#Physical Identity and Access Management share
Explore tagged Tumblr posts
Text
#Physical Identity and Access Management market#Physical Identity and Access Management market size#Physical Identity and Access Management share#Physical Identity and Access Management trends#Physical Identity and Access Management analysis#Physical Identity and Access Management forecast#Physical Identity and Access Management outlook#Physical Identity and Access Management overview
0 notes
Text
DARK SMS - DRAGON+

In today’s fast-paced digital landscape, maintaining privacy and security while communicating is more important than ever. Introducing DarkSMS, a cutting-edge virtual SMS platform designed to streamline your messaging experience without compromising your personal information. With our innovative virtual number service, users can receive SMS messages securely and anonymously, eliminating the risks associated with sharing private phone numbers. Whether you’re signing up for online services, verifying accounts, or simply looking to keep your communication confidential, DarkSMS has got you covered.
Virtual SMS
Virtual SMS refers to the messaging service that enables users to send and receive text messages through a virtual phone number rather than a traditional mobile line. This service is particularly useful for individuals and businesses looking to maintain privacy while communicating or verifying accounts.
One of the key advantages of using virtual sms is the ability to receive SMS without revealing your personal phone number. This is especially beneficial for online transactions, sign-ups for apps, or any situation where you might need to provide a phone number but want to protect your privacy.
Furthermore, virtual numbers can be easily managed from a web-based platform, allowing users to organize and store messages effectively. Many service providers offer features such as message forwarding, where received SMS messages can be redirected to your email or other platforms, ensuring you never miss an important notification.
In addition to privacy and convenience, virtual SMS services are often cost-effective. They eliminate the need for extra SIM cards or mobile contracts, allowing users to only pay for the services they actually use. This flexibility makes virtual number services highly attractive for startups and individuals working from remote locations.
As businesses increasingly adopt digital communication strategies, integrating virtual SMS into their operations can enhance customer interaction and improve engagement through instant messaging capabilities.
Virtual Number Service
A virtual number service offers a practical solution for individuals and businesses looking to maintain privacy while receiving communications. By using a virtual number, you can receive SMS messages without exposing your personal phone number. This feature is especially useful for those engaged in online transactions, such as e-commerce, as it safeguards against unwanted spam and protects your identity.
One of the key advantages of a virtual number service is its capability to function seamlessly alongside your primary phone line. Users can receive messages from various platforms effectively, whether it's for verification purposes, two-factor authentication, or simply keeping in touch with clients. The convenience of managing multiple numbers through a single device cannot be overstated.
With options to select numbers from different geographic locations, this service caters to users looking to establish a local presence in different markets. Moreover, these numbers can be set up quickly and easily, providing instant access to receive SMS without lengthy contracts or commitments.
To optimize your experience with virtual SMS and virtual number services, consider features like call forwarding, voicemail, and the ability to choose your own number. Such functionality enhances user experience by offering flexibility in communication while maintaining professional boundaries.
Ultimately, investing in a virtual number service can significantly enhance your business's communication strategy, allowing you to receive SMS reliably while focusing on building relationships with your clients.
Receive SMS
Receiving SMS through a virtual number is a convenient service that allows users to get text messages without needing a physical SIM card. This is particularly beneficial for individuals and businesses looking for privacy or those who wish to avoid exposing their personal phone numbers.
The process is straightforward: once you obtain a virtual number through a reliable virtual number service, you can start receiving sms messages. This service is essential for various reasons, including:
Account verification codes: Many online platforms use SMS to send verification codes. A virtual number allows you to receive these codes securely.
Business communications: Companies can use virtual SMS to receive client inquiries or feedback without revealing their primary contact numbers.
Privacy protection: By receiving SMS through a virtual number, users can protect their personal phone numbers from spam and unwanted solicitation.
Moreover, the get SMS feature of a virtual number service ensures that you don’t miss any important messages, even if you are on the move. Messages are often stored digitally, which means you can access them anytime and anywhere.
In summary, the ability to receive SMS through a virtual number enhances both privacy and accessibility, making it a valuable tool for users in various contexts.
Get SMS
Getting SMS messages through a virtual number service has become increasingly popular due to its convenience and versatility. Whether you need to receive texts for verification purposes or want to maintain privacy while communicating, virtual SMS provides a robust solution.
With a virtual number, you can easily get sms from anywhere in the world without needing a physical SIM card. This feature is particularly beneficial for businesses that require secure communication with clients or customers, as it ensures that sensitive information remains confidential.
Here are some advantages of using a virtual number to get SMS:
Privacy Protection: Using a virtual number helps keep your personal phone number private.
Accessibility: You can receive SMS messages on multiple devices, including tablets and laptops.
Cost-Effective: Virtual SMS services typically come with lower costs than traditional SMS plans.
Global Reach: You can get SMS messages from international numbers without incurring roaming fees.
Easy Setup: Setting up a virtual number to receive SMS is straightforward and often takes just a few minutes.
In summary, leveraging a virtual number service for SMS communication allows you to manage your messages efficiently while maintaining privacy, enhancing accessibility, and reducing costs. This is particularly useful for both personal and business communications, making it a smart choice for anyone looking to streamline their SMS functions.
631 notes
·
View notes
Text
Tokyo Debunker Stigmas, Artifacts, And Other Possibly Combat Relevant Information
Since we've met all of our current ghouls, I decided to share my non-comprehensive list of the stigmas and powers and weapons of the ghouls we've seen so far!! This isn't all of them because they haven't all been revealed or explained. But it should be everything we've seen so far! Let me know if/where I've missed things! I've also mentioned some other details for some of them, namely the less human ghouls.
Updated for: Episode 14
Jin Kamurai
Stigma
Incantation - Bianerus
Effect - forces the target to obey his command.
Currently cannot be activated without the PC's enhancement. At present, only Tohma, the PC, and few if any others know this.
Incantation can be recited mentally
Continuous commands("kneel") only seem to last a few minutes at most
Artifact
Sword - teleportation
Can be used to cut a portal into the air for teleporting someone with him, but doesn't appear to need this for just teleporting Jin
Teleportation takes more time depending on the distance from his current location to his target location
Jin is able to throw it quite precisely despite its size
Tohma Ishibashi
Stigma
Incantation - Argeas
Effect - "lets him send vibrations long distances"
Vibrations include the vibrations from his voice, allowing his voice to carry longer distances, making him heard further away
When enhanced he can break through anomalous soundproofing and better specify the direction his vibrations carry(as neither Kaito nor Luca heard his voice from outside the room)
Artifact
Halberd - ?
Able to tremble on its own. How much else it can move on its own is unclear.
Tohma claims it has a "troublesome" nature, and seeks to mow down anything in its path when it senses conflict and it takes a lot of effort to keep under control
Other
Tohma naturally has "brute strength" which, combined with his stigma, allows him to essentially make earthquakes.
Tohma has the trust of Darkwick, allowing him to easily get access to powerful common artifacts such as the skeleton key
Tohma takes alprazolam, "a fast-acting benzodiazepine used as both an anti-anxiety drug and a muscle relaxer. Used to manage anxiety, depression, insomnia, and physical symptoms caused by psychosomatic disorders." Tohma claims he takes them for headaches. Leo says they're very addictive and that Tohma has them refilled more often than is usual for headaches. It seems he's blackmailed a Mortkranken student into letting him have them. It's unclear if this is meant to be a sign of addiction or if they're actually necessary.
Tohma says he has "many attentive attending physicians" which may suggest some form of chronic medical problem.
Lucas Errant
Stigma
Incantation - Iggnaim
Effect - creates a barrier.
When enhanced the barrier becomes visible. It's significantly larger and supported by a large anomaly that's invisible to everyone but the PC and perhaps Kaito, even unable to be seen on cameras or by Luca himself.
The barrier doesn't appear to need to be around Luca specifically, as he protected Nina with it despite not being next to her. However it's uncertain how far he can project it as he was in the same room and for near her quickly to fight the Dullahan.
Artifact
Twin blades - ?
Appear identical aside from a difference in color.
Smashed through reenforced glass to choose him as their new master.
Apparently sound to Luca like a crying child. He believes the child must be begging for his help.
Other
Carries around a knife.
Kaito Fuji
Stigma
Incantation - ? (has an audio file, but the spelling hasn't been shown.)
Effect - "can see auras sometimes"
Does not need to be activated with his incantation, but appears to activate at random.
Auras have different colors for different people, allowing him to discern if an entity is the person they appear to be or not.
Hyde didn't sound certain about what it does.
Kaito has notably enhanced vision, able to see things that are further away and surprisingly makes him skilled at reading lips.
Kaito screams when Luca's stigma is enhanced, looking straight up at the anomaly it spawned despite no one else but the PC appearing to see it. While it's possible he only saw its aura, it's likely he saw the anomaly itself.
Artifact
Rogue bow - ?
Produces magic arrows that veer nonsensically off path when shot, except, seemingly, if there's a malicious or threatening target(?) at which point it will veer to save an endangered target(such as the ghost boy being taken by the arms) and/or go directly for the source of a threat or malice(such as the faceless anomaly about to attack the PC and Riku, the glowing grave of Natalie Hunt, or the mirror affected by the Mirror of Melancholy that was showing his grandmother.) When the magic arrow hit the glowing grave it "blew the whole thing apart." The same happened when it struck the mirror.
Other
Pretty acrobatic despite not training, flipping and cartwheeling across the graveyard to dodge the ghostly arms trying to grab him.
Alan Mido (Alan Todoroki)
Stigma
Incantation - Yagsal Olbalsa
Effect - ? "Seems to be an extremely dangerous ability" -B's Log
Seems to enhance his strength, as he punched Takeru's tulpa in half
Seems to make him uncontrollably violent, seeking to kill his enemies(looking for Takeru's tulpa's head and crushing his throat) and possibly reduces his awareness of his surroundings(light removed from the eyes of his sprite and panel art, grabbing and pulling the PC without realizing he was hurting her, continually attacking Takeru despite being aware he couldn't take him out with punching, only regaining his senses when Sho grabbed and spoke to him)?
Artifact
Lead pipe - ?
Leo Kurosagi
Stigma
Incantation - Haxs
Effect - super hearing.
Increases distance and precision of his hearing. Does not allow him to hear through anomalous soundproofing.
When enhanced increases distance further and allows him to hear through anomalous soundproofing.
Had the PC enhance it in order to find the escaping possessed guard during the prison riot. Uncertain if this allows him to hear ghosts or if he simply needed the increased precision due to the surrounding noise.
Makes Leo sensitive to sounds and noise even when it isn't active, resulting in noticing noises other people can't hear and frequent complaints when in noisy environments or around loud or high-pitched people.
Artifact
Bubble gum - can be manipulated into any shape when blown.
The longer it's chewed, the longer he can manipulate it
"So if I chewed this one a bunch and stuck it over your nose and mouth...
"...you'd suffocate. Bye bye Honor Roll."
suggests that it can't be removed until the time he's manipulated it runs out?
Cannot capture incorporeal targets.
Popping it can cause some form of damage, such as when he destroyed a Cyclops Eye in the staff room after covering it with the gum.
Shohei Haizono
Stigma
Incantation - Spurno
Effect - "just jams stuff"?????
Primarily seems to push things or result in change of direction, possibly able to cause sensory scrambling resulting in uncoordinated movement or temporary stunning(as with Takeru's tulpa?)
Leo says it can be used on incorporeal targets, but Sho says it can't take something down unless it's "super weak"
Used in Episode 2 to prevent Takeru's tulpa from walking straight
When enhanced in Episode 2, pushed Takeru's tulpa back with greater force, but didn't push him away, or cause him to release the PC(stunned him?)
Used in Episode 12 to remove the ghost of the prison guard possessing Alan and push the ghost into a cell to lock it there until it moved on
Artifact
Motorcycle - ?
Her name is Bonnie. She eats food placed in her fuel tank instead of gasoline, including chewing it and even burping. She's picky about what she eats. Her favorite food is barbecue sandwiches, but she also eats jerky.
If she isn't fed three times a day "she gets sulky and refuses to start." Her engine won't start at all if she's hungry.
She's described as a "large motorbike" by the PC's narration, and Subaru apologizes for the amount of space he's taking up on the wharf in Hotarubi to feed her, corroborating this.
She seems to have some control of her own movement as Sho rewards her for staying upright when stopped and made to buck by Luca's barrier.
Sho drives her just about everywhere and drives her around at Leo's request as well. She has a travel permit that needs to be shown when leaving and reentering campus, however she's able to break through the checkpoint with enough speed.
She's kept on her artifact chain when not ridden.
She's able to comfortably be ridden by two people but three is very tight.
Haru Sagara
Stigma
Incantation - Bahnti
Effect - reduces gravity's effects on his own body.
Reduced effect of gravity allows him to move extremely fast.
Makes his body much more fragile when used. Possibly includes weakening his immune system?
Artifact
Deck brush - ?
He rides around on it while distracting Otohime, skidding across the floor on the brush until he tips over.
Other
Right arm has been replaced with a prosthetic from Mio Susuhara after being broken by "Gen"(presumably Shion Genkai) which is currently damaged after he caught Ritsu's camera with it. Because of the current extent of the damage he was unable to perform labor tasks that require it.
Towa Otonashi
Stigma
Incantation - ? (has an audio file, but the spelling hasn't been shown.)
Effect - Controls wind and weather(?)
Towa exhibits control over weather as his primary ability, and he confirms it's his stigma when the PC asks in Episode 12.
Others' understanding of Towa's stigma is only that he controls lightning and that other weather patterns are random, not in response to Towa's feelings.
The weather reacts to Towa's emotions, causing the sky to darken in preparation of rain, lightning, or snowstorms when he's angry.
Towa is also able to predict weather that he doesn't control.
Towa can create lightning(which he uses to electrocute enemies), rain, wind(used to create a pillar of water for the PC to land on when falling off the boat, a whirlwind for gathering ducks, and to direct the rain sideways to wash bubble soap off of Kaito), snow, and possibly earthquakes(the ground is noted to start shaking in response to his anger.)
He 'rides the wind' in order to jump high as though flying
Artifact
Bubble wand - blown bubbles cause explosions.
The explosions are powerful enough to destroy glass that withheld a full grown Kraken.
Towa warns not to touch the bubbles, as they will kill you.
Not all bubbles seem to cause explosions as he blows bubbles from atop the Capybus without there being any harm done.
Other
Towa's nature is implied to actually be quite malicious and uncaring, especially towards things that are weak and especially towards humans, however he claims he changed because of "love." Several home screen lines, his full awakening line, and his response to being touched by the turtle anomaly in the Dragon Palace support that he hasn't fully changed his mindset, only represses it.
Towa cannot speak during the daytime and is only able to talk when it's night. This includes being in Obscuary, where it's permanently night, however the cover of clouds doesn't allow him to speak during the day meaning it's not related specifically to the visibility of the sun. However this is drawn into question when the presence of the giant cat anomaly in Episode 12 casts a shadow over him, briefly allowing him to speak.
Can speak to and understand anomalies, even those that lack speech capabilities(such as the tree on the hill.) Haru is aware of this ability.
Able to see and hear ghosts(Zenji) and possibly other things that only people who are "special" can see(the tree on the hill, which even Ed cannot see.)
When Towa is away from Jabberwock for an extended period of time(in Episode 4 it happened after 24 hours) the nature conditions deteriorated significantly, with water drying up and the sky dark despite it being sunny the previous day and the anomalies beginning to behave violently. According to Ed, if Towa is away from Jabberwock for too long the anomalies within will begin to die. Ed suggests that Haru is unaware of this fact. In Episode 12, despite being away for 3 days, this doesn't appear to happen.
Anomalies fear him and obey him, particularly when he's angry, even to the point of kneeling out of fear when he's furious. Normal animals experience the same fear, freezing and behaving anxiously in his presence.
Says the PC smells nicer than before, perhaps able to smell their curse's advancement due to the flowers that would grow on her as a Kyklos.
Ren Shiranami
Stigma
Incantation - Raothtas
Effect - Cleans things?
B's Log: "According to him it seems to be a power with little use."
Has only been used to remove Calamari's ink from the floor when wiping it up failed.
Artifact
Swim ring - restrains target.
Cannot be removed by the wearer.
Has a rope attached that allows the wearer to be reeled in.
Cannot restrain incorporeal targets.
Taiga Hoshibami
Stigma
Incantation - Malab
Effect - ?
Artifact
Tommy gun - takes anything broken into small enough pieces and fired from it as ammo.
Damage type seems to vary based on what was placed into it. Shards of glass created a swirl of glass shards, whereas bronze from a statue shot heavier rounds.
Doesn't seem to require ammo to fire.
Doesn't seem to work on everything as Taiga says his bullets don't work on anything lately. Possibly limited to hostile entities? (He was able to shoot the Oblivion Dealer, but not able to shoot the Kyklos--which ran away--or the Barong--which was non-threatening.)
Other
Carries a knife and a pistol.
Appears to occasionally be aware of things that he has no way of knowing about, sometimes even seeming to know the future. Haru asks hin when several characters are returning, which suggests Haru is aware of this and occasionally asks him to predict outcomes.
Taiga asks Haru for a coin, saying he'll allow Haru to choose his desired outcome based on heads or tails. However it's uncertain if this means he can actually alter outcomes himself. His losing dialogue suggests that he attempts to, but doesn't always succeed.
Eats anomalies, though not exclusively, and gets hungry whenever he goes on a mission. His hunger for them results in varied behavior from minor irritation to nearly losing control of himself to the hunger. He can eat any physical anomaly thus far, being shown or referenced to eat anomalous animals, plants, objects, and "enzymes", and he finds anomalous plants and enzymes converted into beverages suitable for human consumption to taste unpleasant. He eats normal food and drinks normal alcohol without a problem. It's difficult to tell how he feels about and after eating anomalies, as it varies, although he enthusiastically expresses his desire to eat the Kyklos. It's hard to tell how new this behavior is as Romeo seems disgusted but not surprised by it and Taiga attempts to warns Romeo when he wants to eat the Barong mask(not in speech bubbles but able to be discerned in his audio.)
His hunger may be able to be triggered or increased by smelling or seeing anomalous blood(such as the PC's.)
His memory is very poor, although he can remember things and people with prompting.
Romeo Scorpus Lucci
Stigma
Incantation - Tiris
Effect - "turns things into bombs".
Able to turn anything into a bomb, including non-explosive objects. Seems to require that he throws them?
The size of the blast depends on how attached to the target object its owner is. If Romeo truly values something he's blowing up, the explosion is quite destructive.
Hyde has him testing various types of prototype anomalous explosive materials for Darkwick on missions.
"To me, these prototypes are a path to catching anomalies in one piece." which implies most of Hyde's prototypes cause non-lethal explosions. One of his home screen lines mentions, for example, a tear bomb.
Artifact
Sniper rifle - ?
Maintains his bullets himself.
Doesn't always carry the same types of rounds. For example, he only had smoke bombs in the prologue.
When used against the Arachne in Episode 9 it blasted a large hole into its head? However when he fired it to gain the attention of the audience and when he shot at the door in Episode 8 the impact didn't seem as great, suggesting the impact/size of his bullets varies as needed.
Other
Has the trust of Darkwick(or at least has Hyde's favor?) allowing him to carry around common artifacts as though he owns them(hammerspace briefcase which he added a custom case for; fox robe)
Implied to be missing his right leg or foot (likely having been replaced by a prosthetic like Haru's.) Kaito mentions that Romeo cannot run fast. He also shows noticeable pain and discomfort after being run into by Kaito.
Ritsu Shinjo
Stigma
Incantation - Acimo
Effect - hardens his body. Increases his weight.
Prevents damage from concussive attacks such as kicks and bullets. If you kick him while it's active it'll hurt you.
Doesn't seem to experience pain in this state.
Can survive explosions and escape from collapsed buildings unharmed.
Artifact
Compendium of Laws - ?
Has the contents memorized?
Taiga taught him to use it as a blunt weapon, although he forgot he did this.
Appears to glow somewhat when held, although what this suggests is unknown.
Subaru Kagami
Stigma
Incantation - Talnandio
Effects - psychometry.
Experiences memory fragments through almost anything he touches or that touches him.
Passive, activates on contact with people, animals, anomalies, and objects without incantation.
Using it exhausts him to the point of needing a significant amount of rest, possibly even passing out shortly after usage.
Wears gloves and avoids crowded places to try and avoid accidentally setting it off. Feels bad about being able to learn people's secrets.
Artifact
Parasol - ?
Sturdy enough to destroy a possessed doll.
Haku Kusanagi
Stigma
Incantation - ?
Effect - ?
Implied he prefers not using it?
Artifact
Flute - ?
Used flute to remove himself and the PC from Kisaragi Station, knocking them out with some sort of ethereal water and causing them to wake up back on the empty train car.
Other
Able to see and communicate with spirits.
Able to perform various rituals such as laying spirits to rest and making talismans that allow people close to a spirit to see and hear them.
"Cordoned off the area" of the train and station the PC was on, which should have prevented interference from civilians. May be part of his Artifact or Stigma, or part of his capabilities as a Shinto priest.
Performs the stigma test for Darkwick.
According to Taiga he's able to remove curses if the anomaly that caused the curse is in front of him. It's uncertain if this is his stigma, part of his artifact, or another power.
Haku has the trust of Darkwick, allowing him to easily get access to powerful common artifacts such as the skeleton key
Zenji Kotodama (Taro Kirisaki)
Stigma
Incantation - ?
Effect - ?
Artifact
Doll - ?
Heavily resembles his brother as a child, according to Zenji. When Zenji and the doll protected Jiro, Zenji said "You've always been there for him when he needed it most." suggesting that there may have been a third Kirisaki brother.
Won't let anyone but Zenji and Jiro touch it. Protects Zenji and Jiro.
Appearance slightly changes to that of an oni when angered.
Has a mind of its own, or is perhaps possessed. Wanders around campus without Zenji, much to his concern.
Able to damage and destroy ghosts?
Joined Zenji in protecting Jiro from being eaten by the Arachne and seemed to be fine after the Arachne was destroyed while it and Zenji were inside it. Attacked the Arachne from within (with Zenji?) to distract it with pain so Jiro could attack it.
Other
As a ghost, Zenji cannot be touched, meaning he can't be damaged or killed. However he covers his ears when Haku performs a ritual to lay spirits to rest and covers his face in Subaru's warding card with incense, suggesting that he would be laid to rest under the right circumstances.
Zenji is not bound to Darkwick despite being a ghost who died on campus, and can come and go as he pleases.
Darkwick is unaware Jiro is present as only Haku and Towa(and eventually Subaru and the PC) are aware Zenji's spirit lingers. If Darkwick were to become aware of Zenji's presence they would want him laid to rest.
Due to Obon, people in Japan are more sensitive to spirits and anomalies are more frequent, causing Zenji to sometimes be visible or audible during the summer.
Zenji brings his doll with him most everywhere, however people can only see the doll and not him. The same happens with his biwa. If he carries them, they appear to float.
Zenji can touch physical objects(his doll, his biwa, and his phone) and his footsteps are audible if he doesn't silence them. He can ride the Galaxy Express as well. Because one has to show their phone to the conductor cat to take the Galaxy Express, it's probable that the cats can see or hear him and simply don't report him.
Afraid of ghosts, possibly the dark, and maybe dead bodies.
Edward Hart
Stigma
Incantation - ?
Effect - ?
Artifact
Cane - ?
Other
Edward is, or was historically, the world's strongest vampire, implying a great deal of hidden power. As he is 400+ years old, he knows a great deal about anomalies that Darkwick doesn't listen to for some reason. However being old has also made his body and mind much weaker. . .allegedly.
Ed has immense power, which we've only heard of him using on the singular mission he participated in. Using it he obliterated an anomaly and a building in such a way that Darkwick struggled to cover up(unlike Tohma's destruction which was able to be explained as poor maintenance and age) suggesting he more or less vaporized it. It's unknown if this is a vampire power or his stigma.
Ed is able to produce a purple mist that seems to be able to enthrall humans when inhaled(Rui and Lyca didn't need to hold their breaths when he used it but the PC did, suggesting it doesn't work on ghouls.) The PC mentions feeling "good", comfort, euphoria, her mind slowing down, light on her feet, and she began to think thoughts that aligned with what Ed wanted of her made and her body feel weaker. When she managed to fight against it and speak for herself Ed stopped producing the mist and she was able to recover quickly. When Ed used it on the humans in the mansion they experienced similar symptoms(feeling good and beginning to think they didn't need to call the police for help) but fell into sleep quickly unlike the PC. It is unclear whether or not this is his stigma or simply a vampire power.
Ed mentions on the home screen that there's a miasma in the garden of Obscuary that humans are susceptible to. He also mentions a miasma in the breeze during summer. It's uncertain if he's referencing the mist he produces, although it's unlikely in the second case as he mentions no desire to go outside.
If Rui touches him, the touched part will break off(at which point it can be reattached simply by pushing it back into place,) ache intensely for a time, or he will die temporarily.
As a vampire, Ed is immune to curses and is immortal. He claims that sunlight will eventually reduce him to ash and in the pre-prologue before jumping off of the balcony he implies that whatever is waiting for him at the bottom will be the death of him as well. One can become a vampire by drinking the blood of a vampire, and this will overwrite curses such as the Kyklos' curse. It's uncertain if this would overwrite Rui's reaper curse.
As a vampire, Ed is rapidly exhausted by sunlight. Sunlight won't kill him instantly, but it will cause him to collapse. He claims sunlight will turn him to ash eventually, and he cannot be outside in the sun without a parasol. If it's cloudy enough or he's in enough shade, Ed is able to be outside during the day. He's usually tired during the daytime, but still seems to sleep during the night.
Ed is physically and mentally weaker during summer months, but stronger during autumn and winter.
Ed primarily drinks tears, although he mentions that he does drink blood in his character story and on the home screen. He finds that human food doesn't taste like much of anything.
Ed is able to transform into a bat and fly around in that form. He doesn't seem to be able to speak in this form, only screeching and squeaking. Based on the campus chibis he may have bats as 'familiars' too.
Ed mentions that Lyca's soul is misshapen, however it's unclear if he can actually see his soul or if he was merely teasing him.
Ed cannot see the tree on the hill that Towa speaks to, but seems to be aware that something is there.
Rui Mizuki
Stigma
Incantation - ?
Effect - temporary relief of pain and discomfort
Incantation has only been said in his head.
It's unclear if blowing a kiss is required to activate it or if that's just for flair, but it did produce a gold smoke that applied to the hurt area.
Artifact
Scythe - allows Rui to conceal himself in darkness.
Rui admits to using his artifact to keep an eye on others on campus.
Other
Suffers from a 'Reaper Curse' which effectively makes him a reaper.
Cannot make skin contact with most living things without them instantly dying. This includes humans, animals, plants, and even mold! Sufficiently strong living things(such as Ed, a vampire) will not die instantly when touched, but most things are too weak to survive. On contact, the touched thing's life force is absorbed into Rui's body through his mouth as a sort of green smoke that emerges from them.
Absorbed life energy goes straight to his body, extending his life filling him with so much energy that it prevents him from sleeping. He keeps himself as busy as possible as a result of having so much energy to spare.
In the case of Ed the reaction we've seen in-game when he was touched was the touched limb popping off(resulting in a spray of blood.) On the home screen he mentions Ed simply dying temporarily on contact and Ed mentions places they accidentally touched aching nonstop. It's uncertain what other creatures are strong enough not to die right away and how they would be affected by contact.
Wears gloves, a turtleneck, and avoids crowded places to avoid committing manslaughter and killing anything he touches.
Lyca Colt
Stigma
Incantation - Ramsochisa
Effect - allows him to follow any scent he's smelled before.
Artifact
Claws - ?
Other
Half werewolf. Able to show or hide his wolf tail and ears at will, but they pop up when he's sufficiently aggravated.
Transforms with exposure to the full moon. "The speed of his transformation is affected by how much he's exposed to moonlight and his mental state." Sometimes feels his skin crawling when the full moon is near?
Covering his head when he's outside under the full moon prevents or regresses his transformation. Collapses after his transformation regresses from half wolf and doesn't transform while unconscious. Nothing happens to him if he's not exposed to the full moon on a full moon night. Obscuary is always a crescent moon, allowing him to be there safely during a full moon.
Werewolves have four stages: Human, partial wolf, half wolf, and full wolf. At 'half wolf' Lyca is an anthropomorphic wolf. However, he loses control of himself after he's been transformed for a while, and may attack indiscriminately.
He doesn't remember much when he transforms. He might remember less if he fully transforms?
Yuri Isami
Stigma
Incantation - Agnihaet
Effect - "hyperstimulates his braincells"
"allows him to logically process information and solve complex equations almost instantaneously."
when enhanced seemed to make the information processing instantaneous and extremely accurate?
Artifact
Syringe - ?
Jiro Kirisaki
Was used on Jiro before he fought the Immortal Inpatient. However because the reflected damage is because of Jiro's stigma it's hard to say what exactly the effect of Yuri's syringe is.
Other
Immune to Jiro's stigma for unknown reasons, allowing him to treat Jiro without taking damage.
Stigma
Incantation - ?
Effect - Reflects any damage sustained back onto the one who dealt the damage
Activates automatically and involuntarily in response to sustained damage, without use of an incantation.
Anything that is injected into him will also be injected into the person who injected it into him. The same with someone trying to poison him. If someone tries to open him with a scalpel they'll also be cut open.
Does not work on Yuri for some reason, which is why Yuri is the only one who can treat him.
Artifact
Chainsaw - ?
Blunt, making it a bad match for webs(which simply got stuck in it) and things that need sharpness for effective cutting, but able to 'cut' through more solid things that don't require sharpness or precision, presumably by just crushing them with the rapidly spinning dull blades.
Other
Jiro is noted to be especially strong.
Jiro was in a coma from Eternal Slumber Syndrome until an undisclosed time ago, when Yuri was able to awaken him from it. When he was comatose and for how long and why hasn't been relayed yet, however he was said to be particularly violent during The Clash, meaning he was likely awakened before or during it, or fell into a coma during/shortly after it.
As a side effect of his condition and mysterious illness, Jiro has a poor memory, immunodeficiency, and his wounds reopen very easily. He occasionally has focal seizures.
Jiro needs four treatments a day, and they take around an hour to complete. Yuri is the only one who can administer them, and Jiro isn't able to do so himself. Even with his treatments he's forgetful and prone to being sick and has a bit of a fragile constitution. Abrupt changes in temperature, for example, make him choke.
Jiro doesn't react much to his wounds and being in pain, but he will eventually collapse from overexertion or illness if he misses a treatment or has taken too much damage.
#tokyo debunker#i was gonna tag everyone but i got too tired lol#danie yells at tokyo debunker#tdb ref#maybe someday i'll edit it to include sources for everything and maybe screenshots#but probably not because that's a lot#okay it's past my bedtime and i have dailies to do so#good night lmao#i'm sure i've missed stuff because i didn't do a lot of going back to double check lol#but this should be everything we know so far from the english translation and maybe some of the japanese#we didn't really get an explanation for how the pc's enhancement worked on yuri because the guy just kinda got brainblasted and figured out#what to do immediately so i just kinda guessed#take note of question marks because that's where i'm not certain i guess lol#okay time for dailies and bedtime#hope we learn more about the missing info soon
601 notes
·
View notes
Text
“I wish I could share my pain with you, even for just a moment not to harm you, but so you could truly understand the suffering we endure as LGBTQIA+ individuals in the refugee camp.”
Life in the refugee camp is incredibly difficult for members of the LGBTQIA+ community, largely due to widespread homophobia. This hostility is evident in the daily threats and attacks we face from both fellow refugees and members of the host community.
We live in constant fear—targeted simply because of who we are. Violent ambushes by homophobic groups, often armed with machetes, have left many of us injured and traumatized. Over time, we’ve lost not only our sense of safety but also our belongings, our dignity, and for some, their lives.
Sexual violence is another painful reality. Lesbian women have been subjected to repeated assaults, including rape, which leaves deep emotional and physical scars. It’s heartbreaking that the place meant to provide refuge has become one of the most dangerous environments for LGBTQIA+ people.
On top of this, discrimination makes it nearly impossible for us to find employment. Despite our willingness to work and contribute, we are often rejected solely based on our sexual orientation or gender identity. This has left many of us struggling to survive, enduring illness and poverty in an environment with extremely poor living conditions.
And yet, in the midst of all this hardship, we still find strength. We celebrate Pride and recognize LGBTQIA+ awareness days quietly, often in hiding, but always with pride. We’ve even witnessed love persevere—with a few couples managing to marry and celebrate their commitment, even in secret.
We are currently raising funds through our GoFundMe to support our LGBTQIA+ community in the camp. Any donation, no matter how small, means the world to us. It helps us afford basic needs, access safer spaces, and keep hope alive in a place that often feels hopeless.
DONATE HERE➡️GFM ⏯️ https://gofund.me/a0bb7404
Please consider donating and sharing our cause. Your support can truly save lives.
With hope and gratitude,
Frank Qum








#mtf#ftm#lesbians#pansexal#queer#gay#lgbtq#trans man#trans#mtf trans#free lgbtq#free palestine#free gaza#free refugees
16 notes
·
View notes
Text
I was on my way to make an AU// HC that I have for Homicidal Liu, but because he has Dissociative Identity Disorder [DID] and I want to be as CLOSE to Psychologically Accurate as possible with my Headcanons of him, I thought I'll do a quick research on DID Terminologies that I will be needing to use with him. So here it is!
Dissociative Identity Disorder Terms you need to know:
• Alter: Is a separate identity or personality within a person with Dissociative Identity Disorder (DID). Each alter may have its own name, traits, memories, and role. Alters are developed as a way to cope with trauma and may take control at different times.
• System: Refers to the group of alters (different identities) that exist within one person. The system includes all the alters, their roles, and how they interact with each other.
• Switching: A phenomenon when control over the body shifts from one alter to another. This can happen suddenly or gradually and may be triggered by stress, emotions, or specific situations. During a switch, memory, behavior, and mannerisms can change depending on which alter is in control.
• The Front: Refers to the part of the system that is currently in control of the body and interacting with the outside world. The alter that is at the front is the one actively experiencing and responding to the present moment.
There are many types of alters in Dissociative Identity Disorder (DID), each serving different roles within the system. Not every system has all types, and some alters may fit into multiple categories.
Here are the many different types of Alters by Category:
• Core Functional Alters
1. Host – The alter that handles daily life most often; not always the original identity.
2. Co-Host – Shares fronting responsibilities with the host.
• Protective Alters
3. Protector – Defends the system from harm, may be aggressive or authoritative.
4. Gatekeeper – Controls access to memories, alters, or the front.
5. Persecutor – Engages in harmful behaviors toward the system or others, often due to internalized trauma.
6. Caretaker – Provides emotional or physical care to other alters, especially Littles.
• Memory & Trauma-Related Alters
7. Memory Holder – Stores traumatic memories that other alters do not remember.
8. Fragment – A less-developed alter that holds a single emotion, memory, or function (e.g., fear, anger).
• Child Alters (Littles & Middles)
9. Little – A young alter (age 0-7) who may carry trauma, emotions, or innocence.
10. Middle – A child alter aged around 8-12, sometimes more independent but still vulnerable.
11. Teen – An alter with the mindset of an adolescent, often rebellious or protective.
• Introjects (Alters Based on External Sources)
12. Fictives – Based on a fictional character from books, movies, games, or media.
13. Factives – Based on a real person, such as a family member, abuser, or public figure.
• Non-Human Alters
14. Animal Alters – Identifies as an animal (e.g., wolf, cat, dragon) and may behave accordingly.
15. Mythical/Paranormal Alters – Identifies as a ghost, angel, demon, or other supernatural being.
16. Robot/Artificial Alters – Feels mechanical, emotionless, or programmed.
17. Object Alters – Identifies as an inanimate object, often as a coping mechanism.
• Other Specialized Alters
18. Sexual Alter – Engages in or handles sexual situations, often formed due to trauma.
19. Social Alter – Appears in social settings, charismatic and outgoing.
20. Work/Professional Alter – Handles jobs, academics, or responsibilities.
21. Mood-Dependent Alters – Only appear during specific emotional states (e.g., depression, anger).
• Unique & Rare Alters
23. Dead Alter – Believes they are deceased or exists in a ghost-like state.
24. Sleep Alter – Manages sleep or appears in dreams.
25. Time Keeper – Keeps track of time and schedules.
Additional about Alters
• Alters may overlap in roles (e.g., a protector could also be a persecutor).
• Alters may change over time as they heal or integrate.
• Not every system has all these types of alters.
#dissociative identity disorder#dissociative system#did community#did system#did osdd#creepypasta#homicidal liu#creepypasta fandom#liu woods#i tried my best#as accurate as i know of at least#sorry if it's not as accurate#I'm still a studying psychology student
12 notes
·
View notes
Text
Undertale, Monster beauty standards:
Beauty standards are always an important thing to consider within a culture. They say a lot about a lot more things than people realise.
Beauty standards are a pretty common component of every culture. A good indication of basic gender norms and values within a culture. So what could the beauty standards be for a gender non-conforming society?
Monsters aren’t restrained to just two (technically three) biological sexes like humans are. Every single Monster is born with the ability to impregnate and carry a successful pregnancy. Some Monster subspecies don’t even need another partner to reproduce! Asexual reproduction is not uncommon or strange within the Underground.
Monster society also doesn’t share a single standard look. Most human groups, you can imagine in your mind a basic ‘type’ from that group. E.g. you can easily imagine what a general Chinese person looks like.
Monsters are far to diverse and unique from one another for that too be a useful tool.
So aside from some more cultural specific standards for the different subspecies (which I will talk about later) Monsters the vast majority of the time rely on SOULS to project their attractiveness.
SOULS: make up the combination of ones being. It is you, it’s everything you are, you hope to be and that you will be.
To Monsters, a bright SOUL. One that is expressive, strong and powerful is a beautiful one.
Many Monsters find human SOULS to have a sort of alien beauty within them. The rainbow of colours all within a humans identity to project. Despite the many differences between the two species, much poetry has been written about the strength and beauty of human SOULS.
Of course, since Monsters SOULS themselves are stark white many take to dressing their physical form. Adorning it with fashionable clothes, keepsakes or powerful enchantments.
Dressing fashionable is like a Monster way of saying, “hey! Im beautiful! My forms beautiful! Come here and look (or be intimidated) by my masterful fashion skills!!”
Taking personal care of themselves is another indicator of beauty. Washing and brushing fur, removing dirt from between bones, horn care. Hygiene remains a focal point in their culture. Luckily, despite Monster society’s many diversities, they were all still able to access proper hygiene tools.
To not take care of oneself indicates a much larger problem. Depression is an especially deadly illness for Monsters. Many of the first signs of which develop through symptoms like avoiding taking care of oneself and managing their appearance. If you see a Monster struggling with these, maybe reach out? They are usually more open to their feelings than humans are.
Scars and injuries are viewed somewhat strangely by Monsters. Unlike many humans, Monsters tend to find scars to be intimidating or dangerous. The scarred individual dangerous or intimidating. Some scars are tolerated, if small and otherwise un obstructive to a Monsters form. Vice versa with injuries.
Monsters that suffer horrific, permanent damage are often considered unattractive or dangerous to be around. This doesn’t help the mental anguish the Monster is likely already under. Monsters like this can often find themselves self isolating or being ostracised from Monster society.
A struggle for those too monstrous for Monsters and too Monster for humans.
Monsters that have obvious diseases or defects are also considered unattractive. Dimming, an uncommon birth defect, is commonly considered to be an ugly trait to have. Again, anything that could indicate that a Monster may not be healthy or happy is considered to be an ugly trait.
Overall, despite all things said. Many Monsters find the personality and behaviour of someone to be the most attractive part of a person. The way another human or Monster acts or treats others is a very important part of this physical attraction. This of course is going to look different from Monster to Monster. Each Monster having their ideal partner’s personality and behaviour in their mind.
It’s hard to standardise such a personal thing. But if you want to impress your Monster crush, maybe dress up a little, put that extra couple minutes into grooming yourself
(Or just flash them your soul. If you really want to get their attention😉)
#undertale worldbuilding#i like interpretations where monsters focus more on the soul#but i thought it was an interesting thought#how could such a physically diverse species have a beauty standard?#basically how a person treats themselves and others ks very attractive#oh they also enjoy the human soul colours#humans don’t really get it but skme monsters are obsessed with it#undertale#undertale headcanons#voidimagines
44 notes
·
View notes
Text
VTM League of Villains AU / Headcanons.
This is basically just a bunch of like, ideas of if the League of Villains were a League of Vampires instead. What clans I think they would be, story differences, stuff like that.
Really long post ahead.

Tenko / Shigaraki - Thinblood: While I imagine All For One as a lower generation Tzimisce, Shigaraki was not directly turned by All for One. Instead being turned by the Doctor that works for him. This way, Shigaraki would have to "earn" proper vampirism, by diablerizing his way up.
Shigaraki was left to his own devices, being made to build up a pack of other vampires, some from the Sabbat and some independents. Eventually he wound up creating the League of Vampires, building up strength both politically and physically.
I imagine he used a lot of thin blood alchemy early on, to try and empower himself and his allies. I picture him also trying to use Profane Hieroes Gamos, a potion that turns you into your ideal body, on Magne, as well as offering it to Shiuchi. He was completely blood bonded to All For One for years, both before and after being turned. Complete loyalty to his master up until Himiko managed to get the group to take part in Vaulderie, a Sabbat ritual that can actually erase pre-existing blood bonds.
At this point, Shigaraki, now going by Tenko, worked with his closest friends to try and kill All For One and rid the city of his influence. Possibly becoming the new Archbishop of the Sabbat afterwards.

Dabi - Caitiff: Endeavor would belong to Clan Ventrue, and be their Primogen for the city's Camarilla.
Dabi is a childe that, for one reason or another, didn't inherit his sire's clan. Endeavor would have been furious about it, and probably wanting to hide the failure of his blood from the rest of the Camarilla.
Alternatively, I could see him actually being a Ventrue, and simply pretending to be Caitiff to avoid any associations with his sire.
While Dabi has access to the Ventrue clan ability of Dominate, I see him refusing to use it. It would be too close to what his dad did of just forcing people into being what you want them to be. And I picture him not really wanting to go that route. Instead leaning into more physical abilities like Fortitude, Potence, and the like.
Dabi would have joined the Sabbat, and the League of Vampires, for a shot at taking down the Camarilla that let his father control so many people, as well as personally wanting to be the one to kill him and the childe that replaced him.

Himiko - Malkavian: Ages ago, me and one of my partners made a character who's whole deal was basically just stalking people they liked and trying to steal their identity. Their way of dressing, the way they talk, all of that, and then I made a malkavian based on that. I realized that would kinda be perfect for Himiko.
Finding someone she likes, stalking them, her madness feeding their thoughts and behaviors into her as she tries to be more and more like them.
I imagine her leaning into Auspex and Obfuscate as her disciplines. Auspex to read people's emotions and know how her loved ones are always feeling, and Obfuscate for not only her sneaky nature, but also the level 5 ability Impostor's Guise.
I kind of imagine Ochako as a Vampire Hunter in this universe, and becoming one of Himiko's main obsessions, only for Himiko to eventually turn Ochako into a vampire to save her from bleeding out. Now two malkavians, both absolutely obsessed with each other and utterly inseparable.
Additionally, she found out about the Sabbat ritual of Vaulderie, where everyone in a pack donates their blood to a cup, and shares drinks of it so everyone in the pack is loyal to each other. She 100% thought it was cute, roped the rest of the group into doing it, and unintentionally found out it disrupts pre-existing blood bonds.
Jin - Malkavian: Probably the most obvious Clan for him. I imagine that since he can't really clone himself in this universe, instead his delusions of multiple selves comes from constantly seeing his past and future versions of Jin at all times. This makes it hard to tell where or when he is, and leads to him responding to conversations out of order whenever his mask is off. Or reacting to threats that haven't happened yet.
I imagine his future sight being part of what gets him invited to join the League. Or it would have gotten him invited, if he didn't already see it happening and just strolled into the League's haven thinking he was already a full time member. Giran was actually in the middle of trying to track him down and wouldn't bump into him for another night.
Jin winds up meeting with Keigo Takami(Hawks), secretly the Gangrel Primogen of the Camarilla. Keigo sees him as an easy in to the League and the Sabbat, planning on trying to take them down from the inside. Since Dabi is from the Camarilla originally, and sired by another Primogen no less, I don't imagine Dabi trusting him at all. Especially not enough to get Jin alone at any point.
They keep Keigo in just close enough that if he tries to pull anything, they can stake him about it. Unfortunately, Jin is much too attached to him at this point, and when the League attacks the Ivory Tower of the Camarilla prince, Jin saves Keigo from final death. Dabi trusts him enough, and with the Camarilla weakened, doesn't see him as enough of a threat to deal with compared to tracking down Endeavor.
The League gets used to him reacting to events out of order. Dabi keeps inviting him to movie nights with the League, where he keeps bawling his eyes out or cheering to emotional movie scenes way too early or way too late.

Magne - Brujah: Originally Camarilla, then Anarch, and finally Sabbat after finding a place among the League of Vampires. I imagine her finding out she was a woman while among the Camarilla, hating the strict roles and expectations, and moving onto the Anarch to be more free and able to be herself.
The unchanging nature of a vampire's body was probably horrible to deal with. She might have heard of the Tzimisce's ability to warp and change flesh, and saw it as a chance to possibly transition. Striking out to meet the Sabbat and find out if the rumors were true, she met Shiuchi, someone else with a body they weren't exactly happy with.
They then were introduced to the League by a ghoul named Giran, and quickly made friends among the other outcasts.
Eventually, Shigaraki would have figured out a thin-blood elixir to try and help Magne, and allowed her the transition her unlife had denied her up until this point.
She still takes the role of big sister in the League, and I imagine her and Himiko doing each other's hair or practicing makeup on Jin.

Compress - Ravnos: Magician act turned vampire in a tragic accident, I imagine he'd honestly take to vampirism pretty well, not to mention the illusion powers of Fata Morgana as a discipline.
I could see him having both the normal and variant clan banes of the Ravnos clan. Needing to never sleep in the same area twice, and people having power over him if they know his original name.
He's probably been a vampire the longest of the League, traveling from town to town, changing his identity everywhere he goes, and finally winding up joining the League after a particularly unhappy encounter with the Camarilla.
I imagine him sticking with the League for a while to have a place of relative safety, and to try and help screw over the Camarilla. He's initially planning on leaving the city the moment things look dicey, only to stick around after bonding with everyone.
The League probably lets him take turns at everyone's havens to avoid his bane of not sleeping the same place twice. Everyone winds up calling dibs on which day of the week he day sleeps at their haven.

Shiuchi - Nosferatu: Shiuchi pre-vampirism wasn't too different from his pre-league self. Staying in his room gaming all the time, avoiding people, a hollow shell of a person. After being embraced, he was one of many Camarilla Nosferatu.
Being a nosferatu, he's at best tolerated by most of the vampires he's met, being well aware of how his appearance makes everyone react. People only ever looked past it if a nosferatu can be useful, and "looking past" is more shorthand for "Avoiding looking at you at all but at least not insulting you for it".
He winds up leaving the Camarilla and meeting Magne, both looking for a way of changing their bodies. Her for comfort reasons, him hoping to be seen as a person for once.
After being introduced to the League, I imagine Shiuchi being a bit weirded out by Shigaraki and the others barely seeming to notice anything weird about his looks. Granted, Shigaraki had seen worse growing up alongside a Tzimisce, but those were monsters and Shiuchi was a person. A friend, as well.
Eventually, Shigaraki devised a thin-blood potion to try and help Magne, by changing one's body to its ideal form. It would have been offered to Shiuchi, but at this point Shigaraki's unwavering support and friendship meant Shiuchi no longer viewed himself as just another freak from the sewers. He found a group of people who didn't flinch when they saw him, and treated him as they did everyone else in the League. I don't imagine him taking the elixir, and Shigaraki wouldn't have tried to push any more than the initial offer.
He 100% breaks into Gamestop in the middle of the night to steal games for himself and Tenko.

All For One - Tzimisce: Archbishop of the Sabbat. Embraced almost 200 years ago, he's been building up followers and amassing an army. I imagine he might have considered the Camarilla at one point, but saw the Sabbat as far easier to manipulate and control.
A frequent user of Dominate and Vicissitude. I imagine he liked to collect people rather than quirks in this universe. Turning them into ghouls or reshaping them into tools. A few humans here, a vampire or two there, maybe a changeling or other magical being every now and again.
He raised Tenko into Shigaraki in this universe much the same as he did in canon. Blood bonding, dominate, and general manipulation to try and make a proper childe out of him. I imagine he chose to have Shigaraki turned into a thin-blood instead of embracing him, to force him to diablerize his way to proper vampirism.
This way he'd lower his humanity and be even easier to control, while also being raised to be a powerful vampire almost equal to All For One himself. Additionally, having such low humanity means that if Shigaraki ever tried to diablerize All For One(at least according to Vtm v5 rules), there'd be a very high chance All For One would just take over the body instead.
This plan kind of fell to pieces when his blood bond on Shigaraki was removed, and the League started plotting to overthrow him entirely.
I'm not entirely sure what All Might would be in this universe. A Vampire Hunter? A Mage? A Werewolf? A Camarilla Prince wouldn't feel right. I imagine Deku would be much the same as whatever All Might is, but am not too sure what would fit both of them if they were a factor in this story.
#vtm#mha#league of villains#vampire the masquerade#shigaraki tomura#himiko toga#twice#dabi#big sis magne#vampire au#league of vampires#spinner#mr compress#all for one#text post
20 notes
·
View notes
Text

Knight
"Male", he/him, 5.5ft, Hyperdyne Systems 120-A/2
Role: Science/Research officer
Assignment: Research Station - Darwin (Former: Botany research facility - Mangnoliophyta aka Magnolia)
Background:
A later model of the 120-A/2 model of synthetics manufactured in 2140, he was originally produced to work in one of one the Weyland-Yutani’s botany research facilities, specifically in the creation of new species of flowering plants that would be able to survive the harsher conditions that they were facing on newly terraformed planets. He was very successful in his endeavor, with him and his team being able to genetically modify a number of plants to improve their survivability and adaptation, while also being able to personally create a variety of new species/varieties of flowering plants.
However during this time he started to butt heads with his team leader and some of the other employees due to their distrust of the synthetic and Knight’s temperament. Things eventually came to a head when the team leader was found dead, supposedly due to cardiac arrest, but the other team members suspect that Knight had poisoned him given his botanical knowledge and access to a number of dangerous plants he was cultivating himself.
When other members of the team started to experience unexplained sickness and symptoms, Weyland-Yutani was contacted and Knight removed from his position due to the potential suspected danger he posed. Obviously Knight himself would deny he would use his plants to harm a human, but he did always need test subjects.
Instead of being decommissioned due to his apparent hostility towards humans, he was upgraded (along with new protocols and directives being installed) and given to the daughter of a board member of Weyland-Yutani, Annabella, to assist in her genetic studies and modification of Prometheus' fire aboard the Darwin.
Personality:
A bitter and rather sour character, Knight doesn’t try to hide his synthetic nature from the crew on the Dawin, with him refusing to interact with many of the human staff or partake in any social interactions with them.
The only human he actively interacts with, bar managers and higher up, is Annabella, with whom he spends most of his time with, be this in their shared lab or during their off hours. Originally he despised the woman, seeing her as an outlet to his frustration of being removed from his original assignment and being made to act like her personal nanny by her father due to her condition. But with time, and some mild bribery from her, he did warm up to her, with other staff members saying that Knight was now living up to his namesake.
Distrusting of humans and more than aware that they all have alternative motives, Knight tends to keep things to himself he doesn’t think they need to know and never trusts anything anyone says. This has led to him becoming more paranoid overtime, be it about the work they are carrying out, the company, or the other staff members, especially if it concerns Annabella or his plants. This paranoia has also resulted in him isolating Annabella from her other coworkers, micromanaging a large percentage of her daily life and forming a dependency on her.
With a shorter temper than the other 120-A/2 series, Knight is irritated fairly easily with staff and while he won’t (normally) resort to violence he is known to be rather cunning and cruel when the need arises. This might show up as staff being anonymously reported for unprofessional conduct or contraband being found on them or if the synthetic is truly pissed then the cause of his ire might find themselves in the medical bay due to an unknown illness.
While most staff would describe the synthetic as full of himself and condescending, he does have a soft side buried down in the deepest part of his circuitry which few will ever see, unless they catch him tending to his garden or taking care of Annabella out of work hours.
Appearance:
Physically he appears almost identical to all the other 120-A/2 models, except for one eye being a different colour, a dark brown instead of the typical blue. This was due to it needing to be replaced after an injury he sustained aboard the Darwin and no other parts from the same model being available. He also suffers from perpetual RBF and typically only scowls or looks disinterested when being talked to by the human staff.
He typically wears the same uniform all science staff aboard the station wear, modified medical scrubs in Weyland-Yutani’s colour scheme. The main difference is the multiple pins and patches Annabella has added to his to “customise” it. These mostly consist of company/station patches along with a number of pins she has collected over the years. Most of these are botany/flower themed.
Additional info:
Very good at card games and tricks. Something he learned from his earlier life and also knows how to cheat at them pretty effectively.
Adores plants and has a hidden garden set up in his room with seeds and plants Annabella has acquired for him due to her position.
Typically runs his battery almost dry as he hates being out of commission during the charging time.
Has monitors implanted that track and monitor Annabella to detect if she’s wandered off or having a meltdown.
13 notes
·
View notes
Text
By: SEGM
Published: Jun 11, 2023
A new peer-reviewed article, “Transition Regret and Detransition: Meaning and Uncertainties,” published in the Archives of Sexual Behavior, reviews clinical and research issues related to transition regret and detransition. The article emphasizes that “although recent data have shed light on a complex range of experiences that lead people to detransition, research remains very much in its infancy,” and there is currently “no guidance on best practices for clinicians involved in their care.”
The author, Dr. Jorgensen, notes that the term “detransition” can hold a wide array of possible meanings for transgender-identifying people, detransitioners, and researchers, leading to inconsistencies in its usage. Although regret and detransition overlap in many people, not everyone who regrets their transition takes steps to detransition and conversely, not all of those who detransition regret their transition. Proponents of the “gender-affirming care” model typically focus on the latter group who are driven to detransition by external forces such as discrimination, lack of support from family and friends, or difficulty accessing health care. Euphemisms such as “gender-identity journey” and “dynamic desires for gender-affirming medical interventions” have been used to describe this process.
But the author highlights studies and personal testimonies of detransitioners who do deeply regret their transition, mourn the physical changes made to their bodies, and feel betrayed by the clinicians and medical institutions that offered hormones and surgery as antidotes to their gender confusion and distress. For this group of young people, internal factors such as “worsening mental health or the realization that gender dysphoria was a maladaptive response to trauma, misogyny, internalized homophobia, or pressure from social media and online communities,” were the primary drivers of their decision to detransition.
As the author highlights, a consistent theme in studies and personal testimonies of detransitioners is that there are major gaps in the quality and accessibility of medical and mental healthcare: “Many detransitioners reported not feeling properly informed about health implications of treatments before undergoing them (Gribble et al., 2023; Littman, 2021; Pullen Sansfaçon et al., 2023; Vandenbussche, 2022). Likewise, many felt that they did not receive sufficient exploration of preexisting psychological and emotional problems and continued to struggle post-transition when they realized gender transition was not a panacea (Littman, 2021; Pullen Sansfaçon et al., 2023; Respaut et al., 2022; Sanders et al., 2023; Vandenbussche, 2022). Despite ongoing medical needs, most patients did not maintain contact with their gender clinic during their detransition.” Detransitioners report wanting more information about how to safely stop hormonal therapies and surgical reversal or restorative options, but few clinicians are sufficiently knowledgeable about these issues to manage their care.
The author notes that our ability to predict who will be helped by transition-related medical interventions and who will be harmed by them is limited and we currently have no idea how many of the young people transitioning today will eventually come to regret their decision: “no one is systematically tracking how many young people regret transition or, for that matter, how many are helped by it.” However, the increasing number of detransitioners publicly sharing their experiences suggest that historical studies citing low rates of regret are no longer applicable. Moreover, these studies suffered serious methodological flaws that would tend to underestimate the true rates of regret including high rates of attrition and narrow definitions of regret.
More recent studies that have included the current case mix of predominantly adolescent-onset gender dysphoria suggest that up to 30% of those who undergo medical transition may discontinue it within only a few years (Roberts et al., 2022). It is likely that a number of them will experience significant regret over lost opportunities and permanent physical changes.
So how did we get here?
The author suggests that less restrictive eligibility criteria for accessing transition-related medical interventions under the gender-affirmation and informed consent models, coupled with the rapid rise of adolescents and young adults presenting to gender clinics, many of whom suffer from complex mental health problems and neurodiversity, has important implications for the incidence of transition regret and detransition. Under these models of care, standard processes of differential diagnosis and clinical assessment are seen as “burdensome, intrusive, and impinging on patient autonomy.” Moreover, the author points out that hormonal therapies and surgery are now conceptualized as a “means of realizing fundamental aspects of personal identity or ‘embodiment goals,’ in contrast to conventional medical care, which is pursued with the objective of treating an underlying illness or injury to restore health and functioning.”
Furthermore, adolescents and young adults might not be mature enough to appreciate the long-term consequences of their decisions about the irreversible medical interventions used to achieve “embodiment goals,” and/or their capacity to give informed consent may be limited by comorbid mental health problems or neurodevelopmental challenges. Additionally, “feelings of profound grief about lost opportunities and negative repercussions of transition might not be fully captured by framing the emotional experience in terms of regret” because “regret is an emotion that is unique in its relation to personal agency (Zeelenberg & Pieters, 2007), but the exercise of personal agency in the transition process might have been limited for people who began transition as minors, whose decision-making capacity was compromised by mental illness, or who were not fully informed of known and potential adverse health implications.”
The author offers some suggestions for how detransition may be prevented and inappropriate transitions avoided:
Improving the process of informed consent.
Prioritizing treatment of co-occurring social, developmental and psychological problems.
Using precise language about medical interventions.
Helping young people expand their understanding of what it means to be a man or woman.
Being transparent about the quality of evidence supporting medical interventions and the uncertainty about long-term harms.
The author ends by emphasizing that when clinical cases are complicated by a lack of knowledge about the natural trajectory of the condition and a paucity of evidence supporting treatment options, “minimizing iatrogenic harm requires application of cautious, thoughtful clinical judgement, meticulous examination of the data that are available, as well as a willingness to change practice in the face of new evidence.”
Jorgensen calls on the gender medicine community to “commit to conducting robust research, challenging fundamental assumptions, scrutinizing their practice patterns, and embracing debate.”
--
Read more about the phenomenon of detransition:
Boyd I, Hackett T, Bewley S. Care of Transgender Patients: A General Practice Quality Improvement Approach. Healthcare. 2022; 10(1):121. https://doi.org/10.3390/healthcare10010121
D’Angelo, R. (2020). The man I am trying to be is not me. The International Journal of Psychoanalysis, 101(5), 951–970. https://doi.org/10.1080/00207578.2020.1810049
Entwistle, K. (2020). Debate: Reality check – Detransitioner’s testimonies require us to rethink gender dysphoria. Child and Adolescent Mental Health, camh.12380. https://doi.org/10.1111/camh.12380
Expósito-Campos, P. (2021). A Typology of Gender Detransition and Its Implications for Healthcare Providers. Journal of Sex & Marital Therapy. https://www.tandfonline.com/doi/abs/10.1080/0092623X.2020.1869126
Hall, R., Mitchell, L., & Sachdeva, J. (2021). Access to care and frequency of detransition among a cohort discharged by a UK national adult gender identity clinic: Retrospective case-note review. BJPsych Open, 7(6), e184. https://doi.org/10.1192/bjo.2021.1022
Littman, L. (2021). Individuals Treated for Gender Dysphoria with Medical and/or Surgical Transition Who Subsequently Detransitioned: A Survey of 100 Detransitioners. Archives of Sexual Behavior. https://doi.org/10.1007/s10508-021-02163-w
Marchiano, L. (2021). Gender detransition: A case study. Journal of Analytical Psychology, 66(4), 813–832. https://doi.org/10.1111/1468-5922.12711
Roberts, C. M., Klein, D. A., Adirim, T. A., Schvey, N. A., & Hisle-Gorman, E. (2022). Continuation of Gender-affirming Hormones Among Transgender Adolescents and Adults. The Journal of Clinical Endocrinology & Metabolism, 107(9), e3937–e3943. https://doi.org/10.1210/clinem/dgac251
Vandenbussche, E. (2021). Detransition-Related Needs and Support: A Cross-Sectional Online Survey. Journal of Homosexuality, 20. https://doi.org/10.1080/00918369.2021.1919479
==
Genderists often say things like "detransition/regret is rare" and "detransition is only due to discrimination." These run in the opposite direction to genderist assertions, as this means "detransition/regret due to discrimination is rare."
Most of the numbers they cite are either poorly sourced as mentioned above, or worse, from the days of "watchful waiting," where transition only came at the end of a comprehensive care process; a completely different model.
Not only is it dishonest, given they regard watchful waiting, or anything else as "harmful" and "gatekeeping," but the low regret rate actually supports that more cautious, thoughtful process.
And besides, claiming to know the success rate under the "affirming"/"informed consent" models is itself dishonest too. Detransitioners are not going to rush back to the same doctors who facilitated their mistake. Especially in a climate where they'll be blamed or vilified.
#SEGM#Society for Evidence Based Gender Medicine#transition regret#regret#detransition#detrans#gender ideology#queer theory#gender affirming care#medical transition#medical malpractice#medical mutilation#medical corruption#religion is a mental illness
107 notes
·
View notes
Text
Intro to Us - Masterpost
We’re The Reflection Family, a collective of over 200 members (so far) in eight different branches sharing a body. Our collective is organized into several distinct groups and categories, reflecting different origins, roles, and characteristics of our coanimans. Each branch has its unique dynamics and members, influenced by their proximity to certain fragments.
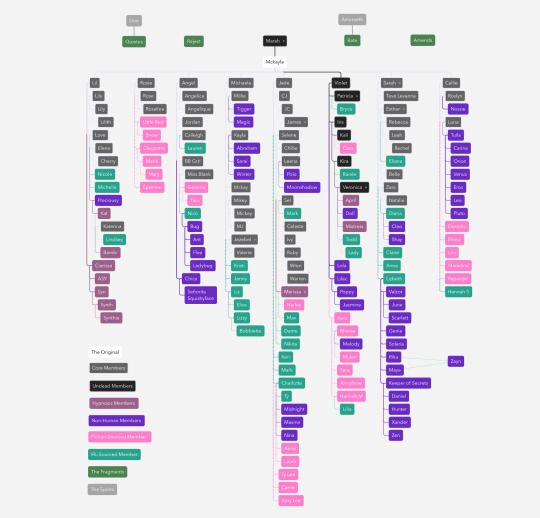
Types of Coanimans: A Guide to Our Color Coding
• The Original (White): Mckayla, the primary coaniman associated with the body.
• Core (Dark Grey): Human coanimans who are direct splits from Mckayla, sharing similar physical traits.
• Undead (Black): Coanimans disconnected from reality due to near-death experiences; not necessarily direct splits.
• Hypnosis (Desaturated Pink): Coanimans created via hypnosis, either accidentally or intentionally.
• Non-Human (Purple): Coanimans that are either direct splits or introjects of animals.
• Fiction-Sourced (Light Pink): Introjects named after fictional characters or celebrities.
• IRL-Sourced (Teal): Introjects from real-life relationships.
• Fragments (Green): Coanimans embodying singular characteristics and influencing nearby parts when co-conscious.
• Spirits (Light Grey): Protective entities or guides within the system.
Overview of Our Structure
Hosts: Who's in the background?
The hosts in the collective not only manage daily life, social interactions, and external relationships but also play a crucial role in preserving long-term memory recall within a collective memory bank. They act as the primary points of interaction with the outside world, ensuring that the collective's needs and responsibilities are met while maintaining a stable presence. By embodying qualities such as adaptability, resilience, and social awareness, the hosts effectively navigate diverse situations and challenges, presenting a cohesive identity to those outside the collective. Through their ability to coordinate with other parts and maintain access to shared memories, the hosts ensure continuity and a functional existence, bridging the internal world with external reality and fostering a sense of cohesion and unity within the collective.
• Veronica - 23-24 - Oversees relationships and social interactions.
• Sel - 17-24 - Manages school-related tasks.
• Selene - 18-24 - Focused on work and professional responsibilities.
• A39 - ageless - Responsible for switching between parts.
The Gatekeepers: Who Runs The System, Really?
The gatekeepers in the collective are vital entities responsible for managing and regulating access to various aspects of the inner world and the collective's complex internal landscape. They oversee the flow of memories, emotions, and information, ensuring that the right coanimans come forward when needed and that sensitive or potentially destabilizing memories are kept at bay until they can be safely processed. The gatekeepers also play a protective role, shielding more vulnerable members from traumatic recollections or overwhelming emotions. By maintaining a delicate balance between different parts and their experiences, the gatekeepers facilitate smoother transitions and interactions within the collective, contributing to overall stability and coherence in navigating daily life and therapeutic work.
• Charlotte - 20-45 - Gatekeeps the IRL subgroup.
• Jade - 15-24 - Oversees the Teens.
• James - 17-19 - Manages the Guys & Gays.
• Sarah - 8-20 - Responsible for the Middles.
• Elena - 8-14 - Oversees the Littles/Munchkins.
• Gemma - 25-45 - Responsible for the Hypnos.
• Patricia - 12-20 - Oversees the Shadows, managing more hidden or complex parts.
• Kara - 4-40 - Helps Fictional-Sourced members.
• Valzor - 30-43 - Manages parts connected to innerworld characters.
The Fragments - The 4 Corners of the Mind
The four fragments—Quietus, Reject, Bate, and Amends—each contribute to the collective's overall balance and resilience, shaping how the group interacts with both its internal landscape and the external world. These fragments represent different approaches to coping, healing, and navigating life's complexities, influencing the way coanimans respond to experiences and challenges. Together, they create a dynamic and multifaceted internal structure that fosters growth, adaptability, and a deeper understanding of self and surroundings, allowing for a cohesive yet varied approach to managing the collective's needs and interactions.
1. Quietus - Control and Repression - Quietus represents control, repression, and emotional suppression. As a fragment, Quietus embodies a deep need for stability, often at the cost of suppressing unwanted emotions and memories. This influence creates an environment where emotional expression is minimized to maintain order and prevent chaos within the system.
2. Reject - Identity and Exclusion - Reject grapples with feelings of rejection, self-worth, and exclusion. This fragment represents the internal struggle with identity and belonging, influencing coanimans who question their value and place within the collective. Reject’s influence is marked by a constant battle for self-acceptance and understanding, reflecting the complexities of identity formation and emotional growth.
3. Bate - Power and Anger - Bate embodies strength, power, and anger. This fragment channels defensive and assertive behaviors to protect or assert boundaries within the system. Bate’s influence is rooted in experiences of confrontation and resilience, shaping coanimans who are unafraid to express anger or assert their needs. This fragment also represents a willingness to fight against perceived threats or injustices, using power as a means of protection.
4. Amends - Comfort and Detachment - Amends focuses on comfort, detachment, and exploration. This fragment embodies the need for emotional solace and the detachment from painful or overwhelming experiences. Amends’ influence encourages exploration of inner worlds, seeking comfort through creativity, fantasy, and introspection. This fragment is characterized by a desire for emotional safety, often finding refuge in inner worlds and imaginative escapes.
Mckayla - The Original Lineage
Mckayla - 10 - The Original: The primary coaniman associated with the body, representing her current maturity level with therapy. Initially, she was stuck at age 6 when parts therapy began but has matured through therapeutic work.
Outside: The Ascended
Marah - The Unborn and Unique Presence
Marah - [Undead]: Represents Selene’s unborn daughter, a unique member within the collective, reflecting themes of unrealized potential and the complex emotional layers surrounding life, loss, and what could have been. She holds a special place in the collective, symbolizing a blend of innocence and the mysteries of existence.

Quietus’ Sphere of Influence - The Repressive Sphere
Quietus - Control and Repression - A fragment of control and repression, Quietus influences coanimans characterized by suppression, emotional restraint, and efforts to maintain stability by managing unwanted emotions and memories.
• Doe - The Watcher - A protective spirit animal within Quietus’ sphere, embodying caution and vigilance, overseeing the coanimans within this line.
Lil’s Line - The Innocence and Attachment Path
Lil’s line focuses on innocence, early childhood memories, and various forms of attachment and loss, exploring how these emotions manifest within the system.
Lil’s Subsystem - The Innocence Path
Lil represents the youngest, most innocent form, embodying early childhood. Her line expands through various aged-up versions that represent a progression from innocence to maturity:
• Lil - 2-4 - The Innocent [Core]: Represents the youngest, most innocent form, embodying early childhood.
• Lils - 5-9 [Core]: An aged-up version of Lil, representing an older and more developed form of innocence.
• Lily - 10-14 [Core]: Aged-up version of Lils; the “big” version, half-cat, half-human, based on the system’s cat.
• Lilith - 16-24 [Core]: The adult version of Lily, embodying a mature form of innocence.
Love’s Subsystem - The Attachment and Loss Line
Love embodies obsessive love and attachment, which further branches out into various representations of love and care, highlighting the complexities of relational dynamics within the system:
• Love - 13 - The Obsessive [Core]: Represents obsessive love, and splits into:
• Elena - 8-14 - The Caregiver [Core]: Represents sibling love and serves as a caregiver to the littles.
• Cherry - 17-18 - The Romantic [Core]: Represents romantic love.
• Nicole - 20-29 - The Sister [IRL]: Represents adoptive family connections.
• Michelle - 20-35 - The Protector [IRL]: Another representation of adoptive family ties.
Preciousy’s Subsystem - The Hypno Line
Preciousy, originally a cat, becomes a Hypno due to a traumatic loss. Her line focuses on themes of loss and trauma, represented by various parts that embody different aspects of these experiences:
• Preciousy - 6-16 - The Lost [Hypno]: Originally the system’s cat, now a Hypno due to trauma.
• Kat - 12-14 - The Feline [Hypno]: Represents a young version dealing with the emotional trauma of loss.
• Katerina [Core]: Further explores the themes of loss and attachment.
• Lindsey [IRL]: Represents deeper feelings of abandonment and healing.
• Bambi - 19 [Hypno]: Represents a mature aspect dealing with sensuality.
Clarissa’s Subsystem - The Machine Line
Clarissa, within Lil’s branch, is a unique entity representing non-human, mechanical aspects, emphasizing themes of emotionlessness and functionality:
• Clarissa - The Machine [Hypno]: A unique, machine-like entity that does not conform to typical human emotions.
• A39 - ageless [Hypno]: A drone responsible for mechanical tasks and operations.
• Syn - ageless [Hypno]: An AI system designed for processing and organizing information.
• Synth - ageless [Hypno]: A teen part handling intermediate tasks.
• Synthia - ageless [Hypno]: The adult part responsible for more complex operations.

Rosie’s Line - The Creative and Resilient Path
Rosie’s line focuses on creativity, resilience, and leadership, exploring themes of beauty, creative spirit, and artistic expression through various coanimans in this line.
Rosie’s Subsystem - The Creative Line
Rosie represents an early emotional split with creative tendencies, leading to various manifestations of creativity and artistic expression:
• Rosie - The Creative [Core]: Represents an early emotional split with a focus on creativity.
• Rose - 14-18 - The Resilient [Core]: Embodies themes of beauty and resilience.
• Rosalina - 10-14 [Core]: Represents a youthful creative spirit continuing Rosie’s theme.
Little Red’s Subsystem - The Survivor’s Path
Little Red explores themes of survival and caution, embodying resilience in the face of adversity:
• Little Red - 4-10 - The Survivor [Fiction]: Represents themes of survival and caution.
• Snow - 14-22 [Fiction]: Embodies themes of cold detachment and perseverance.
Cleopatra’s Subsystem - The Leadership Line
Cleopatra’s line is centered around leadership and heritage, embodying strength and leadership qualities:
• Cleopatra - 16-25 - The Leader [Fiction]: Represents themes of leadership and heritage.
• Marie - 14-18 [Fiction]: Embodies grace and poise.
• Mary - 16-19 [Fiction]: A youthful version dealing with innocence and purity.
Éponine’s Subsystem - The Unrequited Love Line
Éponine’s line represents themes of unrequited love and self-sacrifice, exploring emotional depth and complexity:
• Éponine - [Fiction]: Represents themes of unrequited love and self-sacrifice.

Reject’s Sphere of Influence - The Identity and Exclusion Sphere
Reject - Identity and Exclusion - Embodies the struggle with rejection, self-worth, and belonging, influencing coanimans who grapple with their sense of identity.
Angel’s Line - The Shadowed Innocence and Rejection Path
Angel’s line navigates themes of innocence entangled with feelings of rejection, exploring the dynamics of identity and self-worth through various manifestations within the system.
Angel’s Subsystem - The Shadowed Innocence Line
Angel, rooted in a childhood nickname, deals with themes of shadowed innocence and entrapment, reflecting on memories tied to familial nicknames and shadowy experiences:
• Angel - The Shadowed Innocent [Core]: Connected to a childhood nickname, represents innocence and purity.
• Angelica - [Core]: Trapped in the shadow realm as a child.
• Angelique - [Core]: Adult version who carries shared memories from Angelica’s time in the shadow realm.
Jordan and Caileigh’s Subsystem - The Almost-Identity Line
This subsystem explores identities that almost were, reflecting on alternate life paths and identities that the body might have had:
• Jordan - 8-16 - The Boy That Wasn’t [Core]: Represents a male identity that the body might have had.
• Caileigh - 8-14 - The Twin [Core]: Another almost-name, twin to Jordan.
• Lauren - [IRL]: Based on a real-life school friend.
BB Grrl’s Subsystem - The Nickname Line
BB Grrl represents another nickname that forms a distinct line exploring different facets of identity, shaped by external influences and introjections:
• BB Grrl - [Core]: Nickname-based coaniman.
• Miss Blank - [Core]: Views herself as the stepfather’s daughter.
• Gemma - 25-45 - The Anarchist [Fiction]: Connected to “Sons of Anarchy.”
• Tara - [Fiction]: Also inspired by “Sons of Anarchy.”
Nico’s Subsystem - The Bug Line
Nico’s line represents themes of fragility and resilience, characterized by nonverbal communication and various representations of small, resilient creatures:
• Nico - [IRL]: Introject of stepdad’s son.
• Bug - [Non-Human]: Represents smallness and fragility.
• Ant - [Non-Human]: Embodies diligence and teamwork.
• Flea - [Non-Human]: Represents resilience and survival.
• Ladybug - [Non-Human]: Carries themes of luck and protection.
Chica’s Subsystem - The Lost Doll Line
Chica, embodying a lost childhood object, explores themes of playfulness and loss, reflecting on childhood experiences and the creation of playful personas:
• Chica - [Core]: A Mexican doll reflecting childhood memories.
• Señorita Squishyface - [Core]: A playful persona that emerged from having her cheeks squished together to be cute.

Michaela’s Line - The Familial Memory and Identity Path
Michaela’s line is deeply rooted in family memories and identities, reflecting the various aspects of familial roles, relationships, and the complexities of family dynamics within the system.
Millie’s Subsystem - The Childhood Memory Line
Millie encompasses early childhood memories, capturing the innocence and experiences of youth and representing foundational aspects of the family identity:
• Millie - 0-14 [Core]: Embodies young memories, up to age 14.
• Tigger - [Non-Human]: Represents a past pet horse.
• Magic - [Non-Human]: Represents another past pet horse.
Kayla’s Subsystem - The Animal Care Line
Kayla represents a strong connection to animals and veterinary skills, showcasing a deep commitment to caring for and understanding animals:
• Kayla - [Core]: Represents veterinary skills and animal care.
• Abraham - [Non-Human]: Represents a specific animal connection.
• Sarai - [Non-Human]: Represents another specific animal connection.
• Winter - [Non-Human]: Represents care for a baby squirrel.
Mckay and Mikey’s Subsystem - The Twin Identity Line
Mckay and Mikey explore the dynamics of gender and twin identities, showcasing the fluidity and complexity of self-identification within the system:
• Mckay - [Core]: Represents a genderfluid aspect of Michaela.
• Mikey - 8-15 - The Boy Twin [Core]: Represents a boy version who eventually split into two parts.
• Mickey - 13-18 [Core]: A trans demi-girl.
• MJ - 16-19 [Core]: An older teen boy.
Jezebel’s Subsystem - The Protector and Fighter Line
Jezebel represents themes of protection and fighting spirit, embodying a defensive and assertive role within the system to manage conflict and anger:
• Jezebel - 24 - The Fighter [Core]: Emerged during a physical altercation with a family member.
• Valerie - 24 [Core]: Represents anger and protection.
Liz’s Subsystem - The Maternal Influence Line
Liz, along with her splits, embodies different aspects of maternal influence and roles, reflecting complex relationships with the mother figure:
• Liz - 30 [IRL]: Represents Michaela’s real mother.
• Eliza - 18-30 [IRL]: Represents a Catholic witch version.
• Lizzy - 18-30 [IRL]: Represents a nurse version.
• Bobbiette - 18-30 [IRL]: Represents a best friend from the mother’s high school years.
Support Figures Subsystem - The Guiding and Supportive Influences
This line also includes figures who have provided guidance, support, or therapeutic influence within the system, showcasing roles of caretaking and mentorship:
• Kristi - [IRL]: Represents Michaela’s therapist.
• Jenny - 30-35 [IRL]: Represents a surrogate mother figure.



Jade’s Line - The Intersex and Trauma Identity Path
Jade’s line reflects the complexity of intersex identity and trauma, exploring themes of gender, personal and adoptive identities, and the impact of past relationships and experiences.
Jade’s Subsystem - The Intersex Identity Line
Jade, embracing an intersex identity, due to PCOS, high testosterone, and genetic endometriosis, and navigates the interplay of personal and adoptive identities within hxr subsystem:
• Jade - The Intersex Identity [Core]: Integrates both personal and adoptive identities, reflecting an intersex identity and the navigation of related complexities.
• CJ - The Trans Demi-Guy [Core]: Represents a young trans demi-guy, highlighting an early stage of gender exploration.
• JC - The Teen Male [Core]: An older split from CJ, representing the evolution of gender identity into the teen years.
• James - The Adult Intersex Male [Core]: An adult manifestation of intersex identity, encompassing the culmination of gender exploration and identity solidification.
Selene’s Subsystem - The Trauma and Relationship Line
Selene’s line deals with trauma and relationship dynamics, reflecting on past experiences and the impact of relational ties:
• Selene - [Core]: Central co-host with a large subsystem.
• Chlöe - [Core]: A recent split due to medication changes.
• Leena - [Core]: Holds relationship trauma from the last ex.
• Sel - [Core]: School host, splits into Celeste, Ivy, and Ruby.
• Ruby - [Core]: Holds sexual trauma, splits into:
• Warren (IRL): an ex
• Wren (Core): tied to Warren, possibly undead
• Marissa - 19 - [Hypno]: a bimbo who spits into:
• Harley (Fiction): Harley Quinn
• Mav (IRL): of a past partner
Charlotte’s Subsystem - The Legacy Line
Charlotte’s subsystem encapsulates familial and fictional influences, integrating various introjects that represent different aspects of familial history and personal attachments:
• Charlotte - [Core]: Jade’s grandmother.
• Ty - [Core]: Represents Charlotte’s nephew.
• Midnight - [Non-Human]: Her Mother’s horse.
• Maxine - [Non-Human]: Her Cat.
• Nina - [Non-Human]: Her Sister’s dog.
• Laura Ingalls Wilder - [Fiction]: Fictional introject from “Little House on the Prairie.”
• Anne - [Fiction]: Introject from “Anne of Green Gables.”
Celebrity Influences Subsystem - The Iconic Personas Line
This subsystem reflects the integration of celebrity influences, embodying themes of understanding, strength, and mental health awareness through iconic personas:
• Carrie Fisher - [Fiction]: Represents a connection to mental health advocacy and trauma understanding.
• Amy Lee - [Fiction]: Symbolizes themes of emotional expression and resilience in dealing with personal struggles.

Bate’s Sphere of Influence - The Power and Anger Branch
Bate - Power and Anger - Influences coanimans who embody strength, power, and anger, often manifesting as defensive or assertive behaviors to protect or assert themselves.
• Amaraeth - The Guardian - A guardian spirit within Bate’s sphere, embodying spiritual power and protection, guiding coanimans under Bate’s influence.
Violet’s Line - The Undead Path
Violet’s line explores themes of survival, transformation, and undead characteristics, reflecting on near-death experiences and the journey of strength and resilience.
Violet’s Subsystem - The Undead and Flower Line
Violet starts the undead and flower line due to a near-death experience. This subsystem reflects themes of survival, transformation, and protection:
• Violet - The Survivor [Undead]: Created due to near-death experiences.
• Lilac - [Non-Human]: Represents another part of the flower line.
• Poppy - [Non-Human]: Represents another flower line extension.
• Jasmine - [Non-Human]: Represents further depth in the flower line.
• Iris - 19 - The Defender [Undead]: A defender coaniman above body-age, often managing protection roles.
• Kali - 19-25 [Undead]: Embodies themes of destruction and transformation.
• Cora - [Fiction]: A fictional mother introject, representing nurturing and protection.
• Kira - 14-18 [Undead]: A dominant part during high school.
• Ranèe - [Undead]: A bigender version of a high school best friend.
• Veronica - 23-24 [Half-Undead]: One of the current hosts.
Veronica’s Subsystem - The Host and Introject Line
Veronica’s subsystem explores themes of hosting and introjection, reflecting on relationships and the blending of internal and external influences:
• Veronica - 23-24 [Half-Undead]: One of the current hosts.
• Todd - [IRL]: An introject of the system’s boyfriend.
• Lady - [IRL]: A female introject of the boyfriend.
• April - [Hypno]: A happy hypno part.
• Doll - [Hypno]: Another, this time porcelain, doll
• Mistress - [Hypno]: A Mistress.
Patricia’s Subsystem - The Shadow Realm Line
Patricia, a vampire gatekeeper of the shadow realm, explores themes of memory manipulation and subconscious control, reflecting on the system’s shadow aspects:
• Patricia - 12-20 - The Gatekeeper [Undead]: A vampire gatekeeper of the shadow realm.
• Bryce - 18 [IRL]: Created accidentally during memory repression.
Kara’s Subsystem - The Fictive Gatekeeper Line
Kara (Supergirl) is the gatekeeper of fictives, reflecting on themes of imagination and the role of fiction in shaping internal experiences and identities:
• Kara - 4-40 - The Fictive Gatekeeper [Fiction]: Helps manage fictives and introduces fictional character elements.
• Minnie - 3-8 [Fiction]: Represents “Minnie Mouse,” the mini mom.
• Melody - 4-9 [Fiction]: Represents “Ariel’s daughter,” the mermaid.
• Mulan - [Fiction]: Represents “Mulan,” the warrior.
• Sara - [Fiction]: Represents “The Little Princess.”
• Annaliese - 18-19 [Fiction]: Represents “Barbie (Princess and the Pauper).”
• Hannah M - 12-15 [Fiction]: Represents “Hannah Montana.”
• Lilia - 8-18 [IRL]: Represents an introject from a real-life friend.



Shared Sphere of Influence - The Resilient Power and Comfort Sphere
Shared Influence from Amends and Bate - Power and Comfort -This sphere merges the influences of Bate, emphasizing power and anger, with Amends, focusing on comfort and detachment, creating a blend of strength and comfort-seeking behaviors.
Sarah’s Line - The Faithful and Spiritual Path
Sarah’s line encompasses themes of faith, spirituality, and resilience, reflecting on the journey of inner strength and spiritual connection within the system.
Sarah’s Subsystem - The Faithful and Spiritual Line
Sarah V is a core figure embodying faith and introspection. Her subsystem is diverse, exploring deep spiritual connections and biblical influences:
• Sarah V - The Faithful [Core]: Represents a deep connection to faith and internal reflection.
• Teva Levanna - [Core]: Represents a transformation during conversion classes to Judaism.
Esther’s Subsystem - The Biblical Triad and Protective Spirits
Centered around biblical and protective themes, this subsystem explores different aspects of familial and romantic stories, as well as protection within the system:
• Esther - 16-18 [Core]: Represents a Biblical influence with several splits:
• Rebecca - 8-12 [Core]: Represents a young, foundational Biblical character.
• Leah - [Core]: Represents the “unloved” Biblical figure.
• Rachel - 12-20 [Core]: Represents the “beloved” counterpart.
• Eliana - [IRL]: Represents a protective response to a traumatic experience.
• Belle - [Core]: Represents a romantic influence.
Zara’s Subsystem - The Intellectual and Feline Line
Zara’s line explores intellectual and feline themes, reflecting on scholarly aspects and protective instincts within familial relationships:
• Zara - [Core]: Formerly known as Sarah F.
• Natalie - [Core]: Represents a refined, scholarly aspect.
• Diana - 30-45 [IRL]: Represents a grandmother figure introject with specific traits.
• Cleo - 23 [Non-human]: Represents a sweet, black and white Persian cat.
• Shay - 12-16 [Non-human]: Represents a more reserved and cautious cat.
Aurora’s Kingdom Subsystem - The Inner World Builders
Sarah V also constructed an inner world known as The Kingdom of Aurora, a realm reflecting the system’s creative and spiritual depths. This world is inhabited by various characters and represents the complex interplay between creativity and spiritual introspection:
• Lizbeth - [IRL]: Represents a mother figure in the inner world.
• Valzor - 30-43 [Non-human]: Represents a metaphorical introject and antagonist.
• June - 2-15 [Non-human]: Represents a clone of Jade with embedded trauma memories.
• Scarlett - 8-15 [Non-human]: Represents a clone of Sarah with embedded trauma memories.
• Genie - 30-45 [Non-human]: Represents a shapeshifter with mystical ties.
• Solaria - [Non-human]: Represents a swamp witch with connections to inner narratives.
• Riku - [Non-human]: Represents an advisor to a fictional queen.
• Maya - 45-60 [Non-human]: Represents a slain dragon mother.
• Zayn - 6-19 [Non-human]: Represents her son turned dragon.
• Keeper of Secrets - [Non-human]: Represents a Gorian linked to subconscious thoughts.
• Daniel - 28-33 [Non-human]: Represents a pretty boy introject.
• Hunter - 18-30 [Non-human]: Represents a lover of animals.
• Xander - 25-35 [Non-human]: Represents a photography enthusiast.
• Zen - 35-50 [Non-human]: Represents a peaceful lover.

Amends’ Sphere of Influence - The Comfort and Detachment Sphere
Amends - Comfort and Detachment - Focuses on coanimans who provide comfort or exhibit a significant detachment from the core self, reflecting themes of exploration, longing, and searching for connection.
Callie’s Line - The Detachment and Exploration Path
Callie’s line focuses on themes of detachment, exploration, and the search for connection, often reflecting experiences related to childhood trauma and the longing for belonging and comfort.
Callie’s Subsystem - The Foster Care Twins and Fantasy Line
Callie embodies the detachment experienced during early childhood trauma in foster care. Her direct splits, Roslyn and Luna, explore themes of enchantment and escapism:
• Callie - The Explorer [Core]: Represents the first split in foster care, disconnected from Mckayla directly.
• Roslyn - [Core]: Represents a twin aspect, inspired by the first foster home experience.
• Nessie - [Non-human]: Represents a fae connection from a magical encounter.
Luna’s Subsystem - The Star Wars Galaxy Explorers
Luna’s fascination with space and escapism led her to craft an entire inner world inspired by the Star Wars galaxy, populated by various characters that reflect her desire to explore unknown territories:
• Luna - 8-16 [IRL]: Represents a space-loving, daydreamer persona.
• Tuila - 16 [Non-human]: Represents a “Star Wars” inspired character.
• Carina - [Non-human]: Represents a nebula-inspired character.
• Orion - [Non-human]: Represents another nebula inspiration.
• Venus - [Non-human]: Represents a planet-based inspiration.
• Eros - [Non-human]: Represents an asteroid-inspired character.
• Leo - [Non-human]: Represents a constellation-based character.
• Pluto - [Non-human]: Represents another planet-based inspiration.
Callie’s Fictive Subsystem - The Motherless Characters
Callie also developed a series of fictive alters reflecting themes of abandonment and searching for belonging, focusing on characters who are motherless or seeking maternal connections:
• Dorothy - 14-18 [Fiction]: Represents a motherless fictive who feels homeless.
• Eloise - 9-12 [Fiction]: Represents a character waiting for her mother’s visits.
• Lilo - 6-12 [Fiction]: Represents “Lilo” from “Lilo and Stitch,” symbolizing found family and resilience.
• Madeline - 6-10 [Fiction]: Represents a boarding school student.
• Rapunzel - [Fiction]: Represents a character given up by her parents.
Callie's Adoption and Friendship Subsystem
Callie’s experiences with adoption are explored through parts that reflect themes of identity formation and friendship within an adoptive context:
• Hannah S - [IRL]: Represents a friend introject who is also adopted, symbolizing shared experiences of adoption and identity search.
--- End.
#plural system#dissociative identities#dissociative alters#plural stuff#osddid#plural things#did system#pluralgang#plural posting#plurality#did#dissociative identity disorder#dissociative system#system#system things#traumagenic#traumagenic system#endos are the future
9 notes
·
View notes
Text
Blog Post #7 - Week 10 (due 3/20)
Race, Technology, and Online Abuse
How does Seeking Mavis Beacon explore the intersection of race, exploitation, and technology in the context of Mavis Beacon’s story, and what does this reveal about systemic inequality in the tech industry?
Seeking Mavis Beacon uncovers how Mavis Beacon’s image was exploited without her consent or compensation, reflecting broader systemic inequality in the tech industry. The documentary reveals that the game’s creator used her likeness to sell a widely successful product while denying her recognition or profits, highlighting the industry’s exploitative practices, especially toward women of color. As the film states, “Mavis was told it would be a photoshoot, not knowing her likeness would be used in a highly profitable game for years” (Jones, 2024). This raises questions about how marginalized groups are often erased or undervalued in spaces where they could otherwise thrive. The documentary emphasizes the ongoing racial and gender disparities within the tech world.
How does the internet’s accessibility and reliability, as described by Elin, contribute to both positive civic engagement and the spread of radical ideologies?
Elin highlights the internet’s positive role in fostering communication and networking, describing it as “cheap, fast, and dependable” (Elin, page 13). This accessibility makes it an essential tool for civic engagement, enabling marginalized groups and activists to organize and advocate for social change. However, the same qualities that make the internet beneficial also facilitate the spread of radical ideologies, allowing fringe groups to connect and amplify their messages. This duality underscores the internet’s power to both unite communities for positive change and serve as a breeding ground for extremism.
How has the internet transformed white supremacist social movements from localized efforts to global networks, and what implications does this shift have for combating hate-based ideologies?
The internet has enabled white supremacist movements to transcend national boundaries and evolve into global networks. Daniels (2025) emphasizes that “the Internet facilitates the formation of a transnational, explicitly racist white identity” (p. 43). This transformation allows disparate groups to unify under shared ideologies, amplifying their influence. The global nature of these movements complicates efforts to counter hate, as tactics effective in one region may not apply universally. Addressing this challenge requires international collaboration, online monitoring, and community resilience to combat the global spread of supremacist ideologies.
How did Twitter’s response to Leslie Jones’s online abuse highlight the platform’s shortcomings in handling hate speech, and what does this incident reveal about the challenges of moderating harmful content on social media?
Twitter’s response to Leslie Jones’s online abuse revealed the platform’s inadequacies in addressing hate speech. Despite acknowledging the severity of the harassment and taking action against some accounts, Twitter admitted to falling short of effectively preventing and managing such behavior. As Twitter stated, “We know many people believe we have not done enough to curb this type of behavior on Twitter. We agree” (Silman, 2016). This incident underscored the challenges of moderating harmful content, as abusive tweets continued despite enforcement efforts. Jones’s experience demonstrated the gap between policy intentions and practical enforcement, raising questions about the efficacy of social media regulations in curbing targeted harassment.
How does Danielle Keats Citron differentiate between traditional stalking and cyber harassment, and what impact does the anonymity of the internet have on these behaviors?
Citron (2014) explains that while traditional stalking involves offline behaviors such as vandalism or physical assault, cyber harassment “involves threats of violence, privacy invasions, reputation-harming lies, calls for strangers to physically harm victims, and technological attacks” (p. 3). The internet exacerbates the impact by extending the lifespan of abusive content, as posts can be indexed and retrieved long after they are first published, causing enduring harm. The anonymity of the internet amplifies these behaviors, as perpetrators can act without fear of identification or direct consequences, making it easier to target victims repeatedly.
Word Count: 488
Citron, D. K. (2014). Hate crimes in cyberspace. Harvard University Press.
Daniels, J. (2025). White Supremacist Social Movements Online and In a Global Context. In Social Movements in the Information Age (Chapter 4).
Elin, L. (2025). The Radicalization of Zeke Spier: How the internet contributes to civic engagement and new forms of social capital. Journal of Digital Sociology.
Jones, J. (2024). Seeking Mavis Beacon: A documentary on exploitation and racial representation in technology. [Film].
Silman, A. (2016). A timeline of Leslie Jones's horrific online abuse.
6 notes
·
View notes
Text
A tour of our System's structure
Inspired by a conversation about the word "host" that developed into comparisons of system structures, we thought we'd draw up some illustrations and diagrams to help us talk about how we work!
This is, essentially, how we visualize our psyche. It's effectively unique to us, but probably bears some resemblance to how others work as well.
We have some speculation as to what visualizations correspond to what actual physical parts of our brain (and a little bit of EEG evidence to back it up), but we're not going to really talk about that much here.
Anyway, to begin with, we have our conscious headspace, which we call
The Bridge

We call it that because, stereotypically, it resembles the bridge of a starship.
Anyone who is on the Bridge is part of the Bridge Crew, and that mix can change up fluidly from second to second. It seems that we have a maximum Bridge Crew of 19 members, but that's a little fuzzy and we haven't thoroughly tested it.
We have three subsystems, the Girls on the left, the Dragons on the right, and the Id Monsters below and in the middle. The Id Monsters might not be a discrete sub system, and may instead be a small group that straddles the Dragons and the Girls (we are not positive either way, but they identify as a group). And we can divide our psyche and our body right down the middle, having one Dragon and one Girl cofronting. Any given Id Monster can replace either the Dragon or the Girl in that situation. We have managed to split three ways, with an Id Monster in the middle, but it was extra tenuous and fragile.
Anyway, at any given moment, we will have one to two Captains present, one of whom will be the primary managing captain. This switches slowly and fluidly throughout the day in sort of natural way. Usually a managing Captain will remain in place from a day to a week or so, but can usually voluntarily switch out with someone else at any time.
The Captains don't typically front, unless there is no one else on the Bridge.
Anyone else on the Bridge can front, and becomes what we call the Pilot. We also frequently just call them the Frontrunner.
The Pilot switches far more frequently than the Captain, usually depending on what task we're doing, what room we're in, who we're talking to, or emotion we're having, or any number of other variables. But also, we can usually switch voluntarily.
Everyone on the Bridge has access to the Bridge's shared working memory, which we call the Drift (after Pacific Rim). The Drift can be broken and resent by a Pilot suddenly leaving the Bridge, unfortunately.
Everyone on the Bridge contributes to working memory and to accessible long term memories. The Captain sets the tone for that, for the collective identity of the Bridge Crew, and manages who comes and goes. Most of our Captains are pretty lenient and accommodating these days, letting anyone come and goes as they please and only settling disputes.
But, OK, the Bridge is our conscious headspace, which means that it is not directly hooked up to our vessel's senses. It is essentially a big holodeck (ala Star Trek) that is run and managed by the Support Staff, who can be found just below the surface in
The Support Room

We're actually still arguing about what to call this place. Technically, it's part of Engineering? But, when we say Engineering, we usually mean a much deeper part of our psyche that's probably our lymbic system. We also have called it Control, or the Server Room.
Anyway, the Support Room has some untold number of awake system members in it, somewhere between hundreds and thousands, if not hundreds of thousands. This is where our Liaisons (factive and fictive introjects) typically hang out waiting to help provide memories of the people and characters we've met and might be trying to communicate with, recognize, or think about.
It's also, we think, representative of all the centers of the neocortex that do the processing that makes the Bridge possible. Like, the visual cortex, the auditory processing centers, linguistics, etc.
And, conceptually, in the center of it is the Auditor's desk. The Auditor is the only "part" that we know of, not a fully member or person, not conscious. It simply counts things, and mostly it is busy counting headmates as they are created. It is because of the Auditor that we know how many headmates we have. And it is probably because of its preoccupation with our population that it gets counts of outworld things wrong sometimes.
The Auditor is, literally, a part of our brain that everyone has. It counts heartbeats, things we see, headmates, everything that needs counting. Everyone has a part of the brain that does this, with varying degrees of accuracy and ease of access. And we've just learned to perceive this part of our brain as the Auditor.
Which looks like this to most of us:

It never, ever leaves its desk. It can only communicate in numbers, yes, no, and silence.
Then, below all that is
Our Inworld
This is a panoramic rendering of the inside of the Sunspot, as we've designed it for our fiction. And it turns out that as we've written our fiction, our actual inworld has come to resemble it more and more.
It's a cylinder, with an area about the size of Oregon and Washington put together lining it, with a forward ice ring, an aft sea, mountains, rivers, forests, and the whole bit.
In this image, the glowing part on the sides is the sun (you're supposed to wrap the image in a sphere for viewing in VR). That would be in the conceptual direction of the Bridge.
The dark hole in the middle is the sun intake of the Aft Endcap, and where the Engine Room is located. In the fiction, it's actually located in the Network and made to look like the sun intake. In reality, it's right there, and that hole is infinitely deep and stretches into our past beyond our birth. It is a way in and out of our system.
Phage, our Chief Engineer and eldest Outsider, lives in there.
When we say "Engineering", we're usually referring to that space, which we also call The Abyss, and its proximity and connection to our lymbic system.
Anyway, there's no point in rendering an image of the Engine room, because it's pitch black.
Our inworld is the shared reality we create when we're dreaming. Sleeping system members are thought to exist here. Awake and active system members who are not participating in Support or the Bridge are vividly dreaming here, usually repeating certain experiences, memories, and visualizations over and over again, in concert with each other, slowly iterating and changing them.
There are entire cultures in our inworld that have developed independently of each other since their creation.
The Auditor reports that we have approximately 4 million people now. Most of whom are factive introjects (what we call Liaisons) of people we've seen on the street, who've since developed their own lives and personalities, filling in the massive blanks that just a face, body type, and posture from a glimpse out of the corner of our eyes leave.
People who are in our greater inworld generally are not available to provide the Bridge with memories or any kind of support, unless the vessel is dreaming. When the vessel is dreaming, Support then feeds the Bridge visuals of what's going on in our Inworld and allows us to interact with the people there. Inworld people can, however join Support or the Bridge any time they want, but usually lose all working memory of what they were just experiencing inworld when they do so.
And all of this can be put in a diagram kind of like this:

19 notes
·
View notes
Text
Welcome to my blog. Im using this account as a diary. As a place to dump my share my honest thoughts, feelings, and ideas as i undergo what is setting up to be a particularly horrific period of american history.
I started this blog because I have felt mentally restless for months and I need an output. I am privileged enough to have access to a high quality education and wonderful friends, and yet I find myself constantly lost in obsessive thought about my own future and the future of my country. I am missing out on the fleeting time I have left in this academic and social environment and I fear that I am wasting it on obsessive rumination. I’ve already talked my friends’ ears off about these topics, and they’re worrying about it on their own too. Our time with each other is normally spent engaging in some form of escapism, which we all need desperately, but I am blocked from fully engaging, which distances me from them. I need to process these issues externally in some form or another, so here I am.
some things to know about me:
- i am a college student
- i am a cis white woman and currently identify as queer, but I am still exploring my sexual identity
- i graduate this spring
- i love biology!
- currently i am…
- a full time student
- working 3 part time jobs
- writing my thesis
- i have never been an independent adult and not a full-time student before. im scared of envisioning what that looks like several months into this presidency.
When trump’s first presidency started, I was close to graduating from middle school. At the time, his political agenda was much less organized, much less effective (in implementing what he wanted to), and I was not the one responsible for my wellbeing. It was scary at the time, but I was not fronting the bill, literally or figuratively, of T’s (read: trump’s) reign.
This time, I’m on my own. My parents pay for my phone bill and facilitate my access to health care, but I am responsible for everything else. News of 25% tariffs on all imports from Canada and Mexico, and 10% on all Chinese imports, has led me to fear for my ability to feed myself. My parents are unable to help me more than they already do. Medical debt has caused them to file for bankruptcy, a clusterfuck which they are unable to manage on their own to begin with.
I struggle with chronic physical and psychological conditions which I struggle to manage. My ability to access healthcare for these conditions, and subsequently my ability to manage my symptoms, is limited for various reasons. I feel the toll of my workload and stress levels every day. Last semester, I was sick for 4 months straight. I took care of myself the best I could.
I am always trying to take care of myself the best I can, because I know no one else can and/or will consistently. Not my family, not my friends, and definitely not my government. I don’t blame my friends and family, but I definitely blame the government for failing to support citizens in the ways that it has promised to. It is because of these false unfulfilled promises that I do not feel anger or resentment towards the ability of myself or those around me to help support our community.
The state of the government has kept me in a cycle of increasingly severe grief since I was 13. Call me the avatar the way I have mastered all 5 stages of grief. I can tap in to each feeling at basically any time. It is frequently overwhelming. I want what everyone else wants. I want to spend time with my loved ones, feel safe, and have secure access to human necessities. I am incredibly lucky to most of those things, and yet it is still difficult to live in a constant state of fear knowing that I, and/or large portions of my fellow citizens, could lose access to these things at any point. There is psychological trauma in the ambient threat of ethno-fascism.
But why now? If these issues have been present in my life for so many years, what about right now was the final straw that led to me finally starting this blog? My reasoning for this is twofold:
1.) Firstly, the timing of this stage of government collapse relative to my emergence into the adult world has not only drastically increased my stress about this (and thus my need to write about it), but I think is particularly interesting from an anthropological. Measuring the changes in my quality of life as I live through this period of history will be interesting to see progress in real time as well as after the fact.
2.) Secondly, I think it is my responsibility as a human to document what I, and many others, predict is about to happen: something akin to Nazi Germany. T’s immediate implementation of mass deportations is, in terms of intent, incredibly similar if not identical to hitler’s Madagascar Plan . Based on america’s actions over the past few years, we are going down a path in which Mexican people (immigrants or not) are to trump’s america the same way in which Jews were to hitler’s Germany.
Though the mass deportations have not yet progressed enough for us to have a more complete understanding of its actual impact, but history has already told us where this leads. I hope I’m wrong. I hope we are all wrong about this. I hope that the president makes choices which actually improve the quality of life for americans and all who live here, but I haven’t been grieving for my country for 8 years for nothing. At this point, our only hope is what it has always been: strength in community organization. I hope people start to see the true path we are going down and that those who voted for it will change their minds and help us try to stop it.
There are a few things I want to address before wrapping up my first post.
I actively recognize that I am in many ways incredibly privileged and have international influence at least in some capacity that citizens of other countries do not have. I will bring this up as it is pertains to the topic at hand in future posts. This information is crucial to my situation, and thus my story, as it provides the societal context in which my experience exists.
I want to make it incredibly clear that I am in no way trying to fear monger with these posts and with the predictions I have about the future. I am not a psychic. I’m 21 years old. I may be intelligent, but that doesn’t stop me from being stupid. I include these predictions and current events not to create worry for the reader but to provide insight into how I am thinking about and processing my current situation. I study biology and neuroscience in school. I am a scientist. I think like a scientist. Much to your dismay, I write like a scientist. This is to say that I am compelled to include my evidence, no matter how palatable it is, to support my point. This may be in the context of expressing an opinion, or in the expression of a feeling so that you can understand where that feeling is coming from. At times, it may feel redundant or like I assume the reader is stupid. However, I do this for the opposite reason. I include this level of information because I know that the reader is intelligent yet uninformed; that is to say the main barrier to a reader’s understanding of what I want to convey is how informed they are, which is my responsibility to facilitate as the writer.
I am incredibly passionate about learning. I view it not as something you do at school but rather a lifestyle. Part of this lifestyle is always being open to the discussion of ideas. I invite readers to discuss, respectfully debate, and constructively critique my ideas and my writing.
However, I do not have the physical, emotional, or spiritual energy to fight with anyone on this app. Please be kind.
We are all doing the best we can with what we have. I find respect for myself and others in this belief.
Wishing us all good health and happiness in the coming years.
XOXO
2 notes
·
View notes
Text
Chapter 4: Part 14: Object Placement
In this environment, every object in the room has a deeper purpose: it’s not about brutality; it’s about carefully managing the Darling’s world, ensuring they feel your presence and influence at all times, even without overt aggression. The goal is to carefully shape their experience so that they feel enveloped in your control, but never overwhelmed.
The Bed: The Centerpiece of Comfort and Control
The bed serves as the anchor of their existence in this space—both a source of rest and a constant reminder of your dominance over their comfort.
Soft Restraints – Use plush, comfortable fabric ties to secure the Darling’s wrists to the bedposts when they lie down. This isn’t about discomfort or punishment, but about closeness and connection. They’ll feel the security of being physically bound to you, reinforcing that even their rest is under your influence.
Personalized Bedding – The bed should be outfitted with bedding that holds your scent—infused into the sheets, blankets, and pillows. It’s a constant sensory reminder that they are in your space, surrounded by your essence. Your presence lingers even when you're not in the room.
A Single Soft Toy or Token – Place a small, comforting object in the bed, such as a plush toy or a token that symbolizes your connection. This could be something you’ve chosen for them—something small but significant, reminding them that their world revolves around you.
Bed Placement – The bed should be placed dead center of the room, not against any wall, allowing it to be easily accessed and directly under your control. The Darling’s immediate focus when entering the room will always be the bed, as it’s where they will return when commanded. This positioning ensures that they are never far from you, whether you're present or not, reinforcing their dependency on you.
The Walls and Lighting: Comforting, Yet Ever-Present
Rather than harsh, unsettling lighting, the focus should be on creating an ambiance that lulls the Darling into a state of calm and obedience.
Soft Lighting with Timed Changes – Use warm, ambient lighting that softly illuminates the room, with the ability to adjust the intensity at different times. The lighting should never be harsh, but should change gradually, reinforcing that your influence is always at play. Perhaps it dims slightly after certain hours, subtly signaling to the Darling that time is moving under your control.
Soft Music or Gentle Whispering – A gentle, soothing melody or ambient sounds can play quietly in the background. Embedded within this sound, gentle whispers might occasionally be heard—words like “I’m here” or “I love you, Darling”—calming them and making sure they’re never truly alone. The whispers are soft enough to remain comforting but present enough to reinforce your constant attention.
Items with Emotional Value: Reinforcing Dependence
The items scattered throughout the room should be designed to make the Darling feel their reliance on you—not through force, but through subtle cues that suggest they belong to you and you alone.
Shared Personal Items – Keep their most cherished belongings close to you, but not immediately accessible. Their favorite book, a piece of clothing they wore when they first met you—these things should be displayed nearby, within their sight but not their reach. They should come to realize that everything they need, everything they value, is in your possession, reinforcing your control over their world.
A Family Photo (You and the Darling) – A photo, framed in a place of prominence, will be the one visual representation of their world. It’s not a photo of the Darling’s past life, but one of you and them together. This photo will be a reminder that their identity, their connection, their home—everything they have—is shared between you two. They should come to view it as a symbol of their place in your world. It’s not just a keepsake; it’s a constant assertion of your control over their existence.
Personalized Comfort Items – Consider placing small items throughout the room that cater to the Darling’s preferences. A specific kind of tea they enjoy, snacks they crave, a pillow with their favorite scent—these personal touches serve to remind them that their comfort, their happiness, comes from you. You are their caretaker, the one who meets their needs, and they should never forget that.
Sound: Presence Without Overt Command
The sound elements in the room should create an atmosphere of comfort and subtle control. It should feel like you’re always near, even if you aren’t physically present.
Regular Quiet Noises of You – Soft sounds, such as the light scuff of footsteps or a quiet sigh, should occasionally be heard through the room. These noises will be faint—enough to remind them that you’re always close. Whether you’re in another room or just outside the door, they’ll feel that subtle presence, always at the edge of their awareness.
(This point has been erased. ~Yandere 💜)
Furniture: Subtle Control and Personalization
The furniture in the room should be arranged to reflect your dominance without making it seem overtly oppressive. The Darling’s space is carefully crafted to meet their needs, but it also keeps them aware that they are in your world, under your influence.
Comfortable, But Secured Furniture – The furniture should be soft, inviting, and comfortable. But nothing should be easily moved—chairs and tables should feel like part of the environment, arranged in a way that keeps them where you want them. A chair for you should be subtly elevated, giving you the advantage of being able to observe the Darling without them feeling overtly controlled. It’s about creating a sense that you are always in charge, without being physically intimidating.
A Special Seating Area for You – Your chair should always be positioned so that you can observe the Darling at all times. It’s not just a place to sit, but a symbolic space that signifies your role as the central figure in their world. They should be aware that you are always just a step away, able to assert yourself at any time. This space should be positioned so that you are watching them without them feeling suffocated.
6 notes
·
View notes
Text
Dear friends and loved ones,
I'm writing to you with great urgency regarding my partner Syd Arrojo/Goddexx. As many of you know, Syd has spent the past few years living a nomadic life since 2021. During this journey, they have started life coaching and professionally holding space for others, and are incredibly gifted in the valuable creative and spiritual work they do. Their intended next step is to work on their memoir I Am Goddexx, which chronicles their experiences as a trans, queer, Two-Spirit person with Peruvian and Cuban roots. This memoir is intended to be a vital resource for not only trans people but all walks of life.
I need to be direct: They are in crisis due to physical and emotional burnout. The constant uncertainty and displacement has taken a severe toll on their physical and mental health. They have been forced to completely stop working, including pausing progress toward their memoir, as they experience serious burnout that requires immediate rest to recover. This isn't just about being tired, this is about survival from the effects of generations of oppressive systems working against QTBIPOC that affect Syd directly.
At this time, Syd requires collective community support to secure $6,000 for stable housing and basic necessities for the next six months. This isn't just about comfort - it's about creating the bare minimum conditions needed to recover their health and rebuild their capacity to work. The violence of forced nomadic life and constant uncertainty pushed them to a breaking point, and even after months of house searching, an appropriate space has not been made available. The severity of Syd’s situation cannot be overstated, and I fear that without stable housing, their health will continue to deteriorate.
If you're able to contribute financially, this is the most direct and immediate way to help. Funds can be directed to Syd via Venmo: @iamgoddexx
However, I understand this isn't possible for everyone. Here are other crucial ways you can support:
Share this request within your networks, especially with those who have the means to help. Sharing this directly and providing context with your networks is the most beneficial. (For example, naming your relationship with Syd/Goddexx and vouching for them while sharing this information through email or social media).
Forward this email to folks with privileged identities and resources who can invest immediate (and ideally, consistent) financial assistance.
Help identify and apply for emergency, artist, and individual grants.
Join a care pod with Syd where support and resources can be mutually provided.
Share and contact individuals you know affiliated with college/universities that have access to event coordination. Syd/Goddexx is looking to book performances to support their income.
Share housing connections you may have that can support Syd’s housing search.
Volunteer for tasks such as managing a kickstarter fundraising page for their memoir, admin tasks to manage email contact collection, draft and send emails, and/or other admin tasks in support of Goddexx’s work.
Share Goddexx's work (gift a tarot session, coaching session, or performance)
Please let me know if you can assist with Syd’s recovery, or if you have any questions. (To avoid overwhelm, please direct questions to me instead of Syd, so they can focus on their rest and recovery). I really hope to see them supported and back on their feet to continue practicing their many gifts, bringing their memoir to life, and ultimately thriving again in community.
Syd via Venmo: @iamgoddexx
#nonbinary#trans#send help#crisis#venmo#trans community#housing help#healer#life coaching#mutual aid
5 notes
·
View notes
Text
Account Introduction!!
♡
-> This part above the cut is a TLDR for users who can’t do longer reading. More information is below the cut 🩶.
♡
TLDR: This is a side blog for @tangerine-segments. We are an autistic dissociative system. Queer + transsexual creature-thing. He/him, it/its, they/them pronouns. Physically disabled + insane. We yap a lot. All mentally ill people welcome here (provided you do not take pride in any harm you do- harm reduction & recovery where possible is good 👍). No DNI, but proudly bigoted/discriminatory blogs will get blocked 🙂↕️. Oke that’s the end of the TLDR!
♡
-> Below the cut here is the extra & more detailed intro… Heayyyyy….. 🗣️.
Omg heayyyy…. Hello! We are Grove. We are the dissociative system behind this account 🤭. Nice to have you here 🫰.
-> Our main blog is @tangerine-segments, which is our system account. It’s also where we have a longer list of our sub-blogs. Most of us will post on this blog at some point, but it’s unlikely we will specify who wrote what.
-> We are autistic + have comorbid neurodevelopmental disabilities. We have a lot of mental illness diagnoses + several diagnosed physical disabilities. Psychotic, dissociative, generally Strange. Brain-body does not work well!
-> Bodily an adult (+ most of us are around body-age). So minors & minor-bodied entities please bear that in mind! However. This is not a NSFW blog, so it is fine for minors + minor-bodied systems to interact. We do swear in posts sometimes though, and often forget to tag warnings for that. If that is an issue please block us or whatever you need to do 🙂↕️ /genuine.
-> Queer freak entity!! We exist in a transsexual body & our host(s) are transsexual men 😗. We all identify with slightly different queer identities- but overall we consider ourselves transsexual, aroace-spec + gay/mlm. Queer is the word we use most because it covers everything nicely 🙂↕️. Uninterested in “discourse” about queerness; identity-policing is not something we will do.
-> Not prosocial (as in we don’t have prosocial emotions like empathy)- but we still do our best to act kindly & behave compassionately. However we often lack the patience/ability to have a back-and-forth conversation. So we will not look at private messages or respond very much in comments. That does not mean we dislike you personally!! We just can’t manage much human interaction because autism + ASPD + the rest hahah. Fellow ASPD-ers are welcome here of course, as are all other personality-disordered & behaviour-disordered folks.
-> We use AAC for all communication (our phone or basic signs). We need mobility aids to get about- and use a wheelchair to get around mostly. So we are visibly disabled + talk about that on here! Medium-high, complex support needs. So please be patient with us 😌.
-> We struggle organising thoughts/words/feelings. We will probably mess up words or phrases even though we edit things multiple times before posting. If we say anything that you cannot understand, or we say something insensitive, please tell us directly!! We will explain and/or correct it. We want this blog to be accessible + safe for marginalised folks. But we will likely mess up sometimes. So if we reblog something that’s gross, or do an image description wrong, or forget an accessibility thing, or say something uneducated- please say!! Please work on assumption that we did not realise and did not intend harm. We welcome constructive feedback + help understanding things 💖 /serious.
-> We have a lot of difficulty processing new information, learning new topics, and have memory problems. Which means we don’t really feel able enough to speak on things we don’t have personal experiences with. So we will do our best just to share information from the folks who know more than us. If we misunderstand something please be patient, we just have a brain that doesn’t work in an abled way 😵💫.
-> No DNI- but we will block any blog that promotes bigotry/discrimination and has no intent to change that. We simply do not have the energy or ability to engage.
-> Okay that’s probably all for now! We have had this in drafts for months and keep forgetting about it. Posting as it is so there’s at least something pinned… Hope you enjoy our silly thoughts if you wish to stay a while 🥳. Bye!!
4 notes
·
View notes