#lowercase & uppercase intentional
Explore tagged Tumblr posts
Text
that isn’t me. [a “self-aware” angel concept]
“Angel? Have you seen my jacket?”
it doesn’t take a genius to gather if it is or isn’t themselves when they look in the mirror. at least, at face value. nobody shares your face as much as it is your own.
you might have a twin or a sibling that looks like you. they aren’t you, though. they don’t have your blemishes or your teeth. not your hair or your eyebrows. none of those little details.
some people might wake up and look in the mirror and think ‘wow. i look so different today.’ and go about it.
i can’t. that isn’t me. that isn’t my face.
“Angel?”
he opens the door and i look away from their reflection.
“What was the question?” I smile bashfully. He gives me a faux annoyed look- one that feels like it should be gentle, but in some way there’s judgement there. Is that something they’ve come to terms with? Something I should find endearing?
“Have you seen my jacket?” He appears to repeat, his tone softer. I give a general scan of the room, their fingers playing with the sleeves of my shirt before I shake my head.
“No,” I reply, “I’m sorry. Maybe you left it at work?”
He pauses, giving me a look that holds what I could consider confusion. He’s leaning against the doorframe with crossed arms.
there’s a silence in the pause that i don’t like. what did i say that sounded wrong? what would this person say instead? how do you pretend to be other than yourself?
He then interrupts the discomforting silence.
“That’s definitely possible. I’ll look when I go in.”
I nod, thinking the conversation would end at that point, but it doesn’t. There’s only a short pause before he tilts his head to the side, his eyes softening.
my- or, their- heart is pounding.
“Hey. Are you alright?” He asks.
it’s at this point i realise i don’t actually know this man’s name, but it feels as though it’s on the tip of my tongue. i look back at him almost dumbfounded, looking over his face for an answer to a question i hadn’t asked.
“Yeah.” I lie through my teeth, “when’re you leaving?”
“Five minutes?” He responds, before insisting upon the previous question, “are you sure?”
then is when i realise.
“David,” I smile, “don’t worry. I have, like, a little headache. Not even that.”
David looks at me quietly. He doesn’t seem satisfied, but not because of my poor excuse. Instead, it’s as though he’s heard news he couldn’t hear.
“Okay,” he then says, practically a whisper- “rest up.”
He leaves the room and I blink a few times.
there’s an air of confusion to me. a man who calls me angel. david. a person who isn’t me. angel.
i look back at the mirror. it feels a bit clearer now. not a smudge. my hand reaches out and presses fingertips against the surface, leaving prints.
i pull away and whisper to myself words i don’t speak.
“You aren’t me.”
I then respond.
“Pretend to be so.”
#lowercase & uppercase intentional#redacted audio#less than 300-400 words#redacted asmr#redactedverse#redacted david#redacted angel#empyconcept#redacted fic#📼.txt#notes:#i love self aware concepts#this one plays with the idea that someone who isn’t angel knows they aren’t them#and may be the listener#purely because they know david and angel#but of course it’s also involving angel as a person#lowercase insinuates the listener as a person#uppercase insinuates the listener as a character#one in the same
94 notes
·
View notes
Text
Inside the Character's Mind: Part 6
CHILDHOOD. SLY AND KOUJAKU. THE AVOIDANT BEHAVIOR: part 3

As if all that wasn’t already enough, at the end of the Re:connect, this happens. Aoba thinks to himself that this is not what Koujaku wanted, as much as Sly wants to think that it is, that he’s in the right. As if what he has done has helped the Koujaku inside, the one who’s like him, the true Koujaku, to come out. As if they could be free inside that cell.
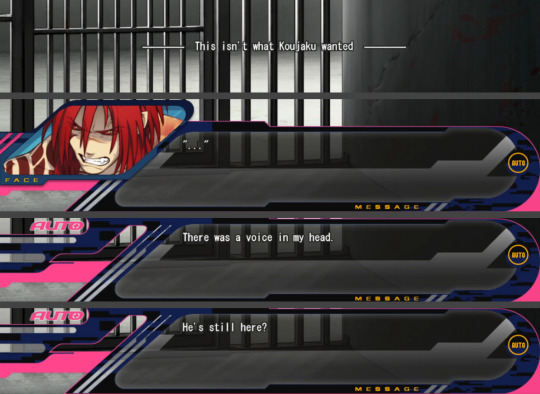
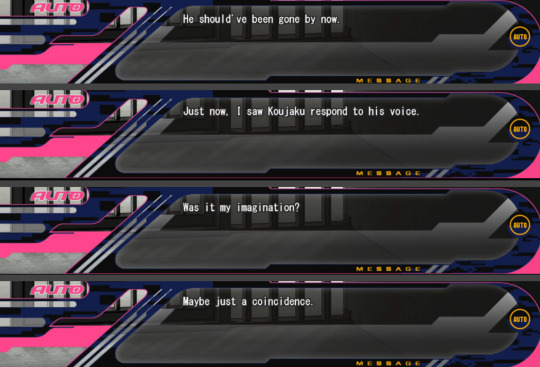

Koujaku reacts to Aoba’s thoughts. Sly thinks for a moment that it’s his imagination, but when Aoba repeats his thoughts, Koujaku says his name. Koujaku, who despite not having articulated a single word all this time, weeks, months, says his name as soon as Aoba “speaks”, that’s what I’m talking about when I mention their spiritual connection, that’s how strong it is. It happening after such a different sex scene, where neither of them can say no, nor show any kind of rejection, is just a reminder that they are both locked away, suffering, and that they will stay there watching this happen day after day until the day they die, not being able to see, or touch, or call each other’s names, or say “I love you” or anything they once wanted to say. They can only just watch each other wither away.
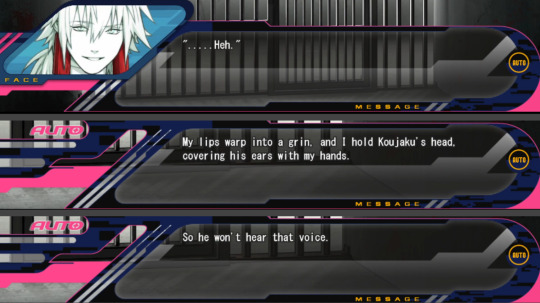
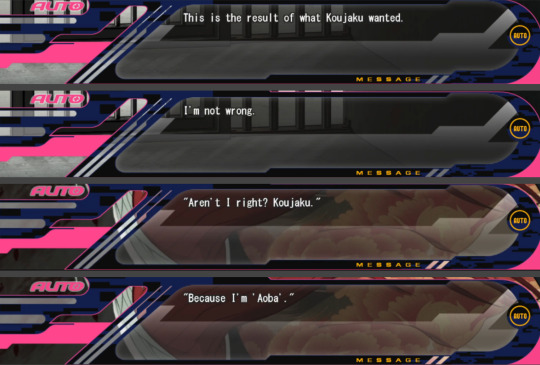
These thoughts of “This isn’t what Koujaku wanted” are very interesting because just like Sly thought, Koujaku really wanted Aoba to accept and love him. But the last thing he wants is having Aoba reciprocate him just because that’s what Koujaku wants. He’d rather be rejected, and even die in the extreme case of the situation hurting Aoba, than having him living something he doesn’t really want, that he doesn’t feel in his heart. Giving himself to Koujaku letting him do whatever he wants without thinking twice, without thinking about his own wishes. A life that doesn’t respect Aoba’s wishes is a nightmare for him. Just like he says in the confession scene “All I can remember is that I didn’t want to touch you like that”.
I mentioned that they don’t treat the tattoo as something that changed Koujaku, but as someone else inside his mind. When Sly appears before him, Koujaku immediately knows that he’s not Aoba, but has a hard time believing it, because physically he’s the same but white. He doesn’t know what’s going on, he can’t process it, but he knows. And the thoughts that tell him that the man in front of him is not Aoba are in red, like someone else’s, with some lowercase and some uppercase, growing more intense as the madness and anger of his tattoo reflects through. Doesn’t it remind you of how Sly’s thoughts appeared in the middle of the screen when Aoba was in charge?
Sometimes I wonder what Sly’s real intention was here. In theory he wants to break Koujaku and bring out the beast because that’s the part of Koujaku that he sees himself reflected in, that destructive entity, his darkest, true side, his pure animal instinct. Exactly what Sly is.
But he still tells the sane Koujaku that he loves him and wants to convince him that he’s Aoba. If that had worked then what would he do next? Because he truly believes that’s what he wanted to hear, and when the narration returns to his point of view he tells us that his love for Koujaku is true. Obviously locked in a cell it would be difficult for anyone to believe him, and Sly wouldn’t get him out of there anyway when he wants to keep Koujaku for himself. But then why does he keep trying to convince him, over and over again, even when Koujaku still doesn’t recognize him as Aoba any time he wakes up? Would he have been satisfied with a sane Koujaku, with those restrictions he hates, just because he accepted his words? It’s only when he sees that Koujaku won’t buy it, no matter what he tells him, that he changes his strategy.
And it’s in this scene that we see Koujaku in control for the last time, and again the last thing he says before losing his mind is Aoba’s name. This ending makes us see how Koujaku once again enters a cycle of abuse. He has gone from being his father’s slave, to Ryuuhou’s, and now Sly’s, and he will probably never get out of that cell alive. He no longer has prayer beads protecting him, only chains imprisoning him.
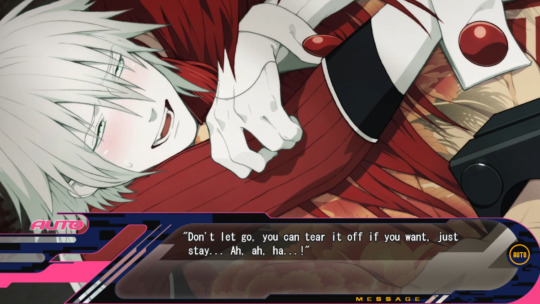
Sly is aware of what he has done, and he believes that since he has destroyed Koujaku’s consciousness/spirit, it’s only fair that he is the one to destroy his body, not only fair but it even seems like an attractive idea, to die at his hands (Sly try not to be Ryuuhou challenge). I really like this dialogue where Sly tells Koujaku that he can tear off his flesh if he wants, on the condition that he stays. Staying with him, a reflection of his desire to feel loved, accepted, after so many years of abandonment. After hearing Koujaku speak back to Aoba, it must feel like a punch to the stomach to think for a moment that he’s wrong with what he’s chosen for the two of them, to think that Koujaku doesn’t really love him.
Having him locked in a cage somehow is perfect to prevent the slightest chance of Koujaku walking away, as well as keeping him in this state, unable to speak, unable to think, unable to reject him. It’s because of these things that I usually think that at least at the beginning the relationship with Koujaku in a good ending would be quite turbulent. He would like to flirt with Koujaku, sure, but when he realizes that he really feels love for him, he feels vulnerable, weak, and needs to protect himself because the people who were supposed to always be with him, guide and protect him, left him. And Koujaku somehow “abandoned” him once too. So before being exposed to that, he would rather push Koujaku away. Regardless, Sly would always come back to him, because as much as he wants to walk away he can’t, he needs Koujaku to stay by his side. It doesn’t matter if it’s love or hate, Sly will take it because it’s intense, real and raw.

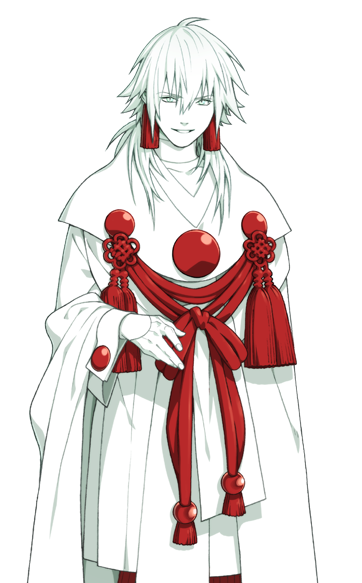
Fun fact: Sly and Beast Koujaku both have golden eyes, when they “transform”. Everyone has those three sides of their conscience but Aoba’s just have a distinct personality and identity each, which I think might lead to thinking that beast Koujaku might have a personality of his own. I think he’s somewhere in between, he’s obviously not like them, but he’s definitely his own entity. Like some kind of natural force, like rain, wind, the energy of the cosmos, possessing him, something more abstract than a spirit or god, which we usually see as human or animal-like appearance wise.

The first thing that strikes us when we see Aoba is that his design radically changes. When Sly takes control of his body it’s not like he suffers any physical changes, besides the shine of his eyes, however here he turns completely white. The only time we see something like that happen is when we see the true forms of Sei and Aoba, but those black marks don’t appear. This is what makes me wonder if the white color has something to do with those forms, as if it were some kind of symbolism of Sly “breaking free” and being himself, without restrictions, without Reason, but they don’t add the black marks to not spoil it, or because it looks like shit with the design, or because it simply has nothing to do with that.
The white color is the color of death, mourning, the color with which the deceased are dressed. A sterile color, without impurities, highly related to the spiritual world. Many white flowers are commonly used in funerals, usually Buddhist, such as the white chrysanthemum, used for its meaning of truth and sincerity. Aoba wears a white kimono and also gives one to Koujaku. These traditional elements could be there just to remember Koujaku but nothing in this document could ever be simple of course.
The hair of a dead person is considered to turn white after a certain period of time, meaning that the hair is no longer a source of impurities, it can't be possessed by an evil spirit, and can be transported beyond the border that marks the separation between the sacred realm of the dead and the ordinary world of the living.
His skin, his characteristic blue hair, his eyes and his clothes turn completely white because at this point Aoba is no longer there. Not in a literal sense, of course, but in a figurative sense, Aoba is dead. And this is basically the same thing that happens with Koujaku. They are both reborn, destroyed, spiritually dying so that something else can be created, the ID, the instinct of destruction, the two beasts freed from the bodies that held them prisoners.
His clothes in general resemble those of a Miko, with a more “fantastical” and sexualized appearance. This post talks about it as well. Again it’s a reference to the spiritual realm, their religious side and how Aoba/Sly is an object of devotion, of how Aoba is somewhat a channeler for Koujaku. Just like there are rituals that call the gods to our world, like I’ve said in the section about hair, which serves as a connection with gods, Aoba is the only thing that connects Koujaku with this world, the only reason why he’s still alive.

#dmmd#koujaku#aoba seragaki#dramatical murder#aoba#kouao#koujaku dmmd#sly blue#slyjaku#essay#They really did that red thread of fate thing with them huh
170 notes
·
View notes
Text
Boothill as your S/O
THIS BOUNTY CONTAINS:
[Just some random hc’s about this skrunkly man]
[Intentional lowercase AND uppercase]
[Horrible grammar ahead]
[Pretty short]

This man is NOT experienced!!!
have you seen him? he has the same charisma and grace as a bird flying into a window!! there is no way he’s had a relationship and it shows in how he nervously hands you flowers or little trinkets he found for you. (that DEFINITELY isn't stolen)
his idea of a date is either something borderline illegal or something surprisingly quiet and nice like a picnic in a field of grass.
Really protective
when you’re out and about with him it doesn’t always end well, he IS a wanted man and the IPC are crawling around everywhere so it’s not surprising when he’s always got one arm wrapped around you and the other near his holster.
Definitely teaches you how to shoot
Boothill is a Galaxy Ranger and if you don’t actively join him on his adventures then he won’t be able to protect you against anyone who has it out for him. (aeons that list is LONG) so naturally, he teaches you how to shoot and the basics of gun safety which he drills into your head (even tho he himself dances around with the damn thing like it‘s a toy.)
A great father
I will die on this hill, Boothill has experience raising a child which is shown in his backstory and I just know he is the most caring father ever, he’d give the best hugs and tell them all about his adventures. (he’s definitely a girl dad too, he wears a tiara and everything if that’s what his baby girl wants.)

#[BOUNTY COMPLETE]#boothill x reader#boothill x you#hsr x reader#headcanon#gn reader#honkai star rail#boothill
194 notes
·
View notes
Text
Are screams more terrifying if they are coherent or incoherent screams?
I am going off the assumption that a coherent scream is either yelling or you can hear distinct sentences, this was made with intent to convey something!
But an incoherent scream is just screaming? Would it be more terrifying because it’s so disjointed? And could it make sense with the screams having an uppercase or lowercase-
Is it just sound at that point or….
#this doesent even make sense#what am I even contemplating rn#4am shitpost#shitpost#I have been awake too long again#starlit says
9 notes
·
View notes
Text
SAINTS? SAENTS. — PROLOGUE

synopsis. where an all korean high school finally gets an international student ... turned into a group of 5.
meet saeboms internationals and peek at their lives as they adapt to the new world their thrown in together!
warning. cussing, intentional lowercase and uppercase, ermmm idk what else but lmk if something should be added

keeho.
another year being the only one alone still struggling with this culture shock in this fuckass school. at this point he had set an alarm every 11:11 and prayed before bed for someone like him to show up the next school day. typing on his phone with a clear frown on his face, he just continued ranting and ranting to the closest online friend he had, chunhua. they befriended each other VERY quickly after she constantly agreed with his movie criticism, opinions against him would never be tolerated! reading the message she sent after the 10 sentence long paragraphs the smile disappeared instantly as he screamed a loud "FUCK YEAH" and ran as fast he could to the school office, choosing to ignore the judging stares because again, OPINIONS AGAINST HIM WOULD NEVER BE TOLERATED!!!
chunhua.
groaning internally, she fought the urge to roll her eyes as the principal continued to ridicule her for her grades. sure she wasn't the best student but she wasn't failing at least! "tch! a pretty face gone to waste, what's the point of looking like that when you can't even be smart!" what a fucking creep. looking down she did her best to discreetly pull out her phone to sent steph a message, fuck the surprise entrance for him. get in the fucking school office this principals coming at my shit grades. the read message tag was all she needed to see to know he was on his way, probably tripped on a few steps as well. the slammed open door approximately 1.43 minutes was enough for her to know this school year was going to be SOMETHING.
skip to a year real quick erm.
yn.
standing in the front of the classroom felt like fucking hell. a duo giggling their asses off in the back of the room didn't help either because were they laughing at YOU or at EACH OTHER. anxiety was taking a TOLL on you and it was absolutely terrifying, you thought your knee was going to start buckling noticeably. hands were clammy and shaky, jesus take the damn wheel. introduce yourself MY ASS, this shit was not necessary in [where ever the fuck you are] and you wish it wasn't here too. the differences were so overwhelming you almost slid yourself off your seat so you could hide under your desk. AND YOUR DESKMATE WAS ALSO A BITCH TOO LIKE... why did your entire class start oooing and screaming. all you knew was this guy was named lee suho or something and that you hated him because all you did was ask for the page on where the class was and he ignored your ass. when the end of the class came you still held in your breath, NO BREATHING NO BREAKS!!! god was clearly not on your side because the duo that was snorting and gasping for air came up to you and you almost collapsed from a heart attack. god they were fucking gorgeous too, pretty people are too terrifying. when the guy spoke up you almost had a seizure because damn he got a real nice voice, "you're not from korea right?" nothing was coming out your mouth and you knew that. sparing yourself that embarrassment, a simple nod was all it took for them to have silent joy, giant grins and clapping enthusiastically with both hands. the english response you received from the girl let you finally start breathing (thank the lord because damn you were probably gonna look like violet from charlie and the chocolate factory), "welcome to the school new int!"
skip to 2 months thanks.
jake.
awkward was all that could be described for how jake was acting. his words were stiff as he introduced himself and he looked like a barbie doll being twisted to be sitting in a chair. when break came around all he could do was sit up straight staring into space. his zoning out was very rudely disrupted by a girl who pushed someone into his desk, waving them along with another guy. even if it seemed more like they were getting bullied, all he could do was start praying they wouldn't bully HIM. the awkward land on his desk made them just try and act cool ... failing to be honest ... putting a hand on their cheek and other hand on hip, "so um ... how are the spiders back home" silence just fell between the both of you as jake simply didn't know how to respond. as i said, awkward. clearly the random stranger had given up on the small talk because all it took was the "we're also abroad just let us adopt you" for him to relax his tensed up shoulders because, well, how bad could this get?
ermmmm gimme a week and a half skip.
yunjin.
in all honesty, jen wasn't used to this fucking name change. all her life it was jennifer, jenni, jen, ferb even. now she had to get used to being called YUNJIN by everyone. god it felt like her parents were everywhere now, yunjin this yunjin that. every time someone spoke to her and they even said her name she had to hold in a groan. standing in front of the classroom, she wanted to sink into the ground so badly as she said her name and as someone shouted out "I USED YOUR YESSTYLE CODE!!!" like... NO YOU DIDN'T. who the fuck brings up the personal work to a first meet class introduction. when class was over one glance at a quartet with a random guy pointing at her was enough for her to put her head down into her arms and try to sleep through the 10 minutes she had. well the lord really said fuck your beauty sleep because the knock on her desk had her looking up, head still in arms up at a guy from the group of 4, the rest cheering him on as he stuttered through his (english) intro (which surprised jen... in a good way of course), "um like hi im uh jake- you know what fuck this. do you wanna be friends with us? we foreigners needa stick together anyways, no?"

taglist. @junoswrlld @beommii @shotaroswifeyily @manooffline
⠀⠀⠀⠀⠀⠀⠀⠀masterlist previous next
notes. for once got to 1k words 😱😱 anyways i think i did good on this added personality ykyk i did that ‼️
#﹒luans ☆ fics ! 💬#﹒series ☆ saints? saents. 🗯#⤷ ❒ divider + loc by plutism ➣ ⁺#kpop smau#kpop fanfic#kpop#smau#keeho p1harmony#p1harmony smau#yunjin smau#keeho smau#lsfm smau#lsfm#jake enhypen#jake smau#enhypen smau#true beauty smau#true beauty#fanfic#keeho fanfic#keeho#yunjin#jake#jake fanfic#yunjin fanfic#kpop fluff#fluff#enhypen#p1harmony#enhypen fluff
12 notes
·
View notes
Note
Hey dado, so uhm...
Look. I have ZERO IDEA if i have to tell you this, and i dont know if YOU know but... theres something.
Its called "Department of Anomalous Drugs and Ordnance".
The uppercase letters spell DADO, and like- your entire thing is "trust dado" and writing lowercase and generally being nice to people.
Now add onto that an UPPERCASE dado, thats probably your opposite, which means good writing but B A D intentions.
...just wanted to warn you.
my goodness dado is thankful for this warning. dado was not aware of this evil dado lurking around in places which it lurks. luckily dado has precautions to deal with this sort of thing. such as fire arm by dado buy now at dado legally ambiguous goods and legal consultancy
5 notes
·
View notes
Text
Wordmarks and Lettermarks: Typography at Work

Welcome back, design traveler! You’ve mastered the art of symbols, explored shapes, and learned about responsive logos. Now, it’s time to dig into the world where type does all the talking: wordmarks and lettermarks. If logos were a band, these guys would be the lead singers—loud, clear, and hard to ignore.
🅰️ What Are Wordmarks and Lettermarks?
Both of these logo types rely entirely on typography—no icons, no illustrations, just pure letterform magic. But they do have different vibes and uses:
Wordmarks (aka logotypes): These are logos made up entirely of a company’s name in a styled font.
Think: Google, Coca-Cola, Disney, FedEx
Lettermarks (aka monogram logos): These are logos based on initials.
Think: IBM, CNN, NASA, HP
Both forms live and breathe typography, and when done right, they are iconic—even unforgettable.
✏️ When Should You Use Each?
Wordmarks are fantastic when:
Your brand name is distinctive and not too long
You want to increase name recognition
You don’t need a symbol to communicate your brand
Lettermarks are the go-to when:
Your company name is long, complicated, or hard to pronounce
You want a simple, scalable identity
You already have strong brand recognition
🎨 Typography: The Real Hero Here
The typeface you choose isn’t just about being pretty. It carries emotion, tone, and intent. Some considerations:
Serif vs Sans Serif
Serif: Traditional, authoritative, trustworthy (e.g., law firms, luxury brands)
Sans Serif: Modern, minimal, clean (e.g., tech startups, lifestyle brands)
Custom vs Stock Fonts
Custom typography (like Coca-Cola’s script) can make a logo iconic and ownable.
Modified stock fonts can still look unique if tweaked properly.
Spacing & Kerning
Letter spacing (kerning) can make or break a wordmark. Improper spacing makes it feel unpolished or amateurish.
Weight & Case
Uppercase tends to feel stronger and more formal.
Lowercase can feel more friendly and casual.
Mixing them? Bold move—but it can work (e.g., eBay or iTunes).
💡 Famous Case Studies
Google: Clean sans-serif wordmark with a playful color palette = instantly recognizable.
CNN: Bold, red lettermark—3 letters and it’s global.
Visa: Wordmark so simple, yet it evokes trust.
NASA: Lettermark that feels futuristic and strong—fitting for space explorers.
Each of these brands tells a story just through their type.
🛠️ How to Design Your Own
If you're working on a wordmark or lettermark, here’s your mini-process:
Start with the brand voice: Is the brand friendly? Premium? Playful? The typeface should echo that.
Explore typography options: Use font pairing tools or draw your own characters.
Experiment with custom tweaks: Ligatures, icon-style letters, or creative negative space (think FedEx’s arrow).
Test it in different contexts: Does it look good tiny? Printed? On a billboard?
Pro tip: Start with black and white. Color can distract you from seeing what really works.
📦 Bonus Thought: Pairing Wordmarks with Symbols
Some brands pair wordmarks with icons (like Spotify or Dropbox), allowing them to switch between full and compact logo modes. This hybrid model gives you the flexibility to grow your logo's ecosystem.
But if you're going for a pure wordmark or lettermark, your type must carry the full brand load. No pressure. 😉
🎯 Final Takeaway
Typography isn’t just design—it’s branding language. With wordmarks and lettermarks, you have the power to create logos that are bold, sophisticated, or fun, using nothing but letters. When done right, these logos become timeless.
🤯 Unique Fact of the Day
The FedEx logo is one of the most famous examples of hidden symbolism in typography. Look closely between the E and the x—see the arrow? It represents speed, direction, and precision. And it’s all just clever use of negative space.
https://letterhanna.com/wordmarks-and-lettermarks-typography-at-work/
0 notes
Text
Celestial Riviera Handwriting Font
Introducing Celestial Riviera, an artistic handwritten script font designed for those who dare to stand out. With its striking strokes and expressive curves, this font exudes confidence and creativity, making it perfect for statement branding, edgy designs, and high-impact visuals. Every letter flows with intentional energy, blending raw artistic flair with refined elegance.
Ideal for logos, posters, fashion editorials, and packaging, Celestial Riviera commands attention while maintaining an air of sophistication. Its strong yet fluid style makes it a go-to choice for designers seeking a font that speaks power, passion, and artistry. Elevate your projects with a typeface that transforms words into works of art.
Easy Access to Glyphs and Swashes
Gain easy access to all alternate glyphs, swashes, ornaments, and underlines by simply using ligatures. You can try them out yourself in the font preview tool on our website, letterhanna.com.
Accessing Swashes and Ornaments
Underline Swashes: Use a hyphen symbol "-" followed by a number between 1 and 30. For example, type "-3", "-22", or "-17" to get various underline swashes.
Head/Beginning Swashes: Use a dollar sign "$" followed by a number between 1 and 9. For example, type "$2" or "$8" to get different head/beginning swashes.
Ornaments: Use an "at" symbol "@" followed by a number between 1 and 26. For example, type "@4" or "@13" to get different ornaments.
PUA Encoding for Ease of Use, which means you can access all the glyphs and swashes with ease!
Font Features
Uppercase and lowercase letters
Numbers and punctuation marks
Multilingual support
Ligatures
Underline swashes
Ornaments
Easy access to swashes using ligatures
Test and get this font at https://letterhanna.com/celestial-riviera-font/ Commercial and Free version









0 notes
Text
➝ Subversive Programming - There are Two Primary Methods of Influence in the Occult World – Magick and Sorcery.

There are two primary methods of influence in the occult world – Magick and Sorcery (or Lesser Magick) – which share the same definition except for one slight difference in terms.
Magick is: the science and art of causing change to occur in accordance with the Will.
Sorcery is: the science and art of causing change to occur in accordance with the will.
While the words are the same, the intent is what differentiates them. For example, teaching Natural Law and sharing knowledge to the world (especially from a distance) in order to cause a positive change can be considered an act of Magick because it aligns with the uppercase-w "Will" of Creation. It's using intentional energy and the voice in the service of truth and humanity as a whole, to uplift human consciousness. On the other hand, Sorcery would be making use of the same knowledge to serve the lowercase-w egoic "will" of selfish desire. Sorcery would utilize the subversive use of imagery, color, symbolism and language to manipulate and control minds such as in mainstream media (news, adverts, entertainment, etc).
"Non-ritual or manipulative magic, sometimes called LESSER MAGIC, consists of the wile and guile obtained through various devices and contrived situations, which when utilized, can create change in accordance with one's will." – Anton LaVey, 'The Satanic Bible'
In modern vernacular, we think of the term "media" as a means of communicating to a larger population. That's true, but the origin of the word has a particular history. The Latin word "media" itself ultimately derives from the name of an ancient sect of sorcerers called The Medes. In turn, it is the origin of the word "mediate." When an enemy needed to be defeated covertly, a ruler would call upon the Medes to be the "mediators" and deceivers to give them an upper hand. Therefore, you could say that the term "mass media" is nothing more than a euphemism for far-reaching sorcery. The dark occultists are getting the "upper hand" on us, psychologically and emotionally.
And while we're all distracted and emotionally tense over these "crises," they are pushing forth their agenda to widen control (medical tyranny, increased dependency on technology, centralized digital currency, uniting countries/governments, increasing police/military power, etc). And anyone who speaks out against it is framed as the enemy. It's a classic cult technique. Government is and always has been a mind-control cult serving as the strong-arm of the dark occult priest class.
All of it, ultimately, is a stepwise progression (that's been going on for ages) towards total human enslavement. The use of health pandemics, terrorism, war, mass shootings, and all the other psy-ops are to de-moralize, de-humanize, de-populate, divide, and control. It's no longer conspiracy "theory" when you finally begin to see the patterns, tactics, and methodologies being used.
As an aside, you might have noticed my own use of blue and gold throughout these slides. This is also deliberate, for a positive reason. Blue is feminine energy, receptive – of information, truth, knowledge, wisdom. Gold is about intuition, understanding, awakening, and is symbolic of the light of the sun and solar chakra. The negative use of red in the Dark Occult section relates to base chakra, base consciousness/desires and dark energy which is what Satanism is rooted in. You might notice the constant use of red in fast food restaurants. That's intentional. Color has a deep psychological impact on us more than we realize, and these social engineers use it constantly.
But it's not just symbols and colors that are used in subversive programming. It's also wordplay – the use of euphemisms and repetition. The lie has to be repeated over and over and over. Things that people might consider wrong or immoral have to be framed in a different light, under different names, with skewed definitions. It's an age-old tactic that never fails... until we start raising our consciousness to a high enough level to see it. All of this continues to happen because we, as Jiddu Krishnamurti said, have a crisis in consciousness. We let our egos harden, clinging to our belief systems, and refuse to see the hidden truth because we fear the unknown; but ultimately, we fear the personal responsibility that comes with knowing the truth.
As the Jesus figure said: the truth shall make you free. Freedom comes from knowledge. In this case, it's symbol literacy. It's occult literacy. Ignorance of these things can only lead us into more suffering, more slavery, and more chaos. Start using your spiritual currencies of Time and Attention. Spend the time and pay attention to what's going on around you (and within you). That hard-work investment brings you the quality income of truth. That's what having higher consciousness means.
When you Know, then you can begin saying the word of power: NO.
You should be aware that the most effective prisons are made of beliefs and not stone or steel.
The most effective mind-control tool on the planet today is television.
THE MAINSTREAM MEDIA'S JOB IS TO CONVINCE THE PUBLIC THAT THE IDEAS OF THE GLOBAL ELITE ARE IN THEIR BEST INTEREST, AND TO CONCEAL HOW THE GLOBAL OLIGARCHY PLANS TO DESTROY AMERICA AND RAVAGE LIVES IN COUNTRIES AROUND THE WORLD.
People make decisions based on the information they have been given and have available to them in their environment. They may make assumptions or decisions based upon false information, and accumulatively the consistent exposure to false narratives shapes their personal reality and influences the popular culture. Those that seek to control or enslave others know that shaping narratives becomes absolutely crucial in controlling groups of people, in order to socially engineer behaviors and move them in the direction the controller wants them to go.
0 notes
Text
Sometimes A Lonely Way
read it on the AO3 at https://archiveofourown.org/works/60135826
by Lightspeed
A companion piece to The Extreme Path. While Spy, Scout, and most importantly Sniper are in Japan, Demoman struggles with being away from his husband for an extended period of time for the first time, and doesn't handle it particularly well. It gives Soldier a chance to learn more about his friend, and question the parallels and differences between the RED and BLU bombers, while the rest of the team takes a little bit to catch up on how to handle their forlorn friend. Pyro learns a secret!
Words: 9891, Chapters: 1/1, Language: English
Series: Part 58 of Monstrous Intent
Fandoms: Team Fortress 2
Rating: Teen And Up Audiences
Warnings: No Archive Warnings Apply
Categories: M/M, Multi
Characters: Demoman (Team Fortress 2), Sniper (Team Fortress 2), Soldier (Team Fortress 2), Pyro (Team Fortress 2), Engineer (Team Fortress 2), Heavy (Team Fortress 2), Medic (Team Fortress 2), Scout (Team Fortress 2), Spy (Team Fortress 2), Eyelander (Team Fortress 2)
Relationships: Demoman/Sniper (Team Fortress 2), Engineer/Pyro (Team Fortress 2), Heavy/Medic (Team Fortress 2), Scout/Soldier (Team Fortress 2), Scout (Team Fortress 2)/Everyone
Additional Tags: Alternate Universe - Creatures & Monsters, Minor Demoman/Soldier (Team Fortress 2), Separation Anxiety, Alcohol Abuse/Alcoholism, team comparisons, depression (lowercase d), maybe a touch of uppercase D too, Team as Family, Flirting, Public Display of Affection, Scents & Smells
read it on the AO3 at https://archiveofourown.org/works/60135826
1 note
·
View note
Text
Cloud Security – Best Practices For Protecting Your Data
In today’s digital landscape, data is the new gold, and the cybercriminals in the dark web exploit any vulnerability. The rise of cloud storage has brought incredible convenience and scalability, but it also presents a new battleground for these “bad guys.”
Hackers are on the lookout for weak spots in cloud defenses, seeking to steal personal, financial, and sensitive business data. So, it’s crucial to implement solid security measures and shield your cloud-stored information like a well-guarded treasure.
Here are the 10 ways to protect your data:
Choose a Secure Cloud Provider
The first step in protecting your data is selecting a provider with a proven track record. Look for those with certifications like ISO27001 or SOC 2, which demonstrate robust security protocols. Additionally, be mindful of data residency—choose a provider that stores data in regions with strong data protection laws, ensuring compliance and reducing legal risk.
Use Strong Passwords Password strength is one of the simplest yet most overlooked security measures. Ensure you’re using long, complex passwords that combine uppercase and lowercase letters, numbers, and special characters. Avoid common phrases or easily guessable information. Also, change your passwords periodically and never reuse them across multiple services.
Enable Multi-Factor Authentication (MFA) Passwords alone aren’t enough. Multi-factor authentication (MFA) adds an extra layer of protection by requiring a second form of verification, such as a text message or authentication app, to access your account. Even if a hacker obtains your password, MFA can block unauthorized access by demanding a secondary proof of identity.
Encrypt Your Data Encryption is the process of converting your data into a scrambled format, making it unreadable to unauthorized users. When using cloud storage, ensure that both client-side (on your device) and server-side (on the provider’s server) encryption are in place. This ensures that even if your data is intercepted, it remains secure. It’s also crucial to maintain control over your encryption keys for added protection.
Implement Role-Based Access Controls (RBAC) Not everyone who accesses your cloud storage should have the same level of permissions. Implementing role-based access controls ensures that users only have the minimum permissions necessary for their tasks. For example, some may only need to view data, while others require editing capabilities. Regularly review these permissions to prevent unauthorized access.
Backup Your Data Regularly Cloud storage isn’t foolproof, and relying solely on one platform can be risky. Always back up your critical data and store it in multiple locations, including both cloud-based and physical backups. Regularly test your backups to ensure they work and can be restored in the event of an emergency, such as a breach or accidental deletion.
Stay Educated and Informed Human error remains one of the biggest risks to cloud services. Regularly educate yourself and your team on the latest security best practices. From recognizing phishing attempts to understanding secure cloud usage, knowledge is a powerful defense against both intentional and accidental data breaches.
Monitor for Unusual Activity Cloud providers typically offer access logs, allowing you to monitor activity within your account. Regularly review these logs for any suspicious behavior, such as logins from unfamiliar locations or excessive data downloads. Early detection of unusual activity can help you respond quickly and mitigate potential damage.
Develop an Incident Response Plan No matter how secure your setup, breaches can happen. Having a well-documented incident response plan ensures you’re prepared to act quickly in the event of a security breach. Your plan should outline how to contain the breach, recover lost data, and minimize damage. Practice this plan regularly so that everyone knows their role in an emergency.
Keep Your Software Up to Date Both your cloud provider and your devices should always be running the latest software. These updates often contain security patches that fix vulnerabilities hackers could exploit. Set up automatic updates where possible to ensure you’re protected against the newest threats without needing to manually intervene.
Conclusion: In an increasingly connected world, protecting your data in the cloud is more essential than ever. With cybercriminals constantly evolving their tactics, it’s critical to stay ahead by implementing strong security practices. Remember, cloud security is not a one-time task but an ongoing process that requires vigilance, regular updates, and constant awareness of emerging threats. Stay proactive, and keep your data safe. For more information and services get in touch with our cloud services and security team
0 notes
Text
Process book 2


Feedback
Before print, I got some feedback based on my current book. The feedback included making all the text on the contents page all lowercase or all uppercase rather than having a mix of the two. I was also told to drag the chapter pages to full bleed so that when they are cropped there is a lesser chance of it being white. I would like to add two evaluations to my process book so I aim to start writing these in the lead-up to my outcome. By doing this, my aims and intentions will be clear. I later asked my peers if I should align the numbers to the last words of the previous page on my contents page. I'm glad that I did this as I got a range of opinions and the majority agreed that this would look better than what I had done.



I took a photo of some of my favourite pages once I had bound the book together. I was so happy with the outcome and glad that I took feedback from Briony before I printed as it made a world of difference to the appearance of the book. The feedback helped me to refine the layout and improve its visual appeal. I was happy with the number of pages I allocated to each brief as I felt that I was able to show enough of my work to explain how far I had come from the start of the briefs.
Next year I will try to think more outside the box with my process book, as I kept it safe this year as I was just getting used to the content I needed to include and how to bind it once it is printed. I plan on experimenting with new layouts and aim to incorporate new colours and textures into my book pages to add depth and detail to my pages. I hope to create an engaging process book that truly reflects my growth and creativity.
Bibliography

Year 1 overview
I was set 4 briefs: Communicating in Colour, There’s an App for That, Place of Words, and Process Books. These projects tested my ability to work as a group, my digital skills and my research skills. I thoroughly enjoyed these briefs as they were all quite different and kept me busy throughout my final term.
Throughout the projects, I was inspired by a number of things such as images I’d seen on Pinterest or books and magazines I had come across. My initial idea for my Place of words project came from a mind map I produced as a starting point for the brief. I enjoy creating mind maps and mood boards before I start a project as they help me think more spontaneously before finalizing any ideas. The main body of my research was conducted online, however I also completed primary research. I found secondary research more useful as it was easier to find, but my primary research helped influence more of my design choices. For the group project we split the research among ourselves and ensured we all fully understood the brief before starting our Adobe XD file.
A challenge I faced during this term was trying to juggle all my projects simultaneously. However, I believe that my time management improved compared to my last brief. This time, I ensured that I worked through all the briefs at the same time to try and complete them with enough time to start my Process Book. Having critiques and getting feedback from peers helped me to keep my projects moving as it gave me more perspective as to what was going well and what I could improve. I completed a number of prototypes in comparison to my last brief, which I believe helped the success of my projects this time around. A valuable piece of critique I received was to always remember and think back to who my target audience is.
Overall I was happy with all of my outcomes and think that I had enough time to complete them all. I feel that these projects have influenced my approach to future projects as I aim to have more of a time plan and structure that I follow like I did during this brief. I think that putting my postcards, app and magazine into mock-ups helped me to visualise my outcomes further and think that they looked professional for the time period that I was given to produce each brief. In conclusion, this term has not allowed me to improve my skills but has also provided me a valuable lesson in time management and the importance of feedback. In future, I will implement these skills to my briefs to aim for a successful approach.
0 notes
Text
Best Cyber Crime Lawyers in Delhi
What is Cyber Crime | Best Cyber Crime Lawyers in Delhi
Cybercrime refers to criminal activities that involve the use of computers, networks, and digital technologies to commit illegal acts. These offenses can range from financial fraud and identity theft to hacking, cyberbullying, and spreading malware. Cybercrimes exploit vulnerabilities in computer systems, networks, and online platforms, posing significant threats to individuals, businesses, and governments.
Common types of cybercrime include:
Financial Fraud: Unauthorized access to financial information, online banking fraud, credit card scams, and other schemes aimed at stealing money.
Identity Theft: Illegally obtaining and using someone else's personal information, such as social security numbers or passwords, for fraudulent purposes.
Hacking:Gaining unauthorized access to computer systems, networks, or websites with the intent to manipulate or steal data, disrupt operations, or spread malicious software.
Phishing: Deceptive techniques, often via email or fake websites, to trick individuals into revealing sensitive information like passwords or financial details.
Malware:The distribution of malicious software (viruses, worms, ransomware) with the intent of damaging or gaining unauthorized access to computer systems.
Cyberbullying: Harassment, threats, or intimidation using digital platforms, causing emotional distress to individuals.
Online Scams:Various fraudulent schemes conducted on the internet, such as lottery scams, fake auctions, or deceptive online purchases.
Cyber Espionage: Covert activities where hackers or state-sponsored entities infiltrate computer systems to gather sensitive information for political, economic, or military purposes.
Denial-of-Service (DoS) Attacks: Overloading a system, network, or website with excessive traffic to disrupt its normal functioning and make it temporarily or permanently unavailable.
The prevalence and sophistication of cybercrimes continue to evolve, necessitating ongoing efforts in cybersecurity and law enforcement to combat these threats. As technology advances, so do the methods employed by cybercriminals, making it crucial for individuals and organizations to stay vigilant and implement robust cybersecurity measures.
How You Can Protect Yourself from Cyber Crime?
Protecting yourself from cybercrime involves adopting proactive measures and practicing good online habits. Here are some tips to enhance your cybersecurity and reduce the risk of falling victim to cybercrime:
Use Strong and Unique Passwords:
Create complex passwords with a mix of uppercase and lowercase letters, numbers, and symbols.
Avoid using easily guessable information like birthdays or names.
Use unique passwords for each of your online accounts.
Enable Two-Factor Authentication (2FA):
Activate 2FA whenever possible to add an extra layer of security to your accounts.
Typically, 2FA involves receiving a code on your mobile device or email, in addition to entering your password.
Keep Software and Systems Updated:
Regularly update your operating system, antivirus software, browsers, and other applications.
Software updates often include security patches that address vulnerabilities.
Be Cautious with Emails:
Avoid opening emails from unknown or suspicious sources.
Do not click on links or download attachments from untrusted emails.
Be wary of phishing attempts, where attackers may impersonate legitimate organizations to steal your credentials.
Secure Your Wi-Fi Network:
Set a strong password for your Wi-Fi network to prevent unauthorized access.
Use WPA3 encryption if available for enhanced security.
Regularly check and update your router firmware.
Use a Reliable Antivirus Software:
Install reputable antivirus and anti-malware software on your devices.
Keep the software updated to ensure it can effectively detect and remove threats.
Monitor Your Financial Statements:
Regularly review your bank and credit card statements for any unauthorized transactions.
Report any suspicious activity to your financial institution immediately.
Educate Yourself on Cyber Threats:
Stay informed about the latest cybersecurity threats and tactics used by cybercriminals.
Be cautious about the information you share online and on social media.
Backup Your Data:
Regularly back up your important data to an external hard drive or a secure cloud service.
In case of ransomware or data loss, you can restore your information from a backup.
Use Secure Websites:
Look for "https://" in the website URL, indicating a secure connection, especially when providing personal or financial information.
Avoid entering sensitive information on unsecured websites.
Protect Your Mobile Devices:
Set up a password or biometric authentication on your mobile devices.
Install security apps and keep your device's operating system up to date.
By adopting these cybersecurity practices, you can significantly reduce the risk of falling victim to cybercrime and enhance your overall online safety. Regularly updating your knowledge about emerging threats is also essential in staying one step ahead of
cybercriminals.
Who is the Best Cyber Crime Lawyers in Delhi - Advocate Deepak (B.Sc, LLB, MBA)
In the ever-evolving landscape of cybercrimes, having a seasoned professional by your side is essential. Deepak Dutt emerges as a beacon of expertise in the field, offering comprehensive legal assistance to those grappling with digital offenses. This blog post explores why Deepak Dutt is considered one of the best cybercrime lawyers in Delhi and how you can benefit from his adept legal guidance.
About Deepak Dutt:
Deepak Dutt is a renowned figure in the legal fraternity, specializing in cybercrime defense. With a wealth of experience and a proven track record, he has successfully represented numerous clients facing a spectrum of digital legal challenges. His commitment to staying abreast of the latest developments in cyber laws and technological advancements sets him apart as a reliable ally in navigating the complexities of cybercrimes.

Key Strengths:
Expertise in Cyber Law:
Deepak Dutt's deep understanding of cyber laws positions him as a go-to expert for individuals and businesses dealing with online threats. From hacking and data breaches to online fraud and identity theft, he has a comprehensive grasp of the legal nuances surrounding digital offenses.
Strategic Defense Approach: Known for his strategic approach to defense, Deepak Dutt formulates tailored legal strategies for each case. Whether it's a complex ransomware attack or a case of online harassment, his meticulous planning and proactive stance ensure a robust defense against a variety of digital threats.
Technological Acumen: In the digital age, having a lawyer with technological acumen is crucial. Deepak Dutt's proficiency in understanding the intricacies of digital forensics and cybersecurity protocols enhances his ability to unravel the complexities of cybercrimes and provide effective legal solutions.
How to Schedule an Appointment: If you find yourself in need of expert legal assistance in a cybercrime case, scheduling an appointment with Deepak Dutt is a prudent step. You can reach him at +917303072764 to discuss your specific situation and explore the best course of action for your defense.
How to Schedule an Appointment: If you find yourself in need of expert legal assistance in a cybercrime case, scheduling an appointment with Deepak Dutt is a prudent step. You can reach him at +917303072764 to discuss your specific situation and explore the best course of action for your defense. In the realm of cybercrime defense in Delhi, Deepak Dutt stands out as a trusted and proficient legal professional. His expertise, strategic approach, and commitment to client success make him a reliable choice for those navigating the intricate legalities of digital offenses. If you're facing cybercrime allegations or seeking proactive legal guidance in safeguarding your digital interests, Deepak Dutt is the seasoned advocate you can rely on. Call +917303072764 to schedule an appointment and take the first step towards securing your digital rights.
Visit - https://bestcybercrimelawyer.in/
0 notes
Text
Week 8: Project #4 Critique & Design Her Refined Sketches






During week 8, my project #5 spreads were submitted for an in-class critique, and I finalized my design sketches for the DesignHer event in March 2024, celebrating Women's History Month.
Before presenting my spreads, I decided to reprint them through FedEx using their copies and custom document printing option. I chose to print my spreads on two different types of paper: 100lb matte cover finish and 87lb gloss cardstock, both in 11x17 size. This allowed me to see how my work would look printed on different paper types. The matte cover gave a nice, heavyweight and durable finish, and the colors and graphics stood out much more compared to printing on standard copy paper. The gloss cardstock also gave off a clean, shiny finish but the colors seemed off from the digital file, and there were many scratches and streak marks from handling and packaging. After considering both options, I decided to present my spreads for the in-class critique on the matte cover paper. Although the gloss finish was nice, the colors were not accurate and there were too many imperfections.
During the presentation of my work, I explained the intentions behind my design choices for the spreads. I discussed my inspiration that I had previously mentioned in my last blog post. I also highlighted the main creative elements within my physical spreads. My design choices are primarily inspired by the modern aesthetic of the typefaces, including the curves and angles of the typeface. For instance, I drew inspiration from the "pointy" and "angular" features of the Roboto Slab typeface. I incorporated more of those pointy and straight-line elements into the final spread design. I even incorporated my letterform into the actual uppercase alphabet of the typeface since the purpose of this project is to create the 27th letter of the alphabet. Similarly, for the Ubuntu Sans Serif typeface, I drew inspiration from the curves of the typeface. This was incorporated into the illusion graphic in my last page. I also placed my letterform into the typeface's uppercase alphabet to maintain consistency within my overall design of the spreads. Designing the second spread was challenging since I did not want any distracting elements that would take the audience's attention away from the information presented on the page. After trying several abstract and creative elements, I focused on creating an organized asymmetrical and heretical grid that would present the information in an easy, digestible way.
After analyzing the feedback I received during the in-class critique, I came to the conclusion that the response was predominantly positive. The creative elements of each spread were carefully reviewed, and it was found that the typeface alphabet was perceived really well. The abstract modern design also complemented the overall look and feel of both letterforms. However, while reviewing the alphabet up close, it was pointed out that the letterforms appeared small when compared to the rest of the alphabet. This error could have been a result of my letterforms being made up of both uppercase and lowercase letters while being placed in an alphabet with only uppercase letters. This issue threw off the consistency of the design, and it followed into my San serif alphabet as well. To rectify this issue, I can either scale the letterforms to make them a little larger or try a lowercase alphabet to see if it fits better. As for the middle spread, the response was mixed. Some believed that there was no need for any additional graphics, as the whole point of the page is to read and list information about the typefaces. The other reaction was that the spreads appeared boring and a little underwhelming. To address this issue, it was suggested to mess with the title copy to make it appear more free-flowing and interesting. It was also suggested that I space out my body copy a little more to give the text more breathing room and to make the space feel less constricted. Overall, the critique I received was mainly positive, with some helpful suggestions on how to improve the overall look and feel of my spreads.
During the fall break and this week, I worked on the rebranding and logo design for Design Her project. Our professor asked all the female students in the class to create a new logo design for a design event that is going to be held in March 2024. The event is aimed to showcase the female designers in the Midlands community as a celebration of Women's History Month. For my design, I chose to focus on botany and flowers as the main theme. I found the flowers to be a perfect representation of feminine beauty, power, and growth. They symbolize personal growth and development, which is something that every designer aspires for. After exploring multiple typefaces, I decided to use the Amandine typeface from Adobe Fonts for my design. This modern sans-serif typeface has a vintage feel, which honors the female designers of the past while keeping it modern. Its style has curves and bold line weights, making it both dainty and strong. I added a tactile element, such as a pencil or pen, between "design" and "her" to highlight the idea that every great idea starts with a sketch. The color palette for my design was inspired by the original Design Her logo. However, I decided to use bold colors to create a strong presence. All the colors complemented each other and helped establish a cohesive look and feel for the design.
The readings for this week discuss the appendix of graphic design. It primarily includes the roles of editing grammatical and writing style mistakes in design. While the overall design and layout of a project are important, the information being presented is just as significant, if not more. The textbook emphasizes the importance of these roles and how they should be designated to someone specific, rather than just the responsibility of the designer. A neutral third party is always a good idea and is often encouraged to ensure that everything in the design not only looks great but also is grammatically correct and proofread. This will be especially important as I start working on Project 5, which requires me to conduct research for the rebranding of an airline company that is no longer in service.
Lupton, Ellen. “Appendix.” Thinking with Type: A Critical Guide for Designers, Writers, Editors, & Students, Princeton Architectural Press, New York City, NY, 2010, pp. 210–219.
0 notes
Text
phone. Do not autocorrect twitter to Twitter. That lowercase is intentional, it's a sign of disrespect. I hate you. Corporations do not get uppercase letters.
0 notes
Text
Flicker beamed at the nod they got from Pearl. They got it right!
They both watched intently as Pearl continued their explanation. That looked like . . . a musical scale? The notes were a different shape, but it would make sense for it to be that, considering the fact that words had to be a specific pitch. Their ears perked in interest as Pearl then combined that with their name, with a little addition to mark what pitch it was in.
They'd specified which one meant Pearl. Valor wondered what all the other ones meant. If they could write on it then they could probably draw, right? But before he could ask, they were going through the rest of the symbols they'd written down.
For every sound they demonstrated, Valor and Flicker repeated them. They were deeeefinitely going to have to actually sit down and study this. He wished he had the tools that he did in the coven to help with that. Even just a pen and paper would be nice, so they wouldn't have to use Pearl's screen all the time.
Valor blinked when the screen was presented to him with the letters he'd written down in the dirt. Oh, they were actually letting him use it? That was good. That was a sign of trust.
He took the screen and began writing down the rest of the letters in their alphabet. After a moment's thought, he wrote it again in uppercase, and then off to the side wrote down some common letter combinations. Ch. Sh. Th. Were there more? Ah, if he thought of any he could always mention them later.
He went through the lowercase alphabet letter by letter, sounding out each one to Pearl as he went. Any that had multiple sounds he tapped multiple times in a row, with each sound. Then he did the same with the letter combinations.
Ah, he didn't want to go through that all over again with the uppercase . . . Instead, he gestured over the lowercase alphabet, said, "Means," and gestured over the uppercase alphabet. He hoped that would get the idea across.
Finally, he wrote out their names once more, making sure to capitalize the first word of each, and pronounced them again. Pearl. Valor. Flicker.
They repeat those same words they said when they first let her go, she she stares warily for a moment. They healed her after saying something almost identical before.
Those words must be some kind of reassurance, and with a few slow breaths, she closes her eyes and forces herself to relax again.

Whatever she did wrong, they aren't going to hurt her over it.
She wishes she knew what she had done wrong, though, to not repeat it. She has no way of being certain how long this mercy will last.
She also wishes she could figure out what exactly they're saying. It might help if they just... talked more. If she heard those words in other contexts, she might be able to pick it apart better.
Flicker getting her name... mostly right, and close enough that there's no mistake of what's being said gets a small smile from her, and she nods
She does take note of them matching her pitch on the separate syllables too, and smiles at that. They understand now for sure, which is a lead in into the encoding of pitch in the syllabary.
In normal speech there are 6 pitches available for each word, which can shift up or down by formal register, and in the syllabary this is shown by one of six markings over each unique pitch.
Register usually isn't written, because writing in the syllabary is inherently informal. But it is MUCH more useful for communicating with someone who is wholly unfamiliar with gem.
She fills in the bars she wrote on the bottom of her screen, placing the note for each of the six pitches in speech- actual music has a much broader range- then the syllable's of her name next to it.
Glancing at them to make certain the pair seems to be paying attention, she points at the musical scale, then sings the bottom note in the syllables of her name, before marking the symbol for it over the syllables of her name. She checks that they seem to be following, before erasing the pitch mark, and repeating the exercise through the whole scale- making sure to indicate the one that actually means pearl.
She'll save this write up, to come back to it, should she need to indicate specific pitch and pronunciation with more ease.
And then, taking just a moment to let them consider the pitch encoding, she runs down through the syllabary.
Once through it, she stops, smiles nervously, and switches to a blank file, writing all the symbols of their language that she's seen- and they confirmed her understand of pronunciation for two of them; which makes this interesting because they aren't complete syllables like she's used to, but fragments of them to presumably be mixed and matched.
She nudges the screen towards Valor in the air, looking at them expectantly, hoping they understand what she wants, after she just did the very same thing with Gem's syllabary.
103 notes
·
View notes