#Encrypted connection
Explore tagged Tumblr posts
Text
SetupVPN - Lifetime Free VPN
SetupVPN – Lifetime Free VPN is a program that provides access to a free virtual private network (VPN) service. VPNs enhance the security of your internet connection by encrypting the data you exchange, offer greater anonymity by masking your real IP address, and allow you to use an IP address from another location. This is particularly useful for accessing content that is restricted to certain…
#access blocked websites#anonymous browsing#encrypted connection#free VPN#free VPN service#Online Privacy#Secure Browsing#SetupVPN#unblock content#VPN#VPN for streaming#VPN service
0 notes
Text
101: How to Protect Your Money from Cyber Threats
The internet has made it easier than ever to manage your money and make financial transactions, but it has also created new opportunities for cybercriminals to steal your personal and financial information. In today’s digital age, protecting your money online is more important than ever. Here are some tips for keeping your money safe online Use strong passwords: A strong password is the first…

View On WordPress
#and don&039;t get hacked! Online safety#Cyber security#Cyber threats#cyber threats are everywhere. But don&039;t worry#Cybercrime Prevention#Cybersecurity Awareness#Data Privacy#Digital age#Digital Security#Encrypted connection#Financial security#in this video#In today&039;s digital age#Internet Safety#Internet security#Online fraud#Online Safety#Online Scams#Online security#Online Security Tips#Online transactions#Personal information#Phishing scams#Protect Credit Card Information#Protect money#Protect Money Online#Protect Personal Information#protecting your money online is more important than ever. From phishing scams to insecure online transactions#Public Wi-Fi#Public Wi-Fi Risks
0 notes
Text
not to brag about being good at my job but I’ve now developed two separate tools for debugging entirely on my own within my company entirely from scratch without help and A. it makes my job so much fucking easier and B. my boss is thinks im incredible just because im too lazy to want to write the same bits of code over and over just for debugging purposes
#unimportant thoughts#one i wrote 2-3 months ago#but i upgraded it this week to add in even more#and its just. perfect now.#given an id from any of the programs we built and run in our company#i instantaneously return everything about it#its name; what it does; what type of program it is; what server its run on; when it runs; where it connects; the parameters needed to#connect to wherever it connects; whether the program is currently turned on; the last 10 times the program ran; how many minutes each of#those runs took; how many files each of those runs created; whether those runs were successful; code snippets you can copy paste and run in#another window to look at the files created by each of those runs; the files created by the most recent run; thise file names; those file s#sizes; what types of files they are; whether theyre encrypted#how theyre encrypted#all of that and MORE#most of the information was already there but it took fucking 20 minutes to get all the information you needed#and you had to run a bunch of different snippets of code to get all the information and then put it all together#and now you can just fucking pop in the id of the program and .02 of a second later all the information is on your screen#AND IT MAKES MY LIFE SO MUCH EASIER#so. so. so. much. easier.#and then this week I wrote another program so I can compare runtimes of two different runs of the same program together based on how we stor#runtime data in our database#csuse i was tired of going back and forth manually between to different runs to compare#so now i have a program that just takes the ids of two different runs and compares them#doesnt even matter if the checkpoints are different I programmed it to figure out the order automatically and plug in any missing holes#finds the differences in runtime automatically and flags the biggest differences#and I can even customize how much of a difference I care about or to hide things I don’t care about
12 notes
·
View notes
Text
Understanding Encryption: How Signal & Telegram Ensure Secure Communication

Signal vs. Telegram: A Comparative Analysis

Signal vs Telegram
Security Features Comparison
Signal:
Encryption: Uses the Signal Protocol for strong E2EE across all communications.
Metadata Protection: User privacy is protected because minimum metadata is collected.
Open Source: Code publicly available for scrutiny, anyone can download and inspect the source code to verify the claims.
Telegram:
Encryption: Telegram uses MTProto for encryption, it also uses E2EE but it is limited to Secret Chats only.
Cloud Storage: Stores regular chat data in the cloud, which can be a potential security risk.
Customization: Offers more features and customization options but at the potential cost of security.
Usability and Performance Comparison
Signal:
User Interface: Simple and intuitive, focused on secure communication.
Performance: Privacy is prioritized over performance, the main focus is on minimizing the data collection.
Cross-Platform Support: It is also available on multiple platforms. Like Android, iOS, and desktop.
Telegram:
User Interface: Numerous customization options for its audience, thus making it feature rich for its intended audience.
Performance: Generally fast and responsive, but security features may be less robust.
Cross-Platform Support: It is also available on multiple platforms, with seamless synchronization across devices because all the data is stored on Telegram cloud.
Privacy Policies and Data Handling
Signal:
Privacy Policy: Signal’s privacy policy is straightforward, it focuses on minimal data collection and strong user privacy. Because it's an independent non-profit company.
Data Handling: Signal does not store any message data on its servers and most of the data remains on the user's own device thus user privacy is prioritized over anything.
Telegram:
Privacy Policy: Telegram stores messages on its servers, which raises concerns about privacy, because theoretically the data can be accessed by the service provider.
Data Handling: While Telegram offers secure end to end encrypted options like Secret Chats, its regular chats are still stored on its servers, potentially making them accessible to Telegram or third parties.
Designing a Solution for Secure Communication
Key Components of a Secure Communication System
Designing a secure communication system involves several key components:
Strong Encryption: The system should employ adequate encryption standards (e.g. AES, RSA ) when data is being transmitted or when stored.
End-to-End Encryption: E2EE guarantees that attackers cannot read any of the communication, meaning that the intended recipients are the only ones who have access to it.
Authentication: It is necessary to identify the users using secure means such as Two Factor Authentication (2FA) to restrict unauthorized access.
Key Management: The system should incorporate safe procedures for creating, storing and sharing encryption keys.
Data Integrity: Some standard mechanisms must be followed in order to ensure that the data is not altered during its transmission; For instance : digital signatures or hashing.
User Education: To ensure the best performance and security of the system, users should be informed about security and the appropriate use of the system such practices.
Best Practices for Implementing Encryption
To implement encryption effectively, consider the following best practices:
Use Proven Algorithms: Do not implement proprietary solutions that are untested, because these algorithms are the ones which haven't gone through a number of testing phases by the cryptographic community. On the other hand, use well-established algorithms that are already known and tested for use – such as AES and RSA.
Keep Software Updated: Software and encryption guidelines must be frequently updated because these technologies get out of date quickly and are usually found with newly discovered vulnerabilities.
Implement Perfect Forward Secrecy (PFS): PFS ensures that if one of the encryption keys is compromised then the past communications must remain secure, After every session a new key must be generated.
Data must be Encrypted at All Stages: Ensure that the user data is encrypted every-time, during transit as well as at rest – To protect user data from interception and unauthorized access.
Use Strong Passwords and 2FA: Encourage users to use strong & unique passwords that can not be guessed so easily. Also, motivate users to enable the two-factor authentication option to protect their accounts and have an extra layer of security.
User Experience and Security Trade-offs
While security is important, but it's also important to take care of the user experience when designing a secure communication system. If your security measures are overly complex then users might face difficulties in adopting the system or they might make mistakes in desperation which might compromise security.
To balance security and usability, developers should:

Balancing Security And Usability
Facilitate Key Management: Introduce automated key generation and exchange mechanisms in order to lessen user's overhead
Help Users: Ensure that simple and effective directions are provided in relation to using security aspects.
Provide Control: Let the users say to what degree they want to secure themselves e.g., if they want to make use of E2EE or not.
Track and Change: Always stay alert and hands-on in the system monitoring for security breaches as well as for users, and where there is an issue, do something about it and change
Challenges and Limitations of Encryption Potential Weaknesses in Encryption
Encryption is without a doubt one of the most effective ways of safeguarding that communications are secured. However, it too has its drawbacks and weaknesses that it is prone to:
Key Management: Managing and ensuring the safety of the encryption keys is one of the most painful heads in encryption that one has to bear. When keys get lost or fall into unsafe hands, the encrypted information is also at risk.
Vulnerabilities in Algorithms: As far as encryption is concerned the advanced encryption methods are safe and developed well, but it is not given that vulnerabilities will not pop up over the years. Such vulnerabilities are meant for exploitation by attackers especially where the algorithm in question is not updated as frequently as it should be.
Human Error: The strongest encryption can be undermined by human error. People sometimes use weak usernames and passwords, where they are not supposed to, and or even share their credentials with other persons without considering the consequences.
Backdoors: In some cases, businesses are pressured by Governments or law officials into adding back doors to the encryption software. These backdoors can be exploited by malicious actors if discovered.
Conclusion
Although technology has made it possible to keep in touch with others with minimal effort regardless of their geographical location, the importance of encryption services still persists as it allows us to protect ourselves and our information from external invaders. The development of apps like Signal and Telegram has essentially transformed the aspect of messaging and provided their clients with the best security features covering the use of multiple types of encryption and other means to enhance user privacy. Still, to design a secure communication system, it's not only designing the hardware or software with anti-eavesdropping features, but it factors in the design of systems that relate to the management of keys, communication of the target users, and the trade-off between security and usability.
However, technology will evolve, followed by the issues and the solutions in secure communications. However by keeping up with pace and looking for better ways to protect privacy we can provide people the privacy that they are searching for.
Find Out More
2 notes
·
View notes
Text
My feelings are encrypted in my head but he knows how to decrypt them, put them in words and make it easy for me to understand myself.

1 note
·
View note
Text
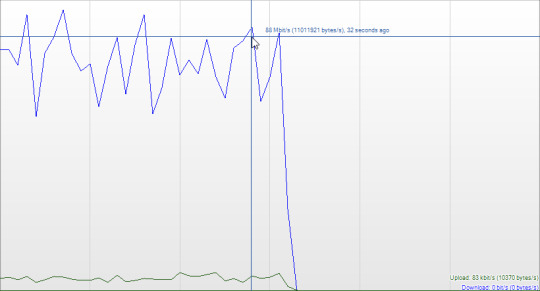
FUCKKKK my school frrr, network is totally capable of allocating me 86Mbp/s for JUST qBITTORRENT but instead of getting access to that we get throttled down to like >400Kbps if even.
#.txt#to explain what this graph is#the blue is my down speed#green is up speed#I have my vpn on and with port forwarding#which is able to circumvent my schools NAT protocol by forwarding the network traffic to a local port on my computer#(its technically remote port forwarding but)#and because I can get traffic directed to my machine a lot of the traffic that gets throttled by the networks security protocols#specifically NAT.( btw I am not inviting hostile activity onto the network I am just choosing to encrypt my data and verify authenticity#with a different protocol than NAT. specifically wireGuard which is the leading VPN protocol now)#however a lot of people dont like port forwarding because of that property and few VPNs support it anymore but its like the only way to#torrent at more than a snails pace#and so my school detected my high network activity and because of the encrypted data I was sending they literally just deny me service#I can just connect back with my regular PC no problem too so its not even stopping me#its just delaying me and making it annoying'
4 notes
·
View notes
Text

23K notes
·
View notes
Text
Understanding the Difference Between 4G and 5G Networks
As our reliance on mobile connectivity grows, so does the need for faster, more efficient networks. Understanding the difference between 4G and 5G networks is crucial as 5G technology becomes more widely available, promising to revolutionise how we interact with the digital world. From browsing the web to powering autonomous vehicles and smart cities, 5G is set to offer significant advancements…
#4G#5G#5G applications#5G benefits#5G rollout#5G security#AI#AR#automation#autonomous vehicles#bandwidth#cell towers#cloud#Connected Devices#connectivity#cyber threats#data transfer#digital#download speed#emerging tech#encryption#firewalls#Healthcare#infrastructure#innovation#IoT#IT leaders#latency#low latency#Mobile
0 notes
Text




1 note
·
View note
Text
Safeguarding Connectivity: Addressing Vulnerabilities in 5G Infrastructure
In the realm of technological evolution, 5G has emerged as the pinnacle of innovation, promising unprecedented connectivity, lightning-fast speeds, and transformative capabilities. However, amidst the euphoria surrounding this groundbreaking technology, concerns about security loom large. As the 5G landscape continues to evolve, ensuring robust security measures is imperative to mitigate potential risks and safeguard sensitive data.
Understanding the Significance of 5G Security
Defining the Paradigm Shift
5G represents a paradigm shift in wireless communication, revolutionizing industries, and empowering IoT ecosystems. With its enhanced speed, capacity, and low latency, 5G is poised to unleash a wave of innovation across various sectors, ranging from healthcare and transportation to manufacturing and entertainment. However, the proliferation of 5G also introduces novel security challenges that demand proactive solutions.
Addressing Vulnerabilities
The unprecedented speed and connectivity offered by 5G networks amplify the attack surface, rendering traditional security measures inadequate. Cybercriminals can exploit vulnerabilities in 5G infrastructure to launch sophisticated cyberattacks, compromising network integrity and data confidentiality. From DDoS attacks to man-in-the-middle assaults, the threat landscape has evolved, necessitating robust security protocols to safeguard against potential breaches.
The Evolution of 5G Security Measures
Encryption and Authentication
Encryption lies at the heart of 5G security, ensuring that data remains confidential and integrity is maintained during transmission. Advanced cryptography algorithms such as AES and Elliptic Curve Cryptography are employed to encrypt data packets, thwarting eavesdropping attempts by malicious actors. Additionally, stringent authentication mechanisms, including digital certificates and biometric authentication, bolster access control and mitigate the risk of unauthorized access.
Network Slicing and Virtualization
Network slicing emerges as a game-changer in 5G security, enabling service providers to partition network resources into distinct virtual networks tailored to specific use cases. By implementing isolated slices with dedicated security policies, organizations can ensure segmentation and isolation of critical services, minimizing the blast radius in the event of a security breach. Furthermore, network function virtualization (NFV) enhances agility and resilience, allowing rapid deployment of security functions to counter emerging threats.
AI-Powered Threat Detection
In the era of 5G, Artificial Intelligence (AI) emerges as a potent ally in the cybersecurity arsenal, leveraging machine learning algorithms to detect and mitigate threats in real-time. By analyzing vast datasets and identifying anomalies in network traffic, AI-driven security solutions can preemptively thwart cyberattacks before they escalate, thereby fortifying 5G infrastructure against evolving threats.
Collaboration and Regulatory Compliance
Industry Collaboration
The complexity and interconnectedness of 5G ecosystems necessitate collaboration among stakeholders to establish industry-wide standards and best practices. From telecommunication providers and equipment manufacturers to government agencies and regulatory bodies, concerted efforts are required to foster a secure and resilient 5G ecosystem. Information sharing and collaborative research play a pivotal role in strengthening cyber defenses and mitigating emerging threats.
Regulatory Frameworks
Regulatory frameworks serve as a cornerstone of 5G security, providing guidelines and compliance mandates to ensure adherence to security standards and privacy regulations. Regulatory bodies such as the National Institute of Standards and Technology (NIST) and the European Telecommunications Standards Institute (ETSI) play a pivotal role in shaping the security landscape by issuing recommendations and certifications to validate compliance with security protocols.
Conclusion
As 5G continues its inexorable march towards global proliferation, security remains paramount in unlocking its transformative potential. By embracing encryption, network slicing, AI-driven threat detection, and fostering collaboration across industry stakeholders, organizations can fortify 5G infrastructure against emerging threats and embark on a journey towards a secure and resilient digital future.
#5G security#telecommunications#connectivity#innovation#cyberattacks#data breaches#encryption#authentication mechanisms#network segmentation#continuous monitoring#digital infrastructure#technology#privacy#artificial intelligence#nextgeneration connectivity#digital future#cyber security
0 notes
Text
Features of the Most Reliable VPN Services
In today’s interconnected world, where privacy concerns and data breaches are rampant, Virtual Private Networks (VPNs) have emerged as indispensable tools for safeguarding online activities. However, not all VPN services are created equal. While some may offer flashy features or enticing deals, the true mark of reliability lies in a set of core features that distinguish the best from the rest. In…

View On WordPress
#A#Cross-Platform Compatibility#Customer Support#Customer support availability#Data encryption#Data encryption standards#Data Protection#Data protection measures#Encryption protocol security#Geo-restriction#Geo-restriction bypass#Geo-restriction circumvention#Internet safety#Internet safety assurance#Kill switch#Kill switch feature#Leak protection#Leak protection mechanism#Network reliability#Network reliability assessment#No-logs guarantee#No-Logs Policy#Online Privacy#Online privacy protection#Privacy policy assurance#Privacy protection#Secure Connection#Secure connection establishment#Security encryption#Server network
0 notes
Text

A little-discussed detail in the Lavender AI article is that Israel is killing people based on being in the same Whatsapp group [1] as a suspected militant [2]. Where are they getting this data? Is WhatsApp sharing it? Lavender is Israel's system of "pre-crime" [3] - they use AI to guess who to kill in Gaza, and then bomb them when they're at home, along with their entire family. (Obscenely, they call this program "Where's Daddy"). One input to the AI is whether you're in a WhatsApp group with a suspected member of Hamas. There's a lot wrong with this - I'm in plenty of WhatsApp groups with strangers, neighbours, and in the carnage in Gaza you bet people are making groups to connect. But the part I want to focus on is whether they get this information from Meta. Meta has been promoting WhatsApp as a "private" social network, including "end-to-end" encryption of messages. Providing this data as input for Lavender undermines their claim that WhatsApp is a private messaging app. It is beyond obscene and makes Meta complicit in Israel's killings of "pre-crime" targets and their families, in violation of International Humanitarian Law and Meta's publicly stated commitment to human rights. No social network should be providing this sort of information about its users to countries engaging in "pre-crime".
#yemen#jerusalem#tel aviv#current events#palestine#free palestine#gaza#free gaza#news on gaza#palestine news#news update#war news#war on gaza#war crimes#gaza genocide#genocide#ai#artificial intelligence
6K notes
·
View notes
Text
Endpoint malware attacks decline as campaigns spread wider - Help Net Security
In Q2 2023, 95% of malware now arrives over encrypted connections, endpoint malware volumes are decreasing despite campaigns growing more widespread, ransomware detections are declining amid a rise in double-extortion attacks, and older software vulnerabilities persist as popular targets for exploitation among modern threat actors, among other trends, according to WatchGuard. “The data analyzed…

View On WordPress
1 note
·
View note
Text
Mobile Device Security: Protecting Your Digital Life On the Go - Cybersecurity Resource
bit.ly/47jNZfw
#Mobile device security#Smartphone security#Mobile data protection#Lock screen protection#App security#Mobile encryption#Two-Factor Authentication (2FA)#Secure Wi-Fi connections#Phishing awareness#App permissions
0 notes
Text
Virtual Private Networks

The best VPN list therefore only includes providers who take the security and virtual privacy of their users seriously. We made sure that they offer no logs (i.e. do not record any data from you) and use good encryption to secure your traffic and hide your personal information.
0 notes
Text
🚨🚨🚨EARN IT ABOUT TO BE PASSED🚨🚨🚨
PLEASE SOMEONE ANYONE HELP US
WE WILL BE SPIED ON DUE TO NO ENCRYPTION
LGBTQ+ CONTENT WILL BE WIPED FROM THE INTERNET
SEX WORKERS WILL BE CRIMINALIZED
THIS BILL WILL KILL THE INTERNET AS WE KNOW IT
what to do?
CALL YOUR STATE REPS
SIGN PETITIONS
DONATE
JOIN DISCORD SERVER
I AM BEGGING YOU PLEASE DO SOMETHING!
🚨🚨🚨🚨 URGENT 🚨🚨🚨🚨
#gay rights#bisexual#pansexual#gay#lesbian#lgbtq+#lgbt#lgbtq#lgbtqia#lgbtqia+#trans rights#transgender#transmasc#mtf#ftm#fuck internet censorship#fuck earn it#earn it#kosa#online privacy#aesthetic#vocaloid#art#molly🚨 aids
11K notes
·
View notes