#Cyber threats
Explore tagged Tumblr posts
Text

Want to put this profile on blast to protect others. Please report this profile and block them. They messaged me and started off nice like all fake mommies/mistresses do. But literally within a minute she had screen captured some of my photos from my blog and was threatening blackmail. Fortunately I never show my face or use my name. Protect yourselves everyone. These people are everywhere and don’t trust someone just because they say the things you want to hear
3 notes
·
View notes
Text

Capitol rioter charged after tweeting death threat to AOC
#Capitol rioter charged after tweeting death threat to AOC#capitolhill#us capitol#capitol riot#rioter#aoc#death threats#cyber threats#threats#usa is a terrorist state#usa politics#usa news#usa#american indian#american#america#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#biden administration#genocide joe#joe biden#president biden
2 notes
·
View notes
Text
Diatribe For A Fandom
I can not wait until Jared, Jensen and Misha get so fed up - with the hate, the threats on their lives, the lies and harassment - that they put an end to the cons. And it WILL happen. (A person can only take so much.) Once it happens, all the miscreants who have thrown around all this ugliness will have no one else to blame but themselves.
In an age where cyberbullying is at an all time high, a small, but very loud part of this fandom shamelessly partake in it. I don't care if the targets are adults, it's still bullying. It's harassment. It's threatening. And all of you who partake should face some kind of consequences. What kind of person are you to think that threatening another person's life is a normal thing to do? Especially if it's for the dumbest, most selfish, insane, ridiculous reasons (that person doesn't fit your narrative, the character they play isn't your favorite, they're friends with someone you don't like). YOU DO NOT OWN THESE PEOPLE. THEY ARE NOT YOURS TO DEMAND THINGS FROM. THEY ARE NOT CIRCUS PERFORMERS!!
If you are one of these POS who think its okay to do this, I am disgusted by your actions. And I'm sure I'm not alone. A small group of degenerates will ruin things for the rest of us. I, for one, don't care if cons are canceled. But as an adult who was raised to respect others, I will NEVER sit idly by and not call you out. I will NOT silence myself when it comes to defending other people who have done NOTHING WRONG TO YOU PERSONALLY. Maybe this comes with age. Maybe it doesn't. I don't know. And I'll never pretend to understand why people are so hateful and ugly.
"Demons I Get. People Are Crazy." - Dean Winchester
(Dean would be ashamed of all of you.)

#cyberbullying#cyber threats#not cool#you should be ashamed#but you have none#toxic fandom#spn fandom
6 notes
·
View notes
Text
Is your iPhone listening to you? Here's what to know... - CyberTalk
New Post has been published on https://thedigitalinsider.com/is-your-iphone-listening-to-you-heres-what-to-know-cybertalk/
Is your iPhone listening to you? Here's what to know... - CyberTalk


EXECUTIVE SUMMARY:
Have you ever found yourself wondering about whether (or not) your iPhone is listening to you? If the phone is on your person nearly 24/7, what is it hearing that you might prefer for someone not to know about or use against you? (For example, that shouting match with your spouse)
As great as the iPhone is – it’s one of the best, if not the best phone around – it’s awkward to feel like you’re continually being overheard by an invisible third-party.
So, what’s really happening? In this article, discover the truth behind iPhone eavesdropping myths, unravel misconceptions and maximize your phone’s potential.
Gain insights into the nuances of iPhone listening (or lack thereof) and see how to protect your privacy in an era rife with hacking and data compromises.
Is your iPhone listening to you?
It’s true that your iPhone might be passively listening, but perhaps not in the lawless, intrusive ways that you might imagine. Apple does not sell data to third-parties for marketing purposes. The company has explicitly stated that:
“The customer is not our product and our business model does not depend on collecting vast amounts of personally identifiable information…,” in response to a 2018 U.S. congressional inquiry.
If that’s the case, why are iPhones listening?
One of the primary reasons as to why iPhone listening occurs is to detect voice commands, like “Hey Siri”.
While highly unlikely due to Apple’s rules and compliance processes, apps could also be “listening”.
When it comes to advertising, the term “listening” really refers to the use of sophisticated machine learning algorithms, which parse apart language to find ad targeting opportunities.
It’s probably not a coincidence if you’ve had a conversation about buying a new car, and shortly thereafter, corresponding advertisements appear.
Note: This isn’t at all common to iPhones, unless they’ve been jailbroken, and typically only occurs on other device types.
What about Siri?
Siri continuously “listens” for the specific “Hey Siri” cue (and for a small number of similar sounds indicating that a person may have attempted to say “Hey Siri”).
Once a person has said “Hey Siri,” the information is largely processed locally; a somewhat recent departure from the past configuration, where information was processed on Apple’s servers.
Is the iPhone listening illegally?
For iPhones, third-party apps are required to obtain explicit user consent when collecting microphone data. At the outset, Apple reviews apps to ensure that they’re compliant.
All apps must go through the Apple Review Process for privacy compliance ahead of being green-lighted for the app store. That said, the process doesn’t guarantee that app developers can’t misbehave at a later point in time.
In other words, in regards to apps, Apple does its best to ensure that iPhones don’t eavesdrop. Accidents could theoretically occur, although the probabilities are slim and they would be clear violations of Apple’s rules.
Is iPhone listening a cause for concern?
Generally, no. If you’re concerned about iPhone listening, note that the newer generations of iPhones have an indicator at the top of the screen that shows when the mic and camera are on.
The light becomes orange when the mic is on. It turns green when the camera is on. This recently added privacy feature assists users in detecting when an app is accessing their device’s systems.
In exceptional circumstances, spyware could be deployed on a phone, resulting in listening. Typically, this only pertains to higher-profile individuals, uniquely targeted individuals, and/or to jailbroken phones.
iPhone listening privacy tips (2024)
If concerned about iPhone privacy, consider the tips below:
1. Shut off the mic for Siri and for individual applications.
To switch off your iPhone’s microphone for Siri, go to Settings > Siri & Search. Then toggle off the following:
Listen for ‘Hey Siri’
Press side button for Siri
Allow Siri when locked
To review permissions and turn off the mic for individual applications, navigate to Settings and then click on individual apps. If you don’t want the mic for that app to remain on, simply toggle the switch.
2. Consider use of a VPN, which will make your device less vulnerable to threats by providing an encrypted, private connection. Do your research and find a reputable VPN provider. Avoid VPN providers who sell your contact information to advertisers. Carefully read through a VPN provider’s privacy policy ahead of agreeing to use their service.
3. Opt for a comprehensive solution like ZoneAlarm mobile security, which uses enterprise-grade technology to protect individuals’ phones and tablets from all kinds of cyber threats.
Related resources
Zero-click iMessage exploits hit iPhones – Read story
The CISO’s Guide to Mobile Device Security – Get eBook
Top mobile security threats and how to prevent them – Learn more
#2024#advertisements#advertising#Algorithms#amp#app#app store#apple#applications#apps#Article#Business#business model#CISO#compliance#comprehensive#cyber#cyber security#Cyber Threats#cybersecurity#data#data privacy#developers#eavesdropping#enterprise#exploits#generations#green#hacking#hearing
2 notes
·
View notes
Text
The Future of Finance: How Fintech Is Winning the Cybersecurity Race

In the cyber age, the financial world has been reshaped by fintech's relentless innovation. Mobile banking apps grant us access to our financial lives at our fingertips, and online investment platforms have revolutionised wealth management. Yet, beneath this veneer of convenience and accessibility lies an ominous spectre — the looming threat of cyberattacks on the financial sector. The number of cyberattacks is expected to increase by 50% in 2023. The global fintech market is expected to reach $324 billion by 2028, growing at a CAGR of 25.2% from 2023 to 2028. This growth of the fintech market makes it even more prone to cyber-attacks. To prevent this there are certain measures and innovations let's find out more about them
Cybersecurity Measures in Fintech
To mitigate the ever-present threat of cyberattacks, fintech companies employ a multifaceted approach to cybersecurity problems and solutions. Here are some key measures:
1. Encryption
Encrypting data at rest and in transit is fundamental to protecting sensitive information. Strong encryption algorithms ensure that even if a hacker gains access to data, it remains unreadable without the decryption keys.
2. Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of verification (e.g., passwords, fingerprints, or security tokens) before gaining access to their accounts.
3. Continuous Monitoring
Fintech companies employ advanced monitoring systems that constantly assess network traffic for suspicious activities. This allows for real-time threat detection and rapid response.
4. Penetration Testing
Regular penetration testing, performed by ethical hackers, helps identify vulnerabilities in systems and applications before malicious actors can exploit them.
5. Employee Training
Human error is a significant factor in cybersecurity breaches. Companies invest in cybersecurity training programs to educate employees about best practices and the risks associated with cyber threats.
6. Incident Response Plans
Having a well-defined incident response plan in place ensures that, in the event of a breach, the company can respond swiftly and effectively to mitigate the damage.
Emerging Technologies in Fintech Cybersecurity
As cyber threats continue to evolve, so do cybersecurity technologies in fintech. Here are some emerging technologies that are making a significant impact:
1. Artificial Intelligence (AI)
AI and machine learning algorithms are used to analyse vast amounts of data and identify patterns indicative of cyber threats. This allows for proactive threat detection and quicker response times.
2. Blockchain
Blockchain technology is employed to enhance the security and transparency of financial transactions. It ensures that transaction records are immutable and cannot be altered by malicious actors.
3. Biometrics
Fintech companies are increasingly adopting biometric authentication methods, such as facial recognition and fingerprint scanning, to provide a higher level of security than traditional passwords.
4. Quantum-Safe Encryption
With the advent of quantum computing, which poses a threat to current encryption methods, fintech companies are exploring quantum-safe encryption techniques to future-proof their security measures.
Conclusion
In the realm of fintech, where trust and security are paramount, the importance of cybersecurity cannot be overstated. Fintech companies must remain vigilant, employing a combination of advanced digital transformation solutions, employee training, and robust incident response plans to protect sensitive financial data from cyber threats. As the industry continues to evolve, staying one step ahead of cybercriminals will be an ongoing challenge, but one that fintech firms must embrace to ensure their continued success and the safety of their customers' financial well-being.
3 notes
·
View notes
Photo
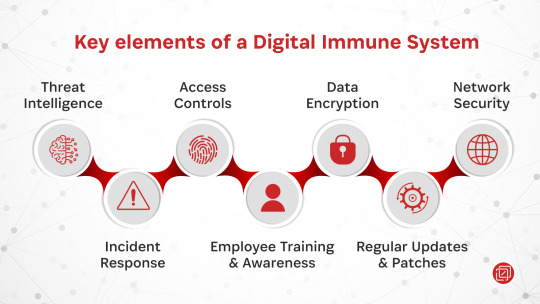
Don't let cyber threats take you down - fortify your digital assets with a Digital Immune System! 🔒🛡️
Discover the key elements, including threat intelligence, data encryption, and network security, that keep your data safe and secure.
#digital immune system#key elements#cyber threats#digital#intelligence#data encryption#network security#data#security
3 notes
·
View notes
Text
Strategies to Protect Cyber Infrastructure - Mr. Mandar Kulkarni, National Security Officer, Microsoft
India’s digital economy is booming—but so are cyber threats. How can businesses stay ahead of evolving attacks?
CT Cyber Charcha 2025 featured an insightful keynote by Mr. Mandar Kulkarni, National Security Officer at Microsoft, on the evolving cyber threat and strategies to protect your cyber infrastructure that every business needs to hear. As enterprises embrace digital transformation, new risks emerge—demanding smarter security strategies.
Key takeaways from his session:
AI-powered cyber-attacks are here—how can you defend against them?
Zero Trust Architecture—why traditional security models are failing
The #1 mistake companies make—ignoring Multi-Factor Authentication (MFA)
Human-targeted cybercrimes—how “digital arrests” and social engineering are on the rise
The shift from “best-of-breed” tools to integrated security platforms
Learn how AI, Zero Trust, and proactive security can protect your business in today’s digital world.
Don’t miss these expert insights. Watch the full session on YouTube: https://youtu.be/Dr3Aq01CI_o?si=8L8nuogBVc-3lAsv
About CT Cyber Charcha CT Cyber Charcha is a premier cybersecurity conference held on February 7, 2025, at FITT, IIT Delhi. The theme of the 1st edition was "Defusing the Mid-Market Time Bomb," focusing on the unique cybersecurity challenges faced by mid-market businesses. The event was hybrid, allowing participants to join either in person or online. Supported by IIT Delhi and ISACA, the event brought together industry leaders, professionals, and academia to discuss the latest threats, challenges, and solutions in cybersecurity. The conference featured expert keynotes, panel discussions, and networking opportunities, providing valuable insights for organizations to enhance their cybersecurity posture. For more information about the CT Cyber Charcha event, visit: https://tinyurl.com/cybercharchact
#CT Cyber Charcha#Channel technologies#Cybersecurity#CybersecurityConference#Cybersecurity Event#IIT Delhi#ISACA#Cyber Threats#CT
1 note
·
View note
Text
Insider Cyber Threats: How HR Can Safeguard Company Data
Insider cyber threats are an increasing concern for organizations worldwide. These threats are carried out by individuals who have authorized access to sensitive data, such as employees, contractors, or business partners. HR plays a vital role in safeguarding against these risks by implementing comprehensive strategies to protect organizational assets. This article explores how HR can proactively address insider cyber threats and maintain a secure and resilient workforce.
What Are Insider Cyber Threats?
Insider cyber threats occur when individuals within an organization exploit their authorized access to harm the company. This can involve stealing sensitive information, sabotaging systems, or accidentally exposing data. Unlike external cyberattacks, insiders already have the trust and access needed to cause significant damage, making these threats harder to detect.
Key HR Strategies for Safeguarding Against Insider Threats
HR has a critical role in preventing insider threats through the implementation of robust policies and practices:
Employee Vetting: Conduct thorough background checks to screen for potential risks during the hiring process.
Access Management: Control access to sensitive information based on job roles, minimizing exposure to unnecessary data.
Cybersecurity Training: Educate employees on the importance of data security and how to recognize phishing attempts and other malicious activities.
Clear Security Policies: Ensure employees are aware of the consequences of unethical behavior and the organization's cybersecurity policies.
Building a Culture of Security Awareness
A proactive approach to preventing insider threats starts with fostering a culture of security awareness. HR can ensure that employees at all levels understand their responsibility to protect company data. This includes offering regular training programs, awareness campaigns, and providing employees with the tools they need to stay vigilant against cybersecurity risks.
Collaboration Between HR and IT for Enhanced Protection
HR and IT teams should work closely together to protect the organization from insider threats. HR can manage the implementation of policies and employee behavior, while IT can provide the technical infrastructure and tools needed to monitor and prevent threats. Joint efforts such as regular audits, cybersecurity assessments, and implementing monitoring tools are essential to detecting and mitigating insider risks.
Monitoring and Responding to Insider Threats
Ongoing monitoring of employee access and behavior is key to identifying potential insider threats before they escalate. HR, in collaboration with IT, can establish systems to track access patterns, detect anomalies, and trigger alerts when necessary. It's important to have a clear response plan in place, which includes an investigation process and steps for addressing identified threats.
For More Info: https://hrtechcube.com/hr-can-safeguard-against-insider-cyber-threats/
Conclusion
HR plays a vital role in protecting organizations from insider cyber threats by implementing preventive measures, fostering a culture of security awareness, and working closely with IT teams. Through strategic planning, ongoing monitoring, and employee engagement, HR can help safeguard sensitive data and ensure a secure organizational environment.
0 notes
Text
Cyber Resilience Market Size and Revenue Forecast: Where is the Industry Headed?

The Cyber Resilience Market has emerged as a critical area of investment for businesses and governments worldwide. With an increasing number of cyber threats targeting organizations across industries, companies are shifting from traditional cybersecurity measures to comprehensive cyber resilience strategies. This market is rapidly expanding as organizations seek solutions that not only prevent cyberattacks but also ensure quick recovery and business continuity in case of an incident.
Understanding the Cyber Resilience Market
Unlike traditional cybersecurity, which primarily focuses on defense mechanisms, the cyber resilience market is centered on ensuring that organizations can continue their operations despite cyber incidents. This proactive approach involves threat detection, data backup, disaster recovery, and incident response strategies.
The global cyber resilience market is projected to grow significantly in the coming years, driven by the rising frequency of cyberattacks, increasing regulatory requirements, and the integration of advanced technologies like artificial intelligence (AI) and machine learning (ML) into security solutions.
Download PDF Brochure: https://www.marketsandmarkets.com/pdfdownloadNew.asp?id=136441705
Key Growth Drivers of the Cyber Resilience Market
The cyber resilience market is expanding due to multiple factors, including the escalating sophistication of cyber threats, rapid digital transformation, and increased regulatory compliance requirements.
Rising Cybersecurity Threats
Organizations worldwide are facing an unprecedented surge in cyberattacks, including ransomware, phishing, and data breaches. The increasing complexity of these threats has necessitated a shift toward comprehensive cyber resilience market solutions that offer real-time threat detection and response.
Regulatory Compliance and Data Protection Laws
Governments and regulatory bodies are imposing stringent data protection laws, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). These regulations require businesses to adopt robust cyber resilience market solutions to protect sensitive data and ensure compliance.
Digital Transformation and Cloud Adoption
With the growing adoption of cloud computing, digital transformation initiatives, and remote work environments, organizations are seeking cyber resilience market solutions that offer seamless integration with cloud infrastructure. This has accelerated the demand for cloud-based security solutions and disaster recovery services.
Advancements in AI and Machine Learning
The integration of AI and ML has revolutionized the cyber resilience market by enabling predictive analytics, automated threat detection, and real-time incident response. AI-driven security solutions analyze large volumes of data to identify anomalies and potential threats before they escalate.
Challenges in the Cyber Resilience Market
Despite its rapid growth, the cyber resilience market faces several challenges that could hinder widespread adoption.
High Implementation Costs
Implementing comprehensive cyber resilience market solutions can be costly, especially for small and medium-sized enterprises (SMEs). The expenses associated with advanced security tools, AI-driven analytics, and cloud-based infrastructure may pose a financial barrier.
Shortage of Skilled Cybersecurity Professionals
The cyber resilience market requires a highly skilled workforce to develop, manage, and maintain security solutions. However, the global shortage of cybersecurity professionals has made it challenging for organizations to build resilient cyber defense teams.
Complexity of Integration
Many businesses operate legacy IT infrastructure that is not easily compatible with modern cyber resilience market solutions. Integrating new security frameworks with existing systems can be complex, requiring significant time and resources.
Opportunities in the Cyber Resilience Market
Despite these challenges, several key opportunities are driving growth in the cyber resilience market.
Cloud-Based Cyber Resilience Solutions
Cloud-based security solutions are gaining popularity due to their scalability, cost-effectiveness, and ease of integration. Organizations are increasingly adopting cloud-based disaster recovery and data backup solutions to enhance their cyber resilience.
AI-Powered Security Solutions
AI and machine learning are playing a transformative role in the cyber resilience market by enabling automated threat detection, predictive analytics, and adaptive security responses. Businesses are leveraging AI-driven security tools to strengthen their cyber defenses.
Increased Focus on Business Continuity Planning
Companies are recognizing the importance of business continuity planning as part of their cyber resilience market strategy. Organizations are investing in solutions that ensure minimal disruption in the event of a cyberattack or system failure.
SME Adoption of Cyber Resilience Solutions
Previously, large enterprises dominated the cyber resilience market, but SMEs are now realizing the importance of protecting their digital assets. The availability of affordable and scalable security solutions is encouraging SMEs to invest in cyber resilience strategies.
Market Ecosystem and Key Players
The cyber resilience market consists of key stakeholders, including cybersecurity solution providers, system integrators, managed security service providers (MSSPs), and end-users across various industries. Major players in the cyber resilience market include:
IBM Corporation
Cisco Systems, Inc.
Palo Alto Networks, Inc.
Fortinet, Inc.
Trend Micro Inc.
Check Point Software Technologies Ltd.
Barracuda Networks
Acronis
Zerto
Veeam Software
These companies are investing in cutting-edge technologies to enhance cyber resilience and provide organizations with robust security solutions.
Recent Developments in the Cyber Resilience Market
AI and ML Integration in Security Solutions
Several companies are integrating AI and ML into their cyber resilience market offerings to improve real-time threat detection, response, and automation. These advancements are making security solutions more efficient and proactive.
Growth of Cloud-Based Cyber Resilience Services
Organizations are shifting towards cloud-based security solutions that offer seamless disaster recovery, data protection, and automated backup services. Cloud adoption is significantly influencing the growth of the cyber resilience market.
Strategic Partnerships and Acquisitions
Key players in the cyber resilience market are forming strategic alliances and acquiring innovative cybersecurity firms to expand their product portfolios. For instance, Cisco’s recent acquisition of a cyber resilience company has strengthened its disaster recovery capabilities.
Regional Outlook of the Cyber Resilience Market
The cyber resilience market is growing across various regions, with North America, Europe, and Asia-Pacific leading the adoption of advanced security solutions.
North America
North America dominates the cyber resilience market due to its high concentration of technology companies, stringent regulatory frameworks, and significant investments in cybersecurity infrastructure.
Europe
European countries are focusing on GDPR compliance and cybersecurity regulations, driving the demand for advanced cyber resilience market solutions.
Asia-Pacific
The Asia-Pacific region is experiencing rapid digital transformation, increasing cyber threats, and a growing need for resilient security solutions, making it a key market for cyber resilience technologies.
Ask for Sample Report: https://www.marketsandmarkets.com/requestsampleNew.asp?id=136441705
The Future of the Cyber Resilience Market
The cyber resilience market is becoming an integral part of modern business operations, ensuring that organizations can withstand and recover from cyber threats. As cyberattacks continue to evolve, businesses must prioritize resilience strategies to protect their digital assets and maintain operational continuity.
With advancements in AI, cloud security, and regulatory compliance, the cyber resilience market is set to grow exponentially in the coming years. Organizations that invest in proactive security measures will be better equipped to handle the ever-evolving cyber threat landscape, securing their place in the digital economy.
#cyber resilience market#cybersecurity solutions#ai-driven security#cloud resilience#business continuity#data protection#cyber threats#cyber resilience strategy
0 notes
Text
Here's Why I Urge You to Have a Strong Cybersecurity Framework Tailored to Your Environment
This case study highlights the crucial intersection of cybersecurity and reliable internet access, especially in underserved regions. #Broadbandnetworker #HigherEducation #RuralConnectivity #SatelliteInternet #NISTFramework #DataBreach #OnlineLearning
I once worked with a small university in a rural region where Internet connectivity was a major challenge. Faculty members often relied on personal Wi-Fi hotspots, and students accessed online learning materials through shared public networks at cafés and libraries. One professor struggled with unstable connections during virtual lectures, leading him to use multiple unsecured devices to stay…
0 notes
Text
Understanding and Mitigating Cybersecurity Threats

In today's hyper-connected world, cybersecurity threats are constantly evolving, posing significant risks to individuals, businesses, and even critical infrastructure. From sophisticated ransomware attacks to data breaches that expose sensitive information, the cybersecurity landscape is becoming increasingly complex.
Common Cybersecurity Threats:
Malware: This encompasses a wide range of malicious software, including viruses, worms, Trojans, ransomware, and spyware. Malware can infect devices, steal data, disrupt operations, and even hold systems hostage for ransom.
Phishing: Social engineering attacks that trick users into revealing sensitive information, such as login credentials, by masquerading as legitimate entities.
Ransomware: A type of malware that encrypts a victim's files and demands a ransom payment for decryption.
Denial-of-Service (DoS) Attacks: Overwhelm a target system or network with traffic, making it unavailable to legitimate users.
Data Breaches: Unauthorized access to sensitive data, often resulting in the exposure of personal information, financial data, or intellectual property.
Insider Threats: Malicious or unintentional actions by employees or other insiders, such as accidental data leaks or deliberate sabotage.
Supply Chain Attacks: Targeting vulnerabilities in software or hardware supply chains to compromise downstream systems and users.
Solutions to Mitigate Cybersecurity Threats:
Strong Passwords and Multi-Factor Authentication (MFA): Implement strong, unique passwords for all accounts and enable MFA for enhanced security.
Regular Software Updates: Keep operating systems, applications, and antivirus software updated with the latest security patches.
Employee Training: Educate employees about cybersecurity threats, such as phishing scams and social engineering tactics.
Data Encryption: Encrypt sensitive data both in transit and at rest to protect it from unauthorized access.
Intrusion Detection and Prevention Systems (IDPS): Implement IDPS to monitor network traffic for malicious activity and block suspicious connections.
Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration tests to identify and address vulnerabilities.
Incident Response Plan: Develop and implement an incident response plan to effectively handle security breaches and minimize damage.
Embrace Cybersecurity Best Practices: Implement robust cybersecurity best practices across all aspects of your organization, including data management, access control, and device security.
To gain a deeper understanding of cybersecurity concepts, best practices, and emerging threats, consider exploring programs like Xaltius Academy's Cybersecurity course. This comprehensive program can provide you with the knowledge and skills necessary to navigate the evolving cybersecurity landscape and build a successful career in this critical field.
0 notes
Link
National security isn't just about military defense anymore; it’s evolved to tackle a range of issues from cyber threats to climate change. Once seen as a simplistic concept, today it spans economic stability and food security, requiring a comprehensive strategy that involves government, international cooperation, and citizen engagement.
As our global landscape shifts, understanding these complexities is key for all of us. We need to stay informed and ready to discuss vital security challenges that impact our lives directly. Building a secure future means being proactive and collaborative.
Want to dive deeper into investment strategies amidst all this nuance? Sign Up to the free newsletter here www.investmentrarities.com.
#national security#cyber threats#climate change#economic stability#food security#global issues#government strategy#international cooperation#citizen engagement#trade security#defense policy#public safety#investment strategies#security challenges#sustainability#collaborative solutions#informed citizens#global cooperation#future planning
0 notes
Text
Protecting Yourself from Cyber Stalking Threats
With the rapid advancement of technology, it has completely changed the way we connect, share, and communicate in this digital age. But with this advancement comes the increase in cyber stalking, defined as the use of the internet or other electronic means to stalk or harass an individual, a serious issue that affects millions worldwide. It can lead to severe emotional, psychological, and even physical harm to the victims, making it crucial to raise awareness about the dangers and preventative measures.
This article provides an in-depth look into cyber stalking, highlighting its threats, legal implications, and preventive measures. Through understanding these dangers, individuals can better protect themselves from becoming victims of cyber stalking.

The Rising Threat of Cyber Stalking
Cyber stalking is a pervasive threat that often starts innocuously but can escalate rapidly, affecting individuals in various aspects of their lives. The growth of social media platforms, online communities, and messaging apps has increased the exposure of personal information, making individuals vulnerable to exploitation. Unlike traditional stalking, which occurs in physical spaces, cyber stalking can happen remotely, and it can affect people regardless of their location.
Cyber stalkers use a variety of methods to harass their victims, such as sending threatening messages, posting private information online, or engaging in defamation campaigns. The anonymity of the internet often emboldens stalkers, as they can hide behind fake profiles, and victims may not always know who is behind the attacks. This sense of anonymity and the widespread access to personal data make cyber stalking a growing concern for individuals, families, and businesses alike.
How Cyber Stalking Works
Cyber stalkers can engage in several practices to monitor, intimidate, or harm their victims. Among the most common practices of cyber stalking includes:
Social Media Harassment: A very common portal for cyber stalking is social media. The abuser may be creating a different profile to harass the victim through impersonation, or following excessively. They could also post any defamatory comments or even private information just to harm one's reputation and invade their personal space.
Email and Instant Messaging Threats: Stalkers can send harassing, threatening, or intimidating emails, messages, or even make phone calls. These threats may be aimed at instilling fear in the victim, and often, the messages contain explicit language or images designed to intimidate.
Identity Theft and Data Breaches: In some cases, cyber stalkers may use information that they stole through data breaches or other methods to impersonate their victims or continue manipulating their lives. For example, cyber stalkers might access private accounts, steal financial information, or engage in identity fraud.
With the proliferation of smart phones and other devices, stalking may be possible through spyware or GPS tracking apps to trace the victim's movements and activities. These spyware and tracking apps enable stalking to trace the real-time location, conversations, and other personal data.
Online Defamation: Cyber stalkers can publish false information or defamatory content about their victims online to tarnish their reputations. This can cause them emotional distress and potentially harm their social or professional life.
Impact of Cyber Stalking
The psychological and emotional impact of cyber stalking is indeed deep. Most victims of cyber stalking are likely to feel anxiety, fear, and helplessness. Such stalking can lead to depression, insomnia, and, in extreme cases, suicidal thoughts. The sense of violation from the inability to escape harassment at home makes victims feel unsafe in their own abode.
In addition to the emotional impact, there is the financial loss and reputational damage to one's profession. Such victims may face missed chances at employment, strained relationships, and extreme stress that comes with the continuous harassment. Cyber stalking has long-lasting effects that can even affect an individual's sense of trust in digital spaces.
Legal Framework and Cyber Stalking
There have been various legislations by several countries regarding cyber stalking and its related crimes. For instance, in the United States, some of the enactments are Violence Against Women Act (VAWA) and the Cyberstalking Law. While these enactments provide a victim with a legal recourse for his or her own protection, they are sometimes enforced and implemented irregularly. Further, the enforcement of the said enactments in all jurisdictions may not be explicit.
Legal action may be taken in cases where the personal information of a victim is being used for malicious purposes through privacy laws, harassment laws, and anti-cyberbullying regulations. Victims are advised to report such incidents of cyber stalking to the law enforcement agencies that can assist in gathering evidence and pursuing legal action against perpetrators.
It is worth noting that building a case against cyber stalkers often proves to be difficult because the anonymity of the Internet does not lend itself well to follow identification, and in some respects, the laws are not developed well enough to grapple with the overall issue of cyber stalking. For this reason, prevention is still the best medicine in dealing with cyber stalking.
Prevention of Cyber Stalking: Proactive Measures
The best way to handle cyber stalking is by avoiding it in the first place. Here are several ways in which one can keep oneself safe:
Online Privacy Settings: Many online services and social media platforms provide privacy settings through which one can control what other people view about oneself. Control of access to personal information and being aware of what one posts online minimizes the chances of falling prey to a cyber stalker.
Use Strong Passwords and Two-Factor Authentication: Securing online accounts with strong, unique passwords and enabling two-factor authentication (2FA) can prevent cyber stalkers from gaining unauthorized access to personal accounts.
Be Careful with Personal Information: Do not over-post personal details on the internet. This includes not sharing your full name, address, phone number, or any other sensitive information that may be used by a stalker.
Report Suspicious Activity: If you see unusual activity online, like unwanted messages, fake accounts, or threatening content, report it right away to the administrators of the platform and, if needed, to the law enforcement agencies.
Seek Legal Protection: If you feel threatened, you may want to pursue legal protection like a restraining order or cyber harassment lawsuit. Most states and countries have laws in place to protect victims of cyber stalking.
Take Control of Your Digital Footprint: Conduct regular audits of your online presence and remove outdated or unnecessary information. Monitor search engine results for your name to ensure your information is not being used maliciously.
Conclusion: Empowering Yourself to Stay Safe Online
Cyber stalking poses a significant danger to the future of online security in a significantly interconnected world. Understanding the characteristics of cyber stalking, the types of potential results, and techniques used by the stalkers makes it possible to take steps and protect oneself in advance. If it is upgrading privacy settings or using safe passwords, one always has the legal right to prosecute the stalkers and ensure security.
A cyber security course will be beneficial for those seeking further knowledge and better security practices in protecting themselves against the ever-growing threats of the digital world. Being well-informed and watchful, individuals can prevent cyber stalking and ensure their digital lives are free from malicious actors.
0 notes
Text
Cel mai mare atac DDoS din istorie: 5.6 Tbps – Escaladarea amenințărilor cibernetice în 2024
Pe 29 octombrie 2024, a fost înregistrat cel mai mare atac DDoS (Distributed Denial of Service) din istorie, atingând un volum impresionant de 5.6 Tbps. Lansat de o variantă a infamului botnet Mirai, atacul a vizat un furnizor de servicii Internet (ISP) din Asia de Est și a durat doar 80 de secunde. Acest incident marchează un nou prag în evoluția atacurilor cibernetice, subliniind complexitatea…
#2024 cybersecurity#5.6 Tbps#atac DDoS#atacuri cibernetice#automated defense#bam#botnet Mirai#Cloudflare#Cloudflare defense#cyber attack prevention#cyber defense#cyber resilience#cyber threats#cybersecurity trends#DDoS mitigation#DDoS record#DDoS statistics#diagnoza#Internet of Things#Internet security#IoT#IoT vulnerabilities#largest DDoS attack#Mirai botnet#network security#protecție automatizată#roman#securitate cibernetică#securitate IT#UDP flood
0 notes
Text
#SMS verification#SMS verification code#two-factor authentication#OTP#online security#cyber threats#user authentication#secure login#SMS security#digital interactions
0 notes
Text
Masa Depan AI dalam Keamanan Siber Bisnis
Perkembangan teknologi kecerdasan buatan (AI) telah membawa perubahan besar dalam berbagai sektor, termasuk keamanan siber. Dalam dunia bisnis yang semakin digital, ancaman keamanan siber menjadi salah satu tantangan terbesar. Serangan siber tidak hanya menyebabkan kerugian finansial tetapi juga merusak reputasi perusahaan. Di sinilah AI memainkan peran penting. Teknologi ini menawarkan solusi…
#AI#AI and machine learning#AI for businesses#AI in cybersecurity#AI innovation#AI-driven security#business security#business technology#cyber threats#cybersecurity#cybersecurity solutions#cybersecurity trends#data protection#digital transformation#ethical AI#future of AI#network security#online safety#predictive analytics#risk management
0 notes