#Cloud Performance
Explore tagged Tumblr posts
Text
Securing the Cloud Computing: Unveiling the Power of Network Security and Intrusion Detection

Cloud computing has revolutionized the way businesses and individuals utilize and manage data and applications. However, with its numerous benefits come inherent security risks that need to be addressed. Understanding the dynamics of cloud computing and implementing robust security measures are crucial in safeguarding cloud environments against potential threats and attacks.
Understanding Cloud Computing and Its Security Risks
Cloud computing, in simple terms, refers to the delivery of computing services—including servers, storage, databases, networking, software, and more—over the internet. This paradigm shift in accessing and storing data brings with it security challenges that need to be navigated effectively to ensure the confidentiality, integrity, and availability of sensitive information. Networks in cloud environments are susceptible to intrusion and unauthorized access, prompting the need for dedicated network intrusion detection systems to reinforce overall security.
Overview of Cloud Computing
Cloud computing provides unparalleled flexibility and scalability, enabling users to harness computing resources as per their dynamic needs. From public cloud services offered by providers like Amazon Web Services, Microsoft Azure, and Google Cloud Platform to private cloud infrastructures maintained by organizations, the diversity of cloud options necessitates comprehensive security strategies.
Security Challenges in Cloud Computing
The decentralized nature of cloud computing introduces unique security concerns, including data breaches, account hijacking, insecure application interfaces, and insider threats. Effective security measures must be implemented to mitigate these risks and ensure the protection of sensitive assets against both internal and external threats.
Importance of Network Intrusion Detection in Cloud Environment
Network intrusion detection plays a pivotal role in fortifying cloud security by actively monitoring and analyzing network traffic to detect and respond to potential threats. Intrusion detection methods and techniques tailored specifically for cloud environments are indispensable in safeguarding cloud resources from unauthorized access and data breaches.
Types of Intrusion Detection Systems for Cloud Security
When it comes to intrusion detection in cloud environments, various systems and techniques come into play, each with its unique strengths and applications.
Host-based vs Network-based Intrusion Detection Systems
Host-based intrusion detection systems focus on monitoring and analyzing the internals of a computing system, such as its operating system and application software, to detect signs of intrusion. On the other hand, network-based intrusion detection systems scrutinize network traffic for suspicious patterns, making them essential for securing cloud networks against external threats.
Behavior-based vs Signature-based Intrusion Detection Techniques
Behavior-based intrusion detection techniques prioritize anomaly detection by establishing a baseline of normal activity and flagging any deviations from the established patterns. In contrast, signature-based detection involves matching known patterns of malicious activity, making it vital for identifying and warding off known security threats in cloud computing environments.
Applying Intrusion Detection System in Cloud Network
Implementing intrusion detection systems in a cloud network requires a comprehensive understanding of the underlying architecture, resource allocation, and security protocols. Tailored intrusion detection and prevention systems, in conjunction with robust security policies, are essential for bolstering the resilience of cloud networks against potential security attacks.
Common Threats and Attacks in Cloud Computing
The evolving landscape of cloud computing is accompanied by a spectrum of security threats and attacks that necessitate proactive security measures and intrusion detection frameworks.
Understanding Security Threats in Cloud Computing
Various threats, such as data breaches, distributed denial of service (DDoS) attacks, and unauthorized access, pose significant challenges to the security of cloud infrastructure and services. Ensuring the integrity and confidentiality of data amidst these threats demands a holistic approach to security and vigilant intrusion detection mechanisms.
Challenges of Intrusion Detection in Cloud Environment
The dynamic nature of cloud environments, combined with the scale and complexity of cloud resources, presents challenges for intrusion detection systems to accurately and efficiently identify and respond to security incidents. Addressing these challenges is crucial in strengthening the defense mechanism of cloud systems against potential intrusions.
Security Measures for Preventing Cloud Security Attacks
Robust security measures, including encryption, access control, and continuous monitoring, are imperative for mitigating cloud security attacks. Intrusion detection and prevention systems, when integrated with security protocols and frameworks, serve as a crucial line of defense against a wide array of security threats prevalent in cloud environments.
Security Measures and Solutions for Cloud Infrastructure
Securing the foundational infrastructure of cloud computing is paramount in safeguarding the data and applications residing within the cloud.
Importance of Data Security in Cloud Computing
Data, being the lifeblood of cloud computing, requires stringent security measures to protect its confidentiality, integrity, and availability. Implementing robust data encryption and access controls is pivotal to ensuring data security in cloud environments.
Implementing Intrusion Detection and Prevention System in Private Cloud
In private cloud environments, where the cloud infrastructure is dedicated to a single organization, implementing intrusion detection and prevention systems is critical in fortifying the security posture of the cloud resources. Tailoring security solutions to the specific needs of the private cloud environment offers a layered defense against potential intrusions and security breaches.
Ensuring Privacy and Compliance in Cloud Security
Adhering to privacy regulations and industry-specific compliance standards is vital for maintaining the integrity and trust within cloud environments. Strong security protocols, coupled with adherence to data privacy and compliance requirements, are imperative for safeguarding sensitive information stored and transacted within cloud networks.
Enhancing Detection Accuracy and Performance in Cloud Security
Challenges of Achieving High Detection Accuracy in Cloud Environment
With the scale and complexity of cloud resources, achieving high detection accuracy in identifying potential intrusions and security threats poses a formidable challenge. Overcoming this challenge requires the utilization of advanced detection methods and techniques in tandem with performance optimization strategies.
Optimizing Intrusion Detection Systems for Cloud Service Models
Refining intrusion detection systems to align with specific cloud service models, whether it be infrastructure as a service (IaaS), platform as a service (PaaS), or software as a service (SaaS), is crucial in enhancing the efficacy of security measures tailored for diverse cloud environments.
Future Trends and Innovations in Cloud Security and Intrusion Detection
As cloud computing continues to evolve, innovative security frameworks, machine learning-based anomaly detection, and advancements in intrusion prevention systems are poised to shape the future of cloud security. Embracing these trends and innovations is essential in fortifying the security and privacy of cloud resources against emerging security threats and vulnerabilities.
Book a Free Consultation with Cloudlink
0 notes
Text
Know About Cloud Computing Services - SecureTech

Introduction
In today's digital age, cloud computing has become an integral part of the business world. Companies are increasingly turning towards cloud computing services to enhance their operations and increase productivity. San Antonio, with its burgeoning technology sector, has become a hub for cloud computing services. One such company, SecureTech, is offering top-notch cloud computing services in San Antonio. In this article, we will explore the benefits of cloud computing and why SecureTech is the go-to company for businesses in San Antonio.
What is Cloud Computing?
Before delving into the benefits of cloud computing, it is essential to understand what it is. Cloud computing refers to the practice of using a network of remote servers hosted on the internet to store, manage, and process data. In simpler terms, it means using the internet to access software and applications that are not installed on your computer or device.
Benefits of Cloud Computing
There are numerous benefits of using cloud computing services, some of which are:
1. Cost-Effective
One of the primary benefits of cloud computing is its cost-effectiveness. It eliminates the need to invest in expensive hardware and software as everything is hosted on the cloud provider's servers.
2. Scalability
Cloud computing offers unparalleled scalability as businesses can easily scale up or down their operations depending on their requirements. This makes it an ideal solution for businesses with fluctuating workloads.
3. Accessibility
Cloud computing services allow businesses to access their data and applications from anywhere with an internet connection. This means that employees can work from anywhere, which enhances productivity and flexibility.
4. Security
Cloud computing services offer robust security measures to protect data and applications from unauthorized access, theft, or loss. Providers like SecureTech offer top-notch security measures to ensure that their clients' data is always secure.
Visit - https://www.getsecuretech.com/cloud-technologies/
#Cloud migration#Cloud storage#Cloud security#Virtualization#Private cloud#Hybrid cloud#Public cloud#Cloud backup#Disaster recovery#Cloud computing#Multi-cloud#Cloud-based#monitoring#Cloud deployment#Cloud scalability#Cloud performance
0 notes
Text
Why Azure Cloud Skills are Crucial in the Digital Age?
Azure Cloud skills are important in today's digital age as businesses move towards cloud technology. Azure, Microsoft's cloud computing platform, offers a range of cloud services, including compute, storage, networking, and analytics that businesses can use to modernize their infrastructure. , improve security and reduce costs.
Having Azure cloud skills can open doors for IT professionals and developers looking to pursue a career in cloud technology. Demand for Azure professionals is growing rapidly as more and more businesses adopt cloud technology. Azure offers a variety of certifications including Azure Administrator, Azure Developer, Azure Solution Architect, and more. that individuals can pursue to demonstrate expertise and advance their careers. Azure also provides a comprehensive set of tools and services for managing and monitoring cloud infrastructure, such as Azure Monitor, Azure Advisor, and Azure Security Center, that can help businesses improve performance, their overall reliability and security in the cloud.
In summary, Azure cloud skills are essential in today's digital age, as they provide IT professionals and developers with the knowledge and expertise to manage and monitor the facility. efficient cloud infrastructure. With the growing demand for Azure professionals, acquiring Azure certifications can provide significant benefits and open up exciting career opportunities. So start building your Azure cloud skills today to stay ahead of the competitive tech industry!
#Azure Cloud Skills#Cloud Computing#Cloud Technology#Microsoft Azure#Cloud Infrastructure#Cloud Certifications#IT Professionals#Azure Professionals#Cloud Performance#Cloud Security#Career Opportunities
0 notes
Text
Haloocom Business Cloud Optimizer Solution

Cloud Optimization is the process of reducing waste and improving performance by choosing and deploying the right cloud resources for specific functions. It involves matching workloads with cloud resources based on their changing requirements over time, while considering factors such as cost and performance. By optimizing cloud infrastructure, companies can benefit from lower costs, increased productivity, and better visibility into their cloud usage. Key benefits of cloud optimization include reducing redundant cloud costs, boosting cloud utilization, improving productivity, and increasing cloud visibility. The process can be complex, so companies may benefit from working with a cloud optimization provider who can examine their environment and provide ongoing optimization support. In conclusion, cloud optimization helps businesses achieve better results from their cloud investment while cutting down on waste.
#Cloud Optimization#Cloud Performance#Cloud Service Provider#DevOps#Cloud Visibility#Cloud Costs#Cloud Utilization#Productivity#Cloud Migration#IT Investment#Cloud Management#Benefits#Cost-Conscious Decisions#Cloud Optimization Services#Engineers#Coding Time#Consumer Experiences#Competition#Time to Market#Haloocom#Cloud Journey#Best-Practice#Ongoing Optimization.
1 note
·
View note
Text

Sasha Waltz: Wolke (Cloud), 2002
1K notes
·
View notes
Text

who are you kidding? how could you doubt me? i've always delivered!
#sorry this fucker is too fun to draw actually i need a name for it#lyrics are from#clouds by nf#(which i saw him perform live a couple nights ago >:])#canine kin#hellhound kin#wolf kin#nonhuman art#eye strain#digital art#artists on tumblr#wolf art#therian art#kin art
359 notes
·
View notes
Note
Cloud Strife Appalachian accent . That's it that's the ask Nibelhiem is West Virginia.
CORRECT
#cloud 'let's mosey' strife#as much as i love cody christian's performance in ff7r i do have one little gripe. Where Is That Country Boy Twang#ffvii#cloud strife#asks
55 notes
·
View notes
Text

wizzy was down for maintenance so I drew my Young Wizard while I (impatiently) waited
#chickenscratch#w101#wizzy101#wizzy fandom#wizard101#the young wizard#Galathea (Eurydice)#I've reached lvl 97!!#my hc that the more magic a wizard uses the more it takes over their features physically. like the fire teachers hair or#those black eyes on malistaire. in this case my YW hair is a cloud and becomes light or stormy depending on her mood#i call her Galathea but you cannot choose that name in game so i go by Eurydice instead <//3#not that it matters considering none of the npcs call you by name anyway dskjafjd#the frankenbunnys name is Gigi. i love her shes great she heals me and freaks other players out lmao#dont remember any of the lore surrounding the frankenbunny so my idea is that Gigi is a botched nercomancy attempt by my YW#half stuffed animal. half actual hare#Galathea had a bad mental health episode early into arc 1 and Made herself a Friend#anyway don’t let diviners perform necromany you get THAT#i realise now the words i was looking for were ‘living taxidermy’
151 notes
·
View notes
Text
I just want to praise John Eric Bentley for delivering an absolute incredible performance in Rebirth. His fight with Dyne made me sob uncontrollably at 3 am. It was amazing. Thank you for being an outstanding VA.

#John Eric Bentley#barret wallace#final fantasy vii#ff7r#ff7#ff7 rebirth#VA#he deserves way more recognition and Barret deserves more damn respect in this house#shout-out for goat VA and goat character#Barret. Tifa and Cloud have the best performances in Rebirth. Period#I don't take any other opinions#they clear#that's golden trio for YOU
33 notes
·
View notes
Text
What if the show let dean grieve? What if they let him drink and rage and sob himself to death? What if they had him snap at Sam and push him and everyone else away? What if they let him show how heartbroken he was? How utterly destroyed? What if they let him scream and cry? What if they let him give up? What if they let him think that he had nothing left to live for? What if they let him die broken and alone in the dungeon where it took cas? What if they let him have peace when he was done? What if they let him in the empty? What if, at the end of their story, Dean and Cas don’t get a happily ever after and Sam goes crazy? What if it ended how all tragedies end? So many open ends, but no one to fill them. So many things to do, but no one to do them. Happy ending just inches away, but still just out of reach.
What if?
#spn#dean winchester#destiel#castiel#sam winchester#supernatural#ror yaps#i think about this a lot#in a perfect world#dean would go to the empty#no performative heaven#no fake clouds and sky#no toyotathon comercial#no “Cas helped”#just darkness#peace#sleep
34 notes
·
View notes
Text










Hush...Hush, Sweet Charlotte (1964)
"Miriam? He really... isn't here, is he? Just now, I thought I heard... sometimes at night, when I wake up, it seems as if he really is here. Don't turn on the light. It's not real when it's light. It's only real when it's dark - dark and still."
#hush...hush sweet charlotte#hush...hush‚ sweet charlotte#robert aldrich#1964#american cinema#lukas heller#henry farrell#bette davis#olivia de havilland#joseph cotten#agnes moorehead#cecil kellaway#victor buono#mary astor#wesley addy#william campbell#bruce dern#george kennedy#frank ferguson#frank de vol#Aldrich's follow up to Baby Jane reunited him with star Davis (and initially Crawford‚ until she left the project under a cloud; she can#just about be glimpsed in one of the long shots of cousin Miriam arriving at the house by taxi) and even provides a cameo for Baby Jane co#star Buono. the rest of his cast is also notably starry: de Havilland‚ Cotten‚ Moorehead‚ even a genuine cinematic legend like Astor not to#mention a pre fame Dern and Kennedy. sadly all that increased star power doesn't translate to a film even better than its predecessor#this is solid‚ a strong and sweaty gothic grotesquerie‚ but it's a little flabby and nowhere near as sharp or as honed as Baby Jane was#Davis often goes very large and brushes caricature more than once with her faded Southern belle but to give her her dues there are other#moments of true heartbreaking beauty in her performance. de Havilland is also very strong altho maybe tips her hat a little soon in#revealing the true personality lingering beneath the surface of her mysterious outsider. Aldrich is as strong as ever helming a killer#fantasy sequence... tbh the more i think about it the kinder my memory of this becomes. it has just one main flaw and that's that it isn't#Baby Jane. but then what is? Aldrich never quite hit those heights again (tho he did some p great work) and this is a commendable try
28 notes
·
View notes
Text

CLOUD SCISSORS
1964-1977
Instructions for the event edited by the artist Seven event cards in envelope, 7.5 x 9.2 cm. Part of: - "Water Yam" 1963, No. 0329E-2 - "Fluxyearbox 2" 1968, No. 0042S - "AQ 16" 1977, No. FXC0502
Bibl.: J.Hendricks, "Fluxus Codex", exhibition catalogue, Detroit-New York 1988, p.187; "George Brecht Events, Eine Heterospektive. A Heterospective", exhibition catalogue, Cologne 2005, p.316
#Cloud Scissors#1964-1977#Fluxus Codex#Fluxus#clouds#scissors#George Brecht#Performance#Event#George Brecht Events
17 notes
·
View notes
Text
Went to Afro Drag tonight and hhhh no words 10/10 the energy was soooo good, everyone was very nice and I danced with strangers and my God some nights you really remember why it is you get to live
#afro drag is a show put on by fierté montreal and its black canadian drag artists and wooowowowoowowow#every single one of them was so good#ive got no voice left#the drag king who performed to 2 lil nas X songs stole my heart#im so full of joy rn#seeing everyone so happy#dancing (possibly for the first time) in the open#without any shame or embarrassment#ok so. my brother called while i was writing those tags and my God. my God. my God.#love is a real emotion im allowed and able to feel and im so full of it so so full#if i was a cloud id rain id rain#im exploding i could die i love you i love you i love you#et je t'aime je t'aime je t'aime je t'aime
29 notes
·
View notes
Text
So, I watched Fed's Backyard Theatre's RTC production...

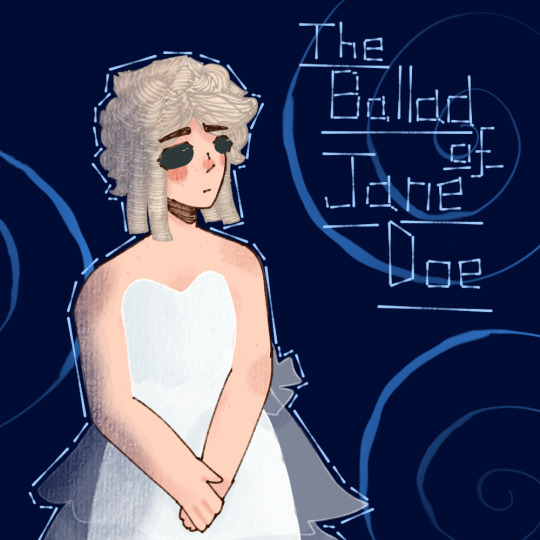
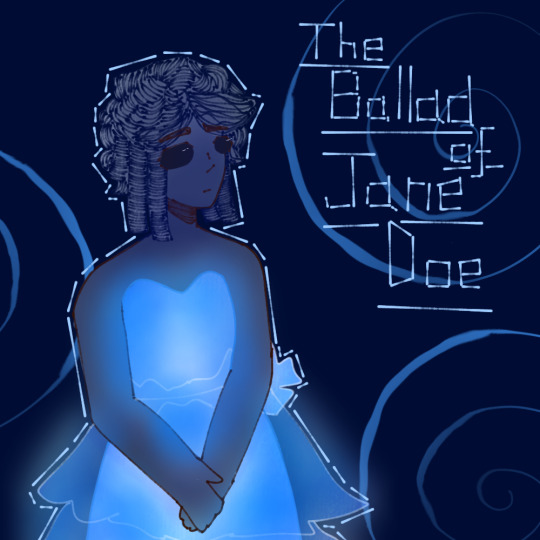
This is only the stuff I've drawn so far. I really want to draw Monique (the costume was 😙👌) and SABM Ricky, because that massive glowing cape was magnificent. I might also draw Ocean in her red waistcoat and Mischa being all gangster to do the full set.
#ride the cyclone#rtc#rtc musical#sugar cloud#constance blackwood#the ballad of jane doe#jane doe#penny lamb#fed's backyard theatre#fed's backyard theater#Ada Jordan#Yaira Spears#this cast was absolutely brilliant oml#the enthusiasm and vocal performances made the perfect blend of brilliant rtc-y goodness#i just loved it#rtc fanart#rtc constance#ride the cyclone constance#constance rtc#constance ride the cycone#ride the cyclone jane doe#rtc jane doe#jane doe rtc#jane doe ride the cyclone
113 notes
·
View notes
Text
I have personally never understood the mania surrounding Colin Firth in terms of attractiveness but I think he’s such a powerful and layered Darcy who does a lot of the heavy lifting of communicating Darcy’s internal world.
#kind of unfair that the mania exists because it clouds the quality of the performance!#which is so good#the wet shirt scene does not need to exist#the getting into the green jacket scene is incredibly powerful#and that’s the acting#(well and the costume design)#(love that he goes from wearing black to more greens and blues and grays)#pride and prejudice (1995)#if that version has a weakness it’s the script in that sometimes Andrew Davies was just being too tehehehe about it#also it can never be the novel but nothing can ever be the novel#anyway just chattering to myself but feel free to chime in
36 notes
·
View notes
Text








MAN SUANG (2023, THAILAND)
Thai Film Available on Netflix
#BEYOND#BE ON CLOUD#TWO LEAD STARS OF KINNPORSCHE#MILEAPO#THRILLER#HISTORICAL#PERFORMING ARTS#DANCE#THAI TRADITIONAL DANCE#My GIFS#MYGIFSET#MY-GIF-EDIT#BL-BAM-BEYOND FAMILY OF BLOGS#THOUGH THIS ISN'T BL IT IS INTERESTING
22 notes
·
View notes