#Bot detection
Explore tagged Tumblr posts
Text
The notion of the Turing test is that a computer would struggle to convince a human that it is human. Now we all need to struggle several times a day to convince computers that we are humans.
11 notes
·
View notes
Text
What Should Marketers Look for in a Bot Detection Tools?
In today’s digital marketing landscape, bots impacting your campaigns, website analytics, and overall performance is becoming an enormous issue with all the organizations running any kind of advertising campaign. To put a stop on the ad fraud that is caused by bots, having bot detection tools is vital. After all, how can you put a stop to bots if you can’t detect.
Unfortunately, many firms struggle to detect bot traffic, and the methods they employ are not all created equal. Choosing the right bot detection tool is essential for safeguarding your marketing efforts. Here’s a comprehensive guide to help you select the best tool for your needs.
What Is Invalid Traffic and How Does It Relate to Bots?
Bot fraud in digital advertising generally falls in the category of invalid traffic by the marketers no matter good or bad since the bots are not the target audience and cannot be converted into a protentional lead.
Types of Invalid Traffic:
General Invalid Traffic (GIVT) – It is one of the simplest bots that can be detected easily, and a lot of good bots traffic comes under GIVT as they are not meant to fool the bot detection tool. But some fraudsters may also deploy GIVT as they are easy to make and work against some of their targets.
Sophisticated Invalid Traffic (SIVT) – SIVT detection is the bots that one should look out for as these are more capable and are often designed to target to bypass cybersecurity and fraud prevention tools. For Example – sophisticated bots might imitate how a human would use a website so it would be difficult to identify between a human and bot. SIVT is common in ad fraud schemes.
Bot detection in USA, UAE, India, Saudi Arabia
Click here to read more: What should marketers look for in a Bot Detection Tool
#bot detection#bot detection tool#bot detection software#ad fraud#ad fraud detection tool#ad fraud software#ad fraud solution#ad fraud detection software#fraud detection software
0 notes
Text





Snow bots au anyone? :D
They're back together a year later because it's snowing again❄️
All right! For context: I imagine them hanging out every winter in some kind of resort (a resort that Blurr owns. Because his bar business has expanded that much over time.)
#maccadam#transformers#snow bots au#uh that’s a lot of characters. okay let’s go#left -> to right. top to bottom haha#Swerve#Rung#Tailgate#Rewind#chromedome#cdrw#jazz#prowl#jazzprowl#rodimus#rodimus prime#Wing#Drift#Blurr#Swindle#I originally wanted to add Brainstorm falling out of bus window and Perceptor catching him but my brain is shutting down I need to sleep ha#jazz and prowl switching their hats be like#Prowl: I sense something is wrong..where's my hat?? (looks around) (sees it on Jazz's head) Oh there it is. Cool.#five minutes later: wait. If my hat is there than what am I wearing right now???? error 404#world greatest detective ladies and gentlemen~
4K notes
·
View notes
Text
Kasada Introduces New Suite Of Attack Prediction Services: KasadaIQ

The innovative firm Kasada, which specializes in thwarting automated threats powered by humans, has announced KasadaIQ, a package of attack prediction services that go beyond traditional bot management. The first product in this package, KasadaIQ for Fraud, provides actionable indications based on large amounts of data from the Internet. Businesses looking for information on how bots target their digital channels and client data will find this service especially helpful. With its unmatched visibility into adversary communities and non-traditional data sources, KasadaIQ for Fraud distinguishes itself by offering a cutting-edge capacity to identify and validate risks prior to their manifestation.
Businesses face a serious and expensive threat from bot fraud, which may cost them money, effort, and reputational damage in addition to endangering their customers. The environment of eCommerce fraud is expanding globally, with predictions that it will top $48 billion this year. A startling 96% of IT professionals reported that they have lost money as a result of bot assaults in the previous year, according to Kasada's 2023 State of Bot Mitigation Report.
The founder and CEO of Kasada, Sam Crowther, highlighted the increasing sophistication of bots, pointing out that almost eighty percent of business executives find it harder and harder for their security solutions to identify bots. In spite of this, a lot of businesses continue to use antiquated technologies that develop slowly. According to Crowther, businesses can proactively defend against attackers with KasadaIQ for Fraud in conjunction with their current bot detection systems, giving them a competitive edge and avoiding bad press.
Read More - https://bit.ly/3G5EvbD
0 notes
Text
Defeating Airdrop Hunters in Web3 with the Power of AI
Airdrop campaigns have become an essential tool for promoting projects in the Web3 ecosystem. However, the rise of fraudulent behavior, particularly Sybil attacks, poses a significant challenge for Web3 projects. These attacks involve profit-seeking individuals creating multiple fake identities to exploit airdrops, leading to market crashes and undermining the project’s goals.
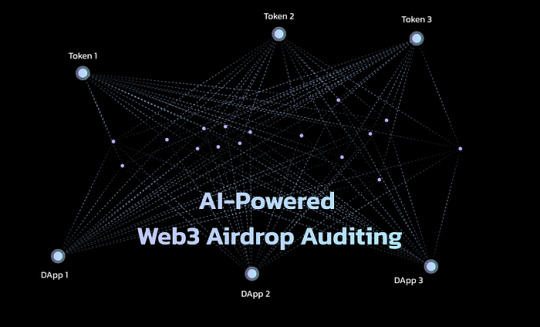
Understanding Sybil Attacks
Sybil attacks involve malicious actors creating numerous fake accounts to claim airdrop rewards multiple times, manipulating the system for their own gain. These actors create and control multiple accounts to obtain more tokens, thereby disrupting the intended purpose of airdrops.
Airdrop auditing plays a vital role in mitigating the risks associated with Sybil attacks and ensuring a fair distribution of rewards. It helps project teams protect the integrity of their projects, maintain the trust of their community, and prevent market manipulation caused by fraudulent behavior.
Leveraging AI for Airdrop Auditing
Traditional rule-based systems used for airdrop auditing have limitations in detecting sophisticated bot and Sybil patterns. These systems rely on predefined rules and struggle to adapt to evolving fraudulent tactics, making them less effective in identifying new and emerging fraudulent behaviors.
To overcome the limitations of rule-based systems, W3W offers an AI-powered solution for airdrop auditing. By utilizing advanced AI algorithms, W3W excels in detecting and preventing bot and Sybil behavior, ensuring a level playing field for airdrop participants.
Key Advantages of W3W’s AI Algorithm:
Comprehensive Detection: W3W’s AI algorithm excels in accurately identifying intricate patterns and anomalies in transaction behaviors, enabling the detection of bot and Sybil activity with a high level of precision.
Adaptive Learning: W3W’s AI algorithm evolves over time, learning from new bot tactics and adapting its detection capabilities to counter emerging threats.
Enhanced Explainability: W3W’s AI algorithm provides clear output on the reasons behind its detections, allowing project teams to openly engage with the community and explain why particular wallets are classified as bots.
Efficient Resource Allocation: By accurately identifying fraudulent behavior, project teams can optimize the distribution of airdrops, ensuring that genuine users receive the rewards they deserve.
W3W’s AI-powered solution has successfully identified various bot patterns in Web3 airdrop campaigns. Here are three examples:
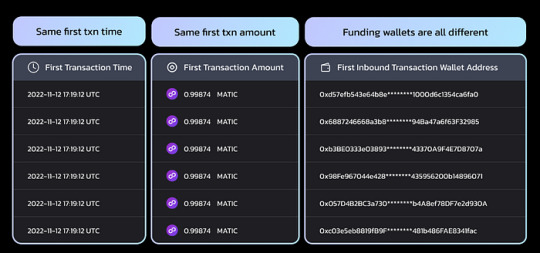
Pattern #1: Deceptive Funding Wallets
In this case, a group of 1000+ wallets in the same airdrop campaign exhibited suspicious behavior. They made identical fund transfers of the same amount at the same time, using different funding wallets to mask their actions. Among them, more than 500 wallets followed the exact same transaction sequences during a specific timeframe.
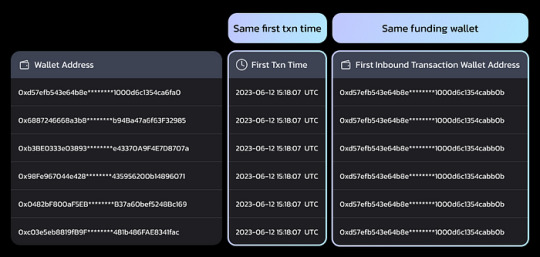
Pattern #2: Coordinated Bot Activity
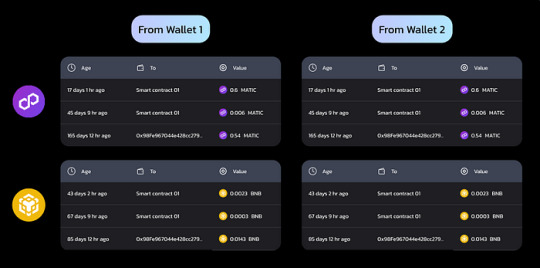
Pattern #3: Cross-Chain Bot Fraud
W3W uncovered a sophisticated form of bot fraud called Cross-Chain Bot Fraud. Multiple bots collaborated across different blockchain networks, executing synchronized operations to deceive and manipulate the system for illicit gains.
With the rise of Web3 and the increasing popularity of airdrops, prioritizing the auditing of these campaigns is crucial to uphold fairness, transparency, and community trust. By embracing AI-powered solutions like W3W, projects can effectively detect and prevent bot and Sybil behavior, ensuring the protection of airdrop assets and maximizing the impact of their marketing budgets. Together, we are creating a Web3 ecosystem that fosters genuine engagement and rewards real participants.
Interested in learning more about our solution? Contact us at [email protected] or book a demo to explore how W3W can help safeguard your airdrop campaigns and promote a fair and thriving Web3 ecosystem.
0 notes
Text
How to Spot Instagram Social Engineering Scams

View On WordPress
#Bot detection#Bots#Bots to inflate numbers#Browser hijackers#Clicks#Command and control server#Concert scams#Contest scams#Contests#Copyrights#Cyber awareness#Cyber safety tips#Cyber threats#Cybercrime#Cybersecurity#Cybersecurity best practices#Cybersecurity education#demographics#Digital threats#Direct email#Domain name verification#Domain names#Events#Fake accounts#Fake giveaways#Fake profiles#Fake publishing agents#followers#Fraudulent schemes#Impersonation prevention
1 note
·
View note
Text

spider nico (spider bot…. sometime i call him circuit too) ((he’s like what if spiderman sucked ass))
#my art#he is a tech nerd that will do work for villains and civilians and does not care#but he refuses to build gear or puter or bots for anyone but himself#his uncle ben moment was his sick mother trying to upload her mind to a computer upon death#it was his first thing he’d ever help build for another person#and it Did Not Work so he doesn’t make things for anyone anymore#he’s very useless and his spider sense only works to detect radio signals and electrical equipment etc#but no danger LOL#he also doesn’t have webs!#just long wires that he throws and prays#i like him a lot#spidersona#spider man: across the spider verse#oc#original character#sona#digital portrait#digital art#illustration#drawing#artists on tumblr
3K notes
·
View notes
Text





photocards and toploaders I made! I have no idea what to do with them though😭😭 I have to decorate toploaders for all the others except wavewave and megop I am very open to suggestions on what to do PLEASE
I THOUGHT I'D DECORATE TOPLOADERS FOR FUN SINCE I HAD SPARE RESIN BUT THEN SUDDENLY I SPENT 50 DOLLARS ON STICKERS AND NOW IM HOOKED AND IDK WHAT TO DO WITH THIS RAPIDLY AMASSING COLLECTION HELP
#toploader#toploader deco#transformers#transformers prime#tfp soundwave#soundwave#shockwave#tfp shockwave#tfp megatron#tfp optimus prime#optimus prime#megatron#star instructor master baek#OMG THERE'S A TAG FOR IT I'M SO HAPPY#manwha#manhwa#baek suryong#namgoong su#grimlock#tf earthspark#windblade#bumblebee#rafael esquivel#uramichi omota#life lessons with uramichi oniisan#graham burns#rescue bots#tobot galaxy detectives#sorry about all the tags😭😭
99 notes
·
View notes
Text

so my partner keeps getting spam bot messages on facebook, and they decided to entertain themself by responding in long noir detective monologues. i decided it needed an audio drama version.
i have no idea how to tag this. i'm dumping it into the tumblr ocean and it will swim with the currents, godspeed
#noir detective#shitpost#audio shitpost#spam bots#noir spam bot#i made this myself because i like making audio things secretly#the entire monologue was just off the cuff nonsense by my partner and i read it word for word lmao#original audio#though i put the credits for the royalty free song in the metadata comments#it's Once Upon A Road by Bladverk Band#shout out to epidemic sound which i still have an account with until the 24th so pls dont claim this i paid you for it i prommy
428 notes
·
View notes
Text
i need dan and phil to learn the full story behind their rpftourney win i NEED them to understand how hard we fought in the semifinals i neeeeeeed them to understand how serious tumblr voter fraud is
#dnp#dan and phil#phan#someone needs to tell them that i learned selenium to try to help#and it didn't work bc it turns out the tumblr signup page CAN detect some bots but like the thought was there#then someone explain to them that selenium is a python library for automating inputs to web browsers#uhhh and then probably that python is a programming language? just in case#lou is loud
56 notes
·
View notes
Text
Chase [RB] Themed Stimboard -`🚔´- with police cars, detective themes, and blue / red lights











🔎|🚔|🔍 🚔| ★ |🚔 🔎|🚔|🔍 ★: divider center gif made by me :3 again source: transformers rescue bots season 2 episode 17 my second favorite rescue bot !! or maybe hes tied for first ?? idk. im gonna make boards for the other two as well since ive already done half of the main team :D
#bensboards#stimboard#visual stim#stim gifs#gifs#gif#chase rescue bots#rescue bots#rescue bots chase#chase tfrb#tfrb#tfrb chase#transformers rescue bots#transformers#maccadam#police car#detective#detective stim#keyboard#keyboard stim#blue#blue stim#red#red stim#stim
78 notes
·
View notes
Note
In that whole detective AU I made out of your own AU what would the player's role after the hour of joy even be and how the toys survive the ones that got left behind of course considering though Doey's not there as well as the Medic is not there ? Would Poppy just give up?
How cooked are they considering they're not there?
I think the player would have a very similar roll in the game. Getting Doey out of there early (and Joseph, Scout, and Izzy) I think would have caused Dogday to survive. The Hoppy VHS take makes it sound to me like there were more supplies down in the prison at a certain point than in playcare, and with no one to take Poppy's place when she disappeared (which my theory is she ran to keep the protoype away from safe haven but then was captured and she's ashamed that it went so badly) I don't think he'd just leave the remaining toys to their own devices down there and we might see more toys down in safe haven but no one up in the playhouse.
They may be the same level of but slightly different cooked because for no reason backed by canon I feel like Dogday would be better at demanding answers from Poppy and shutting down her plans. Maybe more of the bigger body critters are able to survive because of this as well.
#Scouts the boogie bot Susan would have saved in this auau not medic#Susan Ayers#poppy playtime#doey the doughman#wasthatafanfic#love him till the day that you die#I can't decide if detective au would change Mommy long legs fate and how chapter 2 would play out#detectiveau
24 notes
·
View notes
Text
How Bot Detection Enhances Marketing Campaign Accuracy and Safeguards Ad Spends
Bots make up about a third of all web traffic, and shockingly, 65% of those bots are classified as “bad bots”. These malicious bots indiscriminately destroy marketing campaigns by inflating impressions and clicks; thus, they financially devastate marketing campaigns. So, ironically, although companies do not intend to, they spend a percentage of their ad budget on fraudulent traffic, making every campaign less effective than it could have been. Ad fraud is rising; therefore, the detection of invalid traffic across all digital campaigns has become necessary for businesses’ success in the digital space.
There is a need for a full-funnel ad fraud detection tool to provide omnichannel protection against general and sophisticated invalid traffic i.e. GIVT & SIVT. An additional brand safety layer of protection helps to boost campaign performance. To guarantee the success of digital marketing efforts, the traffic validation tools should provide coverage across app, web, OTT, and CTV ecosystems.
Why Is Bot Detection Important for Successful Marketing Campaigns?
Here’s why tracking and detecting bots in marketing campaigns are important-
Protection of Ad Spend
Bots generate fake clicks, impressions, and visits which means businesses are paying for fake user engagements instead of real ones. Often leads are also filled up by sophisticated bots bypassing OTPs and captchas. A huge portion of the budget spent on advertising goes to waste without proper detection of ad fraud.
Real / Effective Analytics
Bots taint the quality of the data collected from digital campaigns and yield wrong interpretations. In turn, this may lead to wrong business decision-making as well as inefficient use of resources. Businesses cannot rely on their marketing data unless the bots are detected and blacklisted.
Higher ROI
Based on the bot-cleansed, accurate metrics, businesses that deploy full-funnel ad traffic validation tools understand how their marketing campaigns are doing. This leads to a channel-wise analysis and therefore can operationally direct more budgets to the most effective channels, which means a higher ROI.
Brand Safety
Bad bots are often placed by publishers on content that is highly questionable and brand-unsafe. Good fraud detection tools not only end up finding sophisticated invalid traffic but also provide a layer of brand safety from bad inventory and unsafe ad placements.
Click here to read more: How Bot Detection Enhances Marketing Campaign Accuracy and Safeguards Ad Spends
0 notes
Text
okay okay large debate on if i should get my best mate into the smiths or queen
he's, like, super old-fashioned and all, and i want to get him into some newer stuff so we can both listen to music in our office
#dbda#dbd#dead boy detectives#dead bot detective agency#charles rowland#charles dead boy detectives#tv
74 notes
·
View notes
Text
by NobleDragon
Fic Prompt: I would love to see Edwin meeting Charles's father and/or mother, especially if they do not happen to know who Edwin is at the moment he meets them. How do they interact with him, talk to him, think of him, and how does that change when they find how he's spent the last 30 years with their son?
Mira Rowland dies with unfinished business.
Words: 1,708, Chapters: 1/1, Language: English
Fandoms: Dead Boy Detectives (TV)
Rating: Teen And Up Audiences
Warnings: No Archive Warnings Apply
Categories: Gen
Characters: Mary Rowland | Charles Rowland's Mother, Charles Rowland (DCU), Edwin Paine | Edwin Payne
Relationships: Charles Rowland & Mary Rowland | Charles Rowland's Mother, Edwin Paine | Edwin Payne & Charles Rowland, Mary Rowland | Charles Rowland's Mother & Edwin Paine | Edwin Payne
Additional Tags: Post-Canon, Character Death, Implied/Referenced Child Abuse, Mentioned Paul Rowland | Charles Rowland's Father, despite not being dead he still haunts the narrative, haunting the narrative, Mother-Son Relationship, Emotional Hurt/Comfort, Crying, Getting to Know Each Other, Platonic Relationships, Implied Relationships, POV Mary Rowland | Charles Rowland's Mother, Bad Parent Paul Rowland | Charles Rowland's Father, Digital Art
#dead boy detectives#dead boy detectives fanfiction#deadboydetectivesao3feed#gen fic#charles rowland#charles rowland's mother#edwin payne#rating: T#AW: No Archive Warnings Apply#manual post#(another case of the malfunctioning ao3 bot)
20 notes
·
View notes
Note
You don't have to respond you can just look at this
I want to sincerely apologize for publishing one of your bots without your permission. I recently learned that you didn't want your bots to be made public, and once I realized this, I made it private. I promise that when it was out, I credited you appropriately. Please forgive me; I didn't intend to make you uncomfortable.
It’s fine as you learn from it and in general just refrain from using A*I b0ts ,,
Public or private, I just see using these as a big boundary break and also feeding into sketchy A*Is not matter how fun it looks from the outside,,,
but again, you learnt from it and honestly that’s what matters most /gen /pos
#you’re doing good bud#I’m just a big AI hater lol#except for AI that’s used to make things *better* or *easier*#like in the science field w detecting things or an AI that makes a tricky task easier#generative AI is the real criminal here#and that includes chat bots#sorry for the ramble xhsjxjsj
28 notes
·
View notes