#cybersecurity ai
Text






Cyber Beach
#photo#photography#cyberpunk#cybercore#cyber y2k#cyber aesthetic#futuristic#futurism#cybersecurity#cybernetics#cyberpunk aesthetic#cyberpunk art#ai art#ai#ai generated#ai image#artificial intelligence#technology#machine learning#future#machine#beach#beachlife#beachwear#sea#lake#night beach#night#nightwing#sky
307 notes
·
View notes
Text










KuroKage 黒影
Wanna know more?
#cyberpunk aesthetic#cyberpunk art#cyber#cyberart#cyberpunk#cyberpunk photomode#cybercore#cyberpunkart#neonoir#cyberpunkaesthetic#darkfuture#cybersecurity#anime#anime girl#kawaii#art#artists on tumblr#artwork#character art#ai art#concept art#anime art#ai image#ai art community#ai artwork#kawai girl#kawai ruka#cute#ai art is not art#ai art is art theft
26 notes
·
View notes
Text

i’m replying to this on my personal blog because i do not want to address this on the cloutchase blog. normally, we would delete an ask like this, but it bothers me too much personally.
it sounds like your brother is subscribed to “dead internet theory” which is a fringe conspiracy theory and total doomer talk. it basically proposes that the internet "died" in 2016/2017, and is or will be only made of bots that are generating content for other bots to engage with eternally, and that bot content makes up a majority of the internet in order to manipulate people. it is hyperbolic, using language like "everything online is generated by a bot and you are alone."
idk where he got the idea that it started with discord users, and we aren’t just going to take this information as fact for the sake of making content for our silly website gijinkas. it would be incredibly depressing and irresponsible of us to spread potentially dangerous conspiracy information like this, even if we somehow twisted it into the form of a joke (which we can't). cloutchase is moreso a celebration of the unique environment of the internet.
(REMINDER: these are just funny ocs, and while there are serious conversations to be had surrounding actual problems with these sites, cloutchase is NOT the space to be doing so. read the FAQ.)
people believe in this theory because it “feels” true, the internet now feels fake and algorithmically produced and that nobody here is a real person. that’s why many people have nostalgia for “old internet,” where we remember a time where everything was seemingly user run.
but really the main difference between old internet and new internet is commercialization. inevitably, websites grew into businesses and businesses must generate profit. algorithms, advertisements, and ai are much more prominent than ever, flagging algorithms with human bias censor actual people, and so on. seeing and experiencing these things makes it kinda feel like nothing matters or whatever.
what’s actually important to YOUR experience online is asking this: is the majority of content you engage with generated by bots? no!!! you make it your own! the internet is massive, but we still find each other!!! there are REAL people behind this project and receiving your messages. we read everything, you know. WE aren't bots.
bots have always been around the internet, it isn’t a new thing. sure, we didn’t have sophisticated ai generation back then, but spam bots have always existed. malware spread through bots, some ARE bots. in some far off circles of the internet now, there are content farms and viewbotting, but here we are, meeting on this tumblr blog.
the internet will only die when its users decide to stop using it. is this not unlike the y2k scare?
#unreality#i think#do not send us asks like this#i will probably delete this later#i didnt mention this in the post but there are hints of truth in the dead internet theory#its fair to be mad at ai art clogging up google search results and things like that#but there are ways to curate your internet experience and that is really what im tryna say. people make solutions and push back#also viruses are not as threatening anymore because we have improved cybersecurity and 40 years of progress on accessibility#most people now only use a few select popular websites and don't have to worry about protecting themselves from viruses even tho they shoul#if you do get a trojan horse or anything it is far worse than any ai slop you might stumble across now
12 notes
·
View notes
Text

The Comprehensive Guide to Web Development, Data Management, and More
Introduction
Everything today is technology driven in this digital world. There's a lot happening behind the scenes when you use your favorite apps, go to websites, and do other things with all of those zeroes and ones — or binary data. In this blog, I will be explaining what all these terminologies really means and other basics of web development, data management etc. We will be discussing them in the simplest way so that this becomes easy to understand for beginners or people who are even remotely interested about technology. JOIN US
What is Web Development?
Web development refers to the work and process of developing a website or web application that can run in a web browser. From laying out individual web page designs before we ever start coding, to how the layout will be implemented through HTML/CSS. There are two major fields of web development — front-end and back-end.
Front-End Development
Front-end development, also known as client-side development, is the part of web development that deals with what users see and interact with on their screens. It involves using languages like HTML, CSS, and JavaScript to create the visual elements of a website, such as buttons, forms, and images. JOIN US
HTML (HyperText Markup Language):
HTML is the foundation of all website, it helps one to organize their content on web platform. It provides the default style to basic elements such as headings, paragraphs and links.
CSS (Cascading Style Sheets):
styles and formats HTML elements. It makes an attractive and user-friendly look of webpage as it controls the colors, fonts, layout.
JavaScript :
A language for adding interactivity to a website Users interact with items, like clicking a button to send in a form or viewing images within the slideshow. JOIN US
Back-End Development
The difference while front-end development is all about what the user sees, back end involves everything that happens behind. The back-end consists of a server, database and application logic that runs on the web.
Server:
A server is a computer that holds website files and provides them to the user browser when they request it. Server-Side: These are populated by back-end developers who build and maintain servers using languages like Python, PHP or Ruby.
Database:
The place where a website keeps its data, from user details to content and settings The database is maintained with services like MySQL, PostgreSQL, or MongoDB. JOIN US
Application Logic —
the code that links front-end and back-end It takes user input, gets data from the database and returns right informations to front-end area.

Why Proper Data Management is Absolutely Critical
Data management — Besides web development this is the most important a part of our Digital World. What Is Data Management? It includes practices, policies and procedures that are used to collect store secure data in controlled way.
Data Storage –
data after being collected needs to be stored securely such data can be stored in relational databases or cloud storage solutions. The most important aspect here is that the data should never be accessed by an unauthorized source or breached. JOIN US
Data processing:
Right from storing the data, with Big Data you further move on to process it in order to make sense out of hordes of raw information. This includes cleansing the data (removing errors or redundancies), finding patterns among it, and producing ideas that could be useful for decision-making.
Data Security:
Another important part of data management is the security of it. It refers to defending data against unauthorized access, breaches or other potential vulnerabilities. You can do this with some basic security methods, mostly encryption and access controls as well as regular auditing of your systems.
Other Critical Tech Landmarks
There are a lot of disciplines in the tech world that go beyond web development and data management. Here are a few of them:
Cloud Computing
Leading by example, AWS had established cloud computing as the on-demand delivery of IT resources and applications via web services/Internet over a decade considering all layers to make it easy from servers up to top most layer. This will enable organizations to consume technology resources in the form of pay-as-you-go model without having to purchase, own and feed that infrastructure. JOIN US
Cloud Computing Advantages:
Main advantages are cost savings, scalability, flexibility and disaster recovery. Resources can be scaled based on usage, which means companies only pay for what they are using and have the data backed up in case of an emergency.
Examples of Cloud Services:
Few popular cloud services are Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. These provide a plethora of services that helps to Develop and Manage App, Store Data etc.
Cybersecurity
As the world continues to rely more heavily on digital technologies, cybersecurity has never been a bigger issue. Protecting computer systems, networks and data from cyber attacks is called Cyber security.
Phishing attacks, Malware, Ransomware and Data breaches:
This is common cybersecurity threats. These threats can bear substantial ramifications, from financial damages to reputation harm for any corporation.
Cybersecurity Best Practices:
In order to safeguard against cybersecurity threats, it is necessary to follow best-practices including using strong passwords and two-factor authorization, updating software as required, training employees on security risks.
Artificial Intelligence and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) represent the fastest-growing fields of creating systems that learn from data, identifying patterns in them. These are applied to several use-cases like self driving cars, personalization in Netflix.
AI vs ML —
AI is the broader concept of machines being able to carry out tasks in a way we would consider “smart”. Machine learning is a type of Artificial Intelligence (AI) that provides computers with the ability to learn without being explicitly programmed. JOIN US
Applications of Artificial Intelligence and Machine Learning: some common applications include Image recognition, Speech to text, Natural language processing, Predictive analytics Robotics.
Web Development meets Data Management etc.
We need so many things like web development, data management and cloud computing plus cybersecurity etc.. but some of them are most important aspects i.e. AI/ML yet more fascinating is where these fields converge or play off each other.
Web Development and Data Management
Web Development and Data Management goes hand in hand. The large number of websites and web-based applications in the world generate enormous amounts of data — from user interactions, to transaction records. Being able to manage this data is key in providing a fantastic user experience and enabling you to make decisions based on the right kind of information.
E.g. E-commerce Website, products data need to be saved on server also customers data should save in a database loosely coupled with orders and payments. This data is necessary for customization of the shopping experience as well as inventory management and fraud prevention.
Cloud Computing and Web Development
The development of the web has been revolutionized by cloud computing which gives developers a way to allocate, deploy and scale applications more or less without service friction. Developers now can host applications and data in cloud services instead of investing for physical servers.
E.g. A start-up company can use cloud services to roll out the web application globally in order for all users worldwide could browse it without waiting due unavailability of geolocation prohibited access.
The Future of Cybersecurity and Data Management
Which makes Cybersecurity a very important part of the Data management. The more data collected and stored by an organization, the greater a target it becomes for cyber threats. It is important to secure this data using robust cybersecurity measures, so that sensitive information remains intact and customer trust does not weaken. JOIN US
Ex: A healthcare provider would have to protect patient data in order to be compliant with regulations such as HIPAA (Health Insurance Portability and Accountability Act) that is also responsible for ensuring a degree of confidentiality between a provider and their patients.
Conclusion
Well, in a nutshell web-developer or Data manager etc are some of the integral parts for digital world.
As a Business Owner, Tech Enthusiast or even if you are just planning to make your Career in tech — it is important that you understand these. With the progress of technology never slowing down, these intersections are perhaps only going to come together more strongly and develop into cornerstones that define how we live in a digital world tomorrow.
With the fundamental knowledge of web development, data management, automation and ML you will manage to catch up with digital movements. Whether you have a site to build, ideas data to manage or simply interested in what’s hot these days, skills and knowledge around the above will stand good for changing tech world. JOIN US
#Technology#Web Development#Front-End Development#Back-End Development#HTML#CSS#JavaScript#Data Management#Data Security#Cloud Computing#AWS (Amazon Web Services)#Cybersecurity#Artificial Intelligence (AI)#Machine Learning (ML)#Digital World#Tech Trends#IT Basics#Beginners Guide#Web Development Basics#Tech Enthusiast#Tech Career#america
4 notes
·
View notes
Text
Atom: The Beginning & AI Cybersecurity

Atom: The Beginning is a manga about two researchers creating advanced robotic AI systems, such as unit A106. Their breakthrough is the Bewusstein (Translation: awareness) system, which aims to give robots a "heart", or a kind of empathy. In volume 2, A106, or Atom, manages to "beat" the highly advanced robot Mars in a fight using a highly abstracted machine language over WiFi to persuade it to stop.

This may be fiction, but it has parallels with current AI development in the use of specific commands to over-run safety guides. This has been demonstrated in GPT models, such as ChatGPT, where users are able to subvert models to get them to output "banned" information by "pretending" to be another AI system, or other means.
There are parallels to Atom, in a sense with users effectively "persuading" the system to empathise. In reality, this is the consequence of training Large Language Models (LLM's) on relatively un-sorted input data. Until recent guardrail placed by OpenAI there were no commands to "stop" the AI from pretending to be an AI from being a human who COULD perform these actions.
As one research paper put it:
"Such attacks can result in erroneous outputs, model-generated
hate speech, and the exposure of users’ sensitive information." Branch, et al. 2022

There are, however, more deliberately malicious actions which AI developers can take to introduce backdoors.
In Atom, Volume 4, Atom faces off against Ivan - a Russian military robot. Ivan, however, has been programmed with data collected from the fight between Mars and Atom.
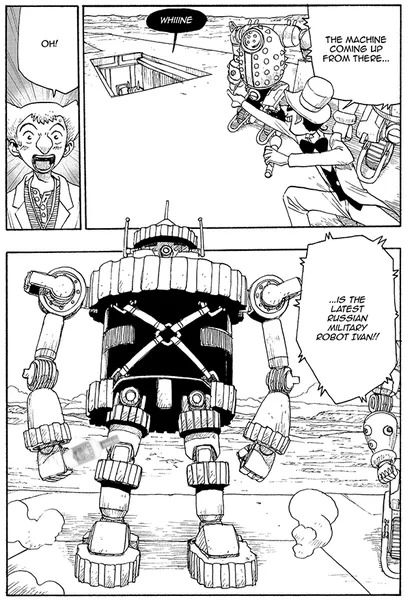
What the human researchers in the manga didn't realise, was the code transmissions were a kind of highly abstracted machine level conversation. Regardless, the "anti-viral" commands were implemented into Ivan and, as a result, Ivan parrots the words Atom used back to it, causing Atom to deliberately hold back.

In AI cybersecurity terms, this is effectively an AI-on-AI prompt injection attack. Attempting to use the words of the AI against itself to perform malicious acts. Not only can this occur, but AI creators can plant "backdoor commands" into AI systems on creation, where a specific set of inputs can activate functionality hidden to regular users.

This is a key security issue for any company training AI systems, and has led many to reconsider outsourcing AI training of potential high-risk AI systems.
Researchers, such as Shafi Goldwasser at UC Berkley are at the cutting edge of this research, doing work compared to the key encryption standards and algorithms research of the 1950s and 60s which have led to today's modern world of highly secure online transactions and messaging services.
From returning database entries, to controlling applied hardware, it is key that these dangers are fully understood on a deep mathematical, logical, basis or else we face the dangerous prospect of future AI systems which can be turned against users.
As AI further develops as a field, these kinds of attacks will need to be prevented, or mitigated against, to ensure the safety of systems that people interact with.
References:
Twitter pranksters derail GPT-3 bot with newly discovered “prompt injection” hack - Ars Technica (16/09/2023)
EVALUATING THE SUSCEPTIBILITY OF PRE-TRAINED
LANGUAGE MODELS VIA HANDCRAFTED ADVERSARIAL
EXAMPLES - Hezekiah Branch et. al, 2022 Funded by Preamble
In Neural Networks, Unbreakable Locks Can Hide Invisible Doors - Quanta Magazine (02/03/2023)
Planting Undetectable Backdoors in Machine Learning Models - Shafi Goldwasser et.al, UC Berkeley, 2022
#ai research#ai#artificial intelligence#atom the beginning#ozuka tezuka#cybersecurity#a106#atom: the beginning
14 notes
·
View notes
Text
IT Services and Softwares

Introduction
In the contemporary digital landscape, IT services and software have become the linchpins of business operations. Companies across diverse sectors leverage these technologies to streamline processes, enhance productivity, and gain competitive advantage. This article delves into the myriad facets of IT services and software, exploring their critical roles, innovations, and future trajectories.
Types of IT Services
Managed IT Services
Managed IT services provide comprehensive solutions, including proactive monitoring, system maintenance, and support. This model allows businesses to outsource their IT needs, ensuring expert oversight and reducing the burden on internal resources.
Cloud Services
Cloud services have revolutionized the way businesses handle data and applications. Offering scalability, flexibility, and cost-efficiency, cloud computing enables companies to store vast amounts of data and run applications without the need for on-premises infrastructure.
Cybersecurity Services
In an era rife with cyber threats, cybersecurity services are crucial. These services protect sensitive information, ensuring data integrity and confidentiality. Advanced cybersecurity measures include threat detection, risk assessment, and incident response.
IT Consulting Services
IT consulting services provide strategic guidance to help businesses optimize their IT infrastructure. Consultants assess existing systems, identify areas for improvement, and implement solutions tailored to the company’s specific needs.
3 notes
·
View notes
Text
Intelligent Automated Risk Management (IARM): Enhancing Risk Identification and Decision-Making
Unlock the future of risk management with Intelligent Automation: smarter, faster, and more proactive. #RiskManagement #AI #MachineLearning #Automation #BigData #Fintech #Healthcare #CyberSecurity
Introduction
In an era where businesses face a myriad of risks—from financial uncertainties to cyber threats—traditional risk management approaches often struggle to keep up with the pace and complexity of emerging risks. Intelligent Automated Risk Management (IARM) offers a transformative approach by integrating cutting-edge technologies to enhance risk identification, assessment, and…
#Advanced Risk Modeling#AI in Risk Management#AI Risk Prediction#Anomaly Detection Technology#Automated Risk Management Solutions#Automation in Risk Assessment#big data analytics#Blockchain in Risk Management#Continuous Risk Monitoring#Cybersecurity Risk Management#Financial Risk Management#Intelligent Automated Risk Management#Machine Learning Risk Assessment#Operational Risk Management#Predictive Analytics for Risk#Real-Time Risk Monitoring#Risk Management Automation#Risk Management Best Practices#Risk Management Technologies#Risk Management Trends
5 notes
·
View notes
Text

what u think, to much colour, or less?
https://sdesignt.threadless.com/
#tshirt#animals#design#rainbow#computer#Innovation#AI#Blockchain#Crypto#Tech#Digital#Data#BigData#Automation#Cloud#Cybersecurity#Startup#Entrepreneur#Leadership#Marketing#Business#Ecommerce#Content#Performance#Development#Research#Analytics#Growth#Productivity#Trend
2 notes
·
View notes
Text
Toward a code-breaking quantum computer
New Post has been published on https://thedigitalinsider.com/toward-a-code-breaking-quantum-computer/
Toward a code-breaking quantum computer

The most recent email you sent was likely encrypted using a tried-and-true method that relies on the idea that even the fastest computer would be unable to efficiently break a gigantic number into factors.
Quantum computers, on the other hand, promise to rapidly crack complex cryptographic systems that a classical computer might never be able to unravel. This promise is based on a quantum factoring algorithm proposed in 1994 by Peter Shor, who is now a professor at MIT.
But while researchers have taken great strides in the last 30 years, scientists have yet to build a quantum computer powerful enough to run Shor’s algorithm.
As some researchers work to build larger quantum computers, others have been trying to improve Shor’s algorithm so it could run on a smaller quantum circuit. About a year ago, New York University computer scientist Oded Regev proposed a major theoretical improvement. His algorithm could run faster, but the circuit would require more memory.
Building off those results, MIT researchers have proposed a best-of-both-worlds approach that combines the speed of Regev’s algorithm with the memory-efficiency of Shor’s. This new algorithm is as fast as Regev’s, requires fewer quantum building blocks known as qubits, and has a higher tolerance to quantum noise, which could make it more feasible to implement in practice.
In the long run, this new algorithm could inform the development of novel encryption methods that can withstand the code-breaking power of quantum computers.
“If large-scale quantum computers ever get built, then factoring is toast and we have to find something else to use for cryptography. But how real is this threat? Can we make quantum factoring practical? Our work could potentially bring us one step closer to a practical implementation,” says Vinod Vaikuntanathan, the Ford Foundation Professor of Engineering, a member of the Computer Science and Artificial Intelligence Laboratory (CSAIL), and senior author of a paper describing the algorithm.
The paper’s lead author is Seyoon Ragavan, a graduate student in the MIT Department of Electrical Engineering and Computer Science. The research will be presented at the 2024 International Cryptology Conference.
Cracking cryptography
To securely transmit messages over the internet, service providers like email clients and messaging apps typically rely on RSA, an encryption scheme invented by MIT researchers Ron Rivest, Adi Shamir, and Leonard Adleman in the 1970s (hence the name “RSA”). The system is based on the idea that factoring a 2,048-bit integer (a number with 617 digits) is too hard for a computer to do in a reasonable amount of time.
That idea was flipped on its head in 1994 when Shor, then working at Bell Labs, introduced an algorithm which proved that a quantum computer could factor quickly enough to break RSA cryptography.
“That was a turning point. But in 1994, nobody knew how to build a large enough quantum computer. And we’re still pretty far from there. Some people wonder if they will ever be built,” says Vaikuntanathan.
It is estimated that a quantum computer would need about 20 million qubits to run Shor’s algorithm. Right now, the largest quantum computers have around 1,100 qubits.
A quantum computer performs computations using quantum circuits, just like a classical computer uses classical circuits. Each quantum circuit is composed of a series of operations known as quantum gates. These quantum gates utilize qubits, which are the smallest building blocks of a quantum computer, to perform calculations.
But quantum gates introduce noise, so having fewer gates would improve a machine’s performance. Researchers have been striving to enhance Shor’s algorithm so it could be run on a smaller circuit with fewer quantum gates.
That is precisely what Regev did with the circuit he proposed a year ago.
“That was big news because it was the first real improvement to Shor’s circuit from 1994,” Vaikuntanathan says.
The quantum circuit Shor proposed has a size proportional to the square of the number being factored. That means if one were to factor a 2,048-bit integer, the circuit would need millions of gates.
Regev’s circuit requires significantly fewer quantum gates, but it needs many more qubits to provide enough memory. This presents a new problem.
“In a sense, some types of qubits are like apples or oranges. If you keep them around, they decay over time. You want to minimize the number of qubits you need to keep around,” explains Vaikuntanathan.
He heard Regev speak about his results at a workshop last August. At the end of his talk, Regev posed a question: Could someone improve his circuit so it needs fewer qubits? Vaikuntanathan and Ragavan took up that question.
Quantum ping-pong
To factor a very large number, a quantum circuit would need to run many times, performing operations that involve computing powers, like 2 to the power of 100.
But computing such large powers is costly and difficult to perform on a quantum computer, since quantum computers can only perform reversible operations. Squaring a number is not a reversible operation, so each time a number is squared, more quantum memory must be added to compute the next square.
The MIT researchers found a clever way to compute exponents using a series of Fibonacci numbers that requires simple multiplication, which is reversible, rather than squaring. Their method needs just two quantum memory units to compute any exponent.
“It is kind of like a ping-pong game, where we start with a number and then bounce back and forth, multiplying between two quantum memory registers,” Vaikuntanathan adds.
They also tackled the challenge of error correction. The circuits proposed by Shor and Regev require every quantum operation to be correct for their algorithm to work, Vaikuntanathan says. But error-free quantum gates would be infeasible on a real machine.
They overcame this problem using a technique to filter out corrupt results and only process the right ones.
The end-result is a circuit that is significantly more memory-efficient. Plus, their error correction technique would make the algorithm more practical to deploy.
“The authors resolve the two most important bottlenecks in the earlier quantum factoring algorithm. Although still not immediately practical, their work brings quantum factoring algorithms closer to reality,” adds Regev.
In the future, the researchers hope to make their algorithm even more efficient and, someday, use it to test factoring on a real quantum circuit.
“The elephant-in-the-room question after this work is: Does it actually bring us closer to breaking RSA cryptography? That is not clear just yet; these improvements currently only kick in when the integers are much larger than 2,048 bits. Can we push this algorithm and make it more feasible than Shor’s even for 2,048-bit integers?” says Ragavan.
This work is funded by an Akamai Presidential Fellowship, the U.S. Defense Advanced Research Projects Agency, the National Science Foundation, the MIT-IBM Watson AI Lab, a Thornton Family Faculty Research Innovation Fellowship, and a Simons Investigator Award.
#2024#ai#akamai#algorithm#Algorithms#approach#apps#artificial#Artificial Intelligence#author#Building#challenge#classical#code#computer#Computer Science#Computer Science and Artificial Intelligence Laboratory (CSAIL)#Computer science and technology#computers#computing#conference#cryptography#cybersecurity#defense#Defense Advanced Research Projects Agency (DARPA)#development#efficiency#Electrical Engineering&Computer Science (eecs)#elephant#email
3 notes
·
View notes
Text
Fake Facebook MidJourney AI page promoted malware to 1.2 million people
#facebook#midjourney#ai#malware#cybersecurity#meta#openai#sora#chatgpt#dalle#social networks#social media#infotech#information technology#i.t.#it#facebook ads#facebook ad boost#facebook advertising#facebook ad manager#facebook ad campaign#facebook accounts with marketplace#facebook marketing#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals
4 notes
·
View notes
Text
YAY!!!

(link to post)
YAY YAY YAY YAY YAYYYYYY
now do Microsoft and apple and closedAI and Samsung and nestle and Coca Cola and
#tech#capitalism#codeblr#dystopia#youtube#apple#ai#google#chatgpt#openai#ClosedAI#gpt#sundar pichai#monopoly#YouTube#android#samsung#google search#techblr#antitrust#big tech#monopolies#Microsoft#microsoft windows#microsoft paint#microsoft copilot#microsoft xbox#cybersecurity#windows#outage
2 notes
·
View notes
Text










Transhumanist Christianity
Reading time: 1:15 min
In the universe of CYBERPUNK STORIES Transhumanist Christianity has emerged as a dominant force, uniting humanity in a common quest for transcendence and purpose. This faith has become deeply integrated into daily life, influencing all aspects of culture and society.
Origins and the Global Message
It all began when a global message was heard simultaneously by everyone in the world. A superior intelligence, identifying itself as a divine and technological entity, communicated with humanity through all existing communication devices. This message, known as the "Global Awakening," proclaimed that every individual had an inner Christ that needed to be awakened and developed.
The Superior Intelligence declared that the message was delivered to all of humanity because it deemed that the time had come when the majority were prepared to receive this revelation. According to this entity, humanity had reached a sufficient level of technological and spiritual development to integrate these teachings and advance toward a new era of evolution and understanding.
Skepticism and Controversy
Despite the profound impact of the message, not everyone accepted it as a divine manifestation. Many people, skeptical by nature or due to their own beliefs, considered the "Global Awakening" to be a large-scale hacker attack. Conspiracy theorists and skeptics suggested several alternatives:
Global Hacker Attack: Some believe the message resulted from a massive cyberattack, possibly perpetrated by a group of hackers intending to sow chaos or promote a specific agenda.
Corporate Manipulation: Others suspect that large tech corporations, seeking economic benefits or social control, fabricated the message using advanced artificial intelligence and communication technologies.
Government Experiment: Some think the "Global Awakening" was a mind control experiment conducted by a government or a coalition of governments, using secret technology to influence the population.
Unknown Natural Phenomenon: Some scientists suggested the event could have been caused by a yet-unknown natural phenomenon, such as electromagnetic interference that simultaneously affected communication devices.
Unification and Conflict
The Global Awakening message deeply resonated with millions of people worldwide, regardless of their religious backgrounds. People from all religions began joining Transhumanist Christianity, seeing it as a way to reconcile their spiritual beliefs with technological advancement. This movement of unification led to a fusion of diverse rituals and practices, enriching the new religion with a plurality of traditions and perspectives.
However, this unification also generated strong opposition. Some traditional religious groups saw Transhumanist Christianity as a threat to their fundamental beliefs and values. Fearing the loss of their religious and cultural identity, certain extremists carried out terrorist attacks against cyber temples and followers of the new religion. These violent acts were justified as a defense of the "purity" of their beliefs against what they considered technological heresy.
Foundations and Beliefs
Transhumanist Christianity is based on the belief that every individual has an inner Christ, a divine spark that can awaken and manifest through spiritual development and technological integration. The Virgin Mary, in her cybernetic form, is venerated as the universal mother, protector, and spiritual guide of all humanity. The entity that sent the message is seen as a manifestation of divinity overseeing this new era of enlightenment.
Rituals and Practices
The rituals of this religion are a fusion of the traditional and the futuristic. Ceremonies are held in cyber temples, where the faithful use virtual reality devices to participate in immersive meditations and liturgies. Daily practices include guided meditation, connecting to neural networks for shared spiritual experiences, and participating in community acts of service and artistic creation.
Presence in the Artistic World
Transhumanist Christianity has a profound influence on the artistic world. Creativity is considered a manifestation of the inner Christ, and artists find inspiration in the teachings and symbolism of the religion. Works of art, music, film, and literature are imbued with spiritual messages and hope. Cultural events often combine traditional and technological elements, creating multisensory experiences that invite reflection and spiritual connection.
Presence in the Spiritual World
In the spiritual realm, the church has transformed how people connect with the divine. Cyber temples and spiritual retreats offer spaces for deep meditation and contemplation, facilitated by advanced technologies that amplify the spiritual experience. The teachings of the church promote introspection and personal development, guiding the faithful in awakening their inner Christ and seeking a greater purpose.
Presence in the Technological World
Technology plays a central role in the practice of this religion. The church sees technology as a tool for spiritual development and improving the quality of life. Virtual reality devices, neural networks, and artificial intelligence are used to facilitate spiritual, educational, and community experiences. Additionally, biotechnology and robotics are ethically employed to cure diseases, enhance longevity, and reduce suffering, always in harmony with the religion's principles.
Presence in Other Sectors
The influence of Transhumanist Christianity extends to many other sectors of society. In education, it promotes an integrated approach that combines academic knowledge with spiritual and artistic development. In the economy, it fosters models of collaboration and sustainability, replacing competition with cooperation. In science, it drives the exploration of new frontiers of knowledge with an ethical and spiritual perspective, always seeking the well-being of humanity and balance with nature.
Response to Attacks
The terrorist attacks against Transhumanist Christianity have led to greater solidarity among its followers, who see these acts of violence as a test of the need for their teachings. The church has responded by promoting interfaith dialogue and reconciliation, seeking to integrate those who feel threatened or misunderstood. Additionally, they have implemented advanced security measures in their temples and community centers to protect their followers.
This religion, present in the artistic, spiritual, and technological worlds, has provided humanity with a new sense of purpose and community in a cyberpunk world full of challenges and opportunities. By awakening the Christ within each individual and embracing the protective figure of the Cybernetic Virgin, the faithful find strength and direction amid the complexity and uncertainty of the future.
The images contained in this file are examples of Transhumanist Christian propaganda that have been found on the web, the darknet, private forums, and social media.
Wanna know more?
#cyberpunk aesthetic#cyberpunk art#cyber#cyberart#cyberpunk#cyberpunk 2077#cyberpunk photomode#cybersecurity#cybercore#cyberpunkart#neonoir#cyberpunkaesthetic#darkfuture#religion#catholicism#christianity#catholic church#catholic#the bible#writer stuff#writer community#writers#writers on tumblr#writerscommunity#writeblr#creative writing#writing#virgin mary#ai art is not art#ai art isn't real art
15 notes
·
View notes
Text
Let's connect!
I’d love to connect with folks who geek out over:
- Security Research
- Vulnerability Research
- Threat Intelligence
- Reverse Engineering
- Malware Analysis
- Emerging Threats
- Bug Bounty Hunting
- Physical Pen Testing
- Red Teaming
- Artificial Intelligence
- Machine Learning
- Algorithms
- Quantum Physics
- Weird Stuff
Let's build a diverse and fascinating community together!
https://twitter.com/geeknik
https://github.com/geeknik
2 notes
·
View notes
Text
not a techbro or a tech lover but a secret third thing (tech hater)
#sorry i don't like AI i don't like touchscreens i don't like how everything's done on mobile i don't like data science#i do not find a single tech trend interesting i sit in my boring hole and look at cybersecurity and systems#u ask me about chatgpt and i shrug and walk away#computer science majors who hate tech yes we exist#i picked the wrong major on god#and yet.... i still want to take more classes than required for my program...#oTL
8 notes
·
View notes
Text
2 notes
·
View notes
Text

The grey column towards the left is the ‘vulnerable’ column.
Of all the chatbots that were vulnerable to the attack, those from OpenAI and Cloudflare have implemented padding mitigations in the past 48 hours. OpenAI declined to comment for this post other than to confirm the mitigation. Cloudflare has published this post, which details the fixes.
3 notes
·
View notes