#Physical Identity and Access Management forecast
Explore tagged Tumblr posts
Text
#Physical Identity and Access Management market#Physical Identity and Access Management market size#Physical Identity and Access Management share#Physical Identity and Access Management trends#Physical Identity and Access Management analysis#Physical Identity and Access Management forecast#Physical Identity and Access Management outlook#Physical Identity and Access Management overview
0 notes
Note
1, 3, 6, 10, 13, 15, 16, 17 for Eoland, Berrie, Aria, and anyone else (tech asks)
1. Describe their phone case
Eoland: goes caseless because she's a monster
Berrie:

Aria:

Vice:

3. Do they use nicknames for their contacts or do they list contacts by full name?
Eoland: full name
Berrie: nickname
Aria: initials and a number if you've got the same initials as someone else
H Wells: full name and where she knows you from
6. Write out a text exchange between them and another OC
(I feel like this would be better presented in a fake screenshot than just text so I'll reblog this with that added soon lol)
10. Describe a photo they have saved on their phone
Eoland: a picture taken through Barbara Allen's bedroom window
Berrie: twelve identical selfies of him and his chess club teammates making silly faces while they were bored waiting for a match to start
Aria: a professionally taken "candid" photo of her to post to her personal social media account
H Wells: an old photo of her wife and daughter playing from when their daughter was still a small child
13. What do they use as an avatar or profile photo on social media sites?
Eoland: doesn't have social media for herself so if she was going to use anything it would probably be someone else's photo
Berrie: whatever new favorite selfie they've taken recently
Aria: a professional headshot
Vice: a photo of their band
14. You’ve just stumbled across their tumblr blog! Describe it
Eoland: kpop fancam type videos but of The Flash
Berrie: reblogs a little bit of everything and occasionally posts funny videos they filmed with her friends or the drawings he's been working on
Aria: it's a business tumblr that she's never even seen, her social media manager tries to be relatable and funny on it and fails horribly
Vice: just pure shitposts and the occasional song from his band
16. Let’s look at their search history. What are the last 5 things they searched?
Eoland: The Flash, Barbara Allen, [REDACTED]
Berrie: FIFA Women's World Cup, am I a lesbian quiz, am I a girl quiz, am I a boy quiz, how does gender work
Aria: local forecast, Moroccan food delivery, Lunaria Saeiqa net worth, local real estate listings, stock market
H Wells: accessibility remodeling, home physical therapy, NSF funding, contractor estimates
17. What’s the last thing they searched in an incognito tab 👀 (doesn’t need to be NSFW!)
Eoland: does not use the incognito tab because she has neither shame nor fear
Berrie: Barry Allen
Aria: does not use the incognito tab because she does not trust it to actually hide anything from anyone
Vice: VX neurotoxin
3 notes
·
View notes
Text
Why Choose a Local Stocktaking Service in Brisbane?
Introduction
In the bustling advertisement panorama of Brisbane, organizations of all sizes face the integral process of managing their stock effectively. A properly-organized stock inventory no longer most effective facilitates in protecting operational efficiency yet additionally performs a amazing function in financial health. This is in which knowledgeable stocktaking prone come into play. But why may want to you favor a neighborhood stocktaking carrier in Brisbane? In this accomplished article, we are able to explore the myriad merits of enticing local stocktaking authorities, dive into what makes them stand out, and grant insights into how they may optimize your stock administration.
What is Stocktaking? Understanding Stocktaking
Stocktaking refers to the course of of counting and verifying the actual stock handy. It entails assessing amounts, comparing situations, and ensuring that the archives align with what's truely reward. This perform is an important for businesses to continue accuracy in their financial statements.
Importance of Accurate Stocktaking
Accurate stocktaking is helping in picking discrepancies among recorded and physical stock stages. This not purely aids in preventing losses because of theft or mismanagement however also allows improved forecasting, paying for selections, and customer satisfaction.
youtube


Why Choose a Local Stocktaking Service in Brisbane? The Advantages of Local Expertise
When you opt for a nearby stocktaking service in Brisbane, you get advantages from specialists who have in mind the neighborhood industry dynamics appropriately. They are widely used with regional suppliers, patron choices, and the exact demanding situations that agencies face inside this brilliant city.
Accessibility and Responsiveness
Local companies normally present greater quick improve. When you desire guidance or have questions referring to your stocktake, being nearby potential sooner responses in comparison to remote suppliers.
https://storage.googleapis.com/stocktaking_brisbane_gstack-gbpmap/Stocktaking%20Brisbane%20HTML/Stocktaking-Brisbane.html Key Features of Reliable Stocktaking Services in Brisbane Comprehensive Inventory Analysis
Best Stocktaking Brisbane products and services present specified prognosis experiences that deliver insights into a number facets like turnover quotes, deadstock identity, and seasonal demand fluctuations.
Inventory Turnover Rate
Understanding your stock turnover rate facilitates establish how fast your merchandise sell inside a specific interval. High turnover exhibits wonderful revenue approaches whereas low turnover would sign overstock issues.
Technologically Advanced Solutions
Many suitable Brisbane stocktaking establishments make use of complex utility strategies to verify accuracy throughout the time of the counting job. These equipment let factual-time updates and simplified reporting.
Choosing Affordable Stocktaking Services in Brisbane Budget-Friendly Options Without Compromising Quality
Finding low-budget stocktaking facilities doesn’t mean sacrificing pleasant. Many dependable prone present competitive pricing with out compromising on their point of carrier or advantage.
1 note
·
View note
Text
Audience Analytics Market Insights 2032: Growth Drivers and Industry Scope
TheAudience Analytics Market Size was valued at USD 5.40 Billion in 2023 and is expected to reach USD 15.01 Billion by 2032 and grow at a CAGR of 12.1% over the forecast period 2024-2032.
The Audience Analytics Market is rapidly transforming how organizations interpret and act on consumer behavior across digital and physical platforms. As businesses face increasing pressure to deliver personalized, real-time engagement, audience analytics has emerged as a critical tool for unlocking insights into preferences, habits, and interaction patterns.
The Audience Analytics Market spans a broad ecosystem of data-driven technologies that help brands, media houses, event organizers, and public institutions assess how individuals interact with content, campaigns, and experiences. Fueled by advancements in AI, machine learning, and computer vision, these systems are reshaping marketing strategies, customer service, product development, and even urban planning.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/5904
Market Keyplayers:
Adobe (Adobe Experience Cloud, Adobe Analytics)
Oracle Corporation (Oracle CX Analytics, Oracle Data Cloud)
IBM Corporation (IBM Watson Marketing, IBM Customer Experience Analytics)
SAS Institute Inc. (SAS Customer Intelligence 360, SAS Visual Analytics)
Google LLC (Google Analytics, Google Ads Data Hub)
Audiense (Audiense Insights, Audiense Connect)
Comscore, Inc. (Comscore Digital Audience Measurement, Comscore Campaign Ratings)
Sightcorp (DeepSight Toolkit, DeepSight Face API)
Unifi Software (Unifi Data Platform, Unifi AI-Driven Analytics)
Telmar (Audience Targeting Solutions, Telmar Planning Tools)
Quividi (Quividi Audience Measurement Platform, Quividi Data Enrichment)
AnalyticsOwl (Real-Time Web Analytics, Audience Engagement Tracker)
Akamai Technologies (Akamai Identity Cloud, Akamai DataStream)
NetBase Solutions (NetBase Quid Consumer Analytics, NetBase Social Listening)
JCDecaux Group (JCDecaux Data Solutions, VIOOH Programmatic Advertising)
Market Analysis
Audience analytics leverages a wide range of input sources—from web behavior and app usage to biometric feedback and in-store sensors—to understand demographics, sentiment, attention span, and engagement levels. The demand for deeper behavioral insights has surged across industries, with organizations seeking to measure ROI, refine messaging, and identify untapped market segments.
Adoption is being driven not only by enterprises aiming for hyper-personalized content delivery, but also by sectors like education, transportation, and public safety that benefit from crowd behavior analysis and predictive modeling.
Scope
The scope of the market includes solutions such as real-time data visualization, facial recognition analytics, audience segmentation, sentiment analysis, and attention tracking. These technologies are deployed across various touchpoints:
Retail and eCommerce: To track shopper behavior and optimize store layout or digital journeys.
Media and Entertainment: For content recommendation and performance benchmarking.
Advertising and Marketing: To evaluate campaign resonance and refine audience targeting.
Events and Venues: To monitor crowd movement, engagement levels, and safety.
Public Infrastructure: For managing traffic flow, urban mobility, and citizen engagement.
Cloud integration, mobile analytics, and edge computing continue to expand the accessibility and scalability of these platforms.
Market Forecast
The market outlook suggests consistent upward momentum, with cloud-native and hybrid platforms becoming the preferred deployment model. Organizations across the globe are shifting from siloed data collection to unified audience intelligence systems that offer holistic views of the customer journey. The evolution toward predictive and prescriptive analytics will play a defining role in the market's maturity over the coming years.
Future Prospects
Looking ahead, the rise of privacy-first architectures, coupled with AI-generated insights, will redefine how audience data is collected and utilized. The implementation of regulatory frameworks such as GDPR and CCPA has led to more ethical and consent-driven data collection practices, enhancing consumer trust and brand loyalty.
Emerging areas of growth include emotion detection, immersive media analytics (AR/VR), and voice-based engagement analysis. Integration with customer data platforms (CDPs) and marketing automation tools is set to further streamline insight-to-action workflows.
Key Trends
AI-Enhanced Insights: Predictive algorithms are replacing static dashboards with dynamic, actionable intelligence.
Omnichannel Synchronization: Unified analytics across digital, mobile, and in-person interactions deliver consistent understanding of audiences.
Edge Computing: Real-time audience monitoring at the point of interaction reduces latency and enhances accuracy.
Emotion & Sentiment Detection: Systems are evolving to capture not just what people do, but how they feel.
Privacy-Driven Design: Increased emphasis on anonymization and secure data practices is fostering greater adoption.
Context-Aware Analytics: Advanced models now factor in environmental and temporal context for more nuanced interpretation.
Access Complete Report: https://www.snsinsider.com/reports/audience-analytics-market-5904
Conclusion
The Audience Analytics Market is redefining engagement through intelligent, ethical, and real-time insight delivery. By combining technological sophistication with user-centric design, it empowers organizations to connect, adapt, and evolve in harmony with audience expectations.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Audience Analytics Market#Audience Analytics Market Growth#Audience Analytics Market Trends#Audience Analytics Market Scope
0 notes
Text
Travel eSIM Market Global Outlook and Forecast 2024-2030
Travel eSIM Market Size, Share 2025
Industry Overview:
A travel eSIM is an electronic SIM card designed for use during international travel. It allows you to connect to local mobile networks without the need for a physical SIM card.
The global Travel eSIM market has shown significant growth over the past few years, with the market valued at approximately US$ 1.32 billion in 2024. This growth is set to continue, with projections indicating that the market will reach a value of US$ 2.8 billion by 2032, reflecting a Compound Annual Growth Rate (CAGR) of 8.9% from 2024 to 2032. The expanding market is driven by several factors, including the rising demand for seamless connectivity, increasing adoption of IoT devices, and the growing number of eSIM-enabled devices.
The eSIM (Embedded Subscriber Identity Module) market is revolutionising mobile connectivity by substituting a more adaptable and digital SIM card for conventional physical SIM cards. This technology is especially helpful for travellers, IoT devices, and organisations that need multi-network connectivity because it enables users to swap carriers remotely without having to change SIM cards. The business is anticipated to grow quickly as eSIM adoption rises, propelled by smartphone manufacturers, IoT applications, and linked autos. Telecom companies, device producers, and software vendors are important participants in ensuring a safe and smooth digital experience. Although there are still issues with international standardisation and compatibility, the eSIM business has a lot of room to development.
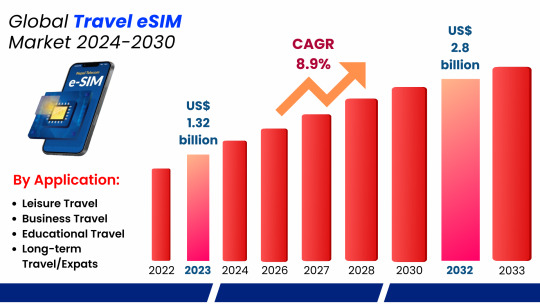
Industry Analysis by Segments
Consumer eSim to hold the highest market share: by type
In terms of type the global travel eSim industry has been segmented as Consumer eSim and Machine to Machine eSim.
The consumer eSIM category holds a dominant market share of 60-65% due to its incorporation into popular consumer devices such as wearables, tablets, and smartphones. The integration of eSIM technology into flagship products by major tech companies including as Apple, Samsung, and Google has greatly increased customer adoption.
The flexibility and ease of use that eSIMs provide have contributed significantly to this expansion. For those who travel frequently or require access to different networks, eSIMs are perfect as they enable carrier switching without the need to physically replace the card, in contrast to standard SIM cards. Users no longer need to visit a physical store to complete the activation process because they can connect to a network digitally instantaneously. To further improve the user experience, eSIMs also support dual-SIM capabilities, which enables users to manage their personal and work numbers on the same device. Demand is anticipated to be driven by the increasing number of eSIM-compatible handsets on the market as well as rising consumer knowledge of its benefits. The use of eSIM technology will probably pick up speed as 5G networks spread and consumers demand more dependable, quicker connectivity, thereby consolidating its dominance in the consumer electronics industry.
Further, the Machine-to-Machine (M2M) eSIMs hold a 35-40% share of the market. These eSIMs are critical in the growing IoT sector, where they enable devices to communicate with each other without human intervention. Their use is expanding in industries such as automotive, logistics, and smart cities.
Smart phone to hold the highest market share: by Application
With 50–55% of the market share, smartphones are the most popular application category in the eSIM industry. The increasing number of smartphones with eSIM support as a result of big manufacturers like Apple, Google, and Samsung including the technology into their most recent models is what is driving this domination. The ease that eSIMs provide—especially for travelers—is a major factor propelling this market's expansion. Since eSIMs eliminate the need to swap out traditional SIM cards, they are the perfect option for frequent travellers who need to access various networks in different areas. Customers find it more appealing when they can handle various profiles or providers on a single device rather than having to carry around multiple SIM cards.
Regional Analysis:
In terms of region the global travel eSim has been segmented as North America, Europe, Asia Pacific, Middle East and Africa and South America.
Leading the global Travel eSIM market, Europe holds a 35-40% market share. The region's advanced mobile infrastructure, high adoption of eSIM-enabled devices, and favourable regulatory environment contribute to its dominance. The travel eSIM market in Europe is quickly becoming one of the most competitive and dynamic areas in the world. Europe is a centre for the adoption of cutting-edge digital solutions like eSIMs because of its high volume of international travel, advancements in technology, and supportive regulatory environments. More and more European travellers are searching for flexible, affordable mobile connectivity options that let them stay connected without having to deal with the inconveniences of traditional SIM cards or exorbitant roaming fees. The growing consumer demand for digital-first solutions and the wide availability of eSIM-compatible products, such as wearables and smartphones, are further factors driving the need for the eSIM era.
The increasing international travel across Europe further accelerating the travel eSim market in the region, In comparison with the previous year, there were more foreign visitors arriving in Europe in 2024. In 2024, the number of inbound arrivals was approximately 708 million, which was less than in 2019. This was despite a notable annual growth.
The European Travel Commission (ETC) has published its most recent "European Tourism Trends & Prospects," which states that as of 2024, the sector is stronger than ever. Overnight stays have climbed by 7%, while the number of foreign visitors has increased by 6% from 2019.
End Use Industry Impact Analysis:
The rapid expansion of the global tour eSIM market is being driven by the rise in global tour, the development of the mobile technology, and the increasing demand for digital solutions that provide seamless connectivity.
A primary factor propelling the growth of the Asia tour eSIM market is the substantial growth of both international and intraregional travels. It is anticipated that the number of international visitor arrivals (IVAs) to Asia Pacific will rise from 619 million in 2024 to 762 million in 2026, representing a recovery rate of 111.6% in comparison to the level of 2019. By 2026, visitor arrivals in Asia are expected to reach 564.0 million, followed by those in the Americas (167.7 million) and the Pacific (30.4 million).
Saudi Arabia alone welcomed over 100 million tourists, marking a 56% increase from 2019 and a 12% rise from 2022. Furthermore more the World Travel & Tourism Council (WTTC) reported that in 2024, tourism contributed AED 220 billion to the UAE’s GDP, a figure expected to increase to AED 236 billion in 2024
According to the World Travel & Tourism Council’s (WTTC) latest Economic Impact Report (EIR), reveals the North America Travel & Tourism sector is projected to grow at an average annual rate of 3.9% over the next decade, outstripping the 2% growth rate for the regional economy and reaching an impressive $3.1 trillion in 2032.
According to the international Trade Association, International travel plays a critical role in the US economy. Prior to the COVID-19 pandemic, in 2019, international visitors spent $233.5 billion experiencing the United States; injecting nearly $640 million a day into the U.S. economy
Competitive Analysis:
Some of the key Players operating within the industry includes:
Airalo
Holafly
MAYAMOBILE
BNESIM
Dent Wirelss
Keepgo
Nomad
Sim Options
Surfroam
Airhub
TravelSim
ETravelSIM
Ubigi
Numero eSIM
Total Market By Segment:
By Type:
Consumer eSIM
M2M eSIM (Machine to Machine)
By Application:
Leisure Travel
Business Travel
Educational Travel
Short-term/Temporary Stay
Long-term Travel/Expats
By Connectivity Type:
Standalone eSIM
eSIM with Roaming
Regional eSIM
Global eSIM
By End User:
Individuals
Enterprises
Telecom Operators
Travel Agencies
By Service Offerings
Data Services
Voice Services
SMS Services
Region Covered:
North America
EuropeAsia Pacific
Middle East and Africa
South Africa
Report Coverage:
Industry Trends
SWOT Analysis
PESTEL Analysis
Porter’s Five Forces Analysis
Market Competition by Manufacturers
Production by Region
Consumption by Region
Key Companies Profiled
Marketing Channel, Distributors and Customers
Market Dynamics
Production and Supply Forecast
Consumption and Demand Forecast
Research Findings and Conclusion
Combined Plans:
There are several distinct players in the highly competitive travel eSIM market, including tech companies, eSIM providers, and mobile network carriers. Important rivals are well-known telecom giants, which use their extensive international networks and strong brand names to sell travel eSIM plans directly to customers. Specialised eSIM providers like Airalo, GigSky, and Ubigi, on the other hand, are becoming more and more popular by providing flexible data packages and multi-country plans as well as affordable, customised travel eSIM solutions that are specifically designed for travellers from outside.
Tech companies like Apple and Google also influence the competitive landscape by integrating eSIM technology into their smartphones, enabling direct access to eSIM services through their app ecosystems. This has created opportunities for third-party eSIM service providers to partner with these tech firms, enhancing their global reach.
Key industry Trends:
Integration with IoT and Connected Device:
The Internet of Things (IoT) and linked devices are integrating eSIM generation, which is greatly expanding its use cases and marketability. As the Internet of Things continues to expand, eSIMs are finding their way into a wider range of electronics than just smartphones, such as wearable’s, connected motors, and smart home appliances. There are various benefits to this integration:
Wearables: Wearables, such as fitness trackers and smart watches, can maintain independent connectivity without relying on a paired phone because of eSIMs. Customers can now benefit from instantaneous message delivery, phone calls, and mobile data access via their wearable device, enhancing functionality and user experience.
Connected Cars: eSIMs in the automotive industry enable smooth connectivity for linked automobiles, providing features like real-time navigation, remote diagnostics, and infotainment services. The incorporation of eSIMs into cars facilitates updates via the air, enhances safety features, and offers improved connectivity for telematics and navigation applications.
Smart Home products: Home automation controllers, security systems, and thermostats are examples of smart home products that are incorporating the eSIM era. Through this connection, devices can communicate with one other and with customers anywhere in the world with consistent and dependable connectivity.
The expansion of eSIM technology into these diverse applications enhances its utility and opens up new market opportunities. For device manufacturers, integrating eSIMs simplifies design and manufacturing processes by eliminating the need for physical SIM card slots, leading to more compact and robust devices. Additionally, eSIMs support global connectivity, allowing devices to operate seamlessly across different regions without the need for multiple SIM cards.
Industry Driving Factor:
Rising Demand for Flexible and Convenient Connectivity Solutions:
Due to the increasing demand for seamless communication and connectivity when on the go, consumers are placing an increasing emphasis on the flexibility and convenience of their connectivity solutions. This trend is particularly noticeable among travellers, who are searching for solutions to make staying connected in unusual locales easier. These demands are met by ESIM technology, which gives traditional SIM cards a more adaptable and user-friendly option. eSIMs, as opposed to physical SIM cards, eliminate the need for physical swaps and let users activate and manage their mobile subscriptions online. With this method, travellers will no longer need to buy and insert several SIM cards or put up with the hassle of switching SIM cards when travelling to different countries. Alternatively, they could easily switch between plans or businesses right from their device, usually through a mobile app. One further factor driving the growing demand for eSIMs is their capacity to support many profiles on a single eSIM. This feature enables users to manage private plans for personal and business use or seamlessly transition between local and international plans. This flexibility now ensures continuous connectivity and helps users avoid paying exorbitant roaming fees in addition to improving comfort. The popularity of eSIM technology is continuing to rise as more customers look for solutions that fit their busy lifestyles and travel habits. This indicates a larger trend towards more flexible, virtual, and hassle-free connectivity options.
Industry Restraining Factor:
Device compatibility is one of the major challenges facing the eSIM business. Although the eSIM technology is increasingly being included into more modern wearable, and smartphones, many older or even less advanced devices do not support eSIM functionality. Due to the fact that a significant section of the customer base still uses devices that require physical SIM cards, this issue limits the market penetration of travel eSIMs. The switch to eSIMs isn't always possible for clients with mismatched equipment, which is likely to cause annoyance and reduce the potential customer base for travel eSIM providers. The challenge of device compatibility is made more difficult by the slow rate of update or modification of older devices. The adoption of eSIM generation may be slow in many places, especially where clients are more price-sensitive or where older devices are still in widespread use. Travel eSIM providers face a challenge as a result of this delayed adoption rate because they must serve a wide range of target customers with different levels of technological proficiency.
Report Scope:
The report includes Global & Regional market status and outlook for 2017-2028. Further, the report provides break down details about each region & countries covered in the report. Identifying its sales, sales volume & revenue forecast. With detailed analysis by types, applications, Connectivity type, end use and Service Offerings. The report also covers the key players of the industry including Company Profile, Product Specifications, Production Capacity/Sales, Revenue, Price, and Gross Margin 2017-2028 & Sales with a thorough analysis of the market’s competitive landscape and detailed information on vendors and comprehensive details of factors that will challenge the growth of major market vendors.Report AttributesReport DetailsReport TitleTravel eSIM Market Global Outlook and Forecast 2024-2030Historical Year2018 to 2022 (Data from 2010 can be provided as per availability)Base Year2024Forecast Year2032Number of Pages107 PagesCustomization AvailableYes, the report can be customized as per your need.
1 note
·
View note
Text
Mobile Key vs. RFID Key Card: What’s Next for Hotels?
As technology advances, the hotel industry continues to evolve in enhancing guest experiences and operational efficiency, particularly in the evolution of hotel access methods. From traditional metal keys to magnetic stripe cards, and now the mainstream use of RFID key cards, hotels are redefining the guest check-in experience. In recent years, discussions have intensified around whether mobile keys will replace RFID key cards. This article will delve into a comparison of mobile keys and RFID key cards, analyzing their advantages and challenges while also forecasting future trends in hotel access systems.

1. Understanding RFID Key Cards
RFID key cards contain an embedded microchip that stores a unique identification code. When the key card is brought close to the RFID reader, the door lock emits a wireless signal, activating the chip within the card to transmit identity information. If the information matches, the lock automatically unlocks.
Advantages of RFID Key Cards:
High Security: The data on RFID cards is encrypted, making duplication difficult and providing significantly higher security compared to traditional keys. Durability: Unlike magnetic stripe cards, RFID cards do not require physical contact, making them less prone to wear and tear, thus offering a longer lifespan. Operational Flexibility: Hotels can quickly configure and reauthorize RFID key cards, enhancing management efficiency.
Challenges of RFID Key Cards:
Environmental Impact: The widespread use of plastic cards can burden the environment. Risk of Loss: Physical key cards may be lost by guests. However, they can be promptly reported and deactivated at the front desk.
Overall, while RFID key cards provide enhanced security and convenience, they also present some challenges, particularly concerning environmental sustainability and loss management.
2. Understanding Mobile Keys
Mobile keys are sent to guests' smartphones through the hotel’s application. Upon check-in, guests can bypass the front desk and simply use their phones to unlock their room doors. This process typically relies on NFC (Near Field Communication) or BLE (Bluetooth Low Energy) technology, ensuring both security and a smooth experience.
Advantages of Mobile Keys:
No Physical Key Card Required: Guests can use their smartphones directly, eliminating the need to carry an extra item. Seamless Integration with Hotel Services: Mobile keys can be integrated with the hotel app, offering features like room service requests and smart room controls, enhancing the guest experience. Environmentally Sustainable: Reducing the use of physical key cards helps lower plastic waste, aligning with sustainability trends.
Challenges of Mobile Keys:
Technology Compatibility Issues: Not all guests' smartphones support NFC or BLE, so hotels still need to offer backup solutions. Dependence on Battery and Connectivity: If a guest’s phone runs out of battery or experiences network issues, room access may be affected, requiring hotels to provide emergency plans. Security Risks: Digital keys can be susceptible to hacking, necessitating hotels to strengthen data encryption and identity verification protocols.
In summary, while mobile keys offer convenience and align with sustainability initiatives, potential challenges concerning technology compatibility, reliability, and security must be carefully managed to ensure a seamless guest experience.
3. Mobile Key vs. RFID Key Card: In-Depth Comparison
When comparing RFID key cards and mobile keys, several key dimensions should be considered:
Convenience:
RFID Key Cards: Although these require collection from the front desk, this traditional method has been validated over the years. It is straightforward and intuitive, and it is not impacted by smartphone battery life or technical issues.
Mobile Keys: They eliminate the step of collecting a card, allowing guests to unlock doors with their smartphones. However, they depend on mobile operation and network connectivity, which can lead to difficulties if the phone runs out of battery or the network is unstable.
Security:
RFID Key Cards: With ongoing advancements in RFID encryption technology, modern RFID cards are very secure.
Mobile Keys: While mobile keys may seem more secure at first glance, they still carry the potential risk of hacking.
Environmental Impact:
RFID Key Cards: Many RFID cards are now made from eco-friendly materials, such as wooden cards or biodegradable BioPolyTM Vinyl, reducing environmental impact.
Mobile Keys: They do not require physical cards, thus minimizing plastic pollution.
Cost:
RFID Key Cards: Although RFID cards require the production and management of physical cards, they tend to be more cost-effective in terms of long-term management and operation.
Mobile Keys: Mobile key systems involve significant initial investment and maintenance costs.
Customer Experience:
RFID Key Cards: As a reliable and widely applicable technology, RFID keys provide a convenient and contactless access method, ensuring a consistent experience for various hotels and customers.
Mobile Keys: Although mobile keys offer smarter and more personalized services, feedback from some hotel managers indicates that guests still tend to prefer using physical hotel cards.

4. Future Trends: How Should Hotels Make Their Choice?
As the hotel industry continues to focus on technological innovation, the decision between mobile keys and RFID key cards has become a challenge for many hotel decision-makers. So, how should hotels choose the most suitable access solution?
Based on feedback from hotel industry managers, RFID hotel cards remain the preferred solution for most hotels, and for good reason. They excel in security, operational stability, convenience, and smart management, perfectly meeting the actual needs of hotel guests, especially in a rapidly changing market environment.
Advantages of RFID Hotel Cards:
Security and Stability: RFID hotel cards use encryption technology, greatly enhancing security and effectively preventing risks of duplication and theft. Furthermore, RFID systems exhibit high stability, unaffected by phone battery life, network issues, or equipment malfunctions, ensuring a worry-free experience for every guest.
Convenience and Universality: RFID cards allow for quick, contactless unlocking, alleviating concerns guests may have about phone battery depletion or technical issues. Additionally, RFID hotel cards do not require any application downloads, avoiding guest concerns regarding privacy violations or complicated procedures—especially for those who are not accustomed to using smart devices.
Smart Management and Cost Efficiency: For hotel managers, the management system for RFID hotel cards is smart and efficient, streamlining the check-in process and reducing labor costs. Compared to the cost of the smart lock systems and high technical investments required for mobile keys, RFID systems lower operational expenses while offering hotels the flexibility to easily adapt to different scales of operations.
Meeting Diverse Guest Needs: Many guests are reluctant to download extra applications on their phones, viewing it as cumbersome and potentially invasive to their privacy. The prevalence of RFID hotel cards and their advantage of not requiring additional app installations make them suitable for a broad range of guests, particularly those who prefer simplicity and privacy protection.
In summary, while mobile keys are popular in certain upscale markets and among specific demographics, RFID hotel cards remain the most aligned solution for the vast majority of hotels and their guests. Their reliability, cost-effectiveness, and guest-friendly nature secure their dominant position in the hotel industry. For operators seeking a stable, efficient, convenient, and secure hotel solution, RFID hotel cards undoubtedly represent the best investment choice.
If you are choosing the right access system for your hotel, please visit our website RFIDcard.com for more expert advice and customized RFID card solutions. For over a decade, we have been dedicated to providing high-quality, reliable RFID products for hotels, helping you enhance operational efficiency and guest satisfaction.
0 notes
Text
Explain secure data sharing and use cases for cross-organization collaboration.

Secure Data Sharing and Use Cases for Cross-Organization Collaboration In today’s data-driven world, organizations frequently need to share data securely across departments, partners, vendors, and regulatory bodies.
Secure data sharing ensures that sensitive data is protected while enabling seamless collaboration, analytics, and decision-making.
🔐 What Is Secure Data Sharing?
Secure data sharing refers to controlled access to data across different organizations or business units without compromising security, privacy, or compliance.
Modern cloud platforms offer mechanisms that allow governed, permission-based sharing without physically moving or duplicating data.
Key Features of Secure Data Sharing:
✅ Access Control — Fine-grained permissions control who can access data.
✅ Encryption & Masking — Protects sensitive data in transit and at rest.
✅ Audit Logging — Tracks who accessed what data and when.
✅ Federated Identity Management —��Ensures only authorized users access shared data.
✅ Multi-Cloud & Hybrid Support — Enables secure sharing across different cloud providers. 🛠 Technologies for Secure Data Sharing Various platforms offer secure data-sharing features, including:
1️⃣ Azure Synapse Analytics & Azure Data Share Azure Data Share enables organizations to share data without duplication. Synapse Analytics allows cross-team collaboration while enforcing access policies.
2️⃣ AWS Data Exchange & Lake Formation AWS Lake Formation provides fine-grained access control for shared data lakes. AWS Data Exchange allows businesses to subscribe to third-party data securely.
3️⃣ Snowflake Secure Data Sharing Enables real-time, zero-copy data sharing across organizations without moving data. Supports row- and column-level security for precise control.
4️⃣ Google BigQuery Data Sharing Uses authorized views and datasets for multi-tenant collaboration. 📌 Use Cases for Cross-Organization Collaboration
1️⃣ Enterprise Data Sharing Across Departments
📊 Use Case: A large multinational company wants to share HR, finance, and marketing data across different departments while maintaining strict access controls.
✅ Solution: Using Snowflake Secure Data Sharing or Azure Data Share, teams can access only the data they are authorized to see, eliminating the need for redundant data copies.
2️⃣ Partner & Vendor Collaboration
🔗 Use Case: A retail company wants to share real-time sales data with suppliers for demand forecasting.
✅ Solution: AWS Lake Formation enables secure data lake sharing, allowing suppliers to access live sales trends while maintaining customer privacy through data masking.
3️⃣ Data Monetization & Marketplace Models 💰 Use Case: A financial institution wants to sell anonymized transaction data to third-party analytics firms.
✅ Solution: AWS Data Exchange or Snowflake enables governed, controlled data sharing with external consumers without exposing personal details.
4️⃣ Healthcare & Research Collaboration
🏥 Use Case: Hospitals and pharmaceutical companies collaborate on medical research while complying with HIPAA & GDPR regulations.
✅ Solution: Federated data sharing models allow hospitals to run analytics on combined datasets without sharing raw patient records.
5️⃣ Regulatory & Compliance Reporting
📜 Use Case: Banks must share financial transaction data with regulators without violating privacy laws.
✅ Solution: Secure APIs with token-based authentication provide regulators with controlled access while maintaining an audit trail.
🔐 Best Practices for Secure Data Sharing
🔹 Role-Based Access Control (RBAC): Assign access rights based on user roles.
🔹 Data Masking & Anonymization: Protect sensitive PII data before sharing.
🔹 Encryption (TLS & AES-256): Encrypt data in transit and at rest.
🔹 Federated Authentication (OAuth, SAML): Ensure secure identity verification.
🔹 Zero Trust Architecture: Implement least privilege access policies.
🚀 Conclusion
Secure data sharing is crucial for modern enterprises looking to collaborate efficiently while protecting data privacy. Technologies like Azure Data Share, Snowflake, and AWS Lake Formation enable organizations to share data securely across departments, partners, and regulators.
By following best practices and using the right platforms, businesses can unlock secure, compliant, and scalable data collaboration.

0 notes
Text
0 notes
Text
Navigating the Entrepreneurial Landscape: Tips for Aspiring Business Owners

In today’s dynamic economy, entrepreneurship is a vibrant and rewarding path for many. With the rise of technology and the increasing accessibility of resources, starting a business has never been more feasible. However, the journey is not without its challenges. Here, we explore essential tips for aspiring entrepreneurs looking to navigate the complex landscape of business ownership.
1. Find Your Passion
The foundation of any successful business is passion. Identifying what you love and are knowledgeable about is crucial. When you start a business that aligns with your interests, you’re more likely to stay motivated during tough times. Conduct self-assessments and consider your hobbies, skills, and experiences to pinpoint what you genuinely care about. This passion will fuel your determination and resilience, essential traits for any entrepreneur.
2. Conduct Thorough Market Research
Understanding your target market is vital. Market research helps you identify customer needs, preferences, and behaviors. Use surveys, focus groups, and online tools to gather insights. Analyze your competitors as well—what are they doing well? Where are their gaps? This information will help you position your business effectively, allowing you to tailor your offerings to meet the demands of your audience.
3. Create a Solid Business Plan
A well-crafted business plan serves as your roadmap. It outlines your business goals, strategies, target audience, and financial projections. This document not only guides your operations but is also crucial when seeking funding from investors or banks. Make sure to include a thorough analysis of your market, a marketing strategy, and a plan for growth. Your business plan should be dynamic; revisit and adjust it regularly as your business evolves.
4. Build a Strong Brand
Branding goes beyond a logo; it encompasses your business’s identity, values, and how you connect with customers. Establish a unique brand voice and visual identity that resonates with your target audience. Consistency is key; ensure that your branding reflects the same message across all platforms—your website, social media, and any physical materials. A strong brand fosters trust and loyalty, setting you apart in a crowded market.
5. Embrace Technology
In the digital age, leveraging technology is essential for business success. From e-commerce platforms to social media marketing, various tools can streamline operations and enhance customer engagement. Consider adopting project management software to improve team collaboration or utilizing data analytics to understand customer behavior better. Staying updated on technological trends can provide a competitive edge, making your business more efficient and innovative.
6. Focus on Financial Management
Sound financial management is the backbone of any successful business. Track your expenses, revenue, and cash flow meticulously. Use accounting software to simplify this process, and consider hiring a financial advisor if your budget allows. Understand the importance of budgeting and forecasting; having a clear picture of your financial health will enable you to make informed decisions and plan for the future.
7. Build a Network
Networking is a crucial element of entrepreneurship. Surround yourself with other business owners, mentors, and industry professionals. Attend networking events, join local business associations, and engage on social media platforms like LinkedIn. Building relationships can lead to partnerships, collaborations, and valuable advice that can significantly impact your business. Remember, collaboration can often be more powerful than competition.
8. Be Adaptable
The business landscape is constantly changing, and adaptability is vital for long-term success. Be open to feedback and willing to pivot your strategies when necessary. Monitor industry trends and customer preferences to stay relevant. Remember, many successful businesses have thrived by innovating and evolving in response to market demands.
9. Prioritize Customer Experience
Your customers are the heart of your business. Providing an exceptional customer experience can differentiate you from competitors. Listen to your customers and engage with them through surveys, social media, and direct communication. Make it easy for them to provide feedback, and be responsive to their needs. Happy customers are more likely to become repeat buyers and refer others to your business.
10. Stay Persistent
Lastly, persistence is key in entrepreneurship. The journey is fraught with challenges, and setbacks are inevitable. Embrace failures as learning opportunities, and maintain a growth mindset. Celebrate your successes, no matter how small, and keep pushing forward. The road may be long, but with determination and hard work, your entrepreneurial dreams can become a reality.
Conclusion
Embarking on an entrepreneurial journey is both exhilarating and daunting. By finding your passion, conducting thorough research, creating a solid plan, and remaining adaptable, you can navigate the complexities of business ownership successfully. With persistence and a commitment to customer satisfaction, you’ll be well on your way to building a thriving enterprise. Remember, every great business starts with a single step—take yours today!
1 note
·
View note
Text
0 notes
Text
Contactless Biometrics Technology Market is Estimated to Witness High Growth Owing to Advancement in Contactless

The contactless biometrics technology market plays a pivotal role in providing ease and convenience for the identification and authentication of individuals using their physiological or behavioral attributes without contact. Contactless biometrics solutions offer advantages such as hygiene, faster processing, and increased security and privacy when compared to contact-based biometric systems. The conventional Contactless Biometrics Technology Market Size for seamless and secured access to physical as well as logical premises is driving the adoption of contactless biometrics technology across sectors such as government, BFSI, healthcare, travel & immigration, and consumer electronics among others.
The Global contactless biometrics market is estimated to be valued at US$ 15.03 Bn in 2024 and is expected to exhibit a CAGR of 15.% over the forecast period 2024 to 2031. Key Takeaways
Key players operating in the contactless biometrics market are Aware, Inc., Fingerprint Cards AB, Fujitsu Limited, HID Global Corporation, IDEMIA Group, M2SYS Technology, NEC Corporation, NVIAsoft Corporation, SITA.
The key opportunities in the contactless biometrics market include rising deployment across airports for passenger processing and mobile payments. Contactless biometrics solutions are also finding increasing usage in smart cities applications for surveillance and access control.
Advancements in contactless authentication solutions such as iris, palm vein, and Contactless Biometrics Technology Market Size And Trends are also expected to drive revenues for vendors. Ongoing R&D towards developing multi-modal biometric systems for identification at distances are further enhancing the capabilities of contactless biometrics technology.
Market Drivers
Stringent regulations for border security and emphasis on modernization of immigration processes are majorly driving the deployments of contactless biometrics technology at airports and ports. The rising popularity of biometric-secured payment cards and mobile wallets is also propelling the demand for contactless biometrics. Significant investments by governments and private organizations to implementsmart identity management systems using biometrics is further augmenting the market growth.
Current challenges in Contactless Biometrics Technology Market:
The contactless biometrics technology market still faces multiple challenges. While the technology promises convenience, many users continue to have privacy and security concerns over how their biometric data is collected, stored and used. There are also technical limitations around accuracy rates, especially for technologies like iris and facial recognition where external factors can impact recognition. Maintaining high performance rates across diverse demographic populations is another key challenge. Regulatory standards around biometric data usage and privacy also vary globally which impacts technology adoption. Widespread deployment will require addressing these core challenges around security, privacy, accuracy and regulatory compliance.
SWOT Analysis
Strength: Provides a convenient and hands-free authentication experience. Eliminates the need for physical contact with biometric devices. Weakness: Accuracy rates can vary based on external conditions. Biometric templates raise privacy and security concerns if data is compromised. Opportunity: Growing demand for touchless authentication due to COVID is driving increased investment. Expanding use cases across access control, payments and government ID programs. Threats: Stricter privacy laws could limit viable business models. Algorithm bias remains a risk for some populations. Alternative authentication methods continue to emerge.
The North American region currently accounts for the largest share of the contactless biometrics technology market in terms of value. This is primarily due to robust technology investments and rapid adoption of biometrics across various government and commercial applications in countries like the US and Canada. The Asia Pacific region is projected to witness the fastest growth during the forecast period driven by the emerging economies of India, China and other ASEAN nations actively deploying biometrics for national ID programs, banking and border security.
Europe is another major regional market supported by the European Union's initiative to deploy digital ID solutions based on biometrics such as facial recognition across member states. As contactless biometric technologies play a vital role in digital transformation ambitions, leading economies across all geographic regions are expected to increasingly invest in touchless biometrics going forward. Get More Insights On, Contactless Biometrics Technology Market For More Insights Discover the Report In language that Resonates with you French, German, Italian, Russian, Japanese, Chinese, Korean, Portuguese About Author: Ravina Pandya, Content Writer, has a strong foothold in the market research industry. She specializes in writing well-researched articles from different industries, including food and beverages, information and technology, healthcare, chemical and materials, etc. (https://www.linkedin.com/in/ravina-pandya-1a3984191)
#Contactless Biometrics Technology Market Size#Contactless Biometrics Technology Market Demand#Contactless Biometrics Technology Market Trends#Contactless Biometrics#Biometrics Technology#Contactless Biometrics Technology Market
0 notes
Text
Multi-factor Authentication Market Outlook, Research, Trends and Forecast to 2030
Multi-factor Authentication Industry Overview
The global multi-factor authentication market size was valued at USD 14.28 billion in 2022 and is expected to grow at a compound annual growth rate CAGR of 14.2% from 2023 to 2030.
Multi-factor authentication (MFA) introduces additional layers of security to authenticate the user identity and secure transactions over the Internet. One of the key trends escalating market growth is the mounting cases of cyberattacks and data breaches across organizations. It coupled with increasing stringency in regulations to protect sensitive data, it is expected to bolster the growth of the MFA market.
Rising investments in cloud technologies, enterprise mobility, and increasing adoption of BYOD across enterprises are anticipated to boost the adoption of multi-factor authentication solutions further. The advent of authentication-as-a-service solutions, which offer advanced security and authentication to organizations, is also projected to bolster the market's growth.
Gather more insights about the market drivers, restrains and growth of the Multi-factor Authentication Market
Companies such as CA Technologies, Vasco Data Security International, Inc., RSA Security LLC, and Symantec Corporation are making significant R&D investments to develop new authentication products, solutions, and services.
Cost and implementation complexities will restrain the market; however, their impact will decrease with time. With the rise in data and security breaches, most industries have launched data security standards. To address security breaches and cyber-attacks, enterprises have adopted MFA solutions. These solution implementations are complex and, at the same time, require more capital investment for procurement, implementation, maintenance, and management. Heterogeneous IT environments across industries further increase the complexity.
The overall investment for implementing MFA is estimated to be high due to increased support services, training, SMS gateway, and hardware and software tokens. The requirement of additional drivers for physical authenticators and interoperability with varying IT environments increase the complexity of deployment. Hence, issues pertaining to the procurement cost and implementation complexity are poised to limit the widespread adoption of multi-factor authentication solutions.
Browse through Grand View Research's Next Generation Technologies Industry Research Reports.
The global cross-border e-commerce logistics market size was estimated at USD 97.85 billion in 2023 and is projected to grow at a CAGR of 25.4% from 2024 to 2030.
The global application integration market size was valued at USD 15.90 billion in 2023 and is projected to grow at a CAGR of 19.8% from 2024 to 2030.
Key Companies & Market Share Insights
The key players in the industry are focusing on organic and inorganic growth strategies to maintain their market position. The industry players are undertaking strategies such as product launches, acquisitions, and collaborations to increase their global reach. For instance, in February 2023, Microsoft introduced a “Number Matching” feature in its Authenticator app to enhance security, particularly against MFA fatigue attacks. These attacks involve social engineering techniques employed by hackers to gain unauthorized access to an individual’s account. From May 2023 onwards, the company enabled this new feature for Microsoft Azure.
Key Multi-factor Authentication Companies:
Vasco Data Security International, Inc.
RSA Security LLC
Fujitsu America, Inc.
NEC Corporation
Symantec Corporation
Thales
3M
aPersona, Inc.
CA Technologies.
Safran S.A
Recent Developments
In April 2023, Thales, a leading global technology and security solutions provider, unveiled the SafeNet Token Fusion series. This innovative collection of USB tokens combines Fast IDentity Online 2.0 (FIDO2) with PKI/CBA, creating a single authenticator. The primary objective of Thales's new tokens was to safeguard Microsoft Azure Active Directory (Azure AD) users by mitigating the risk of account compromise by delivering enhanced security for accessing cloud and web applications.
In April 2022, Trust Stamp unveiled a Biometric Multi-Factor Authentication (Biometric MFA) solution. This innovative system revolutionizes identity verification by automating a strong level of assurance through a simple selfie. By leveraging biometric technology, the Biometric MFA adds two additional layers of authentication to verify the user's liveliness and secure tokenizing data from the selfie.
In March 2022, MIRACL, a cybersecurity software firm and Aware Inc., an authentication company, announced a strategic partnership to continue their cloud-based biometric authentication technology. The collaboration aims to address common challenges in business authentication by leveraging MIRACL's single-step, secure multi-factor authentication technology and Aware's recognized expertise in biometrics.
In May 2021, Microsoft announced the launch of new products, guidance, and employee plans to enhance security and provide enhanced customer support. Additionally, Microsoft revealed its commitment to adopting a zero-trust approach, ensuring that its employees embrace this security framework.
In April 2021, HID Global made its WorkforceID Authentication solution available to the public, offering enterprises a cloud-based platform for issuing, managing, and utilizing digital identity credentials for physical and logical access control. This solution enables organizations to streamline and enhance the security of user logins across all applications within their enterprise environment.
In July 2020, Ping Identity announced a collaboration with One Identity, a leading provider of security solutions centered around identity. This partnership aimed to deliver comprehensive identity management strategies and enhance access security and control. Both companies offered a powerful solution that covers consumers' end-to-end identity management needs by combining the capabilities of Ping Identity's access management technology with One Identity's Identity Governance and Administration (IGA) technology.
Order a free sample PDF of the Multi-factor Authentication Market Intelligence Study, published by Grand View Research.
0 notes
Text
Beyond the Hype: Unveiling the Power of AWS for My Cloud Journey
Deciding on a cloud service provider is a significant choice that impacts the efficiency and scalability of your operations. After a thorough evaluation, AWS emerged as my top pick for several reasons. In this blog, I will outline why AWS stands out as the optimal cloud platform.
Professionals can get the skills and knowledge required to fully utilize AWS for a variety of applications and industries by enrolling in AWS Training in Hyderabad.

Diverse Range of Services
AWS offers an unparalleled selection of services that cover all aspects of IT infrastructure and development. Whether it's computing power, storage solutions, databases, or advanced technologies like AI and IoT, AWS provides comprehensive options. This broad spectrum allows for creating sophisticated, scalable, and customizable solutions.
Key services include AWS’s Elastic Compute Cloud (EC2), which provides scalable computing power, and AWS Lambda, which supports serverless computing by allowing code execution without the need to manage servers.
Extensive Global Infrastructure
With its vast global network of availability zones spread across numerous regions, AWS ensures that applications can be deployed close to end-users. This setup minimizes latency and enhances performance while also offering robust disaster recovery options through redundancy and failover capabilities.
AWS’s global reach also helps meet data sovereignty requirements by enabling data storage in specific geographic locations to comply with local regulations.
Scalability and Adaptability
AWS excels at scaling resources to match demand, which is crucial for handling varying workloads efficiently. Its flexible pricing models, such as pay-as-you-go, reserved instances, and spot instances, help optimize costs and manage resources effectively.
Services like Amazon EC2 Auto Scaling and the AWS Elastic Load Balancer (ELB) ensure high availability and reliability by adjusting capacity and distributing traffic as needed.
Enrolling in the Best AWS Online Training can help people understand AWS's complexities and realize its full potential.

Robust Security and Compliance
AWS prioritizes security with a comprehensive framework that includes physical, operational, and software measures. Its wide range of compliance certifications simplifies meeting regulatory standards. Features like Identity and Access Management (IAM), encryption, and advanced monitoring tools ensure a secure environment for data and applications.
AWS’s shared responsibility model delineates security responsibilities between AWS and the user, supported by tools like AWS Key Management Service (KMS) and AWS CloudTrail for enhanced security management.
Continuous Innovation
AWS is renowned for its rapid innovation pace, consistently introducing new services and features. This commitment ensures access to the latest technologies, helping maintain a competitive edge.
For instance, AWS offers advanced machine learning tools like Amazon SageMaker and AI services like Amazon Rekognition and Amazon Polly, enabling cutting-edge capabilities in image analysis and text-to-speech conversion.
Strong Community and Support Network
The AWS ecosystem includes a vast community of developers, partners, and third-party vendors. This network offers valuable resources such as documentation, tutorials, forums, and a marketplace for additional tools and services, fostering a supportive environment for learning and growth.
AWS re, an annual conference, showcases new innovations and offers extensive educational opportunities. The AWS Partner Network (APN) provides access to technology and consulting partners to help build and optimize AWS-based solutions.
Cost Management and Savings
AWS offers various ways to manage and reduce costs effectively. Its pricing models and cost management tools, such as AWS Cost Explorer and Trusted Advisor, help monitor usage and forecast expenses, enabling cost-saving strategies.
The AWS Free Tier allows new customers to explore and use AWS services for free within certain limits, providing an excellent entry point. AWS Savings Plans also offer significant savings compared to On-Demand pricing.
Seamless Integration
AWS integrates smoothly with various third-party tools and on-premises systems, ensuring a seamless transition to the cloud. This interoperability is crucial for maintaining business continuity and leveraging existing IT infrastructure investments.
AWS Direct Connect and AWS Storage Gateway are examples of services that facilitate integration, enhancing network performance and providing hybrid cloud solutions.
Conclusion
Choosing AWS as my cloud platform was a strategic decision based on its diverse service offerings, extensive global infrastructure, scalability, robust security, continuous innovation, supportive community, cost management, and seamless integration capabilities. AWS not only meets my current needs but also provides the flexibility and tools to adapt and grow. For anyone considering cloud computing, AWS stands out as a reliable and powerful platform.
0 notes
Text
Navigating the Dynamic Landscape of Serviced Office Rental in Singapore

In the bustling metropolis of Singapore, where innovation meets tradition and commerce thrives, the demand for flexible and efficient office solutions is ever-present. Entrepreneurs, startups, and established businesses alike seek agility and convenience in their workspace arrangements. This demand has given rise to the popularity of serviced office rentals, offering a myriad of benefits in a dynamic and competitive market.
Serviced offices, also known as managed offices or business centers, provide fully furnished and equipped workspace solutions on flexible lease terms. They offer a wide range of amenities and services tailored to meet the diverse needs of businesses, from solo entrepreneurs to multinational corporations. Here’s a closer look at why serviced office rental in Singapore has become the preferred choice for many:
Flexibility: One of the key advantages of serviced offices is flexibility. Unlike traditional leases that typically lock tenants into long-term contracts, serviced offices offer short-term agreements that allow businesses to scale up or downsize according to their needs. This flexibility is particularly valuable for startups and rapidly growing companies that require agility in their operations.
Cost-Effectiveness: Serviced offices eliminate the need for hefty upfront investments in office infrastructure and amenities. With a single monthly fee, businesses gain access to fully furnished workspaces, high-speed internet, meeting rooms, administrative support, and other essential services. This all-inclusive pricing model helps businesses forecast their expenses more accurately and avoid the financial burden of managing office facilities independently.
Prime Locations: Singapore is renowned for its strategic location and vibrant business environment. Serviced office providers capitalize on this by offering prime locations in prestigious business districts such as Marina Bay, Raffles Place, and Orchard Road. By establishing their presence in these coveted areas, businesses can enhance their professional image, attract top talent, and network with industry peers more effectively.
Professional Support Services: Serviced office providers go beyond offering physical workspace; they also provide a range of professional support services to streamline business operations. From reception and concierge services to IT support and mail handling, these amenities allow businesses to focus on their core activities while outsourcing non-core functions to experienced professionals.
Scalability and Customization: Whether you need a private office for a small team or a dedicated floor for your entire company, serviced offices offer scalability to accommodate your evolving needs. Furthermore, many providers offer customizable workspace solutions that allow businesses to personalize their environment according to their branding and culture, fostering a sense of ownership and identity.
Networking Opportunities: Shared spaces and communal areas within serviced offices create opportunities for networking and collaboration among tenants. By coexisting with diverse businesses and professionals, tenants can leverage synergies, exchange ideas, and explore potential partnerships. This sense of community fosters innovation and creativity, enriching the overall work experience.
In conclusion, serviced office rental in Singapore offers a compelling proposition for businesses seeking flexibility, cost-effectiveness, and convenience in their workspace solutions. With prime locations, comprehensive amenities, and a supportive environment, serviced offices empower businesses to thrive in the dynamic landscape of Singapore’s business ecosystem. As the demand for flexible office solutions continues to grow, serviced offices are poised to remain a cornerstone of modern workspace strategy for years to come.
0 notes
Text
EAGLEEYE COIN: Pioneering Web3 Investments with Leading Innovators
EAGLEEYE COIN: Pioneering Web3 Investments with Leading Innovators
Anyone who follows the market will know that web3 has been on an upward trend for years. From IMB to Apple, some of the world's largest companies have taken the lead in this space, generating renewed public interest along with financial support.
2024 promises to be a pivotal year for the sector as it can act as a bridge to future growth. Macroview Research forecasts web3 to grow at a CAGR of 49.3% from 2024 to 2030. Needless to say, anyone investing in web3 will want to keep a close eye on the companies operating in it in 2024.
But which companies are expected to stand out? After all, the web3 space is both large and innovative, and between cryptocurrencies, DAOs, and NFTs, the market is full of possibilities.
Even among these companies, the following stand out as companies to watch:
Courtyard [Center] The Courtyard Center is a web3 venture studio dedicated to taking a hands-on, iterative approach to turning ideas into ventures. The studio not only provides financial support, but also expert guidance to its portfolio startups to help them grow into strong web3 businesses. YARD Hub believes that startups thrive under the guidance of its experienced in-house team, which improves the chances of achieving the right product/market fit.
As Sergei Lagutenko, co-founder of YARD Hub, explains, the studio covers a wide range of expertise, from business analytics and product management to marketing and business development, guiding startups through the common pitfalls that lead to failure.
In addition, YARD Hub has launched Growth Camp, a web3 gas pedal program that is now inviting applications for its second cohort scheduled to launch in the second quarter of 2024. The program provides startups with access to elite mentors, partner benefits and six integrated learning paths.
YARD Hub's portfolio offers an enticing opportunity for those keen to track the rise of top web3 companies.
U2U Network The U2U Network stands at the forefront of the Web3 revolution as a pioneer of modular blockchain and decentralized physical infrastructure networks (DePIN). Utilizing advanced subnetting technology, the U2U Network introduces a modular approach to blockchain that enhances scalability and flexibility. This innovative framework allows for the creation of dedicated subnets customized for specific applications or industries, thereby addressing traditional blockchain limitations to reach up to 500,000 transactions per second (TPS) in less than 650 milliseconds of finalization time.

In the DePIN space, U2U Network's strength lies in providing a full suite of decentralized services, including Decentralized Private Networks (DPNs), Decentralized Identities (DIDs), Decentralized Storage, and more. These services embody the essence of DePIN, providing on-demand, decentralized services. solutions that empower users and foster safer, more efficient, community-owned digital ecosystems. U2U Network's commitment to modular blockchain technology and DePIN makes it a key player in shaping the future of decentralized digital infrastructure. U2U Network is a top Web3 company to watch closely as we enter 2024.
Chain Analytics Chainaanalysis, a blockchain analytics company, has stood out as a major player in the web3 space this year. Over the years, Chainaanalysis has been putting out some of the most insightful and groundbreaking blockchain-related research you'll see anywhere. For example, Chainaanalysis has been at the forefront of investigating the activities of the Silk Road marketplace and has even helped authorities recover more than $1 billion from it. The company also uncovered the activities of the Lazarus Group, a North Korean hacking organization.
2024 will be a year of growth in the blockchain and web3 space, and we can trust Chainaanalysis to be at the forefront of that research. The firm began the year with a strong focus on activity in spot bitcoin ETFs, and as halving and other activity unfolds in the space, the industry will turn to Chainaanalysis for its track record of efficient research.
Filecoin Filecoin is a prominent web3 project to watch out for this year and has been a prominent figure in the field for years. It acts as a blockchain-based digital storage and data retrieval cooperative, enabling users to store and access their data independently of centralized entities. This feature gives users important privacy and control over their information, which is in keeping with the spirit of the web3 environment. In the first few weeks of 2024, File Coin released Glif, a liquidity leasing protocol, raised $4.5 million in a seed funding round, and plans to launch a rewards program for users.
All this excitement has had a positive impact on the ecosystem's native token, FIL, with some predicting its value to reach $50 per unit by the end of the year. As web3 comes to the forefront, more users will want to take control of their data and privacy, and File Coin seems perfectly positioned to fulfill that need.
All in all, 2024 is a promising year for web3 and promises to be a transformative bridge for future growth. With projected compounds Grand View Research forecasting an annual growth rate of 49.3%, the momentum behind web3 is undeniable. As the market is full of possibilities, investors and enthusiasts must keep a close eye on the ever-changing landscape. The web3 space embodies innovation and potential, fueled by a host of technologies ranging from cryptocurrencies to decentralized autonomous organizations (DAOs) and non-fungible tokens (NFTs). These advances mark the Internet's paradigm shift towards decentralization and democratization. As we move through this era of unprecedented change, we must remain vigilant and adaptive, embracing the transformative potential of the web3.
0 notes
Text
Securing the Future: An In-Depth Analysis of the Security Technology Market
In an era marked by technological advancements and evolving threats, the security technology market plays a pivotal role in safeguarding individuals, organizations, and critical infrastructure. This comprehensive analysis aims to delve into the intricacies of the security technology market, providing insights into emerging trends, key players, and the dynamics that shape the future of security solutions.
Threat Landscape and Risk Assessment:
1.1. Cybersecurity Threats: A thorough examination of the evolving landscape of cyber threats, including malware, ransomware, and phishing attacks, to understand the challenges faced by the security technology market.
1.2. Physical Security Risks: Analysis of physical security risks, encompassing issues such as unauthorized access, surveillance, and the protection of critical infrastructure.
Emerging Technologies in Security:
2.1. Artificial Intelligence and Machine Learning: Exploration of how AI and machine learning are being integrated into security technologies for advanced threat detection, anomaly identification, and predictive analysis.
2.2. Biometric Solutions: An in-depth look at the adoption and advancements in biometric technologies, including facial recognition, fingerprint scanning, and iris recognition, enhancing identity verification and access control.
Cybersecurity Landscape:
3.1. Security Software Solutions: Analysis of the latest trends in security software, including antivirus programs, firewalls, and endpoint protection, to mitigate the risks posed by cyber threats.
3.2. Network Security: Examination of network security technologies, such as intrusion detection and prevention systems, secure gateways, and VPNs, ensuring the integrity and confidentiality of data.

Buy full report for more insights into the Security market forecast
Download a free report sample
Physical Security Technologies:
4.1. Surveillance Systems: Overview of advancements in surveillance technologies, including CCTV cameras, video analytics, and drone surveillance, enhancing physical security measures.
4.2. Access Control Systems: Analysis of access control solutions, such as smart cards, biometric access, and electronic locks, for managing and restricting entry to secure areas.
Regulatory Compliance and Standards:
5.1. Global Security Standards: An examination of international and industry-specific security standards and regulations governing the development and implementation of security technologies.
5.2. Compliance Challenges: Discussion on the challenges faced by organizations in maintaining compliance with evolving security regulations and the role of technology in addressing these challenges.
Security Technology Market Players:
6.1. Key Industry Players: Profiling major companies in the security technology market, assessing their market share, product portfolios, and strategic initiatives.
6.2. Startups and Innovators: Exploration of emerging startups and innovators that are disrupting the security technology market with novel approaches and solutions.
Future Outlook:
7.1. Technology Convergence: Identification of trends indicating the convergence of cybersecurity and physical security technologies for comprehensive security solutions.
7.2. Evolving Threats and Adaptive Solutions: Anticipation of future threats and the need for security technologies to evolve, adapt, and innovate in response to emerging risks.
Conclusion:
As the security technology market continues to evolve in response to dynamic threats, understanding the landscape and embracing innovative solutions is paramount. This analysis provides a comprehensive overview of the security technology market, offering valuable insights for stakeholders to navigate the challenges and secure the future effectively.
0 notes