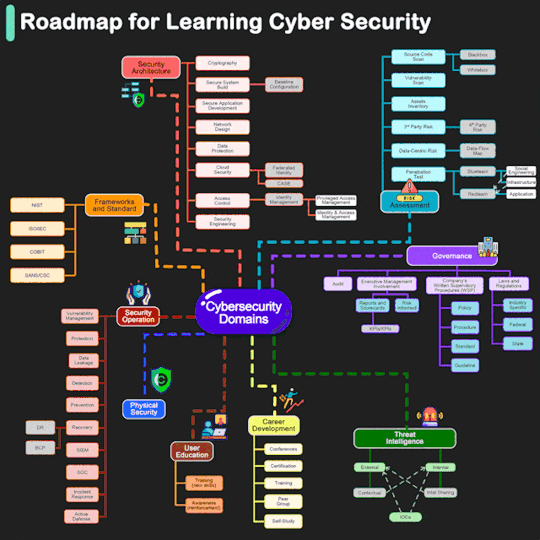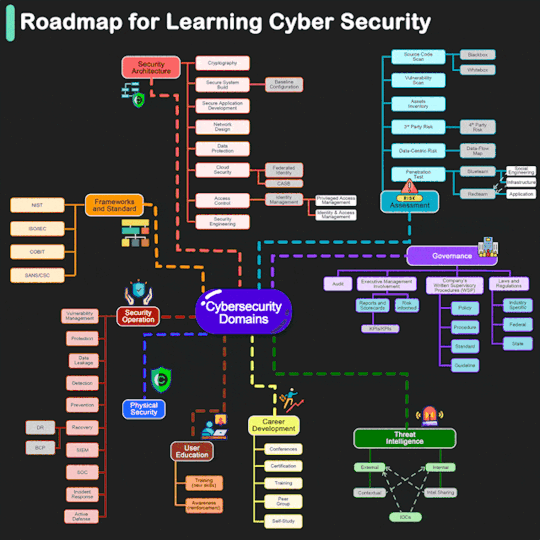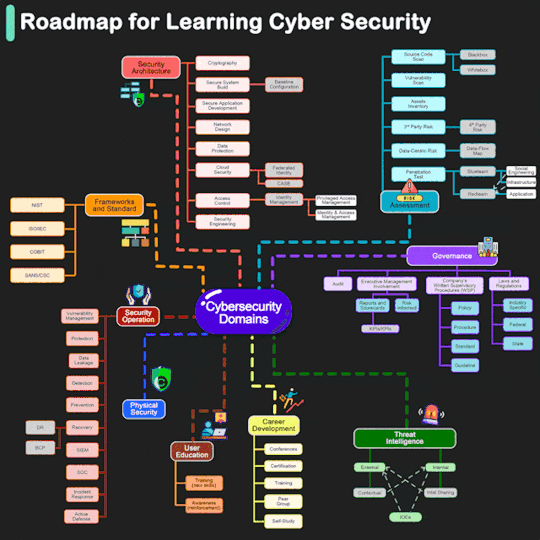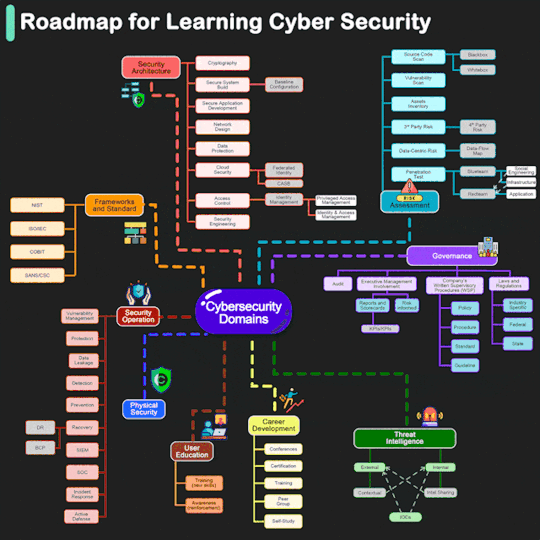
#learn cyber security
Explore tagged Tumblr posts
Text
0 notes
Text
Deepfake misuse & deepfake detection (before it’s too late) - CyberTalk
New Post has been published on https://thedigitalinsider.com/deepfake-misuse-deepfake-detection-before-its-too-late-cybertalk/
Deepfake misuse & deepfake detection (before it’s too late) - CyberTalk


Micki Boland is a global cyber security warrior and evangelist with Check Point’s Office of the CTO. Micki has over 20 years in ICT, cyber security, emerging technology, and innovation. Micki’s focus is helping customers, system integrators, and service providers reduce risk through the adoption of emerging cyber security technologies. Micki is an ISC2 CISSP and holds a Master of Science in Technology Commercialization from the University of Texas at Austin, and an MBA with a global security concentration from East Carolina University.
In this dynamic and insightful interview, Check Point expert Micki Boland discusses how deepfakes are evolving, why that matters for organizations, and how organizations can take action to protect themselves. Discover on-point analyses that could reshape your decisions, improving cyber security and business outcomes. Don’t miss this.
Can you explain how deepfake technology works?
Deepfakes involve simulated video, audio, and images to be delivered as content via online news, mobile applications, and through social media platforms. Deepfake videos are created with Generative Adversarial Networks (GAN), a type of Artificial Neural Network that uses Deep Learning to create synthetic content.
GANs sound cool, but technical. Could you break down how they operate?
GAN are a class of machine learning systems that have two neural network models; a generator and discriminator which game each other. Training data in the form of video, still images, and audio is fed to the generator, which then seeks to recreate it. The discriminator then tries to discern the training data from the recreated data produced by the generator.
The two artificial intelligence engines repeatedly game each other, getting iteratively better. The result is convincing, high quality synthetic video, images, or audio. A good example of GAN at work is NVIDIA GAN. Navigate to the website https://thispersondoesnotexist.com/ and you will see a composite image of a human face that was created by the NVIDIA GAN using faces on the internet. Refreshing the internet browser yields a new synthetic image of a human that does not exist.
What are some notable examples of deepfake tech’s misuse?
Most people are not even aware of deepfake technologies, although these have now been infamously utilized to conduct major financial fraud. Politicians have also used the technology against their political adversaries. Early in the war between Russia and Ukraine, Russia created and disseminated a deepfake video of Ukrainian President Volodymyr Zelenskyy advising Ukrainian soldiers to “lay down their arms” and surrender to Russia.
How was the crisis involving the Zelenskyy deepfake video managed?
The deepfake quality was poor and it was immediately identified as a deepfake video attributable to Russia. However, the technology is becoming so convincing and so real that soon it will be impossible for the regular human being to discern GenAI at work. And detection technologies, while have a tremendous amount of funding and support by big technology corporations, are lagging way behind.
What are some lesser-known uses of deepfake technology and what risks do they pose to organizations, if any?
Hollywood is using deepfake technologies in motion picture creation to recreate actor personas. One such example is Bruce Willis, who sold his persona to be used in movies without his acting due to his debilitating health issues. Voicefake technology (another type of deepfake) enabled an autistic college valedictorian to address her class at her graduation.
Yet, deepfakes pose a significant threat. Deepfakes are used to lure people to “click bait” for launching malware (bots, ransomware, malware), and to conduct financial fraud through CEO and CFO impersonation. More recently, deepfakes have been used by nation-state adversaries to infiltrate organizations via impersonation or fake jobs interviews over Zoom.
How are law enforcement agencies addressing the challenges posed by deepfake technology?
Europol has really been a leader in identifying GenAI and deepfake as a major issue. Europol supports the global law enforcement community in the Europol Innovation Lab, which aims to develop innovative solutions for EU Member States’ operational work. Already in Europe, there are laws against deepfake usage for non-consensual pornography and cyber criminal gangs’ use of deepfakes in financial fraud.
What should organizations consider when adopting Generative AI technologies, as these technologies have such incredible power and potential?
Every organization is seeking to adopt GenAI to help improve customer satisfaction, deliver new and innovative services, reduce administrative overhead and costs, scale rapidly, do more with less and do it more efficiently. In consideration of adopting GenAI, organizations should first understand the risks, rewards, and tradeoffs associated with adopting this technology. Additionally, organizations must be concerned with privacy and data protection, as well as potential copyright challenges.
What role do frameworks and guidelines, such as those from NIST and OWASP, play in the responsible adoption of AI technologies?
On January 26th, 2023, NIST released its forty-two page Artificial Intelligence Risk Management Framework (AI RMF 1.0) and AI Risk Management Playbook (NIST 2023). For any organization, this is a good place to start.
The primary goal of the NIST AI Risk Management Framework is to help organizations create AI-focused risk management programs, leading to the responsible development and adoption of AI platforms and systems.
The NIST AI Risk Management Framework will help any organization align organizational goals for and use cases for AI. Most importantly, this risk management framework is human centered. It includes social responsibility information, sustainability information and helps organizations closely focus on the potential or unintended consequences and impact of AI use.
Another immense help for organizations that wish to further understand risk associated with GenAI Large Language Model adoption is the OWASP Top 10 LLM Risks list. OWASP released version 1.1 on October 16th, 2023. Through this list, organizations can better understand risks such as inject and data poisoning. These risks are especially critical to know about when bringing an LLM in house.
As organizations adopt GenAI, they need a solid framework through which to assess, monitor, and identify GenAI-centric attacks. MITRE has recently introduced ATLAS, a robust framework developed specifically for artificial intelligence and aligned to the MITRE ATT&CK framework.
For more of Check Point expert Micki Boland’s insights into deepfakes, please see CyberTalk.org’s past coverage. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2023#adversaries#ai#AI platforms#amp#analyses#applications#Articles#artificial#Artificial Intelligence#audio#bots#browser#Business#CEO#CFO#Check Point#CISSP#college#Community#content#copyright#CTO#cyber#cyber attacks#cyber security#data#data poisoning#data protection#Deep Learning
2 notes
·
View notes
Text

Summer Internship Program 2024
For More Details Visit Our Website - internship.learnandbuild.in
#machine learning#programming#python#linux#data science#data scientist#frontend web development#backend web development#salesforce admin#salesforce development#cloud AI with AWS#Internet of things & AI#Cyber security#Mobile App Development using flutter#data structures & algorithms#java core#python programming#summer internship program#summer internship program 2024
2 notes
·
View notes
Text
i got accepted into college 😊
#im sad tho#because when i went to show my dad#i was really happy#but then he saw i was majoring in nursing#and got mad i decided not to do cyber security#like i like cybersecurity but i dont want it as a career#i just like learning abt it 😕#but whatever#anw yay#thots!
11 notes
·
View notes
Text
Coding and Scripting for Beginner Hackers
Learning to code and write scripts is a crucial skill for getting into ethical hacking and cybersecurity. Scripting allows you to automate repetitive tasks, develop your own custom tools, analyze data, and program everything from small hacking tools to machine learning models. Understanding and knowing how to code in different languages can be extremely useful when doing deep dives into malware…

View On WordPress
#Cyber Security#cybersecurity careers#Ethical Hacking#hacer certifications#hacking for beginners#hacking guide#hacking homelab#infosec#learn to code#learn to hack#Penetration Testing#Pentesting
3 notes
·
View notes
Text
#Computer Courses after 12th#Computer Courses after 10th#IT Courses after 12th#Digital Marketing#Graphics Designing Training#Cyber Security Training#Machine Learning Training
2 notes
·
View notes
Text
Top Skill development courses for Students to get Good Placement
Please like and follow this page to keep us motivated towards bringing useful content for you.
Now a days, Educated Unemployment is a big concern for a country like India. Considering the largest number of youth population in world, India has huge potential to be a developed nation in the next few years. But, it can be only possible if youth contribute in economy by learning skills which are in global demand. However, course structure in colleges are outdated and do not make students job…

View On WordPress
#Artificial Intelligence and Machine learning#Books for Artificial Intelligence and Machine Learning#Books for coding#Books for cyber security#Books for data science#Books for Digital Marketing#Books for Placement#Cloud computing#College Placement#Cyber Security#Data science and analytics#digital marketing#Graphic Design#high package#Programming and software development#Project Management#Sales and Business Development#Skill development#Web Development
4 notes
·
View notes
Text
Quickly realizing that I am probably going to need to buy a laptop but I barely have any money

#if anyone has noticed my lack of posting recently it’s because I am Working and Studying And I’m Tired.#I’ve been looking into cyber security courses cause school isn’t teaching me anything#but I’ve been doing this one online class for something else and I’ve been doing good on my own#so I’m like. maybe I should just teach myself..#but I would be doing it mostly on my downtime at work#and I can’t use the work laptop obviously#and when I get home the last thing I want to do is go back to sitting at my desk#plus I don’t really want to use a bunch of storage for virtual machines#I’m going to have to learn coding. screams and cries..
2 notes
·
View notes
Text
“ooh you hate cops but who are you gonna call when you get robbed?"
After I do my insurance claim I’m calling my best friend to bitch about it. That’s a better way to spend my time than cop.
"ooh you hate cops but who are you gonna call when you get robbed?" uhhhhh your moms house? a great tragedy has befallen me and i need to have sex immediately
#“Yjw you’re learning about legal system why don’t you have faith in the police system”#I’m learning about the legal system because I don’t trust police#seriously I’m taking a criminal law and procedure class because I don’t trust cops and the government#in kinder universe I would be getting a degree in writing#in this universe I’m studying law and cyber security
118K notes
·
View notes
Text
The Future of Real Estate in Jamaica: AI, Big Data, and Cybersecurity Shaping Tomorrow’s Market
#AI Algorithms#AI Real Estate Assistants#AI-Powered Chatbots#Artificial Intelligence#Automated Valuation Models#Big Data Analytics#Blockchain in Real Estate#Business Intelligence#cloud computing#Compliance Regulations#Cyber Attacks Prevention#Cybersecurity#Data encryption#Data Privacy#Data Security#data-driven decision making#Digital Property Listings#Digital Transactions#Digital Transformation#Fraud Prevention#Identity Verification#Internet of Things (IoT)#Machine Learning#Network Security#predictive analytics#Privacy Protection#Property Management Software#Property Technology#Real Estate Market Trends#real estate technology
0 notes
Text
Every Protocol Explained As FAST As Possible!
In this comprehensive video, we break down 100 essential networking protocols that every ethical hacker, cybersecurity enthusiast, and IT professional should know. From the foundational HTTP and HTTPS to advanced industrial protocols like MODBUS and DNP3, we've got you covered.
We'll explore:
Web Protocols: HTTP, HTTPS, FTP, SFTP Network Foundations: TCP/IP, UDP, ICMP, ARP Security Protocols: SSH, SSL/TLS, IPSec, Kerberos Email Protocols: SMTP, POP3, IMAP Remote Access: Telnet, RDP File Sharing: SMB/CIFS, NFS, AFP Routing Protocols: OSPF, RIP, BGP, EIGRP Wireless & IoT: MQTT, Z-Wave, Zigbee, Bluetooth, NFC Industrial Protocols: MODBUS, DNP3, BACnet Streaming Protocols: RTSP, RTP, SRTP Virtualization & Tunneling: GRE, MPLS, VXLAN, LISP And so much more!
Using simple explanations, relatable metaphors, and a touch of humor, we'll make these complex protocols easy to understand and remember.
Who is this video for?
Ethical Hackers & Penetration Testers Cybersecurity Students & Professionals Network Administrators & Engineers IT Enthusiasts & Tech Learners Why watch this video?
Enhance your cybersecurity knowledge Prepare for certifications and exams Stay updated with networking fundamentals Learn how different protocols can be vulnerable Get tips on securing your network infrastructure
#hacking#security#technology#free education#youtube#education#educate yourselves#tips and tricks#educate yourself#secure https#Every Protocol Explained#hacking tips#cybersecurity#data breach#cyber security#learn to hack#learn how to hack#learn how to code
0 notes
Text

Vivint is often considered one of the best security systems for a few reasons:
1. Smart Home Integration: Vivint systems integrate seamlessly with various smart home devices, making it easy to control everything from one app.
2. Professional Monitoring: They offer 24/7 professional monitoring, so you can be sure someone is always watching over your home.
3. Customizable Packages: Vivint allows you to customize your security package to fit your specific needs, whether it's cameras, sensors, or smart locks.
4. Advanced Technology: Their equipment is top-notch, featuring things like doorbell cameras with two-way talk and smart thermostats.
5. User-Friendly App: The Vivint app is highly rated for its ease of use, allowing you to monitor and control your system from anywhere.
These features make Vivint a strong contender for anyone looking to secure their home with advanced technology and reliable service.
#cyber security#entreprenuerlife#positive thoughts#self improvement#beautiful words#side hustle#thepersonalquotes#foryou#learning#personal finance#vivint#data security
0 notes
Text
The Implications of Quantum Supremacy on Encryption: A New Era in Cryptography

#Cybersecurity #ArtificialIntelligence #AI #MachineLearning #QuantumComputing #DataSecurity #FutureTech #DigitalSecurity
#cyber security#artificial intelligence#ai#machine learning#quantum computing#data security#future technology#digital security
0 notes
Text
B.Tech in Cyber Security and Forensics

In today's digitally-driven world, the importance of cybersecurity and forensics cannot be overstated. With the exponential growth of cyber threats and digital crimes, the demand for professionals adept at protecting and investigating digital systems has surged. In this blog I am going to discuss the course and future for this degree, also I am going to suggest the best engineering college in Dehradun that I was in. A Bachelor of Technology (B.Tech) in Cyber Security and Forensics emerges as a pivotal educational pathway, equipping students with the skills and knowledge to combat cybercrime and safeguard information.
What is B.Tech in Cyber Security and Forensics?
A B.Tech in Cyber Security and Forensics is an undergraduate program that combines the principles of computer science, information technology, and criminal justice. This multidisciplinary approach prepares students to understand the intricacies of digital security, investigate cyber incidents, and develop robust defense mechanisms against cyber threats.
Curriculum Overview
Program Overview at DBUU
Offered by the School of Engineering & Computing at Dev Bhoomi Uttarakhand University (DBUU), this course includes the fundamentals of security, encompassing data and information security. DBUU strives to equip students with superior technical skills, transforming today's students into tomorrow's competent professionals. The program covers key areas and electives such as cyber security and digital forensics.
Curriculum Highlights
The B.Tech in Cyber Security and Forensics program at DBUU provides a comprehensive foundation in both practical and theoretical aspects of cybersecurity. Key subjects include:
Introduction to Cyber Security: Fundamentals of protecting computer systems and networks from cyber attacks.
Digital Forensics: Techniques and tools for investigating digital crimes and retrieving evidence from electronic devices.
Cryptography: Methods of securing information through encryption and decryption.
Network Security: Protecting data during transmission over networks.
Ethical Hacking: Identifying vulnerabilities in systems by simulating cyber attacks.
Malware Analysis: Studying malicious software to understand its behavior and impact.
Cyber Law: Legal aspects related to cybercrimes and digital evidence.
The course helps students build a solid foundation in software security, information security, computer science, network security, computer forensics, penetration testing, system security measures, and vulnerability evaluation.
Why Choose B.Tech in Cyber Security and Forensics?
High Demand for Cybersecurity Professionals: With cyber attacks becoming more sophisticated, there is a growing need for skilled cybersecurity experts who can protect sensitive information and prevent data breaches.
Diverse Career Opportunities: Graduates can pursue various roles, including cybersecurity analyst, digital forensic investigator, ethical hacker, security consultant, and more. These positions are available across multiple industries, including finance, healthcare, government, and technology.
Lucrative Salaries: Cybersecurity professionals are among the highest-paid in the IT sector, reflecting the critical nature of their work and the expertise required.
Impactful Work: By defending against cyber threats and investigating cybercrimes, professionals in this field play a crucial role in maintaining the integrity and security of digital environments, making a significant impact on society.
The Growing Importance of Cyber Security and Forensics
As technology continues to evolve, so do the methods employed by cybercriminals. From ransomware attacks to data breaches, the frequency and complexity of cyber threats are escalating. This makes the role of cybersecurity and forensics experts indispensable. They not only prevent attacks but also provide critical insights and evidence to track down and prosecute cybercriminals.
Furthermore, the integration of the Internet of Things (IoT), artificial intelligence, and cloud computing into everyday life increases the attack surface for cyber threats. Consequently, the need for robust cybersecurity measures and skilled professionals to implement them is more critical than ever.
Conclusion
A B.Tech in Cyber Security and Forensics is an excellent choice for those passionate about technology and justice. This program offers a unique blend of skills that are in high demand, opening doors to diverse and rewarding career opportunities. As the digital landscape continues to grow, so does the importance of cybersecurity and forensics, making this a future-proof field with a significant impact on the safety and security of our digital world. Whether you're looking to defend against cyber threats or investigate digital crimes, a career in cybersecurity and forensics is both promising and fulfilling.
#cyber security#digital marketing#project managers#engineering#forensics#education and learning#degree#college#education#design#management
0 notes
Text
Business readiness for the impending deepfake superstorm - CyberTalk
New Post has been published on https://thedigitalinsider.com/business-readiness-for-the-impending-deepfake-superstorm-cybertalk/
Business readiness for the impending deepfake superstorm - CyberTalk


EXECUTIVE SUMMARY:
Deepfake technologies, as powered by artificial intelligence (AI), are rapidly proliferating, affecting businesses both large and small, worldwide. Between last year and this year, AI-driven deepfake attacks have increased by an astonishing 3,000%. Although deepfake technologies do have legitimate applications, the risk that they pose to businesses is non-trivial. The following serves as a brief overview of what to keep track of:
Business risk
1. Deepfakes impersonating executives. At this point, deepfakes can mimic the voices and appearances of high-ranking individuals so effectively that cyber criminals are manipulating financial transactions, ensuring authorization of payments, and weaponizing videos to gain access to information. The financial losses caused by deepfakes can prove substantial. Think $25 million or more, as exemplified in this incident. Millions of dollars lost can affect the company’s gross revenue, jeopardizing a company’s future.
What’s more is that impersonation of an executive, even if it only occurs once, can send stakeholders into a tailspin as they wonder who to trust, when to trust them and whether or not to only trust people in-person. This can disrupt the fluidity of day-to-day operations, causing internal instability and turmoil.
2. Reputational damage. If deepfakes are used publicly against an organization – for example, if a CEO is shown to be on stage, sharing a falsehood – the business’s image may rapidly deteriorate.
The situation could unravel further in the event that a high-level individual is depicted as participating in unethical or illegal behavior. Rebuilding trust and credibility after such incidents can be challenging and time-consuming (or all-out impossible).
3. Erosion of public trust. Deepfakes can potentially deceive customers, clients and partners.
For example, a cyber criminal could deepfake a customer service representative, and could pretend to assist a client, stealing personal details in the process. Or, a partner organization could be misled by deepfake impersonators on a video call.
These types of events can erode trust, lead to lost business and result in public reputational harm. When clients or partners report deepfake issues, news headlines emerge quickly, and prospective clients or partners are liable to back out of otherwise value-add deals.
Credit risk warning
Cyber security experts aren’t the only people who are concerned about the impending “deepfake superstorm” that threatens to imperil businesses. In May, credit ratings firm Moody’s warned that deepfakes could pose credit risks. The corresponding report points to a series of deepfake scams that have impacted the financial sector.
These scams have frequently involved fake video calls. Preventing deepfake scams – as through stronger cyber security and related measures – can potentially present businesses with greater opportunities to ensure good credit, acquire new capital and obtain lower insurance rates, among other things.
Cyber security solutions
Deepfake detection tools can help. Such tools typically use a variety of deepfake identification techniques to prevent and mitigate the threats. These include deep learning algorithms, machine learning models and more.
Check Point Research (CPR) actively investigates emerging threats, including deepfakes, and the research informs Check Point’s robust security solutions, which are designed to combat deepfake-related risks.
To see how a Check Point expert views and prevents deepfakes, please see CyberTalk.org’s past coverage. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#000#ai#Algorithms#analyses#applications#Articles#artificial#Artificial Intelligence#Behavior#Business#CEO#Check Point#Check Point Research#customer service#cyber#cyber criminals#cyber security#cyber security solutions#Cyber Threats#cybersecurity#deals#Deep Learning#deepfake#deepfake detection#deepfake readiness#deepfakes#details#detection#Events#executives
0 notes