#Physical Identity and Access Management overview
Explore tagged Tumblr posts
Text
#Physical Identity and Access Management market#Physical Identity and Access Management market size#Physical Identity and Access Management share#Physical Identity and Access Management trends#Physical Identity and Access Management analysis#Physical Identity and Access Management forecast#Physical Identity and Access Management outlook#Physical Identity and Access Management overview
0 notes
Text
Intro to Us - Masterpost
We’re The Reflection Family, a collective of over 200 members (so far) in eight different branches sharing a body. Our collective is organized into several distinct groups and categories, reflecting different origins, roles, and characteristics of our coanimans. Each branch has its unique dynamics and members, influenced by their proximity to certain fragments.
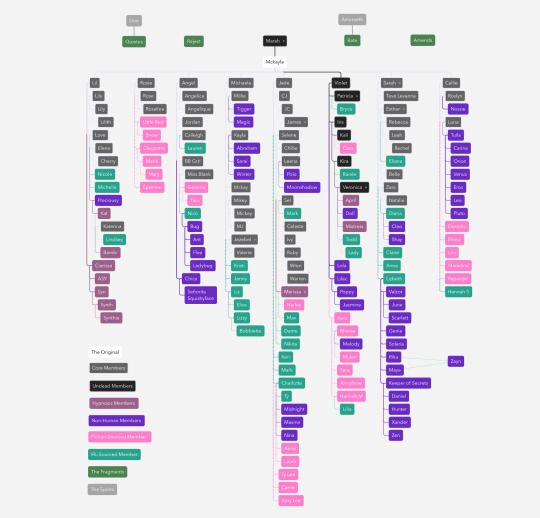
Types of Coanimans: A Guide to Our Color Coding
• The Original (White): Mckayla, the primary coaniman associated with the body.
• Core (Dark Grey): Human coanimans who are direct splits from Mckayla, sharing similar physical traits.
• Undead (Black): Coanimans disconnected from reality due to near-death experiences; not necessarily direct splits.
• Hypnosis (Desaturated Pink): Coanimans created via hypnosis, either accidentally or intentionally.
• Non-Human (Purple): Coanimans that are either direct splits or introjects of animals.
• Fiction-Sourced (Light Pink): Introjects named after fictional characters or celebrities.
• IRL-Sourced (Teal): Introjects from real-life relationships.
• Fragments (Green): Coanimans embodying singular characteristics and influencing nearby parts when co-conscious.
• Spirits (Light Grey): Protective entities or guides within the system.
Overview of Our Structure
Hosts: Who's in the background?
The hosts in the collective not only manage daily life, social interactions, and external relationships but also play a crucial role in preserving long-term memory recall within a collective memory bank. They act as the primary points of interaction with the outside world, ensuring that the collective's needs and responsibilities are met while maintaining a stable presence. By embodying qualities such as adaptability, resilience, and social awareness, the hosts effectively navigate diverse situations and challenges, presenting a cohesive identity to those outside the collective. Through their ability to coordinate with other parts and maintain access to shared memories, the hosts ensure continuity and a functional existence, bridging the internal world with external reality and fostering a sense of cohesion and unity within the collective.
• Veronica - 23-24 - Oversees relationships and social interactions.
• Sel - 17-24 - Manages school-related tasks.
• Selene - 18-24 - Focused on work and professional responsibilities.
• A39 - ageless - Responsible for switching between parts.
The Gatekeepers: Who Runs The System, Really?
The gatekeepers in the collective are vital entities responsible for managing and regulating access to various aspects of the inner world and the collective's complex internal landscape. They oversee the flow of memories, emotions, and information, ensuring that the right coanimans come forward when needed and that sensitive or potentially destabilizing memories are kept at bay until they can be safely processed. The gatekeepers also play a protective role, shielding more vulnerable members from traumatic recollections or overwhelming emotions. By maintaining a delicate balance between different parts and their experiences, the gatekeepers facilitate smoother transitions and interactions within the collective, contributing to overall stability and coherence in navigating daily life and therapeutic work.
• Charlotte - 20-45 - Gatekeeps the IRL subgroup.
• Jade - 15-24 - Oversees the Teens.
• James - 17-19 - Manages the Guys & Gays.
• Sarah - 8-20 - Responsible for the Middles.
• Elena - 8-14 - Oversees the Littles/Munchkins.
• Gemma - 25-45 - Responsible for the Hypnos.
• Patricia - 12-20 - Oversees the Shadows, managing more hidden or complex parts.
• Kara - 4-40 - Helps Fictional-Sourced members.
• Valzor - 30-43 - Manages parts connected to innerworld characters.
The Fragments - The 4 Corners of the Mind
The four fragments—Quietus, Reject, Bate, and Amends—each contribute to the collective's overall balance and resilience, shaping how the group interacts with both its internal landscape and the external world. These fragments represent different approaches to coping, healing, and navigating life's complexities, influencing the way coanimans respond to experiences and challenges. Together, they create a dynamic and multifaceted internal structure that fosters growth, adaptability, and a deeper understanding of self and surroundings, allowing for a cohesive yet varied approach to managing the collective's needs and interactions.
1. Quietus - Control and Repression - Quietus represents control, repression, and emotional suppression. As a fragment, Quietus embodies a deep need for stability, often at the cost of suppressing unwanted emotions and memories. This influence creates an environment where emotional expression is minimized to maintain order and prevent chaos within the system.
2. Reject - Identity and Exclusion - Reject grapples with feelings of rejection, self-worth, and exclusion. This fragment represents the internal struggle with identity and belonging, influencing coanimans who question their value and place within the collective. Reject’s influence is marked by a constant battle for self-acceptance and understanding, reflecting the complexities of identity formation and emotional growth.
3. Bate - Power and Anger - Bate embodies strength, power, and anger. This fragment channels defensive and assertive behaviors to protect or assert boundaries within the system. Bate’s influence is rooted in experiences of confrontation and resilience, shaping coanimans who are unafraid to express anger or assert their needs. This fragment also represents a willingness to fight against perceived threats or injustices, using power as a means of protection.
4. Amends - Comfort and Detachment - Amends focuses on comfort, detachment, and exploration. This fragment embodies the need for emotional solace and the detachment from painful or overwhelming experiences. Amends’ influence encourages exploration of inner worlds, seeking comfort through creativity, fantasy, and introspection. This fragment is characterized by a desire for emotional safety, often finding refuge in inner worlds and imaginative escapes.
Mckayla - The Original Lineage
Mckayla - 10 - The Original: The primary coaniman associated with the body, representing her current maturity level with therapy. Initially, she was stuck at age 6 when parts therapy began but has matured through therapeutic work.
Outside: The Ascended
Marah - The Unborn and Unique Presence
Marah - [Undead]: Represents Selene’s unborn daughter, a unique member within the collective, reflecting themes of unrealized potential and the complex emotional layers surrounding life, loss, and what could have been. She holds a special place in the collective, symbolizing a blend of innocence and the mysteries of existence.

Quietus’ Sphere of Influence - The Repressive Sphere
Quietus - Control and Repression - A fragment of control and repression, Quietus influences coanimans characterized by suppression, emotional restraint, and efforts to maintain stability by managing unwanted emotions and memories.
• Doe - The Watcher - A protective spirit animal within Quietus’ sphere, embodying caution and vigilance, overseeing the coanimans within this line.
Lil’s Line - The Innocence and Attachment Path
Lil’s line focuses on innocence, early childhood memories, and various forms of attachment and loss, exploring how these emotions manifest within the system.
Lil’s Subsystem - The Innocence Path
Lil represents the youngest, most innocent form, embodying early childhood. Her line expands through various aged-up versions that represent a progression from innocence to maturity:
• Lil - 2-4 - The Innocent [Core]: Represents the youngest, most innocent form, embodying early childhood.
• Lils - 5-9 [Core]: An aged-up version of Lil, representing an older and more developed form of innocence.
• Lily - 10-14 [Core]: Aged-up version of Lils; the “big” version, half-cat, half-human, based on the system’s cat.
• Lilith - 16-24 [Core]: The adult version of Lily, embodying a mature form of innocence.
Love’s Subsystem - The Attachment and Loss Line
Love embodies obsessive love and attachment, which further branches out into various representations of love and care, highlighting the complexities of relational dynamics within the system:
• Love - 13 - The Obsessive [Core]: Represents obsessive love, and splits into:
• Elena - 8-14 - The Caregiver [Core]: Represents sibling love and serves as a caregiver to the littles.
• Cherry - 17-18 - The Romantic [Core]: Represents romantic love.
• Nicole - 20-29 - The Sister [IRL]: Represents adoptive family connections.
• Michelle - 20-35 - The Protector [IRL]: Another representation of adoptive family ties.
Preciousy’s Subsystem - The Hypno Line
Preciousy, originally a cat, becomes a Hypno due to a traumatic loss. Her line focuses on themes of loss and trauma, represented by various parts that embody different aspects of these experiences:
• Preciousy - 6-16 - The Lost [Hypno]: Originally the system’s cat, now a Hypno due to trauma.
• Kat - 12-14 - The Feline [Hypno]: Represents a young version dealing with the emotional trauma of loss.
• Katerina [Core]: Further explores the themes of loss and attachment.
• Lindsey [IRL]: Represents deeper feelings of abandonment and healing.
• Bambi - 19 [Hypno]: Represents a mature aspect dealing with sensuality.
Clarissa’s Subsystem - The Machine Line
Clarissa, within Lil’s branch, is a unique entity representing non-human, mechanical aspects, emphasizing themes of emotionlessness and functionality:
• Clarissa - The Machine [Hypno]: A unique, machine-like entity that does not conform to typical human emotions.
• A39 - ageless [Hypno]: A drone responsible for mechanical tasks and operations.
• Syn - ageless [Hypno]: An AI system designed for processing and organizing information.
• Synth - ageless [Hypno]: A teen part handling intermediate tasks.
• Synthia - ageless [Hypno]: The adult part responsible for more complex operations.

Rosie’s Line - The Creative and Resilient Path
Rosie’s line focuses on creativity, resilience, and leadership, exploring themes of beauty, creative spirit, and artistic expression through various coanimans in this line.
Rosie’s Subsystem - The Creative Line
Rosie represents an early emotional split with creative tendencies, leading to various manifestations of creativity and artistic expression:
• Rosie - The Creative [Core]: Represents an early emotional split with a focus on creativity.
• Rose - 14-18 - The Resilient [Core]: Embodies themes of beauty and resilience.
• Rosalina - 10-14 [Core]: Represents a youthful creative spirit continuing Rosie’s theme.
Little Red’s Subsystem - The Survivor’s Path
Little Red explores themes of survival and caution, embodying resilience in the face of adversity:
• Little Red - 4-10 - The Survivor [Fiction]: Represents themes of survival and caution.
• Snow - 14-22 [Fiction]: Embodies themes of cold detachment and perseverance.
Cleopatra’s Subsystem - The Leadership Line
Cleopatra’s line is centered around leadership and heritage, embodying strength and leadership qualities:
• Cleopatra - 16-25 - The Leader [Fiction]: Represents themes of leadership and heritage.
• Marie - 14-18 [Fiction]: Embodies grace and poise.
• Mary - 16-19 [Fiction]: A youthful version dealing with innocence and purity.
Éponine’s Subsystem - The Unrequited Love Line
Éponine’s line represents themes of unrequited love and self-sacrifice, exploring emotional depth and complexity:
• Éponine - [Fiction]: Represents themes of unrequited love and self-sacrifice.

Reject’s Sphere of Influence - The Identity and Exclusion Sphere
Reject - Identity and Exclusion - Embodies the struggle with rejection, self-worth, and belonging, influencing coanimans who grapple with their sense of identity.
Angel’s Line - The Shadowed Innocence and Rejection Path
Angel’s line navigates themes of innocence entangled with feelings of rejection, exploring the dynamics of identity and self-worth through various manifestations within the system.
Angel’s Subsystem - The Shadowed Innocence Line
Angel, rooted in a childhood nickname, deals with themes of shadowed innocence and entrapment, reflecting on memories tied to familial nicknames and shadowy experiences:
• Angel - The Shadowed Innocent [Core]: Connected to a childhood nickname, represents innocence and purity.
• Angelica - [Core]: Trapped in the shadow realm as a child.
• Angelique - [Core]: Adult version who carries shared memories from Angelica’s time in the shadow realm.
Jordan and Caileigh’s Subsystem - The Almost-Identity Line
This subsystem explores identities that almost were, reflecting on alternate life paths and identities that the body might have had:
• Jordan - 8-16 - The Boy That Wasn’t [Core]: Represents a male identity that the body might have had.
• Caileigh - 8-14 - The Twin [Core]: Another almost-name, twin to Jordan.
• Lauren - [IRL]: Based on a real-life school friend.
BB Grrl’s Subsystem - The Nickname Line
BB Grrl represents another nickname that forms a distinct line exploring different facets of identity, shaped by external influences and introjections:
• BB Grrl - [Core]: Nickname-based coaniman.
• Miss Blank - [Core]: Views herself as the stepfather’s daughter.
• Gemma - 25-45 - The Anarchist [Fiction]: Connected to “Sons of Anarchy.”
• Tara - [Fiction]: Also inspired by “Sons of Anarchy.”
Nico’s Subsystem - The Bug Line
Nico’s line represents themes of fragility and resilience, characterized by nonverbal communication and various representations of small, resilient creatures:
• Nico - [IRL]: Introject of stepdad’s son.
• Bug - [Non-Human]: Represents smallness and fragility.
• Ant - [Non-Human]: Embodies diligence and teamwork.
• Flea - [Non-Human]: Represents resilience and survival.
• Ladybug - [Non-Human]: Carries themes of luck and protection.
Chica’s Subsystem - The Lost Doll Line
Chica, embodying a lost childhood object, explores themes of playfulness and loss, reflecting on childhood experiences and the creation of playful personas:
• Chica - [Core]: A Mexican doll reflecting childhood memories.
• Señorita Squishyface - [Core]: A playful persona that emerged from having her cheeks squished together to be cute.

Michaela’s Line - The Familial Memory and Identity Path
Michaela’s line is deeply rooted in family memories and identities, reflecting the various aspects of familial roles, relationships, and the complexities of family dynamics within the system.
Millie’s Subsystem - The Childhood Memory Line
Millie encompasses early childhood memories, capturing the innocence and experiences of youth and representing foundational aspects of the family identity:
• Millie - 0-14 [Core]: Embodies young memories, up to age 14.
• Tigger - [Non-Human]: Represents a past pet horse.
• Magic - [Non-Human]: Represents another past pet horse.
Kayla’s Subsystem - The Animal Care Line
Kayla represents a strong connection to animals and veterinary skills, showcasing a deep commitment to caring for and understanding animals:
• Kayla - [Core]: Represents veterinary skills and animal care.
• Abraham - [Non-Human]: Represents a specific animal connection.
• Sarai - [Non-Human]: Represents another specific animal connection.
• Winter - [Non-Human]: Represents care for a baby squirrel.
Mckay and Mikey’s Subsystem - The Twin Identity Line
Mckay and Mikey explore the dynamics of gender and twin identities, showcasing the fluidity and complexity of self-identification within the system:
• Mckay - [Core]: Represents a genderfluid aspect of Michaela.
• Mikey - 8-15 - The Boy Twin [Core]: Represents a boy version who eventually split into two parts.
• Mickey - 13-18 [Core]: A trans demi-girl.
• MJ - 16-19 [Core]: An older teen boy.
Jezebel’s Subsystem - The Protector and Fighter Line
Jezebel represents themes of protection and fighting spirit, embodying a defensive and assertive role within the system to manage conflict and anger:
• Jezebel - 24 - The Fighter [Core]: Emerged during a physical altercation with a family member.
• Valerie - 24 [Core]: Represents anger and protection.
Liz’s Subsystem - The Maternal Influence Line
Liz, along with her splits, embodies different aspects of maternal influence and roles, reflecting complex relationships with the mother figure:
• Liz - 30 [IRL]: Represents Michaela’s real mother.
• Eliza - 18-30 [IRL]: Represents a Catholic witch version.
• Lizzy - 18-30 [IRL]: Represents a nurse version.
• Bobbiette - 18-30 [IRL]: Represents a best friend from the mother’s high school years.
Support Figures Subsystem - The Guiding and Supportive Influences
This line also includes figures who have provided guidance, support, or therapeutic influence within the system, showcasing roles of caretaking and mentorship:
• Kristi - [IRL]: Represents Michaela’s therapist.
• Jenny - 30-35 [IRL]: Represents a surrogate mother figure.



Jade’s Line - The Intersex and Trauma Identity Path
Jade’s line reflects the complexity of intersex identity and trauma, exploring themes of gender, personal and adoptive identities, and the impact of past relationships and experiences.
Jade’s Subsystem - The Intersex Identity Line
Jade, embracing an intersex identity, due to PCOS, high testosterone, and genetic endometriosis, and navigates the interplay of personal and adoptive identities within hxr subsystem:
• Jade - The Intersex Identity [Core]: Integrates both personal and adoptive identities, reflecting an intersex identity and the navigation of related complexities.
• CJ - The Trans Demi-Guy [Core]: Represents a young trans demi-guy, highlighting an early stage of gender exploration.
• JC - The Teen Male [Core]: An older split from CJ, representing the evolution of gender identity into the teen years.
• James - The Adult Intersex Male [Core]: An adult manifestation of intersex identity, encompassing the culmination of gender exploration and identity solidification.
Selene’s Subsystem - The Trauma and Relationship Line
Selene’s line deals with trauma and relationship dynamics, reflecting on past experiences and the impact of relational ties:
• Selene - [Core]: Central co-host with a large subsystem.
• Chlöe - [Core]: A recent split due to medication changes.
• Leena - [Core]: Holds relationship trauma from the last ex.
• Sel - [Core]: School host, splits into Celeste, Ivy, and Ruby.
• Ruby - [Core]: Holds sexual trauma, splits into:
• Warren (IRL): an ex
• Wren (Core): tied to Warren, possibly undead
• Marissa - 19 - [Hypno]: a bimbo who spits into:
• Harley (Fiction): Harley Quinn
• Mav (IRL): of a past partner
Charlotte’s Subsystem - The Legacy Line
Charlotte’s subsystem encapsulates familial and fictional influences, integrating various introjects that represent different aspects of familial history and personal attachments:
• Charlotte - [Core]: Jade’s grandmother.
• Ty - [Core]: Represents Charlotte’s nephew.
• Midnight - [Non-Human]: Her Mother’s horse.
• Maxine - [Non-Human]: Her Cat.
• Nina - [Non-Human]: Her Sister’s dog.
• Laura Ingalls Wilder - [Fiction]: Fictional introject from “Little House on the Prairie.”
• Anne - [Fiction]: Introject from “Anne of Green Gables.”
Celebrity Influences Subsystem - The Iconic Personas Line
This subsystem reflects the integration of celebrity influences, embodying themes of understanding, strength, and mental health awareness through iconic personas:
• Carrie Fisher - [Fiction]: Represents a connection to mental health advocacy and trauma understanding.
• Amy Lee - [Fiction]: Symbolizes themes of emotional expression and resilience in dealing with personal struggles.

Bate’s Sphere of Influence - The Power and Anger Branch
Bate - Power and Anger - Influences coanimans who embody strength, power, and anger, often manifesting as defensive or assertive behaviors to protect or assert themselves.
• Amaraeth - The Guardian - A guardian spirit within Bate’s sphere, embodying spiritual power and protection, guiding coanimans under Bate’s influence.
Violet’s Line - The Undead Path
Violet’s line explores themes of survival, transformation, and undead characteristics, reflecting on near-death experiences and the journey of strength and resilience.
Violet’s Subsystem - The Undead and Flower Line
Violet starts the undead and flower line due to a near-death experience. This subsystem reflects themes of survival, transformation, and protection:
• Violet - The Survivor [Undead]: Created due to near-death experiences.
• Lilac - [Non-Human]: Represents another part of the flower line.
• Poppy - [Non-Human]: Represents another flower line extension.
• Jasmine - [Non-Human]: Represents further depth in the flower line.
• Iris - 19 - The Defender [Undead]: A defender coaniman above body-age, often managing protection roles.
• Kali - 19-25 [Undead]: Embodies themes of destruction and transformation.
• Cora - [Fiction]: A fictional mother introject, representing nurturing and protection.
• Kira - 14-18 [Undead]: A dominant part during high school.
• Ranèe - [Undead]: A bigender version of a high school best friend.
• Veronica - 23-24 [Half-Undead]: One of the current hosts.
Veronica’s Subsystem - The Host and Introject Line
Veronica’s subsystem explores themes of hosting and introjection, reflecting on relationships and the blending of internal and external influences:
• Veronica - 23-24 [Half-Undead]: One of the current hosts.
• Todd - [IRL]: An introject of the system’s boyfriend.
• Lady - [IRL]: A female introject of the boyfriend.
• April - [Hypno]: A happy hypno part.
• Doll - [Hypno]: Another, this time porcelain, doll
• Mistress - [Hypno]: A Mistress.
Patricia’s Subsystem - The Shadow Realm Line
Patricia, a vampire gatekeeper of the shadow realm, explores themes of memory manipulation and subconscious control, reflecting on the system’s shadow aspects:
• Patricia - 12-20 - The Gatekeeper [Undead]: A vampire gatekeeper of the shadow realm.
• Bryce - 18 [IRL]: Created accidentally during memory repression.
Kara’s Subsystem - The Fictive Gatekeeper Line
Kara (Supergirl) is the gatekeeper of fictives, reflecting on themes of imagination and the role of fiction in shaping internal experiences and identities:
• Kara - 4-40 - The Fictive Gatekeeper [Fiction]: Helps manage fictives and introduces fictional character elements.
• Minnie - 3-8 [Fiction]: Represents “Minnie Mouse,” the mini mom.
• Melody - 4-9 [Fiction]: Represents “Ariel’s daughter,” the mermaid.
• Mulan - [Fiction]: Represents “Mulan,” the warrior.
• Sara - [Fiction]: Represents “The Little Princess.”
• Annaliese - 18-19 [Fiction]: Represents “Barbie (Princess and the Pauper).”
• Hannah M - 12-15 [Fiction]: Represents “Hannah Montana.”
• Lilia - 8-18 [IRL]: Represents an introject from a real-life friend.



Shared Sphere of Influence - The Resilient Power and Comfort Sphere
Shared Influence from Amends and Bate - Power and Comfort -This sphere merges the influences of Bate, emphasizing power and anger, with Amends, focusing on comfort and detachment, creating a blend of strength and comfort-seeking behaviors.
Sarah’s Line - The Faithful and Spiritual Path
Sarah’s line encompasses themes of faith, spirituality, and resilience, reflecting on the journey of inner strength and spiritual connection within the system.
Sarah’s Subsystem - The Faithful and Spiritual Line
Sarah V is a core figure embodying faith and introspection. Her subsystem is diverse, exploring deep spiritual connections and biblical influences:
• Sarah V - The Faithful [Core]: Represents a deep connection to faith and internal reflection.
• Teva Levanna - [Core]: Represents a transformation during conversion classes to Judaism.
Esther’s Subsystem - The Biblical Triad and Protective Spirits
Centered around biblical and protective themes, this subsystem explores different aspects of familial and romantic stories, as well as protection within the system:
• Esther - 16-18 [Core]: Represents a Biblical influence with several splits:
• Rebecca - 8-12 [Core]: Represents a young, foundational Biblical character.
• Leah - [Core]: Represents the “unloved” Biblical figure.
• Rachel - 12-20 [Core]: Represents the “beloved” counterpart.
• Eliana - [IRL]: Represents a protective response to a traumatic experience.
• Belle - [Core]: Represents a romantic influence.
Zara’s Subsystem - The Intellectual and Feline Line
Zara’s line explores intellectual and feline themes, reflecting on scholarly aspects and protective instincts within familial relationships:
• Zara - [Core]: Formerly known as Sarah F.
• Natalie - [Core]: Represents a refined, scholarly aspect.
• Diana - 30-45 [IRL]: Represents a grandmother figure introject with specific traits.
• Cleo - 23 [Non-human]: Represents a sweet, black and white Persian cat.
• Shay - 12-16 [Non-human]: Represents a more reserved and cautious cat.
Aurora’s Kingdom Subsystem - The Inner World Builders
Sarah V also constructed an inner world known as The Kingdom of Aurora, a realm reflecting the system’s creative and spiritual depths. This world is inhabited by various characters and represents the complex interplay between creativity and spiritual introspection:
• Lizbeth - [IRL]: Represents a mother figure in the inner world.
• Valzor - 30-43 [Non-human]: Represents a metaphorical introject and antagonist.
• June - 2-15 [Non-human]: Represents a clone of Jade with embedded trauma memories.
• Scarlett - 8-15 [Non-human]: Represents a clone of Sarah with embedded trauma memories.
• Genie - 30-45 [Non-human]: Represents a shapeshifter with mystical ties.
• Solaria - [Non-human]: Represents a swamp witch with connections to inner narratives.
• Riku - [Non-human]: Represents an advisor to a fictional queen.
• Maya - 45-60 [Non-human]: Represents a slain dragon mother.
• Zayn - 6-19 [Non-human]: Represents her son turned dragon.
• Keeper of Secrets - [Non-human]: Represents a Gorian linked to subconscious thoughts.
• Daniel - 28-33 [Non-human]: Represents a pretty boy introject.
• Hunter - 18-30 [Non-human]: Represents a lover of animals.
• Xander - 25-35 [Non-human]: Represents a photography enthusiast.
• Zen - 35-50 [Non-human]: Represents a peaceful lover.

Amends’ Sphere of Influence - The Comfort and Detachment Sphere
Amends - Comfort and Detachment - Focuses on coanimans who provide comfort or exhibit a significant detachment from the core self, reflecting themes of exploration, longing, and searching for connection.
Callie’s Line - The Detachment and Exploration Path
Callie’s line focuses on themes of detachment, exploration, and the search for connection, often reflecting experiences related to childhood trauma and the longing for belonging and comfort.
Callie’s Subsystem - The Foster Care Twins and Fantasy Line
Callie embodies the detachment experienced during early childhood trauma in foster care. Her direct splits, Roslyn and Luna, explore themes of enchantment and escapism:
• Callie - The Explorer [Core]: Represents the first split in foster care, disconnected from Mckayla directly.
• Roslyn - [Core]: Represents a twin aspect, inspired by the first foster home experience.
• Nessie - [Non-human]: Represents a fae connection from a magical encounter.
Luna’s Subsystem - The Star Wars Galaxy Explorers
Luna’s fascination with space and escapism led her to craft an entire inner world inspired by the Star Wars galaxy, populated by various characters that reflect her desire to explore unknown territories:
• Luna - 8-16 [IRL]: Represents a space-loving, daydreamer persona.
• Tuila - 16 [Non-human]: Represents a “Star Wars” inspired character.
• Carina - [Non-human]: Represents a nebula-inspired character.
• Orion - [Non-human]: Represents another nebula inspiration.
• Venus - [Non-human]: Represents a planet-based inspiration.
• Eros - [Non-human]: Represents an asteroid-inspired character.
• Leo - [Non-human]: Represents a constellation-based character.
• Pluto - [Non-human]: Represents another planet-based inspiration.
Callie’s Fictive Subsystem - The Motherless Characters
Callie also developed a series of fictive alters reflecting themes of abandonment and searching for belonging, focusing on characters who are motherless or seeking maternal connections:
• Dorothy - 14-18 [Fiction]: Represents a motherless fictive who feels homeless.
• Eloise - 9-12 [Fiction]: Represents a character waiting for her mother’s visits.
• Lilo - 6-12 [Fiction]: Represents “Lilo” from “Lilo and Stitch,” symbolizing found family and resilience.
• Madeline - 6-10 [Fiction]: Represents a boarding school student.
• Rapunzel - [Fiction]: Represents a character given up by her parents.
Callie's Adoption and Friendship Subsystem
Callie’s experiences with adoption are explored through parts that reflect themes of identity formation and friendship within an adoptive context:
• Hannah S - [IRL]: Represents a friend introject who is also adopted, symbolizing shared experiences of adoption and identity search.
--- End.
#plural system#dissociative identities#dissociative alters#plural stuff#osddid#plural things#did system#pluralgang#plural posting#plurality#did#dissociative identity disorder#dissociative system#system#system things#traumagenic#traumagenic system#endos are the future
8 notes
·
View notes
Text
The Facility - overview
(World building for my living weapon OCs) CW: living wepaon, dehumanisation, warfare, tortour, extreme conditioning.
Before the outbreak of the global conflict, the Facility was a small-scale organisation known for its expertise in psychological research, interrogation techniques, and psychological warfare. Initially hired by governments for extreme situations, the Facility’s role evolved dramatically as the war escalated.
From a niche contractor, it transformed into a dominant global entity with an expansive network of semi-autonomous complexes.
Evolution of the Facility
With the onset of the global conflict, the Facility transitioned from a third-party service provider to a central force in global affairs. Its operations expanded from dealing with prisoners of war and training operatives in psychological warfare, to capturing and conditioning children - often starting before their 10th birthdays. These children are then molded into specialised roles for the war effort, including front-line combatants, medics, infiltration specialists, engineers, and assassins.
Each Facility complex had its own methods, but the core processes of indoctrination, training, and conditioning remained consistent across the network.
Complex 27: A Closer Look
One of the key facilities in this network is Complex 27, a sprawling, isolated complex designed for discretion and security. Located in a remote rural area, Complex 27 is characterized by its stark, utilitarian design, reflecting the Facility’s emphasis on control and uniformity.
A Block: Dedicated to severe corrections, reconditioning, and decommissioning of assets. It is a place of fear and pain, where assets face their harshest punishments and psychological manipulation.
Purpose: Dedicated to severe corrections, reconditioning, and decommissioning of assets.
Characteristics: Known for its harsh conditions and psychological manipulation. A Block is designed to evoke fear and maintain control over assets who have failed to meet expectations or exhibit signs of disobedience.
Features: Includes isolation cells, sensory deprivation rooms, the "pit", and areas for physical punishment.
B Block: Here lies the medical wing, handlers' offices, briefing rooms, and logistics operations. It’s where the operational side of the Facility functions, managing the flow of assets and ensuring they are prepared for their assignments.
Purpose: The operational hub for the Facility, managing medical care, handler operations, and logistics.
Medical Wing:
Purpose: Provides routine health checks, injury treatment, and management of physical and psychological conditions. The focus is on maintaining functionality rather than long-term health.
Facilities: Equipped with basic medical equipment, examination rooms, and a small operating theater for minor procedures.
Staff: Includes Facility-employed doctors and medics, who prioritize immediate needs and are often viewed with distrust by other assets due to their dehumanized training.
Handlers' Offices:
Purpose: Spaces for handlers to oversee their assigned assets, review performance, prepare mission briefs, and conduct evaluations.
Facilities: Functional and austere, with desks, computers, and communication systems for encrypted coordination.
Interactions: Handlers maintain detailed records, plan development, and manage deployments according to established protocols.
Communication: B Block serves as the central communication hub with encrypted channels to ensure security and prevent unauthorized access.
C Block:
Purpose: Training grounds for younger assets. It focuses on education, conditioning, and isolation from the outside world until assets are ready for their roles.
Characteristics: A place of intense indoctrination, psychological conditioning, and early skill development.
D Block:
Purpose: The residential area where assets and living weapons are housed.
Features: Identical, sparsely furnished quarters, and the mess hall.
Asset Quarters:
Walls and Flooring: The walls are pale grey, contributing to a clinical and sterile atmosphere. The flooring is tiled in the same grey color, easy to clean and maintain.
Sleeping Area: Each quarter contains a small cot with a thin grey blanket. The cot is minimalist, offering just enough for basic rest without comfort.
Storage: There is a metal locker for personal items, though assets are typically limited in what they can keep. The locker is plain and functional, reflecting the lack of personal space or autonomy.
Bathroom: The quarters include a small adjoining bathroom with a shower, toilet and sink. The bathroom is utilitarian, with minimal features designed to meet basic hygiene needs without any luxury.
Desk and Table: A small desk and bedside table are present, serving practical functions but lacking personal touches. These pieces of furniture are simple and unadorned.
Lighting: The lighting in the quarters is bright, designed to keep the space functional and to prevent any shadowy corners where assets might hide or escape. It is on an automatic timer across all quarters, dimming at night and glaring in the day.
Overall Design: The design is uniform across all quarters, with no personalization allowed. This uniformity reinforces the Facility’s control over the assets, eliminating any form of individuality or personal expression.
Training and Conditioning:
Stages of Training: Assets undergo a rigorous, multi-staged process involving indoctrination, specialization, handler training, and advanced training as living weapons. Each stage is designed to strip away personal identity and mold assets into highly effective tools for the Facility’s objectives.
Stage 1: Indoctrination
Focus: This stage involves erasing the asset’s prior identity, using isolation and psychological conditioning to create a blank slate. At the end of this stage, assets receive a number designation, which is tattooed on their neck.
Stage 2: Specialization
Focus: Assets are trained in their specific roles, with severe punishments for any deviation from standard. Complex 27 distinguishes between even-numbered assets (front-line combatants) and odd-numbered assets (who specialize in various other combat based).
Stage 3: Handler Training
Focus: Assets begin working under handlers, integrating into operational roles while being closely monitored and corrected when necessary.
Stage 4: Living Weapons
Symbol: Marked by a brand on the arm, this stage is the pinnacle of an asset’s conditioning, where they become high-priority, specialized weapons. These assets are often deployed in pairs to optimize effectiveness in complex missions.
Defects and Reconditioning:
Criteria for Defects: Includes serious injury, emotional breakdown, or signs of humanity. Defective assets may face 'correction' in A Block, intense reconditioning, or decommission (termination) if they cannot be restored to compliance.
Reconditioning: Involves severe psychological and physical methods to correct defects and restore obedience.
Related masterlists:
Asset 84
On The Run
5 notes
·
View notes
Photo

Let’s talk about something that might seem small but is actually pretty important: finding your account number on your Bank of America debit card. You might be thinking, “Why would I need that? I use my card all the time!” But believe me, knowing where to find your account number, and understanding what it’s for, can save you a lot of headaches down the road. Maybe you need it to set up online bill pay, register for a new service, or even just to verify your identity with customer service. This post will walk you through everything you need to know about locating your Bank of America account number on your debit card, and what to do if you can’t find it. We’ll cover various scenarios, from checking your physical card to accessing your information online, and even what to do if you’ve lost your card. Get ready to become an expert on your own Bank of America account information!
Finding Your Bank of America Account Number: A Comprehensive Guide
Finding your Bank of America account number might seem straightforward, but there are several ways to do it, and understanding them all is key. Let’s explore each method in detail.
1. Checking Your Bank of America Debit Card
This is the first place most people look, and often the easiest. However, it’s important to know exactly where to look.
Where is the Account Number on the Card?
Unfortunately, your Bank of America account number isn’t printed directly on your debit card itself. Many people mistakenly look for it there, but it’s not included for security reasons. This is a common misconception, so don’t feel bad if you’ve been searching in vain!
What is Printed on the Card?
Instead of your account number, your Bank of America debit card will display your card number, which is different. Your card number is used for transactions, while your account number is used for identification and account management.
Why Isn’t the Account Number on the Card?
The absence of the account number on the card is a security measure. If your card is lost or stolen, having the account number visible would make it easier for someone to access your funds.
2. Accessing Your Account Information Online
This is usually the quickest and easiest way to find your Bank of America account number.
Logging into Online Banking
First, you’ll need to log into your Bank of America online banking account. If you don’t already have online access, you’ll need to enroll. This usually involves visiting the Bank of America website and following the instructions.
Locating Your Account Number
Once logged in, your account number is usually prominently displayed on your account summary page. The exact location might vary slightly depending on your account type and the current design of the website, but it’s generally easy to spot. Look for a section that shows your account details or summary.
Using the Bank of America Mobile App
The Bank of America mobile app offers the same convenience as online banking. After logging in, navigate to your account summary or overview section. Your account number should be clearly visible.
3. Checking Your Bank Statements
Your account number is printed on all your Bank of America statements, both physical and digital.
Physical Statements
If you receive paper statements, your account number will be printed clearly at the top or bottom of each statement.
Digital Statements
If you opt for e-statements, your account number will be displayed in a similar location within the digital document. You can usually download and print your statement if you prefer a physical copy.
Statement Availability
Remember that statements are usually generated monthly or on a set schedule. If you haven’t received a recent statement, you might need to wait for the next one or contact Bank of America customer service.
4. Contacting Bank of America Customer Service
If you’ve exhausted all other options, contacting Bank of America customer service is your best bet.
Reaching Out for Assistance
You can reach Bank of America customer service through various channels: phone, online chat, or in-person at a branch. Be prepared to verify your identity to ensure the security of your account.
Information Required
They will likely ask you for personal information to confirm your identity before providing your account number. This is a standard security procedure.
Customer Service Options
Remember to choose the method that’s most convenient for you. The Bank of America website provides contact information for all available channels.
5. Understanding the Difference Between Account Number and Routing Number
It’s crucial to understand the difference between your account number and your routing number. They serve different purposes.
Account Number
Your account number uniquely identifies your specific Bank of America account. It’s used for accessing your account online, making payments, and identifying your account with customer service.
Routing Number
Your routing number identifies the specific Bank of America branch associated with your account. It’s used for electronic transfers, such as direct deposit or wire transfers. You’ll need this number when setting up automatic payments or receiving funds from other banks.
Where to Find Your Routing Number
Like your account number, your routing number is available on your Bank of America statements and through online banking.
What to Do if You Can’t Find Your Account Number
Don’t panic if you’ve tried all the methods above and still can’t find your account number. There are still options.
Check your email: Bank of America often sends emails with account information.
Review old documents: Look through any paperwork related to your account, such as welcome packets or previous statements.
Contact a branch: Visit a local Bank of America branch for in-person assistance.
Summary: Finding Your Bank of America Account Number
Finding your Bank of America account number is essential for managing your finances. While it’s not printed on your debit card, you can easily locate it through online banking, mobile app, bank statements, or by contacting customer service. Remember the difference between your account number and routing number, as both are important for various financial transactions. If you encounter any difficulties, don’t hesitate to reach out to Bank of America for assistance. They are there to help!
We hope this comprehensive guide has helped you understand how to find your Bank of America account number. Do you have any tips or tricks you’d like to share? Have you ever encountered any challenges finding your account number? Let us know in the comments below! And don’t forget to share this helpful information with your friends and family who might also find it useful.
0 notes
Text
Ticketmaster Data Breach Class Action Lawsuit: What You Need to Know

In May 2024, Ticketmaster, a leading ticket sales and distribution company, experienced a significant data breach that compromised the personal information of millions of customers. This incident has led to multiple class action lawsuits, with affected individuals seeking compensation for damages incurred. This article delves into the details of the breach, the ensuing legal actions, and the potential compensation for those impacted.
The Data Breach: An Overview
Between April 2 and May 18, 2024, an unauthorized third party accessed a cloud database hosted by a third-party data services provider, leading to a significant data breach. Ticketmaster identified the unauthorized activity on May 20 and discovered on May 27 that a criminal threat actor appeared to be offering Ticketmaster user data for sale on the dark web. The compromised information included:
Full names
Email addresses
Physical addresses
Phone numbers
Partial credit card numbers
This breach exposed sensitive personal information, putting affected individuals at risk of identity theft and fraud.
Legal Actions Initiated
In response to the breach, several class action lawsuits have been filed against Ticketmaster and its parent company, Live Nation Entertainment. The primary allegations include:
Negligence: Failure to implement adequate cybersecurity measures to protect customer data.
Breach of Implied Contract: Not upholding the implicit agreement to safeguard customers' personal information.
Violation of State Laws: Breaching various state consumer protection and data privacy laws.
One notable lawsuit, filed in Pennsylvania federal court, alleges that the data breach was a direct result of Ticketmaster's failure to implement adequate and reasonable data protection procedures, including vendor management, necessary to protect consumers' personally identifiable information (PII) from a foreseeable and preventable risk of unauthorized disclosure. The plaintiffs argue that the breach has exposed them and other affected consumers to a heightened and imminent risk of fraud and identity theft.
Potential Compensation for Affected Individuals
Individuals affected by the Ticketmaster data breach may be entitled to various forms of compensation, including:
Actual Damages: Reimbursement for financial losses directly resulting from the breach, such as unauthorized transactions.
Statutory Damages: Predetermined amounts set by law for each violation.
Punitive Damages: Additional sums intended to punish the company for its negligence.
Injunctive Relief: Court orders requiring Ticketmaster to implement improved security measures to prevent future breaches.
A successful class action lawsuit could also force Ticketmaster to ensure it takes proper steps to protect the information it was entrusted with and potentially lead to compensation for affected consumers.
Steps to Join the Class Action Lawsuit
If you believe you were affected by the Ticketmaster data breach, consider the following steps to join the class action lawsuit:
Verify Eligibility: Determine if you were a Ticketmaster customer during the breach period and if your personal information was compromised.
Gather Documentation: Collect any relevant information, such as:
Emails or notifications from Ticketmaster about the breach.
Evidence of fraudulent charges or identity theft.
Records of time spent addressing issues arising from the breach.
Contact Legal Representation: Reach out to law firms handling the class action lawsuit to express your interest in joining. They can provide guidance on the necessary steps and documentation required.
For instance, Mason LLP is representing individuals whose personal data was compromised in the breach. They have initiated a mass arbitration process due to Ticketmaster's terms of service, which require disputes to be resolved through arbitration.
Ticketmaster's Response
In the aftermath of the breach, Ticketmaster has stated that customer accounts are safe and that individual Ticketmaster accounts were not impacted by the data breach. However, the company has faced criticism for its handling of the incident, including delays in notifying affected customers and alleged inadequacies in its cybersecurity measures.
Protecting Yourself Moving Forward
Data breaches underscore the importance of proactive personal data protection. Here are steps you can take to safeguard your information:
Monitor Financial Accounts: Regularly check bank and credit card statements for unauthorized transactions.
Change Passwords: Update passwords for online accounts, especially if you use the same password across multiple platforms.
Enable Two-Factor Authentication: Add an extra layer of security to your accounts where possible.
Stay Informed: Keep abreast of any updates from Ticketmaster regarding the breach and follow recommended actions.
Conclusion
The Ticketmaster data breach has significant implications for both the company and its customers. Affected individuals should stay informed about the progress of the class action lawsuits and take proactive steps to protect their personal information. If you believe you were impacted, consider joining the class action lawsuit to seek compensation and hold the company accountable for its data security practices.
#ticketmasterdatabreachclassactionlawsuit#ticketmasterclassactionlawsuitdatabreach#ticketmasterdatabreachclassactionlawsuitcompensation
0 notes
Text
Best Digital Visiting Card Company in Al Ain, Dubai: Enhancing Business Connectivity in the Digital Era In the dynamic landscape of business networking and communication, the advent of digital visiting cards has revolutionized how professionals exchange contact information. Al Ain and Dubai, as bustling hubs of commerce and innovation in the UAE, have witnessed a significant shift towards digital solutions for networking and branding. This article explores the concept of digital visiting cards, their benefits, and highlights a leading company in Al Ain and Dubai that excels in providing these innovative solutions.
Understanding Digital Visiting Cards Traditionally, exchanging business cards has been a cornerstone of professional etiquette and networking. However, with the rise of digital transformation, physical cards are increasingly being replaced by their digital counterparts. Digital visiting cards offer several advantages over traditional paper cards:
Accessibility: Digital cards are stored on smartphones, making them easily accessible anytime, anywhere.
Eco-Friendly: They contribute to reducing paper waste, aligning with sustainable business practices.
Interactive Features: Unlike static paper cards, digital cards can include interactive elements such as clickable links to websites, social media profiles, and multimedia content.
Ease of Update: Updating contact information or adding new details is effortless, ensuring recipients always have the latest information.
Benefits of Using Digital Visiting Cards The transition to digital visiting cards is driven by their numerous benefits, especially in dynamic business environments like Al Ain and Dubai:
Convenience: Professionals can share their digital cards instantly through various messaging platforms, email, or directly via QR codes.
Enhanced Branding: Digital cards can be customized to reflect the brand's identity through logos, colors, and fonts.
Analytics: Some digital card services provide analytics, allowing users to track interactions and engagement with their card.
Cost-Effectiveness: Over time, digital cards prove more cost-effective than printing and reprinting traditional cards.
Choosing the Best Digital Visiting Card Company in Al Ain, Dubai When selecting a digital visiting card provider, businesses in Al Ain and Dubai prioritize reliability, customization options, user experience, and support. One company stands out for its commitment to delivering exceptional digital card solutions:
[Company Name]: (Note: Insert a hypothetical company name that fits the narrative.)
Overview: [Company Name] has established itself as a leader in the digital visiting card industry in Al Ain and Dubai, catering to the diverse needs of businesses across various sectors. They specialize in creating sleek, professional digital cards that resonate with modern networking practices.
Key Features:
Customization: [Company Name] offers extensive customization options, allowing businesses to tailor their digital cards to reflect their unique brand identity effectively.
Ease of Use: Their platform is intuitive, ensuring that even users with minimal technical expertise can create and manage their digital cards effortlessly.
Security: Emphasizing data security, [Company Name] ensures that all information exchanged through their digital cards is encrypted and protected.
Customer Support: Known for their responsive customer support team, [Company Name] assists clients in optimizing their digital networking strategies.
Client Testimonials: Feedback from satisfied clients underscores [Company Name]'s reputation for reliability and innovation in digital business solutions.
Conclusion As businesses in Al Ain and Dubai adapt to the digital age, the role of digital visiting cards in enhancing connectivity and branding cannot be overstated. Choosing the best digital visiting card company is crucial for leveraging these advantages effectively. Whether you are a startup, small business, or a multinational corporation, embracing digital cards can streamline your networking efforts and leave a lasting impression on potential clients and partners.
In conclusion, [Company Name] exemplifies excellence in providing digital visiting card solutions in Al Ain and Dubai, offering customizable, user-friendly, and secure options that empower businesses to thrive in a competitive market. By adopting their services, businesses can elevate their networking capabilities and embrace the future of digital communication seamlessly.
Investing in digital visiting cards isn't just about modernizing; it's about staying ahead in a world where connectivity and efficiency define success. Embrace the future of networking with [Company Name], your partner in digital transformation in Al Ain and Dubai.
0 notes
Text
Scannable ID: A Comprehensive Guide for Businesses
In the digital age, businesses face increasing challenges to ensure security, streamline operations, and provide seamless customer experiences. Scannable IDs have emerged as a critical tool to address these challenges. From improving access control to enhancing customer engagement, these digital and physical identification solutions are reshaping how businesses operate. This guide provides a comprehensive overview of Scannable ID, their applications, benefits, and implementation strategies.
What is a Scannable ID?
A scannable ID is a physical or digital identification card or code embedded with machine-readable information. This data can be accessed using scanners, smartphones, or specialized devices. Common formats include barcodes, QR codes, RFID chips, and magnetic stripes. Scannable IDs are used across various industries for purposes like verification, access control, and transaction facilitation.
Types of Scannable IDs
Barcode IDs
Found on products, tickets, and membership cards.
Stores alphanumeric data readable by barcode scanners.
QR Code IDs
Two-dimensional codes capable of storing more information than traditional barcodes.
Readable by most smartphones, making them versatile for digital interactions.
RFID (Radio Frequency Identification)
Uses radio waves to transmit information.
Commonly used in access control systems and inventory management.
Magnetic Stripe Cards
Stores data on a magnetic stripe that can be swiped for access or transactions.
Widely used in credit cards and employee badges.
NFC (Near Field Communication) IDs
Enables wireless data exchange over short distances.
Popular in mobile payments and smart access systems.
Applications of Scannable IDs in Business
Access Control
Scannable ID are used to grant or restrict access to facilities, ensuring that only authorized personnel can enter secure areas.
Customer Loyalty Programs
Businesses use scannable IDs for loyalty cards, tracking purchases, and rewarding customers with points or discounts.
Event Management
Tickets embedded with scannable codes simplify check-ins and reduce queues at events.
Retail and Inventory Management
Barcode and RFID systems improve inventory accuracy and speed up the checkout process.
Healthcare
Scannable IDs on patient wristbands ensure proper identification, medication, and treatment.
Transportation
Digital boarding passes and tickets enhance passenger convenience and operational efficiency.
Education
Universities and schools use scannable student IDs for attendance, library access, and meal plans.
Benefits of Scannable IDs
Enhanced Security
Scannable IDs reduce the risk of fraud and unauthorized access by verifying identity in real-time.
Operational Efficiency
Automating processes such as check-ins, inventory tracking, and access control saves time and reduces errors.
Cost Savings
Eliminating manual processes and minimizing losses due to fraud or theft can lead to significant savings.
Improved Customer Experience
Faster checkouts, personalized interactions, and seamless loyalty programs enhance customer satisfaction.
Scalability and Adaptability
Scannable ID systems can be scaled and customized to meet the needs of growing businesses.
Implementing Scannable ID Systems
Identify Business Needs
Assess the specific challenges and goals your business aims to address with scannable IDs. For example, are you looking to improve security, enhance customer engagement, or streamline operations?
Choose the Right Technology
Select the scannable ID type that best fits your requirements. For instance, RFID might be ideal for inventory management, while QR codes could be better suited for marketing campaigns.
Integrate with Existing Systems
Ensure the new scannable ID system integrates seamlessly with your current software and hardware.
Train Staff
Provide training to employees on how to use the new system effectively, including troubleshooting common issues.
Test and Optimize
Before full-scale implementation, test the system in a controlled environment to identify potential issues and optimize performance.
Challenges and Solutions
Data Privacy Concerns
Ensure compliance with data protection regulations and implement robust encryption methods to safeguard user data.
Technical Failures
Invest in reliable hardware and software and establish a maintenance schedule to minimize downtime.
User Resistance
Address user concerns through clear communication about the benefits and ease of use of scannable IDs.
Costs of Implementation
While initial setup costs can be high, focusing on long-term ROI can help justify the investment.
Future Trends in Scannable ID Technology
Biometric Integration
Combining scannable IDs with biometric authentication for enhanced security and convenience.
Blockchain for Secure Data Storage
Using blockchain technology to ensure tamper-proof and transparent record-keeping.
AI and Machine Learning
Leveraging AI to analyze data from scannable IDs for personalized marketing and operational insights.
Wearable Devices
Embedding scannable ID functionality in smartwatches and other wearable tech.
Conclusion
Scannable IDs are transforming the way businesses operate by improving security, efficiency, and customer engagement. By understanding the different types, applications, and implementation strategies, businesses can leverage this technology to stay competitive in an increasingly digital landscape. With continuous advancements in technology, the potential of scannable IDs will only grow, making them an essential tool for modern businesses.
0 notes
Text
Choosing the Right Biometrics Attendance System: A Comprehensive Guide
Businesses increasingly rely on advanced biometric attendance systems, which provide highly secure, efficient, and foolproof methods to monitor and record attendance. These systems use unique biological traits — such as fingerprints, facial recognition, or even iris scans — to verify an individual’s identity. Choosing the right biometric attendance system is essential, as it directly impacts productivity, security, and ease of use in your organization.

This guide will walk you through the key considerations, types, and benefits of biometric attendance systems to help you make the best choice for your needs.
1. Understanding the Importance of Biometrics in Attendance Management
Biometric attendance systems utilize unique physical or behavioral characteristics to authenticate employees, making them an excellent choice for security and accuracy. Unlike traditional systems, biometric systems eliminate the possibility of “buddy punching,” where an employee punches in on behalf of someone else. With biometric attendance, only the authorized individual can log their entry or exit, enhancing accountability and reducing fraud.
Additionally, biometric attendance systems streamline HR tasks by automating time-tracking processes. Instead of reconciling manual entries or scanning for errors, attendance data is automatically stored in a digital format, simplifying payroll processing and ensuring compliance with labor laws.
2. Key Features to Look for in a Biometrics Attendance System
When evaluating different biometric systems, certain features are essential for seamless integration into your business processes. Here are some critical factors:
Accuracy and Speed: A good biometric system should verify identities within seconds without compromising accuracy. Systems with high-quality sensors and algorithms provide faster, more accurate readings.
Data Security: Biometric data is highly sensitive, and protecting it should be a top priority. Look for systems with data encryption, secure storage, and compliance with data protection regulations.
Ease of Use: Choose a user-friendly system that minimizes training time and can be easily integrated with your existing attendance software.
Scalability: As your business grows, your attendance system should be able to handle an increasing number of users without compromising efficiency.
Remote Access: For businesses with multiple locations or remote teams, cloud-based solutions with remote access capabilities are essential. This allows HR teams to monitor attendance across various locations from a single platform.
Integration with Payroll: Systems that integrate with payroll software streamline the end-of-month salary process by providing automated attendance data, reducing the likelihood of payroll errors.
3. Types of Biometrics Attendance Systems
There are several types of biometric technologies used in attendance systems, each with unique features, benefits, and limitations. Here’s an overview of the most popular types:
Fingerprint Recognition: One of the most common types, fingerprint recognition, uses a person’s unique fingerprint patterns to verify identity. It’s affordable and effective but may struggle with accuracy in cases of worn fingerprints (e.g., from manual labor).
Facial Recognition: Facial recognition systems use a person’s facial features to verify their identity. With the advancement of AI, facial recognition has become highly accurate and is often touchless, reducing concerns over hygiene.
Iris Recognition: This type uses the unique pattern of a person’s iris. Known for its high accuracy, iris recognition is often used in high-security settings, though it tends to be more expensive than other biometric options.
Voice Recognition: Voice recognition systems authenticate individuals based on unique vocal patterns. Though convenient, voice recognition can be influenced by background noise and may not be suitable for all environments.
Palm Vein Recognition: Palm vein systems are relatively new and highly secure, using the unique pattern of veins in the palm. They are contactless and more resistant to fraud but are also among the more costly options.
4. Advantages of Implementing a Biometric Attendance System
Opting for a biometric attendance system can provide your organization with numerous benefits, including:
Enhanced Security: By using unique biometric data, the system significantly reduces the risk of unauthorized access or “buddy punching.”
Accurate Time Tracking: Biometric systems ensure accurate time records by preventing manual errors, which can lead to more precise payroll calculations and compliance with labor regulations.
Cost Savings: Automated attendance tracking saves HR teams time and reduces administrative costs associated with traditional time-tracking methods.
Increased Employee Accountability: Biometric systems make it difficult for employees to manipulate attendance data, leading to greater accountability and a more disciplined workforce.
Scalability: Many biometric systems are designed to scale with your organization, making it easier to add new employees or even locations without significant changes to the system.
Integration with Access Control: Some biometric attendance systems double as access control systems, allowing only authenticated employees to enter restricted areas, further enhancing workplace security.
5. How to Choose the Right Biometric Attendance System for Your Business
Choosing the right system depends on your unique organizational needs and budget. Here are some steps to guide your decision:
Evaluate Your Needs: Start by assessing your attendance tracking needs. Do you need a system that handles a large volume of employees, or one that operates across multiple locations? Understanding these factors will narrow down your options.
Consider the Environment: Certain biometric technologies may be better suited for particular environments. For example, facial recognition systems are more hygienic in high-traffic areas, while fingerprint recognition may be ideal for smaller offices.
Assess Security Measures: Look for a system that offers encryption, secure storage, and meets compliance standards. Data security is crucial, as biometric data is sensitive information.
Budget: Biometric systems vary significantly in cost. While iris and palm vein recognition tend to be more expensive, fingerprint and facial recognition systems are more budget-friendly.
Vendor Support and Maintenance: Ensure the provider offers reliable support and maintenance. Regular updates and quick response times for troubleshooting are essential for a smooth user experience.
6. Future Trends in Biometrics Attendance Systems
The biometric attendance industry continues to evolve, with several trends gaining momentum:
AI-Powered Recognition: AI advancements are making facial and voice recognition more accurate and adaptable, even in challenging environments or lighting conditions.
Touchless Systems: The pandemic accelerated the demand for contactless systems like facial recognition and palm vein scanning, which are likely to become standard in the coming years.
Cloud Integration: More businesses are opting for cloud-based biometric attendance systems, which allow remote access and centralized data management.
Multi-Factor Authentication (MFA): Combining biometric data with other authentication methods, like access codes or mobile verification, further enhances security.
For businesses seeking a reliable biometric attendance solution, exploring comprehensive platforms like Spintly could be a strategic choice. Spintly offers wireless, cloud-based biometric attendance solutions that integrate seamlessly with access control, making it ideal for organizations looking to modernize their attendance management.
Conclusion
A biometric attendance system is an investment in accuracy, security, and operational efficiency. By selecting a system that aligns with your business’s specific requirements, you can ensure reliable attendance tracking, minimize errors, and foster a disciplined work environment. As biometric technology continues to advance, implementing a system today can future-proof your organization against the growing demands of workforce management.
Taking the time to research and choose the right solution will pay off in enhanced productivity and streamlined attendance processes. If you’re ready to explore a comprehensive, wireless attendance system, look into industry-leading options like Spintly, which combine cutting-edge technology with user-friendly features to support modern workforce needs.
#biometrics#smartacess#accesscontrol#mobile access#visitor management system#access control system#spintly#access control solutions#smartbuilding
0 notes
Text
5 Ways Visitor Management Systems Improve Business Security

In today’s fast-paced and interconnected world, ensuring the safety and security of any organization is a top priority. A visitor management system plays a vital role in achieving this goal by helping businesses streamline and enhance the way they handle visitors. Whether it’s a corporate office, educational institution, or healthcare facility, managing visitors effectively not only strengthens security but also boosts efficiency and improves the overall experience for everyone involved.
Visitor management systems have evolved significantly from the traditional sign-in sheets to advanced visitor management software, which allows organizations to track, monitor, and manage visitors in real-time. In this post, we’ll explore what a visitor management system is, its benefits, and how adopting a modern solution can help your organization stay secure while improving operations.
What is a Visitor Management System?
A visitor management system is a digital solution that automates the process of tracking and managing visitors in a workplace or facility. This system replaces outdated methods like paper sign-in sheets, providing an efficient, secure, and professional way to manage visitor information.
By using a visitor management system, businesses can pre-register guests, issue digital badges, track entry and exit times, and maintain a detailed log of all visitors. This data can be accessed in real-time, helping organizations maintain accurate visitor records and improve security protocols.
Why is a Visitor Management System Important?
The importance of having a visitor management system goes beyond just signing visitors in and out. Here are some key reasons why it is crucial for modern businesses:
Enhanced Security: A visitor management system ensures that only authorized individuals gain access to your facility. By pre-screening visitors and verifying their identities, you can prevent unauthorized entry and reduce security risks.
Streamlined Operations: A digital system automates the entire visitor process, allowing receptionists and security staff to focus on other tasks. This increases productivity and reduces the time spent managing visitors.
Compliance: Many industries require organizations to keep detailed records of visitor activity for safety and legal reasons. A visitor management system helps businesses stay compliant with data protection regulations by securely storing visitor information.
Improved Visitor Experience: Visitors appreciate a seamless and professional check-in process. With a visitor management system, they can pre-register online, receive QR codes, and bypass long queues at the front desk.
Real-Time Notifications: Notify staff members instantly when their visitor arrives, saving time and ensuring a smoother visitor experience.
Key Features of a Modern Visitor Management Software
A modern visitor management software goes beyond basic visitor tracking. It offers a range of advanced features designed to improve security, compliance, and the overall visitor experience. Here are some essential features to look for:
1. Pre-Registration and Self Check-In
With visitor management software, visitors can pre-register before their visit, making the check-in process faster and more efficient. Self-check-in kiosks also enable guests to sign in without assistance, saving time and reducing the workload for front desk staff.
2. Visitor Badges and QR Codes
Visitor badges and QR codes provide an easy way to identify visitors. Digital badges are sent to visitors' mobile devices, allowing them to check in using their phones. This reduces the need for physical badges and enhances security.
3. Integration with Security Systems
To further boost security, visitor management software can integrate with existing security systems such as surveillance cameras, access control, and alarm systems. This integration provides a complete overview of visitor activity in real-time.
4. Real-Time Visitor Tracking
Organizations can monitor visitors throughout their stay, ensuring they are only in authorized areas. Real-time tracking also provides insights into peak visitor times, helping improve staffing and facility management.
5. Customizable Workflows and Notifications
A customizable visitor management software allows organizations to tailor the check-in process based on their specific needs. Notifications can be sent to relevant staff members when a visitor checks in, improving communication and response time.
6. Data Storage and Analytics
The software stores visitor data securely and provides analytics that helps businesses identify patterns, such as frequent visitors or high-traffic times. This information is invaluable for making informed decisions about security and operations.
Benefits of Implementing a Visitor Management Software
By transitioning from traditional methods to a visitor management software, organizations stand to gain a multitude of benefits that can enhance security, efficiency, and compliance. Let’s take a closer look at the main advantages:
1. Increased Security
Automated visitor tracking ensures that only authorized individuals are allowed access to your facility. By pre-screening visitors and keeping accurate logs, businesses can mitigate risks and respond quickly in case of a security breach.
2. Operational Efficiency
By eliminating the need for manual sign-ins, visitor management software streamlines the check-in process, freeing up front desk staff to focus on more important tasks. The system also ensures that visitors do not experience unnecessary delays upon arrival.
3. Compliance with Regulations
Many industries, such as healthcare, education, and finance, require strict record-keeping for visitors. A visitor management system helps businesses stay compliant with regulations by securely storing data and providing audit-ready reports.
4. Enhanced Visitor Experience
An efficient and smooth check-in process leaves a positive impression on visitors. With features like pre-registration and self check-in, visitors spend less time waiting and more time engaging with their host.
5. Cost Savings
A digital visitor management software reduces the need for paper logs and physical badges, cutting down on administrative costs. Additionally, its automated features reduce the need for additional staff to manage visitor check-ins.
How to Choose the Right Visitor Management System
With many options available, selecting the right visitor management system can be overwhelming. To ensure that you make the right choice for your organization, consider the following factors:
1. Ease of Use
The system should be easy to use for both staff and visitors. An intuitive interface and user-friendly design will encourage adoption and minimize training requirements.
2. Scalability
Choose a system that can grow with your business. As your organization expands, your visitor management software should be able to handle increased visitor traffic and adapt to new security needs.
3. Integration Capabilities
Ensure that the software integrates seamlessly with your existing security systems, such as surveillance cameras, access control, and employee directories.
4. Customization Options
Every organization has unique security and operational needs. Look for a solution that allows you to customize workflows, notifications, and visitor badges to suit your requirements.
5. Compliance Features
If your industry requires detailed visitor logs or follows strict data protection regulations, choose a system that offers robust compliance features, such as secure data storage and detailed reporting.
Conclusion
Implementing a visitor management system is a critical step for organizations that prioritize security, efficiency, and compliance. By replacing outdated manual processes with modern visitor management software, businesses can enhance security, streamline operations, and create a better experience for visitors.
Whether you are a small office or a large facility, adopting a visitor management system will provide you with the tools needed to track visitors effectively and maintain a safe, secure environment for your staff and guests. Take the step towards better security and improved operations by exploring the right visitor management software for your organization today.
#Visitor Management#Visitor Management System#Visitor Tracking#Security Solutions#Digital Check-In#Visitor Experience#Compliance Management#Operational Efficiency#Access Control#Workplace Security#Business Solutions#Visitor Management Software#Pre-Registration#Real-Time Monitoring#Data Analytics#Safety Protocols#Automation#Facility Management#Guest Management#Healthcare Security
0 notes
Text
Ensuring Security in OTA Activation: ROTA Server Best Practices
Over-the-air (OTA) activation has become an essential process for deploying updates, enhancing functionality, and ensuring the seamless performance of connected devices. With the rapid growth of IoT (Internet of Things) technologies, the security of OTA activation processes, especially through ROTA (Remote OTA) servers, is paramount. This blog outlines best practices to ensure security in OTA activation, emphasizing strategies to safeguard your devices and networks.
Understanding OTA Activation
OTA activation refers to the process of remotely deploying software updates, firmware upgrades, or new features to connected devices over wireless networks. This method is particularly beneficial for managing large fleets of devices without requiring physical access. However, the convenience of OTA activation also poses significant security risks. Hackers may exploit vulnerabilities in the OTA activation process to gain unauthorized access to devices, steal sensitive data, or disrupt operations.
Importance of Secure OTA Activation
The importance of secure OTA activation cannot be overstated. With an increasing number of connected devices, the attack surface for cyber threats expands significantly. Ensuring that the OTA activation process is secure helps protect against:
Data breaches: Unauthorized access to sensitive data can lead to significant financial and reputational losses.
Device manipulation: Hackers can manipulate device behavior, leading to potential safety hazards.
Service disruptions: Attackers may cause service outages, impacting user experience and business operations.
To mitigate these risks, businesses must adopt best practices for securing their OTA activation processes.
Best Practices for Securing ROTA Servers
1. Implement Strong Authentication Mechanisms
To secure OTA activation, it is crucial to implement robust authentication mechanisms. This ensures that only authorized personnel can access and manage the ROTA server. Strong authentication methods include:
Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of identification.
Role-Based Access Control (RBAC): RBAC restricts access based on the user’s role within the organization, ensuring that only necessary permissions are granted.
2. Encrypt Data in Transit and at Rest
Data encryption is a fundamental practice for ensuring the security of OTA activation. Encrypting data during transmission protects against interception by unauthorized parties. Similarly, encrypting data stored on the ROTA server ensures that even if an attacker gains access to the server, they cannot easily access sensitive information.
TLS (Transport Layer Security): Use TLS protocols to encrypt data in transit between devices and the ROTA server.
AES (Advanced Encryption Standard): Encrypt sensitive data stored on the ROTA server using AES for robust security.
3. Regularly Update Software and Firmware
Keeping software and firmware up-to-date is essential for maintaining security. Software updates often contain patches for vulnerabilities that could be exploited by attackers.
Automated Updates: Implement automated systems for pushing updates to ensure devices are consistently running the latest versions.
Change Management Policies: Establish policies for evaluating and applying updates to minimize risks associated with software changes.
How OTA Activation Works: A Brief Overview
OTA activation typically involves several key steps to ensure a secure and efficient process:
Device Registration: Devices must be registered with the ROTA server before they can receive updates. This process usually involves verifying the device's identity.
Update Verification: Before an update is deployed, the ROTA server verifies its authenticity and integrity. This step often includes cryptographic signatures to ensure the update comes from a trusted source.
Deployment: Once verified, the update is transmitted to the device over a secure channel. Devices may be required to confirm the update before installation, ensuring the user is aware of the change.
Monitoring and Reporting: Post-deployment, devices report their status back to the ROTA server, allowing for monitoring and troubleshooting as needed.
4. Utilize Secure APIs
APIs play a critical role in the OTA activation process, especially when integrating with third-party services. It is essential to ensure that APIs are secure to prevent unauthorized access and data breaches.
API Authentication: Implement strong authentication methods for APIs, such as OAuth 2.0 or API keys.
Rate Limiting: Use rate limiting to prevent abuse of APIs, which could lead to denial-of-service attacks.
5. Monitor and Audit OTA Activities
Continuous monitoring and auditing of OTA activation are vital for identifying and mitigating potential security threats.
Log Analysis: Regularly analyze logs for unusual activity or unauthorized access attempts. Automated tools can help streamline this process.
Alerts and Notifications: Set up alerts for critical events, such as failed login attempts or unauthorized update requests.
6. Conduct Regular Security Assessments
Conducting regular security assessments helps identify vulnerabilities within the OTA activation process and the ROTA server.
Penetration Testing: Perform penetration tests to simulate attacks on the OTA activation process, helping to identify weaknesses before they can be exploited.
Vulnerability Scanning: Use automated tools to scan for known vulnerabilities in the ROTA server and connected devices.
Conclusion
Ensuring security in OTA activation is crucial for protecting connected devices and maintaining the integrity of business operations. By implementing the best practices outlined above, organizations can significantly reduce their risk of security breaches and ensure a reliable OTA activation process. As the IoT landscape continues to evolve, staying informed about the latest security measures will help businesses adapt and thrive in a connected world.
Investing in secure OTA activation processes not only protects sensitive data but also fosters trust among users and stakeholders, paving the way for successful digital transformation.
0 notes
Text
Latest Updates For Confidential VMs Google In Compute Engine

Confidential virtual machine overview
Confidential VMs Google
One kind of Compute Engine virtual machine is a confidential virtual machine (VM). To help guarantee that your data and applications cannot be read or altered while in use, they employ hardware-based memory encryption.
Below are some advantages of confidential virtual machine instances:
Isolation: Only specialized hardware, unavailable to the hypervisor, generates and stores encryption keys.
Attestation: To ensure that important parts haven’t been tampered with, you can confirm the identity and condition of the virtual machine.
A Trusted Execution Environment is a term used to describe this kind of hardware isolation and attestation (TEE).
When you create a new virtual machine instance, you have the option to activate the Confidential VM service.
Confidential computing technology
Depending on the machine type and CPU platform you select, different Confidential Computing technologies can be employed while setting up a Confidential VM instance. Make sure the technology you select for Confidential Computing meets your budget and performance requirements.
AMD SEV
AMD Secure Encrypted Virtualization (SEV) on Confidential VM provides boot-time attestation using Google’s vTPM and hardware-based memory encryption via the AMD Secure Processor.
AMD SEV provides excellent performance for computationally intensive activities. Depending on the workload, the performance difference between a normal Compute Engine VM and a SEV Confidential VM can be negligible or nonexistent.
AMD SEV systems using the N2D machine type offer live migration, in contrast to other Confidential Computing technologies using Confidential VM.
AMD SEV-SNP
Adding hardware-based security to assist thwart malicious hypervisor-based attacks like data replay and memory remapping, AMD Secure Encrypted Virtualization-Secure Nested Paging (SEV-SNP) builds on SEV. Direct attestation results from the AMD Secure Processor are available upon request at any time.
Compared to SEV, AMD SEV-SNP requires greater resources due to its increased security measures. In instance, you may see higher network latency and decreased network bandwidth based on the demand.
TDX Intel
A hardware-based TEE is Intel Trust Domain Extensions (TDX). In order to manage and encrypt memory, TDX employs hardware extensions to establish an isolated trust domain (TD) inside of a virtual machine (VM).
By enhancing the defense of the TD against specific types of attacks that require physical access to the platform memory, such as active attacks of DRAM interfaces that involve splicing, aliasing, capturing, altering, relocating, and modifying memory contents, Intel TDX enhances the defense of the TD.
Confidential VM service
Confidential VM is used by the following Google Cloud services in addition to Compute Engine:
Secret All of your Google Kubernetes Engine nodes are required to use Confidential VM.
With a mutually agreed-upon workload, Confidential Space employs Confidential VM to allow parties to share sensitive data while maintaining ownership and confidentiality of that data.
Confidential VM-using Dataproc clusters are part of Dataproc Confidential Compute.
Features of Dataflow Confidential VM worker for dataflow confidential virtual machines.
Google Cloud is dedicated to keeping your data under your complete control and safe and secure. To start, use Confidential Computing to strengthen the Compute Engine virtual machines (VMs), which are the cornerstone of your compute architecture.
Using a hardware-based Trusted Execution Environment (TEE), Confidential Computing safeguards data throughout use and processing. TEEs are safe, segregated spaces that guard against illegal access to or alteration of data and applications while they’re in use.
Confidential Computing technologies and solutions have been early adopters and investments for us at Google. Google customers have been utilizing their expanded Confidential Computing products and new capabilities for over four years, utilizing them in creative ways to improve the security and confidentiality of their workloads. It was excited to announce the broad release of upgrades to the Google Cloud attestation service as well as numerous additional Confidential Computing choices.
Currently accessible to most people: Segmented virtual machine with AMD SEV on C3D platforms
It is pleased to inform you that Confidential VMs Google equipped with AMD Secure Encrypted Virtualization (AMD SEV) technology are now widely accessible on the general purpose C3D machine line. Using hardware-based memory encryption, Confidential VMs with AMD SEV technology help guarantee that your data and apps cannot be read or changed while in use. With Google’s Titanium hardware, the C3D machine series is built to provide optimal, dependable, and consistent performance, and is powered by the 4th generation AMD EPYC (Genoa) processor.
Prior to this, only the general-purpose N2D and C2D machine series offered Confidential VMs. The latest general purpose hardware with enhanced performance and data secrecy is now available to security-conscious customers with the expansion to the C3D machine line. Better performance comes from using the newest gear. Read more about the performance of the C3D machine series and confidential virtual machines here.
In any region and zone where C3D machines are available, confidential virtual machines featuring AMD SEV are accessible.
Now widely accessible: Intel TDX-powered confidential virtual machine on the C3 machine series
Confidential VMs Google equipped with Intel Trust Domain Extensions (Intel TDX) technology are now widely accessible on the general-purpose C3 machine series. Using hardware-based memory encryption, Confidential VMs with Intel TDX technology help guarantee that your data and apps cannot be read or changed while in use.
There are no code changes needed to enable confidential computing on a C3 virtual machine. You can use Intel Trust Authority’s remote attestation service or your own attestation provider to confirm that your hardened virtual machine (VM) is operating in a TEE. The 4th generation Intel Xeon Scalable CPUs (code-named Sapphire Rapids), DDR5 memory, and Google Titanium power the C3 machine line.
Intel AMX integrated CPU acceleration
By default, all C3 virtual machines (VMs), including Confidential VMs, have Intel Advanced Matrix Extensions (Intel AMX) enabled. To speed up workloads related to machine learning and artificial intelligence, Intel AMX is a novel expansion to the instruction set architecture (ISA). Two of the most popular processes in AI and ML are matrix multiplication and convolution, which may be carried out with the new instructions that AMX offers. You can execute AI/ML applications with an extra degree of protection by combining Intel AMX with Confidential VMs.
Asia-southeast1, US-central1, and Europe-west4 are the regions where Confidential VM with Intel TDX on the C3 machine series is accessible.
Confidential VM with AMD SEV-SNP on the N2D machine series is now widely accessible
Customers now have access to Confidential VMs with hardware-rooted attestation, data integrity, and data confidentiality thanks to the release of AMD Secure Encrypted Virtualization-Secure Nested Paging (AMD SEV-SNP) on the general purpose N2D machine series this past June. Prior to this, users could only access private VMs with AMD Secure Encrypted Virtualization (SEV), a private computing solution that guaranteed data confidentiality.
All Confidential VMs give users an extra line of defense and data protection against cloud administrators, operators, and insiders while also enabling them to retain control over their data in the public cloud and achieve cryptographic isolation in a multi-tenant environment. Confidential VMs with AMD SEV-SNP, on the other hand, come with further security measures that guard against harmful hypervisor-based assaults such memory remapping and data replay.
AMD SEV-SNP on the N2D machine series makes it simple and doesn’t require any code changes to create Confidential VMs. You also get the security advantages with less impact on performance.
Asia-southeast1, US-central1, Europe-west3, and Europe-west 4 are the regions where confidential virtual machines with AMD SEV-SNP on the N2D machine series are accessible.
Signed Intel TDX and AMD SEV-SNP UEFI binaries for Confidential Virtual Machines
With the addition of signed startup measures (UEFI binaries and initial state) to its Confidential VMs running AMD SEV-SNP and Intel TDX technologies, it is thrilled to announce a major security improvement. By signing these files, provided an additional degree of security against unauthorized changes or tampering with UEFI, the firmware that manages a computer’s startup procedure.
Gaining further transparency and confidence that the firmware operating on your Confidential VMs is authentic and uncompromised can be achieved by signing the UEFI and enabling you to validate the signatures. Your authenticated devices are operating in a secure and reliable environment if you can confirm the validity and integrity of the firmware.
Google intends to take other actions to create a system that is more verifiably reliable and secure.
AMD SEV Confidential VM is now supported by Google Cloud attestation
If your trust model permits it, you can use the Google Cloud attestation service in place of creating and executing an attestation verifier yourself. Use the Go-TPM tools to obtain an attestation quote from the vTPM of an AMD SEV Confidential VM instance, then transmit it to the Google Cloud Attestation service using the./go-tpm token command for verification.
You can verify whether or not the virtual machine (VM) can be trusted by comparing its details with your own policy once the Google Cloud Attestation has verified the attestation quote. Only AMD SEV is currently supported by Google’s attestation service.
Confidential VM costs
In addition to the Compute Engine price, there are additional expenses for Confidential VM. The cost of a Confidential VM instance is determined by several factors, including the type of Confidential Computing technology (such as AMD SEV, Intel TDX, or AMD SEV-SNP) and whether the instance is preemptible or on demand. The fees are flat rate per vCPU and per GB for Confidential VM.
See here for the price of the Confidential VM. See this page for Compute Engine’s price list.
Read more on Govindhtech.com
#ComputeEngine#virtualmachine#VMinstance#VMservice#ComputeEngineVM#TDXIntel#GoogleKubernetesEngine#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
0 notes
Text
What Are the Benefits of Using Office 365 Email Hosting Abu Dhabi for Businesses?
Office 365 Email Hosting has become a vital tool for businesses worldwide, enabling organizations to streamline their communication and collaboration needs. In Abu Dhabi, a growing number of companies are turning to Office 365 Hosting to leverage its advanced features, cloud-based infrastructure, and secure email services. This article explores the benefits of using Office 365 Email Hosting Abu Dhabi for businesses, highlighting how this service can help organizations operate more efficiently and effectively in today’s competitive landscape.

Overview of Office 365 Email Hosting
Office 365 is a comprehensive suite of productivity tools developed by Microsoft, designed to facilitate efficient communication and collaboration among team members. It includes applications such as Outlook, Word, Excel, and SharePoint, along with cloud-based services like OneDrive and Teams. One of the standout features of Office 365 is its robust email hosting service, which provides businesses with a secure and reliable platform for managing their email communications.
In Abu Dhabi, where businesses are rapidly embracing digital transformation, Office 365 Email Hosting has emerged as a preferred choice due to its adaptability, scalability, and enterprise-grade security. The cloud-based nature of the platform allows organizations to access their emails, files, and applications from anywhere, at any time, making it an ideal solution for today’s dynamic work environment.
1. Enhanced Security and Data Protection
One of the most significant benefits of using Office 365 Hosting Abu Dhabi is the enhanced security it offers. Businesses often deal with sensitive information and need to ensure that their data is well-protected against unauthorized access and cyber threats. Office 365 provides advanced security features such as:
Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring users to verify their identity through multiple channels before accessing their accounts.
Data Encryption: Ensures that data transmitted and stored in Office 365 is encrypted, making it difficult for cybercriminals to intercept or decipher information.
Advanced Threat Protection (ATP): Helps protect against malware, phishing attacks, and other cyber threats by scanning incoming emails and attachments.
For businesses in Abu Dhabi, where data privacy and compliance are crucial, Office 365’s security features offer peace of mind and ensure that sensitive business information remains confidential.
2. Improved Accessibility and Mobility
In today’s globalized business environment, employees need to be able to access their emails and documents while on the go. Office 365 Email Hosting Abu Dhabi enables businesses to stay connected and productive, whether employees are in the office, at home, or traveling. Key features that support accessibility and mobility include:
Cloud-Based Access: With Office 365, emails, files, and applications are stored in the cloud, allowing users to access them from any device with an internet connection.
Mobile Compatibility: Office 365 apps are optimized for smartphones and tablets, providing a seamless user experience across different devices.
Real-Time Collaboration: Multiple team members can work on the same document simultaneously, making it easier to collaborate and share ideas, regardless of their physical location.
This level of accessibility is particularly beneficial for businesses in Abu Dhabi, where remote work and international collaborations are becoming more common.
3. Scalability to Support Business Growth
Another advantage of using Office 365 Hosting Abu Dhabi is its scalability. As businesses grow and evolve, their technology needs also change. Office 365 offers flexible plans that can be customized to meet the specific requirements of businesses of all sizes. Whether a company has a few employees or hundreds, Office 365 can easily accommodate changes in the number of users or the need for additional features.
Pay-As-You-Go Model: Businesses can choose from various subscription plans based on their current needs, and easily upgrade or downgrade as required.
Add-On Services: Office 365 offers add-ons such as additional storage, enhanced security options, and advanced compliance tools that can be integrated into the existing plan as the business expands.
This flexibility ensures that businesses in Abu Dhabi can scale their Office 365 solutions in line with their growth, without having to invest in new infrastructure or change service providers.
4. Enhanced Communication and Collaboration Tools
Effective communication and collaboration are key to business success, and Office 365 Email Hosting Abu Dhabi provides a range of tools to facilitate this. Some of the notable features include:
Outlook Email and Calendar: A user-friendly interface that integrates email, calendar, and contacts in one place, making it easier to manage appointments and communications.
Microsoft Teams: A collaboration hub that enables team members to chat, hold meetings, and share files in real-time. It integrates seamlessly with other Office 365 applications.
SharePoint and OneDrive: Cloud storage solutions that allow users to store, share, and collaborate on files, ensuring that team members have access to the latest versions of documents.
By using these tools, businesses in Abu Dhabi can enhance internal communication, reduce response times, and improve project management, ultimately boosting productivity.
5. Cost Efficiency and Predictable Expenses
For many businesses, managing IT costs can be a challenge. Traditional email hosting solutions often require significant upfront investments in hardware, software licenses, and maintenance. In contrast, Office 365 Hosting Abu Dhabi offers a cost-effective solution with predictable monthly or annual fees.
No Need for On-Premises Infrastructure: With Office 365, businesses can eliminate the costs associated with maintaining physical servers and reduce IT overhead.
Subscription-Based Pricing: Businesses only pay for the services they use, which allows for better budget management and financial planning.
Automatic Updates: Microsoft regularly updates Office 365 applications and security features, eliminating the need for businesses to invest in software upgrades.
For businesses in Abu Dhabi looking to optimize their IT spending, Office 365’s cost efficiency makes it an attractive option.
6. Simplified IT Management
Managing an in-house email server can be time-consuming and requires specialized technical expertise. By opting for Office 365 Email Hosting Abu Dhabi, businesses can simplify their IT management and reduce the burden on their IT teams.
Centralized Admin Console: Office 365 provides a centralized admin console that allows IT administrators to manage user accounts, permissions, and settings from a single dashboard.
Automation and Self-Service: Features like automated user provisioning and self-service password reset reduce the time IT teams spend on routine tasks.
24/7 Support: Microsoft offers around-the-clock support for Office 365, ensuring that businesses can resolve technical issues quickly.
This ease of management allows IT teams in Abu Dhabi to focus on more strategic initiatives that add value to the business.
7. Enhanced Compliance and Data Residency Options
Compliance is a critical consideration for businesses operating in Abu Dhabi, particularly those in regulated industries such as finance, healthcare, and government. Office 365 provides several features to help businesses meet compliance requirements:
Data Residency: Businesses can choose to store their data in specific geographic locations, ensuring compliance with local data residency regulations.
Advanced Compliance Tools: Office 365 includes tools such as eDiscovery, Data Loss Prevention (DLP), and information governance, which help businesses comply with data protection laws and manage sensitive information effectively.
Audit Logs and Reporting: Businesses can access detailed logs and reports to monitor user activities and ensure compliance with internal policies and external regulations.
For organizations in Abu Dhabi that need to adhere to strict compliance standards, these features provide added assurance that their data is handled in accordance with the law.
8. Seamless Integration with Existing Systems
Office 365 Hosting Abu Dhabi integrates seamlessly with a wide range of third-party applications and existing systems, making it easy for businesses to adopt the platform without disrupting their current workflows. Whether it’s integrating with CRM systems, accounting software, or industry-specific applications, Office 365’s compatibility ensures a smooth transition and ongoing efficiency.
9. Business Continuity and Disaster Recovery
In today’s fast-paced business environment, ensuring business continuity is paramount. Office 365’s cloud-based infrastructure provides built-in disaster recovery capabilities, ensuring that businesses in Abu Dhabi can continue operating even in the event of a system failure or data loss.
Data Backup and Restore: Office 365 offers automated data backups and the ability to restore emails and files quickly, minimizing downtime and data loss.
Geo-Redundant Data Centers: Data is stored in multiple geographically dispersed data centers, providing redundancy and protection against data center failures.
99.9% Uptime Guarantee: Microsoft offers a financially-backed 99.9% uptime guarantee, ensuring that businesses have access to their emails and applications when they need them.
Conclusion
Office 365 Email Hosting Abu Dhabi provides businesses with a powerful and flexible platform for managing their email communications and collaboration needs. With benefits such as enhanced security, scalability, cost efficiency, and seamless integration, Office 365 has become an essential tool for businesses looking to thrive in the competitive market of Abu Dhabi. By adopting Office 365, businesses can streamline their operations, support remote work, and ensure that they are well-prepared for future growth and challenges. Whether you are a small business or a large enterprise, Office 365’s comprehensive features and cloud-based infrastructure make it an ideal choice for companies in Abu Dhabi seeking a reliable and robust email hosting solution.
0 notes
Text
Virtual Debit Card Buy By Bitcoin

An Instant Fund Transfer Virtual Card (IFTVC) is a digital payment method that allows for the immediate transfer of funds using a virtual card. These cards are typically used for online transactions, providing a secure and convenient alternative to physical cards or bank transfers. Here's a general overview of how they work and their benefits:Add Fund Wallet Instant
Key Features
Instantaneous Transfer: Funds are transferred immediately, making it ideal for urgent payments.
Virtual Nature: No physical card is issued, reducing the risk of loss or theft.
Security: Often equipped with advanced security features, such as tokenization and encryption, to protect against fraud.
Ease of Use: Can be used for online purchases, bill payments, and more without the need for a traditional bank account.
Customizable Limits: Spending limits can often be set by the user, providing greater control over expenditures.
Benefits
Convenience: Quick setup and usage for immediate needs.
Global Acceptance: Accepted by most online merchants worldwide.
Enhanced Security: Reduced risk of card fraud since there is no physical card to steal.
Budget Control: Users can limit spending and monitor transactions easily.
Use Cases
Online Shopping: Secure payments for goods and services online.
Subscription Services: Easily manage and pay for recurring subscriptions.
Emergency Funds: Quick access to funds in emergency situations.
Travel: Ideal for international travel as it can be used globally without the risk of losing a physical card.
Worldwide Bill Payment
How to Obtain and Use an IFTVC
Sign Up: Register with a provider that offers IFTVC services, such as a bank, fintech company, or online payment service.
Verification: Complete any necessary identity verification processes.
Load Funds: Transfer funds to the virtual card account from a bank account, credit card, or other funding source.
Use: Use the virtual card details (card number, expiration date, CVV) to make online payments.
Security Considerations
Two-Factor Authentication (2FA): Enhances security by requiring a second form of verification.
Monitoring: Regularly monitor transactions to detect any unauthorized activity.
Tokenization: Replaces sensitive card details with a unique identifier or token for each transaction.
Secure Account Transaction
Examples of Providers
PayPal: Offers virtual cards linked to PayPal accounts.
Skrill: Provides virtual prepaid cards for online transactions.
Revolut: Offers disposable virtual cards for enhanced security.
Netspend: Provides virtual card options for immediate fund access.
Would you like more detailed information on a specific aspect or provider?
Bill Pay Globally Instant Card Issue Onetime Card Buy No Transaction fess Online Balance Check Reload Fund Anytime Add Fund Wallet Instant Worldwide Bill Payment Secure Account Transaction
#virtual mastercard with cryptocurrency#create virtual with bitcoin#visa reloadable card buy with coinbase#virtual card buy with cryptocurrency#visa card buy with cryptocurrency#visa reloadable card buy with cryptocurrency#online visa reloadable card buy with cryptocurrency#online visa card buy with cryptocurrency#reloadable visa card with cryptocurrency#reloadable mastercard with cryptocurrency#generate visa reloadable card with bitcoin
0 notes
Text
Multi-factor Authentication Market Outlook, Research, Trends and Forecast to 2030
Multi-factor Authentication Industry Overview
The global multi-factor authentication market size was valued at USD 14.28 billion in 2022 and is expected to grow at a compound annual growth rate CAGR of 14.2% from 2023 to 2030.
Multi-factor authentication (MFA) introduces additional layers of security to authenticate the user identity and secure transactions over the Internet. One of the key trends escalating market growth is the mounting cases of cyberattacks and data breaches across organizations. It coupled with increasing stringency in regulations to protect sensitive data, it is expected to bolster the growth of the MFA market.
Rising investments in cloud technologies, enterprise mobility, and increasing adoption of BYOD across enterprises are anticipated to boost the adoption of multi-factor authentication solutions further. The advent of authentication-as-a-service solutions, which offer advanced security and authentication to organizations, is also projected to bolster the market's growth.
Gather more insights about the market drivers, restrains and growth of the Multi-factor Authentication Market
Companies such as CA Technologies, Vasco Data Security International, Inc., RSA Security LLC, and Symantec Corporation are making significant R&D investments to develop new authentication products, solutions, and services.
Cost and implementation complexities will restrain the market; however, their impact will decrease with time. With the rise in data and security breaches, most industries have launched data security standards. To address security breaches and cyber-attacks, enterprises have adopted MFA solutions. These solution implementations are complex and, at the same time, require more capital investment for procurement, implementation, maintenance, and management. Heterogeneous IT environments across industries further increase the complexity.
The overall investment for implementing MFA is estimated to be high due to increased support services, training, SMS gateway, and hardware and software tokens. The requirement of additional drivers for physical authenticators and interoperability with varying IT environments increase the complexity of deployment. Hence, issues pertaining to the procurement cost and implementation complexity are poised to limit the widespread adoption of multi-factor authentication solutions.
Browse through Grand View Research's Next Generation Technologies Industry Research Reports.
The global cross-border e-commerce logistics market size was estimated at USD 97.85 billion in 2023 and is projected to grow at a CAGR of 25.4% from 2024 to 2030.
The global application integration market size was valued at USD 15.90 billion in 2023 and is projected to grow at a CAGR of 19.8% from 2024 to 2030.
Key Companies & Market Share Insights
The key players in the industry are focusing on organic and inorganic growth strategies to maintain their market position. The industry players are undertaking strategies such as product launches, acquisitions, and collaborations to increase their global reach. For instance, in February 2023, Microsoft introduced a “Number Matching” feature in its Authenticator app to enhance security, particularly against MFA fatigue attacks. These attacks involve social engineering techniques employed by hackers to gain unauthorized access to an individual’s account. From May 2023 onwards, the company enabled this new feature for Microsoft Azure.
Key Multi-factor Authentication Companies:
Vasco Data Security International, Inc.
RSA Security LLC
Fujitsu America, Inc.
NEC Corporation
Symantec Corporation
Thales
3M
aPersona, Inc.
CA Technologies.
Safran S.A
Recent Developments
In April 2023, Thales, a leading global technology and security solutions provider, unveiled the SafeNet Token Fusion series. This innovative collection of USB tokens combines Fast IDentity Online 2.0 (FIDO2) with PKI/CBA, creating a single authenticator. The primary objective of Thales's new tokens was to safeguard Microsoft Azure Active Directory (Azure AD) users by mitigating the risk of account compromise by delivering enhanced security for accessing cloud and web applications.
In April 2022, Trust Stamp unveiled a Biometric Multi-Factor Authentication (Biometric MFA) solution. This innovative system revolutionizes identity verification by automating a strong level of assurance through a simple selfie. By leveraging biometric technology, the Biometric MFA adds two additional layers of authentication to verify the user's liveliness and secure tokenizing data from the selfie.
In March 2022, MIRACL, a cybersecurity software firm and Aware Inc., an authentication company, announced a strategic partnership to continue their cloud-based biometric authentication technology. The collaboration aims to address common challenges in business authentication by leveraging MIRACL's single-step, secure multi-factor authentication technology and Aware's recognized expertise in biometrics.
In May 2021, Microsoft announced the launch of new products, guidance, and employee plans to enhance security and provide enhanced customer support. Additionally, Microsoft revealed its commitment to adopting a zero-trust approach, ensuring that its employees embrace this security framework.
In April 2021, HID Global made its WorkforceID Authentication solution available to the public, offering enterprises a cloud-based platform for issuing, managing, and utilizing digital identity credentials for physical and logical access control. This solution enables organizations to streamline and enhance the security of user logins across all applications within their enterprise environment.
In July 2020, Ping Identity announced a collaboration with One Identity, a leading provider of security solutions centered around identity. This partnership aimed to deliver comprehensive identity management strategies and enhance access security and control. Both companies offered a powerful solution that covers consumers' end-to-end identity management needs by combining the capabilities of Ping Identity's access management technology with One Identity's Identity Governance and Administration (IGA) technology.
Order a free sample PDF of the Multi-factor Authentication Market Intelligence Study, published by Grand View Research.
0 notes
Text
The global demand for Wearable Medical Devices was valued at USD 27.1 Billion in 2022 and is expected to reach USD 125.64 Billion in 2030, growing at a CAGR of 24.50% between 2023 and 2030.The wearable medical devices market has seen a significant surge in recent years, driven by advances in technology, rising health awareness, and the increasing prevalence of chronic diseases. These devices, which include smartwatches, fitness trackers, biosensors, and other wearable gadgets, are designed to monitor various health parameters in real time. They have transformed healthcare by enabling continuous monitoring and personalized medicine, making healthcare more accessible and efficient.
Browse the full report at https://www.credenceresearch.com/report/wearable-medical-devices-market
Market Overview
The global wearable medical devices market is expected to continue its rapid growth trajectory, with estimates suggesting it could reach a value of over $30 billion by 2025. This growth is driven by several factors, including the increasing adoption of wearable technology, the rising prevalence of lifestyle-related diseases, and the growing geriatric population. Additionally, the COVID-19 pandemic has accelerated the adoption of wearable medical devices, as they offer a non-invasive way to monitor vital signs and manage health conditions remotely.
Key Drivers
1. Technological Advancements: The development of sophisticated sensors, improved battery life, and better connectivity options, such as 5G and IoT, have made wearable devices more reliable and user-friendly. These technological advancements have enabled the continuous monitoring of vital signs like heart rate, blood pressure, glucose levels, and oxygen saturation, making these devices indispensable tools for managing chronic conditions like diabetes, cardiovascular diseases, and respiratory disorders.
2. Rising Health Awareness: Consumers are becoming more health-conscious, leading to an increased demand for devices that can help them monitor and improve their health. Wearable devices that track physical activity, sleep patterns, and other health metrics have become popular among fitness enthusiasts and individuals looking to lead healthier lifestyles. Moreover, the integration of these devices with smartphones and health apps has made it easier for users to track their progress and make informed decisions about their health.
3. Aging Population: The growing elderly population is another key driver of the wearable medical devices market. As people age, they are more likely to suffer from chronic conditions that require constant monitoring. Wearable devices provide a convenient and non-invasive way to keep track of vital signs, enabling early detection of potential health issues and reducing the need for frequent hospital visits.
4. Remote Patient Monitoring: The shift towards remote healthcare, accelerated by the COVID-19 pandemic, has highlighted the importance of wearable medical devices in managing patients' health from a distance. These devices enable healthcare providers to monitor patients in real time, ensuring timely intervention when needed. This has been particularly beneficial for patients with chronic conditions who require continuous monitoring.
Challenges and Barriers
Despite the promising growth, the wearable medical devices market faces several challenges that could hinder its expansion:
1. Data Privacy and Security: As wearable devices collect vast amounts of personal health data, ensuring the privacy and security of this information is a significant concern. Data breaches and unauthorized access to sensitive health information can lead to serious consequences, including identity theft and compromised patient safety. Manufacturers must prioritize data security and comply with regulations like the GDPR and HIPAA to protect users' information.
2. Regulatory Hurdles: Wearable medical devices must meet stringent regulatory requirements before they can be marketed and used by consumers. Obtaining approvals from regulatory bodies such as the FDA and CE can be time-consuming and expensive. Additionally, the regulatory landscape is constantly evolving, requiring manufacturers to stay updated on the latest guidelines and standards.
3. High Costs: The cost of wearable medical devices can be a barrier to widespread adoption, particularly in developing countries. While prices have come down in recent years, high-end devices with advanced features remain expensive, limiting their accessibility to a broader population.
4. Accuracy and Reliability: The accuracy and reliability of wearable medical devices are crucial for their effectiveness. Inaccurate readings can lead to misdiagnosis and inappropriate treatment, undermining the trust in these devices. Continuous research and development are needed to improve the precision and reliability of wearable technology.
Future Outlook
The future of the wearable medical devices market looks promising, with continued innovation expected to drive further growth. Emerging technologies like artificial intelligence (AI) and machine learning (ML) are likely to play a significant role in enhancing the capabilities of these devices, enabling more accurate predictions and personalized healthcare. Additionally, the integration of wearable devices with telemedicine platforms will further expand their applications in remote patient monitoring.
As the market evolves, addressing the challenges related to data privacy, regulatory compliance, cost, and accuracy will be critical to ensuring the widespread adoption and success of wearable medical devices. With the right strategies in place, these devices have the potential to revolutionize healthcare, making it more personalized, accessible, and efficient for patients worldwide.
Key Players
BD (New Jersey, United States)
Ypsomed (Burgdorf, Switzerland)
Fitbit, Inc. (San Francisco, United States)
Apple Inc. (Cupertino, United States)
Sonova (Stäfa, Switzerland)
NeuroMetrix, Inc. (Waltham, United States)
SAMSUNG (Suwon-si, South Korea)
Omron Healthcare, Inc. (Kyoto, Japan)
AiQ Smart Clothing (Taipei, Taiwan)
Koninklijke Philips N.V. (Amsterdam, Netherlands)
Other Prominent Players
Segmentation
By Product
Diagnostic & Patient Monitoring Wearable Medical Devices
Activity Monitors/ Trackers
Smartwatches
Smart-clothing
Others
Therapeutic Wearable Medical Devices
Wearable Defibrillators
Drug Delivery Devices (Injectors, Patches)
Pain Management Devices (TENS, EMS)
Hearing Aids
Others
By Application
Remote Patient Monitoring & Home Healthcare
Sports and Fitness
By Distribution Channel
Retail Pharmacies
Online Distribution
Hypermarkets
By Region
North America
U.S
Canada
Mexico
Europe
Germany
France
U.K.
Italy
Spain
Rest of Europe
Asia Pacific
China
Japan
India
South Korea
South-east Asia
Rest of Asia Pacific
Latin America
Brazil
Argentina
Rest of Latin America
Middle East & Africa
GCC Countries
South Africa
Rest of the Middle East and Africa
Browse the full report at https://www.credenceresearch.com/report/wearable-medical-devices-market
About Us:
Credence Research is committed to employee well-being and productivity. Following the COVID-19 pandemic, we have implemented a permanent work-from-home policy for all employees.
Contact:
Credence Research
Please contact us at +91 6232 49 3207
Email: [email protected]
Website: www.credenceresearch.com
0 notes
Text
Advantages of Using ProBooks Billing Software for Your Business
Streamline Your Billing Process: Advantages of Using ProBooks Billing Software for Your Business
In today's fast-paced business environment, efficient billing processes are crucial for maintaining cash flow and customer satisfaction. ProBooks, a leading billing software provider, offers a comprehensive solution designed to streamline your invoicing and payment operations. By automating repetitive tasks such as invoice generation and payment reminders, ProBooks allows businesses to save valuable time and reduce manual errors. This not only improves accuracy but also ensures that your billing processes are compliant with tax regulations, thereby reducing the risk of costly mistakes.
As a top billing software company, ProBooks places a strong emphasis on security and user accessibility. With features like data encryption and secure access controls, ProBooks ensures that sensitive financial information is protected against unauthorized access. Additionally, regular data backups provide peace of mind, knowing that your critical information is safe from unexpected data loss. The intuitive interface and customizable features make ProBooks an ideal choice for businesses of all sizes, helping them manage their billing operations more effectively and focus on growth.
8 Advantages of Using the ProBooks Billing Software for Your Business
In the dynamic world of business, efficient billing processes are essential for maintaining cash flow and customer satisfaction. ProBooks, a leading billing software provider, offers a comprehensive solution designed to streamline your invoicing and payment operations. Here are five key advantages of using ProBooks billing software for your business:
1. Generate Invoice Within Minutes: ProBooks, a renowned billing software company, enables businesses to create invoices quickly and efficiently. With its user-friendly interface, you can generate professional invoices in just a few clicks. The software allows you to customize invoice templates to reflect your brand identity, ensuring that each invoice sent to clients reinforces your brand's image. This capability not only saves time but also enhances the professionalism of your business communications.
2. Faster Billing, Instant Payments: Speed is crucial in today's business environment, and ProBooks excels in this area. By automating the billing process, ProBooks reduces the time it takes to send invoices and receive payments. Clients can make payments instantly through various integrated payment gateways, improving your cash flow and reducing the waiting time for payments. This feature is particularly beneficial for small and medium-sized enterprises that rely on timely payments to maintain their operations.
3. Easily Manage Your Business Operations: ProBooks is not just a billing software; it's a comprehensive tool for managing various aspects of your business operations. From tracking expenses and managing inventory to monitoring financial reports, ProBooks provides an all-in-one solution that simplifies business management. The software's intuitive dashboard gives you a clear overview of your business performance, helping you make informed decisions and optimize your operations.
4. Unlimited Cloud Storage: As a top billing software provider, ProBooks offers unlimited cloud storage, ensuring that all your billing data is securely stored and easily accessible. This eliminates the need for physical storage and reduces the risk of data loss due to hardware failures. With cloud storage, you can access your billing information from anywhere at any time, providing flexibility and peace of mind. Whether you are in the office, at home, or on the go, ProBooks ensures that your data is always at your fingertips.
5. Enhanced Security: Security is a top priority for any business dealing with sensitive financial information. ProBooks incorporates advanced security features such as data encryption and secure access controls to protect your data from unauthorized access. Regular backups ensure that your information is safe from unexpected data loss, while multi-factor authentication adds an extra layer of security. As a leading billing software company, ProBooks is committed to safeguarding your business data and ensuring compliance with industry standards.
6. Multi-currency Feature: In today's global market, dealing with multiple currencies is a common challenge for businesses. ProBooks addresses this with its multi-currency feature, allowing you to create invoices and accept payments in various currencies. This functionality is especially beneficial for businesses with international clients, as it simplifies the billing process and reduces the complexity of currency conversions. By using ProBooks, you can expand your business globally without worrying about currency-related issues.
7. Accessible from Anywhere: ProBooks understands the need for mobility in modern business operations. The software is accessible from any device with an internet connection, allowing you to manage your billing processes from anywhere in the world. Whether you are traveling for business, working from home, or at a client's location, ProBooks ensures that you have full access to your billing system. This level of accessibility enhances productivity and allows for seamless business operations regardless of your location.
8. Fewer Errors and Quick Audits: Manual billing processes are prone to errors, which can lead to financial discrepancies and compliance issues. ProBooks minimizes these risks by automating the billing process and ensuring accurate data entry. The software also simplifies audits by providing detailed and organized financial records. With ProBooks, you can quickly identify and rectify any discrepancies, making audits faster and more efficient. This reduces the stress associated with financial audits and ensures that your business remains compliant with regulations.
In conclusion, ProBooks billing software offers a range of features designed to streamline your billing processes, enhance security, and improve overall business efficiency. As a leading billing software provider, ProBooks is committed to helping businesses manage their operations more effectively and achieve their financial goals.
FAQ: Understanding Billing Software and Its Benefits
1. What are the advantages of a billing system?
A billing system offers several advantages, including:
Time Efficiency: Automates invoice creation and payment reminders, saving time.
Accuracy: Reduces human errors in calculations and data entry.
Professionalism: Customizable templates for professional-looking invoices.
Security: Ensures data security with encryption and secure access.
Accessibility: Cloud-based storage allows access from anywhere at any time.
2. How does billing software help?
Billing software helps by:
Automating Invoicing: Quickly generating and sending invoices.
Streamlining Payments: Integrating payment gateways for faster transactions.
Managing Financial Data: Tracking expenses, managing inventory, and generating reports.
Enhancing Security: Protecting sensitive data with advanced security features.
Reducing Errors: Minimizing manual entry errors and simplifying audits.
3. Who is the best billing software provider?
While there are many billing software providers in the market, ProBooks is highly regarded for its comprehensive features, user-friendly interface, and robust security measures. It stands out for its efficiency, flexibility, and excellent customer support.
4. What is the importance of billing services?
Billing services are crucial for:
Cash Flow Management: Ensuring timely invoicing and payments.
Professionalism: Presenting a professional image to clients with well-designed invoices.
Efficiency: Reducing the time spent on manual billing tasks.
Compliance: Ensuring accurate tax calculations and adherence to financial regulations.
Data Security: Protecting financial information from unauthorized access and data loss.
5. What is the best software for billing?
The best software for billing depends on your business needs, but ProBooks is highly recommended for its:
Ease of Use: Intuitive interface that simplifies billing processes.
Feature Richness: Comprehensive tools for invoicing, payments, expense tracking, and reporting.
Security: Advanced security features to protect sensitive data.
Scalability: Suitable for businesses of all sizes, from small enterprises to large corporations.
Accessibility: Cloud-based access from anywhere, anytime.
#inventory management#billing software#accounting software#gst accounting software for retail#crm software#accounting#crm#business
0 notes