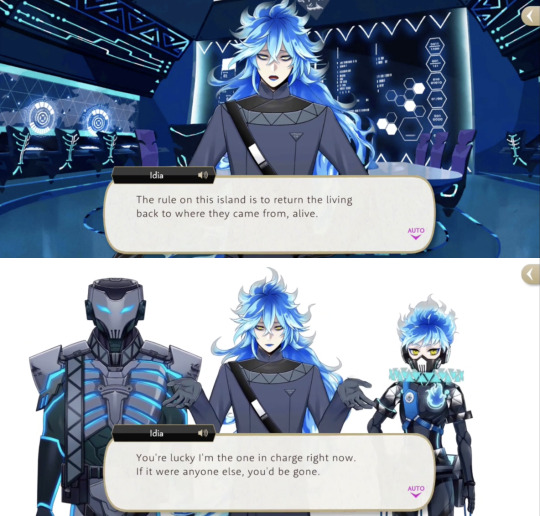
Idia Facts Part 3: Family (pt3)
Idia says that the rule on the island is to return the living back to where they came from, alive, but this might only apply to those they kidnap rather than those who attack them: When Rook, Epel and the prefect appear, he tells them that, if anyone but himself had been in charge at the time, they’d be gone.


In addition to Tartarus and Cerberus, STYX also has the River Lethe: a system that can erase STYX from anyone’s memories, and from any data.
“There’s no point even thinking about making friends with people on the outside. After all…sooner or later, they wouldn’t remember it happened.”
At the end of Book 6 Ortho deletes the River Lethe’s configuration program, which Idia decides to leave to his parents to sort out, while he gets left with a group of classmates that remember everything that happened to them.
“And that’s…normal.”



In Book 7 Idia explains that due to a “tiny fraction” of what STYX does leaking to the public, the press has gone into a feeding frenzy to try and unearth their secrets.
We meet his parents in Book 7, with Idia’s father worrying that the worst may have happened to everyone on the island (“—including our boys…?”), but Idia’s mother says that she guarantees they are alive, based on “a mother’s hunch.”



His mother deduces that Idia has been using STYX communication satellites via access logs (“I’m sure he thought he covered his tracks, but he can’t fool his mom!”), saying, that she knows Idia would absolutely think he needed the internet to survive no matter what.
There is a vague reference to trouble that Aidne Shroud, Idia’s grandmother, had in the past with Briar Valley.
Idia’s mother seems to have great faith in Idia’s abilities: when debating how they will approach the Malleus-controlled Sage’s island with the insufficient AI in STYX power armor she says, “if only (Idia) were here!” (Idia’s mother refers to him as Onii-chan/Ide-kun on JP and “Idy” on EN.” Shroud Family dynamics explained here.)


Ortho asks their mother to craft him a set of gear that can survive Malleus’ spell, which she does by using a copy of Ortho’s schematics on one of Idia’s computers.
Ortho exclaims, “You actually got through Idia’s super-ultra-ironclad security program!?” and she assures him that she didn’t look into any of his password-protected folders.
102 notes
·
View notes
Text

Welcome to The Simblr Office Directory
This blog is an archive of the submissions for the office-centric OC prompt posted by the light of Simblr, @kashisun.
Here you can browse all the amazing creations submitted by your fellow simblrs. Feel free to scroll to your delight or click one of the links under the cut to see who's on roster under (or over) a particular bureau or delegation.
Want to be added to the directory or confirm that you've been queued? Just include a link to your post in an ask off anon and it will be queued within 48 hours. Until we get through the backlog and can queue at a more leisurely pace, all ask submissions will receive a confirmation. You can always mention us, but we won't be able to provided confirmation for that method.
Leaving the company? If you'd like your post removed, just include a link to the post in an ask off anon and it will be removed. Sideblogs may require additional verification. Please allow, at most, 48 hours for the request to be honored. Removal requests will not be confirmed, only acted upon.
Every company's hierarchy is a little different. Designations for this directory are based on some of the companies I've worked for, but especially on the multi-media marketing company I work for now.
Bureaus and Their Delegations
Delegations with an * currently have low or no headcount (posted and queued). Excludes leadership.
Bureau of Client Engagement
Leadership
Billing*
Escalations*
Product Support*
Quality Assurance*
Sales*
Bureau of Compliance (Bureau-specific Internal Affairs and Auditing)
Leadership
Client Engagement*
Facilities*
Finance*
Human Resources*
Information and Technology*
Legal (General)
Legal (Leadership)
Marketing*
Bureau of Facilities
Leadership
Catering*
Environmental (Janitorial, HVAC, and Plumbing)*
Mechanical (Electrical, Elevators, Equipment Maintenance)*
Premise* (Grounds Maintenance and Real Estate)
Purchasing* (From pushpins to pallet jacks)
Security
Warehousing* (Shipping, Receiving, Mail room, and Inventory)
Bureau of Finance
Leadership
Accounting
Asset Management*
Investments*
Travel and Accommodations*
Vendor Relations*
Bureau of Human Resources
Leadership
Career Development (Internships and Internal Role Transitions)
Dependent Care*
Employee Activities Committee (Members are volunteers)
Employee Benefits*
Floating Delegates (Administration) (For profiles that list a nondescript secretary/admin/receptionist/assistant role)
Floating Delegates (General) (For profiles that do not list a position)
Floating Delegates (Leadership) (For profiles that list a nondescript managerial role)
Health Services*
Payroll*
Recruiting*
Training*
Union Relations*
Bureau of Information & Technology
Leadership
Data Security*
Infrastructure*
Public Relations
Research and Development*
Systems and Devices*
Telecommunications*
Bureau of Marketing
Leadership
Copy
Design
Planning and Implementation*
Board of Directors
Chief Officers
CEO - Chief Executive Officer/President
COO - Chief Operations Officer/Vice President
CCO - Chief Compliance Officer/Vice President
CFO - Chief Finance Officer/Vice President
CITO - Chief Information and Technology Officer/Vice President
CMO - Chief Marketing Officer/Vice President
Executive Administration* (Admins that report to chief officers)
206 notes
·
View notes
Text
黒影 (KuroKage) Fever










These images are KuroKage (黒影) propaganda from Kage Corp (影社), designed to circulate on the darknet and reaffirm the corporation's absolute control over global information, security, and counterintelligence. They sometimes contain encrypted messages in their metadata.
Through KuroKage (黒影), Kage Corp (影社) projects an invisible yet omnipresent force, ensuring that their enemies know no network is inaccessible and no threat goes unanswered. It serves as a stark reminder of Kage Corp's (影社) unstoppable power in a world where control of data and counterintelligence determines who rules. This propaganda is crafted to strike fear into the hearts of their enemies and inspire unwavering loyalty in their followers.
"Thank you for placing your trust in KageCorp (影社). As pioneers in cutting-edge technology, we are committed to delivering excellence and innovation in everything we do. We extend our heartfelt wishes for unparalleled success and prosperity in your endeavours. Rest assured, we will prevail."
[Initializing scan… █░░░░░░░░░░░░░░░░░░░░░ 10%]
[Scanning metadata… ████░░░░░░░░░░░░░░░░░░ 30%]
[Decrypting hidden data… ██████░░░░░░░░░░░░░░ 50%]
[Analyzing encrypted code… ████████░░░░░░░░░░░░ 70%]
[Extracting hidden message… ██████████░░░░░░░░░░ 85%]
[Finalizing decryption… ████████████░░░░░░░░ 95%]
[Decryption Complete… ███████████████ 100%]
Hidden Message Detected:
"Through the shadows, we see all. Nothing is hidden. Nothing is safe. KuroKage prevails."
#kurokage#kage corp#cyberpunk#cybercore#japancore#artists on tumblr#character art#ai artwork#concept art#ai art community#ai art#pop art#pop icon#pop culture#counterculture#counterpropaganda#counterintelligence#anime art#spotify#cyborg#gynoid#skull art#anime girl#cute girl
24 notes
·
View notes
Text
The FreeCodeCamp Study Challenge!

I literally just completed this challenge and I thought why not share the challenge on here for other people to take part in if they wanted to!
FreeCodeCamp is an open-source platform that offers various coding courses and certifications for web developers. The goal of this challenge is to choose one of the available courses on the FreeCodeCamp platform, complete the course, and earn the certificate at the end.
The challenge is self-paced, so the duration is entirely up to you. The challenge is there to motivate people into coding and/or continue their coding studies! Especially people in the Codeblr community!
FreeCodeCamp [LINK] offers the following courses:
(NEW) Responsive Web Design Certification (I've done this one)
JavaScript Algorithms and Data Structures Certification (I am going to do this one next)
Front End Libraries Certification
Data Visualization Certification
APIs and Microservices Certification
Quality Assurance Certification
Scientific Computing with Python Certification
Data Analysis with Python Certification
Information Security Certification
Machine Learning with Python Certification
Each course is broken down into multiple sections, and completing all the sections in a course will earn you a certification for that course.

To start the FreeCodeCamp Challenge, follow the steps below:
Choose a course on the FreeCodeCamp platform that you would like to complete.
Complete the course and earn the certificate.
Post about your progress every day that you study using the #freecodecampchallenge hashtag. You can post about what you have done towards the challenge, what you have learned, and any challenges you faced and how you overcame them.
The FreeCodeCamp Challenge is an excellent opportunity to improve your coding skills and earn a valuable certification!!!! Even add that to your resume/CV! I completed this challenge and you can see me posting about it - LINK.
Remember to post about your progress using the #freecodecampchallenge hashtag to track your progress and connect with other participants AND you don't have to study straight days, meaning you can take days off whenever you feel like it!
Good luck!
#freecodecampchallenge#freecodecamp#studyblr challenge#study challenge#codeblr#learn to code#progblr#studyblr#cs studyblr#cs academia#computer science#online learning#coding#programming#compsci#studying#webdev#frontend development#html css#html#css#comp sci#100 days of code#coding study#coding bootcamp
256 notes
·
View notes
Text
youtube
Introducing the latest innovation in pet safety: the NEW HALO COLLAR 3. Elevating the standards of GPS dog fences and trackers, this groundbreaking device is poised to transform the way you safeguard your furry companion. Explore the exciting enhancements packed into the HALO COLLAR 3:
✅ Enhanced PrecisionGPS(™) Technology
✅ Advanced Active GPS Antenna
✅ Extended 24-Hour Battery Life
✅ Seamless Auto-connectivity to Any Cellular Network Worldwide
✅ Innovative Perfect Fit System
✅ Convenient Magnetic Charging Port
✅ Vibrant New Colors: Orchid and Sunburst
Discover all the essential details about the HALO COLLAR 3. What sets it apart? How does the GPS dog fence function? How accurate is its tracking system? Uncover these answers and more as we delve into the comprehensive features of this remarkable device.
With the HALO COLLAR 3, bid farewell to conventional fences and constant monitoring of your pet's whereabouts. This state-of-the-art collar harnesses real-time GPS technology to establish an invisible yet highly effective containment boundary. Say goodbye to cumbersome installations and physical barriers limiting your pet's freedom!
Powered by cutting-edge Global Navigation Satellite Systems tracking technology, the HALO SYSTEM delivers unparalleled location accuracy, comparable to the latest advancements in autonomous vehicles and drones. In fact, the HALO COLLAR's geolocation feature rivals that of leading smartphones, ensuring pinpoint accuracy within a few feet. Plus, with nightly satellite data downloads, your pet's GPS location is instantly precise the moment they step outside.
A standout feature of the HALO COLLAR 3 is its customizable virtual boundaries via the intuitive mobile app. Create secure zones for your pet and receive immediate alerts if they venture beyond these designated areas. Stay seamlessly connected to your furry friend, providing peace of mind and assurance of their safety.
Experience the epitome of tracking prowess with the HALO COLLAR 3. Monitor your pet's real-time location on the app's map, facilitating swift retrieval in case they wander off. Track their movements, access historical data, and receive boundary breach alerts—all with unmatched precision.
This groundbreaking feature effortlessly connects to the strongest and fastest cellular signal worldwide, at no additional cost.
Rest assured, the HALO COLLAR 3 prioritizes your pet's comfort and safety. Waterproof, durable, and ergonomically designed for a secure fit, it ensures uninterrupted adventures with its extended battery life—20% more than its predecessor, the HALO 2+ dog collar.
With upgraded features and advanced technology, the HALO COLLAR 3 offers unparalleled value at the same price as the HALO 2+. Experience the future of pet safety today with the HALO COLLAR 3.
30 notes
·
View notes
Text
So how did Russell Myers hear about it?
The world renowned hospital where the Princess of Wales was treated has launched an investigation over claims staff attempted to access her private medical records.
Bosses have launched a probe into the claims Kate’s confidentiality was breached while she was a patient in The London Clinic in January. At least one member of staff was said to have been caught trying to access the 42-year-old’s notes. The allegations has sent shock waves through the hospital in Marylebone, Central London, which has a reputation for discreetly treating of the royal family, former presidents, PMs and celebrities.
One insider revealed: “This is a major security breach and incredibly damaging for the hospital, given its unblemished reputation for treating members of the Royal Family. Senior hospital bosses contacted Kensington Palace immediately after the incident was brought to their attention and assured the palace there would be a full investigation. The whole medical staff have been left utterly shocked and distraught over the allegations and were very hurt that a trusted colleague could have allegedly been responsible for such a breach of trust and ethics.”
The probe comes after comes as video and pictures emerged this week of Kate and Prince William at a farm shop in Windsor, amid conspiracy theories being churned out by internet trolls about her absence since having an abdominal operation. It is a criminal offence for any staff in an NHS or private healthcare setting to access the medical records of a patient without the consent of the organisation’s data controller. The Metropolitan Police did not confirm whether it had been informed of the allegations.
The London clinic refused to comment on the claims but said: “We firmly believe that all our patients, no matter their status, deserve total privacy and confidentiality regarding their medical information.” The hospital informed the Palace of the alleged breach as soon as it was discovered, sources said. Kensington Palace said: “This is a matter for The London Clinic.”
Who contacted Russell to let him know this happened?
Did someone at The London Clinic notify Russell about this? Or was it someone at Kensington Palace?

#fleet street#uk#the mirror#Russell myers#kate middleton#Catherine The Princess of Wales#kensington palace#palace officials#rumors...conjecture
27 notes
·
View notes
Text
Humans are weird: In the line of duty
( Please come see me on my new patreon and support me for early access to stories and personal story requests :D https://www.patreon.com/NiqhtLord Every bit helps)
The bulkhead slowly rose and Feneci walked on to the command bridge with her film crew. It wasn’t the most ideal of jobs she had been tasked with over the years but it was proving to be one of the most taxing.
She was never fond of interacting with humans and when she had been told by her editor that she would be covering the evacuation convoys from the Temeril homeworld onboard the human cruiser “Queen Ann” she had rightly protested. Humans were known to be suspicious and untrusting of new comers and she had felt as much when she and her crew had first set foot on the ship as it escorted Temeril ships to their refugee locations.
The human’s never said anything openly to her or her team. They treated them with respect and answered all of the questions they were able to; yet there was always a lingering presence in the air that radiated off the general crew that Feneci couldn’t help but summarize to be a general disdain. To them this ship was their home and she was an outsider that had been forced upon them to raise awareness for the ongoing crisis. This feeling thankfully was not shared with the ship’s captain who Feneci had finally been able to secure an interview with.
“Welcome, Ms. Feneci.” An old human in a captain’s uniform stated as the bridge crew parted to let him through. Unlike the other humans he radiated no such ill intent and his smile appeared genuine. He held out a hand for Feneci who took it to shake in standard human greeting rituals.
“Captain Amar, thank you for sparing the time to meet with us.” Feneci replied. “I know you must have your hands full with the evacuation efforts.”
Captain Amar released his hand and straightened out his uniform before motioning Feneci and the camera crew to follow him to the captain’s chair. The chair was situated at the back of the bridge so that the captain could observe the on goings of his entire crew but not higher to give the impression he was lording over them.
“You give me too much praise.” Captain Amar replied as he sat down in his chair. Feneci sat opposite him as the camera feed went green to show the recording had begun. “The real praise should be given to the Temeril’s for organizing an evacuation so quickly.”
“There are those, including some within the Terran government itself, that have stated that the entire evacuation process is unnecessary; that the Temeril homeworld could have been saved had the adequate tectonic stabilizers been deployed.”
Feneci looked down at her data pad for the notes she had written for this interview. “They say the cost of the stabilizers would have been a fraction of what this fleet of ships is now running.”
Captain Amar rocked side to side in his chair as if debating internally how to respond to this statement. After a moment to collect his thoughts he replied. “It is not for me to question the policies of my government, but I can assure you that having seen the Temeril homeworld from orbit adding a few tectonic stabilizers would have only delayed the inevitable.”
“You are an expert in seismic theology?” Feneci countered, hoping to catch the captain in a trap of words.
“I’m afraid I never had time for such studies,” the captain admitted, “but from high orbit I saw a lake of fire the size of a continent appear in the span of three days; consuming everything it touched like a gapping maw of some great beast of old.”
The captain shook his head regretfully. “The Temeril homeworld would become their tomb had we not come to assist with the evacuation and soon to be relocation effort to a new homeworld once we have finished establishing a colony on Techlon V.”
Feneci waved her hand around the bridge. “Since when does evacuation and relocation efforts require military escorts?” She held out a pad for the captain to see. “By our recent count there are at least five military grade vessels in this convoy alone, including this ship we’re on right now which is a cruiser class no less.”
For the first time the captain looked uneasy. “We have received recent reports of marauders operating in the area; preying on isolated ships or small convoy’s to steal either their ships or the passengers onboard.”
This was an actual shock to Feneci. Not only had she not heard any of these reports before, but she was surprised that the human captain would reveal it so freely.
“Was this information made public to the Temeril’s?” she asked, to which the captain shook his head.
“At the time there was a concern that many would instead seek to remain on the planet when faced with the potential danger in space that the marauders posse.” Captain Amar admitted. “As such it was felt that only after the trip was underway would this information be released.”
“Do you have any idea how deceitful that is?” Feneci pressed. “You intentionally withheld vital information from these people!”
Before the captain could reply alarm bells rang out around the control room. Bridge crew that had been ideally listening to the exchange scattered back to their terminals and sounded off their findings.
“Unknown cluster of contacts approaching from the rear of the convoy,” the scanner officer sounded off, “twenty minutes until they’re on us.”
In a flash the captain was up from his chair while Feneci bade her camera crew to continue filming. This would only further highlight the mismanagement the humans had over the convoy as a result of her report.
“Unidentified vessels this is Captain Amar of the Terran Alliance,” Captain Amar stated with authority, “you are approaching a evacuation convoy from the planet Temeril under our protection; identify yourself.”
There was no reply save the resounding pings from the scanner terminal indicating the unknown ships location. The communication officer shook his head and looked back at his captain.
“Full spread across all channels.” Captain Amar stated and the communication officer replied in kind.
“I repeat, this is a Temeril evacuation fleet under the protection of the Terran Alliance; you will identify yourselves at once.”
Once more silence.
“They’ve increased speed, ten minutes to contact.” The scanner officer called out.
“Escorts two and three, break off from the convoy and intercept the approaching vessels; and send word to Terran command we will need reinforcements.” A tactical hologram appeared above the bridge showing not only the formation of ships in the convoy but the approaching craft as well. At the captain’s command the two mentioned escort vessels began pulling away and set course to meet the unknown vessels.
“Escort three is asking for permission to engage if provoked.” The communication officer called over his shoulder looking at Captain Amar. The captain paused to consider his next steps before replying “Permission to engage only if fired upon first; we don’t know if these are the raiders we heard about or some convoy ships that were late to the party.” The officer nodded and relayed the order to the escort ships.
Feneci watched as the two opposing forces drew closer until finally they were right on top of each other when suddenly the coms channels were alive with chatter.
“This is escort two, contacts are not friendly! I repeat, they are not frie-“
The transmission was cut off half way as Feneci watched the marker for the second escort ship vanish. Captain Amar slammed his fist into a nearby terminal leaving an indentation.
“Escort three break off and rejoin the Queen Ann;” Captain Amar barked, “escorts four and five form up on us as well. Keep them away from the convoy at all costs.”
This time Feneci felt the entire ship lurch beneath her feet as the engines powered on and the ship began to turn around. Another round of pings came from the scanner terminal.
“Another twelve contacts just appeared and they’re heading right for us.”
“Clever bastards.” Captain Amar remarked as he took up his command chair once more. “They sent a small force ahead to gauge our numbers. They must think we’re easy pickings if they’ve fully committed now.”
“How far until the convoy reaches the jump point?” the captain called to his scanning officer.
“They need thirty minutes to reach the edge of the system before they can make the jump.” was his answer. Feneci added the time in her head and the raider fleet would easily reach them before they could escape to the jump point. The convoy would either be captured or destroyed dealing a crippling blow to the Temeril people.
“Ms. Feneci, I believe you should make for the hangar bay, get on your shuttle and head back to the convoy at once.” Feneci turned to see Captain Amar addressing her directly. “I can no longer guarantee your safety and this ship is about to enter into combat; we will buy as much time for the convoy to escape.”
“You’re not seriously going to fight them are you?” Feneci found herself asking despite herself. From the tactical hologram it looked like a swarm of red angry dots was rushing them while a thin blue line of Terran ships stood between them and the convoy.
“We were entrusted with the safety of this convoy and the Terran Navy has never shirked its commitments before.”
With that the captain turned from the reporter to focus on the battle at hand while a pair of naval guards stepped forward to escort the crew to the hangar. The last sight Feneci had of the captain was of him directing targeting orders as the first barrages of incoming fire impacted the shields.
-------------------
On this day during the stellar year of 2573, a small Terran fleet under the command of Captain Amar Jabal protected an evacuation convoy of defenseless Temeril’s from a horde of marauders.
Outnumbered three to one, Captain Amar did not hesitate to engage the enemy fleet to buy the fleeing Temeril’s enough time to escape the system safely. The battle was fierce and uncompromising as both sides dueled it out in the void of space with the brave human captain using every trick in his book to keep the enemy focused on him.
Moving his ships in close to threaten the enemy carriers, the vile fiends were forced to keep their fighter wings close at hand to defend their carrier ships rather than chase down the fleeing innocents.
When presented with the overwhelming power of his flagship, the cruiser “Queen Ann”, the raiders found that alone they could not pierce through the mighty shields of the vessel and were likewise pinned in place engaging it lest they be picked off one by one.
But as the battle unfolded the Terran fleet lost many of its ships as they heroically held the line until only the Queen Ann remained.
With her decks breached in a dozen places, weapon systems damaged beyond repair, and her communications cut from the rest of the rescue fleet that was already on their way at max jump speed; the Queen Ann defiantly rammed the enemy flagship and detonated her jump drive in a final act of defiance. The resulting explosion and shower of debris crippled the few marauders that remained leaving them unable to continue their barbarous hunt against the Temeril’s which had safely made it to their own jump points and fled the system.
When the Terran relief fleet finally arrived in system they found a dozen survivor pods from the Queen Ann that had jettisoned from the vessel moments before the captain had initiated the ramming maneuverer.
The surviving crew stated that the captain had ordered all hands to abandon ship and that he alone remained to initiate the final act against his enemies stating:
“It has been an honor to serve alongside each and every one of you. You have done the Terran Navy proud, so hold your heads high in the days to come.
As for myself, it makes a poor captain that does not go down with their ship; and I will be damned if I let these bastards make my Ann into another trophy in their motley fleet of vagabonds and cowards.
Look for me on the horizon when you reach the solar seas of the afterlife.”
In honor of his sacrifice, it has been announced that the new Temeril colony known previously as “Techlon V” is to be renamed to “Amar Prime” and that the Temeril people have already put forward an application to join the Terran Alliance.
Reporting live from Amar Prime this is Feneci Jubal.
-----------
#HUMANS ARE WEIRD#humans are insane#humans are space orcs#humans are space oddities#scifi#story#writing#original writing#niqhtlord01
211 notes
·
View notes