#Pentest
Explore tagged Tumblr posts
Photo



Hello guys! How are you doing? I am trying to keep up with Angular studies, plus I am doing a short Pentest classes in order to understand it a little bit more, as I requested some Pentests at work for a special team inside the company. It is very interesting, to understand the vulnerabilities that can occurs, and how to think about them while we are creating the architecture of applications, databases, etc. I will start new Spring boot courses as soon as possible too. Yesterday I started for real in the architecture team at work, and I am terrified as I already have some deadlines I must look forward to things I am not an expert yet (✖﹏✖) Well, I will do my best, and ask for help whenever I need (≖͞_≖̥) Keep studying, keep pursuing your dreams!
#study#studyblr#studyblr community#programming#programming community#programming struggles#coding#coding community#angular#springboot#must learn java#java#pentest#pentesting#software development#study daily#javascript#keep dreaming#keep fighting#keep studying#somebody help#study struggles
11 notes
·
View notes
Text
2 notes
·
View notes
Text
Intercepting Flutter app traffic
Introduction this is an extract and sample of some of the work we do while pentesting in CyberSift Flutter and the underlying dart engine do not respect certificate and proxy system settings. Sometimes, frameworks like reFlutter dont work 😢 The below helps get around this. The idea at a high level is to: Setup a burpsuite transparent proxy Transfer the burpsuite CA to a rooted android…
View On WordPress
0 notes
Text
¿Qué es una prueba de Pentesting o Pentest?
La práctica del Pentesting, o Penetration Testing, es un componente esencial de la ciberseguridad.
Es un método simulado y autorizado para atacar un sistema informático, una red o una aplicación web para identificar vulnerabilidades que un atacante podría explotar.

La prueba de penetración a menudo se compara con un chequeo médico regular. Así como los médicos realizan una serie de pruebas para comprender la salud general de un paciente, los profesionales de seguridad de la información utilizan Pen Testing para descubrir debilidades en la seguridad de un sistema.
Las pruebas de penetración se clasifican en tres tipos: pruebas de caja blanca, pruebas de caja negra y pruebas de caja gris. En las pruebas de caja blanca, el evaluador tiene toda la información sobre el sistema que se va a probar. En las pruebas de caja negra, el evaluador no tiene información sobre el sistema. La prueba de caja gris es un híbrido de las dos anteriores, donde el evaluador tiene acceso parcial a la información del sistema.
El proceso de prueba de penetración se divide en cinco fases: reconocimiento, escaneo, obtención de acceso, mantenimiento de acceso y cobertura de senderos. Recon implica recopilar información sobre el objetivo. El escaneo es la fase en la que el evaluador identifica posibles debilidades. Obtener acceso es cuando el evaluador intenta explotar estas vulnerabilidades. Mantener el acceso implica que el evaluador intente permanecer en el sistema para recopilar la mayor cantidad de datos posible. Trail Coverage es la fase en la que el evaluador intenta borrar toda evidencia de que el sistema ha sido pirateado.
Pen Testing es una práctica importante para garantizar la seguridad de un sistema. Permite a las organizaciones identificar vulnerabilidades en sus sistemas y tomar medidas para corregirlas antes de que un atacante pueda explotarlas. Además, Pen Testing también ayuda a las organizaciones a cumplir con las normas de seguridad de la información y proteger sus datos confidenciales.
Para realizar pruebas de penetración efectivas, es esencial tener una comprensión sólida de los conceptos de seguridad de la información, así como habilidades prácticas en diversas herramientas y técnicas de piratería. Además, los evaluadores de penetración deben seguir un estricto código de ética para garantizar que no causan daño a los sistemas que están probando ni violan la privacidad de los usuarios.
En resumen, el Pen Testing es una parte vital de la seguridad de la información. Proporciona una evaluación realista de la postura de seguridad de un sistema y ayuda a las organizaciones a proteger sus sistemas de las amenazas cibernéticas. Con el aumento constante de los ciberataques, la demanda de profesionales capacitados en Pen Testing está en su punto más alto. Por lo tanto, aprender sobre Pen Testing y adquirir habilidades en esta área puede abrir muchas oportunidades profesionales en el campo de la seguridad de la información.
Este capítulo de nuestro curso de libro electrónico lo equipará con el conocimiento y las habilidades necesarias para realizar pruebas de penetración efectivas. Cubre todos los aspectos del Pen Testing, desde conceptos básicos hasta técnicas avanzadas. Al final de este capítulo, podrá identificar vulnerabilidades en sistemas y redes, explotarlas para obtener acceso y tomar medidas para solucionarlas. Además, también aprenderá sobre las responsabilidades éticas de un evaluador de penetración y cómo seguir las mejores prácticas para garantizar la seguridad y privacidad de los datos.
0 notes
Text
#linuxcommands#TheCyberNerd#pentesting#pentest#linux#cybersecurityawareness#cybersecurity#LinuxDistros#kali#hackers#hacker#hacking#kalilinux#systemadministration#rhcsa#linuxsystemadministration#linuxadmin#linuxadministrator#pentester#cybersecuritycourse#cybersecurityprofessional#cybersecuritytraining#problemsolving#troubleshooting
0 notes
Text
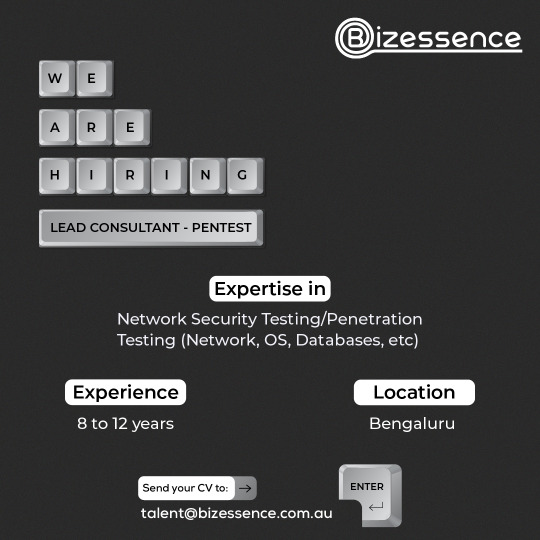
Are you a seasoned Penetration Tester ready to lead the charge in securing digital landscapes? As a Lead Consultant in our cybersecurity team, you'll spearhead penetration testing initiatives, fortify defenses, and guide a talented team of ethical hackers. Apply now and be a part of our mission to safeguard digital landscapes!
Apply now!
Job Description - https://bizessence.com.au/jobs/lead-consultant-pentest/
#bizessence#leadconsultant#pentest#cybersecurity#penetrationtesting#cyberdefense#digitalsecurity#techjobs#itsecurity#ethicalhacking#cyberrisk#networksecurity#cyberthreats#techsecurity#newjob#jobvacancy#jobseekers#jobsearch#nowhiring#hiringnow#bengalurujobs
0 notes
Text
0 notes
Text
Você sabe a diferença entre Gerenciamento de Vulnerabilidades e Análises de Vulnerabilidade?
O gerenciamento de vulnerabilidades e a análise de vulnerabilidades são dois conceitos distintos, embora estejam relacionados na área de segurança da informação. Vamos explorar as diferenças entre eles:
Gerenciamento de Vulnerabilidades:
Definição: O gerenciamento de vulnerabilidades é um processo contínuo que visa identificar, avaliar e tratar as vulnerabilidades presentes em sistemas, redes e aplicativos de uma organização.
Fases do Processo:
Detecção: Identificação de vulnerabilidades por meio de escaneamento, testes de segurança e outras técnicas.
Priorização: Classificação das vulnerabilidades com base em critérios como severidade, potencial de exploração e impacto nos negócios.
Remediação: Desenvolvimento e implementação de planos de ação para corrigir ou mitigar as vulnerabilidades identificadas.
Monitoramento Contínuo: Acompanhamento constante para garantir que as medidas de segurança sejam eficazes e para lidar com novas vulnerabilidades.
Análise de Vulnerabilidades:
Definição: A análise de vulnerabilidades é uma atividade específica que envolve examinar um sistema, rede ou aplicativo em busca de possíveis falhas de segurança.
Foco na Identificação:
Exploração: Uso de ferramentas e técnicas para identificar e explorar vulnerabilidades existentes.
Testes Manuais: Inspeção detalhada por profissionais de segurança para descobrir vulnerabilidades que podem não ser detectadas por ferramentas automatizadas.
Relatórios: Documentação das vulnerabilidades encontradas e fornecimento de recomendações para correção.
Resumo: O gerenciamento de vulnerabilidades é um processo mais amplo e contínuo que abrange a identificação, avaliação, priorização e remediação de vulnerabilidades ao longo do tempo. A análise de vulnerabilidades, por outro lado, é uma atividade específica dentro desse processo, focada na identificação e exploração de falhas de segurança em um ponto específico no tempo. Ambos são essenciais para manter a postura de segurança de uma organização.
1 note
·
View note
Text
hackthebox sink writeup
0 notes
Text
youtube
𝐋𝐚𝐬𝐭 𝐂𝐡𝐚𝐧𝐜𝐞 𝐭𝐨 𝐆𝐞𝐭 𝐮𝐩 𝐭𝐨 𝟓𝟏% 𝐨𝐟𝐟 𝐨𝐧 𝐂𝐲𝐛𝐞𝐫 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐂𝐞𝐫𝐭𝐢𝐟𝐢𝐜𝐚𝐭𝐢𝐨𝐧𝐬 𝐚𝐧𝐝 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐄𝐧𝐫𝐨𝐥𝐥 𝐧𝐨𝐰: https://forms.gle/PSYx6787FhDmjYgG7
𝐃𝐌 𝐭𝐨 𝐠𝐞𝐭 𝐚𝐧 𝐮𝐩𝐭𝐨 𝟓𝟏% 𝐝𝐢𝐬𝐜𝐨𝐮𝐧𝐭 𝐨𝐧 𝐭𝐡𝐞 𝐂𝐲𝐛𝐞𝐫 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐜𝐨𝐮𝐫𝐬𝐞𝐬. 𝐄𝐧𝐫𝐨𝐥𝐥 𝐧𝐨𝐰: https://mailchi.mp/b8e123dd9bf8/securium-academy
🔗Linkedin: https://www.linkedin.com/company/secu… 🔗Twitter: https://twitter.com/Securium_academ 🔗Facebook: https://www.facebook.com/SecuriumAcad… 🔗Instagram: https://www.instagram.com/securiumaca…
#insecure#dataprivacy#data#android#mobileapplication#mobileappsecurity#androidsecurity#pentesting#cybersecurity#ethicalhacking#cybersecuritytraining#pentest#datastorage#securiumacademy#Youtube
0 notes
Text
youtube
0 notes
Text

For many organizations, one vital benefit of pen testing is that it will give you a baseline to work upon to heal the risk in a structured and optimal way. A pen test will present you with a list of vulnerabilities in the target environment and other adjoining risks. And what you acquire from the engagement is high-order risk evaluation so that the vulnerabilities get segmented into High/Medium/Low-risk issues. To book your customized consultation, bridge our pen testing specialists now.
0 notes
Text
Secure Your Laravel App: Fix Insufficient Transport Layer Security (TLS)
Introduction
Transport Layer Security (TLS) is vital for ensuring secure communication between clients and servers over the Internet. Insufficient TLS configurations can leave your Laravel web applications exposed to various cyber threats, like Man-in-the-Middle (MitM) attacks. In this blog post, we’ll explain the risks associated with insufficient TLS security in Laravel and provide a detailed guide on how to configure your Laravel application for optimal security.

Additionally, we’ll show you how to check and resolve potential TLS issues using our free Website Security Scanner tool.
What is Insufficient Transport Layer Security?
Insufficient Transport Layer Security occurs when a website fails to use strong encryption protocols like TLS 1.2 or higher, or when it doesn't properly configure SSL certificates. This exposes web applications to data interception, tampering, and attacks. A properly configured TLS ensures that all data transmitted between the server and client is encrypted and secure.
Common Issues in Laravel with Insufficient TLS Security
Some common causes of insufficient TLS in Laravel include:
Outdated SSL Certificates: Using deprecated SSL/TLS protocols (like SSL 3.0 or TLS 1.0) that are no longer considered secure.
Improper SSL/TLS Configuration: Misconfiguration of the web server or Laravel app that doesn’t force HTTPS or downgrade protection.
Weak Cipher Suites: Servers using weak ciphers, making it easier for attackers to break the encryption.
Lack of HTTP Strict Transport Security (HSTS): Without HSTS, an attacker can force the browser to use an insecure HTTP connection instead of HTTPS.
How to Fix Insufficient TLS in Laravel
Upgrade Your Laravel App’s TLS Protocol To enforce TLS 1.2 or higher, you'll need to configure your server to support these protocols. Here’s how you can configure your server to prioritize stronger encryption:
In Apache: Modify the ssl.conf file:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
In Nginx: Edit your nginx.conf file:
ssl_protocols TLSv1.2 TLSv1.3;
These configurations will ensure that your server uses only secure versions of TLS.
2. Force HTTPS in Laravel Laravel provides an easy way to force HTTPS by modifying the .env file and the config/app.php file:
In .env file:
APP_URL=https://yourdomain.com
In config/app.php file:
'url' => env('APP_URL', 'https://yourdomain.com'),
This will ensure that all requests are redirected to HTTPS, preventing insecure HTTP access.
3. Enable HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security is a web security policy mechanism that helps to protect websites against Man-in-the-Middle (MitM) attacks by forcing clients to communicate over HTTPS. Here's how to add HSTS headers to your Laravel app:
In Apache: Add the following line to your ssl.conf or .htaccess file:
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains"
In Nginx: Add the following line to your nginx.conf file:
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always;
4. Use Strong Cipher Suites Weak cipher suites allow attackers to break the encryption. You can configure your server to use strong ciphers:
In Apache:
SSLCipherSuite HIGH:!aNULL:!MD5:!3DES
In Nginx:
ssl_ciphers 'ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';
5. Use a Valid SSL/TLS Certificate Ensure that your website uses a valid SSL/TLS certificate from a trusted Certificate Authority (CA). You can get a free SSL certificate from Let's Encrypt.
How to Check TLS Configuration with Our Free Tool
Before and after implementing the changes, it’s essential to check the security status of your website. You can use our free Website Security Checker Tool to evaluate your website’s TLS configuration.
Go to https://free.pentesttesting.com.
Enter your website URL to start the scan.
Review the vulnerability assessment report for TLS issues.
Screenshot of the Free Tool
Here’s a screenshot of the free Website Security Checker tool in action:

Screenshot of the free tools webpage where you can access security assessment tools.
Screenshot of a Vulnerability Assessment Report
After running the scan to check website vulnerability, you’ll receive a detailed report highlighting any security vulnerabilities, including issues related to TLS. Here’s an example of the vulnerability assessment report:

An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Ensuring sufficient Transport Layer Security in your Laravel app is crucial to protecting sensitive data and preventing attacks. By following the steps outlined in this blog, you can fix any TLS issues and enhance the security of your web application.
Don’t forget to check your website using our free Website Security Checker tool to identify any existing TLS vulnerabilities and other security flaws.
Need help? Contact us at Pentest Testing Corp for professional vulnerability assessments and penetration testing services to secure your website further.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#tls
4 notes
·
View notes
Text
Info Sec Machines página de Search Engines dónde las maquinas se pueden explotar para encontrar vulnerabilidades y reportarlas ¡Muchísimo repertorio! donde podrás practicar de forma totalmente gratuita.

0 notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
27 notes
·
View notes