#cyber in South Asia
Explore tagged Tumblr posts
Text
Cambodia: Hundreds of Indians rescued from cyber-scam factories (BBC)
The Indian government has so far rescued 250 citizens in Cambodia who were forced to run online scams.
They were promised jobs but "forced to undertake illegal cyber work", India's foreign ministry said.
Recent reports have said more than 5,000 Indians stuck in Cambodia were forced to operate cyber-fraud schemes.
Hundreds of thousands of people from around the world are estimated to have fallen prey to human traffickers running job scams in South East Asia.
Victims, mostly young and tech-savvy, are promised jobs and then lured into illegal online work ranging from money laundering and crypto fraud to so-called love scams, where they pose as lovers online.
Read more
0 notes
Text
instagram
1 note
·
View note
Text
Digitised Archival Sources on India and South Asia
The days when only members of the upper class of urban society had access to knowledge-producing sites (mostly archives) are long gone. Today, one may easily access digitised archival sources thanks to the internet on mobile phones. The growth of digital technology has also enabled a new arena of history-keeping. Publicly-owned digitised archival sources have gained popularity in recent years as…

View On WordPress
#1947 partition archive#abhilekh patal#archival sources on india#archives in india#asiatic society of mumbai#colonialism documents#digital archives#digital sources on south asia#digitised archival sources on india#granth sanjeevani#ideas of india#indian archives#internet archive#iqbal cyber library#LUMS archive#lums digital archive#national archives of India#nehru memorial museum and library#primary sources on India#rahul sagar#research and writing in India#south asia open archives
0 notes
Text
The Best News of Last Week - May 15, 2023
🐕 - Now It's a Paw-ty
1. World's oldest ever dog celebrates 31st birthday

Bobi was born on 11 May 1992, making him 31 years old, in human years. A big birthday party is planned for Bobi today, according to Guinness World Records.
It will take place at his home in the rural Portuguese village of Conqueiros in Leiria, western Portugal, where he has lived his entire life.
2. The FDA has officially changed its policy to allow more gay and bisexual men to donate blood

The Food and Drug Administration (FDA) has announced that they’ve eased restrictions on blood donations by men who have sex with men in an effort to address blood shortages. The new policy recommends a series of individual risk-based questions that will apply to all donors, regardless of their sexual orientation, sex, or gender. Gay or bisexual men in monogamous relationships will now be permitted to donate blood.
3. Illinois passes bill to ensure community college credits transfer to public universities

The Illinois General Assembly has passed a bill that would help community college students transfer to public universities.
It would ensure that certain classes taken at community colleges could be transferred to any higher education institution in the state. Some schools currently only count community college coursework as elective credits.
4. Brazilian President Lula recognizes 6 new indigenous territories stretching 620,000 hectares, banning mining and restricting farming within them

Brazilian President Luiz Inácio Lula da Silva has decreed six new indigenous reserves, banning mining and restricting commercial farming there. The lands - including a vast area of Amazon rainforest - cover about 620,000 hectares (1.5m acres).
Indigenous leaders welcomed the move, but said more areas needed protection.
5. More than 1,000 trafficking victims rescued in separate operations in Southeast Asia
More than 1,000 trafficking victims were rescued in separate operations in Southeast Asia over the last week, officials in Indonesia and the Philippines said.
Indonesian officials said Sunday they freed 20 of their nationals who were trafficked to Myanmar as part of a cyber scam, amid an increase in human trafficking cases in Southeast Asia. Fake recruiters had offered the Indonesians high-paying jobs in Thailand but instead trafficked them to Myawaddy, about 567 kilometers (352 miles) south of Naypyidaw, the capital, to perform cyber scams for crypto websites or apps, said Judha Nugraha, an official in Indonesia's Foreign Affairs Ministry.
6. A peanut allergy patch is making headway in trials

An experimental “peanut patch” is showing some promise for toddlers who are highly allergic to peanuts. The patch, called Viaskin, was tested on children ages one to three for a late-stage trial, and the results show that the patch helped children whose bodies could not tolerate even a small piece of peanuts safely eat a few.
After one year, two-thirds of the children who used the patch and one-third of the placebo group met the trial’s primary endpoint. The participants with a less sensitive peanut allergy could safely tolerate the peanut protein equivalent of eating three or four peanuts.
7. Critically endangered lemur born at Calgary Zoo

The Calgary Zoo has released pictures of its newest addition, a baby lemur. The zoo says its four-year-old female black-and-white ruffed lemur, Eny, gave birth on April 7. The pup’s father is eight-year-old Menabe. The gender of the pup has not been confirmed but the Calgary Zoo says the pup appears bright-eyed and active and is on the move.
The black-and-white ruffed lemur is registered among the 25 most endangered primates in the world, due mostly to habitat loss and hunting.
----
That's it for this week :)
This newsletter will always be free. If you liked this post you can support me with a small kofi donation:
Buy me a coffee ❤️
Also don’t forget to reblog.
SUBCRIBE HERE for more good news in your inbox
657 notes
·
View notes
Note
what;s your thoughts on ionia if you have any? from a design perspective? I personally feel like ionia lacks design coherency, and kind of forces a bunch of unrelated design elements into what is suppose to be a single nation.
I feel pretty mixed. The concept art and conceptual ideas behind Ionia's aesthetics are genuinely beautiful - if you check the Universe page for the art, you'll find some visual absolute bangers.

One of the major ideas of Ionia is the idea that people live in symbiotic harmony with nature by way of magic and spirit magic, and one of the very clever ways this is reflected is that Ionian buildings are not built by felling trees, but by asking trees to arrange themselves into structures that buildings can be built around, in return for the occupants nourishing and honouring the tree that shelters them, which is a super cool idea and genuinely comes across in a lot of the region's concept art:



And the artists at Riot explored some genuinely incredibly creative visual ideas for the aesthetics of the region that draw from various fantasy aesthetics without feeling like it's merely regurgitating lesser imitations of Chinese, Korean or Japanese fantasy. Like, it does at least try to imagine and synthesize something novel out of its influences, mixing stark rocky environments with impossibly vibrant nature colors to create the sense of a dreamlike, shifting landscape, something that makes sense in a region defined by a living environment animated by magic. Plants and rocks flow into one another and merge, rock formations sprout like trees, the boundaries between land and life blur.






Unfortunately, outside of the concept art, Ionia really is just treated as Magic Asia: The Region. China, Korea and Japan, with sometimes a bit of south and south-east Asia conglomerated in there, it's all just mushed together into one homogenate; and that rankles a bit in a game that devotes four entire regions to various flavors and time periods of Europe Shit.™
And that's where your complaint comes from, I think. Ionia is a big soup of pan-Asian fantasy tropes all packed into a single compressed region, where none of them really have enough room to define themselves, and it leads to a lot of incoherency. Wukong is drawn straight out of Wuxia, and he runs around alongside a Batteries Not Included minor Teenage Mutant Ninja Turtle villain-looking cyber samurai in Master Yi, a samurai-ninja in Shen, a Korean kumiho in Ahri, a fantasy Yakuza in Sett and random spirit creatures like Treebeard On Weed Ivern and Disney Princess Bambi in Lillia. It's messy.
It could be genuinely brilliant, I think, if Riot committed more to inventing their own mythology and aesthetic here, rather than merely reproduce pop-culture tropes and archetypes, but we're 150 champions deep in this now and I don't think there's much chance they'll pivot at this point.
218 notes
·
View notes
Text

a terra incognita introduction
cast: jake ✗ fem.reader
synopsis: as the world entered the middle of the 21st century, many things have changed for the better or for worse in the newly united korea peninsula: the preparation for the succession of the new conglomerates of the past decade, the uprising of deviant androids, and the new layer of life shield by walls of codes. in the middle of it, two beings are trying to understand each other and the situation of the world they live in; an unknown territory
genre: cyberpunk, cyber noir, psychological thriller, science fiction, dystopian future, politics and philosophies regarding artificial intelligence and humanity, romance, drama, angst, mature content (war and revolution, explicit smut)
based on: video game cyberpunk 2077 (2020) and detroit: become human (2018), anime serial experiments lain (1998), and tv show succession (2018-2023)
masterlist

united korea
the united republic of korea (known as "united korea") is an east asia nation on the korean peninsula. as a result of the reunification agreement back in 2025 of the former north and south korea, the state has now prospered in terms of sociopolitical and economic issues from the korean war. it now excels technologically as one of the firsts in the world to introduce commercialized androids along with other east asian countries such as japan and china. in the aftermath of the social media collapse and the cyber world war of 2027-2030, the private conglomerates of the state have released a new way to connect to the information superhighway.
FLAG

(flag link to r/alternatehistory on reddit)
INFORMATION
capital cities: neo seoul | neo pyongyang
population: 65.5 million
language: korean | english | japanese | chinese
>> HISTORY
>> GEOGRAPHY
>> GOVERNMENT
>> SOCIETY
>> ECONOMY
>> MILITARY
>> MAJOR CITIES
neo seoul
one of the capital cities of united korea and the former capital of south korea, neo seoul is a metropolis for the state's bustling life from the most traditional to the most modern. neo seoul is known for six districts that are divided by the han river flowing in the middle, known as the division of north seoul and south seoul
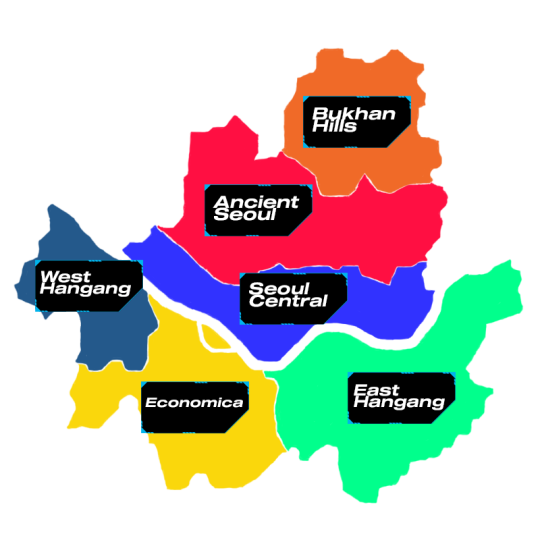
north seoul encapsulates the traditional side of neo seoul and the center for the city's and state's government administration
south seoul lies the center of neo seoul's economy where conglomerates build their headquarters. a distinct living cost gap can be seen to compare those living in the north and those in the south where it is connected to incheon, a major city of transportation with its international seaports and airport
neo pyongyang
one of the capital cities of united korea and the former capital of north korea, neo pyongyang is the capital of the parliament of united korea. it's located on the taedong river kilometers upstream from the yellow sea. it is known as the city where the declaration of unification was signed along with its establishment as half of the capitals of the unified countries. much of the population of neo pyongyang are citizens coming from the southern of the peninsula as they migrate to fill in the spaces and utilize materials. it is also a growing industrial hub where conglomerates built their factories, along with kaesong.
with the rise of deviancies from androids made by shim laboratories, journalists have made observations and assume that neo pyongyang is the main hub of the rebellion between androids and their creator (as one human equates to two androids), creating unrest between the two parties. yet, they also say that neo pyongyang is a better refuge for deviant androids than neo seoul.

taglist: @raeyunshm @endzii23 @fluffyywoo @camipendragon @hiqhkey @wccycc @cha0thicpisces @y4wnjunz @yeehawnana @beansworldsstuff @kimipxl @blurryriki @reallysmolrenjun @frukkoneeeeg
© writingmochi on tumblr, 2021-2025. all rights reserved
#enhypen imagines#enhypen smut#enhypen x reader#enhypen scenarios#enhypen angst#enhypen fanfiction#jake x reader#rsc: t.i.#cr: jake#cs: enhypen#sc: regina
36 notes
·
View notes
Text

The Federal Bureau of Investigation (FBI), Cyber National Mission Force (CNMF), and National Security Agency (NSA) assess that People’s Republic of China (PRC)-linked cyber actors have compromised thousands of Internet-connected devices, including small office/home office (SOHO) routers, firewalls, network-attached storage (NAS) and Internet of Things (IoT) devices with the goal of creating a network of compromised nodes (a “botnet”) positioned for malicious activity. The actors may then use the botnet as a proxy to conceal their identities while deploying distributed denial of service (DDoS) attacks or compromising targeted U.S. networks.
Integrity Technology Group, a PRC-based company, has controlled and managed a botnet active since mid- 2021. The botnet has regularly maintained between tens to hundreds of thousands of compromised devices. As of June 2024, the botnet consisted of over 260,000 devices. Victim devices part of the botnet have been observed in North America, South America, Europe, Africa, Southeast Asia and Australia.
While devices aged beyond their end-of-life dates are known to be more vulnerable to intrusion, many of the compromised devices in the Integrity Tech controlled botnet are likely still supported by their respective vendors.
FBI, CNMF, NSA, and allied partners are releasing this Joint Cyber Security Advisory to highlight the threat posed by these actors and their botnet activity and to encourage exposed device vendors, owners, and operators to update and secure their devices from being compromised and joining the botnet. Network defenders are advised to follow the guidance in the mitigations section to protect against the PRC-linked cyber actors’ botnet activity. Cyber security companies can also leverage the information in this advisory to assist with identifying malicious activity and reducing the number of devices present in botnets worldwide.
For additional information, see U.S. Department of Justice (DOJ) press release....
4 notes
·
View notes
Text
News Post
Israel war on Gaza updates: Health Ministry declares polio epidemic in Gaza | Israel-Palestine conflict News | Al Jazeera
Palestine Is a Core Election Issue, and We Won’t Let Our Politicians Ignore It | Truthout
Turkey threatens to ‘enter’ Israel to protect Palestinians – POLITICO
14 Palestinian groups, including Hamas and Fatah, sign China-brokered deal: Why it matters | Explained News - The Indian Express
Ukraine
US will send $1.7 billion in military aid to Ukraine | AP News
Tuaregs photographed with Ukrainian flag after defeating Wagnerites in Mali | Ukrainska Pravda
‘Nowhere is safe in Belgorod’: Fears grip Russian region bordering Ukraine | Russia-Ukraine war News | Al Jazeera
Ukraine's hopes and challenges after long wait for F16s (bbc.com)
Sudan
Khartoum: Women and girls subjected to widespread sexual violence by warring parties, HRW report finds | CNN
https://sudantribune.com/article288840/
South Sudan Considering Oil Pipeline Shutdown Amid Economic Crisis | Pipeline Technology Journal (pipeline-journal.net)
Sudan civil war hits close to home for CT’s Sudanese community | Connecticut Public (ctpublic.org)
Other
Egypt warns of dangers of new war in Lebanon | Arab News
Prosecution calls for 25 death sentences in DR Congo rebellion trial (voanews.com)
Mike Kalambay: Nine die in DR Congo gospel concert chaos (bbc.com)
The Taliban say they no longer recognize Afghan diplomatic missions set up by the former government | AP News
In Afghanistan, Taliban ban on girls’ education leaves thousands of classrooms empty | Arab News
Ethiopia boat disaster kills 19 in Amhara region (bbc.com)
Horror, grief, trauma in Ethiopia’s Gofa a week after deadly landslides | Environment News | Al Jazeera
The Silent Winner of Myanmar’s Northern Conflict – The Diplomat
China and neighbors pressure Myanmar as regime reels from battle losses - Nikkei Asia
Under siege in Myanmar’s cyber-scam capital | Crime News | Al Jazeera
Russia's Wagner has deadliest loss in Africa’s Sahel, highlighting the region's instability | AP News
#News Post#Palestine#Gaza#Free Palestine#Free Gaza#Justice for Palestine#Long Live Palestine#Ukraine#Save Ukraine#Keep Fighting For Ukraine#Victory to Ukraine#Sudan#Dafur#El Fasher#Save Sudan#Sudan Civil War#Sudan Genocide#Egypt#Congo#Afghanistan#Ethiopia#Myanmar#Sahel
2 notes
·
View notes
Text
It is now common knowledge that whenever protest movements could make political gains through digital media and technologies, the regimes these very movements seek to challenge would catch up with their progress. From the 2010-2011 Arab Spring to popular contestations of Southeast Asia’s autocracies in 2020-2021, optimism regarding digital activism has been met with regime adoption of digital repression. 1 This development has reinforced ‘digital authoritarianism’ in the region. 2 Digital arsenals to suppress dissent have multiplied and diversified over the past decades, following disruptive mass mobilizations that challenged the status quo in countries such as Cambodia (2013), Malaysia (2015-16), Myanmar (2021-present), Thailand (2020-21) and Indonesia (2020). In long-standing autocracies like Vietnam in which the Internet is a potential regime destabilizer, stringent cyber laws and information manipulation through cyber troops enable ruling elites to tighten their grip on the population. 3 While domestic factors are key drivers, there is reason to believe that governments in Southeast Asia‘cross-learn’ tactics of digital repression and inspire one another. 4
Digital arsenals to suppress dissent have multiplied and diversified over the past decades, following disruptive mass mobilizations that challenged the status quo in countries such as Cambodia (2013), Malaysia (2015-16), Myanmar (2021-present), Thailand (2020-21) and Indonesia (2020). In long-standing autocracies like Vietnam in which the Internet is a potential regime destabilizer, stringent cyber laws and information manipulation through cyber troops enable ruling elites to tighten their grip on the population. 3 While domestic factors are key drivers, there is reason to believe that governments in Southeast Asia‘cross-learn’ tactics of digital repression and inspire one another. 4
Digital repression encompasses various methods of social control to preemptively deter and lower the impact of protest movements. Digital repression toolkits include Internet filtering, surveillance via high-tech spyware 5 and social media monitoring, state-aligned misinformation online, 6 prosecution of activists through cyber- or information-related laws, 7 and Internet shutdowns. 8 These can help governments achieve the goal of control, in many cases, without resorting to armed clampdown of challengers.
Governments in the region possess varying degrees of digital capacities, leading to their different tactical preferences. Based on the 2019 Digital Society Project data, the most oft-used form of digital repression in Singapore and Vietnam is prosecuting online users, while in Cambodia, it is Internet filtering. In Malaysia and Thailand, social media monitoring was the most common trend. The two remaining electoral democracies – Indonesia and the Philippines – lean toward misinformation campaigns. Myanmar seems to be the only one among its autocratic counterparts that most frequently relies on Internet shutdowns.
13 notes
·
View notes
Text
Every now and then I think about how a game with the plot of Splinter Cell: Chaos Theory could NEVER be made today
I felt like talking about this in light of some recent news in East Asia. TL;DR but Chaos Theory, despite being a game ostensibly inspired by the writings of Tom Clancy, is essentially a political thriller where a rogue American PMC company and Japanese Admiral try to start WWIII, and where China and NORTH KOREA are kind of presented as the good guys in the conflict?! Here's a general plot summary: Japan has just created a new warfare branch, the "Information Self-Defence Force" or ISDF, headed by Admiral Toshiro Otomo. The role of the ISDF is to conduct and intercept electronic warfare, which many in Asia feel is a violation of Japan's post war constitution forbidding them from maintaining a military force capable of striking outside its borders. In response, China and North Korea mobilize a naval blockade in the Yellow Sea to intercept and search all Japanese shipping, so America sends their newest electronics warfare ship, the USS Clarence E. Walsh to the area as a show of force, carrying the NSA's top operative (and player character) Sam Fisher. While on the way, Sam is sent to Peru to rescue kidnapped American computer programmer Bruce Morgenholt, who was part of a two-man United Nations to decipher a cyber warfare weapon called the "Masse Kernels" which were part of a previous game. Sam unfortunately finds Morgenholt dead, and pursues the kidnappers to sea, where he finds they were paid for their services using a Panamanian bank as a proxy. Sam is then sent to Panama, where he finds evidence that the payment was went by the other member of the UN task force, computer programmer Abrahim Zherkezhi (and also steals $50 million in French bearer bonds in the process, best level in the game). Further implicating Zherkezhi is that both New York and Japan are hit with a Masse Kernel attack that shuts off their entire electricity grids,so Sam is sent to his Penthouse in New York to investigate, where he finds out that he has a protection detail from American PMC outfit Displace International, headed by his best friend and former war buddy, Douglas Shetland, who were also supposedly protecting Morgenholt. Reluctantly, Fisher infiltrates the offices of Displace and learns that Zherkezhi was relocated to Hokkaido for his protection, so he is sent there, meeting up with Shetland along the way, and the two watch on the news in the bar that the USS Walsh was just hit and sunk by a North Korean anti-ship missile. North Korean officials, backed by China, claim they did not intentionally fire the missile, and the Secretary of Defence claims that the Walsh's cyber warfare systems were way too advanced to be tracked and hit by a fifty year old Chinese-manufactured missile, but Sam's boss, Irving Lambert, believes that before the attack, the Walsh was hit by a Masse Kernel attack disabling it's defence systems. Fisher is sent to Hokkaido to bring Zherkezhi in for questioning, but as he witnesses a meeting between him and Shetland, the latter reveals his intentions to start a war in Asia before murdering Zherkezhi.
Fisher wants to go after Shetland, but with diplomacy rapidly deteriorating after the sinking of the Walsh, war in Korea seems inevitable, so he is instead sent to the North Korean missile battery that sank the Walsh to find proof of the North Korean claims. Fisher finds evidence of the Masse Kernals being used to force launch the missile, but before the information can be sent, North Korea crosses the DMZ and invades the South.
After a stop in Seoul to gather information from a data routing centre, Fisher learns that Shetland is meeting a third party at a bathhouse in Tokyo, which turns out to be the ISDF, who are revealed to be collaborating with Shetland to start a war. Fisher catches and kills Shetland, and is then sent to the Japanese Ministry of Defence to find out if the Japanese government itself is involved. There, Fisher eavesdrops a meeting between high ranking SDF members and finds out that it was Admiral Otomo acting alone, wishing to use the pretext of a war to restart Japanese Imperialism. The GSDF attempt to apprehend Otomo, but fail, and in retaliation, he uses the Mass Kernels to launch a North Korean missile aimed at Japan, knowing that if it hits, World War III will truly be inevitable.
Fisher stops the attack by destroying the ISDF's servers, and apprehends Otomo as he tries to commit seppuku. Otomo confesses to his actions, North Korea withdraws its forces, Displace and the ISDF are disbanded, and the Chinese Ambassador to the United States wins the noble peace prize for his efforts in trying to mediate peace in Asia. Job finished, game over. So, you can probably see why this would never be made today, right? Anything that even remotely positively portrays China, let alone North Korea in a positive light nowadays would get torn to shreds, not to mention the game makes the taboo of bringing light to how the Japanese government has never really owned up to the crimes they committed during WWII because of Cold War politics, as well as showing how Japan rebuilding its military has created lots of tensions in East Asia.
No other real point to this, I just wish we had more complex stories like this where the stereotypical "good and bad guys" don't automatically fill their roles.
21 notes
·
View notes
Text
ASATA Statement on Palestine | October 2023

ASATA members joined hundreds of protesters in front of the Israeli consulate in San Francisco on October 8, 2023.
The Alliance of South Asians Taking Action stands in solidarity with the people of Palestine in the face of the current escalation of violence unfolding in Gaza and the West Bank. Over the last two weeks, ASATA members looked to the leadership of Palestinian activists in the San Francisco Bay Area who continue to lead protests that lift up the unrelenting resistance of those living under violent occupation.
As we mobilized for direct actions and joined the call for Palestinian liberation, we also deepened our understanding of how the state of Israel’s settler colonial tactics are proliferated and being replicated in the Indian government’s violent occupation of Kashmir. As part of a diverse South Asian Diaspora, ASATA members clearly see the close relationship between Hindutva (Hindu Nationalism) and Zionist ideologies. As South Asians, we challenge all forms of imperialism. Thus, we oppose Zionism, a settler colonial project displacing indigenous Palestinians, resulting in the world’s largest diasporic refugee population.
The current close relationship between India and Israel has enabled a security regime where India has adopted Israeli tactics of collective punishment (such as the arbitrary revocation of residency and citizenship rights, arbitrary detention, statewide suspension of internet, etc.) in its occupation of Kashmir. The deployment of the Israeli hacking software Pegasus to spy on Indian journalists, lawyers, activists, academics, supreme court judges, opposition politicians, and many others must be seen in the context of the announcement by India and Israel that cyber security is a key area of cooperation between them. The NSO group, an Israeli firm that’s an expert in cyber surveillance, has in effect abetted the Indian government’s surveillance of its own citizens as it has done in a dozen other countries.
The Israeli government’s alliance with and support of the BJP’s Hindutva agenda is part of a longer history where it has exported its violent policies and military tactics to South Asia in order to suppress resistance movements there. For example, The New York Times has reported that as early as the 1980s, Israeli intelligence agents trained their Sri Lankan counterparts in their fight against Tamil groups. Israeli human rights lawyer Eitay Mack has raised questions about Israel’s more recent role in war crimes committed during the Sri Lankan civil war, and has called for criminal investigations into the involvement of Israeli companies, officials, and individuals.
India’s embrace of Israel is polarizing the Indian-American diaspora, and has exacerbated the islamophobia of those who subscribe to the toxic ideology of Hindutva. The US-India Political Action Committee (USINPAC) is modeled after AIPAC and the AJC, and the Hindutva lobby’s use of the accusation of “Hinduphobia” to shut down critical discourse is inspired by the Zionist lobby’s success in silencing critics of Israel’s policies by weaponizing charges of anti-semitism.
The BJP’s fearsome “IT Cell” is a massive disinformation machine that amplifies Hindutva propaganda through an army of paid employees and volunteers that flood social media with fake news, and through a large-scale use of bots that power harassment and trolling campaigns. Many accounts known to push Hindutva content are now being used to spread disinformation about Hamas while continuing their systematic spreading of islamophobic content.
Indeed, as documented by BOOM, one of India's most reputable fact-checking websites, India is now one of the largest sources for disinformation targeting Palestinians negatively. We call on fellow South Asians in the diaspora to condemn the demonization of Palestinians, and ensure we do not contribute to the spread of disinformation and anti-Muslim hate.
We take inspiration from the women of India’s National Federation of Dalit Women (NFDW) who have declared their solidarity with Palestinians — invoking the “historic oppression” and “systematic dehumanization” that both communities have faced.
We are also in solidarity with the many anti-Zionist Jewish groups and individuals both within Israel and world-wide that are opposing the Israeli state’s attacks on Palestine, and its long standing policy of apartheid against the Palestinian people.
We call on our fellow South Asians and South Asia- led organizations in the United States to reject the “both sides” argument that invisiblizes the experiences and dignity of the Palestinian people. We call for an immediate ceasefire and end to the ongoing siege and genocide in Gaza. We call on the US to stop arming the Israeli apartheid regime with billions’ of dollars worth of weaponry. And finally, We invite our communities to embrace the ways our histories of anti-imperialist struggles are connected so that we may build power and protect our communities against anti-Musilm hate violence and state-sponsored terrorism. Free Palestine.
4 notes
·
View notes
Text
A mention of North Korean hackers typically conjures images of either crippling cyberattacks or, more often, massive cryptocurrency heists. But a new report on the authoritarian state’s capabilities and tendencies paints a different picture.
The report, prepared by cyber-intelligence firm Recorded Future and shared exclusively with Foreign Policy, labels espionage as the predominant motive of North Korea’s cyberprogram. Recorded Future analyzed 273 cyberattacks over a 14-year period linked to North Korean state-sponsored groups and found that information collection was the primary motivation for more than 70 percent of them.
“The narrative seems to be that North Korea is a bunch of cybercriminals that are backed by a state, but they’re just pulling off all of this financially motivated cybercrime, and that is one aspect of their strategy,” said Mitch Haszard, a senior threat intelligence analyst at Recorded Future and lead author of the report.
“But what this report shows is that they’re still heavily focused on information collection, or cyber-espionage, and they conduct more of those operations than they do financially motivated or financial theft operations.”
Pyongyang predominantly seeks to use cyber-operations to either “gain insight into how its adversaries think” or “access to information on technologies” that will help it in a conflict with those adversaries, the report said. Government entities are the most frequent targets, followed by cryptocurrency, media, finance, defense, and nongovernmental organizations.
“North Korea’s leadership appears to be much more interested in learning about what others think of them, gathering information that can help them develop nuclear and ballistic missile technology, and stealing money to fund their regime,” the report added.
However, North Korea’s obsession with cryptocurrency is unique, and the country’s cyber-operations are one of its biggest avenues to prop up its nuclear arsenal. Anne Neuberger, the White House’s cyber czar, said at an event in Washington last month that half of the regime’s missile program is funded by cryptocurrency and cyberheists.
“There aren’t really any other states or countries that are trying to steal cryptocurrency, so North Korea is unique in that perspective, but they still do a lot of things that other states do,” Haszard said.
The heists tend to make headlines, with North Korean hackers linked to thefts worth billions of dollars from cryptocurrency exchanges around the world in recent years, with two high-profile attacks on exchanges in Estonia and California so far this year. Beyond crypto, North Korea has been linked to larger and more disruptive global attacks, starting with the crippling of Sony Pictures just under a decade ago that put its cybercapabilities on the map. That was followed by a hack of Bangladesh’s central bank that compromised the global financial transfer system known as Swift, and a crippling of the United Kingdom’s National Health Service.
However, Haszard and his colleagues found that the vast majority of North Korea’s cyberactivity goes after targets much closer to home. Nearly 80 percent of the attacks for which geographic information is available took place in Asia, according to the report. Most of that is in its immediate neighborhood: South Korea accounted for just over 65 percent of the targets among the 29 countries where attacks took place. The United States is a distant second, at 8.5 percent, and no other country accounted for more than 3 percent of North Korean attacks.
Recorded Future found that Lazarus, the most notorious and high-profile hacking group linked to the authoritarian regime, tends to go after more global targets but is not the most common perpetrator of cyberattacks. That distinction belongs to a group called Kimsuky, which mainly targets Asian government and civil society entities and accounted for more than one-third of total attacks. According to multiple U.S. law enforcement agencies, Kimsuky hackers pose as South Korean journalists, exchanging emails with their targets on the pretext of setting up interviews before sending them a link or document embedded with malware. That malware, known as BabyShark, gives hackers access to the victims’ device and communications. “Kimsuky actors have also been known to configure a victim’s email account to quietly auto-forward all emails to another actor-controlled email,” a joint cybersecurity advisory by the FBI, National Security Agency, and South Korean authorities earlier this month said.
While Pyongyang has established its ability to disrupt critical infrastructure in the West and conduct ransomware attacks, it is increasingly less likely to conduct those types of attacks compared to other cyber-capable adversaries such as Russia and China. It prefers to go smaller, faster, and more frequently, deploying more basic techniques such as stealing passwords or phishing emails, which infect systems with viruses by fooling users into clicking on dodgy links.
“The thing that I see in my tracking of North Korean threat actors is an incredible amount of activity that is generally low-sophistication in nature,” Haszard said, adding that that’s likely a matter of strategy rather than ability. “They’re achieving a lot of success doing the kind of lowest-common-denominator cyberattacks. So if it were me, why would I change?”
3 notes
·
View notes
Note
For the ask game - Cyber
Terra Darling ❤️🌹❤️
Cyber: yeeesss!!! I'm online almost 24 hours a day, my Tumblr & Twitter moots live mostly in North & South America or in Asia, so I must be awake if I want to interact with them lmao
But don't worry, sometimes I fall asleep (at least for 2 hours) or I have to work / do irl stuff or I'm with my family so I'm afk 😉
Thanks for asking, I didn't mean to make you worry about me 🥺🥺 I'll touch grass & breathe fresh air & enjoy nature in a few days in the Alps 🏞️
Lots of love for my Darling 😘🌹❤️
3 notes
·
View notes
Text
About Us
IFW Global is an international investigation team helping clients with cybercrime.
Around the clock, around the world
We deliver unique services. Law enforcement agencies are often restricted in their efforts to locate individuals and their operations. IFW Global has built a company culture that ensures every case is handled with urgency and sensitivity.
Investigations, Intelligence and Asset Recovery
Our head office is located in Australia with an operation and monitoring centre in the heart of Asia.
Understanding the internal structures of such groups requires in-depth investigative work. Regardless of what the end result might be, addressing networks, removing counterfeits from the market or recovering assets always requires a buildup of evidence necessary to turn investigations into intelligence. Each case requires an individual approach, while standard solutions are unable to deliver the desired outcome.
This is why IFW Global offers its clients a methodical process – a set of established actions that follow a systematic and meticulous procedure – rather than a predetermined product. This approach has proven successful and allows adaptability – each element of the process is adjusted to the situation.
Management Team
Ken Gamble – Executive Chairman
Ken Gamble is the co-founder and current Executive Chairman of IFW Global. Ken has extensive qualifications and experience in investigation, intelligence, surveillance and asset recovery, developed over a 35-year career. Ken has consulted to various foreign governments and law enforcement agencies and presented on cybercrime topics at Interpol events.
Allan Watson – Director of Global Investigations
Allan Watson is the Director of Global Investigations and has 38 years’ experience in varying fields of investigations. These include investment issues, asset tracing and recovery, business intelligence and security and crisis management in both the corporate and government sectors. Allan is presently in charge of coordinating investigations in many continents across the world including Asia, Europe, Africa, Middle East and the Americas.
Michael Nasca – Director of US Operations
Michael Nasca is the Director of US Operations, who has over 25 years of federal law enforcement experience as a special agent in both criminal and civil proceedings. Michael retired as a special agent with Homeland Security Investigations (HSI), where he was responsible for investigating financial matters, customs issues, intellectual property rights violations, and cyber-related activities. Michael has been recognized for collaborating with other governments and non-government entities to address transnational activities. Michael also retired as a US Navy Reserve Intelligence Officer.
Credentials
In 2016, Gamble Investigations International and cyber intelligence firm Internet Fraud Watchdog joined forces to form IFW Global led by Ken Gamble.
Ken Gamble is a private investigator licenced by the New South Wales Police Force (Australia). Licence number: 406928335 Allan Watson is a private investigator licenced by the New South Wales Police Force (Australia). Licence number: 409398018 IFW Global is licenced by the New South Wales Police Force (Australia). Master Licence Number: 410843633 IFW Global is licenced by the Florida Department of Agriculture and Consumer Services. Licence number: A 1900003
0 notes
Text
A Deep Dive into the Managed Security Services Market: Insights and Analysis
The global managed security services market size is expected to reach USD 87.5 billion by 2030, growing at a CAGR of 15.4% from 2023 to 2030, according to a recent report from Grand View Research, Inc. Factors such as the growing demand for outsourcing services across various BFSI, healthcare, manufacturing, IT & telecommunication industries, and the enterprises focus on their key competencies are expected to drive the market’s growth.
Businesses rely on managed security service providers (MSPs) to avoid the costly burden of maintaining their IT infrastructure and keep pace with constant technological dimensions. By leveraging standardized products, reducing time to market, and improving service quality, managed service providers helps an organization in saving costs.
MSPs have created a vast space in business operations by providing advanced cybersecurity tools to predict and mitigate cyber threats. Additionally, as emerging technologies like artificial intelligence, DevOps, and machine learning gain maturity, organizations are expected to look forward to specialized MSPs to stay at the forefront of innovation. A Managed Security Service Provider (MSSP) offers various sub-functions that cover the overall security needs of an enterprise.
The major sub-segments of MSSs have managed endpoint security that monitors all endpoints across the enterprise and intrusion prevention detection system (IPS) that regularly monitors the network for signs of forced intrusion. Extended Detection, and Response (XDR), gathers security details across endpoints and threat intelligence-related visibility to help detect future attacks provide.
Gather more insights about the market drivers, restrains and growth of the Managed Security Services Market
Managed Security Services Market Report Highlights
• The cloud security segment is anticipated to observe a CAGR of 18.5% during the forecast period. The massive growth of cloud 3.0, Industry 4.0, and digitalization has resulted in the surge of managed cloud security services. Cloud security facilitates 24/7 system protection without any human intervention, real-time alerts, and proactive managed services
• The managed DDoS segment is anticipated to observe a CAGR of 18.7% during the forecast period. The DDoS services enhance operational services that depend on the web is projected to rise owing to the growing demand among enterprises to manage the complexity of resources
• Small and medium-sized enterprises (SMEs) are anticipated to observe a CAGR of 18.1% during the forecast period. An increased zero trust security among small and medium-sized businesses (SMEs) surged the adoption of secured management solutions, owing to the growing importance of managed services
• The manufacturing segment is anticipated to observe a CAGR of 16.4% during the forecast period The growing demand among manufacturers to adopt managed security services for cyber safety and vendors’ data accessibility is fueling the demand for the market
• Asia Pacific is expected to grow at the fastest CAGR of 18.2% from 2023 to 2030, owing to the increasing adoption of managed security services and the growing digitalization of businesses in the region. Countries such as China, India, Japan, and South Korea have implemented privacy legislation and data protection that force enterprises to build robust security management solutions
Managed Security Services Market Segmentation
Grand View Research has segmented the global managed security services market based on security, services, enterprise size, vertical, and region:
Managed Security Services Security Outlook (Revenue, USD Billion, 2018 - 2030)
• Cloud Security
• Endpoint Security
• Network Security
• Data Security
• Others
Managed Security Services Outlook (Revenue, USD Billion, 2018 - 2030)
• Managed SIEM
• Managed UTM
• Managed DDoS
• Managed XDR
• Managed IAM
• Managed Risk & Compliance
• Others
Managed Security Services Enterprise Size Outlook (Revenue, USD Billion, 2018 - 2030)
• Small and medium-sized enterprises
• Large enterprises
Managed Security Services Vertical Outlook (Revenue, USD Billion, 2018 - 2030)
• BFSI
• Healthcare
• Manufacturing
• IT and Telecom
• Retail
• Defense/Government
• Others
Managed Security Services Regional Outlook (Revenue, USD Billion, 2018 - 2030)
• North America
o U.S.
o Canada
• Europe
o UK
o Germany
o France
o Italy
o Spain
• Asia Pacific
o China
o India
o Japan
o Australia
o South Korea
• Latin America
o Brazil
o Mexico
o Argentina
• Middle East and Africa
o UAE
o Saudi Arabia
o South Africa
Order a free sample PDF of the Managed Security Services Market Intelligence Study, published by Grand View Research.
#Managed Security Services Market#Managed Security Services Market Size#Managed Security Services Market Share#Managed Security Services Market Analysis#Managed Security Services Market Growth
0 notes
Text
The Future of Oil and Gas Security: Market Dynamics and Opportunities
The global oil and gas security and service market size was estimated at USD 25.51 billion in 2023 and is expected to expand at a CAGR of 5.4% from 2024 to 2030. Various factors such as technologies and security threats, rising regulatory compliance, Growing adoption of advanced technologies, and focus on operational safety are driving the growth of the market. The oil and gas industry is a target for various security threats, including terrorism, piracy, theft, and sabotage. As these threats become more advanced, oil and gas companies are investing more in security measures to protect their assets and personnel.
The surge in the use of cloud technologies in the oil and gas sector has increased its exposure to cyber threats. Historically, industry has managed to protect data and ensure privacy by segregating networks and bolstering outer defenses. However, the introduction of cloud computing presents both a challenge and an opportunity for the sector to enhance and renew its security measures through the adoption of cyber security practices. One of the hurdles is that many firms lack the necessary expertise, funds, and in-house servers, pushing them toward cloud solutions for better data security.
Stringent government regulations and policies concerning energy security and environmental preservation require the oil and gas industry to implement robust security measures. Furthermore, the growing adoption of advanced technology like surveillance, access control, and intrusion detection systems is driving the market growth. Companies are proactively pouring resources into security solutions to mitigate risk and protect essential infrastructure. Additionally, the development of new exploration and production opportunities, especially in offshore and hard-to-reach areas, has created a need for specialized security services to address distinct challenges. These factors collectively are driving the growth and development of the security and services market in the oil and gas sector.
Global Oil And Gas Security And Service Market Report Segmentation
This report forecasts revenue growth at global, regional, and country levels and provides an analysis of the latest industry trends in each of the sub-segments from 2017 to 2030. For this study, Grand View Research has segmented the global oil and gas security and service market report based on component, security, services, operation, application, and region.
Component Outlook (Revenue, USD Billion, 2017 - 2030)
Solution
Services
Security Outlook (Revenue, USD Billion, 2017 - 2030)
Physical Security
Network Security
Services Outlook (Revenue, USD Billion, 2017 - 2030)
Risk Management Services
System Design, Integration, and Consulting
Managed Services
Operation Outlook (Revenue, USD Billion, 2017 - 2030)
Upstream
Midstream
Downstream
Application Outlook (Revenue, USD Billion, 2017 - 2030)
Exploring and Drilling
Transportation
Pipelines
Distribution and Retail Services
Others
Regional Outlook (Revenue, USD Billion, 2017 - 2030)
North America
US
Canada
Mexico
Europe
UK
Germany
France
Asia Pacific
China
India
Japan
Australia
South Korea
Latin America
Brazil
MEA
UAE
South Africa
KSA
Key Oil And Gas Security And Service Companies:
The following are the leading companies in the oil and gas security and service market. These companies collectively hold the largest market share and dictate industry trends.
Cisco Systems, Inc.
Honeywell International Inc.
Huawei Technologies Co., Ltd.
Intel Corporation
Microsoft
NortonLifeLock Inc.
Schneider Electric
Siemens
United Technologies Inc.
Recent Developments
In April 2024, Siemens launched Siemens Xcelerator, to automatically verify vulnerable production assets. Therefore, it is imperative for industrial firms to detect and mitigate potential security gaps within their systems. Siemens introduced a new cybersecurity software-as-a-service solution in response to the urgency of pinpointing cybersecurity in shop floor promptly,
In September 2023, Huawei Technologies Co., Ltd. launched intelligent architecture and intelligent Exploration & production (E&P) solution for oil and gas industry. Huawei Technologies Co., Ltd.'s intelligent architecture for the oil and gas sector is constructed around six smart components: connectivity, sensing, platform, application, AI models, and foundation. Each component is structured with hierarchical decoupling. This design is adaptable to widely used third-party frameworks and is capable of integrating with third-party platforms and data lakes, whether they are existing or newly established.
In September 2022, ABB introduced ABB Ability Cyber Security Workplace (CSWP), which integrates security solutions from ABB and other providers into a unified, comprehensive digital platform, enhancing the protection of critical industrial infrastructure. This platform enables engineers and operators to more swiftly identify and resolve issues, thereby reducing risk exposure by making cybersecurity data more accessible and easier to manage.
Order a free sample PDF of the Oil And Gas Security And Service Market Intelligence Study, published by Grand View Research.
0 notes