#cloud backup services
Explore tagged Tumblr posts
Text
Do you want to seize control of your financial destiny?
Skyrocket Your Income: The GotBackup Powerline focuses on accelerating your earnings like never before. As new members join, they're positioned in a linear hierarchy, one after the other. This unique structure means that you can reap the rewards of the entire organization's collective efforts, amplifying your income potential. A Rapidly Growing Market: GotBackup is a state-of-the-art cloud backup solution with an ever-increasing customer base. As the world embraces the critical need for data security, you'll be at the vanguard of this booming market, primed to profit from this fast-growing industry. The Clock is Ticking: The Powerline structure instills a sense of excitement for newcomers to sign up, as each recruit is placed directly beneath the most recent joiner. The quicker you take action, the higher you'll be positioned in the powerline, enhancing your chances of benefiting from the efforts and growth of those who follow. Embark on Your Success Story: The GotBackup Powerline is your key to achieving financial independence. Its pioneering structure, coupled with a high-demand product, equips you with all the resources you need to build a flourishing business and generate life-altering income. Don't let this exceptional opportunity slip away. Seize the moment and join the GotBackup Powerline to unlock your boundless income potential. Set off on your journey towards financial liberation today!. Click the link below to embark on this exciting adventure: chatgpt16 Join the Powerline and secure your position for FREE: >>> https://gotbackuptour.com/build-my-downline?id=gilbertogarcia

#earn extra money#GotBackup Review#product review#gotbackup joel therien#gotbackup#gotbackup powerline#gotbackup review#gotbackup online#gotbackup global opportunity#gotbackup compensation plan#gotbackup demo review#best cloud storage#cloud backup for business#cloud backup services#best cloud backup#best online backup service#secure cloud backup
3 notes
·
View notes
Text
The Importance of Cloud Backup for Small Businesses: A Lancashire Perspective | Use It Computers
Protect your small business with reliable online backup! In this video, we explore why cloud backup is vital for small businesses in Lancashire and across the UK. Discover how data backup services safeguard your business from cyberattacks, hardware failures, and other unexpected disruptions.
We also delve into key benefits, including enhanced security, easy accessibility, cost-effective solutions, and robust disaster recovery options for businesses in the UK.
At Use It Computers, we specialise in providing and recommending efficient cloud backup systems for homes and businesses. Don’t risk losing your valuable data—watch this video now to learn how to secure your business effectively!
👉 Visit Use-It.co.uk to learn more about our services.
📞 Contact us today to protect your business data!
#CloudBackup #SmallBusinessUK #DataProtection #LancashireBusiness #BestCloudBackup #UseItComputers
youtube
0 notes
Text
Secure Configurations on your Technology

Ensuring secure configurations on your technology is crucial to protect against cyber threats and vulnerabilities. Here are some tips to make sure your configurations are secure:
-Change Default Settings: Always change default usernames and passwords on your devices.
-Enable Firewalls: Use firewalls to block unauthorized access to your network.
-Regular Updates: Keep your software and firmware up to date to patch any security holes.
-Strong Passwords: Use complex and unique passwords for all your accounts and devices.
-Disable Unnecessary Services: Turn off services and features you don't use to reduce potential entry points for attackers.
-Monitor and Audit: Regularly monitor and audit your configurations to ensure they remain secure.
Stay vigilant and keep your technology secure! #CyberSecurity #SecureConfigurations #StaySafe – www.centurygroup.net
#Cybersecurity#managed it services#data backup#Secured Configuration#cloud technology services#phishing
3 notes
·
View notes
Text
Why SpectraCloud is the Best Choice for Dedicated Hosting Services in India
Are you searching for a dependable host that can move your numerous high-traffic websites and provides high-performance Dedicated Servers with a 100% uptime guarantee? Are you trying to run your resource-demanding applications on a dedicated server that offers limitless bandwidth? Server Basket is the ideal hosting partner to use in that case. We offer low- to high-end dedicated servers with a range of operating system options, both managed and unmanaged. Our dedicated servers are all prepared with web application firewalls, IDS, and IPS for complete security.

Superior Efficiency with SpectraCloud
Regarding Dedicated Hosting, performance is an important consideration. With dedicated hosting, you have exclusive access to every resource on a single server, unlike with shared hosting, where several websites use the same server resources. As a result, performance is noticeably improved, load times are sped up, and enormous traffic volumes may be handled without sacrificing dependability or speed.
SpectraCloud offers cutting-edge hardware, such as the newest processors, fast SSD storage, and lots of RAM, to elevate performance to a new level. This guarantees that your application or website functions properly even during periods of high traffic. Furthermore, SpectraCloud scalable dedicated hosting solutions enable companies to expand their resources in line with their expanding requirements. Because of its adaptability, SpectraCloud is the finest Dedicated Hosting Company for companies of all kinds.
Robust Security Measures
Security is a top priority for any online business. With growing cyber threats, a secure hosting environment is essential to protect sensitive data and maintain customer trust. SpectraCloud understands the importance of security and offers a range of advanced security features in its Dedicated Hosting Services.
Each dedicated server is equipped with a robust firewall, DDoS protection, and regular security updates to protect against potential threats. In addition, SpectraCloud provides an SSL certificate, which is essential to encrypt data and ensure secure communication between your website and its visitors. These complete security measures ensure that SpectraCloud offers a secure hosting environment, making it the perfect choice for Dedicated Hosting for businesses where data protection is a top priority.
Excellent Customer Support
One of the key factors that set SpectraCloud apart from other hosting providers is its excellent customer support. Managing a dedicated server can be complicated, especially for companies without in-house IT expertise. SpectraCloud recognizes this challenge and offers 24/7 customer support to address any issues or questions that arise.
Whether you need help setting up your server, troubleshooting, or tuning performance, SpectraCloud team of experienced experts is always available to provide timely and effective solutions. This level of support ensures that your website or application stays online and functioning optimally, giving you peace of mind so you can focus on growing your business.
Cost-Effective Solutions with Cheap Dedicated Server Hosting
While dedicated hosting is known for its superior performance and security, it often comes with a higher price tag compared to other hosting options. However, SpectraCloud is committed to offering affordable solutions without compromising on quality. As a result, SpectraCloud provides some of the Cheap Dedicated Server Hosting plans in India, making it accessible to businesses with varying budgets.
SpectraCloud pricing model is transparent and includes no hidden or unexpected costs. This combination of affordability and high-quality service makes SpectraCloud the dedicated hosting provider of choice for businesses looking to maximize their return on investment. Additionally, SpectraCloud offers flexible billing options, allowing businesses to choose monthly, quarterly, or yearly plans depending on their financial preferences.
Customization and Control One of the key benefits of dedicated hosting is the level of customization and control it offers. Unlike Shared Hosting and VPS Hosting, which are limited in resources and configuration, dedicated hosting gives businesses full control over their server environment. SpectraCloud goes a step further, offering a wide range of customization options to meet the unique needs of each business.
From choosing the operating system to configuring software and applications, SpectraCloud Dedicated Hosting Services allow businesses to tailor their server environment to their specific requirements. This level of control is particularly beneficial for businesses with complex applications or those that require specific software configurations. With SpectraCloud, you have the freedom to optimize your server for performance, security, and functionality, making it the Best Dedicated Hosting choice for businesses with unique needs.
Comprehensive Backup Solutions – Reliability and Availability Guaranteed
Downtime can be costly for any online business, resulting in lost sales, damaged reputation, and dissatisfied customers. Therefore, reliability is a key factor when choosing a Dedicated Hosting Provider. SpectraCloud understands the importance of uptime and is committed to providing a reliable hosting experience.
SpectraCloud Dedicated Hosting Services offer a 99.9% uptime guarantee, keeping your website or application online and accessible at all times. This reliability is backed by a robust infrastructure that includes multiple data centers, redundant power sources, and advanced monitoring systems. By minimizing downtime and ensuring consistent performance, SpectraCloud proves to be the Dedicated Hosting Provider of choice for businesses that require high availability.
Data loss can have a ruinous impact on any business, leading to significant setbacks and potential legal issues. SpectraCloud recognizes the importance of data protection and offers comprehensive backup solutions as part of its Dedicated Hosting Services. These backups are performed on a regular basis and can be customized as per your business needs: daily, weekly, monthly, etc.
In the event of data loss or server failure, SpectraCloud Backup Solutions ensure that your data can be restored quickly, minimizing downtime and reducing the impact on your business. This commitment to data protection further cements SpectraCloud position as the Best Dedicated Hosting Provider in India.
Green Hosting Initiative
SpectraCloud not only offers top-notch hosting services, but is also committed to sustainability. As part of its green hosting initiative, SpectraCloud uses energy-efficient hardware and processes to reduce its carbon footprint. By choosing SpectraCloud as your Dedicated Hosting Provider, you are not only investing in a high-performance Hosting Solution but also contributing to environmental sustainability.
Conclusion
In a competitive market like India, finding the Best Dedicated Hosting Provider can be difficult. However, for businesses looking for a reliable, secure, and cost-effective hosting solution, SpectraCloud should be your first choice. With unmatched performance, robust security measures, excellent customer support, and Affordable Pricing, SpectraCloud gives you everything you need to succeed online. Whether you're a small business looking for Cheap Dedicated Server Hosting or a large enterprise needing a customized hosting solution, SpectraCloud has the expertise and resources to meet your needs. When you choose SpectraCloud, you're not just choosing a hosting provider; you're working with a company committed to helping your business succeed in the digital world.
#spectracloud#dedicatedhosting#dedicated server#hosting service provider#hosting service#backup solution#cloud computing service#cheap hosting#affordable hosting#cheap dedicated server hosting
2 notes
·
View notes
Text
Kamatera Review – The Best Scalable Cloud Host Yet?
New Post has been published on https://thedigitalinsider.com/kamatera-review-the-best-scalable-cloud-host-yet/
Kamatera Review – The Best Scalable Cloud Host Yet?
This Kamatera review will help you decide whether the web host is the best option for you!
Being able to scale your resource demand effortlessly as your website grows… paying only for the resources you use… no-single-point-of-failure security guarantee… what’s not to love about cloud hosting?
As a web hosting consultant I have helped hundreds of my clients choose the best web hosts to migrate their websites to – and many times, they were also upgrading from a shared or VPS plan to cloud hosting. Kamatera has always been high up in the list of options when we were considering cloud hosts, so I decided to check out their service and take you along.
In the rest of this Kamatera review, I’ll discuss all the web host’s plans, features you can expect to enjoy, how much you should budget, real-time performance figures, their dedication to customer support, and other important factors you should look out for.
Kamatera Review
Founded in 1995, Kamatera is no new kid on the block. They offer generic cloud hosting and every other cloud hosting hybrid you can think of – from managed and unmanaged cloud servers to virtual private cloud (VPC) services and cloud VPS hosting. They also offer reseller hosting for mini hosting companies and web professionals who want to cross-sell this with their core services.
I get it. The differences between their virtual private cloud hosting and cloud VPS hosting can be subtle but don’t worry we’ll discuss them in detail.
Kamatera’s cloud hosting plans are incredibly affordable too. I also like that on all their core plans, you can choose between ready-made packages or customize your plan yourself by setting the number of CPUs, memory (RAM), traffic, storage, and bandwidth. Kamatera also allows you to choose where you want your servers to be located.
Kamatera has been reviewed by 200 users on TrustPilot and users give them a rather decent 3.2 stars. Their positive reviews are from users praising how easy it to set up a server, transparent pricing, and uncommon level of support.
Kamatera Ratings – My Personal Take
It’s been a tradition for me to always give my personal ratings of each host I recommend – and Kamatera will be no different. there’s really no guarantee you can trust the reviews that many web hosts publish on their websites. Plus many businesses doctor reviews on popular platforms like TrustPilot.
The best approach to know exactly how great a web host’s services are? A non-biased overall rating of the web host through expert eyes.
Considering Kamatera’s key features and their real-life performance, here’s how I’d rate the web host on a scale of 1-5. Note that these scores are not static and only reflect their offerings at the time of this writing:
Quality My rating Why I gave this score Features and specs 5.0 Exceptional scalability, a cloud firewall, load balancing tech, and their specialized disaster recovery service makes Kamatera one of the most reliable cloud hosts on the market. They get a resounding 5.0 stars here. Pricing 4.9 Starting at $4/month for their cloud servers, Kamatera’s services are also undoubtedly some of the cheapest on the market. Many VPS plans from other hosting providers even cost more. Performance stats 4.7 My personal tests of Kamatera’s servers recorded a response time of 270 ms. That’s really decent and up there, even though a good number of hosts still perform better so they get a 4.7 in this category. Ease of use 4.0 One of the chief complaints users filed about Kamatera was how it logged you out repeatedly with an IP error message and I experienced this first-hand. Asides that, Kamatera makes it easy to manage your website backend using cPanel, Plesk, Vesta, and CyberPanel. I give them a 4.0 here Customer support guarantee 4.5 Several call lines for their different support portals, email addresses, ticketing, and a knowledgebase are how Kamatera caters to its users’ inquiries. However, I’d have loved to see a live chat option for real-time support. I give them a 4.5 here.
Kamatera Hosting Plans and Prices – 2024
Kamatera offers cloud servers, managed cloud services, virtual private cloud hosting, cloud VPS hosting, and reseller hosting. One small caveat you need to know about Kamatera’s plans is they don’t have a money back guarantee and even if you cancel your plans within the first month, they still charge you the full month’s fee.
You can pay for any Kamatera hosting plan you’ve decided on using your credit card or via Paypal.
Kamatera cloud servers
Kamatera ‘Simple’ cloud hosting plans come in three tiers and allow you to choose your server location and server specs – Windows, Linux, or SSD-optimized.
These plans start at $4/month and you get between 1-2 vCPUs, 1-2 GB RAM of memory, 20-30 GB SSD storage, and 5TB of data transfer on all plans. I love just how much server flexibility you get with Kamatera’s hosting.
Custom cloud servers on Kamatera
What’s more? Kamatera also allows you to configure your hosting plan – you can choose the number of processors you want, where you want your data centers to be located, the amount of memory you need, amount of storage, your OS, amount of traffic, and number of IPs. You also get to decide whether you want to pay for their services per month or per hour. Amazing!
Who this is for:
Kamatera’s cloud servers are for businesses that need to be able to add or remove hosting resources when necessary. With these plans, you can manage your spending exceptionally and don’t have to pay for infrastructure you may not use. Monthly payment drives home your control over what you spend even further.
Kamatera’s managed cloud hosting
Pro Managed
Features – OS monitoring, firewall & networking management, DNS setup, server resources performance metrics, apps installation and configuration, 24/7 NOC support, dedicated account manager on plans with 10+ servers.
Price – $50/month
Premium Managed
Features – Everything in Pro Managed plus custom and application monitoring, database high availability setup, application/service updates, quicker customer agent response times, and dedicated account managers on all plans.
Price – $150/month
Who this is for:
Kamatera’s managed cloud hosting plans take the hassle of managing the technical aspect of your cloud servers out of your hands. From monitoring and setup, to technical support, reporting, and application management, the host does these critical processes for you. What’s more? Kamatera also dedicates a particular human support agent to you who’ll be in charge of your account and you can count on to respond to any inquiries you might have.
Don’t know much about the server-side of websites? Kamatera’s managed cloud hosting plans might just be for you.
Kamatera’s virtual private cloud hosting
Kamatera’s virtual private cloud (VPC) packages are exactly identical to their cloud server plans on both the ‘Simple’ and ‘Customized’ fronts. They are also priced similarly and give you the same features.
Kamatera’s reseller hosting plans
Want to create your own web hosting business or are you a web dev, IT guy, or marketing professional looking to sell web hosting with your core services as a comprehensive package to your clients? Kamatera’s reseller hosting plans are just for you.
Here are some of the benefits you get to enjoy:
Managed setup
With Kamatera’s reseller hosting, their agents support you through setting up your servers and handling client requests.
Outsourced support
You have access to Kamatera’s support team to service your clients whenever they have inquiries.
Less as you grow
The more customers you get, the more discounts you get and the less you have to pay, meaning more profitability for your business.
Ready to get started with Kamatera’s reseller hosting? You’ll need to contact their sales department by creating a support ticket:
Who this is for:
Selling web hosting is one of the best ways to scale your business as a web dev, marketer, or IT professional. You can offer these as part of a comprehensive package and your clients are more likely to buy from you since they already buy your core services from you.
And for web-hosting-only businesses, you can rest assured that you have a business that’s evergreen. Websites will always need website hosting to stay online and it’s an excellent recurring revenue model.
Kamatera Features
Here’s an overview of some of Kamatera’s main features:
SSD storage
Custom hosting plans
Superior load balancing technology
High-performance block storage
Cloud firewall
Transparent pricing
Kamatera, as a cloud-only host, provides premium features that emphasize superior performance and security with its packages.
But some of its more unique features are the load balancers that instantly distribute workloads across a network of servers, ensuring high speeds and quick response times.
Kamatera’s block storage technology emulates a virtual private disk for your cloud plans and ensures there’s no single point of failure. It also ensures extremely low latency (or very quick response times and data transfer) further improving the performance of your website.
Kamatera Performance Tests
Your web host’s servers are your website home and how they perform are exactly how your website will perform. Some important factors to consider when choosing a hosting provider like Kamatera are the server response speeds and uptime.
The web host’s server speed is a measure of how quickly their servers respond and send back your website data to a visitor. On the other hand, the uptime measures the availability of their servers – i.e how much of the time their servers are online to serve up your website’s content to visitors.
The quicker the server speeds are, the less time it will take for your website to load. And the higher the uptime, the more reliable your website will be and you won’t risk losing traffic just because your website was down.
To measure Kamatera’s speed and uptime, I tested a website hosted on their platform and these were the results I got:
Kamatera’s servers started sending the first byte of data back in 276 ms. Quite impressive, even though I still expected better as some high performers respond in sub 100ms.
For the uptime, the website I tested has been available 100% of the time over the last 30 days:
This confirms their 99.9% uptime guarantee!
Kamatera’s Customer Support
It’s easy for web hosts to promise heaven and earth but once many of them take your money, it’s cricket-y silence. Kamatera does well though in terms of customer support. You can reach out to their agents via:
Phone
Kamatera has phone lines for its sales and account managers, technical support, and billing departments.
Email
You can also reach out to Kamatera via email at [email protected], [email protected], and [email protected].
I tried reaching out to their technical support agents via email and got a response in a few hours – quite decent!
Support ticket
Create a support ticket to talk with an agent, fill in your details and phone, and write down your inquiry. Kamatera will reach out to you via email.
Knowledgebase
Simple and straight-to-the-point, Kamatera’s knowledgebase is just how I like it. The built-in search engine also makes it easy to find answers to questions around server setup and security.
Blog
And finally, Kamatera has an up-to-date blog with relevant posts on latest industry information for website and business owners.
Kamatera Security Features
If there’s one thing I like about Kamatera, it’s their security guarantee. First, is their native Cloud Firewall designed to protect your website from attacks while monitoring your servers in real time.
Kamatera’s Cloud Firewall allows you to set rules and filter data packets, exclusively authorizing the entry of certified and approved data packets to your servers. What’s more? The firewall can also function as a VPN giving you even more functionality!
Another core part of Kamatera’s security is the disaster recovery portal. Unforeseen events can impact your website severely. Kamatera’s disaster recovery provides backups, recovery, and failover systems to minimize service disruptions.
Your website’s database is archived at restore points for immediate recovery. And finally, Kamatera’s backup machines are automatically triggered in the event of a system failure to ensure your user experience is not affected.
Kamatera’s hosting plans also allow you to install a free Lets Encrypt SSL certificate, giving your website the padlock seal of trust in the eyes of search engines.
Kamatera User Friendliness – Ease of Use
How to register an account on Kamatera
Setting up an account on Kamatera is super easy. Simply select the plan you want and click on ‘Create server’. You’ll be redirected to the sign up page:
Fill in your email and choose a password you can remember easily – your password should contain at least one lowercase letter, one uppercase letter, a number, and should be at least 8 characters long. Click on ‘Create Free Account’
You’ll receive a confirmation link in your email. Click on it and your account should be ready to go!
How to create a server on Kamatera
To create a new server on Kamatera, from your account dashboard, navigate to “My Cloud” on the left and under the dropdown options, select “Create New Server”
Next, select your preferred data center location and then the operating system you want on the server.
Once that’s done, choose the number of CPUs and specify your server specs – RAM and SSD storage amount.
And finally, configure the fine print – backup, select whether you want a dedicated account manager, set a password, and select your billing schedule. Click on ‘Create server’ and it should be done in a few minutes.
Kamatera control panel
Kamatera doesn’t come with a custom control panel like some other high performing hosts – SiteGround, Hostinger, and A2Hosting – however, Kamatera gives you access to cPanel, Plesk, Vesta, and CyberPanel.
How to install WordPress on Kamatera
The swiftest way to deploy WordPress on Kamatera is via your control panel. Using cPanel as an example, we’ll use the Softaculous installer:
In your cPanel account, navigate to ‘Tools’ and click on ‘Softaculous Apps Installer’.
In the search engine, type in ‘WordPress’. Click ‘Install’ and then ‘Choose protocol’.
Next, choose the domain name you want WordPress installed on and configure the directory. If you’re not sure, just choose the default values and proceed.
Configure your ‘Site Name’ and ‘Site description’. Whatever you put here will be shown in the title bar of a website visitor’s browser.
Next, configure your ‘Admin Username’, ‘Admin password’, and ‘Admin Email’. These are the login details you will use to access your WordPress dashboard once it is installed.
Select the auto update boxes for WordPress, plugins, and themes.
Now configure where you want your website backups to be stored and check the ‘Automated backups’ so Softaculous makes backups of your website at specified intervals.
Review all the installation options and click ‘Install’. Voila!
Kamatera Server Footprint
If Kamatera had just one thing going for them, it’d be their continent-wide server footprint. Their servers are spread across dozens of data centers in Europe, the Americas, and Asia and several countries in between.
This guarantees exceptional website performance for businesses targeting audiences spread across the globe.
Conclusion – Should You Choose Kamatera?
Kamatera is a very decent dedicated cloud host and their performance and built-in features are no joke. I recommend Kamatera if you’re looking for affordable packages and have outgrown your shared/VPS plans.
Their block storage, load balancers, cloud firewall, and disaster recovery ensure your website performs exceptionally and is protected from bad actors.
My only fault with Kamatera would be their account creation process. Their IP address protocol system glitches often and may log you out for no reason at all.
Visit Kamatera →
FAQs
What is Kamatera?
Kamatera is a cloud hosting company that provides web hosting infrastructure mainly to eCommerce businesses and other enterprises that require exceptionally scalable resources.
What is cloud server monitoring?
Cloud server monitoring is one of the services offered by Kamatera to customers. The host constantly monitors your website servers to prevent malware and minimize service disruptions.
What payment methods does Kamatera accept?
Kamatera accepts payments for their hosting plans via credit cards and standing order. They also accept Paypal payments.
#A2Hosting#admin#agent#agents#amazing#Americas#amp#approach#apps#Asia#backup#backups#Best cloud hosting#Blog#browser#Business#Byte#Cloud#Cloud hosting#cloud services#Companies#comprehensive#content#control panel#credit card#dashboard#data#Data Center#Data Centers#data transfer
2 notes
·
View notes
Text
I don't know I'm not done talking about it. It's insane that I can't just uninstall Edge or Copilot. That websites require my phone number to sign up. That people share their contacts to find their friends on social media.
I wouldn't use an adblocker if ads were just banners on the side funding a website I enjoy using and want to support. Ads pop up invasively and fill my whole screen, I misclick and get warped away to another page just for trying to read an article or get a recipe.
Every app shouldn't be like every other app. Instagram didn't need reels and a shop. TikTok doesn't need a store. Instagram doesn't need to be connected to Facebook. I don't want my apps to do everything, I want a hub for a specific thing, and I'll go to that place accordingly.
I love discord, but so much information gets lost to it. I don't want to join to view things. I want to lurk on forums. I want to be a user who can log in and join a conversation by replying to a thread, even if that conversation was two days ago. I know discord has threads, it's not the same. I don't want to have to verify my account with a phone number. I understand safety and digital concerns, but I'm concerned about information like that with leaks everywhere, even with password managers.
I shouldn't have to pay subscriptions to use services and get locked out of old versions. My old disk copy of photoshop should work. I should want to upgrade eventually because I like photoshop and supporting the business. Adobe is a whole other can of worms here.
Streaming is so splintered across everything. Shows release so fast. Things don't get physical releases. I can't stream a movie I own digitally to friends because the share-screen blocks it, even though I own two digital copies, even though I own a physical copy.
I have an iPod, and I had to install a third party OS to easily put my music on it without having to tangle with iTunes. Spotify bricked hardware I purchased because they were unwillingly to upkeep it. They don't pay their artists. iTunes isn't even iTunes anymore and Apple struggles to upkeep it.
My TV shows me ads on the home screen. My dad lost access to eBook he purchased because they were digital and got revoked by the company distributing them. Hitman 1-3 only runs online most of the time. Flash died and is staying alive because people love it and made efforts to keep it up.
I have to click "not now" and can't click "no". I don't just get emails, they want to text me to purchase things online too. My windows start search bar searches online, not just my computer. Everything is blindly called an app now. Everything wants me to upload to the cloud. These are good tools! But why am I forced to use them! Why am I not allowed to own or control them?
No more!!!!! I love my iPod with so much storage and FLAC files. I love having all my fics on my harddrive. I love having USBs and backups. I love running scripts to gut suck stuff out of my Windows computer I don't want that spies on me. I love having forums. I love sending letters. I love neocities and webpages and webrings. I will not be scanning QR codes. Please hand me a physical menu. If I didn't need a smartphone for work I'd get a "dumb" phone so fast. I want things to have buttons. I want to use a mouse. I want replaceable batteries. I want the right to repair. I grew up online and I won't forget how it was!
59K notes
·
View notes
Text
Another approach is to use Git. No, seriously, I know it's like a programmer thing, but it works for all text files and can technically work for xml based files like Word also.
If you're not confident on using a command prompt, check out Github Desktop. Contrary to the name you don't have to put repositories it makes online (and if you do they don't have to be public).
Git is helpful because all those versions of files don't remain visible in one folder, you always just see the most recent version. Past versions exist in the commit history, and you can. Roll back to specific versions, branch off from them, all that good stuff.
REMEMBER: WHEN YOU'RE WORKING ON A PIECE OF WRITING, NEVER DELETE ANYTHING
Ok, so you have a big paper due in July. You make a folder for the project called "Big Paper." You get to work, and save a file titled "PaperTopic.doc" in that folder.
You go back to your draft the next day. DO NOT simply open "PaperTopic.doc" and start editing/adding/revising. You are going to make a folder titled "Paper Versions." You are going to make a copy of "PaperTopic.doc." You are going to move it into the "Paper Versions" Folder.
Then you are going to go back to the original "PaperTopic.doc," and rename it "PaperTopic 5.14.24.doc." And you're going to repeat this EVERY DAY that you work on this project. Soon the "Paper Versions" will look like this:
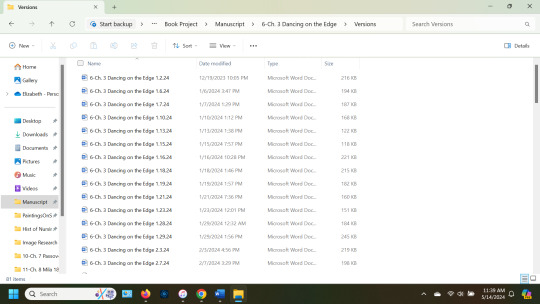
I post about this every 6 months or so, and I will continue to do so; because one day, it WILL save your ass. You're welcome.
Also, back it up to an external hard drive at least once a week.
#writing#writers#creative writing#also please please make backups!!!#they dont have to be in a cloud service#but if you want the peace of mind of cloud stuff without them spying on you consider putting your backups on cloud platforms in password#protected zip files. those are encrypted so Google or whoever wont be able to peek at them#i personally use a free tier Oracle Cloud server as my “house fire” level backup but ik thats not practical for most#remember that backups living on the same device arent really backups at all#since your whole hard drive could fail#and a bad power surge could take out all the drives in your computer#stay safe yall!
2K notes
·
View notes
Text
More companies are choosing cloud services in Orange County because they are secure, affordable, and flexible. With IT support services in Orange County and backup disaster recovery in Orange County, businesses can run smoothly. A reliable cloud service provider in Orange County helps them stay ahead in the digital world.
0 notes
Text
Future Applications of Cloud Computing: Transforming Businesses & Technology
Cloud computing is revolutionizing industries by offering scalable, cost-effective, and highly efficient solutions. From AI-driven automation to real-time data processing, the future applications of cloud computing are expanding rapidly across various sectors.

Key Future Applications of Cloud Computing
1. AI & Machine Learning Integration
Cloud platforms are increasingly being used to train and deploy AI models, enabling businesses to harness data-driven insights. The future applications of cloud computing will further enhance AI's capabilities by offering more computational power and storage.
2. Edge Computing & IoT
With IoT devices generating massive amounts of data, cloud computing ensures seamless processing and storage. The rise of edge computing, a subset of the future applications of cloud computing, will minimize latency and improve performance.
3. Blockchain & Cloud Security
Cloud-based blockchain solutions will offer enhanced security, transparency, and decentralized data management. As cybersecurity threats evolve, the future applications of cloud computing will focus on advanced encryption and compliance measures.
4. Cloud Gaming & Virtual Reality
With high-speed internet and powerful cloud servers, cloud gaming and VR applications will grow exponentially. The future applications of cloud computing in entertainment and education will provide immersive experiences with minimal hardware requirements.
Conclusion
The future applications of cloud computing are poised to redefine business operations, healthcare, finance, and more. As cloud technologies evolve, organizations that leverage these innovations will gain a competitive edge in the digital economy.
🔗 Learn more about cloud solutions at Fusion Dynamics! 🚀
#Keywords#services on cloud computing#edge network services#available cloud computing services#cloud computing based services#cooling solutions#cloud backups for business#platform as a service in cloud computing#platform as a service vendors#hpc cluster management software#edge computing services#ai services providers#data centers cooling systems#https://fusiondynamics.io/cooling/#server cooling system#hpc clustering#edge computing solutions#data center cabling solutions#cloud backups for small business#future applications of cloud computing
0 notes
Text
One of my decade old videos on youtube got taken down for "spam, deception, ect" cus the link I put in the description to credit where I got the music from went lights out lol.
It didn't count as a strike on my account, but I'm not gonna bother appealing it. I don't even post videos on youtube anymore, any recording I do is lost media and when it's gone, it's gone.
#reen talks#youtube is shit and i hope one day it'll all go up in flames#anyway backup your shit and don't rely on cloud service#also back up your stuff
0 notes
Text
impermanent/cloud storage fad rant coming along:
why is everything so hell bent on making me store my data in the cloud?
like the PS4 was designed to work beside an external HDD or SSD if you ran low on space, the PS5 on the other hand *really* wants you to use their cloud storage (the options to back up data are so limited when you try to back up PS4 data vs PS5)--for which you must be subscribed to PS+ also!
computers come integrated with OneDrive storage on them for easy backing up of files (sure, I've lost files to corruption or deletion before, this is nifty for things that *should* be backed up continuously like a thesis or a research paper--but then again, space is finite, so to get more space, that's more money!) but they also word the storage options so weirdly. what do you mean "free up space" frees up the physical space and not the cloud storage backup?
and now my antivirus has removed the interface for me to choose *where* to store my back ups, and has now renamed and re-shopped the "backup" panel to "cloud backup"--for which they have their own specialty server--which you have to subscribe to on top of your anti-virus.
I'm just so tired of the cloud. it's so impermanent. it's not practical in the long run. and so many devices are now hardwired to best back up on cloud software than hard-drive to hard-drive. maybe I'm just getting old but this doesn't seem sustainable or fiscally applicable.
#technology rant#cloud storage#data backup#subscription services#turning into the sims 3 trait technophobe rn
0 notes
Text
Choosing between cloud and on-premise IT infrastructure is a crucial decision for businesses. This guide explores the benefits and challenges of both options, helping you determine which solution aligns best with your company's needs. Whether you're looking for scalability, cost-efficiency, security, or control, understanding the key differences between cloud and on-premise setups will enable you to make an informed decision for your business’s future growth and technological requirements.
#cloud backup service#remote computer support#server management services#it manpower outsourcing#network operations center
0 notes
Text
Law Firms IT Support Services

Managing cybersecurity, ensuring system uptime, and maintaining government-enforced regulations can overwhelm law firms. Ensuring your caseloads are maintained while having efficient, reliable network support is paramount to your and your clients’ success in Atlanta, Georgia.
Connect us: https://centurygroup.net/industries/legal-it-support/
#LawFirmsITServices #ITConsulting #itsupport #itsupportcompany #itsupportservices #centurygroupIT #
#Law Firms IT Support#Legal IT Support#managed it services#data backup#managed it solutions#cloud technology services
1 note
·
View note
Text
The 10 Best Cloud Hosting Providers (June 2024)
New Post has been published on https://thedigitalinsider.com/the-10-best-cloud-hosting-providers-june-2024/
The 10 Best Cloud Hosting Providers (June 2024)
Cloud hosting has transformed the way businesses manage their online presence by providing scalable, flexible, and reliable hosting solutions. Unlike traditional hosting, cloud hosting uses multiple servers to distribute resources, ensuring high availability and superior performance. Choosing the best cloud hosting provider is essential for businesses seeking robust performance, security, and the flexibility to efficiently handle varying resource demand as your website grows. This guide highlights the best cloud hosting providers, helping you find the ideal solution for your needs.
What is Cloud Hosting and How Does it Work?
Cloud hosting is a type of web hosting that uses multiple servers to balance the load and maximize uptime. Unlike traditional hosting solutions that rely on a single physical server, cloud hosting utilizes a network of interconnected servers to store and manage data. This setup ensures that resources are dynamically allocated across the servers, providing enhanced flexibility, scalability, and reliability.
In cloud hosting, websites and applications are hosted on a cluster of servers, often referred to as the “cloud.” When a user accesses a website, the request is distributed across multiple servers, ensuring that no single server becomes a bottleneck. This distribution allows for better handling of traffic spikes and provides a more consistent performance, even during high demand periods.
One of the key benefits of cloud hosting is its scalability. Users can easily scale their resources up or down based on their needs, without experiencing downtime or performance issues. This makes cloud hosting ideal for businesses that experience variable traffic patterns or are planning for growth. Additionally, cloud hosting typically includes features such as automated backups, disaster recovery, and enhanced security measures, ensuring that data is protected and easily recoverable in case of an emergency.
Who is Cloud Hosting For?
Cloud hosting is designed to cater to a wide range of users, from individual developers to large enterprises, offering scalability, flexibility, and robust performance. Here are some of the key audiences who can benefit significantly from cloud hosting:
Growing Businesses and Startups
Scalability and Flexibility: Startups and growing businesses often experience fluctuating traffic and require a hosting solution that can scale resources up or down based on demand. Cloud hosting provides this flexibility, allowing businesses to pay for only what they use and scale effortlessly as they grow.
E-commerce Websites
High Performance and Reliability: E-commerce sites require high uptime and fast load times to ensure a smooth shopping experience for customers. Cloud hosting offers excellent performance and reliability, which are crucial for online stores to prevent downtime and maintain customer satisfaction.
Ecommerce stores are also prone to traffic spikes especially for brands selling seasonal products – e.g: Christmas gifts shops will have peak sales towards the end of the year. A cloud hosting plan allows you to scale easily and pay only for the resources you nees.
Developers and Tech-savvy Users
Customization and Control: Developers and tech-savvy users benefit from the control and customization options that cloud hosting provides. With root access and the ability to configure server environments, they can tailor the hosting setup to meet specific application requirements.
Enterprises and Large Organizations
Robust Infrastructure: Large organizations with complex infrastructure needs require a robust and scalable hosting solution. Cloud hosting offers the necessary resources and reliability to support enterprise-level applications, ensuring business continuity and data integrity.
Educational Institutions and Research Organizations
Resource-intensive Applications: Educational and research institutions often run resource-intensive applications and simulations. Cloud hosting provides the computational power and storage needed for these applications, along with the ability to handle large datasets.
SaaS Providers
High Availability and Scalability: Software as a Service (SaaS) providers need hosting solutions that offer high availability and the ability to scale quickly to accommodate a growing user base. Cloud hosting delivers these capabilities, ensuring their applications remain accessible and perform excellently.
These Are The Very Best Cloud Hosting Providers
Cloudways stands out as a leading managed cloud hosting platform, offering exceptional flexibility and performance.
Known for its exceptional performance optimization tools, Cloudways ensures your website runs smoothly and efficiently. Users benefit from features such as automated backups, staging environments, and advanced caching mechanisms. Additionally, Cloudways offers 24/7 expert support to help you tackle any issues promptly.
It allows users to deploy applications across multiple cloud infrastructures, including AWS, Google Cloud, DigitalOcean, Vultr, and Linode.
Cloudways Unique Features:
Cloudways excels with its managed services, providing a user-friendly platform that simplifies server management. Key features include 1-click server deployment, automated backups, and advanced caching mechanisms like Varnish, Memcached, and Redis.
Why you should choose Cloudways:
Flexible server management: Choose from multiple cloud providers and easily scale resources.
Excellent performance and uptime: High-speed performance with optimized stack and SSD-based servers.
Robust security measures: Regular security patches, dedicated firewalls, and SSL certificates.
Cloudways is the best overall choice for cloud hosting, offering unmatched flexibility, performance, and managed services.
Read Review →
Visit Cloudways →
Hostinger is renowned for its affordable cloud hosting solutions, making it an excellent choice for individuals and small businesses looking for cost-effective yet powerful hosting.
With its intuitive control panel and robust performance, Hostinger is perfect for users seeking budget-friendly yet reliable cloud hosting solutions. Hostinger’s commitment to affordability does not compromise the quality, making it an excellent choice for small businesses and individuals alike.
Hostinger Unique Features:
Hostinger provides a balance of performance and affordability, featuring a custom control panel, daily backups, and a 99.9% uptime guarantee. Their cloud plans also include a dedicated IP and resources.
Why you should choose Hostinger:
Very affordable pricing: Competitive rates for cloud hosting plans.
User-friendly control panel: Custom-built control panel designed for ease of use.
Decent speed and uptime: Reliable performance with adequate speed for most applications.
Hostinger is ideal for budget-conscious users seeking reliable cloud hosting without compromising on essential features.
Read Review →
Visit Hostinger →
3. SiteGround (Best customer support)
SiteGround is well-regarded for its exceptional customer support and robust cloud hosting solutions. It offers scalable and fully managed cloud hosting, perfect for growing businesses.
Their cloud hosting plans are powered by Google Cloud, ensuring top-notch performance and reliability. SiteGround provides automatic daily backups, a free CDN, and advanced security solutions. Their support team is available 24/7 via phone, chat, and ticket system, ensuring that you receive timely and knowledgeable assistance whenever needed.
SiteGround Unique Features:
SiteGround’s standout features include fully managed hosting, automatic scaling, and daily backups. They provide a dedicated support team available 24/7 via phone, chat, and ticketing systems.
Why you should choose SiteGround:
Outstanding customer support: Highly responsive and knowledgeable support team.
Scalable resources: Easily adjust CPU, RAM, and storage as needed.
Enhanced security features: AI anti-bot system, daily backups, and free SSL certificates.
SiteGround excels in customer support, making it the best choice for users who prioritize responsive and effective assistance.
Read Review →
Visit SiteGround →
Bluehost is ideal for beginners due to its user-friendly interface and seamless integration with popular platforms like WordPress. Their cloud hosting plans offer enhanced performance, scalability, and security features.
Bluehost provides a straightforward setup process, making it easy for new users to get started. Additionally, they offer 24/7 customer support and a range of helpful resources to guide you through your hosting journey.
Bluehost Unique Features:
Bluehost’s cloud hosting features include easy scalability, resource monitoring, and seamless integration with various CMS platforms, especially WordPress. Their enhanced cPanel provides a simple and intuitive user interface.
Why you should choose Bluehost:
Easiest to use: Beginner-friendly interface and straightforward setup.
Reliable performance: Solid uptime and load speeds.
Comprehensive support: 24/7 support with extensive documentation and tutorials.
Bluehost is the perfect choice for beginners, offering an intuitive interface and strong performance at an affordable price.
Read Review →
Visit BlueHost →
ScalaHosting is known for its security-centric approach to cloud hosting, offering a range of features designed to protect users’ data and applications.
ScalaHosting is known for its focus on security, offering robust cloud hosting solutions that prioritize the safety of your data. . Their proprietary SPanel ensures easy and secure management, while the SShield security system offers real-time monitoring and protection against cyber threats. ScalaHosting’s cloud plans include free daily backups, a free CDN, and fully managed services. Their commitment to security and performance makes them an excellent choice for businesses looking to protect their online presence.
ScalaHosting Unique Features:
ScalaHosting provides innovative security features such as SShield real-time cybersecurity protection and free SPanel control panel. They also offer daily backups and free SSL certificates to enhance security.
Why you should choose ScalaHosting:
Most secure: Advanced security features like SShield and daily backups.
User-friendly control panel: SPanel is intuitive and easy to navigate.
Scalable plans: Flexible options to scale resources as your business grows.
ScalaHosting is the top choice for users who prioritize security, offering robust protection features and a user-friendly management interface.
Read Review →
Visit ScalaHosting →
A2 Hosting is renowned for its speed, providing some of the fastest cloud hosting solutions available. Their Turbo Servers offer up to 20x faster page loads compared to standard hosting. A2 Hosting’s cloud plans come with SSD storage, free site migrations, and a range of developer-friendly features. Their commitment to performance and reliability ensures that your website will run at optimal speed.
A2 Hosting Unique Features
A2 Hosting stands out with its Turbo Servers, which can load pages up to 20 times faster than standard servers. The company also provides free site migrations, SSD storage, and a developer-friendly environment.
Why you should choose A2 Hosting:
Speed: Turbo Servers for enhanced speed.
Free Migrations: Hassle-free website transfers.
Developer-Friendly: Supports multiple development tools and frameworks.
A2 Hosting is the best choice for users prioritizing speed and performance in their cloud hosting solution.
Read Review →
Visit A2Hosting →
Verpex offers exceptional value for money, providing cloud hosting services packed with features at competitive prices. Their plans include free domain registration, SSL certificates, and daily backups.
Verpex’s cloud hosting ensures high performance and reliability with multiple data center locations. Their excellent customer support and generous resource allocations make them a great choice for those seeking affordable yet feature-rich cloud hosting.
Verpex Unique Features
Verpex includes features such as free migrations, daily backups, and 24/7 support. Their cloud hosting plans are designed to offer flexibility and scalability at an affordable price.
Why you should choose Verpex:
Affordable Plans: Cost-effective hosting solutions.
Free Migrations: Easy site transfers.
24/7 Support: Around-the-clock customer service.
Verpex provides the best value for money, making it an excellent choice for budget-conscious users seeking reliable cloud hosting.
Read Review →
Visit Verpex →
InterServer stands out with its commitment to providing unlimited resources, making it an excellent choice for users who need flexible and scalable hosting solutions. InterServer’s cloud hosting plans include unlimited storage, bandwidth, and email accounts, ensuring that users have the resources they need to grow their websites.
Their infrastructure is designed for high performance and reliability, with features like daily backups, free website migrations, and 24/7 customer support. InterServer’s affordability combined with unlimited features makes it a top choice for those seeking robust cloud hosting without worrying about resource limits.
InterServer Unique Features
InterServer stands out with its unlimited resources feature, which includes unlimited storage, bandwidth, and email accounts. Additionally, it offers price lock guarantees, ensuring that users do not face unexpected price hikes.
Why you should choose InterServer:
Unlimited Resources: No caps on storage or bandwidth.
Price Lock Guarantee: Fixed pricing with no surprise increases.
Strong Security: Advanced security features to protect data.
InterServer is ideal for businesses or individuals with high resource demands, providing a cost-effective solution with extensive features.
Visit Interserver →
Kamatera offers highly customizable cloud hosting solutions, allowing users to configure their server resources to meet specific needs. Their cloud platform provides flexible scaling, a wide range of server configurations, and global data centers.
Kamatera’s pay-as-you-go pricing model ensures you only pay for the resources you use. Their 24/7 customer support and high performance make them an excellent choice for businesses with unique hosting requirements.
Kamatera Unique Features
Kamatera’s standout feature is its high level of customization, allowing users to configure CPU, RAM, storage, and other resources as needed. It also offers a wide range of server locations globally.
Why you should choose Kamatera:
High Customizability: Tailor resources to specific requirements.
Global Data Centers: Multiple server locations for optimal performance.
Scalability: Easily scale resources up or down based on demand.
Kamatera is perfect for users who need a customizable and scalable cloud hosting solution with a global presence.
Visit Kamatera →
DreamHost’s cloud hosting plans are tailored for developers, offering scalable resources, full root access, and a wide range of developer tools. Their OpenStack-based cloud platform provides flexibility and reliability.
DreamHost’s cloud plans include free bandwidth, SSD storage, and high security. Their excellent performance and developer-friendly features make them a top choice for tech-savvy users.
DreamHost Unique Features
DreamHost offers features like full root access, scalable SSD storage, and compatibility with a variety of development languages and frameworks. Its DreamCompute service allows for flexible and powerful cloud computing.
Why you should choose DreamHost:
Developer Tools: Extensive tools and APIs for developers.
Scalable SSD Storage: Fast and scalable storage solutions.
Reliable Infrastructure: High performance and uptime guarantees.
DreamHost is the top choice for developers seeking a flexible, powerful, and developer-centric cloud hosting environment.
Visit DreamHost →
How We Chose The Best Cloud Hosting Providers
Selecting the best cloud hosting providers involved a thorough evaluation process where we considered several key factors to ensure that our recommendations meet the highest standards. Below, we detail the critical considerations we made when choosing these hosts.
Unique Value
We considered any unique features that add value to the hosting service. This includes tools for performance optimization, user-friendly control panels, website builders, and integration with third-party services. These features can enhance the overall hosting experience and provide users with additional functionality that simplifies website management and development.
Performance
Performance is paramount when it comes to cloud hosting. We assessed the speed, uptime, and overall reliability of each provider. High-performance cloud hosting ensures that websites and applications run smoothly, providing an optimal user experience without downtime or slow loading times.
Support
Customer support is a crucial aspect of any hosting service. We evaluated the quality and availability of customer support provided by each host. This includes looking at support channels (live chat, phone, email), the responsiveness of the support team, and the availability of helpful resources like tutorials and knowledge bases. Excellent support can significantly impact the overall hosting experience, especially for users who may need assistance with technical issues.
Security
Security features were a significant factor in our evaluation. We examined the security measures each provider implements, such as SSL certificates, DDoS protection, regular backups, and compliance with security standards. Robust security features protect sensitive data and ensure the integrity of websites and applications hosted on these platforms.
Pricing
Affordability and value for money were also key considerations. We compared the pricing plans of each host, looking for competitive rates that offer excellent value. This includes assessing what features and resources are included in each plan and ensuring that there are no hidden costs. We aimed to recommend providers that offer a good balance of cost and quality, making cloud hosting accessible to a wide range of users.
Scalability
Scalability is essential for businesses that anticipate growth. We looked at how easily users can scale their resources up or down with each provider. This includes the flexibility to upgrade or downgrade plans and the ability to add resources like storage or bandwidth as needed without significant downtime or technical hurdles.
FAQs
What is cloud hosting?
Cloud hosting is a type of web hosting that uses multiple servers to balance the load and maximize uptime. Instead of relying on a single server, websites and applications are hosted on a network of connected servers, providing greater flexibility and reliability.
How is cloud hosting different from traditional hosting?
Cloud hosting differs from traditional hosting by distributing resources across multiple servers, reducing the risk of downtime and improving scalability. Traditional hosting often relies on a single server, making it less flexible and more vulnerable to outages.
What are the benefits of cloud hosting?
The main benefits of cloud hosting include enhanced performance, better scalability, improved reliability, and robust disaster recovery options. It also offers automatic updates, flexible pricing, and easy resource management, making it ideal for growing businesses and high-traffic websites.
How do I choose the best cloud hosting provider?
To choose the best cloud hosting provider, consider factors such as performance, customer support, security features, pricing, scalability options, and additional features like backups and monitoring. Reading reviews and comparing the specific needs of your website or application can also help in making an informed decision.
#2024#A2Hosting#Accounts#ai#APIs#applications#approach#as a service#automatic updates#AWS#backups#bases#Best cloud hosting providers#Best cloud providers#BlueHost#bot#brands#Business#business continuity#cdn#certificates#Christmas#Cloud#cloud computing#Cloud hosting#cloud platform#cloud providers#cloudways#cluster#CMS
2 notes
·
View notes
Text
Sell Your Old Laptop in Bangalore for Instant Cash
Selling your old laptop in Bangalore has never been easier. Whether upgrading to a new device or decluttering, you can get instant cash in exchange for your unused laptop. Here’s how you can make it happen seamlessly.
Why Sell Your Old Laptop?
Laptops lose value over time, and holding onto unused devices can clutter your space. Selling your old laptop allows you to:
Earn extra money instantly.
Upgrade to better technology.
Contribute to eco-friendly recycling efforts.
Where to Sell Old Laptops in Bangalore?
Bangalore offers several options for selling old laptops. You can choose the one that best fits your needs:
1. Online Platforms
Websites like OLX, Cashify, and Quikr make selling laptops simple. Create a listing, set your price, and connect with buyers in your area.
2. Cash-for-Gadgets Services
Services like CashyGo specialize in offering cash for old electronics. They provide quick quotes and hassle-free transactions, making them a top choice in Bangalore.
3. Local Shops and Marketplaces
Bangalore’s local electronic shops or marketplaces like SP Road can offer competitive prices for used laptops. Visit them to negotiate in person.
How to Prepare Your Laptop for Sale
1. Backup Your Data
Save your essential files on an external drive or cloud storage before selling your laptop.
2. Factory Reset the Device
Restore your laptop to factory settings to remove personal data and make it ready for the next user.
3. Clean and Package It Properly
A clean and well-maintained laptop creates a better impression and fetches a higher price.
Benefits of Choosing CashyGo in Bangalore
CashyGo is a reliable option for selling laptops in Bangalore. Here’s why:
Quick Cash Payments: Get instant cash upon selling.
Fair Price Evaluation: They assess the condition and brand of your laptop to offer the best value.
Convenience: Avoid the hassle of negotiating with multiple buyers.
Top Brands That Sell Well
If you own a laptop from top brands like Dell, HP, Lenovo, Apple, or Asus, you’re likely to get a better resale value. These brands are in high demand due to their quality and durability.
Tips for Getting the Best Price
Highlight Features: Mention specifications like RAM, processor, and screen size in your listing.
Be Honest: Disclose any defects or issues to build trust with buyers.
Compare Offers: Don’t settle for the first offer; compare rates from multiple sources.
Final Thoughts
Selling your old laptop in Bangalore is a smart way to declutter, earn cash, and embrace sustainable practices. Choose a reliable service like CashyGo to ensure a smooth and rewarding experience.
Take the first step today and turn your old laptop into instant cash!

#Selling your old laptop in Bangalore has never been easier. Whether upgrading to a new device or decluttering#you can get instant cash in exchange for your unused laptop. Here’s how you can make it happen seamlessly.#Why Sell Your Old Laptop?#Laptops lose value over time#and holding onto unused devices can clutter your space. Selling your old laptop allows you to:#Earn extra money instantly.#Upgrade to better technology.#Contribute to eco-friendly recycling efforts.#Where to Sell Old Laptops in Bangalore?#Bangalore offers several options for selling old laptops. You can choose the one that best fits your needs:#1. Online Platforms#Websites like OLX#Cashify#and Quikr make selling laptops simple. Create a listing#set your price#and connect with buyers in your area.#2. Cash-for-Gadgets Services#Services like CashyGo specialize in offering cash for old electronics. They provide quick quotes and hassle-free transactions#making them a top choice in Bangalore.#3. Local Shops and Marketplaces#Bangalore’s local electronic shops or marketplaces like SP Road can offer competitive prices for used laptops. Visit them to negotiate in p#How to Prepare Your Laptop for Sale#1. Backup Your Data#Save your essential files on an external drive or cloud storage before selling your laptop.#2. Factory Reset the Device#Restore your laptop to factory settings to remove personal data and make it ready for the next user.#3. Clean and Package It Properly#A clean and well-maintained laptop creates a better impression and fetches a higher price.#Benefits of Choosing CashyGo in Bangalore#CashyGo is a reliable option for selling laptops in Bangalore. Here’s why:
0 notes