#digital identity bill 2024
Explore tagged Tumblr posts
Text

31 notes
·
View notes
Text
Canada sues Google

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/12/03/clementsy/#can-tech

For a country obsessed with defining itself as "not America," Canada sure likes to copy US policies, especially the really, really terrible policies – especially the really, really, really terrible digital policies.
In Canada's defense: these terrible US policies are high priority for the US Trade Representative, who leans on Canadian lawmakers to ensure that any time America decides to collectively jump off the Empire State Building, Canadian politicians throw us all off the CN Tower. And to Canada's enduring shame, the USTR never has to look very hard to find a lickspittle who's happy to sell Canadians out.
Take anti-circumvention. In 1998, Bill Clinton signed the Digital Millennium Copyright Act, a gnarly hairball of copyright law whose Section 1201 bans reverse-engineering for any purpose. Under DMCA 1201, "access controls" for copyrighted works are elevated to sacred status, and it's a felony (punishable by a five-year prison sentence and a $500k fine) to help someone bypass these access controls.
That's pretty esoteric, even today, and in 1998, it was nearly incomprehensible, except to a small group of extremely alarmed experts who ran around trying to explain to lawmakers why they should not vote for this thing. But by the time Tony Clement and James Moore (Conservative ministers in the Harper regime) introduced a law to import America's stupidest tech idea and paste it into Canada's lawbooks in 2012, the evidence against anti-circumvention was plain for anyone to see.
Under America's anti-circumvention law, any company that added an "access control" to its products instantly felonised any modification to that product. For example, it's not illegal to refill an ink cartridge, but it is illegal to bypass the access control that gets the cartridge to recognise that it's full and start working again. It's not illegal for a Canadian software developer to sell a Canadian Iphone owner an app without cutting Apple in for a 30% of the sale, but it is illegal to mod that Iphone so that it can run apps without downloading them from the App Store first. It's not illegal for a Canadian mechanic to fix a Canadian's car, but it is illegal for that mechanic to bypass the access controls that prevent third-party mechanics from decrypting the error codes the car generates.
We told Clement and Moore about this, and they ignored us. Literally: when they consulted on their proposal in 2010, we filed 6,138 comments explaining why this was a bad idea, while only 53 parties wrote in to support it. Moore publicly announced that he was discarding the objections, on the grounds that they had come from "babyish" "radical extremists":
https://www.cbc.ca/news/science/copyright-debate-turns-ugly-1.898216
For more than a decade, we've had Clement and Moore's Made-in-America law tied to our ankles. Even when Canada copies some good ideas from the US (by passing a Right to Repair law), or even some very good ideas of its own (passing an interoperability law), Canadians can't use those new rights without risking prosecution under Clement and Moore's poisoned gift to the nation:
https://pluralistic.net/2024/11/15/radical-extremists/#sex-pest
"Not America" is a pretty thin basis for a political identity anyway. There's nothing wrong with copying America's good ideas (like Right to Repair). Indeed, when it comes to tech regulation, the US has had some bangers lately, like prosecuting US tech giants for violating competition law. Given that Canada overhauled its competition law this year, the country's well-poised to tackle America's tech giants.
Which is exactly what's happening! Canada's Competition Bureau just filed a lawsuit against Google over its ad-tech monopoly, which isn't merely a big old Privacy Chernobyl, but is also a massively fraudulent enterprise that rips off both advertisers and publishers:
https://www.reuters.com/technology/canadas-antitrust-watchdog-sues-google-alleging-anti-competitive-conduct-2024-11-28/
The ad-tech industry scoops up about 51 cents out of every dollar (in the pre-digital advertising world the net take by ad agencies was more like 15%). Fucking up Google's ad-tech rip off is a much better way to Canada's press paid than the link tax the country instituted in 2023:
https://www.eff.org/deeplinks/2023/05/save-news-we-must-ban-surveillance-advertising
After all, what tech steals from the news isn't content (helping people find the news and giving them a forum to discuss it is good) – tech steals news's money. Ad-tech is a giant ripoff. So is the app tax – the 30% Canadian newspapers have to kick up to the Google and Apple crime families every time a subscriber renews their subscriptions in an app. Using Canadian law to force tech to stop stealing the press's money is a way better policy than forcing tech to profit-share with the news. For tech to profit-share with the news, it has to be profitable, meaning that a profit-sharing press benefits from tech's most rapacious and extractive conduct, and rather than serving as watchdogs, they're at risk of being cheerleaders.
Smashing tech power is a better policy than forcing tech to share its stolen loot with newspapers. For one thing, it gets government out of the business of deciding what is and isn't a legit news entity. Maybe you're OK with Trudeau making that call (though I'm not), but how will you feel when PM Polievre decides that Great Replacement-pushing, conspiracy-addled far right rags should receive a subsidy?
Taking on Google is a slam-dunk, not least because the US DoJ just got through prosecuting the exact same case, meaning that Canadian competition enforcers can do some good copying of their American counterparts – like, copying the exhibits, confidential memos, and successful arguments the DoJ brought before the court:
https://www.justice.gov/opa/pr/justice-department-sues-google-monopolizing-digital-advertising-technologies
Indeed, this already a winning formula! Because Big Tech commits the same crimes in every jurisdiction, trustbusters are doing a brisk business by copying each others' cases. The UK Digital Markets Unit released a big, deep market study into Apple's app market monopoly, which the EU Commission used as a roadmap to bring a successful case. Then, competition enforcers in Japan and South Korea recycled the exhibits and arguments from the EU's case to bring their own successful prosecutions:
https://pluralistic.net/2024/04/10/an-injury-to-one/#is-an-injury-to-all
Canada copying the DoJ's ad-tech case is a genius move – it's the kind of south-of-the-border import that Canadians need. Though, of course, it's a long shot that the Trump regime will produce much more worth copying. Instead, Trump has vowed to slap a 25% tariff on Canadian goods as of January 20.
Which is bad news for Canada's export sector, but it definitely means that Canada no longer has to worry about keeping the US Trade Rep happy. Repealing Clement and Moore's Bill C-11 should be Parliament's first order of business. Tariff or no tariff, Canadian tech entrepreneurs could easily export software-based repair diagnostic tools, Iphone jailbreaking tooks, alternative firmware for tractors and medical implants, and alternative app stores for games consoles, phones and tablets. So long as they can accept a US payment, they can sell to US customers. This is a much bigger opportunity than, say, selling cheap medicine to Americans trying to escape Big Pharma's predation.
What's more, there's no reason this couldn't be policy under Polievre and the Tories. After all, they're supposed to be the party of "respect for private property." What could be more respectful of private property than letting the owners of computers, phones, cars, tractors, printers, medical implants, smart speakers and anything else with a microchip decide for themselves how they want to it work? What could be more respectful of copyright than arranging things so that Canadian copyright holders – like a games studio or an app company – can sell their copyrighted works to Canadian buyers, without forcing the data and the payment to make a round trip through Silicon Valley and come back 30% lighter?
Canadian politicians have bound the Canadian public and Canadian industry to onerous and expensive obligations under treaties like the USMCA (AKA NAFTA2), on promise of tariff-free access to American markets. With that access gone, why on Earth would we continue to voluntarily hobble ourselves?
#pluralistic#link tax#big tech#corruption#canpoli#cdnpoli#monopolies#ad-tech#publishing#canada#competition bureau#usmca#nafta#anticircumvention#r2r#right to repair#interoperability
272 notes
·
View notes
Text
I'm sure many of you are already aware of this, but in case I have any newer tumblr users, pet bill donation scams are very common on this site. If someone DMs or sends you an ask asking you to reblog some sort of donation post for a sick/injured pet, it is most likely a scam.
Below the cut, I have included tips to spotting a scam, and why I believe the post by 507-on-queue is a scam. @kyra45 runs an excellent tumblr scam awareness blog, and has more information and tips here about spotting pet scams. I have archived the scam post in question on my side blog here.
Here's some ways to spot these scams:
Age of the blog - most scam blogs are a week old or younger, they are often under a day old
Similar urls being used for multiple blogs - scam blogs are typically blocked/deleted rapidly, and the OP makes a new account with almost the same name
The blog bio/pfp are not unique
You can only access the dashboard view of the blog so the post archive cannot be accessed (for example, my dashboard view is this, but you can also visit my webpage view and see my 9 years of post history via /archive lol)
The blog has never interacted with you before
The blog follows you and immediately sends a DM/ask
The DM/ask is overly polite and guilt trips (they often ask you to reply privately to reduce digital footprint)
Images of pets can be found via reverse image search
OP's story is inconsistent or unrealistic
The Paypal link does not match the supposed country OP lives in
Most recently, a scam post has been going around about a sphynx cat named Draven. This has been done using multiple urls, including:
meer-lion (deactivated)
507-on-queue (deactivated)
507onqueue (deactivated)
507-onqueue (current as of Jan 13th, 2024)
Here's how this blog meets our scam watch criteria:
The current blog (507-onqueue) is less than a day old (19 hours at the time of this post). The oldest post:
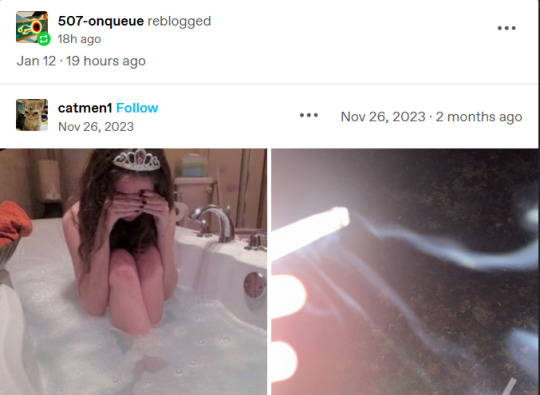
As listed above, OP uses multiple, similar URLs.
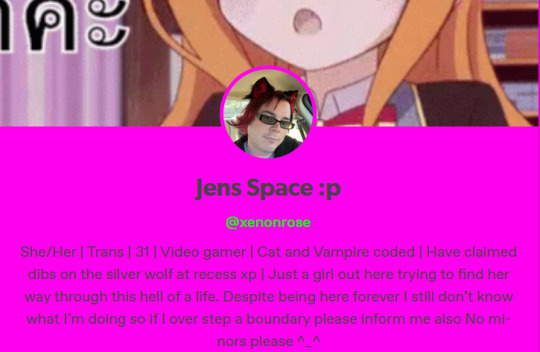
The bio of 507-onqueue is taken almost directly from another user (said user). Due to the same bio being used in previous scams, I suspect this is the same or related person to kappa-tundra/kappatundra (about this scam).
Scam blog:

Copied blog:
Only dashboard view is available.
The blog follows and immediately DMs/sends and ask. From my account:
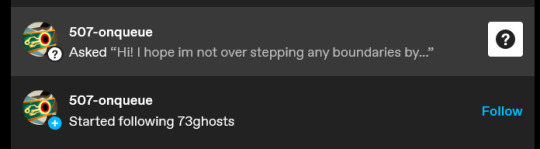
The ask from the account is very polite, guilt trips, and asks me to answer to the post privately. The goal of being so polite is to win your trust and lower your defenses. This isn't the worst guilt trip I've been in a scam (that goes to the child support scam from several years ago). By asking me to reply privately, they're attempting to reduce their digital footprint (making them harder to google) and disguise how much they are spamming asks.

The information in that post was taken from a private Facebook account (source). I found the Facebook account in question and confirmed that the information was taken from there. I do not want to share the page because I view that as a further violation of the Facebook OP's privacy. For transparency, the images of Draven are not on Facebook OP's page any longer, but there are several other identifiable pieces of information that make it more than likely that the claims of her information being stolen are true.
The ask is inconsistent itself with the name of the cat (Draven vs Indie). This is also nearly identical to another scam ask from user captbridges. This user was using a real GoFundMe for a sick cat to scam.
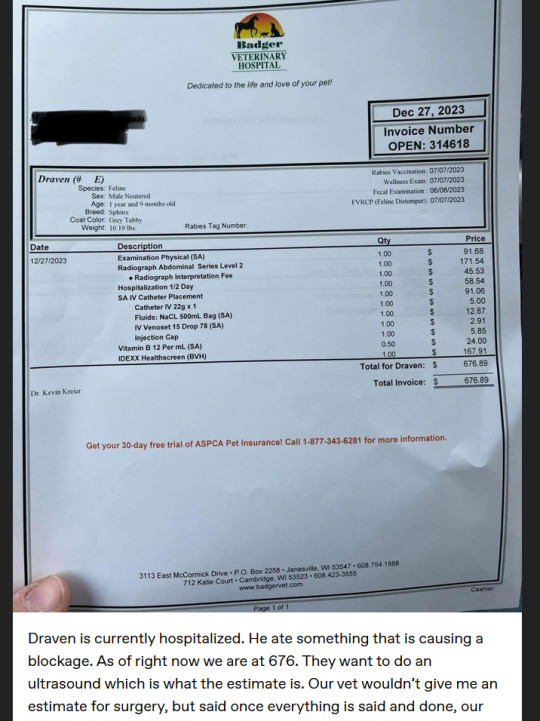
The medical paperwork in OP's post is for a veterinary hospital in Wisconsin. However, OP's PayPal is based in the Philippines. The country.x= part of the url indicate the country of origin of the account; PH is the Philippines. The local.x= part of the url shows that the link was localized to the United States (making the donation currency USD). (PayPal's information page about country codes).

Stay safe out there and remain vigilant, everyone. If you don't already know them, try to pick up some boolean operators to refine your google searches when checking for scams. The tumblr search function sucks, so this is your best bet of finding information about scams like these online.
#meer-lion#507-on-queue#507-onqueue#507onqueue#scam alert#scam#You all can feel free to reblog this if you want#I normally make posts like this when a scam comes my way#But I haven't actually seen one in a while lol
242 notes
·
View notes
Text
Webcomics at Day 100 #1: Kevin & Kell

Pages read: 9/3/1995 – 9/3/1996 & 4/13/2009 – 8/18/2009; about 380 pages
Reason for selection: Best I can tell this is the oldest webcomic that’s still running as well as among the first ones made. It updated every weekday from 1995-2000 and every day since then without breaks, totaling around 4500 strips as of 2009 and 10,000 strips as of 2024. This webcomic is older than I am and has been around for over 90% of the internet’s public history. While not originally intended as a ‘furry comic’ it quickly gained popularity among furries, who are an important internet subculture. K&K meetups happened at furry conventions in the 2000s.
Current status: This comic is an eternal truth of the internet
Content warnings: predator/prey dynamics
Overall thoughts: I think this strip is charming. It’s functionally identical to a newspaper strip, and there’s nothing about its presentation that couldn’t be done in print – which makes sense as its creator was already a newspaper cartoonist before starting this. Being published on the internet allows readers easy and instant access to the archives without having to buy the newspaper each day, although the sections I’ve read don’t take advantage of this by having long running storylines that require reading the archive. There is overall continuity, but jumping from 1996 to 2009 wasn’t super confusing. At the time of writing this the website is quick to load, well organized and really easy to navigate, so it’s no work at all to just start reading and get lost in the comic.

Content wise, the strip features anthropomorphic animals living in modern society (humans appear to be mythical creatures?) and includes a lot of jokes about animal traits manifesting in school, work and day to day life. Some specific jokes such as the hedgehog character getting stuck to things with her many spines are used often. Quite a few jokes rely on the fact that a significant portion of society are killing and eating the other portions on a daily basis, which is written in a lighthearted way but won’t be to everyone’s taste. I’d also describe the comic as ‘boomer humor’ in some places. Bill Holbrook began writing the strip in his late 30s so is older than the average early webcomics artist, and writes about family and technology from that perspective. The content also focuses on both nontraditional relationships and traditional family dynamics, and the ways these rub up against one another, while avoiding any genuinely controversial topics.
I love how Holbrook draws rabbits – Kevin and baby Coney’s designs are adorable to me and are the visual highlights of most strips. The character R.L., wolf and CEO of Herd Thinners Inc., is never shown in full – only his drooling mouth, fangs, and hands clasped on his desk are shown, which kicks ass as a villain design. Holbrook is also really good at conveying a character’s overall mood or vibe just through their body language in a still image, which is impressive considering how many different species he’s working with. The comic began in black and white and switched to color in 2000, and while I don’t think the color significantly improves the strip, it does make it easier to distinguish between characters of similar species as the cast has grown.

Connections to Homestuck: K&K doesn’t use the affordances of the internet (such as including gifs/sound in the comic) but it is definitely about the internet. It’s established imemdiately that titular couple Kevin & Kell first met and fell in love online, and that Kevin’s job is the system operator for the ‘herbivore forum.’ Kevin attends an online high school reunion, daughter Lindesfarne (INCREDIBLE character name) attends a virtual prom, and son Rudy stays in touch with his long distance girlfriend via email. Jokes about online life being inferior to digital are rare, and spending a lot of time online is normalized within the world of the comic, a decade or two before it became normalized in the real world.
K&K also plays with the boundary between digital and real space, and commonly depicts a character typing something into the computer to cause a physical effect in the world far away. Computers physically react to the digital content they are used for, such as Kevin’s computer starting to grow leaves and plants when he spends too much time on the herbivore forum, and digital phenomena are represented physically such as this depiction of a firewall:

I don’t think Rudy and Dave are the exact same archetype but Rudy does wear sunglasses 24/7 and is a different flavor of above it all coolguy whose feelings aren’t as secret as he thinks.
Continue reading? Probably! Despite being loosely drawn archetypes I did start caring about the characters quickly, enjoyed reading enough to go well past day 100, and have marked my place to come back to. It’s sweet and low effort entertainment that I can easily see myself digging into when I’m tired or sick.
I have sponsored today’s update which only costs $5 and is a small contribution to webcomics history.

25 notes
·
View notes
Text
Across the internet, communities of queer and trans youth have mobilized to oppose KOSA as the legislation became increasingly entangled in longstanding culture war debates over sex education and queer visibility in schools.
By Mike Ludwig , Truthout Published August 13, 2024
Despite many changes to the bill’s language since it was first introduced in 2022, KOSA continues to face stiff opposition from LGBTQ and digital rights groups. They take umbrage with the bill’s so-called “duty of care” provision for content recommendation, which makes internet companies responsible for designing their products to mitigate for broad threats to minors, such as “suicide,” “gambling” and “sexual exploitation.” Digital rights groups argue the provision would encourage tech companies to overcorrect and respond to threats from politicians by censoring reproductive and mental health resources, particularly for transgender youth and others who rely on the internet for support and information to navigate the marginalization of their identities. Across the internet, communities of queer and trans youth have mobilized to oppose KOSA as the legislation became increasingly entangled in longstanding culture war debates over sex education and queer visibility in schools. “The changes that I, LGBTQ+ advocates, parents, student activists, civil rights orgs, and others have fought for over the last two years have made it less likely that the bill can be used as a tool for MAGA extremists to wage war on legal and essential information to teens,” Wyden recently wrote on social media. “While constructive, these improvements remain insufficient.” Wyden and LGBTQ rights groups have reason to worry. Sen. Marsha Blackburn, a Republican from Tennessee who worked with Democrats on KOSA, said in 2023 that the bill could be used to censor content and shield young people from “indoctrination” and, as she put it, “the transgender.” After Democrats updated the bill earlier this year in an attempt to appease LGBTQ groups, Republicans, fed a diet of online misinformation about queer people, began to see KOSA as part of some liberal conspiracy to promote gender nonconformity, which does not exist.
#kosa#queer#lgbqti#protest#lgbt#trans#lgbtq#kosa bill#stop kosa#kids online safety act#bad internet bills#kids online safety bill#censorship#privacy#marsha blackburn#ron wyden#gop#republicans#maga#democrats#internet#legislation#2024
25 notes
·
View notes
Text
The thoroughly Technocratic “Digital Public Infrastructure” (DPI) originally slid in on the back of the global warming hoax. Unaccountable and unelected Bill Gates is rebranding the effort with his Modular Open-Source Identity Platform (MOSIP).
On 1-3 October, the Global DPI Summit 2024 was held in Cairo, Egypt. The principal sponsor was a NGO called Co-Develop Fund, who promised to,
… bring together key stakeholders from the public, private, and civil society sectors, including:
Countries: Countries that are seeking best-in-class approaches to digitization.
Bilateral and multilateral institutions: Institutions that support country governments in their digitization efforts.
Open-source digital public good providers: Providers of scalable digital solutions that can be used by countries to implement DPI.
Private sector companies: Companies with the expertise and capacity to help governments implement digital solutions at a population scale.
Civil society actors: Actors who are working to ensure that DPI is implemented in a way that is inclusive and protects the rights of all citizens.
Global DPI thought leaders: Experts on DPI who can provide valuable insights and guidance to countries on their DPI implementation journeys.
Domain-focused actors: Actors who are working to implement DPI solutions in specific sectors, such as education, healthcare, and agriculture.
⁃ Patrick Wood, Editor.
Microsoft co-founder Bill Gates is pushing governments to adopt the new global system for digital cash and ID that is backed by the World Economic Forum (WEF).
Gates and his foundation are doubling down on support for s digital public infrastructure (DPI).
DPI supports both digital IDs and payments and is backed by the WEF, the European Union (EU), and the United Nations (UN).
Gates is now pressuring governments around the world to begin incorporating DPI as the globalist groups push for payments and IDs to switch to a fully digital system on a global level.
The billionaire laid out his vision for global DPI in a new blog post.
The Silicon Valley oligarch is once again attempting to establish his reputation as a visionary on these matters.
Gates praised several third-world “developing countries” for allowing DPI to be tested on their citizens.
He revealed that the system has already been “trialed for the rest of the world” in India, Kenya, Brazil, and Togo.
One of the major criticisms leveled at digital IDs and payments is that they will lead to “enhanced,” digital government surveillance, and subsequent disenfranchisement of people.
Many have also raised concerns about the rush to usher in the technology.
Globalists have been pushing for DPI to be rolled out globally for large-scale adoption by 2030, ostensibly to fight “climate change.”
However, Gates does not share these concerns about the technology and is heavily pushing for DPI to be rolled out for the general public.
According to Gates, citizens should not be concerned about government surveillance because “a properly designed” DPI will in fact “enhance” privacy.
He claims DPI includes “safeguards” which he didn’t elaborate on.
Gates also touches on what he says are the benefits of using Modular Open-Source Identity Platform (MOSIP).
MOSIP is a global digital ID tool backed by the Gates Foundation.
However, MOSIP is yet another point of contention from the privacy standpoint.
But MOSIP featured as a key participant during the recent Global DPI Summit 2024 held in Egypt.
At the event, those behind MOSIP, as well as the World Bank, the UN’s development agency UNDP, and the globalist Tony Blair Institute all took part.
The event provided another opportunity for these organizations to push for global adoption of DPI by 2030.
In addition, the organizations pledged to work on accelerating this process.
MOSIP demonstrated its identity platform at the summit.
At the same time, it stressed that the goal of digital ID and payments is to improve accessibility of identification, “particularly for developing nations.”
The platform is already in use in Ethiopia, Morocco, and Sri Lanka.
Meanwhile, the World Bank announced that it is about to launch its own global Digital Public Infrastructure (DPI) program.
Read full story here…
3 notes
·
View notes
Text
Bill Blake [FNAF, Renegade AU]

https://www.deviantart.com/paigelts05/art/1104060944
Published: Sep 29, 2024
William Blake, whom prefers to be called Bill, is a friend of William Afton's. Whilst a people pleasing pushover, he's only a people pleaser to those who stand to benefit him. Else, he'll just use you. Whilst is is a rather proficient manipulator, sometimes his attempts are pathetic. Now onto his story.
He was around 20 in the mid-80's. He knew about the bite, he knew about one of the robots allegedly being haunted, but his interest in Freddy's and William was truly piqued after five kids went missing. After hearing rumours of nightmarish robots and catching wind of the digital consciousness transfer experiments, he wanted in on it. Come 1987, he managed to track down William, who had been masquerading as a nobody named Dave Miller whilst operating Faz Ent from the shadows.
Bill had connected the dots between the vanishing of William Afton and his comatose son David, and the emergence of Dave Miller and his not comatose son Evan: the Millers were occupying the same now abandoned Afton household, 'Evan' had scars that lined up with the injuries from the big bite, and 'Dave' was covered in springlock scars, and only a handful of people had survived a full body springlock failure, so the suspect list was limited. The conclusion was obvious.
Upon approaching William, the man almost killed Bill, thinking that he was an investigator, but once Bill revealed that he found William's work interesting and wanted to help him, William was much more receptive of what Bill had to say, and he let Bill join Faz Ent's inner circle.
Bill dealt with a handful of behind the scenes work, acting on William's behalf as William took on several fake identities. Bill made sure that new establishments ran whilst William was 'MIA'.
Meanwhile, he also was working on his own 'project'. William had a fourth child whom he had 'adopted' in the very early 80's after her parents suffered a 'tragic accident' at a business meeting. William had raised this daughter to help him cover up his crimes. Bill decided that a child of his own would be beneficial. He decided that 'suprise adoption' would be too risky, so he simply charmed a woman around his age who; this woman was Joy Diego, the daughter of the late Ina Diego. The women of the Diego family had always been susceptible to possession, so she was a perfect target. Faz Ent had tried to hire Joy after her mother's death because of her susceptibility to possession, but she'd gotten away. Some time between then and now, Joy had gone blind, so he knew that she wouldn't recognise him, not that their paths crossed back then anyway. They got together, and had a child. Joy wanted to call their child Sylvia, but Bill wanted to name their daughter after William's fourth child (not that he'd tell her his reasons for the name). They compromised to name their daughter "Sylvia Vanessa Blake", but Bill switched the forename and middle name on the birth certificate. Four years later, Bill divorsed Joy as her connections to those who wished to bring down Faz Ent was becoming a real risk to his safety. To secure his custody over his daughter, he threatened his attorney, the judge, and his daughter to comply with his lies against Joy Diego that should ruin her life. However, when he felt as if victory was in his grasp, his own daughter betrayed him and revealed his ploy and that Joy was innocent of everything that she had said and that Bill had threatened her. This made his attorney reveal that himself and the judge had been threatened too. The judge, however, was terrified of Bill, so gave him custody anyway. The judge stepped down from his position of judge a few months later, but Bill had gotten what he wanted.
Even though he now had to stay on the move, his job of checking on Freddy's locations was perfect for that. Even though most of them had closed by now - with only a handful remaining open - he had to check in on each location with near identical frequency, regardless of whether it was open for business or not. This constant mobility also came in handy, as he begun to put Sylvia (he calls her Vanessa) through electroshock 'therapy' to try and make her mote obedient. It failed, and after Sylvia met Vanessa Shelly, the woman whom Bill had named Vanessa Syivia Blake after, Sylvia kept on trying to run away. Whilst Bill had been able to recapture his 'wayward' daughter every time, once she turned 16, she escaped for good.
Bill was furious, but he was busy dealing with Faz Ent's current plans for the future and keeping tabs on Faz Ent locations to have the time to care: he knew who she'd been talking to, and he knew where she would have gone, so he already accepted that he had no shot at dragging Sylvia back this time.
Some years later, a fortunate coincidence struck: his daughter had been investigating an old Faz Ent HQ and been captured by the robots - which were all under the direct control of the science team. However, when he went to visit his daughter and give her a warm welcome to the Fazbear Family, he found out that she had escaped. The scientist in charge, Alistair Anadem, wasn't bothered as she'd gotten the stem cell sample that she wanted, but Bill was fuming. But with nothing he could do about it (the science team was under Adelaide's control, not William's, no matter how much the two work together), all he could do was suck it up, as it wasn't all bad. Alistair used the extracted stem cells to synthesise a person, and Al even gave the girl Bill's surname. The kid, a girl who was given the name Cassie Blake, was trained in the labs to be a killer, but six years later, Alistair and the girl went missing, and only the doctor returned. Bill was once again fuming.
A few years later, Bill had yet another stroke of luck. Faz Ent was making a means to allow William to not only escape the ghostly predicament he'd had himself in, but also the freedom to choose a new host for himself. The details of William's ghostly predicament are that there is something within the code of the animatronic chip that he was trapped in that keeps him trapped, and he needs a third party to escape. So Faz Ent devised a plan of creating a VR game that pulled triple duty: a cover up for Faz Ent's crimes, allow William to escape from being trapped in the old spring bonnie chip, and if all goes well, allow William to possess anyone in the world.
And the development team that this game was handed to after the first few teams 'expired' was none other than Silver Parasol: a small company of four, and one of those four was his wayward daughter Sylvia.
Bill had hoped that William would posess her, and when he received news that she had been posessed, he was ecstatic. For the whole of ten seconds, as he was also informed that about two days after she had been posessed, her friend Cassey Tapper had managed to push William back into the computer. After listening to the rest of what Dale had to say, he found a lot of the information infuriating.
He learned that Sylvia was not as susceptible to possession as her mother and grandmother (as it turns out, she got more than her hair colour from Bill).
He also learned that Joy had remarried shortly after his and Joy's divorce, so Syivia now had a half sister, also bearing the forename Vanessa (named after what Joy believed to be the middle name of her first child).
He also learned that it was that half sister who was both susceptible to possession AND wound up posessed by William and unable to force him back into the game.
Upon learning that last part, Bill changed his tune. He could get Sylvia's half sister Ness to be the pawn that he wanted, AND he could use that to blackmail Sylvia into the same position.
It took a few years for the peices to fall into place, and William controlling Ness, but he finally managed his goal of having Sylvia fully working for him. However, it was a mutual blackmail agreement: Faz Ent had Ness, which was Bill's blackmail against Sylvia, but Sylvia had 28 years worth of evidence of many terrible things against Bill. The safety of a sister Vs 28 years of shit looming over one's head. Sylvia got her position as a guard (head guard no less) at the megaplex, and all she had to do was some delivery errands for her father. Meanwhile, Bill had to get her that security guard position (Bill had to pull a favour from William for that one) and not rat her out to the execs that managed the megaplex. A part of this deal also protected Sylvia from the mass layoffs. Well, it protected her as far as it ment that she'd keep her job: she still had to fight in order to live to see the light of day like the others.
However, Bill also took advantage of the situation and had execs spike Sylvia with remnant, in hopes of it making her more 'manageable'
About a week after the mass layoffs, everything went to shit.
He was partially to blame.
Cassie, the MIA assassin girl, has returned, and Bill had managed to put her in the VR environment, yet unbeknownst to him, that was exactly where she wanted to be.
An 'incident' caused partially by outside interference and partially by letting Cassie into the VR environment caused a domino effect. Whilst the details were unknown to Bill, all he knew is that Cassie saved a young boy from Faz Ent's VR environment, and then that young boy went on to indirectly collaborate with Sylvia in freeing Ness from William.
With all his power over Sylvia dissolved in one night, he was so pissed that he wasn't even mentally present when he was informed that a Raid on the megaplex had taken place. With William now in dire straits again, about to lose use of the Burntrap body, Bill thought it was over. Until Cheryl informed him of the counterattack plan: if they could recapture Ness, Sylvia and that boy, named Gregory, would surely follow. Plus, as Gregory and Cassie were friends, then she would follow suit soon after.
Bill was glad of the plan, and whilst Cheryl M, Todd C, and Charles R were dealing with kidnapping Ness, Bill was making preparations for Sylvia and Gregory's inevitable attempt to take Ness back. Everything went well for Faz Ent.
Until the point where Sylvia, Ness, and Gregory had more fight in them than what Faz Ent had hoped. Ness was hardly fazed by Todd's crude attempt at vivisecting her to see "how Vanny functioned". The control device Charles R jammed onto Sylvia got blocked by the remnant that she'd been injected with, letting her reject Adelaide's control, but not without side effects. Sylvia and Ness then saved Gregory from Cheryl. To make it worse, Sylvia had now job-hopped to being a demolitions expert, and due to the control device blocking Sylvia's impulsive control, she set off some of the demolition explosives when everyone was still inside!
Fortunately, nobody died, but the megaplex was left in such a state that navigation was nigh-impossible without Adelaide's assistance.
But at least Cheryl was able to give Bill the clips of Gregory's voice. Clips they could use to lure Cassie to the labs. So Bill left a Roxie-talkie near the elevators in the megaplex's lobby, and with a regular walkie-talkie, he sent out the initial distress signal to outside the megaplex, then used the clips via the walkie-talkie to communicate with Cassie via the Roxy-talkie and lure her down.
Though he wasn't the only one who wanted to bring Cassie down to the labs. Tech Exec Burrows had his pet project, the mimic, wrecking havoc and complicating things. As the mimic became more and more of a potent threat to William and Cassie, Bill wound up cutting the elevator.
After watching Sylvia jump into the elevator shaft to find Cassie, Bill slowly lowered himself down to assess the damage, only to fortunately find Cassie alive and well already having a conversation with Sylvia.
Due to the dire straits, Cassie actually voluntarily agreed to work with William on the matter of eliminating the mimic, and by extension, Sylvia also agreed to work alongside Faz Ent for this matter only. He was, however, annoyed at William for how he felt the need to further terrify Sylvia and Cassie with the finer details of the control device and MXES respectively.
Bill didn't feel much of anything at Burrows's death. But he did feel abject terror when the mimic begun chasing him and the others down.
After hiding in the scoping room and watching Cassie push the button to kill the mimic, a sense of calm washed over him. He was alive, his daughter and granddaughter were alive. And now was the time for just getting out of the megaplex because it had been over thirty eight since he'd last showered and with being in the grimy labs for at least the past twenty-something of them, he REALLY needed to get cleaned up.
During the long track out, Bill chipped Cheryl to make her an AR mask wielder to make their escape easier. Bill and Alistair had been the ones who had been working on Faz Ent's VR environment since its infancy, so Bill knew enough about it.
Once down the stairs that were only visible through the VANNI network, and after Roxy used Sylvia's grappling hook to take them the rest of the way, Bill left the scene after hearing some choice words from his daughter. It was clear that she was not willing to join Faz Ent still.
He returned to HQ, and after a long bath, he begun trying to plan how to being Cassie back to Faz Ent, but has not yet come up with a decent plan.
#art#artwork#fnaf#fnaf au#renegade au#fnaf renegade au#fnaf fanart#fnaf security breach#fnaf sb#fnaf patient 71's father
2 notes
·
View notes
Text


Nostalgic Sound Review Round-Up
Profiler - A Digital Nowhere
A couple of albums came out recently that both fit the bill for being in the vein of having a nostalgic sound, regardless of the style, and I wanted to talk about both albums briefly, because I don’t have a whole lot to say about either album, but I’d like to talk about them. Both of these albums are very similar, yet they’re also relatively different. The first album I wanted to talk about is the debut from British nu-metal band Profiler, entitled A Digital Nowhere, and this band came to my attention out of nowhere, just from seeing this album pop up on Apple Music. They’re signed to SharpTone, which was a big reason as to why I decided to check this out, and this album is a solid little nu-metal / nu-metalcore album that also incorporates some shoegaze and grunge. If you love bands like Korn, Deftones, Linkin Park, and all things late 90s and early 00s, you’ll dig this. You can pinpoint a lot of their influences, but it never becomes annoying, it’s just cool hearing a lot of different influences instead of one or two key ones, and leaving it at that. This album is a lot of fun, even if the album’s rapped sections aren’t great, but they’re fine for what they are.
The Requiem - A Cure To Poison The World
On the other side of the spectrum, you got The Requiem, a band that sounds like they should have been huge in the early 00s, and their debut album, A Cure To Poison The World. Think if My Chemical Romance, Hawthorne Heights, and The Used kept making melodramatic post-hardcore albums in 2024, and that’s how this would sound. It’s big, epic, catchy, melodramatic, and everything you’d expect from an album in that vein. For that, it’s a lot of fun, even if it sounds like stuff I’ve heard before, but hearing it now with a modern flair is really cool. I have to give this band credit for not trying to sound exactly like the past, either, so the album never comes off as parody or satire, but they play it straight. The album is executed well, so I can’t fault it for that. So-called “elder emos,” which is a phrase that makes me cringe when I hear it, although I get why people use it, should really enjoy this, because it sounds like music that they would have consumed 20 years ago, yet it still has a modern flair behind it that fans of newer music would enjoy, too. It’s not perfect, as they don’t have too much of an identity yet, but I’ll give it another album and they’ve got some potential there.
#profiler#a digital nowhere#the requiem#a cure to poison the world#post hardcore#nu metal#metalcore#rock#alternative rock#my chemical romance#taking back sunday#limp bizkit#deftones
2 notes
·
View notes
Text
Right, let me debunk some of this.
This isn't a law, this isn't even a bill. It's a proposal to pass legislation. (See the official media release from government here. and the full news conference is available here.) It's not in effect. There has been no vote on it because it hasn't been passed into law. The proposed legislation is expected to be put to the parliament during the first week of the next parliamentary sittings, which means we can expect to see the full text somewhere between November 24-27. Feel free to @ me after that date and I'll pull up the bill for you, but if you want to do it yourself here's where you can find the full text of every single bill before the parliament at any given time.
Secondly, the method of determining people's ages is currently under debate. Many have been proposed, including building further on the previously proposed age assurance trial. By the way, if anyone wants to throw the Senate Committee hearing with Greens senator David Shoebridge questioning Jenny McAllister at me, then no, what he was implying is not right. The e-safety commissioner's 2023 roadmap for age verification supports a double-blind approach using tokens. People would verify their ages with a third party who already has their age data (e.g. bank, phone company) who then issues a token that gets used as a digital confirmation of users being of age. This is to ensure that age-restricted websites do not know the identity of a user, and the age assurance service provider does not record which sites a user visits. That's the theory and a tender was awarded to ACCS on November 15, 2024 to test the process and see if it will work.
Finally, this is a proposal with no teeth: 'There would be no penalties for users who managed to access social media under the age of 16, or their parents, but Rowland said there would be penalties for platforms that did not heed the new laws.' (quote taken from an article by the Guardian.) If this proposal was passed into law as it stands now - you could break the law and no one would do anything apart from tut at you. Because it's unenforceable.
So yeah, don't worry that this is a problem now because it's not.
This entire proposal is a signal flag for the 2025 federal election by both Labor and the Coalition parties to tell the voting public that they take parental concerns seriously... without doing anything to actually alleviate those concerns.
Concentrate instead on contacting your federal MPs and telling them exactly how you'd like the original problem - kids being exposed to unsuitable material on social media and the mental health consequences.
tl:dr - Don't get side tracked by this furphy, do your research and go tell your MP what YOU want.
fucking australia’s trying to get everyone to link their government id to their social media accounts else you cant use them anymore, the actual fuck is wrong with this country
#Australia#auspol#Australian politics#social media ban for under 16s#social media#age verification roadmap#age assurance trial#stop. think. check.#tackling misinformation#not mine#but I debunked it
30K notes
·
View notes
Text
"🔥🔥🔥BREAKING
At 4.50pm this afternoon, and with only token opposition from the Liberals & Nationals the Digital ID Bill was passed by the Parliament.
A sad day for Australia, as the nation marches further down the road towards a totalitarian society.😥
And never forget tricks used to stifle debate and public discussion.
Contrary to precedent, the spirit of the Constitution and Westminster tradition, Labor introduced the Digital ID in the Senate (the House of review) instead of the House of Representatives.
Then they guillotined debate in the Senate.
And in House of Representatives, Labor shifted debate to the Federation Chamber where the Liberals put up token resistance with only one Liberal MP and two National MP’s bothering to speak on the Bill - and they didn’t even try any amendments to protect privacy or to try and safeguard against it being made compulsory." - Craig Kelly.
7 notes
·
View notes
Text
This day in history

Picks and Shovels is a new, standalone technothriller starring Marty Hench, my two-fisted, hard-fighting, tech-scam-busting forensic accountant. You can pre-order it on my latest Kickstarter, which features a brilliant audiobook read by Wil Wheaton.

#1yrago Kickstarting "The Bezzle" audiobook, sequel to Red Team Blues https://pluralistic.net/2024/01/10/the-bezzle/#marty-hench
#5yrsago The Monsters Know What They’re Doing: an RPG sourcebook for DMs who want to imbue monsters with deep, smart tactics https://memex.craphound.com/2020/01/10/the-monsters-know-what-theyre-doing-an-rpg-sourcebook-for-dms-who-want-to-imbue-monsters-with-deep-smart-tactics/
#5yrsago For the first time, you can search the database of money that publicly funded researchers in Illinois received from pharma companies https://www.propublica.org/article/dollars-for-profs-illinois-professors-conflicts-of-interest
#5yrsago A company that makes spy-tech for cops threatened to sue Vice for publishing its sales literature (because Iran!) https://www.vice.com/en/article/this-secretive-surveillance-company-is-selling-cops-cameras-hidden-in-gravestones/
#5yrsago Virgin’s subsidized smartphones come with unremovable Chinese malware https://www.zdnet.com/article/unremovable-malware-found-preinstalled-on-low-end-smartphone-sold-in-the-us/
#5yrsago Pranksters produce enlistment ads featuring Trump Jr: “I’m not enlisting but YOU should” https://www.huffpost.com/entry/donald-trump-jr-army-enlisting-sign-pranksters_n_5e1874f1c5b650c621dd0041
#5yrsago Howto: file your taxes for free without getting defrauded into paying a big tax-prep firm https://www.propublica.org/article/how-to-file-state-federal-taxes-free-2020#175169
#5yrsago Boris the Babybot: a picture book about resisting surveillance https://memex.craphound.com/2020/01/10/boris-the-babybot-a-picture-book-about-resisting-surveillance/
#5yrsago NYPD ordered to disclose records of secret X-ray vans https://www.propublica.org/article/judge-orders-nypd-to-release-records-on-x-ray-vans
#15yrsago If HP Lovecraft wrote C manuals http://www.bobhobbs.com/files/kr_lovecraft.html
#15yrsago Britain’s Digital Economy Bill will cost ISPs £500M, knock 40K poor households offline https://torrentfreak.com/piracy-surcharge-set-to-force-40000-households-offline-091228/
#15yrsago Bugs in the Arroyo: sf podcast about metal-eating bug apocalypse https://reactormag.com/bugs-in-the-arroyo/
#15yrsago Slovak aviation cops sneak explosives into travellers’ luggage, jailarity ensues http://news.bbc.co.uk/2/hi/europe/8441891.stm
#15yrsago Orson Welles on privacy, prescient remarks from 1955 https://web.archive.org/web/20100114060742/http://www.thejanuarist.com/orson-welles-on-privacy-the-passport-and-personal-rights/
#20yrsago Desperate Ken Lay paying search-engines to return links to his “version” of Enron https://web.archive.org/web/20050108125640/https://www.chron.com/cs/CDA/ssistory.mpl/business/2982765/
#20yrsago EFF defends bloggers’ rights to keep informants’ identities secret https://web.archive.org/web/20050105112953/http://www.eff.org/news/archives/2005_01.php#002190

Check out my Kickstarter to pre-order copies of my next novel, Picks and Shovels!
5 notes
·
View notes
Text
Benefits of Using VPA in UPI Applications
Have you spotted a mysterious alphanumeric code in your UPI apps and wondered what it signifies? That code is known as a VPA. Since UPI launched in India in 2016, digital payments have skyrocketed from 20 million transactions in the first year to 131 billion transactions worth ₹200 trillion in 2024. What's the secret behind this seamless payment revolution? It is all due to the VPA. It is a unique identifier that simplifies and secures your transactions within the UPI money transfer app. Curious to know more about how VPA powers your UPI experience? Let's see about it!
24/7 Transactions
One of the standout features of VPAs is their ability to facilitate transactions around the clock. Whether it's midnight on a holiday or early morning on a Sunday, VPAs enable users to send and receive funds at any time, every day of the year. This constant availability is particularly beneficial for urgent transactions or when dealing with recipients in different time zones. The flexibility to conduct financial transactions without worrying about bank hours adds a significant layer of convenience for users.
Low Transaction Fees
Traditional banking methods like NEFT, IMPS, and RTGS often come with additional charges for processing transactions. These fees can add up, especially for frequent transactions or large amounts. In contrast, using VPAs through UPI usually incurs no additional transaction fees. This cost-effectiveness makes UPI a more attractive option for individuals and businesses looking to minimize their financial transaction costs. VPAs in UPI account can save money while benefiting from the seamless transfer of funds.
Enhanced Security
Security is a major concern in digital transactions, and VPAs significantly bolster this aspect. VPAs in UPI reduce the risk of fraud and unauthorized access. When you use a VPA, the recipient only sees your VPA or UPI ID, not your bank account information. This added layer of security helps protect your financial information from being exposed and minimizes the risk of identity theft. Additionally, UPI platforms use encryption and secure protocols to safeguard your transactions further.
Instant Transfers
Speed is another critical advantage of VPAs. Traditional methods like NEFT and RTGS can be slow, often requiring several hours or days to process transactions. In contrast, UPI transactions using VPAs are completed within minutes. This rapid processing is ideal for time-sensitive transactions, such as paying bills or splitting expenses with friends. The ability to add beneficiaries easily and complete transactions swiftly enhances the overall efficiency of financial operations.
Error Reduction
Manual entry of bank details is a common source of errors, which can lead to transaction failures or misdirected funds. VPAs help mitigate this risk by automating the verification process. Once you enter a VPA on the payment page, the UPI system automatically verifies it and displays the account holder's name. This feature allows you to double-check the details before completing the transaction.
Final Words
Virtual Payment Addresses are game-changers in the UPI ecosystem. From simplifying transactions to reducing costs and ensuring instant transfers, VPA in UPI enabled app to enhance every aspect of digital payments. Explore UPI today and discover how these capabilities may improve your banking transactions!
#UPI accounts#upi-enabled app#UPI enabled app#UPI money transfer app#UPI Payment#UPI money transfer#UPI app#UPI payment App.#UPI earning App#check balance#UPI account#UPI payment app#check bank balance#check transaction history#UPI bank apps#upi enabled app
0 notes
Text
Digital Nation Pakistan Bill tabled in NA to establish unified identity for citizens
Bill tabled by state minister Shaza Fatima seeks to centralise social, economic, and governance data Minister of State for IT and Telecommunication Shaza Fatima Khawaja tables digital Pakistan bill in the National Assembly on December 16, 2024. — Screengrab via National Assembly of Pakistan/YouTube ISLAMABAD: The federal government on Monday tabled the Digital Nation Pakistan Bill in the…
0 notes
Text
HDFC Bank Home Loan Apply in Ahmedabad

HDFC Bank Home Loan in Ahmedabad
HDFC Bank is one of India's leading financial institutions, trusted for its extensive range of financial services. For many, owning a home is a lifelong dream, and a HDFC bank home loan makes this dream a reality. Offering competitive interest rates and flexible repayment options, HDFC Bank serves various financial needs. If you’re in Ahmedabad, Adiyogi Enterprise is your go-to for expert guidance and seamless support in securing the best HDFC bank home loan online in Ahmedabad.
HDFC Bank Home Loan Interest Rate
Interest rates play a crucial role in determining the affordability of a home loan. In 2024, HDFC home loan online apply offers some of the most competitive rates in the market. Borrowers can choose between floating and fixed interest rates, ensuring they find an option that suits their financial goals.
HDFC Home Loan Interest Rate 2024
For 2024, HDFC Bank offers attractive floating interest rates for both salaried and self-employed individuals. Here’s a quick breakdown of the rates:
Loan Amount Salaried Interest Rate Self-Employed Interest Rate
Up to ₹30 Lakhs 8.50% 8.75%
₹30-75 Lakhs 8.60% 8.85%
Above ₹75 Lakhs 8.70% 9.00%
These rates make HDFC bank home loan apply an excellent choice for affordable financing.
Types of HDFC Home Loan Schemes
HDFC Bank provides various home loan schemes, tailored to meet diverse needs:
Home Purchase Loan: Ideal for buying a new or resale property.
Home Construction Loan: Designed for constructing a house on a plot.
Home Extension Loan: Perfect for adding extra space to your home.
Plot Loan: For purchasing residential plots.
Each scheme comes with unique features, making HDFC bank home loan online apply suitable for all borrowers.
How to Apply for a Home Loan on HDFC Bank?
Follow these steps for a hassle-free HDFC home loan online apply:
Visit the Adiyogi Enterprise official website.
Navigate to the home loan section.
Fill out the online application form with personal and financial details.
Upload the required documents.
Submit the form and await approval.
Adiyogi Enterprise in Ahmedabad can also assist you in the application process for the best results.
What Are the Documents Required to Apply for the Home Loan from HDFC Bank?
When you opt for HDFC bank home loan apply, ensure you have the following documents ready:
Proof of identity (Aadhar, PAN card, etc.)
Proof of address (utility bills, voter ID, etc.)
Income proof (salary slips or IT returns)
Bank statements (last 6 months)
Property documents (agreement, approved plans, etc.)
Proper documentation ensures a quick and smooth approval process.
Who Can Apply for the HDFC Home Loan?
Eligibility criteria for HDFC bank home loan apply include:
Indian residents or NRIs.
Salaried individuals aged 21-65 years.
Self-employed professionals and business owners.
Applicants with a stable income and good credit history.
Whether you’re a first-time homebuyer or upgrading your property, HDFC bank home loan online in Ahmedabad suits diverse needs.
Who Is the Best HDFC Home Loan Provider in Ahmedabad?
Adiyogi Enterprise stands out as the leading provider of HDFC Bank Home Loan Apply in Ahmedabad services. Known for excellent customer support, competitive rates, and expert advice, Adiyogi Enterprise ensures a seamless loan application experience.
Benefits of HDFC Bank Home Loan Online Apply
Opting for HDFC bank home loan online apply offers multiple advantages:
Quick and easy process from the comfort of your home.
Transparent information on interest rates and fees.
Instant tracking of loan application status.
Reduced paperwork through digital uploads.
For Ahmedabad residents, Adiyogi Enterprise enhances these benefits with personalized service.
Conclusion
Owning a home is easier than ever with a HDFC bank home loan. Whether you’re looking to build, purchase, or renovate, HDFC Bank offers tailored options to meet your needs. For residents of Ahmedabad, Adiyogi Enterprise provides unmatched guidance and support.
Take the first step today! Visit our website or contact us directly at +91-9624-9999-44 to apply for the best HDFC home loan online apply. Transform your dream home into a reality.
#HDFC bank home loan#HDFC home loan online apply#HDFC bank home loan apply#HDFC bank home loan online apply#HDFC bank home loan online in ahmedabad#HDFC Bank Home Loan Apply in Ahmedabad
0 notes
Text
CYBER INSURANCE COVERAGE SILVERFORT
Businesses are facing more and more cyberthreats in the current digital era, such as ransomware attacks and data breaches. Protecting sensitive data and IT infrastructure has grown increasingly important as these threats become more frequent and complicated. Cyber insurance coverage silverfort is a useful tool for reducing these risks, and businesses like Silverfort are at the forefront of offering reliable solutions.

What is Cyber Insurance?
A specialist policy called cyber insurance is intended to shield companies from monetary damages brought on by data breaches, cyberattacks, and other disasters involving technology. Data recovery, legal bills, customer notification expenses, and even reputational harm to a business are all covered by this kind of insurance.
Why Cyber Insurance is Essential
The strategies employed by cybercriminals are always changing along with the digital environment. Regardless of the size of the company, these hazards can affect every organisation. Without the proper defenses in place, a cyberattack might cause serious financial losses in addition to eroding consumer confidence.
Businesses may make sure they have a safety net in place to deal with the fallout from a cyber disaster by purchasing cyber insurance coverage. These plans give access to professionals who may help reduce risks and offer financial assistance for recovery from attacks.
Silverfort’s Approach to Cyber Insurance
An inventive method to cyber insurance coverage is provided by Silverfort, a pioneer in identity protection and security. Silverfort assists companies in improving their cybersecurity posture and lowering the probability of a successful attack by combining its cutting-edge protection platform with insurance plans.
Identity-based threats, which are becoming more prevalent in today's cyber environment, are the main emphasis of Silverfort's technology. Since user credentials are frequently the target of cyberattacks, identity protection is an essential component of any security plan. Continuous authentication and risk assessment are offered by Cyber insurance coverage silverfort solution for all access points, including remote workspaces, on-premises systems, and cloud environments.
Businesses may show insurers that they have strong security measures in place by utilizing Silverfort's state-of-the-art technology, which could result in cheaper insurance prices and more alternatives for coverage.
Benefits of Cyber Insurance Coverage with Silverfort
Complete Protection: Protect your company from monetary losses brought on by cyberattacks.
Identity-Based Security: Use Silverfort's cutting-edge security technology to thwart identity-related assaults.
Reduced Premiums: Insurance premiums may go down as a result of improved cybersecurity.
Expert Access: In the event of a compromise, seek assistance from cybersecurity specialists.
Conclusion
Businesses must continue to take proactive measures to safeguard their digital assets as cyber threats continue to change. Businesses can obtain the peace of mind they need to handle the challenging cybersecurity environment of 2024 and beyond with Silverfort's Cyber insurance coverage silverfort.
0 notes