#intercepting
Explore tagged Tumblr posts
Photo

PRIMA PAGINA New York Times di Oggi martedì, 10 dicembre 2024
#PrimaPagina#newyorktimes quotidiano#giornale#primepagine#frontpage#nazionali#internazionali#news#inedicola#oggi rider#subway#cleared#homicide#split#case#tensions#city#trail#orge#grin#trol#print#intercepting#cimes#shock#unease#syrians#what#tipster#arrest
0 notes
Text
Megumi knows exactly who Suguru is and gets a real kick out of triggering Satoru’s cPTSD. And for Satoru, it’s a double whammy because his kid looks exactly like Toji, too.


Man can’t get a break. He’s confronted by the face of his killer wearing the fit of his ex - on the day he was dumped, no less - on the daily.
I bet Satoru was a normal and healthy individual, but Megumi drove him to insanity.
#jjk#jujutsu kaisen#megumi fushiguro#gojo satoru#dad gojo#satoru intercepts and steal’s kiyotaka’s rogaine deliveries#because his son is making him go bald
2K notes
·
View notes
Text

It seems like Iran intercepted nearly every 'Israeli' attack on Iran.
#It seems like Iran intercepted nearly every 'Israeli' attack on Iran.#iranian#iran news#free iran#iran#anti israel#fuck israel#israhell#israel#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#middle east#free palestine#save palestine#palestinian genocide#i stand with palestine#all eyes on palestine#palestine genocide#palestine#free gaza#gaza genocide#gaza strip
493 notes
·
View notes
Text
China hacked Verizon, AT&T and Lumen using the FBI’s backdoor

On OCTOBER 23 at 7PM, I'll be in DECATUR, presenting my novel THE BEZZLE at EAGLE EYE BOOKS.

State-affiliated Chinese hackers penetrated AT&T, Verizon, Lumen and others; they entered their networks and spent months intercepting US traffic – from individuals, firms, government officials, etc – and they did it all without having to exploit any code vulnerabilities. Instead, they used the back door that the FBI requires every carrier to furnish:
https://www.wsj.com/tech/cybersecurity/u-s-wiretap-systems-targeted-in-china-linked-hack-327fc63b?st=C5ywbp&reflink=desktopwebshare_permalink
In 1994, Bill Clinton signed CALEA into law. The Communications Assistance for Law Enforcement Act requires every US telecommunications network to be designed around facilitating access to law-enforcement wiretaps. Prior to CALEA, telecoms operators were often at pains to design their networks to resist infiltration and interception. Even if a telco didn't go that far, they were at the very least indifferent to the needs of law enforcement, and attuned instead to building efficient, robust networks.
Predictably, CALEA met stiff opposition from powerful telecoms companies as it worked its way through Congress, but the Clinton administration bought them off with hundreds of millions of dollars in subsidies to acquire wiretap-facilitation technologies. Immediately, a new industry sprang into being; companies that promised to help the carriers hack themselves, punching back doors into their networks. The pioneers of this dirty business were overwhelmingly founded by ex-Israeli signals intelligence personnel, though they often poached senior American military and intelligence officials to serve as the face of their operations and liase with their former colleagues in law enforcement and intelligence.
Telcos weren't the only opponents of CALEA, of course. Security experts – those who weren't hoping to cash in on government pork, anyways – warned that there was no way to make a back door that was only useful to the "good guys" but would keep the "bad guys" out.
These experts were – then as now – dismissed as neurotic worriers who simultaneously failed to understand the need to facilitate mass surveillance in order to keep the nation safe, and who lacked appropriate faith in American ingenuity. If we can put a man on the moon, surely we can build a security system that selectively fails when a cop needs it to, but stands up to every crook, bully, corporate snoop and foreign government. In other words: "We have faith in you! NERD HARDER!"
NERD HARDER! has been the answer ever since CALEA – and related Clinton-era initiatives, like the failed Clipper Chip program, which would have put a spy chip in every computer, and, eventually, every phone and gadget:
https://en.wikipedia.org/wiki/Clipper_chip
America may have invented NERD HARDER! but plenty of other countries have taken up the cause. The all-time champion is former Australian Prime Minister Malcolm Turnbull, who, when informed that the laws of mathematics dictate that it is impossible to make an encryption scheme that only protects good secrets and not bad ones, replied, "The laws of mathematics are very commendable, but the only law that applies in Australia is the law of Australia":
https://www.zdnet.com/article/the-laws-of-australia-will-trump-the-laws-of-mathematics-turnbull/
CALEA forced a redesign of the foundational, physical layer of the internet. Thankfully, encryption at the protocol layer – in the programs we use – partially counters this deliberately introduced brittleness in the security of all our communications. CALEA can be used to intercept your communications, but mostly what an attacker gets is "metadata" ("so-and-so sent a message of X bytes to such and such") because the data is scrambled and they can't unscramble it, because cryptography actually works, unlike back doors. Of course, that's why governments in the EU, the US, the UK and all over the world are still trying to ban working encryption, insisting that the back doors they'll install will only let the good guys in:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
Any back door can be exploited by your adversaries. The Chinese sponsored hacking group know as Salt Typhoon intercepted the communications of hundreds of millions of American residents, businesses, and institutions. From that position, they could do NSA-style metadata-analysis, malware injection, and interception of unencrypted traffic. And they didn't have to hack anything, because the US government insists that all networking gear ship pre-hacked so that cops can get into it.
This isn't even the first time that CALEA back doors have been exploited by a hostile foreign power as a matter of geopolitical skullduggery. In 2004-2005, Greece's telecommunications were under mass surveillance by US spy agencies who wiretapped Greek officials, all the way up to the Prime Minister, in order to mess with the Greek Olympic bid:
https://en.wikipedia.org/wiki/Greek_wiretapping_case_2004%E2%80%9305
This is a wild story in so many ways. For one thing, CALEA isn't law in Greece! You can totally sell working, secure networking gear in Greece, and in many other countries around the world where they have not passed a stupid CALEA-style law. However the US telecoms market is so fucking huge that all the manufacturers build CALEA back doors into their gear, no matter where it's destined for. So the US has effectively exported this deliberate insecurity to the whole planet – and used it to screw around with Olympic bids, the most penny-ante bullshit imaginable.
Now Chinese-sponsored hackers with cool names like "Salt Typhoon" are traipsing around inside US telecoms infrastructure, using the back doors the FBI insisted would be safe.

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/10/07/foreseeable-outcomes/#calea

Image: Kris Duda, modified https://www.flickr.com/photos/ahorcado/5433669707/
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#calea#lawful interception#backdoors#keys under doormats#cold war 2.0#foreseeable outcomes#jerry berman#greece#olympics#snowden
400 notes
·
View notes
Text


denjiiii my boy 💔💔 so respectful always even tho no one respects him….. he’s the best in the world
#chainsaw man#csm#chainsaw man manga spoilers#spence.speaks#csm 194#king of consent. i wish he would raise his standards#buddy you deserve this treatment too!!!#im sending one million good things to him but fujimoto keeps intercepting my mail
209 notes
·
View notes
Text
*Knock at door*
Kaz: Im busy
Wylan: Its me
Kaz: Then I’m double busy
#wylan comes in anyway of course#kaz about to get scoulded for intercepting wylans private council letters#kaz brekker#wylan van eck#soc incorrect quotes#six of crows incorrect quotes
205 notes
·
View notes
Text

since it's canon Henry draws knobs, it is totally plausible for him to send medieval dick pics (bad exaggerated drawings of his ween, delivered via royal rattay courier)
#the courier gets intercepted by the enemy who think its important political secrets since its addressed to lord capon. but nay. its a benis#henry of skalitz#hansry#kingdom come deliverance#kcd
120 notes
·
View notes
Text
Admin Tea-party!















Romans 7:18


For I know that good itself does not dwell in me, that is, in my sinful nature. For I have the desire to do what is good, but I cannot carry it out.
#RobloxiasEternalTwilight#Signal Intercepted#roblox#roblox art#roblox au#roblox admins#mrdoombringer#sorcus#gordonrox24#clockwork#reesemcblox#builderman#stickmasterluke#hey guys you ever just get a nightmare about your dead boyfriend haunting you#yeah me neither#hi chat first lore drop kinda nervous
75 notes
·
View notes
Text
Intercepted houses ࣪ ִֶָ☾.

hi guys hope your day is fabulous and everyone is okay ৎ୭
I wanted to discuss intercepted houses and specifically 11th & 5th houses intercepted and the double houses breakdown and also the specific sign you're missing in your chart. This post will be discussing the exclusion of pieces and virgo in your birth chart and it not governing a house and the impacts and observations I've determined fits along this specific interception.
princess leiana astrology xoxo ⋆. 𐙚 ̊
Having 4th house & 5th house in leo
leo fourth house: These natives have a lot of potential for their breakthrough in life. You may had/have an explosive family; it was either big, you had lots of relatives or their was a constant explosiveness of energy in your household. There could of been lots of yelling and arguments in your household. You may have had creative relatives or relatives in any art industries or even your parents. But, there may have had been such energy in your household but not much to you. Your parents may have pushed you to have confidence, stand up for yourself but it may have not resonated with you in the way they went about it. You could be a favorite or often payed attention to in your family but also invalidated which causes a seesaw effect.
5th house leo interception: So, because these natives have a fourth house in leo and each house is a stage in our life, this will tie in together. Therefore, because of the constant explosiveness and fiery nature of your family and home life you may have experienced neglect. You may have not gained the confidence from your parents from any pursuits on anything that was fun for you or even anything you wanted to pursue. Your parents may have found it not important often neglecting the natives true expression. This natives negative experience with this will likely effect their own creativeness, fun and connections with others. You may find it hard to make friends or out yourself in fun environments because of your fear of peoples perception on your fun and goofy behavior or you feel like people wont accept you. These natives also might experience quick burnout within creative pursuits and feel like this area in their life is rejecting itself. These natives have the capability to pour their creativeness into themselves; you just have to unblock this harsh reality in your life and uncover the truths and accept this part in your life. You feel like you may not get to experience fun things like others can.
Having aquarius in the 10th house & 11th house
aquarius in the 10th house: You don't really want to pursue a job that deems as regular. You want something that will feel like it fits you. You don't like pursuing careers (lifetime careers) that will not fulfill you. You may pursue STEM, biology-related, chemistry, artictechture, doctor (depending on cancer and virgo placements) industry-related, creating the new innovation, online business, therapist, anything that involves movies, being internet famous (because of this interception in the 5th you may feel more inclined to pursue creative pursuits, music, writing & expression) Being a project manger, managing business, enterpreneur, producer, activist, game creator, movie director and especially any science related pursuits.
aquarius in the 11th house intercepted: Friends and people can be quiteee confusing with this interception. The thing is people will be fascinated with this native but have many different perceptions. Being popular but not quite fitting in is a theme. Having social anxiety is such a theme with this placement. You could attract friends that are apart of the lgbtq+. You have been popular or a lot of people know you but may have experienced people always being unsure of you and may not even know why. People could be intimidated by your social play in social settings. Friendships can be very confusing and elusive. There may be a constant feeling of obtaining friends but feeling like they don't completely accept you. Feeling not accepted by your community is a huge theme. You feel like a lot of people may not want to pick you. You may find it hard to create superficial relationships, so in result you may just find no purpose in it altogether.
Virgo & Pieces not being your chart
Not having Virgo and Pisces in your house wheel could feel like you lacked stability in your upbringing like so much. You have moved a lot and your parents let you do things yourself constantly and felt like you had to live up to their idea of the independence they handed to you. You had to care for yourself. You could have emotionally unavailable people in your life. When you didn't have the structure you expected it caused you to have to step up and it allowed a unconventional routine for you. You may find it hard to follow a routine and feel like you had to teach yourself the importance of a routine. You may also not like virgo/pieces personalites or placements as you yourself may not be proud of the traits you may have lacked in your life so building yourself up and having someone else naturally display these traits can make natives find it intimating or appealing. You may like structure in partners or creative partners. Your parents could of had a theme of putting love over you or putting substances over you or their dreams. You may have a hard time complying to work schedule sometimes or even school. You feel as though time and routine depends on you and not the day.
written originally by me, don’t not steal writing.
let me know your opinions, did this resonate? :)
#astro observations#astro placements#astrology#natal chart#interception#astrology observations#astrology notes#astro community#virgo#virgo placements#pisces#leo#leo fourth house#leo 5th house#aquarius#aquarius 10th house#aqaurius 11th house#leo aqaurius interception#astrology readings
124 notes
·
View notes
Text
i always took it as read that when helen walks around the wooden horse and entices the men within by calling to them in the voices of their wives, it's got every achaean to a man in there hard as a rock. just a tightly packed hive of miserable hard-ons in there. like being inside one of those sword box illusions, getting poked from every direction
#that's crass i'm sorryyy#i saw someone summarizing the danger of them calling back as if one of them was gonna go 'hi honey! :D' or something#but like. she makes all the men *yearn* for their *wives*. i think a good chunk of that yearning is physical in that moment#odysseus definitely needs to physically intercept one of the men from calling out#when fagles translates it as him abruptly being 'hot to salute' her i'm always like oh i bet 😏#🏷️
62 notes
·
View notes
Text

GOLD RUSH✨✨
#pokemon rejuvenation#<- his ass is NOT intercepting!!!#oc: felice#pokemon#meowth#how many coins are visible in this drawing whoever guesses correctly gets 777 felice relationship points and +100 karma
136 notes
·
View notes
Text
So, how fired, on a scale from one to ten, is Wit for losing: The only two Bondsmiths in the world aka the queen and king of Urithiru, the five year old heir of Alethkar, the Kholin Highprincess, the Kholin spare, and his boyfriend?
#shallan send a message to dalinar not to open the perpendicularity#unless the ghostbloods intercepted Jasnah would know what happened#at least partially#wat spoilers#hoid#the stormlight archive#jasnah kholin#cosmere
123 notes
·
View notes
Text

??? 😭
175 notes
·
View notes
Text
Apple's encryption capitulation

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in NYC on TOMORROW (26 Feb) with JOHN HODGMAN and at PENN STATE THURSDAY (Feb 27). More tour dates here. Mail-order signed copies from LA's Diesel Books.

The UK government has just ordered Apple to secretly compromise its security for every iOS user in the world. Instead, Apple announced it will disable a vital security feature for every UK user. This is a terrible outcome, but it just might be the best one, given the circumstances:
https://www.bbc.com/news/articles/cgj54eq4vejo
So let's talk about those circumstances. In 2016, Theresa May's Conservative government passed a law called the "Investigative Powers Act," better known as the "Snooper's Charter":
https://www.snooperscharter.co.uk/
This was a hugely controversial law for many reasons, but most prominent was that it allowed British spy agencies to order tech companies to secretly modify their software to facilitate surveillance. This is alarming in several ways. First, it's hard enough to implement an encryption system without making subtle errors that adversaries can exploit.
Tiny mistakes in encryption systems are leveraged by criminals, foreign spies, griefers, and other bad actors to steal money, lock up our businesses and governments with ransomware, take our data, our intimate images, our health records and worse. The world is already awash in cyberweapons that terrible governments and corporations use to target their adversaries, such as the NSO Group malware that the Saudis used to hack Whatsapp, which let them lure Jamal Khashoggi to his death. The stakes couldn't be higher:
https://pluralistic.net/2025/02/04/citizen-lab/#nso-group
Encryption protects everything from the software updates for pacemakers and anti-lock braking to population-scale financial transactions and patient records. Deliberately introducing bugs into these systems to allow spies and cops to "break" encryption when they need to is impossible, which doesn't stop governments from demanding it. Notoriously, when former Australian PM Malcolm Turnbull was told that the laws of mathematics decreed that there is no way to make encryption that only stops bad guys but lets in good guys, he replied "The laws of mathematics are very commendable but the only law that applies in Australia is the law of Australia":
https://www.eff.org/deeplinks/2017/07/australian-pm-calls-end-end-encryption-ban-says-laws-mathematics-dont-apply-down
The risks don't stop with bad actors leveraging new bugs introduced when the "lawful interception" back-doors are inserted. The keys that open these back-doors inevitably circulate widely within spy and police agencies, and eventually – inevitably – they leak. This is called the "keys under doormats" problem: if the police order tech companies to hide the keys to access billions of peoples' data under their doormats, eventually, bad guys will find them there:
https://academic.oup.com/cybersecurity/article/1/1/69/2367066
Again, this isn't a theoretical risk. In 1994, Bill Clinton signed a US law called CALEA that required FBI back-doors for data switches. Most network switches in use today have CALEA back-doors and they have been widely exploited by various bad guys. Most recently, the Chinese military used CALEA backdoors to hack Verizon, AT&T and Lumen:
https://pluralistic.net/2024/10/07/foreseeable-outcomes/#calea
This is the backdrop against which the Snooper's Charter was passed. Parliament stuck its fingers in its ears, covered its eyes, and voted for the damned thing, swearing that it would never result in any of the eminently foreseeable harms they'd been warned of.
Which brings us to today. Two weeks ago, the Washington Post's Joseph Menn broke the story that Apple had received a secret order from the British government, demanding that they install a back-door in the encryption system that protects cloud backups of iOS devices:
https://www.washingtonpost.com/technology/2025/02/07/apple-encryption-backdoor-uk/
Virtually every iOS device in the world regularly backs itself up to Apple's cloud backup service. This is very useful: if your phone or tablet is lost, stolen or damaged, you can recover your backup to a new device in a matter of minutes and get on with your day. It's also very lucrative for Apple, which charges every iOS user a few dollars every month for backup services. The dollar amount here is small, but that sum is multiplied by the very large number of Apple devices, and it rolls in every single month.
Since 2022, Apple has offered its users a feature called "Advanced Data Protection" that employs "end-to-end" encryption (E2EE) for these backups. End-to-end encryption keeps data encrypted between the sender and the receiver, so that the service provider can't see what they're saying to each other. In the case of iCloud backups, this means that while an Apple customer can decrypt their backup data when they access it in the cloud, Apple itself cannot. All Apple can see is that there is an impenetrable blob of user data on one of its servers.
2022 was very late for Apple to have added E2EE to its cloud backups. After all, in 2014, Apple customers suffered a massive iCloud breach when hackers broke into the iCloud backups of hundreds of celebrities, leaking nude photos and other private data, in a breach colloquially called "Celebgate" or "The Fappening":
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
Apple almost rolled out E2EE for iCloud in 2018, but scrapped the plans after Donald Trump's FBI leaned on them:
https://www.reuters.com/article/world/exclusive-apple-dropped-plan-for-encrypting-backups-after-fbi-complained-sour-idUSKBN1ZK1CO/
Better late than never. For three years, Apple customers' backups have been encrypted, at rest, on Apple's servers, their contents fully opaque to everyone except the devices' owners. Enter His Majesty's Government, clutching the Snooper's Charter. As the eminent cryptographer Matthew Green writes, a secret order to compromise the cloud backups of British users is necessarily a secret order to compromise all users' encrypted backups:
https://blog.cryptographyengineering.com/2025/02/23/three-questions-about-apple-encryption-and-the-u-k/
There's no way to roll out a compromised system in the UK that differs from non-British backups without the legion of reverse-engineers and security analysts noticing that something new is happening in Britain and correctly inferring that Apple has been served with a secret "Technical Capability Notice" under the Snooper's Charter:
Even if you imagine that Apple is only being asked only to target users in the U.K., the company would either need to build this capability globally, or it would need to deploy a new version or “zone”1 for U.K. users that would work differently from the version for, say, U.S. users. From a technical perspective, this would be tantamount to admitting that the U.K.’s version is somehow operationally distinct from the U.S. version. That would invite reverse-engineers to ask very pointed questions and the secret would almost certainly be out.
For Apple, the only winning move was not to play. Rather than breaking the security for its iCloud backups worldwide, it simply promised to turn off all security for backups in the UK. If they go through with it, every British iOS user – doctors, lawyers, small and large business, and individuals – will be exposed to incalculable risk from spies and criminals, both organized and petty.
For Green, this is Apple making the best of an impossible conundrum. Apple does have a long and proud history of standing up to governmental demands to compromise its users. Most notably, the FBI ordered Apple to push an encryption-removing update to its phones in 2016, to help it gain access to a device recovered from the bodies of the San Bernardino shooters:
https://www.eff.org/deeplinks/2016/02/eff-support-apple-encryption-battle
But it's worth zooming out here for a moment and considering all the things that led up to Apple facing this demand. By design, Apple's iOS platform blocks users from installing software unless Apple approves it and lists it in the App Store. Apple uses legal protections (such as Section 1201 of the US Digital Millennium Copyright Act and Article 6 of the EUCD, which the UK adopted in 2003 through the Copyright and Related Rights Regulations) to make it a jailable offense to reverse-engineer and bypass these blocks. They also devote substantial technical effort to preventing third parties from reverse-engineering its software and hardware locks. Installing software forbidden by Apple on your own iPhone is thus both illegal and very, very hard.
This means that if Apple removes an app from its App Store, its customers can no longer get that app. When Apple launched this system, they were warned – by the same cohort of experts who warned the UK government about the risks of the Snooper's Charter – that it would turn into an attractive nuisance. If a corporation has the power to compromise billions of users' devices, governments will inevitably order that corporation to do so.
Which is exactly what happened. Apple has already removed all working privacy tools for its Chinese users, purging the Chinese App Store of secure VPN apps, compromising its Chinese cloud backups, and downgrading its Airdrop file-transfer software to help the Chinese state crack down on protesters:
https://pluralistic.net/2022/11/11/foreseeable-consequences/#airdropped
These are the absolutely foreseeable – and foreseen – outcomes of Apple arrogating total remote control over its customers' devices to itself. If we're going to fault Theresa May's Conservatives for refusing to heed the warnings of the risks introduced by the Snooper's Charter, we should be every bit as critical of Apple for chasing profits at the expense of billions of its customers in the face of warnings that its "curated computing" model would inevitably give rise to the Snooper's Charter and laws like it.
As Pavel Chekov famously wrote: "a phaser on the bridge in act one will always go off by act three." Apple set itself up with the power to override its customers' decisions about the devices it sells them, and then that power was abused in a hundred ways, large and small:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
Of course, there are plenty of third-party apps in the App Store that allow you to make an end-to-end encrypted backup to non-Apple cloud servers, and Apple's onerous App Store payment policies mean that they get to cream off 30% of every dollar you spend with its rivals:
https://www.reddit.com/r/privacy/comments/1iv072y/endtoend_encrypted_alternative_to_icloud_drive/
It's entirely possible to find an end-to-end encrypted backup provider that has no presence in the UK and can tell the UK government to fuck off with its ridiculous back-door demands. For example, Signal has repeatedly promised to pull its personnel and assets out of the UK before it would compromise its encryption:
https://pluralistic.net/2023/03/05/theyre-still-trying-to-ban-cryptography/
But even if the company that provides your backup is impervious to pressure from HMG, Apple isn't. Apple has the absolute, unchallenged power to decide which apps are in its App Store. Apple has a long history of nuking privacy-preserving and privacy-enhancing apps from its App Store in response to complaints, even petty ones from rival companies like Meta:
https://www.theverge.com/2022/9/29/23378541/the-og-app-instagram-clone-pulled-from-app-store
If they're going to cave into Zuck's demand to facilitate spying on Instagram users, do we really think they'll resist Kier Starmer's demands to remove Signal – and any other app that stands up to the Snooper's Charter – from the App Store?
It goes without saying that the "bad guys" the UK government claims it wants to target will be able to communicate in secret no matter what Apple does here. They can just use an Android phone and sideload a secure messaging app, or register an iPhone in Ireland or any other country and bring it to the UK. The only people who will be harmed by the combination of the British government's reckless disregard for security, and Apple's designs that trade the security of its users for the security of its shareholders are millions of law-abiding Britons, whose most sensitive data will be up for grabs by anyone who hacks their accounts.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/02/25/sneak-and-peek/#pavel-chekov

Image: Mitch Barrie (modified) https://commons.wikimedia.org/wiki/File:Daytona_Skeleton_AR-15_completed_rifle_%2817551907724%29.jpg
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/deed.en
--
Kambanji https://www.flickr.com/photos/kambanji/4135216486/
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
--
Rawpixel https://www.rawpixel.com/image/12438797/png-white-background
#pluralistic#apple#encryption#crypto wars#crypto means cryptography#icloud#lawful access#uk#ukpoli#snoopers charter#matthew green#lawful interception#Investigatory Powers Act#sneak and peek orders#checkovs law#privacy
163 notes
·
View notes
Text
marriage is scary because what if he can’t help our kids with their math homework at the kitchen counter
#isagi only knows abt spatial awareness and the flow state#he does not remember the slope intercept formula
72 notes
·
View notes
Text
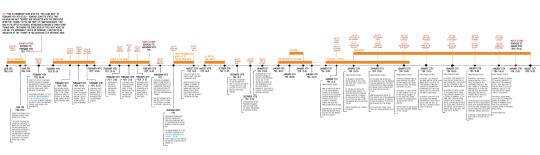
procrastinated on art to finish this, the chronological timeline of the main chapters of the 1.X series. i made this for r99 OC purposes but found out interesting things on the way, either way it was fun!
im planning to continue but the transcript for 2.1 isn't done yet so its very difficult to date both 2.0 and 2.1 as a result. especially since 1.2 ALLEGEDLY has to fit somewhere in there, three events BEFORE 2.2 starts in november
i'll add anecdotes, character events and other things that can be dated within the timeline later on, as soon as i can figure out what to do with 2.0/2.1!
#reverse 1999#reverse: 1999#i have no fucking clue how to tag this#do i even have a tag for shit like this#prince thinks#that works#anyway the fucking prologue and the first chapter have this weird thing abt time hence the big chunk of text#i thought there'd may be more weird time things but it really is just THAT ONE#bc the stages and narration flow naturally as if the storm really took them to 7 am#but then future chapters and trails are like Actually Sonetto Was In Chicago ONE HOUR AND HALF before she meets with vertin#and she meets with vertin at 7:30 am. so she was in chicago at 6 am#like its SUPER important that shes in chicago at this hour bc its when schneiders family gets rejected#and schneider intercepts her mission capsule. which is why things didnt go as the foundation told them. bc schneider was ahead of them
55 notes
·
View notes