#privacy tool
Explore tagged Tumblr posts
Text
PrivaZer Download - Clean Junk Files & Protect Privacy
PrivaZer is a free tool with an optional premium version that acts as a privacy protector, registry cleaner, and junk file remover for your PC. It helps users safeguard sensitive data by eliminating unwanted traces left behind during regular computer use. PrivaZer goes beyond typical cleaning; it can securely erase data, making it nearly impossible to recover. This feature is especially…
#data protection#data security#deep cleaning#disk cleanup#file eraser#junk file cleaner#PC privacy#portable software#privacy protection#privacy tool#PrivaZer#registry cleaner#secure deletion#system optimization#Windows cleaning tool
0 notes
Text
still confused how to make any of these LLMs useful to me.
while my daughter was napping, i downloaded lm studio and got a dozen of the most popular open source LLMs running on my PC, and they work great with very low latency, but i can't come up with anything to do with them but make boring toy scripts to do stupid shit.
as a test, i fed deepseek r1, llama 3.2, and mistral-small a big spreadsheet of data we've been collecting about my newborn daughter (all of this locally, not transmitting anything off my computer, because i don't want anybody with that data except, y'know, doctors) to see how it compared with several real doctors' advice and prognoses. all of the LLMs suggestions were between generically correct and hilariously wrong. alarmingly wrong in some cases, but usually ending with the suggestion to "consult a medical professional" -- yeah, duh. pretty much no better than old school unreliable WebMD.
then i tried doing some prompt engineering to punch up some of my writing, and everything ended up sounding like it was written by an LLM. i don't get why anybody wants this. i can tell that LLM feel, and i think a lot of people can now, given the horrible sales emails i get every day that sound like they were "punched up" by an LLM. it's got a stink to it. maybe we'll all get used to it; i bet most non-tech people have no clue.
i may write a small script to try to tag some of my blogs' posts for me, because i'm really bad at doing so, but i have very little faith in the open source vision LLMs' ability to classify images. it'll probably not work how i hope. that still feels like something you gotta pay for to get good results.
all of this keeps making me think of ffmpeg. a super cool, tiny, useful program that is very extensible and great at performing a certain task: transcoding media. it used to be horribly annoying to transcode media, and then ffmpeg came along and made it all stupidly simple overnight, but nobody noticed. there was no industry bubble around it.
LLMs feel like they're competing for a space that ubiquitous and useful that we'll take for granted today like ffmpeg. they just haven't fully grasped and appreciated that smallness yet. there isn't money to be made here.
#machine learning#parenting#ai critique#data privacy#medical advice#writing enhancement#blogging tools#ffmpeg#open source software#llm limitations#ai generated tags
54 notes
·
View notes
Text
On Wednesday before I gave my presentation I confessed to a new employee that I was worried it would be too long and she brightly told me her life hack was to just let AI rewrite things for her. She said I should put in all my talking points and ask ChatGPT to give me a five minute exactly presentation. I was like....how is the most polite possible way (since this is a new colleague I shouldn't get off on the wrong foot with) that I can express that I will Not be taking this advice. Ever. I told her that I didn't think we were allowed to use ChatGPT at this job (we most certainly are not, it is a nightmare for any type of protected information) and also that I prefer to write all of my own work. Despite my best efforts the last part of that was still passive aggressive, lol.
Something about being a writer makes it so that it's almost offensive to me for someone to suggest I use AI to do my work instead? Like, the day I reach the point where I let AI write something for me is the day y'all need to be checking me for brain damage because clearly I'm losing it
#i also told her i was capable of making a 5 minute presentation but that i had too much information to cover to explain the project in 5 min#and she was like oh that makes sense!!#but like im sorry 😭am i the insane one or like....#idk to me suggesting I use AI isn't a helpful suggestion it reads as someone telling me i don't know how to do my job#does that make sense?#i don't consider it a lifehack or working smarter instead of harder. it seems like you're suggesting i am incapable of writing well myself#i know a lot of people right now thing AI is the best thing ever#to me it's a blatant omission that you can't do your own work or think for yourself#this is also even crazier of a suggestion to me because that morning i had TWO managers on call debating wording of a sentence#like we were reveiwing this presentation tightly so that we said exactly what we wanted to and met the standards of our administration#chatgpt is not going to understand the nuances of what we can/cannot say or official/approved wording lol#i think we use ai tools in the sense of like...photoshop generative fill or ai stuff in scientific research/arcgis#but i'm like 99% sure we were banned from using chatgpt over privacy concerns of putting controlled information into it#anyway. idk. i know not everyone writes as well as i do.#but i'd rather read bad writing that came from a person than something that was generated for you tbh#and i will help review my colleagues' writing any day
33 notes
·
View notes
Text
In these shitty times I remind you to DITCH CHROME AND GOOGLE and use a reliable browser who won't sell you and your mom.
TL;DR. DuckDuckGo both search engine and browser is a good option for everybody and everyday purpose
I'd think duckduckgo both browser and search engine is a good
If you use iPhones and Mac Safari isn't the worst.
Tor is the best in terms of privacy, but it's run by volunteers so it's better if you don't use it to watch YouTube and download stuff, it's also very slow for socials.
Brave browser is slightly better then duckduckgo, but for average use it's almost the same. Also it has had a couple of controversies overtime.
I've recently found out that duckduckgo has it's own browser as well!!!!! AND it's available on both pc and android and I believe even ios and Mac.
Duckduckgo is (mainly) a search engine that doesn't try to sell you stuff like Google, gives you what you search for unfiltered, doesn't collect your data's, AND datas are filtered and bounced around multiple times to encrypt them better.
I know ecosia is appealing because of the trees, you can still use it, but be aware that there's basically no difference between that and Google. It's not secure nor you're guaranteed the results aren't filtered according to whatever strikes them at the moment
#browser#private#privacy#search engine#google#chrome#how about we put our actions where our mouths are and don’t keep using big capital shit#Also your privacy is actually important#And I don't say that just for shits and giggles#You actively trying to protect your privacy is a huge tool against totalitarian regimes#The thing that you agree to every cookie and shit because they're annoying and you have nothing to hide and you're a public person#Is shitty propaganda that benefits those with power and they did this consciously#Fight for your privacy
11 notes
·
View notes
Text
Anyway, the wedding had a fire ritual and I'm healed
#it was actually wonderful#i was told this tradition is like the newlyweds being in front of fire and the wofe gets apron and the guy some tool like hammer and they#they have to play to do smth like make soup#but none of that lame ass things were here#there was fire there were circles there was dancing and there was going round in circles and there was chanting of newlywed names#and there was yelling of goodwill for the newlyweds and overall it was everything ive ever wanted to do around the fire#that was truly the highlight of my sinking summer#also before the wedding the wedding the newlyweds were teasing me and saying id probably get together with someone in the wedding#and i knew the guestlist and i knew that most of the staff attending were married already and i was like haha maybe the DJ#and guys the dj was really nice actually. he even talked with me a bit.#yeah. yeah. he even talked with me a bit. thats like. someone being nice to me for 2 minutes lol. i know thats like. nothing#but either way idk how old is he. could be a freshly sprouted 19yo.#i already tried to google him to find out but a huge win for his privacy bc i cant find him#so yeah it is what it is. the fire was cool and the dj was nice thats it#oh! and the newlyweds had a dance that transitioned in everyone's dance and as soon as that happened i was like lemee slip to my seat real#quick but the bride pulled me in and we had a really nice dance switching multiple dance partners#even though her main aim was to set me up w her brother lol bc she dragged me and asked her man to drag her brother in to pair us up#but either way as i said i switched partners a lot so it was actually nice even though i cannot dance for my life#also my high heels were extremely comfortable. like i was a bit tired from them at the end of the day but thats it. no pain. lovely.#either way. thank you for reading my friends wedding experience lol xoxo a tired being
4 notes
·
View notes
Text
idk character talking into the void
I’m like. puzzling eshka and romance in my head. what does that look like for her. how does this all fit in her head
#rotating her in my head. like a rubix cube#maybe I’m so ??? about romance that it’s hard#there’s a lot of gender stuff going on too#she’s had relationships before but it’s all been. superficial#it’s hard for her to open up. it’s easy to stand in a room alone and call herself attractive m#putting her next to someone else. someone else who might find her attractive#and the walls come up#the authenticity people want goes away#she can put on this whole feeling pain in her skin but deep down there’s still a lot#thinking about it from a warden perspective really kinda ties stuff in#the other thing w her feeling like her body is a tool#one she uses but it’s there to be used#she loves herself in privacy#I dunno!! new character pondering#oc: eshka
4 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
Make your data invisible online by generating unlimited identities.
- 1.7K+ Upvotes on Product Hunt
- #1 Product of the week
- 14 Days Free Trial
→ http://t.ly/ILF6r

2 notes
·
View notes
Text
found a much easier way to place windows im unstoppable now
#went into the TOOL settings to turn off the camera snapping and found out you can turn off terrain snapping#now i can just use a spare wall to place all these bastards#and the get to work privacy windows are working for me quite well#but now that i can just position whatever wall objects i want with relative ease#i can return to previous ideas like blocking out windows with blank paintings#or mirrors.#simoleon
4 notes
·
View notes
Text
CyberGhost VPN: Unlocking Digital Freedom
Unveil the Power of CyberGhost VPN Are you tired of restrictions on your online activities? Look no further than CyberGhost VPN, the ultimate solution for unlocking digital freedom. With our exclusive deal offering 3 months FREE with the 2-year plan, CyberGhost VPN empowers you to experience the internet without boundaries. Unlock Digital Freedom Now The United Kingdom Welcomes CyberGhost…

View On WordPress
2 notes
·
View notes
Text
Keeping private information private is so hard if you have a weird name. Like how many people are named Johnathkins Hackensmithingflubber? Yeah bro the data brokers ain’t confusing you for your uncle, Johnathkins Hackensmithingflubber IV.
#data brokers can eat it#privacy#i have to pay for identity monitoring tools 🥲#johnathkins is a family name#no seriously my weird name has been used in every generation of my grandmother’s family
5 notes
·
View notes
Text
fucking grammarly’s using their ai model to make a text generator like you absolute fuckheads. fiction writers have been your bread and butter for YEARS and now that there’s a writers’ strike you’re gonna use our work to fuck them over like. new levels of cyberpunk dystopia on that one
#i’m gonna start using prowritingaid instead i think but like#idk i’m kinda pissed about it. like i read their terms and conditions and privacy policy. but there really wasn’t an alternative at the time#that worked and it IS a really important service like. i don’t mind paying for it. i don’t even mind my stuff being used to train a grammar#checker model bc that’s kinda collaborative yknow? like other people benefit even if they are making money. but using it to fuck over the#writers on the strike is fucking evil.#idk i liked ai a lot when it was like. doing things to make our lives better and not being used as a bludgeoning tool against creatives#i would like to return to a time when ai was not being used for this shit
5 notes
·
View notes
Text
That does not seem possible. Unless every computer in your house was running the new snapdragon thing:
"As you might imagine, all this snapshot recording comes at a hardware penalty. To use Recall, users will need to purchase one of the new "Copilot Plus PCs" powered by Qualcomm's Snapdragon X Elite chips, which include the necessary neural processing unit (NPU). There are also minimum storage requirements for running Recall, with a minimum of 256GB of hard drive space and 50GB of available space. The default allocation for Recall on a 256GB device is 25GB, which can store approximately three months of snapshots. Users can adjust the allocation in their PC settings, with old snapshots being deleted once the allocated storage is full.
I think you must mean Copilot installed itself. It's an AI thingy but it's not taking snapshots of everything you do, that is a special extra level of privacy invasion for people who have bought one of those new fancy "Copilot+" "AI" machines.
However! Copilot IS still an "ai" thingy and I don't want it on my computer either, and it seems like the apps linked above are pretty useful for increasing privacy! So. Check them out!
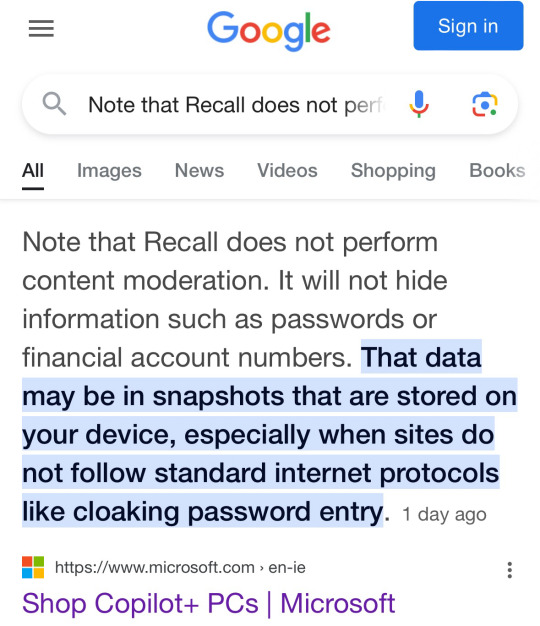
Literal definition of spyware:
Also From Microsoft’s own FAQ: "Note that Recall does not perform content moderation. It will not hide information such as passwords or financial account numbers. 🤡
#anti ai#tech shit#not exactly fandom but#privacy#so#fandom adjacent#don't panic folks this isn't happening on your machine#but these tools do seem useful :)
226K notes
·
View notes
Text
At the California Institute of the Arts, it all started with a videoconference between the registrar’s office and a nonprofit.
One of the nonprofit’s representatives had enabled an AI note-taking tool from Read AI. At the end of the meeting, it emailed a summary to all attendees, said Allan Chen, the institute’s chief technology officer. They could have a copy of the notes, if they wanted — they just needed to create their own account.
Next thing Chen knew, Read AI’s bot had popped up inabout a dozen of his meetings over a one-week span. It was in one-on-one check-ins. Project meetings. “Everything.”
The spread “was very aggressive,” recalled Chen, who also serves as vice president for institute technology. And it “took us by surprise.”
The scenariounderscores a growing challenge for colleges: Tech adoption and experimentation among students, faculty, and staff — especially as it pertains to AI — are outpacing institutions’ governance of these technologies and may even violate their data-privacy and security policies.
That has been the case with note-taking tools from companies including Read AI, Otter.ai, and Fireflies.ai.They can integrate with platforms like Zoom, Google Meet, and Microsoft Teamsto provide live transcriptions, meeting summaries, audio and video recordings, and other services.
Higher-ed interest in these products isn’t surprising.For those bogged down with virtual rendezvouses, a tool that can ingest long, winding conversations and spit outkey takeaways and action items is alluring. These services can also aid people with disabilities, including those who are deaf.
But the tools can quickly propagate unchecked across a university. They can auto-join any virtual meetings on a user’s calendar — even if that person is not in attendance. And that’s a concern, administrators say, if it means third-party productsthat an institution hasn’t reviewedmay be capturing and analyzing personal information, proprietary material, or confidential communications.
“What keeps me up at night is the ability for individual users to do things that are very powerful, but they don’t realize what they’re doing,” Chen said. “You may not realize you’re opening a can of worms.“
The Chronicle documented both individual and universitywide instances of this trend. At Tidewater Community College, in Virginia, Heather Brown, an instructional designer, unwittingly gave Otter.ai’s tool access to her calendar, and it joined a Faculty Senate meeting she didn’t end up attending. “One of our [associate vice presidents] reached out to inform me,” she wrote in a message. “I was mortified!”
24K notes
·
View notes
Text
Elevate Your Web Security Game with Sucuri
In our increasingly digital world, website security is not just optional; it’s essential. Now, imagine you’re on the way to an important meeting, and you get that dreaded email: “Your website has been hacked.” Nightmare, right? You need a security solution that stands guard 24/7 so you can focus on what truly matters. That solution is Sucuri. Sucuri: The All-In-One Security Platform Done with…

View On WordPress
2 notes
·
View notes
Text
There's no names tho? We don't even know if it's the teacher's official account so not only the kid's info is not revealed but possibly their own as well. Also sorry but I don't think a banana is the full solution here. I mean. The kid broke the teacher's glasses. To hell with glasses, he actually *punched* them, no matter the result that's still bad.
And the only consequence is the kid gets is an extra snack? Wtf? No "we talked with him about how to better regulate emotions" no "we will pay for the new glasses" not even "we told him that it's wrong and he understood he has to apologize to you."
I mean sure, we don't know the full story. Maybe the teacher is an ass and, idk, was being gross towards the kid's classmate and the kid just protected their friend and so parents rewarded him with an extra snack and probably a high five at home and some extra pocket money because the action was justified.
But we don't know that - from all we know from the context the kid punched the teacher. Generally a big no-no. And upon informing the parents? "We gave him an extra snack to calm him down and keep him from being antsy 😊💕"
Now don't get me wrong - I'm glad it's not "we grounded him for a month with no phone, tv or pc" or worse "dw after we're done with him he won't ever raise his eyes at you" (and I don't think the teacher wants this either tbh). It's great that the parents want to figure out the reason for the behavior! It's amazing actually!
Question is - will it be enough to make the kid realize "punching people is not the right way to express anger"? 'Cuz from the limited knowledge we have from the og post the kid received little to no correction. Sure he may turn out ok but rn that's a great way to put him on the path of "lashing out can be justified by hunger" (that werewolf pic is on point here lol) or even worse "lashing out is rewarded."
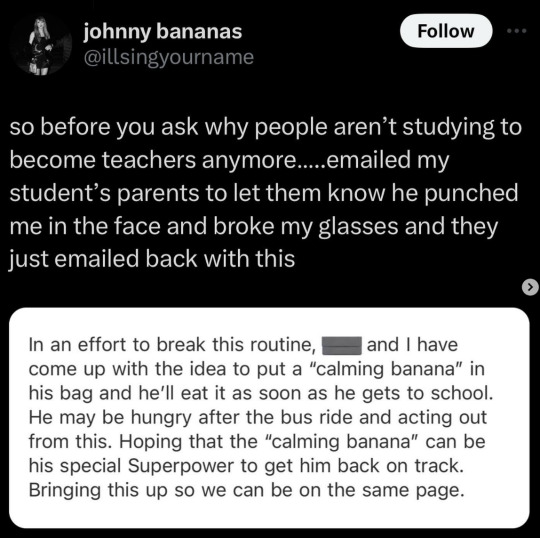
#we either didn't get the whole mail or the parents really did nothing except from deciding between each other on the snack#it will do nothing if the kid isn't told why is that#different story if they did talk with the kid and he admitted that hunger was a factor in the situation#but there's no such info given#I think the teacher has all the right to expect the parents to at least tell the kid to apologize and tell him why he should to do so#and I didn't get the impression the teacher wants the kid to be outright punished?#sure; could be; but I'd be super let down with such approach too#apology + paying for fixing the glasses (if the family can afford it) should be the main thing#extra snack is just a secondary tool to help in the future but I doubt it'll help at all if nothing else was done#sorry for the wall of text#also if it's the teacher's official account with a real name then yeah; that IS a privacy violation
43K notes
·
View notes