#Compliance Checks
Explore tagged Tumblr posts
Text

At FineX Outsourcing we have clear liability with giving wide VAT Return HMRC relationship to ensure your business remains clear with all cost rules. Our party of experts is learned in the intricacies of VAT rules and HMRC essentials, raising the cycle smooth and crushing free for you. Our affiliations coordinate careful appraisals to ensure that each trade is tended to unequivocally, keeping the bet of messes up, and titanic locale to adhere to HMRC deadlines, avoiding any late trains or interest charges.
#VAT Return#HMRC#FineX Outsourcing#Tax Compliance#VAT Services#Business Tax#Accurate Calculations#Timely Submissions#Record Keeping#VAT Consultation#Tax Advice#Compliance Checks#Cost Effective Solutions#Professional Tax Services#Business Growth#Tax Experts#VAT Returns for Businesses#Outsourced Tax Services#Financial Accuracy#Tax Regulation Compliance#HMRC Deadlines#Tax Record Management#VAT Audit Preparation#VAT Law Expertise#VAT Filing Assistance#Tax Efficiency
0 notes
Text
Home Office Sponsor Licence Compliance Visits: Strategies for Success
For UK companies holding a Sponsor Licence, the prospect of a Home Office compliance visit can be a source of unease, especially when unprepared. In this article, our business immigration solicitors provide insights into handling these visits effectively. Our leading London Immigration Law Firm can prepare you via pre and post-licence mock compliance audits, including mock interviews with key…

View On WordPress
#Best Immigration Solicitors London#Business Immigraiton#BUSINESS IMMIGRATION NEWS#Business Immigration Solicitors#Compliance#Compliance Check#Compliance Checks#David J Foster & Co#David J Foster & Co Solicitor#DJF Solicitors#High Net Worth Immigration#Home Office#Home Office Checking Service#Home Office Compliance#Home Office Compliance Visit#Immigration Policy#key personnel#Lexvisa#London Immigration Solicitors#Migrant Workers#mock audit#mock compliance#Mock Compliance Audit#post-licence#pre-licence#Sponsor Duties#Sponsor Licence#Sponsor Licence Compliance Visits#Sponsor Licence holder#Sponsor Management System
0 notes
Text
Boosting cybersecurity: Siemens launches new all-in-one security testing suite for industrial networks
🔒 Navigating the complexities of industrial #cybersecurity just got easier. Introducing the #SINECSecurityInspector by @Siemens, the all-in-one solution for safeguarding your IT/OT network. Discover seamless security testing made efficient. #SIEX
SINEC Security Inspector: Offering a single user interface for a software framework combining different cybersecurity tools. Includes market-tested solutions for asset detection and identification, compliance checks, malware scans and vulnerability checks. Originally developed by and used for Siemens only, now available for any industrial environment. With the evolving convergence of IT and OT…

View On WordPress
#asset detection#compliance checks#cybersecurity#digital transformation#industrial networks#IT/OT convergence#malware scans#manufacturing cybersecurity#network security#security testing suite#Siemens#SINEC Security Inspector#Tenable#vulnerability checks
0 notes
Text
bell atthebell's spiderbit fics masterpost
in chronological order of when i posted them & grouped by canon compliance (i.e. how feasible it would be within canon/lacking in significant plot or characteristic changes). asterisks next to personal favorites/recs.
Canon-Compliant Works
*not quite but we're almost there - early spiderbit, post-bobby's death but pre-regret. fluff & minor angst. Complete, twoshot.
promise me you'll try - spiderbit talk about the egg disappearance and taking care of themselves. Complete, oneshot.
so bad all my bones shake - spiderbit host a halloween party! Complete, oneshot.
*won't you lover chase me down - purgatory spiderbit :D Complete, twoshot.
true love waits - another spiderbit reunion :D Complete, oneshot.
tucked away from the world with you - spiderbit building fluff + cuddling! Complete, oneshot.
*bright as the morning - roier does yoga, cellbit is very normal about it. someone had to write it! Complete, oneshot.
if it's your hands - roier cooks cellbit feijoada while he's sick. Complete, oneshot.
*won't you lover chase me down - purgatory spiderbit! Complete, twoshot. [chapter 2 was for this event]
back to the hedgerows - roier doesn't mind cellbit's murder spree one bit-- in fact, he's very fond of his husband covered in blood. Complete, oneshot.
put to mind of all that i wanna be - spiderbit dancing after their wedding. Complete, oneshot.
the reason is you - spiderbit wedding!! Complete, oneshot.
so much of the living - spiderbit family fluff (w/richas and pepito). Complete, oneshot.
some bright morning comes - spiderbit vow renewal!!! Complete, oneshot.
***push forward push back - spiderbit sparring :DD Complete, oneshot.
nothing more i could ask for - spiderbit family fluff (w/richas and pepito). Complete, oneshot.
it's about spending time together - spiderbit date night! Complete, oneshot.
***i wanna feel your lips on mine - spiderbit weedfic!!!! so much making out :D Complete, oneshot.
*i'll say it a thousand times and every time it gets sweeter - spiderbit being the most obnoxious couple on the island frfr. Complete, oneshot.
every cut another kiss - purgatory spiderbit again! Complete, oneshot.
every sunrise begins a new day - spiderbit family fluff (w/richas and pepito)! the kids find a gift for pai cellbit :D Complete, oneshot
say it in the seconds - roier writes a list of all the reasons he loves cellbit a pros and cons list of being married to cellbit. Complete, oneshot.
Canon-Divergent Works/AUs
Spiderbit Reunions (yes that's its own subclass):
*like a lighthouse always waiting - roier waits for good news after purgatory. luckily, he finds what he's looking for. spiderbit reunion, minor angst, roier-centric, happy ending. Complete, oneshot.
**outpace the dawn - post-reset spiderbit reunion (i am desperate okay) + fluff, with some minor angst. Complete, oneshot.
just to have you in my arms again - spiderbit reunion (once again) + wearing each others' clothes. Complete, oneshot.
**cutting the strings - post-reset cellbit saving roier and getting rid of doied (aka my idea of where that arc would have gone). Complete, oneshot. my pride and joy!
Hybrid/Creature AUs:
*now you surround me - vampire roier & human cellbit who very much enjoys providing for his husband's needs. Complete, twoshot [chapter 1 was for this event].
*flew like a moth to you - hybrids + cuddling spiderbit fluff <3 Complete, oneshot.
*now you surround me - vampire roier & human cellbit who very much enjoys providing for his husband's needs. Complete, twoshot [chapter 2 was for this event].
your creature in the night - spiderbit fae au, featuring fae!cellbit! Complete, oneshot.
***fall on me like night - cat shifter cellbit + spiderbit fluff + cuddling! Complete, oneshot.
Other AUs:
solo pienso en tenerte - obsessedduo <33333 Complete, oneshot. will eventually get a sequel!
#bell.txt#qsmp#spiderbit#qsmp fic#bell fics masterpost#technically the reunions are like canon compliant but getting into the weeds#about canon compliance vs canon divergence is a whole other thing#anyway i THINK this is all of them??#the archive is having some issues rn so i cant fully check
88 notes
·
View notes
Text
Regulations: A New Trucker's Guide to Staying Compliant and Safe
This is the third in our series of blog posts for new truckers. This information is very basic, but even if you have been a trucker for most of your life, this information is still valid. Today, let’s talk about something crucial: regulations. These are the rules of the road that go beyond just stopping at red lights and obeying speed limits. In the trucking world, there’s a whole layer of…
#business#compliance tips trucking#DOT check preparation#DOT compliance trucking#DOT inspection tips#DOT regulations trucking#ELD for truckers#ELD requirements trucking#ELD tips truckers#Freight#freight industry#Freight Revenue Consultants#hours of service limits#hours of service rules#hours of service tracking#logistics#new driver regulations#new trucker compliance#new trucker rules#owner-operator regulations#small carriers#Transportation#truck driver compliance tips#truck driver hours#trucker legal requirements#Trucking#trucking compliance guide#trucking HOS compliance#trucking industry#trucking regulations guide
2 notes
·
View notes
Text
Judge whose opinion I'm reviewing today has a major Thing about sprinkling Latin phrases around but then not citing to any cases within this jurisdiction to support his application of those concepts.
"Applying the canon of statutory interpretation expressio unius est exclusio alterius, the court finds . . . ." Okay boss but that canon doesn't exist in a vacuum and you should really cite a New Jersey case that says we apply it. We DO, but...this is a judicial opinion that's going to be published. You need to cite actual sources not nebulous concepts.
EDIT: I have just realized that, even worse, "expressio unius est exclusio alterius" isn't even the most appropriate phrase for what he's trying to say.
#kidk says stuff#real lawblr#technically for the type of review i'm supposed to be doing i'm not technically required to correct this kind of thing#i'm supposed to be checking the cites he DOES have for compliance with the blue book#and making sure the opinion conforms with our manual on style#like i'm not supposed to go haring off after citations for this dude#but i...HNNNNNGH i feel like i should at least put in a comment to say 'there should be a citation to a case here'#but just because I FEEL that way doesn't mean i'm supposed/allowed to do that ;____;#work
19 notes
·
View notes
Text
i am a legal/comms person, why are you messaging me about tech/banking stuff, i Do Not Know which banks you need to connect to the cashier on this domain, i can give you like... all the documents for the company holding the domain. Do you need that??? I have their license i can sure show you that
#same with the compliance department asking me to ask the company for compliance stuff#YOU are the compliance department not ME#the company pays us (YOU) to do the compliance checks for them#me in the team leads gc: WHO asked for this and why is your guy messaging ME for it. you know im the documents guy right.#im the talking to the clients people guy#the client gave us (YOU) the company to manage it as you see fit they do not know shit or fuck about our bank options and so do i
3 notes
·
View notes
Text
Liking things is so fun cause when you see something related you get a burst of joy. I was once so happy I felt like I was going to buzz out of my skin and it was because I saw a VERY OSHA complaint spiral staircase. There really was no other way to put stairs there. It HAD to be a spiral. I get giddy thinking about it.
#like yknow all the typical crush symptoms? I had that from seeing that staircase#don’t get me started on checking the OSHA compliance of various structures WITHIN other stuff I like#like in the Batman 2022 movie they wear harnesses!!! on the catwalk!!!#I get an extra burst of joy from eating food because of Dungeon Meshi#I get an extra burst of joy from making well rounded meals and imagining the stat blocks#bonemeal says silly stuff#I also usually get annoyed by spiral staircases cause I look at them and think#‘this could’ve been a normal staircase’#cause I have this irrational fear of spiral staircases#but that one was like ‘wow that was necessary’
6 notes
·
View notes
Text
VAT Return HMRC
Keeping the complexities of VAT returns can be a gigantic endeavor for any business. At FineX Outsourcing we have clear liability with giving wide VAT Return HMRC relationship to ensure your business remains clear with all cost rules. Our party of experts is learned in the intricacies of VAT rules and HMRC essentials, raising the cycle smooth and crushing free for you. Our affiliations coordinate careful appraisals to ensure that each trade is tended to unequivocally, keeping the bet of messes up, and titanic locale to adhere to HMRC deadlines, avoiding any late trains or interest charges. We stay aware of standard need records of all VAT related stories to help your return and for any future assessments, give conversation and asking on VAT related proposing help you with seeking after informed decisions, and direct consistence actually looks at by persistently taking a gander at your records to ensure pushing consistence with changing VAT rules. FineX Outsourcing offers limit, re-attempted approaches changed by meet the specific necessities of your business, sharp advantages that save you time and resources, and progressing forward through quality in conveying watchful VAT bring relationship back. From careful assessments to lucky locale, FineX Outsourcing manages each not unequivocally clear sharpness concerning, you to focus in on encouraging your business. Trust us to manage your VAT get back with the exactness and confusing flourishing that FineX Outsourcing is known for. Contact us today to look further into how we can assist with your VAT bring needs back.
#VAT Return#HMRC#FineX Outsourcing#Tax Compliance#VAT Services#Business Tax#Accurate Calculations#Timely Submissions#Record Keeping#VAT Consultation#Tax Advice#Compliance Checks#Cost Effective Solutions#Professional Tax Services#Business Growth#Tax Experts#VAT Returns for Businesses#Outsourced Tax Services#Financial Accuracy#Tax Regulation Compliance#HMRC Deadlines#Tax Record Management#VAT Audit Preparation#VAT Law Expertise#VAT Filing Assistance#Tax Efficiency
0 notes
Text
4 ways to advance your global security operations center - CyberTalk
New Post has been published on https://thedigitalinsider.com/4-ways-to-advance-your-global-security-operations-center-cybertalk/
4 ways to advance your global security operations center - CyberTalk


EXECUTIVE SUMMARY:
If your organization maintains a Global Security Operations Center (GSOC), ensure that you’re not heavily reliant on legacy systems and processes. In this article, find out about how to strategically advance your operations, enabling you to effectively prevent threats and drive more sustainable business outcomes.
What is a global security operations center?
In the early days of computing, a Security Operations Center (SOC) functioned as a physical ‘command center’ for security analysts. SOCs were comprised of rooms where staff sat shoulder-to-shoulder, looking at screens showing details from dozens of different security tools.
Large organizations with multiple Security Operations Centers (SOCs) began to consolidate them into Regional Security Operations Centers (RSOC) or a Global Security Operations Center, leading to faster remediation, reduced risk and a stronger cyber security posture overall.
In terms of function, a global security operations center monitors security, addresses threats before they become disruptive issues, responds to incidents, and liaise with stakeholders.
What are the benefits of a global security operations center?
A global security operations center allows an organization to contend with diverse security threats at-scale. Specific benefits include continuous monitoring, centralized visibility, increased efficiency and reduced costs. A global security operations center can also oversee and coordinate regional SOCs, network operations centers (NOCs) and operational teams.
What makes a good global security operations center?
For any global security operations center, access to timely and relevant threat intelligence is critical. GSOC staff need to remain updated on emerging cyber and physical security threats, as to stay ahead of potential risks.
Highly trained staff who can collaborate effectively with all stakeholders are also invaluable assets for a global security operations center.
Top-tier GSOCs have built-in redundancies of all kinds; from communication to data backups.
All GSOCs need to ensure that their organization adheres to industry regulations and compliance standards.
4 ways to advance your global security operations center
1. Ensure that the cyber security strategy aligns with business objectives. GSOCs need to know what the business aims to achieve, and must understand the corresponding threats and vulnerabilities that could hamper progress. Risk assessments should include both cyber security and business stakeholders, who can assist with the identification of resources that require protection.
Security policies and standards should also meet customer expectations. To gain insight around this, cyber security leaders may wish to join business planning meetings. Attendance can also assist with awareness around any upcoming business changes and implementation of appropriate, corresponding security measures.
2. Global security operations centers should shift towards the zero trust model. Zero trust is designed to reduce cyber security risk by eliminating implicit trust within an organization’s IT infrastructure. It states that a user should only have access and permissions required to fulfill their role.
Implementation of zero trust can be tough, especially if an organization has numerous interconnected and distributed systems. Organizations can simplify zero trust implementation through vendor-based solutions.
Tools like Quantum SASE Private Access allow teams to quickly connect users, sites, clouds and resources with a zero trust network access policy. In under an hour, security teams can apply least privilege to any enterprise resource.
Security gateways also enable organizations to create network segmentation. With detailed visibility into users, groups, applications, machines and connection types, gateways allow security professionals to easily set and enforce a ‘least privileged’ access policy.
3. Advance your global security operations center by mapping to industry standards and detection frameworks. Explore the MITRE ATT&CK framework. Standards like NIST and ISO27001 can also assist with identifying and reconciling gaps in an organization’s existing security systems.
4. Consider deploying a tool like Horizon SOC, which allows organizations to utilize the exact same tools that are used by Check Point Security Research, a leading provider of cyber threat intelligence globally.
Horizon SOC offers 99.9% precision across network, cloud, endpoint, mobile and IoT. Easily deployed as a unified cloud-based platform, it has powerful AI-based features designed to increase security operations efficiency.
Further thoughts
Strategic updates to global security operations centers not only enhance cyber security, they also enrich overarching business resilience – an increasingly common point of discussion among C-level stakeholders and the board.
By implementing the suggestions outlined above, organizations will maximize their opportunities for business longevity and continued business success.
Related resources
#ai#amp#applications#Article#assets#awareness#backups#board#Business#business resilience#c-level#Check Point#Cloud#clouds#collaborate#command#communication#compliance#computing#consolidation#continuous#cyber#cyber security#cyber security strategy#cyber threat#data#details#detection#efficiency#endpoint
2 notes
·
View notes
Text
hmm. I think I have to read batgirl (2008) now
#river's dc phase 2.0: now with more canon compliance#i've been. scrolling through cass/rose posts. and i keep seeing panels from it#but first i should check how long it is
1 note
·
View note
Text
o7


#art#notes#profile pic#tumblr#funny#if sad check this tag#default#june 2024#1115#malicious compliance#tumblr culture#fave genre
302K notes
·
View notes
Text
I cant believe this tweet is how I find out
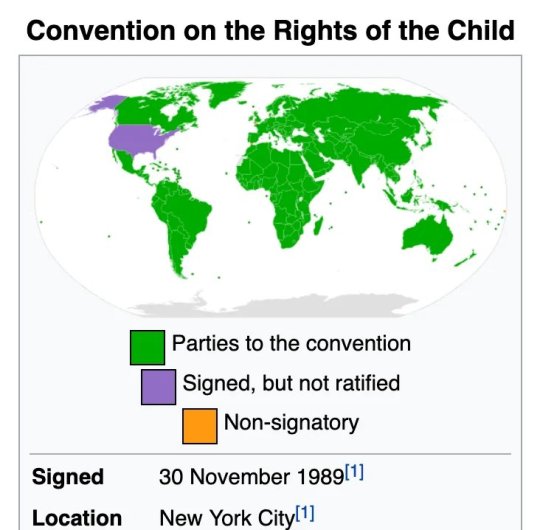
Edit: Now that we're talking about it, look. There is all the countries ratification dates, along with considerations for their laws.
And you can check the convention here.
Edit 2: For those in the US who want to check their state's laws compliance to the convention, there is this site.
Edit 3: The map source btw. Its from wikipedia.
Thank you people in the notes for the info and image desc.
70K notes
·
View notes
Note
What do you think are good qualities to have for a librarian?
Caring about people and being comfortable with anarchy
Anything else can be taught but those are, I feel, the two key personality traits that you need if you’re
1. Going to be a good librarian
2. Going to last as a librarian
#librarians are MUCH less ‘quiet bookworm types that want everything organized and orderly and quiet’#and much more ‘your local chaotic good cryptid-adjacent who will break laws if the laws are bad’#and are also MASTERS of malicious compliance like if there’s a way to do it WITHIN the rules they will find it#you would be surprised how much chaos tolerance you need to work in a library#some people think oh I’d love to work in a nice quiet library around books: forget that#you are a preschool teacher you’re an IT specialist you help people file taxes there WILL be a sword fight at some point in your career#some days would be like ‘I have to pause from teaching these kids how to juggle so I can catch a bat loose in the stacks’#and then pivot to helping 93 year old Ethel make her first email account#and then go fix a plumbing leak on the second floor#all the while finding checking out checking in and shelving books#you will be paid a quarter of what your worth and have to fight the town gov and board of directors over everything#but it’s SO rewarding
0 notes
Text

AML Checks for Legal Industry | NameScan
0 notes
Text
Lmao at mark zucchini saying the antis were right and they had to comply and delete all the content the us government told them 🤓
#LMFAOOOOO#now we’re right? 😂😂😂😂😂😂😂😂😂#I’m so glad I never took that shit and that my family listened to everything I told them#every warning vent sess and any explanation as to why they were bio weapons#for instance I’ve posted ‘anti’ shit on here and it hasn’t been deleted#maybe the rules are changing indeed#no more fast checking? we’ll see#oh and by the way I don’t feel sorry for the celebs who took it and died or promoted it and are now sick#or promoted it and are flopping in their career#here’s my big fuck you 🩷����#I’ve worked for instagram and they make u sign a compliance doc to say you won’t reveal anything but they fucking suck#meta in general#for some things I lit don’t shut my mouth and tell everyone to fuck off#this was one of those moments#didn’t give a f#mfs are out of touch#al final la gente se cansa y abandona las redes sociales - q es lo q está pasando !!!#tengo amigas que ni ig tienen ya 😂 whatsapp y da gracias
1K notes
·
View notes