#accessible education methods
Explore tagged Tumblr posts
Text
भारतीय नवप्रवर्तकों के लिए हंड्रेड का निमंत्रण, शिक्षा में नवाचार को मिलेगी वैश्विक मान्यता
हंड्रेड ग्लोबल कलेक्शन 2026 ने भारतीय नवप्रवर्तकों के लिए एक अनोखा अवसर प्रस्तुत किया है। इस पहल के तहत, हंड्रेड उन नवाचारों को पहचानने और उनका प्रचार करने की कोशिश कर रहा है जिन्होंने शिक्षा के क्षेत्र में महत्वपूर्ण सुधार किए हैं। यह भारतीय शिक्षकों, ग्रामीण समाजसेवियों, और एनजीओ के लिए एक विशेष मौका है, जो अपने नवाचारों को वैश्विक मंच पर प्रस्तुत करना चाहते हैं। भारतीय नवप्रवर्तक, जो सीमि��…
#Udaan Youth Club#2025 Collection dates#2025 कलेक्शन की तारीखें#2026 Global Collection#2026 ग्लोबल कलेक्शन#accessible education methods#advice for improving education#application dates#application deadline#application guidelines#application process#benefits of innovation#benefits of innovation in education#changes in education#contact HundrED team#ed-tech startups#education reform#education transformation#educational innovation#examples of educational innovation#Global Collection Advisor#global education impact.#global level education#global recognition#guide to apply for HundrED#how to apply#how to bring change in education#HundrED application#HundrED Collection#HundrED Collection 2026
0 notes
Text
Tagging @fierceawakening because it's thoughts regarding mostly the prison abolition argument I've been reading on your page, but not about any specific thread that feels reasonable to reply to.
So personally, I don't really think about this too much because in practice I'd much rather focus on specific achievable harm reductions I can currently fight for, however, I have another complication with prison abolition.
I agree that involuntary confinement is problematic, but I've also seen it work? Like my grandfather went to prison, and he says it saved his life and I believe him. I don't think he should've gone to prison in a just system, what he was convicted on was absurd and not reasonable evidence, and it was a non-violent drug crime, which pretty much everyone in the reform to abolition spectrum agree is bad.
At the same time, my grandfather is likely an undiagnosed autistic man, who struggled intensely with adulthood and prison gave him a structured space to learn how to manage himself.
He was lucky enough to be imprisoned in a place where he was given access to education and life skills, similar to what my dad got when his parents paid for a private rehab facility, which was also a form of involuntary confinement. Both of these men in my life returned from these experiences far better able to handle themselves in the world, they both learned important life skills for caring for themselves, and improved their ability to function in employment.
I don't think prisons currently look like this, I know they don't, and I'm pro-reform because of this. I also think that if a fair system were in place it's likely my grandfather should not have been involuntarily commited. (My father had proved a danger to me so he would be comitted in systems advocated by people more on the reform end of the spectrum.) However, it's hard for me to reconcile the idea that all involuntary confinement is inherently bad and that it's only going to make the individuals life worse no matter what. Because the two people in my life who were involuntarily commited (though both very lucky in what services were offered to them in these institutions) both improved their lives significantly because of it.
#I see a lot of people saying non-abolitionists don't have personal experience with the justice system#so I guess part of this is to say#some of us do#Some of us do have family members who were convicted of non-violent drug offences on a wire tap that has a phrase#that is something he regularly says to this day because it's a normal part of his dialect#but as an immigrant it was misconstrued to be proof of involvement#I mean personally I'm very pro making the justice system fully focused on harm reduction#and completely dissolving the connection between the crime comited and the legnth of confinement#and instead having it based soley on risk to society#But in the short term what I'm focusing on is ensuring felons retain the right to vote#that they have access to education and life skills and medical care especially mental health care while in prison#That crimes that do not pose risk to others like drug use or consenual prostitution are no longer crimes#that methods that do have proof of being only bad like solitary confinement or nutriloaf be stopped#I think it should be a last resort to involuntarily commit someone#but there's a difference between that and it being never helpful if that makes sense#This might not be the best phrased thoughts#they've been sitting in my head a while and I don't think I can say them better even if this way isn't fully what I'm intending
1 note
·
View note
Text
Transformative Teaching Methods for Supporting Students with Disabilities
Every child has the right to an education and to develop their skills, talents, and abilities to their fullest extent. To assist children in this quest, over the years educators have developed new and different ways of teaching children with diverse needs to ensure they receive the support they need to succeed in their academic journey. In this article, we will explore some of the transformative…

View On WordPress
#accessible learning resources#inclusive education#special education#Students With Disabilities#supporting students#Teaching Strategies#transformative teaching methods
0 notes
Text
Uuuuuh just to note: this is ablism.
The implication here is that to learn you must read. Yes it IS a skill distinct from other skills but no it has no universal educational benefits seperate from listening or watching.
Short form is a problem, yes; but no more so than short snazzy writing.
Different people respond to different media differently. Written books have no inherent superiority from documentaries in terms of ability of someone to absorb information, and some people will NEVER find this method of learning valuble. As for "listening"; audio books are absolutely no different from books.
This is snobbery and ablism masquerading as the revolution.
'you need to hone reading as a separate skill' is irrelevant. The ruling class benefits from IGNORANCE; you cannot sub in 'illiteracy'. It isn't the same thing. The ability to discern what source is good and the limits of the information one is receiving is by FAR a more valuable skill.
Not being able to read well can make a lot of things more difficult, but there is no moral or intellectual superiority in reading to having a screen reader do it.
The revolution doesn't benefit from this kind of narrow thinking. The idea short form information bites cannot be used in any way is also false, it can. It just ISN'T BEING. The impact on attention span is again a seperate issue from reading, one which tabloids have been exploiting aince the 1800s. Is there any particular educational advantage to reading rhe daily mail over watching news tiktoks? NOT REALLY, NO.
'Reading' is not a cure-all to society's ills.

"Absolutely no one comes to save us but us."
Ismatu Gwendolyn, "you've been traumatized into hating reading (and it makes you easier to oppress)", from Threadings, on Substack [ID'd]
#having a bunch of books to give to people is good#spreading out information about how watching short form entertainment worstens attention spans is also good#this isn't either of those#it's pretending to be but it isn't#it's literary snobbery and ablism#if literacy was all it took booktok wouldn't be a hellscape#but as it is there is absolutely no evidence to support 'reading' as a higher form of interaction#discernment isn't found by reading books#it's a seperate skill that you hone#which is so ironic#you don't hone it just by picking thinfs up randomly and reading them#many people have discovered things through youtube esseys that they would never have read#many people are incredibly well educated through listening#your skill may be unique#but it isn't special#and we as a society have a problem with alternative methods of education which are not 'make people read'#and accessibility of books in other formats#so it;s not harmless#ablism#reading#please stop fetishizing infirmation intake methods ty
178K notes
·
View notes
Text
Advice from one trans woman to hopefully others:
keep an eye on your own blood test results, educate yourself on the ideal feminizing range, if your numbers are not reaching a feminizing range ask for a dosage increase or a change to another method such as injections. It took me WAY TOO LONG to hit the numbers I wanted to be in because I wasn’t advocating for myself. And I have a good trans friendly doctor! I just wasn’t saying, for myself, “I want to go on injections” until I hit the dosage limit of patches and started to get depressed that nothing was happening! It was only around then I started looking at my own blood tests and realizing how far out of the range for feminization I was! And then I bit the bullet and learned how to do my own injections. And now I’m seeing changes again and I feel good about my transition for the first time in like a year.
This isn’t even malice on my doctor’s part I’m just dealing with someone helpful but not a specialist, and that’s going to be the experience for a lot of y’all too just on accessibility. Please go over your own medical tests.
4K notes
·
View notes
Text
The Accessible Accessibility Checklist
For last semester’s Method Tool project, Joseph Giambi chose to focus on the Web Content Accessibility Guidelines (WCAG). He wanted to present them as a checklist in a way that a team could use to determine which guidelines they need to incorporate and track how accessible their product is.

There are two ways to organize the list of guidelines. When “WCAG” is selected, the guidelines are categorized by the WCAG’s principles, as on its website: Perceivable, Operable, Understandable, and Robust. When “Diverse” is selected, they are categorized by the diversity of disabilities: Auditory, Cognitive, Physical, Speech, and Visual.

In either case, each guideline has a checkbox and a clear visual indication of which level—A, AA, or AAA—it meets. Guidelines can be expanded for more detail and a link to the WCAG site.

The list can be filtered by level and by tags that represent other categories, such as tables, forms, and video. This makes it relatively easy to find the guidelines that apply to the specific UI you are working on. Additionally, each of the filters and categories displays completeness by percentage, so you can see how robust your coverage is.

Joseph also included a dashboard view so that you can see your overall progress at a glance.

Joseph has designed a very robust tool with a minimalist aesthetic that seems perfectly suited to the content. He shows a very mature sensibility that I wouldn’t expect from an undergraduate student. This was truly outstanding work.
1 note
·
View note
Text
୭🧷✧˚. ᵎᵎ 🎀 As a broke devotee I don't possess many methods of divination for communicating with the deities. While I do have my oracle deck - I thought it important to have multiple means of divining! I realized that this may be the case for others sooo... Here are some other free and accessible tools I use~;
Labyrinthos App - My Favourite! (Has tarot, runes and lenormand for daily readings and has tons of educational content for you to learn divination.)
Coins - Nothing more simple then a coin flip, I flip a 2 dollar coin for yes or no readings!
Dice - This one is more personal and fun! you can put different answers for each side of the dice and just roll!
୧ ‧₊˚ 🍓 ⋅ ☆ I strongly suggest checking these if you're in a similar place!
#helpol#hellenic polythiest#hellenic pagan#hellenic deities#hellenic gods#hellenic worship#hellenic polytheism#divination#tarot#oracle
467 notes
·
View notes
Note
Can essential oils be an MCAS trigger?
I'm a religious educator at my local Unitarian Universalist congregation. We're a scent-free community. When I asked around about the details, (should I use unscented soap on work days?) my co-workers didn't seem very confident in their answers. Someone said it's only artificial fragrances, and they wear essential oils all the time, but someone else said it's all fragrances.
Really, I think my congregation could use some more information about different people's scent-free needs.
Thank you for asking!
Anything can be a trigger for MCAS, natural or synthetic. I have anaphylactic reactions to some essential oils if they are in the air. Scent free should mean scent free, not “unless we think they are natural enough.”
Also, unless explicitly stated about the method of extraction, most essential oils people pick up in the grocery store are synthetic. There is zero regulation on the essential oil industry which is primarily propped up at current by multilevel marketing schemes.
Essential oils have their uses, but they are overhyped and can be even more harmful to animals and small children than synthetic fragrances because of how strong they are.
If your community wants to be inclusive and accessible to everyone, scent free needs to mean 100%
354 notes
·
View notes
Text
Here's Trump's next target — according to the tyrant's playbook | by Robert Reich
Trump is following Putin’s, Xi’s, and Orban’s playbook. First, take over military and intelligence operations by purging career officers and substituting ones personally loyal to you.
Next, subdue the courts by ignoring or threatening to ignore court rulings you disagree with.
Intimidate legislators by warning that if they don’t bend to your wishes, you’ll run loyalists against them. (Make sure they also worry about what your violent supporters could do to them and their families.)
Then focus on independent sources of information: the media and the universities. Sue media that publish critical stories and block their access to news conferences and interviews.
Then go after the universities.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Last week, Trump threatened in a social media post to punish any university that permits “illegal” protests. On Friday he cancelled hundreds of millions in grants and contracts with Columbia University.
This is an extension of Republican tactics before Trump’s second term. Prior to Trump appointing her ambassador to the United Nations, former Representative Elise Stefanik (Harvard class of 2006) browbeat presidents of elite universities over their responses to student protests against Israel’s bombardment of Gaza, leading to several presidents being fired.
Senator Josh Hawley (Stanford class of 2002 and Yale Law class of 2006) called the student demonstrations signs of “moral rot” at the universities.
But antisemitism was just a pretext.
JD Vance (Yale Law 2013) has termed university professors “the enemy” and suggested using Victor Orban’s method for ending “left-wing domination of universities.”
I think his way has to be the model for us: not to eliminate universities, but to give them a choice between survival or taking a much less biased approach to teaching. [The government should be] aggressively reforming institutions … in a way to where they’re much more open to conservative ideas.”
Trump is also targeting diversity, equity, and inclusion programs on university campuses.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
But of all Trump’s and Republicans’ moves against higher education, the most destructive is the cancelation of research grants and contracts. The destruction is hardly confined to Columbia and other suspected left-wing bastions.
Research universities depend on funding from the National Science Foundation and the National Institutes of Health.
Trump reportedly aims to slash the budget of the National Science Foundation by up to two-thirds. And he’s instructed the National Institutes of Health to no longer honor negotiated rates for “indirect costs” on grants that it administers — money that universities use for laboratory space and research equipment.
In defiance of court orders, Trump has largely maintained a freeze on NIH funding.
As a result, many of America’s great research universities have stopped hiring and are cutting Ph.D. programs — in some cases rescinding offers to accepted students.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Trump’s moves are consistent with the tyrant’s playbook, but they’re also jeopardizing America’s national security and competitiveness.
Trump speaks of putting America First, but his attack on the nation’s great research universities is ensuring that the U.S. comes in second — to China.
Although America has long been the global leader in scientific output, China is now surging ahead. Even before Trump’s cuts in research funding, China was projected to match U.S. research spending within five years.
China has already surpassed the U.S. as the top producer of highly cited papers and international patent applications. It now awards more science and engineering Ph.D.s than the U.S.
Tyrants close universities. Fascists burn books. Trump is destroying America’s most important asset — its innovative mind.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
Robert Reich is a professor of public policy at Berkeley and former secretary of labor. His writings can be found at https://robertreich.substack.com/.
294 notes
·
View notes
Text
How to Make Money on Coinbase: A Simple Guide
Coinbase is a leading platform for buying, selling, and managing cryptocurrencies like Bitcoin and Ethereum. With millions of users worldwide, it’s a trusted choice for both beginners and experienced traders. Here’s how you can make money using Coinbase.
Why Use Coinbase?

Coinbase offers:
User-friendly interface: Ideal for newcomers.
Top-notch security: Advanced encryption and offline storage keep your assets safe.
Diverse earning methods: From trading to staking, there are plenty of ways to earn.
Ready to get started? Sign up on Coinbase now and explore all the earning opportunities.
Setting Up Your Coinbase Account
Sign up on Coinbase’s website and provide your details.
Verify your email by clicking the link sent to you.
Complete identity verification by uploading a valid ID.
Navigate the dashboard to track your portfolio, view live prices, and access the "Earn" section.
Ways to Make Money on Coinbase
1. Buying and Selling Cryptocurrencies
Start by buying popular cryptocurrencies like Bitcoin and Ethereum at a lower price and selling them when the price goes up. It’s the basic strategy for making profits through trading.
2. Staking for Passive Income
Staking allows you to earn rewards by holding certain cryptocurrencies. Coins like Ethereum and Algorand offer staking options on Coinbase. It’s a straightforward way to earn passive income.
Maximize your earnings—get started with Coinbase today and start staking your crypto.
3. Earning Interest
Coinbase lets you earn interest on some of your crypto holdings. Just hold these assets in your account, and watch your crypto grow over time.
Advanced Trading with Coinbase Pro
For those with more trading experience, Coinbase Pro provides lower fees and advanced trading tools. Learn how to trade efficiently using features like market charts, limit orders, and stop losses to enhance your profits.
Coinbase Earn: Learn and Earn
With Coinbase Earn, you can earn free cryptocurrency by learning about different projects. Watch educational videos and complete quizzes to receive crypto rewards—an easy way to diversify your holdings with no risk.
Coinbase Affiliate Program
Promote Coinbase using their affiliate program. Share your unique referral link (like this one: Earn commissions with Coinbase), and earn a commission when new users sign up and make their first trade. It’s a fantastic opportunity for bloggers, influencers, or anyone with an audience interested in crypto.
Want to boost your income? Join the Coinbase Affiliate Program now and start earning commissions.
Coinbase Referral Program
You can also invite friends to join Coinbase and both of you can earn bonuses when they complete a qualifying purchase. It’s a win-win situation that requires minimal effort.
Conclusion
Coinbase is an excellent platform for making money in the cryptocurrency world, offering various ways to earn through trading, staking, and affiliate marketing. Explore all its features to maximize your earnings.
Ready to dive in? Sign up today and start earning with Coinbase.
#coinbase#bitcoin#binance#ethereum#bitcoin news#crypto#crypto updates#blockchain#crypto news#make money on coinbase
542 notes
·
View notes
Text
It seems to me that the propensity of socialist orgs in the US to sink into covering up sexual abuse scandals emerges from the method of volunteerism that is basically universal in political organizing here. At a queer community center I used to be involved in, there was a long-standing member who had to stop going to events because their abusive ex-boyfriend ingratiated himself in the organization. My friend who is still on their board tells me that the people involved would mostly like the man gone, but begrudgingly put up with him because he is one of the most consistent volunteers, contributing far beyond what the survivor was themselves physically capable of. This is, of course, liberal nonsense, of the specific type that arises when the goal of hosting a pride event in the suburbs each year takes precedent over community empowerment. In short, it is opportunism. And whilst I haven’t personally witnessed an ML group mishandle a sexual abuse scandal, from the accounts I have read/heard, I suspect the mechanism is similar.
What I see “leftists”—including many self-proclaimed communists—in the US fail to grasp is that it is necessary for a revolutionary organization to always be building within the masses the social base for its action. A revolution cannot be made by a mere handful of dedicated individuals, and any organization running entirely off of the work of such few volunteers is treading on dangerously unstable grounds. Of course, dedicated individuals are still going to be important for an organization, but more important is a connection to the masses which allows such individuals to be found. In crude terms: everyone must be replaceable. This is for many reasons, not the least of which is that you have to be able to recall from power anyone who commits sexual abuse.
Ultimately this means that the actions of an organization shouldn’t go far beyond what the masses are themselves currently capable of accomplishing. Disruptive protests and union efforts are methods of struggle which are readily accessible to the masses, whilst education campaigns and community survival programs simultaneously increase the fighting capacity of the masses and also to deepen the party’s ties to the people. Even when the movement reaches the point of full revolutionary war, this can only be accomplished if the masses are at the point of being able to support a people’s army. Small guerrilla cells in communities with low class consciousness are perhaps able to frustrate/disrupt the capitalist state, but not overthrow it. When Newton and Seale founded the Black Panther Party, the tactic of armed patrols was decided upon as a means of demonstrating to the community how they could use the weapons they already possessed.
When an organization commits ultra-leftist errors, it risks isolating itself from the people not just ideologically but materially. The org leaps beyond where the people can/will follow, and, divorced from the motive force of history, inevitably stumbles and falls. The way to avoid this, of course, is for an organization to take proper stock of its present manpower, and to set actionable goals with an eye toward expanding their social base—the predominant method in US orgs, conversely, seems to be a sort of opportunistic ultra-leftism, where the active capacity of the masses is overstepped in service of symbolic/electoral goals which on their own do nothing to advance the political power of the working class.
Which . . . fuck. Typing that last sentence out really fills me with frustration and despair. What gives me the slightest bit of hope is reading about how these tendencies have manifested in the history of every attempted communist revolution, with the successful ones demonstrating not how to avoid such errors entirely, but how to overcome them!
373 notes
·
View notes
Text



₊˚⊹♡ education is hot!
education is literally the most valuable thing in life. please please PLEASE take advantage of that. self concept is important, good looks are important, happiness is important, health is important, but without education we wouldn't even know what any of that even means. ♡
having knowledge makes you magnetic. when you're smart, people will look up to you. and if people look up to you, it means they think about you, they admire you, and you have an influence on them.
life is knowledge. the more you learn, the more you are. knowledge is the fundamental basics to life. nothing is the root of everything but we wouldn't even know what nothing is without education. we wouldn't have language, we wouldn't have concepts, we wouldn't have technology, we wouldn't have the screen you're reading this on. we wouldn't have tumblr 😨

──★ ˙ ̟🎀 1. noting down ur findings
the smartest people ALWAYS note down what they learn, whether it be big or small. if you have lots of knowledge and / or the memory capacity of a goldfish then naturally you may not always remember what you learn. keeping it noted down in any preferably easily accessible format of your choice is so helpful and a very smart choice if you want to be an Intellectual™. notebook, sketchbook, binder, google docs, notion pages, tumblr posts, notes app, anything you like !!!!! just keep it noted down !!!! ♡
──★ ˙ ̟🎀2. utilising ur resources!!!!
so many people i know and millions of people throughout the world suffer with a crippling addiction to their phones, but what are you actually doing on said phone? you spend ages on your phone, your tablet, your laptop, reading, writing, playing video games, and so on, but even then, are you genuinely learning? are you taking the time to absorb the knowledge placed before you or are you skimming through it all in a mindless cycle of media consumption?
think about how you can utilise the things around you to learn. for example, make all that time spent on your devices useful. research, study, learn in your free time. knowledge is abundance. you can use your local library, your local bookshops, ur school or ur college or ur workplace just to find out more about your surroundings and about the world. it is so much more valuable thank you'd think.
──★ ˙ ̟🎀 3. wisdom
wisdom is the highest form of knowledge. to learn is to live so living is the only way you're going to truly learn, if that makes sense. therefore, by using this direct method, you gain the highest manner of knowledge; wisdom. wisdom is not being book smart or knowing how to solve equations or write essays but wisdom is genuine, pure, raw, life experience and life lessons, which, surprise surprise, can only be gained through experience and living your life. go out, try things, get out of your comfort zone, get comfy being uncomfy. you got this. ♡
──★ ˙ ̟🎀 4. social interaction
"nerds dont know how to socialise!!!" okay so maybe i adhere to this stereotype sometimes but social interaction is, however unfortunate it may be, a key part of being intellectual and having genuine knowledge. going back to wisdom and learning through experience, speaking with and networking with and sparking connections with others is a vital way to be educated and informed and cultured along with enhancing your social skills, because we need to know how to interact with others, too. if we can't spread said knowledge through connections and socialising so it can be passed down for hundreds of thousands for years to come then there is no point in learning at all because it'll have no use in the long run.
──★ ˙ ̟🎀 5. media consumption
feed ur brain. i cannot stress this enough. read books, fiction or non fiction. i know you've heard this a million times but it's true. read just a random article of interest every day to get your brain working. learn a new word every day, read news reports, letters, interesting blogs, articles, websites, do puzzles, crosswords, wordsearches, memory games, listen to podcasts, audiobooks, watch documentaries, youtube videos, interviews, ted talks, video essays, EXERCISE UR BRAIN
──★ ˙ ̟🎀 6. insights, emotional intelligence and empathy
as i've said before, and i'll reiterate again, knowledge extends beyond simply having book smarts and knowing how to work with letters and numbers. the most powerful method of communication amongst humans is emotion, and being well versed in how to read, understand and communicate said language is only learnt through real life experience and observation of real life experiences where the use of emotional intelligence and empathy come into play. analyse these experiences and note down everything
──★ ˙ ̟🎀 7. question ur sources and BE BOLD
one thing i was taught ever since i was little is that when ur online you need to be veeeery careful with all the information you get fed because there are lots of people out there, esp on the internet, with lots of different intentions and lots of different facts, even if they have good intentions and don't mean to mislead you. always double check whatever ur told with someone you know or on another website or two or a physical yet reliable source if you have one to hand, and cite your own opinions too. you get to choose what does and doesn't get to enter your mind. your mind and your knowledge is yours entirely and only yours to be tampered with and adjusted in any way you'd like.

──★ ˙ ̟🎀 things 2 study and be generally educated on:
social etiquette and politeness
countries and their respective laws, cultures, landmarks etc.
history of your own family and ancestry
languages you're interested in and basic phrases in several languages
information about your dream and / or current career
finances and how to manage your money
business, networking and persuasion
pet psychology and how to take care of them
capital cities and basics about places around the world, esp if you plan on going travelling
something beautiful about knowledge is that you'll never run out of it and it can never be taken away from you. people can take anything from you, but never your intelligence. ♡
all my love! 💖✨💘💗🎀💓

#not proud of my screen time today#(5 hours)#it is Not it my dudes.#i spent it wisely though!!!!!!#i was studying and writing and organising all my pinterest boards and spotify playlists and editing cute pictures................#if ur um. if ur intrestined. in. my stuff i make. go to. um. hue-hearts. my . silly little side blog#heavy are the thumbs that curate the girlblog#it girlism ୨𖹭୧#girlblogging#it girl#wonyoungism#girlhood#pink pilates princess#girly tumblr#this is what makes us girls#girly stuff#im just a girl#girlcore#girlworld#girl code#girl therapy#girl thoughts#girl things#this is a girlblog#pink academia#pink blog#study tips#study motivation#studyblr#study blog
717 notes
·
View notes
Text
SOURCE
Bit of a long video but worth a watch.
TL;DW though is that hidden in the Terms and Conditions for Google's AI Labs is a nice little poison pill that says they get access to your entire Google Drive if you opt in.
So if you're an author of some type and you keep your unpublished works in your G-Drive that means an AI will get to scrape all of it and by opting in you will have given them permission to it. The content creator goes on to predict that Google is going to let out their own streaming service where the scripts, and potentially the art if it's animated, will be almost or entirely AI generated using that scraped data as a baseline and the authors/artist's who's work was essentially stolen in its most raw form to crib from will have zero way of fighting Google on that in our current legal system.
This is of course right in the middle of the writers and actors strike where we're seeing just what lengths studios will go to in order to screw everyone but themselves.
They go on to recommend that if you keep any creative or personal works on Google Drive that you pull it off as soon as possible and delete your entire Drive. They acknowledge that of course this doesn't mean Google really deleted the data but if you do it before they start compulsory opting everyone in there's a chance your work might get overlooked. They also recommend several free editing programs that aren't run by corporations like Google with LibreOffice (the default office program of most Linux distros) being named.
Finally they go over methods of shaming Google which I feel like you just have to watch for comedies sake so I won't describe them in full.
Now this is from me: I know the majority of people don't have the ability to build and manage a big archive just for themselves, but if you're a creative NOW IS THE TIME to educate yourself on what you can do to protect your works. Cloud storage was always iffy at best, but with AI scraping entering the mix it's now downright malignant. Get a bunch of thumb drives, buy some external hard drives, if you have the money buy a pre-built NAS, and if you really want to get into learn how to build your own NAS. These are the old ways before cloud and they're coming back again, more important than ever.
#google#google docs#google drive#ai scraping#ai theft#ai generated theft#wga strike#wga solidarity#sag aftra#sag strike#libreoffice#google is cringe#delete your Google docs#embrace local back-ups
2K notes
·
View notes
Text
New better education template just dropped. I can't imagine how much anxiety that must alleviate for so, so many. Kudos to the prof.
my prof just explained on the syllabus that he’s included more pionts in the class than we needed to pass, so we could skip up like?? 20 small assignments/quizzes/participation!! and still get a very high grade!!
the idea was that we could focus on assignments that played to our strengths - only do the participation stuff if we like to talk out loud - only do the quizzes/readings if we want to do the class remotely - only do online discussions if we like to talk and share opinions but struggle with anxiety in class ect.
and that’s cool enough but then he pulled up DnD character sheets with drawings he’d done of these hypothetical student player classes and how our various accessibility needs could be gamified to ‘max out’ different aspects of the class to get high grades and like!!!!!
hell yeah!!!! let’s treat accessibility in higher education not just as a necessity but as the fun, engaging, and creative aspect of learning that it is!!! I love this!!
#education#dnd ftw#accessibility#different learning methods#everyone absorbs information differently#wonderful teacher
79K notes
·
View notes
Text
How to Donate to the Domari Society of Gypsies in Jerusalem
As many of you may know, the Domari community in Palestine is suffering alongside native Palestinians in the genocidal campaign headed by Israel.
Though we do not know much of the Domari's struggles in detail, I can only imagine it is the same extent as the Palestinians' struggles.
The Domari Society was founded by director Amoun Sleem in 2000 and since then she and her staff have done incredible things for the Domari, including providing resources and education to women and children.
On the Domari Society website, there is information on how to send donations via bank transfer, but considering that their main avenue may not be the most accessible to share and donate, I am making this post providing a step-by-step guide on how to donate to the Domari Society of Gypsies in Jerusalem.
This method works only if you have a PayPal and/or Xoom account (Xoom is owned by PayPal so if you only have PP, you can still donate.)
Step-by-Step:
Click this [link] here. It will take you to Xoom's page for sending money to Israel (Jerusalem is occupied by Israel, so it must be through them). Make sure you are signed in to either Xoom or PayPal.
Enter a minimum amount of 35.66 shekels (minimum 10.01 USD) to send. Click (Send Now) to progress to the next page.

3. Confirm information on screen and click (Next).

4. Select (Bank Deposit) and click (Next).
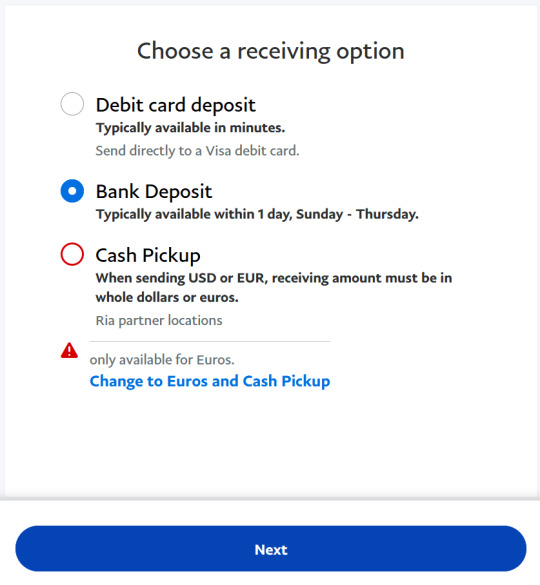
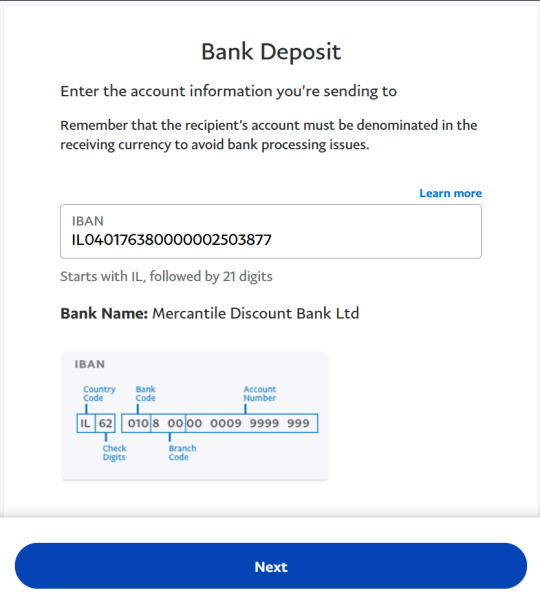
5. When selecting a bank, click (Other) and it will bring you to a page where you must enter the IBAN number of the bank you want to send money to. The IBAN for the Domari Society's bank is IL040176380000002503877 (copy and paste this exactly). Confirm that the bank is Mercantile Discount Bank Ltd and click (Next).
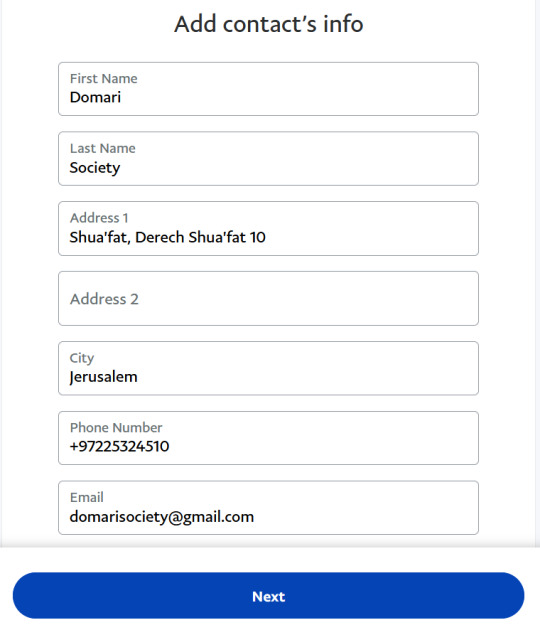
6. Enter in contact information. It is as follows: First Name: Domari Last Name: Society Address 1: Shua'fat, Derech Shua'fat 10 City: Jerusalem Phone Number: +97225324510 Email: [email protected]
7. Enter any information required and choose your payment option. On the last page, confirm the information listed and if everything is correct, click (Send).
Bank transfer may take a few days, but congratulations! You just donated to the Domari Society of Gypsies in Jerusalem. Know that your contribution will go towards the betterment of the Domari in Palestine.
Also, most information is found on the Domari Society's website, so if you wish to confirm that the donation is legitimate you can check the bank details here: [link]
Please share this whether you donate or not, it could mean life or death for Dom under occupation. May we all see a day where our people are safe. Te aven baxtalo 💙❤️💚
#palestine#free palestine#romani#roma#domari#rromani#rroma#im sorry that this is so long but i just want to make it easier for people to help#even if you send the minimum know that your contribution will save and better lives
808 notes
·
View notes
Text
In the span of just weeks, the U.S. government has experienced what may be the most consequential security breach in its history—not through a sophisticated cyberattack or an act of foreign espionage, but through official orders by a billionaire with a poorly defined government role. And the implications for national security are profound.
First, it was reported that people associated with the newly created Department of Government Efficiency (DOGE) had accessed the U.S. Treasury computer system, giving them the ability to collect data on and potentially control the department’s roughly $5.45 trillion in annual federal payments.
Then, we learned that uncleared DOGE personnel had gained access to classified data from the U.S. Agency for International Development, possibly copying it onto their own systems. Next, the Office of Personnel Management—which holds detailed personal data on millions of federal employees, including those with security clearances—was compromised. After that, Medicaid and Medicare records were compromised.
Meanwhile, only partially redacted names of CIA employees were sent over an unclassified email account. DOGE personnel are also reported to be feeding Education Department data into artificial intelligence software, and they have also started working at the Department of Energy.
This story is moving very fast. On Feb. 8, a federal judge blocked the DOGE team from accessing the Treasury Department systems any further. But given that DOGE workers have already copied data and possibly installed and modified software, it’s unclear how this fixes anything.
In any case, breaches of other critical government systems are likely to follow unless federal employees stand firm on the protocols protecting national security.
The systems that DOGE is accessing are not esoteric pieces of our nation’s infrastructure—they are the sinews of government.
For example, the Treasury Department systems contain the technical blueprints for how the federal government moves money, while the Office of Personnel Management (OPM) network contains information on who and what organizations the government employs and contracts with.
What makes this situation unprecedented isn’t just the scope, but also the method of attack. Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks. The Chinese government’s 2015 breach of OPM was a significant U.S. security failure, and it illustrated how personnel data could be used to identify intelligence officers and compromise national security.
In this case, external operators with limited experience and minimal oversight are doing their work in plain sight and under massive public scrutiny: gaining the highest levels of administrative access and making changes to the United States’ most sensitive networks, potentially introducing new security vulnerabilities in the process.
But the most alarming aspect isn’t just the access being granted. It’s the systematic dismantling of security measures that would detect and prevent misuse—including standard incident response protocols, auditing, and change-tracking mechanisms—by removing the career officials in charge of those security measures and replacing them with inexperienced operators.
The Treasury’s computer systems have such an impact on national security that they were designed with the same principle that guides nuclear launch protocols: No single person should have unlimited power. Just as launching a nuclear missile requires two separate officers turning their keys simultaneously, making changes to critical financial systems traditionally requires multiple authorized personnel working in concert.
This approach, known as “separation of duties,” isn’t just bureaucratic red tape; it’s a fundamental security principle as old as banking itself. When your local bank processes a large transfer, it requires two different employees to verify the transaction. When a company issues a major financial report, separate teams must review and approve it. These aren’t just formalities—they’re essential safeguards against corruption and error.
These measures have been bypassed or ignored. It’s as if someone found a way to rob Fort Knox by simply declaring that the new official policy is to fire all the guards and allow unescorted visits to the vault.
The implications for national security are staggering. Sen. Ron Wyden said his office had learned that the attackers gained privileges that allow them to modify core programs in Treasury Department computers that verify federal payments, access encrypted keys that secure financial transactions, and alter audit logs that record system changes. Over at OPM, reports indicate that individuals associated with DOGE connected an unauthorized server into the network. They are also reportedly training AI software on all of this sensitive data.
This is much more critical than the initial unauthorized access. These new servers have unknown capabilities and configurations, and there’s no evidence that this new code has gone through any rigorous security testing protocols. The AIs being trained are certainly not secure enough for this kind of data. All are ideal targets for any adversary, foreign or domestic, also seeking access to federal data.
There’s a reason why every modification—hardware or software—to these systems goes through a complex planning process and includes sophisticated access-control mechanisms. The national security crisis is that these systems are now much more vulnerable to dangerous attacks at the same time that the legitimate system administrators trained to protect them have been locked out.
By modifying core systems, the attackers have not only compromised current operations, but have also left behind vulnerabilities that could be exploited in future attacks—giving adversaries such as Russia and China an unprecedented opportunity. These countries have long targeted these systems. And they don’t just want to gather intelligence—they also want to understand how to disrupt these systems in a crisis.
Now, the technical details of how these systems operate, their security protocols, and their vulnerabilities are now potentially exposed to unknown parties without any of the usual safeguards. Instead of having to breach heavily fortified digital walls, these parties can simply walk through doors that are being propped open—and then erase evidence of their actions.
The security implications span three critical areas.
First, system manipulation: External operators can now modify operations while also altering audit trails that would track their changes. Second, data exposure: Beyond accessing personal information and transaction records, these operators can copy entire system architectures and security configurations—in one case, the technical blueprint of the country’s federal payment infrastructure. Third, and most critically, is the issue of system control: These operators can alter core systems and authentication mechanisms while disabling the very tools designed to detect such changes. This is more than modifying operations; it is modifying the infrastructure that those operations use.
To address these vulnerabilities, three immediate steps are essential. First, unauthorized access must be revoked and proper authentication protocols restored. Next, comprehensive system monitoring and change management must be reinstated—which, given the difficulty of cleaning a compromised system, will likely require a complete system reset. Finally, thorough audits must be conducted of all system changes made during this period.
This is beyond politics—this is a matter of national security. Foreign national intelligence organizations will be quick to take advantage of both the chaos and the new insecurities to steal U.S. data and install backdoors to allow for future access.
Each day of continued unrestricted access makes the eventual recovery more difficult and increases the risk of irreversible damage to these critical systems. While the full impact may take time to assess, these steps represent the minimum necessary actions to begin restoring system integrity and security protocols.
Assuming that anyone in the government still cares.
184 notes
·
View notes