#Online Monitoring Data
Explore tagged Tumblr posts
Text
Brand Monitoring Services
Online brand monitoring works straightforwardly. It helps analyze your brand on social media and other web sources. Additionally, it stores the relevant data for future analysis. We efficiently provide brand monitoring services using different data scraping tools.
#Brand Monitoring Services#Online Monitoring Data#Brand Channel Data Monitoring#Map Violations#Brand Data Monitoring#Web Data Scraping#Data Scraping Services#Online Brand Solution
1 note
·
View note
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Text
What happens when you post info and pictures of your kids:
youtube
#data brokers#identity theft#baby monitors#data collection#surveillance#protect kids#protect children#data privacy#online privacy#internet privacy#privacy#digital footprint#Youtube
0 notes
Text
parental internet monitoring pisses me off.
#it’s so fucking invasive#one time my parents witchhunted one of my online friends who was exactly who he said he was because they decided he’s a predator#he was not#he was a disabled child on the internet#which completely obliterated like 50% of my friends#now they’re using some app that doesn’t accurately report data and also monitors messaging????#like wtf#i am no longer subject to it but my siblings are#also my mom cried because i watched the trailer for deadpool at like 14 years old#delete later
0 notes
Text
Cloud-Based Time Attendance Systems
Cloud-based time attendance systems provide flexibility and scalability for modern businesses. These systems allow real-time tracking of employee attendance from any location, making them ideal for remote teams and companies with multiple locations. By leveraging cloud technology, data is stored securely and can be accessed from any device with an internet connection. Cloud-based systems eliminate the need for on-premise hardware, reducing maintenance costs and ensuring that all records are synchronized and up-to-date. They integrate easily with payroll and HR platforms, offering seamless management of work hours, overtime, and leave tracking. This improves efficiency and enhances decision-making based on real-time data.
More info: https://ahalts.com/solutions/hr-services/outsourcing-time-attendance

#cloud-based time attendance#online employee tracking#remote attendance solutions#real-time attendance monitoring#cloud time tracking#attendance data syncing
0 notes
Text
Your Social Security Number Might Be at Risk
Your Social Security Number Might Be at Risk: Here’s What You Need to Know Imagine waking up one day to find out that your Social Security number, address, and other personal details have been stole and are being sold on the dark web. Scary, right? Unfortunately, this nightmare scenario could be a reality for millions of Americans, thanks to a recent massive data breach. Let’s dive into what…
#credit monitoring#Data breach#digital safety.#identity theft#National Public Data#online security tips#personal information theft#Social Security number#USDoD
0 notes
Text
To the people in the OTW Tumblr Inbox asking about how the OTW is responding to the American Election.
This is a separate post (and not a response to a specific message) because we all need to see it.
Folks have been asking Support (through the form) as well as the other social media mods, and we have now been given the following to tell you.
We are continuing to closely monitor political developments that may affect AO3 and the OTW as a whole. First, we want to assure you that there are several factors that tend to protect AO3 and its users from legal risks and challenges. These include that we are a non-profit, do not host images, do not use algorithms to promote or advertise content to users, are not aimed at children, and collect very little user data. The results of the 2024 U.S. election are deeply concerning, but the OTW remains committed to providing an inclusive space for fannish expression and will continue to fight for fans' free expression, both in court and through legislative efforts, in the U.S. and worldwide. We have seen that fans are a powerful force for promoting free expression, and we will continue to inform people about opportunities for their voices to be heard. If a bill is likely to be passed in the future that could impact our ability to provide services, our legal team will be prepared to offer updates, guidance, and legal support to our users. Fans are not alone in this fight. Both the American Civil Liberties Union (ACLU) (https://www.aclu.org/news/civil-liberties/the-aclu-is-fighting-back-against-trump ) and the Electronic Frontier Foundation (EFF) (https://www.eff.org/deeplinks/2024/11/2024-us-election-over-eff-ready-whats-next ) made preparations for this outcome and have developed strategies to combat anticipated efforts to curtail online freedoms. We urge our users to support these organizations and others as they fight for your rights and ours.
<3 Mod Remi
#organization for transformative works#otw#archive of our own#ao3#election 2024#i'm not tagging any of the folks who sent in asks#but know that i (mod remi) have been waiting for the Official Response about it
6K notes
·
View notes
Text
Brand Tracking Guide: Methods, Benefits, and a Case Study
Discover the essential methods and numerous benefits of brand tracking in our comprehensive guide. Learn how to effectively monitor brand performance and make informed decisions to enhance your brand's success.
#Brand tracking#Brand awareness#Brand perception#Brand equity#Market research#Consumer insights#Competitive analysis#Marketing strategy#Consumer behavior#Brand loyalty#Customer satisfaction#Market trends#Data analytics#Performance measurement#Brand positioning#Market intelligence#Tracking metrics#Brand health#Brand image#Brand recall#Purchase intent#Customer engagement#Social media monitoring#Online presence#Customer sentiment#Brand consistency#Trend analysis#Benchmarking#Perception gaps#Target audience
0 notes
Text
Between these four walls



pairing: lee felix x afab!reader
genre: thriller/sci-fi, smut, fluff
synopsis: lee felix is your 89% match. please proceed to the house assigned to you where your relationship will be subjected to various tests. if you manage to complete all objectives and get your match to 100% you may proceed to leave. sex is strictly prohibited. remember, they're always watching.
wc: 13.4k
warnings: desc. of drowning, illness, drugging, tripping (psychedelics/stimulants), mention of needles, paralysis, gutting a fish (yes that's a warning), some blood
nsfw warnings: fingering, handjob, unprotected sex, spanking, cumshot
a/n: felix always inspires me for these kinds of concepts. i hope you enjoy💜
~ divider by @anitalenia
~ masterlist
Lee Felix. 89% match. Congratulations!
You stared at the device in your hand, your heartbeat picking up speed. Finally. Finally you had someone you matched with. The last time you tried a similar, underdeveloped program like this, it only led you to more disappointment and heartbreak.
But, everyone you knew was raving about Cupid Corp. and how they found the love of their life after participating in their program. You asked questions, curious about why they stayed so long in the Cupid Corp. village, what they had to do to get their match to a 100, to walk out with them hand in hand.
Their faces would change from the happy expressions and shiny eyes into something dull, drained of color.
"We signed a document that prohibits us from revealing anything." they'd answer.
It all sounded so mysterious and a little alarming but you were so damn tired of being lonely and seeing all these people walking out of Cupid Corp. with big dumb smiles on their faces.
So, after doing some thinking, you applied.
It was a long process, to say the least. There were tests you had to take, all of them online. Starting with a psychological test, then an IQ test, then a personality test. It took them a month as they asked for everything, from your family disease history to your hopes and dreams for the future.
The more data they gathered, the more detailed your profile became. You even had a few online interviews with a woman named 'Cherry' whose face you couldn't see as she was wearing some sort of mask, only her cherry red lips were visible to you.
"We will take your data into consideration and calculate the best match. Thank you for applying at Cupid Corp. We hope you find your dream lover." the woman talked in a monotone voice.
You didn't wait for too long. Only four days later, you got a package from them, inside it a round device with a screen and one button. You pressed it and when it came to life you were greeted with your match. Just his name and the percentage.
With it, you got a document that stated the location of the village as well as your house number, 14B and a ton of rules, most of them prohibiting you from talking about the activities and 'tests' inside the village as well as a 'no cellphone' rule. You thought it was kind of weird, but you didn't want to back out now. Not when you had a match with such a high number.
It can't be so hard to get it up to 100, right?
You read through all the rules, coming up to the last one.
'You and your partner are not allowed to engage in sexual activites during your stay in the village. Kissing and physical touch is fine unless it is erotic or stimulating in that sort of way. After you sign this paper, you have agreed to all the rules above and are aware that you will be filmed and monitored 24/7.'
You gulped, some kind of unease washing over you as you stared at the document. The little cupid drawing that was the company's logo looked so sweet and innocent but it didn't help the churning of your stomach. Taking a deep breath in, you grabbed you pen and signed the paper.
There is no going back now.

As soon as you entered the village through the gate, it felt like you walked right into a fairytale. The houses were all pretty pastel colors with white picked fences and gardens full of all sorts of beautiful flowers. Everything looked perfect.
The only weird thing was that you didn't see another person anywhere as you walked. It was eerily quiet, only your footsteps were echoing on the pavement and the sounds of your suitcase being dragged behind you. The village was far away from the bustling city so you couldn't hear any sound for miles.
Then you saw it, 14B, a pretty pastel blue house and you smiled to yourself, it looked so cute and cozy. Your heart suddenly skipped a beat when you noticed someone standing outside by the fence.
It was a guy close to your age, and as soon as he noticed you coming towards him, a big smile spread on his face. He waved awkwardly and you waved back as you neared him, your heart hammering in your chest. When you got closer to him, your stomach did a little flip.
He is so beautiful!, you thought as you observed his smiling face, his warm chocolate eyes, his plump heart shaped lips and all the pretty freckles adorning his skin.
"I'm Felix. Nice to meet you." he said, pleasantly shocking you with his deep voice.
"Y/n. Nice to meet you too." you smiled, your face burning up. You hoped you didn't look like an awkward tomato in front of this beautiful man, who was your match! You were already swooning over him as he helped you get your suitcase inside, dragging both of your luggage together while you looked around the garden.
"I guess this is our house." he said as the two of you walked in. You noticed right away that it was decorated in the way you wanted to decorate your dream house, a question you had to answer in one of the tests they gave you. You also noticed some knick knacks you didn't recognize, they were probably something Felix wanted to have in his house.
"They really went all out with the decorations." you said as the two of you made your way to the kitchen and Felix chuckled.
"They did." he nodded, the air between you a little awkward.
"Oh. What's this?" you noticed an envelope adressed to the both of you on the kitchen table.
You picked it up and opened it as Felix peered over your shoulder.
"Dear Felix and Y/n. Welcome to our Village of Love! We hope you enjoy your stay, no matter how short or long it is. You'll find everything you need inside your house, we hope you find it cozy and that you settle in well. Take your time to get used to your surroundings and learn a little about each other before you move onto the next phase. Tests will begin shortly. Have fun!" you read out loud before looking up and seeing a camera staring right at you, the red dot blinking.
"Tests, huh? Doesn't sound too fun." Felix said and you nodded.
"No, it doesn't." you shook your head. "Do you know anything about what happens here?"
"I have no idea. I asked a few of my friends and no one would tell me."
"Isn't that kind of suspicious?" you asked and Felix chuckled nervously, looking up at the camera.
"Aren't they like listening to us right now?" he whispered.
"I'm sure everyone who came here wondered about the program." you shrugged.
"I guess we will find out." Felix said, still being somewhat quiet as he kept eyeing the camera.
You walked over to the fridge and opened it, finding all sorts of groceries inside it, mostly your favorite food and probably Felix's.
"Hungry?" you looked back at him and as if on que, his stomach growled.
You giggled and he laughed, the sound filling up your ears and tugging at your heart.
"I'll take that as a yes. Do you wanna cook together?" you asked and he nodded eagerly.
"I'd love that." Felix answered with a sweet smile so the two of you pulled your sleeves up and washed your hands, getting ready to tackle dinner together as you maneuvered the unknown space.
"What made you decide to apply to this program? You don't seem like you'd have a problem finding a partner." you started the conversation and his cheeks became rosy as he chuckled.
"Well, I tend to fall for the wrong people. The ones who use my kindness against me. And I really don't wanna hurt anymore or just experiment and 'try' again. I want to know that I have the real deal, you know? To be sure that the person is my ride or die."
The honesty in his answer took you by surprise.
'I want my partner to always be honest with me, to tell me the truth even if it is painful.'
You remembered the line you wrote when you were asked to put down on paper everything you wanted in a partner. They had probably looked at Felix's personality test as well as yours, and the things you had written down as your dream partner, putting the two of you together that way.
Your cheeks burned as you remembered how high your percentage is. He must really be the man from your dreams which would make you the woman of his. Butterflies swarmed your stomach.
"What about you?" Felix snapped you out of your thoughts as you continued cleaning the meat.
"Oh, same. I was disappointed many times before. I just want to find someone that will feel like home." you smiled at him.
"Exactly." he agreed. "So, what do you think the tests will look like? Do you think they'll be similar to the ones we had to do while applying?"
"My guess is as good as yours. Though, I must admit I do feel a bit uneasy with all the people not being allowed to say what happened while they were here..." you trailed off, before sighing.
"Then again, they all looked so happy with their partners." you finished. "And I want that."
"Yeah, I feel a bit uneasy myself but we'll go through this together, right?" Felix gave you a shy smile and you nodded as your cheeks warmed up.
After cooking dinner and eating, you had learned a bit more about each other, finding it incredibly easy to keep the conversation going like you've already talked many times before, sharing similar viewpoints and interests. It seemed too easy and you knew that you didn't have to necessarily agree on everything or love all the same things to be a match.
There was definitely something deeper there than the superficial stuff like hobbies and favorite colors when you've already gotten to 89% without even interacting with each other.
"Should we do a tour of the house?" Felix asked when you finished cleaning up.
"Sure, let's do it." you smiled and one by one, you visited all of the rooms starting with the living room that was next to the kitchen.
"Oh, we have a tv." you pursed your lips. "I thought we weren't allowed any kind of electronics."
"I guess they thought having movie nights at home is a date we'd both enjoy." Felix pointed to all the dvds on the shelves around the tv. "We have a good collection of every genre. Skipping horror though, I'm not a fan of scary things." he visibly shivered and you chuckled a little.
"I'm fine with those." you said and Felix gasped a little.
"Well if you want us to watch horror movies together just be prepared that I will be hiding behind like five blankets and probably crying my eyes out."
"Aw, it's okay, we don't have to watch them if they scare you so much." you smiled at him, making his heart skip a beat.
"I'll watch them for you. Well, kinda watch them since I'll be under all those protective blankets."
You chuckled together before you made your way upstairs. Your heart immediately skipped a beat and a shiver ran through your entire body when you saw the bed. Of course, you were meant to sleep together in it.
Felix noticed you staring at it, both of your faces red.
"I can sleep downstairs on the couch." he said, as if reading your mind.
"No!" you said a little too quickly. "I mean, I'd feel a lot safer if you were here with me." you admitted sheepishly.
"Oh." his smile was shy. "Then I'll be here with you."
Gosh, he is so sweet!, you thought, feeling overwhelmed that such a sweet person was your very own match. Not even a day with him and he already checked so many of your boxes. You hoped he felt the same for you.
"We have separate bathrooms." Felix noted and you looked to the right to see a door labeled with your name and on the left his name.
"I think there are no cameras in there, so that's why..." he trailed off and immediately you felt your stomach doing flips. They were really making sure you don't do any funny business which was kind of understandable since everything was being filmed. But then again, why wouldn't they make a special room for the two of you? You had so many questions and any possible answer created even more questions.
The two of you then decided to unpack, the sounds of opening and closing drawers filling up the space.
"We have a backyard." Felix said as he stood by the window in your room. "And a pool."
"It looks cozy except the pool. I don't know how to swim." you confessed, shivering a little.
"Really?" Felix looked a bit surprised. "Well, I love swimming so you can sunbathe while I swim?" he added with a giggle.
"I can." you nodded. "The entire house and the neighborhood looks so nice. Which brings me to this, have you seen another person since you got here?" you asked and Felix shook his head no.
"Neither have I. Weird, huh?" you said.
Felix opened his mouth to answer but the sound the doorbell ringing frightened you both.
"Is that... someone at the door?" he lifted one eyebrow.
"Let's go check together." you stood by his side as your heart hammered in your chest.
Felix walked first and you followed behind him, peering over his shoulders as he slowly opened the door.
You were greeted by a smiling woman and man, standing somewhat similarly to you and Felix.
"Hello, sorry to bother you. I'm Gina and this is Ethan. We were paired up today and noticed we were neighbours so we just wanted to say hi."
"Oh." Felix chuckled and you visibly relaxed, now standing beside him.
"This is y/n, and I'm Felix. Nice to meet you." you all shook hands, deciding to meet up tomorrow for breakfast since the program encouraged couples who were paired up at the same time to become friends.
"You okay?" Felix asked after closing the door.
"I just can't shake off this weird feeling." you shook your head.
Felix bit on his lip, his eyes raking all over your form gently as you hugged yourself. Tentatively, he reach out and brushed his knuckles on your cheek.
"I'm sure you just need time to adjust." he smiled, and you shivered from his gentle touch, your eyes fluttering.
"Yeah. Maybe a good night's sleep is all I need."
"There you go. Positive thoughts." Felix smiled brightly, warming you up instantly.
You got ready in your separate bathrooms and you came out first, claiming your side of the bed as you sat, leaning your back against the headboard and fidgeting with your fingers. Felix came in after a minute or so, smiling at you slightly as he hesitantly lifted up the covers and slid in.
"You sure you're okay with this?" he turned to you, his deep brown eyes looking big and doe like.
"Yes, I'm comfortable." you nodded. "You?"
"Of course. Just making sure you feel okay." Felix then smiled sweetly, making your stomach flip again.
"I am." you whispered. "Um, it's just weird not to have my phone to play with before sleeping." you looked around, noticing a stack of books on a shelf.
"Tell me about it. I'm like chronically online, it's a problem." Felix shook his head with a chuckle. "Or like playing videogames. My computer will be so dusty when we get out of here."
You giggled at him as he scrunched up his face and made a cute whiny sound.
"I like videogames too. We should play together soon."
"Wow, you really are the girl of my dreams." Felix looked at you, wiggling his eyebrows and you laughed, your entire body on fire from the giddiness he made you feel.
He slid down then, getting comfy on his side and you followed suit, relaxing between the clean sheets and melting into the soft pillow.
"How long do you think it will take us to get out of here?" you whispered after a few moments of silence.
"I hope not too long." Felix whispered back. "Sweet dreams, y/n." he added after another pause.
"Night, Felix." you smiled before turning on your side and closing your eyes.
You were nervous for what's to come but Felix's presence gave you a sense of comfort and safety you didn't know you needed. Just the sound of his breathing calmed you down and slowly lulled you to sleep.

Your eyes fluttered open and for a moment you were completely confused. You blinked a few times, rubbing the sleepiness from your eyes as you took in your surroundings.
Right. You had come to the Village of Love yesterday, with your match. Which made you turn around quickly and gasp when you noticed the other side of the bed was empty.
"F-Felix?" you said, your voice a little raspy from sleeping. For a moment, you felt the dread creeping in but then you heard clinking, followed by a few curses coming from downstairs.
Upon arriving to the kitchen you were greeted by a frantic and disheveled Felix. You had to supress in a laugh, but it still seeped out in small giggles.
"Oh, y/n!" he exclaimed, turning around with his eyes slightly widened and his pink lips parted. "I barely slept last night so I got up like at 6am? I wanted to make myself useful so I tried making pancakes? I swear they taste better than they look! It's just that I'm usually not a morning person so-"
"Felix." you stopped his rambling, coming closer to him as you chuckled into your palm, your other hand gently placed on his arm to soothe him.
"Felix, it's okay. I'm sure the pancakes are delicious." you looked down at the half burned scraps of pancakes. "It's the thought that counts." you added with a giggle. "Aren't we meeting our neighbors for breakfast anyways?"
"Oh. That's right, we are. I'm silly." he sighed, turning the stove off with a defeated pout.
"You're cute." you said without thinking, your cheeks warming up as soon as those words left your mouth.
"You think so?" Felix chuckled, a little smirk forming on his lips and you nodded as he stared at you intently. "You're cuter." he leaned in, his breath hitting your face and you almost dissolved right then and there.
"Oh, shut up." you chuckled, making him laugh. "Let's go get dressed."
You got ready in your separate bathrooms, wondering how everything will play out for however long you'll be here. You decided to wear a dress with a floral pattern, something comfy and flowy. You hoped Felix would like it as much as you did.
And he seemed to be stunned the moment you walked out of the bathroom, giving you elevator eyes as he gulped visibly, his cheeks becoming rosy. You stood there nervously as he seemed to be lost in a trance.
"Felix?"
"Oh." he looked up at your face, the redness creeping up on his neck. "You look really pretty."
"Thank you." you giggled, your heart rate picking up while he smiled at you.
"Shall we?" he asked, reaching his hand towards you. You nodded, sliding your hand into his, your palms pressed together and fingers entwined.
They fit perfectly together, like two pieces of a puzzle that were waiting to be completed forever.
You met up with Gina and Ethan who were also holding hands, waving at you enthusiastically.
"Morning, neighbors!" Ethan smiled at the two of you.
"Good morning." you smiled back as everyone greeted each other.
"Did you get the map of the village?" Gina asked and Felix nodded.
"Found it in the living room this morning."
"Us too. Isn't it crazy having all these cameras around?" Gina chuckled and you looked around, noticing that all over the neighborhood there were cameras on every lamp post, every driveway, every front door.
The uneasiness settled in your chest again and you squeezed Felix's hand. He looked at you, squeezing back and giving you a small, reassuring smile. The restaurant wasn't too far away, it was a garden with lots of big trees giving shade to the tables, the sweet smell of colorful flowers mixed with the nice smell of food being cooked, making you even more hungry than you were. Finally, you saw other couples, chatting at different tables and you felt much more at ease. It felt normal.
There was soft music playing from the little building where you presumed the kitchen and servers were situated. The four of you found a table near a koi pond, excitement taking over you as you looked at the pretty fishes swimming around.
"I was about to reach for my phone and take a picture." Felix chuckled and Ethan nodded.
"Same." he said and you shook your head, thinking about how you'd probably do the same thing.
You stared at the koi fishes, who seemed to be mindlessly floating back and forth, confined in such a small pond. You wondered if they ever wanted more freedom, a bigger pond or was this all they knew so they could never think about having more space. Maybe they felt safe in a familiar, tiny enviroment.
One of the servers came to your table with a pen and notepad, writing down your orders and snapping you out of your thoughts.
The four of you made small talk before your food arrived.
"At least these pancakes look better than mine." Felix noted when the plate was placed before him and you chuckled.
"So, what do you guys think the tests will look like?" Gina asked suddenly while you ate. You looked up at the camera above your table and swallowed nervously.
"Isn't it kinda like a video game? We got a map of the place, we will have objectives or tests, we got our 'safe room', like our house where we have supplies..." Felix started and Ethan chuckled.
"I just hope there are no zombies or such. Or like damage." he added and the four of you laughed.
"I'm sure it can't be that bad." you said.
"How high is your percentage?" Gina asked.
"89%." you answered and she gasped a little.
"Ours is 74%. I guess we'll be here longer than y'all." she pouted.
"Well, we can't know that. When we have no idea what awaits us." Ethan said. He was right, you had no idea what Cupid Corp. planned out to put your connection to the test. Your eyes fell on the pond again, the koi fishes spinning around and around in circles, the repetitive motion almost making you dizzy.
~
"Do you wanna take a walk around the village?" Felix asked after you parted ways with the friendly couple next door.
"Yeah, sounds good. I need to get some blood flowing in my legs, we sat for so long."
"We did, I think we clicked with them too. Could it be they put us close to each other so we could become friends?" Felix asked when the two of you started walking, your hands entwined again, making your heart beat faster.
"Probably. I have a feeling nothing is random here." you pursed your lips.
"Me too." he agreed.
The village was really something out of a fairytale book. Not only were the houses cute but there was a cute bakery, a gallery, a flower shop, a cafe and a few other stores for groceries and such scattered around. There was even a little park for picnics and a forest to ride your bike or take a walk there. You saw other people working in all the buildings and couples walking around or sitting in the cafe or riding their bikes. It looked different than yesterday, when everything seemed eerily quiet and abandoned.
You and Felix talked about your families and job, getting to know some random facts about each other as you walked around, the sun warming your bodies up. It felt like you knew each other forever.
That evening, you decided to have your first movie night date. After a short debate since you were both indecisive, you settled on Clueless, a classic, and prepared some snacks and blankets to make the viewing more cozy.
Felix seemed a little nervous and fidgety as you got comfy on the couch, some distance created between you. He played with his fingers and the blanket, picking on it as you clicked play on the tv.
"You okay?" you asked and he nodded quickly, grabbing the bowl of popcorn.
"It's just... I like to cuddle while watching movies. Or um, I like to cuddle whenever, a lot. Physical touch is definitely one of my biggest love languages. I hope you're okay with that." Felix confessed, redness covering his freckled cheeks.
You sighed in relief, a giggle escaping your lips as you scooted closer to him, making his breath hitch.
"Okay? I'm estatic. I'm a big cuddler, it's one of my top love languages too." you nodded and Felix smiled sweetly at you.
"Right. I keep forgetting we matched so well and start feeling nervous. I don't wanna do something wrong, you know? And with the cameras watching, it adds to the awkwardness." he explained.
"I'll tell you if I'm uncomfortable with anything, okay? And you tell me too. Open communication is important." you said and Felix nodded, agreeing. "And forget about the cameras for now. I'm trying not to think about them supervising us the entire time. Let's just enjoy the movie."
"You're really sweet, y/n." Felix smiled cutely, his eyes shining as he stared at you, tongue darting out to wet his plump lips.
You followed the movement for a second, your heart fluttering.
"Says you." you chuckled, poking his cheek and he giggled, relaxing next to you and scooting even closer so that your legs and shoulders touched.
Pretty soon, both of you were relaxed, forgetting that you were being filmed as you enjoyed the movie, laughing and repeating the iconic lines. Your head ended up on Felix's shoulder at one point and his heart started beating fast instantly, his hand reaching for yours. He caressed your skin with his thumb as you giggled at the tv. You've never felt this comfortable with someone you just met.
The entire day was filled with positive experiences that you almost forgot about the weird dread gathering in the pit of your stomach.
You felt a huge attraction towards Felix, your body craved to be in his warmth and when you laid in bed next to him that night, you wanted nothing more than to roll over and hold him. But maybe it was too early for that, you thought as nervousness washed over you.
"Good night, y/n." his warm voice was quiet in the darkness of the room.
"Good night, Felix."
~
The man in the chair leaned over his computer, typing in the log of the day. The two of you were perfect subjects for this village, both of you sweet and kind, ready to welcome each other into your lives. He looked at all the screens that filmed your quiet house, eyes lingering on your calm, sleeping forms. Soon, everything will change.

A whole week has passed by perfectly. It was a little too quiet, too perfect for your liking. You wondered when the actual tests would start, when you were gonna get an envelope with some objective you have to fulfill. It made you feel uneasy the entire time and you had always trusted your intuition so you knew your gut feeling was right.
You had expressed this to Felix and even though he was nervous about the whole experience too, he tried to reassure you that it can't be that bad. That maybe the test had already started by just watching the two of you interact with each other.
It sounded plausible so it calmed you down just a little bit.
At the same time, you couldn't deny the connection building between you and your match. Felix was everything you ever wanted and more, kind and thoughtful, funny and sweet, he listened to you with interest, happy to know every little detail about you; his heart was pure and full of love, not just for you but for everyone. He made you melt on the spot with just one look and smile.
Every time you cuddled while watching movies, you got a little closer, the warmth of his body enveloping you, messing with your senses. You loved being close to him like that and he loved being held or holding you, it didn't matter as long as you were embracing each other in any way.
"It's such a beautiful sunny day. We could have a date by the pool?" Felix suggested one morning, batting his eyelashes at you and pouting cutely.
"Oh, sure. But I'll be watching you as I sunbathe because well, you know." you shrugged.
"Are you scared of the water? I could help you, teach you how to swim. It's good to face your fears." he smiled encouragingly and you chuckled, grabbing his hand.
"Maybe it is. I'll think about it." you smiled.
"Great! That's progress." Felix leaned in, pressing a chaste kiss on your cheek and it was enough to make your heart burst.
For some reason, you didn't think about how the two of you will be almost naked by the pool and that thought crossed your mind only after you put your bathing suit on in the bathroom. A little gasp escaped your lips as your cheeks became completely red.
You decided to throw a little dress over your frame before you walked into the room. Felix was already waiting for you, dressed in swim trunks and a t-shirt. You blushed at the sight of his legs, mentally scolding yourself and trying to calm down your heart.
Felix didn't hesitate to throw his shirt off as soon as you got to the pool. Your eyes immediately went to his abs and chest, a warmness spreading within you as you shifted. He noticed your look, his face and ears warming up. He smirked a little, enjoying the fact that he made you squirm.
"Ugh, I- I left my sunscreen upstairs." you whined.
"I'll go get it for you." Felix said. "Is it in the bathroom?"
You nodded and thanked him as he made his way into the house. After you took your dress off, your attention was grabbed by a sloshing sound of water inside the pool. Your brows furrowed, there was no wind. You gulped, coming closer to the edge of the pool, staring at your distorted reflection as the water kept sloshing.
It was just a milisecond, you couldn't react or realize what was happening, it was as if something invisible had pulled you into the water. With a loud splash your body was submerged under the surface as you started flailing your arms and legs, bubbles coming up where you were desperately trying to breathe. You managed to pull your head above water for a second, panicking as you tried to grab onto the edge of the pool, turning around just in time to see Felix running towards the pool with a terrified expression on his face. You couldn't keep yourself above water but just before you were completely submerged again, a pair of arms wrapped around you, pulling you up to the surface.
You gasped, trying to catch your breath as you clutched onto Felix and he pulled you close, pressing your body into his.
"You're okay, love. I got you. I got you." he kept repeating as he caressed you, holding you tightly as he led you to the shallow part of the pool.
Tears spilled out of your eyes as you sobbed, wrapping your arms around Felix's body, your face buried in his neck.
"It's okay. I'm here. Shh." he tried to soothe you as your body shook against him.
Neither of you noticed the shadow moving away from the window inside your kitchen.
"Let's get you out." Felix led you towards one of the chairs and you sat down as he wrapped a towel around you. He caressed your hair shortly as he grabbed another chair, pulling it closer so it was facing you. He sat down and grabbed your face gently.
"Can you tell me what happened?"
"I- I don't know." your lips trembled.
"I was just standing there and next thing I know, I'm underwater."
"Maybe you slipped?" Felix wondered, his brows furrowed.
"No, it was like something pulled me in." you swallowed and Felix looked back at the calm water.
"Well, whatever it was I am not leaving you alone by the pool anymore. I won't let this happen to you again." he promised, pulling you into a hug, your cheek pressed against his chest. You shivered as you held onto him, but this time it was because you felt his skin against yours. Sure, you held onto him in the pool but you were in such a state of panic that you didn't even feel your body let alone his.
You leaned back a little and looked up at Felix. His eyes travelled down to your lips and he licked at his. Your stomach swarmed with butterflies as your face neared his. Felix held you tighter as your hot breaths mingled, before he pressed his plump lips on yours. You melted instantly as you started moving together, kissing gently and savoring every second of your lips touching like that.
It felt like it was meant to be, like you were made to kiss his lips and he was made to be yours. Felix licked at your bottom lip and you parted them, letting his tongue touch and play with yours. Pressing your body against his even more, you almost forgot about Cupid Corp., the cameras, the pool. But when he bit on your bottom lip, pulling it between his teeth, his hands squeezing your waist, you had a moment of clarity and pulled away with a gasp.
"We can't get carried away." you panted and Felix nodded, swallowing as his dark eyes lingered on your lips. His cheeks were red, his hair messy and his lips looked even more pink after kissing you.
"Sorry. I couldn't help myself, love. I'm really attracted to you." Felix said, pressing his forehead against yours.
"Me too. I like you a lot, Lixie." you smiled and he chuckled sweetly, pressing a few kisses on your lips and cheeks.
"I like you a lot too. I'm so glad I signed up for this program." he said, pulling you into another hug.
"I'm glad to be here too." you tangled your hands in his hair, caressing him and he sighed happily.
"Do you still wanna stay by the pool or you wanna do something else?" he asked and you looked at the water.
"I'll sit here and you go swim." you smiled.
"Are you sure?"
"100%." you nodded and with that, he pecked your lips again and practically skipped towards the pool. You giggled to yourself, knowing he really wanted to swim so you were content with sitting by the pool and just watching his beautiful form in the water.
Goosebumps rose on your neck and you turned to look at the house, feeling like there was some kind of presence there. You tried shrugging it off as you turned back to Felix, watching him having fun and waving at you cutely.
When he got out of the water, you couldn't help the admiration in your eyes as they raked all over his naked wet body, the droplets of water sliding from his chest to his abs and disappearing under the waistband of his swim trunks. Your throat was very much dry in that moment, but your panties were not. Felix smirked at you as he walked slowly, probably trying to seduce you even though you already folded.
He leaned over you, his hands on the armrests of the chair, the water from his body dripping onto yours.
"Enjoyed the view?" he asked as you looked up at him.
"Very much so." you smirked back and he leaned in to kiss you.
"I'm glad you did." he kissed you again. "Let's get inside, it's getting dark." Felix added and the two of you made your way into your house.
As soon as you walked in, a loud beeping noise scared the both of you. You covered your ears as Felix looked around.
"What is that?!" you asked.
"I don't know." Felix yelled over the piercing noise. He followed it with you trailing behind him and holding onto his back.
"Oh. Look!" he exclaimed, grabbing the round device you had gotten in the mail.
As soon as he clicked the button, the loud sound stopped, the screen lighting up.
90%. Congratulations, Felix and Y/n!
"D-did we get a point because of me drowning in the pool?" you shivered.
"I think we got a point 'cause I saved you." Felix bit on his lip, his expression turning into one of worry. You looked up at the camera in the kitchen, your eyes wide. Just what kind of sick game were Cupid Corp. playing? And what did they have in store for you?
~
"You think they really tried to drown me on purpose?" you asked Felix when the two of you got under the covers.
"It seems so." he said as he chewed on his lip.
"I think they could escalate things." you gulped and Felix looked at you, scooting closer to your side.
"What kind of test is that? Who wouldn't jump in to save someone they love? And even someone they don't know. I'd jump in anyways." Felix got upset.
"I know, I don't understand either."
"At least we are closer to 100%." Felix said, reaching out for you. You got closer to him and he smiled sweetly, his arm wrapping around your waist.
"Will you let me hold you like this?" he whispered, rubbing the tip of his nose against yours.
"Yeah, of course." you whispered back, kissing his sweet lips.
"I'll keep you safe, love." he smiled.
"I hope they don't hurt you."
"They can try. I'm stronger than I seem."
"I belive that." you nuzzled into him as you wrapped around each other. It felt so good to be in his embrace, like nothing bad could ever happen to you.

When Felix opened his eyes the next morning and saw you sleeping so soundly in his arms, he almost melted into a puddle. He gently tucked your hair behind your ear, caressing your face as his sleepy eyes observed you.
It didn't take long for you to wake up too, seeing that Felix was already looking at you made you whine and shut your eyes tightly.
"Don't look at me." you said.
"Why?" Felix chuckled as you tried hiding your face with your hands.
"Because I don't look the best when I wake up."
"What are you talking about?" Felix gently moved your hands away. "You're beautiful." he added and leaned in to kiss you but you blocked him quickly with your hand.
"Morning breath."
"Do I look like I care?" he giggled against your palm, grabbing your hand in his and kissing you despite your protests.
"So beautiful." he rasped.
"Has anyone ever told you that you're a sweet talker?" you smirked.
"No, but I'll take that as a compliment." Felix giggled. "Mm. Let's stay like this." he pulled you closer, his chin resting on the top of your head.
"I'd love to. But don't we have a brunch with Gina and Ethan?"
"Ugh. We do. Five more minutes." Felix said and you giggled, pressing your lips into his pulse. You heard his breath hitch and felt him tremble as your lips brushed against his skin.
"Don't make it harder for me to resist you, love." he whispered and kissed your head, making your cheeks warm up instantly.
"Sorry." you leaned back and he gave you a lazy smirk as he played with your hair.
~
"Ethan is sick." Gina whispered to the two of you after you rang the doorbell.
"Sick?" your brows furrowed as you noticed her eyes being shifty, darting left to right like she was on high alert, looking around to spot danger.
"Yes. High fever. Tremors. Headache." she craned her neck to look behind the two of you and you followed her eyesight, not noticing anything out of the ordinary.
"I have to go. I have to go. They're watching, you know? They're watching." she murmured before disappearing into the darkness of her house and closing the door, the clicking sound indicating she had locked it.
"T-that was weird." you swallowed.
"Very weird." Felix backed away, pulling you with him. "You wanna go to brunch still?"
"Yeah." you nodded as the two of you walked away from your neighbor's house.
You kept throwing glances back, noticing the curtain on one of the windows moving as a figure disappeared behind it.
You couldn't stop thinking about the state Gina was in and what the hell was happening inside her house?
Sitting by the koi pond, you couldn't help but think that all of you were just koi fishes and the village was just one small pond that was being observed by a bigger creature.
"You okay?" Felix put his arm around your shoulder, his other hand placed on your knee.
"Just worried about Gina and Ethan. And... us."
"Us?"
"What if the same happens to us. Or worse." you swallowed, your eyes becoming big as you looked at Felix, fear bubbling up inside you.
"It won't."
"How do you know that?" you asked, your eyes filling up with tears.
"I'll keep us safe, I promise." Felix pressed a lingering kiss on your forehead.
Your heart was still hammering in your chest, your stomach churning.
Something was wrong.
~
"Y/n, do you trust me?" Felix held you as the two of you stood in the shallow part of the pool.
"I do. It's just-"
"You're scared, I know. If it becomes too much, we'll get out immediately. But I'd love it if you at least tried. I'll hold you the entire time, okay? I won't let you out of my sight."
His reassuring words chipped away at your fear, replacing it with warmness and safety. You've never met someone like Felix, someone who was so invested in helping you get over your phobia.
"Okay, we'll start walking first." he pulled you in, holding you against him as you clutched at him.
"Relax." he tried soothing you as his hands caressed you and slowly but surely you started feeling relaxed.
"I'll hold you and swim. You try to move your legs like I told you, okay?" Felix guided you and you struggled a little at the beginning but the more he smiled at you and reassured you, the more confident you felt.
"Just stay close." you said.
"Of course, sweetheart." he smiled and your heart leaped out of your chest as your face warmed up.
Soon, you didn't even realize you were moving on your own, with Felix hovering next to you.
"You did it, y/n!" he laughed, his arms wrapping around your waist as he pulled you into his body.
"All thanks to you, Lixie." you giggled, turning around in his arms so you could look at him.
"Well, you had the will to try so it's on you too." he said, pecking your lips. His kisses were addictive, whenever he'd press his lips on yours, it was hard to stop as the two of you clung onto each other like you've been glued together.
The kisses escalated as your tongues massaged each other, your hands roaming on his freckled back. Your legs wrapped around him and he pulled you in closer, chest against chest, his hands on your butt.
"F-Felix." you stuttered, nails digging into his shoulders when you felt his erection brushing against your core.
"I'm sorry." his arms wrapped around your waist as he buried his face in your neck, lapping at the droplets of water dripping down your skin. "I can't help it. You're so delicious, sweetheart." he nipped at your sensitive neck.
"T-the cameras." you looked around at the five different cameras in the backyard.
"I know. I know." Felix kissed your lips with a huff before he swam you both back to the shallow part.
"You can get out if you want. And give me a second to calm down." he looked at you sheepishly.
"Okay." you giggled, wrapping your body up with a towel.
Felix swam a little more while you made some lemonade, keeping an eye on him from the kitchen window.
He got out just in time as you brought the refreshing drink outside. He wiped his body with the towel quickly, throwing it aside as he pulled you closer, making you squeal, the two of you losing balance. You ended up in his lap as he sat in the chair and you chuckled as he squeezed you tightly, rubbing his cheek against your back.
"Are you sure this is a smart position right now?" you asked and he smirked at you.
Before he could answer, the familiar beeping sound blasted next to the two of you. Your heads snapped towards the device you brought everywhere, hoping the percentage would go up.
"Felix! 92%!" you gasped when you grabbed it.
"92? How did we get two points?" he stared at it.
"I have no idea! But we should celebrate. Just 8 more. And then we can leave together." you smiled as you turned you body towards him.
"I can't wait, my love." Felix smiled, leaving kisses on your arm.
You wondered why you got two points. And if it was really that easy.
~
That night, Felix was clingier than usual, completely wrapped around you as he spooned you. His lips kept pressing gentle kisses on your neck and shoulder, making goosebumps rise on your skin, heat erupting inside you.
Felix couldn't help it anymore, his own body betrayed him as he got excited again, being so close to you, feeling you pressed against him, he craved nothing more than to be even closer to you.
"L-Lix." you felt him against your backside.
"Fuck, I'm sorry. Don't worry about it, it'll go away." Felix whimpered quietly, and you squeezed his wrist as he pressed into you tighter, unable to contain himself.
"It's okay." you guided his hand down to your panties, feeling desperate for his touch too.
"Y/n." he whispered. "What about the camera?"
"It's dark. And they can't see under the covers. As long as we stay quiet and don't move too much, we should be fine." you whispered back, pushing his hand beneath the waistband of your underwear.
"That's a test within itself." Felix joked and you giggled.
"Please, Felix." you begged as he hesitated.
"Fuck, baby. You don't have to beg for me. You have me always." he bit on your shoulder, his fingers exploring until they pressed into your clit when you spread your legs just a little so he can have more access. Felix started drawing slow figure eights on your sensitive clit, dipping his fingertips into your heat to gather some wetness and smear it around.
Your breath hitched and you gripped onto the cover, bringing it closer to your lips so you could muffle the little sighs coming out. His tongue darted out to lick at you neck as he played with your clit, moving slower but pressing hard. Felix sunk his teeth into your neck, sucking on it and creating a purple bruise marking you as his. You moaned quietly and he shushed you, teasing your little clit and making you clench around nothing.
"Felix." you said quietly.
"Yes, baby?" he whispered between kisses.
"I wanna touch you too." you said, so quiet so that only he could hear it. Felix's cock twitched against the back of your thigh.
"Okay." he said and you turned around, sliding your panties off and pushing them aside. Felix did the same with his underwear and grabbed your leg, putting it over his so he could spread you a little.
His hand was back between your legs, now without any tight obstacles and you had to bite back a moan as your eyes flitted towards the red dot blinking in the corner. You gripped the cover and pulled it up, only leaving some space for air and so you and Felix can kind of see each other.
You sneaked your hand down his chest and abs, fingers playing with his happy trail leading down to his leaky cock. The tip was already wet with pre cum and Felix almost groaned when you touched him, smearing it around as your fingers massaged him.
"B-baby." the tip of his nose touched yours and he leaned in to kiss you as your hand wrapped around his length. He sighed into your mouth and you swallowed it, breathing in his air while he slowly pushed his finger inside your welcoming heat.
You bit on his lower lip when he pushed in deep, your pussy clenching and begging for more. Felix groaned quietly, pushing into your hand while you moved it slowly, giving him gentle pleasure. Both of you moved in sync with each other, keeping the slow and torturous pace that was somehow sweet. You were both lingering on edge, wanting more.
Felix pulled his finger out and before you could protest, he started pushing two fingers in. The entire time you were making out, swallowing each other's moans and breaths.
"God, faster please." Felix whispered and you looked at the direction of the camera again, excitement rushing through you at the thought of getting caught. You sped up, pumping his cock as he fucked your pussy harder.
"Shh, quiet down love." he said when you started moaning silently.
"Sorry." you whispered and leaned in to kiss his neck. Felix immediately threw his head back, a quiet grunt escaping his lips as you attacked his skin with bites and kisses, flicking your wrist.
"I- I- can't." Felix groaned quietly. "Y/n." his fingers stilled inside you as he came, spilling his hot cum on your thigh, hand and the sheets. You helped him ride his high, kissing his lips and whispering quiet praises against them.
"Bring your legs up." he said, pressing your legs together, sliding his arm under your knees and lifting them towards him.
"Wh-what..."
"Shh. Trust me, sweetheart." he said as he leaned over you a little, his fingers sliding on your wet slit. He slowly pushed them back in, the position of your legs lifted up and pressed together like you were in a fetal position added to the pressure between your legs, his fingertips pressing right into your sweet spot.
"F-Felix!" you whimpered and he pressed his free hand against your lips, shushing you as he started fucking his fingers in and out of you.
You feared that this was definitely visible on the camera, the movement of his hand was too frantic under the sheets. Your muffled whines made Felix lean in and leave sweet kisses on your face.
"Shh, it's okay, just relax and let go, sweetheart." he cooed at you, his tongue licking at your ear.
Your eyes fluttered closed as he removed his hand from your face and pressed his lips on yours, his fingers ramming into your sweet spot repeatedly.
"Lix." you whined against his lips as he licked at them.
"Cum for me love." he encouraged and your pussy clenched around his fingers, your heart beating out of your chest as you let go, spilling your release on his fingers, some of it ending up on the mattress below you.
"Shit." he cursed quietly, caressing your wet pussy.
You clutched onto him, kissing him again like you needed it to breathe.
"You okay?" he asked, his hand searching around for his boxers.
"Y-yeah." you answered. "You?"
"More than okay." he smiled as he grabbed the boxers and cleaned both of you up as much as he could. "Um. We can't really change the sheets now, it would look suspicious." he added, throwing both of your underwear sneakily on the floor next to his side, where the camera wouldn't see.
"We can sleep on your side?"
Felix smiled and pulled you over, making you giggle quietly as the two of you settled against each other. He buried his face in your neck, his hand gently caressing your figure as you played with his hair, running your fingers through his soft locks.
The man in the chair smirked. Bingo.

When your eyes fluttered open the next morning, you were greeted with the cutest sight. Felix was still sleeping, his face smushed against the pillow as he drooled a little. Overwhelmed with your growing feelings for him, you leaned in and bit at his cheek.
Felix groaned quietly and you giggled, kissing where you had bitten him before you went lower, biting his neck and then his shoulder.
"Y/n." his deep voice made you shiver and you giggled against his soft skin again before sinking your teeth into his arm. His eyes fluttered open as he smacked his lips and looked at you.
"Interesting way to wake me up, not gonna lie." he smirked a little before grabbing you and making you squeal as he suddenly flipped the two of you, him being on top.
"Felix!" you chuckled when his fingers ghosted on your sides, tickling you slightly.
"Yes, sweetheart?" he smirked, burying his face in your neck and teasing you with little licks and kisses.
"D-don't. It's daytime, the camera-"
"I'm just gonna bite you a little. Return the favor." he blew on your neck before biting into your skin and sucking. You had to bite on your lip to stop yourself from moaning. Isn't this prohibited too?
"F-Felix, you have to stop." you whined.
"You're lucky the cameras are here. Otherwise, nothing would be able to save you from me." he wiggled his eyebrows and you chuckled, playfully pushing him away.
The morning started beautifully and you completely forgot about the rules whenever Felix smiled at you. You were both walking on cloud 9 and you couldn't wait to get out of this place so you can go anywhere with him by your side.
"Do you think they saw us last night?" Felix asked while the two of you munched on your food.
"I hope not." you said, your cheeks becoming red as you looked away from him.
"Getting shy on me, sweetheart?" Felix smirked, fingers brushing against your cheek.
"A little." you confessed, biting on your lip as your heart sped up.
"Don't be." he smiled wide as he leaned in, pecking your face with kisses. You started chuckling before you grabbed his face and kissed his lips.
"There. Better?" you asked and he nodded.
"Much better." Felix said and stood up to put his plate away. You took another sip of your coffee before a loud crash made you jump.
You turned around instantly to see the plate broken into pieces and Felix grabbing at his stomach.
"F-Felix?" you stood up abruptly, your chair flying on the floor.
Felix struggled to open his mouth and speak, he struggled to breathe as he clutched at both his stomach and chest.
"Oh my god! Felix!" you cried, grabbing at him as his face got red and his eyes watered.
"W-what is happening?!" you panicked, not having any kind of phone or knowing what to do in that moment. You turned to the camera in the corner.
"Help us, you fucking assholes!" you yelled at the camera as Felix shook and heaved in your arms.
A moment passed and his breathing started getting more normal, his face becoming paler in contrast to the redness that appeared before. His eyes were glassy, hands shaking as he slumped against you, falling to his knees. You quickly wrapped your arms around him as he gripped at you, seeking comfort from you. Heat radiated from his body and you touched his forehead, realizing he was burning up with a fever.
"Oh, Felix. Can you hear me?" you held his face in your hands as he looked through you.
His lips opened and closed a few times and he blinked before focusing on your eyes.
"I-it hurts." he rasped, his fingers desperately digging into your arms.
"What hurts, baby?" your body filled up with fear and anger. They did this.
"Everything." Felix sniffled and you helped him get up as he leaned on you.
"Let's get you to the couch." you led him to the living room before making him sit down. He looked horrible, a 180 from just a few moments ago when everything was normal. He was sweating profusely, his skin pale, his breathing heavy.
The doorbell suddenly rang, making you jolt.
"I'll be right back." you said, covering Felix up with a blanket as he was shivering even though he was burning up.
You had no idea who to expect at the door, maybe a paramedic, maybe a savior, maybe an explanation.
But you didn't expect Gina.
"G-Gina?" you eyes widened.
"Here." she shoved a box in your arms.
"W-what is this?" you asked.
"Medicine. They said... I had to deliver it to you. He'll be okay like Ethan. Just be careful. Be careful. They watch, you know? They know everything. They know." she looked a little panicked before she turned around, murmuring to herself and repeating how they watch and they know.
You opened up the box and sure enough there were different vitamins, medicine and bags of tea inside it.
You turned to look at the camera with a scowl on your face before you rushed off to Felix.
"Y/n." Felix whimpered, his bottom lip trembling as he looked up at you with teary eyes.
"It's okay, baby. You'll be okay." you tried to calm him down even though you were panicking too. You quickly fluffed up the pillows and helped him lie down.
"Are you comfy?" you asked.
"C-cold." he shivered, clutching onto the blanket.
"I'll bring another blanket for you." you said.
"Don't leave me!" Felix looked panicked as he gripped at your wrist.
"I won't, I'll be right back, I promise." you leaned down to kiss his burning forehead. He made a little noise but still let you go, albeit reluctantly. After finding another blanket, you tucked him in, taking it upon you to make him some tea, give him medicine and try to get his fever down however you could. You say next to his legs and placed a wet cloth on his forehead making him whine as he threw his arm around your thighs.
It was weird. The way he suddenly developed a high fever was unnatural. He wasn't sneezing or coughing, just shaking and sweating. You racked your brain, spinning different scenarios in your head and ways of how they could make him sick.
Then it clicked. The food.
But, how did you not get sick, just Felix? You couldn't understand how it was possible for these faceless and nameless individuals to play god with your health and safety. And what the hell did that have to do with you being a good match?
You wondered if the two of you could leave before you get to 100. You've never heard of such cases but surely there was a way? Maybe you could run away? Who could stop you, right? You have free will and you can leave whenever you want, you're not a prisoner.
"Y/n." Felix said weakly, his eyes fluttering open.
"Lixie. How do you feel? Any better?" you asked and he nodded.
"A bit." he said.
"I'll make you some soup." you said, knowing you have no other choice than to trust that not all your groceries were laced with some kind of virus.
"Okay." he said and you caressed his face shortly before standing up.
"Call me if you need anything. I won't be long." you said and he nodded again.
As the soup boiled, so did your anger. First they try to drown you then they make Felix sick? What's next on the menu? You looked up at the camera for the nth time.
"Hurt him again and I'll find you." you said quietly but the man behind the screen heard you, typing away on his laptop. He felt a bit bad for you but there was nothing he could do, he was just tasked to watch and report the progress.
"Can you sit up?" you asked Felix after you brought the warm soup to the living room.
"Ugh. Help me." Felix whimpered and you wrapped your arms around him as he held onto you, pulling him into a sitting position.
"I feel weakness in my arms and legs." he muttered.
"You'll be back on your feet in no time." you tried to soothe him as you sat next to him. "If they don't lace more of our food with a virus."
"How are you so sure?" Felix gulped.
"Because I'm taking care of you. And if they try something again I will burn this fucking village down." you made sure the camera picked up what you said and Felix let out a pained chuckle, grabbing at his side.
"Feeling protective over me?" he asked and your cheeks reddened instantly.
"I- I mean... Yes." you nodded and he smiled.
"If I wasn't in so much pain, I'd be really turned on right now." he said and you giggled, rolling your eyes playfully.
"Shut up and eat your soup."
"Feed me?" he pouted.
"Sure." you chuckled, shaking your head a little as he acted cute. Well cuter than usually.
"Will you cuddle me?" he asked after you managed to feed him the soup without making too much of a mess and you nodded, scooting closer to him and covering yourself up with the blanket too.
"Come here." you whispered and Felix leaned in, pressing his forehead into your neck. He was still warm but less than before and you hoped that the worst had passed.
"I don't think it was the food." he whispered suddenly, making goosebumps rise on your skin. The tv was loud enough to not let the camera hear what you were whispering about and after glancing at it you glanced down at Felix's sleepy face pressed against your chest.
"What do you mean?" you whispered into his hair.
"Look at my arm. Very carefully." he whispered back and you pretended to caress him until you uncovered his sleeve, acting nonchalant for the camera. Your brows furrowed as you stared.
"Is that a needle mark?" you asked.
"I think so." he looked up at you and you covered him up and held him tighter against you.
"You think they snuck in while we were sleeping and put some kind of virus into your body?" you asked and he nodded against you.
"That's sick. That's really sick. I- I think we should leave."
"We can't, not until we get to a 100." Felix said, rubbing his cheek against you and squeezing you tighter.
"B-but what if they do something worse?"
"It'll be okay." he muttered as he drifted off.
You sighed, running your hand through his hair soothingly as you stared at the tv absentmindedly, a random movie from the dvd collection playing on it.
You looked at him occasionally, admiring his cute sleeping face. Did you really have to wait until 100 to start your life with Felix?

Over the course of the next two days, you had been by Felix's side the entire time. The medicine worked perfectly and pretty soon Felix was back to his old self, healthy and full of energy.
"Y/n. Love." he held you tightly. "Thank you for taking care of me." he stared at you with sparkly eyes before he kissed you like his life depended on it, stealing your breath away.
"Of course." you smiled as you parted.
The loud sound of the device startled you both. Felix neared it, picking it up and looking at the screen.
"95." he scoffed.
"For what? Almost killing you." you said. "This is some sick game to you, isn't it?" you turned to the camera then, furious.
"Sweetheart, don't. We're almost done." Felix pulled you into him. "I have a plan." he whispered into your hair and you nodded.
You were going to escape the village.
~
That night, you got ready for bed as usual, your hands reaching to open the covers so you could get in. Before you could even touch the blanket, you were grabbed as Felix wrapped his arms around you and lifted you up, almost making you scream.
"Come with me." he pulled you into his bathroom.
"Felix we can't-"
"We're leaving anyways." he said, closing the door before pinning you against it. His hands held your wrists gently but firmly as he pressed his body against yours, nudging your legs apart with his knee.
"Felix." you let out a little gasp when his thigh pressed against your warmth.
He couldn't wait anymore, one hand still pinning your wrists and the other gently holding your chin as he crashed his lips into yours. Both of you whimpered quietly into each other's mouth as your tongues collided. Your mind became fuzzy instantly and Felix was becoming impatient, his hand wrapping around your neck and squeezing ever so slightly as his other hand slid down towards your chest.
"It's hard to keep my cool around you. I just want you so much." Felix talked lowly, both of his hands grabbing your breasts and massaging them. You whimpered, grinding against his thigh on instict.
"I want you too, Lixie. I can't wait anymore."
"Yeah? You want me to take you right here, against the door?" he smirked and you gasped as he leaned back with a smirk, pushing your panties aside and touching your clit.
"Y-yes." you whispered and he chuckled, hands on your waist as he swiftly turned you around to face the door. Your palms slapped against it and you dug your nails in as he slid fingers over your wet pussy.
"I think she's ready to take me." he leaned over you, lips brushing your ear as he pulled his boxers down. You swallowed when you felt the tip of his cock pressing against you. Warmness washed over you and you clenched in anticipation.
"Tell me if it's okay. Or do you want me to prep you?" he asked, his hand sliding down your back.
"J-just fuck me, Felix." you begged and he chuckled darkly.
"My baby has a dirty mouth, hm?" he slid his tip between your folds, back and forth, slowly, teasing you and torturing you.
"Please." you whimpered again and his own desperation got the best of him, he couldn't tease you and himself anymore so he slowly pushed in.
You moaned while he filled you up, your eyes fluttering shut as your knees buckled.
"Fuck. So tight." he groaned, bottoming out.
"L-Lix." you whimpered and he gripped your hips, moving slowly at first, letting you adjust.
You pushed back into him, meeting his thrusts as you let out moans of pleasure, your voice getting more high pitched every time his tip pressed into your sweet spot.
"You take me so well, baby. You really were made just for me." Felix moaned, fucking harder into you, his hips smacking against you.
You were a mess, not even able to answer as he got you drunk on his cock instantly.
"Fuck." Felix groaned as he looked at your ass, his hand coming down on your flesh, spanking you and making you whine out loud.
"You like that, sweetheart?" he smirked behind you and spanked you again.
"Y-yes!" you moaned and he sped up, his hips unforgiving as he shook your body, his hands gropping and slapping. He felt you clenching around him, his arms wrapping around you, hands on your breasts as he pulled on your nipples and played with them.
"Are you gonna cum for me, baby? Make a mess on my cock?" Felix fucked into you harder.
"Yes, ah!" you whimpered, your legs shaking as you spasmed and came all over his length.
"Good girl. You make me so proud." he groaned, chasing his high.
"Y-you have to pull out, I didn't take the pill... Since I got here." you moaned, feeling overstimulated.
"S-shit!" Felix whimpered, pulling out of your pussy and giving himself a few tugs, exploding behind you, his cum landing on your ass and back.
"So pretty." he gripped at your ass. "Mine."
"Yours." you whined back when he spanked you again.
He let out a low chuckle and wrapped his arms around you, turning you so you were facing him.
"That was absolutely not how I imagined our first time." Felix said, pecking your lips.
"How did you imagine it?" you held onto him with a smile on your face.
"Dinner, flowers, you know the whole thing. You put on some pretty lingerie for me and then we make love the entire night." he pressed his forehead against yours.
"Aren't you romantic?" you giggled, kissing him gently.
"I am. A lot." he grinned, pulling you into a hug.
"We can do all that when we get out of here. Which is what we should be doing right now."
"Yeah. You got your bag ready?" he asked and you nodded.
"Let's clean up then."
~
The streets were dark and empty, the only light that was coming from the lamp posts was dim and barely illuminated your path. It must've been around 3am. Dead silence filled up the space, every house was dark and quiet. No one was awake. The two of you stalked towards the gate, knowing the cameras are watching you.
There was no blind spots, they thought of everything. You didn't give a damn anymore. They can come and stop you themselves instead of playing these sick games.
Of course, the gate was locked.
"Felix?" you swallowed and his head snapped towards you. "That wasn't there when we got here, right?" you pointed and he gasped.
Electric fence.
Everywhere you turned to look, there it was.
"What the hell?" Felix frowned. "Are they crazy?"
"Obviously they are." you stated. "What should we do now?"
"How about the forest? Could be connected to like a main road? There's no way they put this electric fence all around." Felix looked frustrated.
"We could try." you nodded, your hand reaching out for his. With fingers entwined you hurried the other way.
Suddenly, a loud alarm pierced through the calm night air, making you both scream out as you grabbed at your ears, the sound pounding inside your head, making you want to pull your hair out.
Your vision became blurry and you tried to stay close to Felix as the sound became even louder and in the corner of your eye, you saw shadows moving.
Everything went black.
~
You woke up in your room, drenched in sweat. It was still dark out and you looked around, noticing Felix was still sleeping and the device on his night stand was blinking.
"Lix." you shook him gently.
"Hm."
"Lix." you repeated, leaning over him to look at the little screen.
"98?" you frowned. "Why?"
"What?" Felix sat up slowly. "What is it?"
"We're up to 98. Because we tried to escape?"
"I- I don't know. Ugh, I feel weird." Felix said and as soon as those words left his lips, you felt lightheaded yourself.
"I can't feel my legs." he gasped.
"What's happening to us? What did they do?" your eyes watered as you felt the same paralyzing feeling.
"T-they drugged us." Felix tried to grab at you but his arms weren't listening to him no matter how much he willed them to move.
"Felix." you whimpered, feeling some kind of tiredness washing over you. "I love you."
"I love you." he whispered back before everything went black again, neither of you noticing the device was now blinking with 99.

The light was barely coming in through the branches, the sun not being completely up yet. The air was damp and smelled of the earth, rain and trees. You took in a deep breath, wiggling your fingers against the ground, feeling the texture of moss under your fingertips.
You felt as if you were floating even though you were very clearly touching the ground. Your eyes slowly fluttered open and you gasped. Everything seemed distorted, like you couldn't focus your eyes on what's in front of you. Weird sounds filled up your ears, ones you couldn't recognize or understand. One moment they seemed like distant shouts and the other it was as if someone was talking gibberish right into your ear.
You lifted your shaky hands towards your face as you felt hot tears sliding down your cheek and into your hair splayed on the earth. Your hands. You were looking at them but it was as if they were separated from your body, like you weren't in control of them. You stared for however long, not being able to conceptualize if it was 10 seconds or an hour.
When you finally sat up, your head started spinning and you saw shadows moving in the corner of your eye, hiding behind the trees and melting into the ground. You blinked a couple of times but your sight remained blurry even when you got up. Your legs buckled for a second and you almost fell, grabbing at a tree next to you.
Find him. Find him.
Something whispered and you felt a buzzing sensation spreading all over your body. You grabbed at your ears as the whispers kept getting louder until-
FIND HIM!
A yell, a dark screeching voice echoed inside your brain.
Felix. You have to find him.
You had no idea how you even ended up in the forest and what was wrong with you while you were walking, your limbs felt like they were disconnected, your head pounded with a headache and your forehead was covered in a thin sheen of sweat.
You heard a smacking sound on your right, like something hit the wet ground and you turned to look but couldn't see anything there.
"Felix?!" your voice came out weak, your throat burning. "Felix!" you whimpered, more tears spilling out your eyes.
The whispers and the smacking sounds became louder, closer, more of them surrounding you. You started freaking out, panic building up within you. The sound of cracking caught your attention and you screamed out when the trees started growing in towards you, their branches becoming longer and reaching out to grab you. You kept screaming as you squatted down, covering your head up and crying.
"Please, stop!" you cried. It was silent. You lifted your head up slowly and the trees were exactly how they were before. No menacing branches hovering over you, reaching to take you.
You quickly stood up, your sight a little less blurry as adrenaline from the fear kicked in. Your legs reacted faster than you could anticipate as you started running, small twigs snapping under the weight of your feet.
The smacking sounds were back and now you could see what they were. All around you, koi fishes wiggled and smacked against the floor, trying to breathe in the dry air. You gasped, wondering how the hell was this happening.
You must be tripping.
The rational part of your mind reminded you that whoever was behind Cupid Corp. didn't hesitate to use all sorts of methods to execute their 'tests'.
They probably drugged you and everything you were seeing right now was a hallucination.
With that realization in mind, you carried on through the forest as it got thicker, ignoring all the voices around you and the fishes seemingly falling from the sky.
Things lurked in the bushes and behind trees, shivers running up your spine as it got darker. You thought you heard Felix calling for you among all those distorted voices.
"Felix?!"
"Y/n!" you heard a distant sound.
"Felix? Where are you?" you hurried up, almost slipping on the moss.
"I'm here!" the voice was clearer now, to your left and you ran and ran until you were stopped in your tracks. A huge koi wish wriggled on the ground where Felix should've been.
"Felix?" you were perplexed as you stared at the sight before you.
"Get me out of here."
Is he... inside the fish?
You noticed a knife on the floor next to it. You blinked and the next thing you knew you were standing in front of the fish with the knife in your hand. You stabbed into the flesh, blood oozing out as you started cutting up the fish like a maniac, guts spilling from the inside until Felix emerged, covered up in all of the fish goo, the stench of it making you nauseous.
"What the fuck?" you swallowed and then everything disappeared, pulling you into the darkness again.
~
The loud piercing sound of the device you prayed to every single day shook your entire body. You jolted up, realizing you were in bed and Felix was waking up next to you.
No fishes, no guts, no forest, no whispers.
100%! Congratulations and have a safe departure from our Village of Love!
"Village of love? More like village of horror." you said as Felix leaned in to look at the screen. A loud sound scared you again, a masked voice following after it.
"Thank you for participating in our program. You've proved your love to each other, built up devotion and trust in just a month. You are now the perfect match. We apologize for any discomfort you felt here and offer you The Juice of Oblivion so you may forget about the... less fun experiences you had here. You can choose not to drink the juice, but remember after you leave through the gate, you're obligated by law to not talk about our tests here. Enjoy the rest of your life together!"
You glanced at the night stand, seeing the suspicious blue liquid inside a bottle.
Felix suddenly started laughing next to you and you looked at him. Laughter bubbled up from your throat too and the two of you cackled for a good minute, until you were heaving for breath and wiping tears away.
"This was fucking insane." he said.
"Were you really stuck inside a fish?" you asked and Felix looked at you like you were insane.
"Was I what?"
"I had to gut a koi fish to get you out, in the forest." you explained and he shook his head.
"You were tripping. We both were, I figured that the moment I stepped foot on the pool. Like on the water. And you were under it, trying to get out but it was as if there was some kind of barrier keeping me from you. I had to find a spot to pull you out. The amount of anguish it gave me..." Felix licked at his dry lips and you reached out to grab his hand.
"Do you wanna drink the juice?" you asked.
"I just wanna get the hell out of here." he said and you agreed.
You were pretty sure this was illegal, all of the stuff happening here; them not disclosing the use of psychedelic stimulants or whatever the drugs were in the contract was also illegal.
But at the same time, if you never participated, maybe you would've never met Felix.
"What are you thinking about?" he asked as you approached the gate with a few other couples, including Gina and Ethan.
"How I'm glad I met you. But I'm gonna need therapy." you said and Felix laughed.
"We'll go together. This is just the first day of the rest of our life." he smiled, kissing your forehead and squeezing your hand.
The man in the chair watched all the couples leave. His lips turned upwards into a smirk as he saw new cars approaching the village.
He wondered what kind of sick tests they had in store for the new inhabitants of the Village of Love?
taglist: @moonchild9350 @janepg @velvetmoonlght @hwanghyunjinismybae @jehhskz @porangporangmeong @laylasbunbunny @laughatdanger @jeonginslefthand @sapphirewaves @s3ungm1nxxl0ve @painterhyunjin @moon-ttokki-x @saintcosette @ooshyana @frehyun @scarlet789 @skzdust @schniti-is-in-the-house @eastjonowhere @sona1800 @channiesrightasscheek @justwonder113 @yvettemint @inaribu00 @httpdwaekki @possum-playground @ria-april @yn-x-them @mariahxrrera @0omillo0 @halfwinterhalfuniverse @cooldeermagazine @delulkpopstan143 @todorokiskitten @compersian @azxulskz @stayp1eceposts @minniesverse @skzdreamer13 @0325ale @j-ji-jia @shannthewriter
#stray kids x reader#stray kids smut#stray kids#skz x reader#skz smut#lee felix x reader#lee felix smut#stray kids scenarios#stray kids imagines#stray kids fluff#stray kids felix#lee felix imagines#lee felix fluff#lee felix x y/n#lee felix x you#skz lee felix#lee felix scenarios#skz imagines#skz scenarios#skz felix#skz fluff#skz angst#lee felix imagine#felix fluff#skz felix smut#felix smut#felix imagines#felix x reader#felix x you#felix x y/n
2K notes
·
View notes
Text
Things you can do to actively participate in the revolution
Here's the list !
I know some of those will look really silly, i promise they are not. And obviously, this is not a checklist, you don't have to do everything. But they're steps that you can absolutely take if you wish to, and they WILL help.
(Thanks everyone for your help, and for adding things yourself with your reblogs <3)
(under the cut !)
1) Let's start off with a very easy one you can do right now: stop using Chrome. It's a google owned browser, and it sents all of your data towards it. Mozilla is a very good replacement, but almost anything will do, really. Also, resign your amazon prime subscription. We revolting against capitalism as a whole, and this is a good first step to not freely give em your data and money
2) Start stealing things from supermarkets and malls. I am not kidding. Little things, that aren't really monitored: a can of food, a lighter, a pair of socks. Condiments are particularly easy to hide in bags or pockets. Steal hygiene products, steal food.
Remember that you should have access to those for free, and you don't because a few rich guys don't want you to.
Additional tip: train station stores are very easy to steal from, because they're so busy. But don't put yourself in danger. Check beforehand if they check bags at checkout, look out for employees that might notice what you're doing. Don't be reckless.
(edit: imma say this, you should read up on what the risks of stealing are, for you and others. Stealing from big stores is IMO always morally right, but it is risky for many reasons. Be careful)
3) In the same line, if you see someone stealing anything from a big store, no you didn't.
4) I know a lot of people are scared of disrespecting rules. By fear of being caught, or by guilt. My advice is: start disrespecting stupid, meaningless rules. I don't have specific exemples, but you'll encounter them and wonder why you're doing that. Stop doing it. This will train you to be able to disobey autority way easier.
5) Put stickers everywhere. If you already have them, go ham. Especially on public property (lamposts are amazing). If you don't, buy them from artists or independant stores, not big brands. If you cannot afford them, remember that you can simply write stuff on an A4 paper and plaster it to walls. Or even post its !
6) Carry a sharpie with you at all time, the big black ones. If you see propaganda, scribble it out. Keep a look out for terfs stickers, maga posters, etc. Also good for getting rid of transphobic and sexist stuff written on public restroom stalls !
7) Buy locally. This means going to the market or small stores, and thrifting your clothes. If you can't for money or accessibility reasons, try trading with your friends, family and neighbours. Get communication going in your circles, and you'll realise there are a lot of things that you can simply trade with or buy from people around you. Like a jar of jam against some eggs, or a pair of socks for a t-shirt you don't wear anymore !
8) Learn how to sew. I know, that sounds dumb ! But i promise you, not only will it be amazing to trade with other people ("i'll sew back ur shirt and in exchange, you give me a can of peaches !"), corporations also haaaate when you know how to fix your clothes. Because they want you to buy more. You'll spend a lot less money if you know how to fix em
9) If you have the space and the money, grow your own food, and share it or sell it around you. Be careful, some assholes will call the FDA on you. Do that with people you trust.
Additional tip: growing vegetables and fruits can be a real nightmare. You can absolutely start by just growing some basil or mint :)
10) Organise. Join leftist groups online, even if it's just to see what's being said, you don't even need to interact. Follow creators, repost and share their content. By doing that, you'll stay informed on group movements like strikes, protests and boycotts, which you can then participate in. It's very important you're connected to other ppl and the movements that are started !
11) Unionize. I'm very sorry I don't know the exact way unions work in the US, but if you can, join one. They will help you in times of needs, especially if you're a student or a worker. If you're not sure how to do that, absolutely ask around to people you know are very active politically, around you or online. People will help.
12) Stay. Informed. Follow independant papers and news outlet. If you can afford it, give them a dollar or two. They are fighting everyday for access to unbiased information for all, and sadly, their independance means that they rely almost entirely on donations and people simply engaging with what they put out.
If you can't access those: do not get your news from TV. Ever. Or anywhere else that has been bought by the far right. Sadly, the majority of TV channels are just the worst.
And, most importantly: fact check. All of the time.
13) Share that information. Talk to those you trust and who are ready to listen to you, and tell them about what's happening. Get angry with them. Revolution stems from people coming together and realising that they're being used and profited off of. Share videos and posts relating to politics, especially informative videos.
14) Go to protests ! If you've never been, i know it can be scary. But you can stay in the middle (don't go all the way to the front, that's where stuff can get heated) and scream and walk with everyone else. You'll meet people who, like you, want things to change. Capitalism wants you to stay as unconnected to others as possible, and that's a great way to fight that.
Sometimes, there are sites that have a planning for all protests happening in a city. Look up if one exists for yours
15) Create and strenghten community. I know i really struggled with this one, because it's so vague. But here's a few places you can start:
-Go and introduce yourself to your neighbours, if you deem it safe. Give them a little gift if you can afford it, like a pack of pasta.
-Make new friends, even if they aren't deep friendships. You need connections. Online or irl, both are fine- don't stay isolated.
-If you already have community, go check on them right now. Ask your friends how they're doing, and if they need anything- ask how they're being impacted by what's happening right now politically.
16) Look for ways to fuck over the institutions in easy ways. One example that went around tumblr a lot is letting dandelions grow in your backyard, because landlords fucking hate it. If you work in retail or fast food, cheat. Accidentally forget to scan the diapers. Put in 7 nuggets instead of 6.
(edit: been told that it's very risky for walmart workers to not scan things, so beware.)
17) Engage in art. MAKE art. Music, shitty paint drawings, craft, anything as long as you're being creative. Share it. If you feel like you can't do that, then support artists. Make a point to look up cool illustrations, and new music. Go to the cinema.
If you're an artist currently in an underpaid office job, please, by the love of god, be creative during office hours. You're underpaid, they do not deserve your full time and attention. Take 30 minutes to write that snippet you've been thinking about.
(and actually, if you're underpaid at all: do the minimum required. So that you can't be fired, but that's it. Any more effort is not worth it. Companies will never be thankful for what you do.)
18) Look up books that your state banned, and go read them. You can get them secondhand, or as pdfs online. (if anyone needs ressources, i will glady look for and share them.)
And, actually, read books in general if you can. Yes, fanfics count !
19) Seek education. There's a lot of youtube channels out there talking about educational subjects in a fun way. Some things the rich assholes who run the country specifically don't want you to learn more about are: biology, history and archeology, social and economic sciences. GO LEARN ABOUT THOSE.
The people in power don't want you to be educated. It's why they eviscerated the education system.
20) PIRATE. I cannot stress this enough, anything you can pirate (that isn't from small, indie creators, except if you absolutely can't afford it) do it. Download music illegally, torrent movies and games. If you want access to academical studies and papers, some writers will give them to you for free if you email them about it. There are also ways to go around paywalls.
21) Don't fall for the traps of "progressive brands". Lately, i've seen a lot of praise for Ben and Jerry's for openly supporting lgbtq rights and being globally anti-trump. They are still a brand. Avoid buying from any big names when you can. That being said, if you have to, check beforehand which ones and what their history is. Some are more evil than others.
Additional tip: a lot of brands you see in stores are actually owned by bigger brands. One prime example of this is Nestle, who are fucking evil, but they own a shitload of other big names. Be careful what you buy.
22) I hate to say this, but be prepared to defend yourself. Revolutions are never peaceful. You will get in danger. If you can, get in ok physical shape. Learn how to run fast and fight well.
If none of those are available options to you, please, make sure you have someone around you that will be able to protect you, or a place where you can be safe. Whether you are disabled, a minor, or anything else. Don't put yourself in more danger than is necessary.
(this used to also include getting a gun. I deleted it because i don't feel comfortable recommending this. But it's still an option.)
23) Last but not least, be kind. When someone cuts off a woman speaking, interrupt and give her the floor back. Shame those who think it's right to say bigoted shit in public. Listen to those around you. If you can't act, then remember to always have empathy for the homeless, for drug users, for immigrants. Understand they are people just like you. You are not immune to propaganda and prejudice, no matter who you are. Always question yourself and your biases.
(if you've read this far, please repost. We need this to reach as many people as possible)
I want to remind you that you're not alone. I know things seem hopeless, but the simple fact that you're reading this is proof it's not. I don't live in the US, but i'm supporting you as best i can from where i am, and sending you strenght.
If you have any questions, do ask away. I'll end on this image that's very dear to me:
#us politics#eat the rich#my credentials are that i am french btw#i hope this helps even one person#if that's the case then i succeeded#donald trump
2K notes
·
View notes
Text
Safeguard Your Electronics with a Robust Battery Backup System
In a digital age where we're dependent on electronic devices for work and leisure, unexpected power disruptions can be a real buzzkill. But fear not! The answer to your power-related worries lies in one powerful solution: the battery backup system. In this article, we'll delve into the world of battery backup systems and highlight why they are a must-have for anyone seeking uninterrupted power.
The Power of Battery Backup Systems: Imagine you're in the middle of an important video call or finalizing an important document when suddenly, darkness envelops your room. Enter the superhero of electronics – the battery backup system. This ingenious device steps in immediately during power outages, ensuring your devices stay online and operational.

Exploring Different Types of Battery Backup Systems: When it comes to safeguarding your electronics, not all battery backup systems are created equal. There are three primary types:
Offline/Standby Systems: Basic yet effective, they're perfect for safeguarding home devices like computers and entertainment systems.
Line-Interactive Systems: A notch up in protection, these systems offer voltage regulation and battery power during outages, ideal for small businesses.
Online/Double-Conversion Systems: The cream of the crop, they provide continuous AC-to-DC conversion, making them indispensable for critical operations like data centers.
Crucial Components of a Battery Backup System: Let's crack open the anatomy of a battery backup system:
Batteries: The powerhouse that stores energy, ready to leap into action when the main power falters.
Inverters: These wizards convert battery-stored DC power into usable AC power for your devices.
Automatic Transfer Switches: The gatekeepers that detect power disruptions and swiftly switch to battery power, ensuring seamless operations.
Advantages Galore with Battery Backup Systems:
Device Defender: Shield your devices from power surges and voltage spikes.
Data Protector: Keep your data safe during sudden outages, whether you're working from home or running a business.
Operational Savior: Crucial processes in businesses like servers and communication systems remain unaffected and uninterrupted.
Life Extender: Ensure the longevity of your electronic gadgets with consistent power supply.
Stress Reliever: Bid adieu to power-related stress as you continue your tasks seamlessly.
Choosing the Right Battery Backup System: The key to a harmonious power backup experience lies in selecting the right system for your needs:
Load Capacity: Calculate the combined power requirements of all connected devices.
Runtime Consideration: Determine how long the battery can sustain your devices during an outage.
Device Compatibility: Match the power needs of your devices with the capabilities of the battery backup system.
Simple Setup and Easy Maintenance: Installing a battery backup system isn't rocket science. Stick to the manufacturer's instructions or consult a pro for complex setups. Regular maintenance includes battery checks and system functionality tests.
Real-Life Stories:
Home Heroics: A homeowner's crucial work project was saved by a battery backup system during an unexpected outage.
Business Triumph: An online store didn't lose a penny in revenue during a blackout because their online operations were backed by a battery backup system.
Medical Marvel: Hospitals rely on these systems to ensure life-saving medical equipment remains operational, even during power failures.
Battery Backup vs. Generators: Making the Choice: While generators offer prolonged power supply, battery backup systems are compact, noise-free, and provide instant power. They're a cost-effective solution for short-duration outages.
Conclusion : When darkness threatens to disrupt your digital world, a dependable battery backup system steps in as your guardian angel. Whether you're safeguarding your home office, ensuring business continuity, or protecting critical systems, investing in a robust battery backup system is a smart move. Empower yourself with uninterrupted power and embrace the future of electronics resilience.
#battery backup#ups uninterruptible power supply#line interactive ups#SLA Battery#VRLA Battery#automatic voltage regulator#data center ups system#double conversion ups#ups monitoring system#online ups Malaysia#Automatic voltage stabilizer#UPS Battery#ups for server room#ups delivery Malaysia#ups rack#ups true online#ups management software#modular ups Malaysia#online ups system#inverex ups#batterybackup#ups#battery#solarpower#batterypower#saveelectricity#upssystems#energyefficiency#solar#upsinverter
0 notes
Text
Your monitor's my destination
Attention seeking, online bitch
Endless data propagation
Plug in the wire, throw the switch
Can't see you from inside the screen
Are you watching, is this thing on
I'm the ghost in the machine
My own digital panopticon
426 notes
·
View notes
Text
DO YOU REALLY LOVE ME DO YOU LOVE ME OR NOT?! Wondering if you love them how they love you… featuring CATER DIAMOND and IDIA SHROUD.
Cater Diamond! Who was so sure that you knew what you were doing to him, after all, your hints weren’t exactly subtle - looking at him with those eyes whenever he walked into a room, your fingers brushing into his when you’d helped pick up a pencil he’d dropped, the tiny ping! notification that came from your phone whenever he’d post something new on Magicam… until Ace mentioned you practically stalking his account, and now poor Cater’s spiralling. Was it all a fluke? Were you just perking up whenever you saw him because you thought you were friends? Was the physical contact really just coincidental? Were the notifications on your phone for Magicam on for everyone? Jeez, and here he thought he was the man of your dreams, when really, maybe he was just one bad joke away from getting blocked… Going back to his room and practically burying his face into his pillow, legs kicking back and forth, mentally berating himself for being so delusional for the last few days, thinking he actually had a chance with you… love really did make people go soft, because now he couldn’t think of anything but you - the way the corners of your eyes crinkled when you smiled, how your laugh reverberated in his mind during those restless, sleepless nights, the little spark he felt when your fingers brushed against his, whether you really loved him or not, the way he loved you… Sevens, he’d even gone so far as to put your name and his in an online compatibility checker(23% on the first try, sending Cater to go check using other websites, all the way until four AM, completely wrecking his usual doom-scrolling schedule)… hey, won’t you come over and help your poor Cay-Cay with sorting this mess out? (By kissing his face silly, of course) ;)
Idia Shroud! Who was disgusted by the gross lovey-dovey normie feelings he was dealing with right now, and even more at himself - after all, why would someone like you want a total loser like him? :((((( The probability rates of you liking him were just like the rates of scoring an SSR with no gems… practically zero. That is, until Ortho began monitoring you for any signs of romantic interest for his big brother, and came back with what could only be described as a mountain of data. “Flushed cheeks, increased tendency to smile around you, dilated pupils… they like you too, Idy!” And now that Idia was sure he had a silver of a chance with you, he began pulling out all the stops to make sure you would agree to be his player 2 - as in inviting you to his room to play video games(nearly combusting when you sat too close to him, hair flickering a dangerous shade of pink), sharing his prized snacks with you(eyes averting yours when he felt your gaze on his lips, licking away crumbs from the biscuits you’d shared earlier), Sevens, he’d even given you one of his prized figurines(a calculated move, after all, it’d only be yours for a bit before the two of you officially became an item, so he’d have it back it no time!). Getting so excited at the idea of becoming an official item with you, that he’d failed to notice that one classmate that seemed to be hanging around you more and more, sending him falling from cloud nine. Eh? This wasn’t in the romance route he'd planned, nor in the twenty-seven different simulations he’d run! Ugh, and how could he compete with him? You’d probably take that normie classmate over him, a gloomy shut-in, anyway… locking himself in his room more often than usual, emotional walls raised so high even Muscle Red was starting to get concerned - but hey, Ortho had a solution! Come over and kiss Idia ‘till he pops, or at least until he knows your true feelings, okay? ;)
#twisted wonderland x reader#twst x reader#disney twst#twst x yuu#cater x reader#cater diamond x reader#cater x yuu#cater diamond x yuu#idia shroud x yuu#idia shroud x reader#idia x reader#idia x yuu
304 notes
·
View notes
Text
Holy CRAP the UN Cybercrime Treaty is a nightmare

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If there's one thing I learned from all my years as an NGO delegate to UN specialized agencies, it's that UN treaties are dangerous, liable to capture by unholy alliances of authoritarian states and rapacious global capitalists.
Most of my UN work was on copyright and "paracopyright," and my track record was 2:0; I helped kill a terrible treaty (the WIPO Broadcast Treaty) and helped pass a great one (the Marrakesh Treaty on the rights of people with disabilities to access copyrighted works):
https://www.wipo.int/treaties/en/ip/marrakesh/
It's been many years since I had to shave and stuff myself into a suit and tie and go to Geneva, and I don't miss it – and thankfully, I have colleagues who do that work, better than I ever did. Yesterday, I heard from one such EFF colleague, Katitza Rodriguez, about the Cybercrime Treaty, which is about to pass, and which is, to put it mildly, terrifying:
https://www.eff.org/deeplinks/2024/07/un-cybercrime-draft-convention-dangerously-expands-state-surveillance-powers
Look, cybercrime is a real thing, from pig butchering to ransomware, and there's real, global harms that can be attributed to it. Cybercrime is transnational, making it hard for cops in any one jurisdiction to handle it. So there's a reason to think about formal international standards for fighting cybercrime.
But that's not what's in the Cybercrime Treaty.
Here's a quick sketch of the significant defects in the Cybercrime Treaty.
The treaty has an extremely loose definition of cybercrime, and that looseness is deliberate. In authoritarian states like China and Russia (whose delegations are the driving force behind this treaty), "cybercrime" has come to mean "anything the government disfavors, if you do it with a computer." "Cybercrime" can mean online criticism of the government, or professions of religious belief, or material supporting LGBTQ rights.
Nations that sign up to the Cybercrime Treaty will be obliged to help other nations fight "cybercrime" – however those nations define it. They'll be required to provide surveillance data – for example, by forcing online services within their borders to cough up their users' private data, or even to pressure employees to install back-doors in their systems for ongoing monitoring.
These obligations to aid in surveillance are mandatory, but much of the Cybercrime Treaty is optional. What's optional? The human rights safeguards. Member states "should" or "may" create standards for legality, necessity, proportionality, non-discrimination, and legitimate purpose. But even if they do, the treaty can oblige them to assist in surveillance orders that originate with other states that decided not to create these standards.
When that happens, the citizens of the affected states may never find out about it. There are eight articles in the treaty that establish obligations for indefinite secrecy regarding surveillance undertaken on behalf of other signatories. That means that your government may be asked to spy on you and the people you love, they may order employees of tech companies to backdoor your account and devices, and that fact will remain secret forever. Forget challenging these sneak-and-peek orders in court – you won't even know about them:
https://www.eff.org/deeplinks/2024/06/un-cybercrime-draft-convention-blank-check-unchecked-surveillance-abuses
Now here's the kicker: while this treaty creates broad powers to fight things governments dislike, simply by branding them "cybercrime," it actually undermines the fight against cybercrime itself. Most cybercrime involves exploiting security defects in devices and services – think of ransomware attacks – and the Cybercrime Treaty endangers the security researchers who point out these defects, creating grave criminal liability for the people we rely on to warn us when the tech vendors we rely upon have put us at risk.
This is the granddaddy of tech free speech fights. Since the paper tape days, researchers who discovered defects in critical systems have been intimidated, threatened, sued and even imprisoned for blowing the whistle. Tech giants insist that they should have a veto over who can publish true facts about the defects in their products, and dress up this demand as concern over security. "If you tell bad guys about the mistakes we made, they will exploit those bugs and harm our users. You should tell us about those bugs, sure, but only we can decide when it's the right time for our users and customers to find out about them."
When it comes to warnings about the defects in their own products, corporations have an irreconcilable conflict of interest. Time and again, we've seen corporations rationalize their way into suppressing or ignoring bug reports. Sometimes, they simply delay the warning until they've concluded a merger or secured a board vote on executive compensation.
Sometimes, they decide that a bug is really a feature – like when Facebook decided not to do anything about the fact that anyone could enumerate the full membership of any Facebook group (including, for example, members of a support group for people with cancer). This group enumeration bug was actually a part of the company's advertising targeting system, so they decided to let it stand, rather than re-engineer their surveillance advertising business.
The idea that users are safer when bugs are kept secret is called "security through obscurity" and no one believes in it – except corporate executives. As Bruce Schneier says, "Anyone can design a system that is so secure that they themselves can't break it. That doesn't mean it's secure – it just means that it's secure against people stupider than the system's designer":
The history of massive, brutal cybersecurity breaches is an unbroken string of heartbreakingly naive confidence in security through obscurity:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But despite this, the idea that some bugs should be kept secret and allowed to fester has powerful champions: a public-private partnership of corporate execs, government spy agencies and cyber-arms dealers. Agencies like the NSA and CIA have huge teams toiling away to discover defects in widely used products. These defects put the populations of their home countries in grave danger, but rather than reporting them, the spy agencies hoard these defects.
The spy agencies have an official doctrine defending this reckless practice: they call it "NOBUS," which stands for "No One But Us." As in: "No one but us is smart enough to find these bugs, so we can keep them secret and use them attack our adversaries, without worrying about those adversaries using them to attack the people we are sworn to protect."
NOBUS is empirically wrong. In the 2010s, we saw a string of leaked NSA and CIA cyberweapons. One of these, "Eternalblue" was incorporated into off-the-shelf ransomware, leading to the ransomware epidemic that rages even today. You can thank the NSA's decision to hoard – rather than disclose and patch – the Eternalblue exploit for the ransoming of cities like Baltimore, hospitals up and down the country, and an oil pipeline:
https://en.wikipedia.org/wiki/EternalBlue
The leak of these cyberweapons didn't just provide raw material for the world's cybercriminals, it also provided data for researchers. A study of CIA and NSA NOBUS defects found that there was a one-in-five chance of a bug that had been hoarded by a spy agency being independently discovered by a criminal, weaponized, and released into the wild.
Not every government has the wherewithal to staff its own defect-mining operation, but that's where the private sector steps in. Cyber-arms dealers like the NSO Group find or buy security defects in widely used products and services and turn them into products – military-grade cyberweapons that are used to attack human rights groups, opposition figures, and journalists:
https://pluralistic.net/2021/10/24/breaking-the-news/#kingdom
A good Cybercrime Treaty would recognize the perverse incentives that create the coalition to keep us from knowing which products we can trust and which ones we should avoid. It would shut down companies like the NSO Group, ban spy agencies from hoarding defects, and establish an absolute defense for security researchers who reveal true facts about defects.
Instead, the Cybercrime Treaty creates new obligations on signatories to help other countries' cops and courts silence and punish security researchers who make these true disclosures, ensuring that spies and criminals will know which products aren't safe to use, but we won't (until it's too late):
https://www.eff.org/deeplinks/2024/06/if-not-amended-states-must-reject-flawed-draft-un-cybercrime-convention
A Cybercrime Treaty is a good idea, and even this Cybercrime Treaty could be salvaged. The member-states have it in their power to accept proposed revisions that would protect human rights and security researchers, narrow the definition of "cybercrime," and mandate transparency. They could establish member states' powers to refuse illegitimate requests from other countries:
https://www.eff.org/press/releases/media-briefing-eff-partners-warn-un-member-states-are-poised-approve-dangerou

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/07/23/expanded-spying-powers/#in-russia-crime-cybers-you

Image: EFF https://www.eff.org/files/banner_library/cybercrime-2024-2b.jpg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/us/
844 notes
·
View notes
Note
Hey! Can I Get a headcannon of Wheeljack, Bulkhead, Optimus and Ratchet with S/O that got infected in cybonic plague?
Wheeljack, Bulkhead, Optimus and Ratchet with S/O Who Got Infected with Cybonic Plague
➽───────────────❥➽───────────────❥
I try my best to make the portrayal of their character based on their personality, and I would like to apologize for replying to the ask late because I had horrible carpal tunnel syndrome in my right hand and depression, and I had to focus on finding jobs as well as therapy. Thankfully, I graduated in July from my university and able to get a quick 6 months of internship before leaving to find a new job.
Gender: Neutral
Warning: Angst to Fluff, sickness, mention of injuries and Profanities
➽───────────────❥➽───────────────❥
OPTIMUS PRIME - Autobot

When Ratchet first tells Optimus you're infected, his spark clenches. He masks the fear behind his usual stoicism, but his optics dim. The Cybonic Plague is a deadly, ancient virus, and he vows silently that you will not meet the same fate.
Optimus spends long hours at your side, even when he should recharge. He watches your spark signature fluctuate on the monitor with quiet intensity. Every labored intake of your vents feels like a countdown ticking louder.
He searches the archives for ancient medical data, something even Alpha Trion once wrote. Sleepless and single-minded, he sifts through fragments of forgotten science. If the answer lies buried in the Well of All Sparks itself, he’ll find it.
When Megatron offers a cure to him but in exchange a cruel price. Optimus would consider surrendering himself if it means you’ll live going through Megatron’s database to get the cure. He volunteers instantly to deliver it, no matter the danger.
Inside your subconscious, he finds a corrupted image of yourself. It’s terrified, glitching, dissolving into plague data. He kneels beside it, shielding you with his own spark energy.
The process nearly destabilizes both of you. Your systems scream under the pressure, and Optimus begins to fade. But his spark surges, wrapping you in protective light.
After what feels like forever, your optics flicker back online. You see him there, battered and dim, but smiling just for you. “You… stayed,” you rasp, and he nods, servos brushing your cheekplate.
Recovery is slow, and he never rushes you. He adjusts your routines, brings Energon himself, and reads to you aloud. No mission takes priority over your healing, not even war. He keeps a fragment of your corrupted code stored away safely. Not as a reminder of the pain, but of the strength you showed.
Your near-loss changes him, even if subtly. He becomes gentler in the quiet moments, less afraid to show his affection. When you reach for his servo now, he squeezes back without delay. He lets you stay by his side in the command center now.
Sometimes, he wakes up from recharge fearing he lost you again. You always pull him close, resting your helm against his chest plate as your arms wrap around him to comfort your sparkmate. “No plague. No pain. I’m here,” you remind him.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
The first symptom was a flicker. Just a minor glitch in your visual sensors, nothing big, just a half-second blackout that you chalked up to fatigue. But then came the spasms. Your servo twitched, then locked. The base lights blurred, the floor shifted beneath your feet, and Ratchet’s voice faded into a muffled hum. By the time you collapsed in the medbay, Optimus was already on one knee beside you, calling your name repeatedly.
Ratchet’s diagnosis was quick, in a second, and brutal: the Cybonic Plague. A virus from Cybertron’s darkest past. You barely heard the details, lost in a haze of heat and static, but through the buzzing in your head, you caught one thing: from your receptor, the fear in Optimus’s voice. No, he didn’t shout; he didn’t panic. He never did. But when he asked, “Ratchet, is there a cure?” The weight behind his words could’ve cracked stone.
You drifted in and out of stasis, each moment flickering between memory and dream. Sometimes you were back on Cybertron, laughing in golden-lit corridors. Other times, you were locked inside your own mind, fighting the virus as it twisted your code. On the other hand, the leader of the Autobots sat beside you, silent, his servo resting against yours.
When your vitals began to crash, Ratchet proposed a dangerous solution: someone had to enter your mind through a neural link and manually inject the cure. Optimus didn’t hesitate. “Prepare the link,” he said. "Optimus Prime, Are you sure?" Ratchet was surprised. The medic even warned him of the risk, of the chance he might not return, but Optimus had already decided. “She is worth the risk.”
Inside your mindscape, the virus had created a corrupted version of you. It was ugly, fractured, glitching, and afraid. Optimus found you there, curled in a pit of static. He didn’t rush to pull you out; instead, he knelt beside you, his sparklight flickering in the dark like a pulse. “You’re stronger than this,” he said, his voice echoing like thunder through the data storm. “And I’m not leaving without you,” His voice was louder. You reached for him with a trembling servo as his hand gently held your hand.
The battle inside your mind was like drowning in code, each surge of infection trying to rewrite who you were. But with every wave, Optimus pushed back, pouring light into the cracks. He shielded you with part of his own spark signature, even as his systems began to flicker too. “Stay,” he whispered when your form began to fade. “Stay with me.” And this time, you did.
You woke to the soft hiss of medbay monitors and the familiar warmth of his servo against yours. Your optics blinked open, and there he was, damaged, dim, but alive. And smiling. “You’re back,” he said, as if those two words were enough to rewrite the universe. You tried to speak, but all you could do was nod, the heat of tears burning behind your eyes. He leaned forward, pressing his helm gently to yours. “I believe in you; I know you could do it.”
Recovery was slow, but he was patient. He helped you walk again, holding you up when your joints trembled. He sat through quiet recharge cycles with you, read aloud during your checkups, and let the others take the front lines so he could stay close. The war could wait, he told them. Because for the first time in a long while, the hope had won against the cybonic plague virus.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
❀
❀
❀
RATCHET - Autobot
Warning: The doctor is tsundere

The moment Ratchet scans you and detects the Cybonic Plague, his spark skips a beat. He double-checks the readings, then checks them again. But the data doesn’t lie, your code is breaking down. “…No. No, no, not them. Not you,” he mutters while already grabbing tools.
He doesn’t even try to hide how shaken he is, there’s no time for pride. His servo trembles for the first time in centuries. You try to joke about him being dramatic while the rust starts to form, but he silences you with a look.
Ratchet keeps a close vigil at your bedside, monitoring blinking over your spark signature. He rarely leaves your side, only to mix compounds or pace violently. The others offer help, but he snaps at them without meaning to.
He digs into archives older than the war itself to find a possible cure. Your medical file grows thicker by the hour, stained with energon smudges. He barely recharges, too afraid that he’ll wake to silence from your berth. Your steady pulse is the only thing keeping him from destroying himself.
When your systems crash temporarily, Ratchet genuinely breaks down. He slams a servo into the wall, a spark roaring behind his chassis. The monitors scream, and he’s barking orders at the others like a war general. No one dares disobey him when you're on the line.
He eventually constructs a prototype antivirus—but testing it is risky. Ratchet debates for only seconds before deciding: he'll inject it directly. If it fails, it could speed up the deterioration… But doing nothing is worse. “Better to die trying than to watch you fade.”
He injects the cure with a shaky servo, optics locked on your frame. You seize up, systems sparking, and he nearly overloads from panic. But then your vitals stabilize a little. It was not perfect, but enough. He doesn’t breathe until your optics flutter open.
He’s exhausted, hunched over your berth like a rusted-out frame. When you whisper his name, his entire posture softens. “Don't ever do that again,” he says quietly, voice raw. But there's relief under the gruffness, and it bleeds through.
Ratchet orders a full scan every two hours after your recovery. No exceptions, no excuses, even if you insist you're fine or if you just have a simple cough from dust. It’s annoying… but deeply sweet in a Ratchet kind of way.
He brings you energon personally, even if he pretends it's 'standard check-in protocol'. He triple-checks its composition, temperature, and nutritional balance. When you smile at him, He huffs and mutters, “Don’t get used to this.”
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
You were just teasing him over another one of his grumpy lectures when it happened. A sharp pain cracked through your spark, and suddenly your systems seized up, dropping you to your knees. Ratchet barely caught you in time, optic panels wide in alarm, shouting your name like it was a medical emergency code. “No, no, no! Stay with me!” He barked, already scanning you with shaky, frantic digits.
The diagnosis was something Ratchet had hoped he’d never see again: the Cybonic Plague. A virus so ancient and insidious that even whispering its name made bots flinch. You were already twitching, glitching, fighting to hold onto reality as the virus gnawed at your code like rust in your processor.
Ratchet didn’t react with panic. No, panic was inefficient. But his voice lost its edge of sarcasm, and his hands never once stopped moving. “You are not dying on my table.” The others offered help "Ratchet What happened?!" Bulkhead asks with panic in his voice. "We can help you," Arcee tried to step up as Bumblebee buzzes.
But Ratchet didn’t let anyone else touch you. Instead, his optics silently glare at the other Autobot teammates and blocking them away. “No one knows their system like I do!” he snapped, the words heavy with something more than professional pride. "You all step away from (Y/N)!"
He worked tirelessly for hours, then days, ignoring recharge and energon warnings, digging through corrupted Cybertronian medical files older than Orion Pax. You were more than just a patient. You were the only one who’d ever made the old medic feel again, you're his sparkmate and the only one who could understand him.
Every time your spark signature flickered, something in Ratchet faltered. He’d pace the medbay like a caged beast, muttering equations under his breath, cursing the virus and whatever careless god had let it survive this long. He really wishes that time Megatron hadn't made a virus as the biology weapon as he remember all of those passing comrades who rusted away from the cybonic. Even when Optimus offered to assist, Ratchet nearly shouted him down. “Don’t take this from me! I have to be the one to save (Y/N)!”
When your systems dipped into emergency stasis, Ratchet broke protocol. He ignored the risks, activated a neural bridge, and entered your mind full in desperation and determination. Inside, your consciousness was a mess of static and corrupted data. He found you in the center of it, your voice distorted and broken, barely able to reach out. But he knelt beside you anyway, optics locked on yours, his touch gentle as he whispered, “I am not losing you, too.”
Fighting the plague from the inside was like performing surgery in a hurricane. Every data spike you sent at him nearly knocked him offline. But he kept moving forward, shielding you with pieces of his spark signature, injecting the antivirus into your core line of code while taking damage himself. “You're worth every scratch,” he said quietly, even when you begged him to leave. “Don’t ask me to walk away from the only thing that makes me feel alive.”
You came back slowly, stuttering and disoriented, optics dim but conscious. Ratchet was there, slouched in his chair, faceplate smudged with energon and exhaustion. When your hand twitched, his optics widened, and the relief that washed over him nearly dropped him to the floor. “You stubborn glitch,” he whispered, and for once there was no bite in his voice. Just soft gratitude, like your survival had rebooted something inside him.h
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
❀
❀
❀
WHEELJACK - Autobot
Wheeljack doesn’t panic often, but the moment Ratchet says 'Cybonic Plague' his spark freezes. He clenches his servos so tightly they spark. He’s used to battlefield injuries, not watching someone he loves slip away without a fight. “You’re not fraggin’ leaving me,” he growls, already planning something reckless.
He tries to play it cool around the others, but you can tell he’s on edge. His optics flicker faster, and he paces like a caged beast. He gets into three arguments and almost punches a wall in the first hour. No one dares call him out, except maybe Ratchet.
He hates not being able to fight the plague with his blades or explosives. But he sits beside you anyway, blades sheathed, just watching you breathe. Because being there is the only fight he can win right now.
Wheeljack once storms into the medbay covered in Energon because he thought you flatlined. Turns out it was just a system recalibration. Ratchet yells at him for scaring everyone and nearly bleeding out but he doesn't care, he just wants to see your condition.
When Ratchet finally gets a possible cure, Wheeljack insists on testing it himself. He offers his own code as a host “Load me with it. I can take it.” Ratchet refuses, but Wheeljack doesn’t stop trying to bargain.
He holds you through the injection of the antivirus, despite Ratchet’s warnings. You’re spasming, screaming, nearly overheating, but he won’t leave. His armor gets scorched, his frame rattles with yours. “Easy, sweetspark. You’re tougher than this thing. Just hold on.”
Once you are awake when your vital stabilized, , he cracks the dumbest joke to make you smile. It’s so bad you groan, but it breaks the tension. Of course he does this is because he wants to distract you and himself from what just happened.
He actually hugs Ratchet after the cure works, and then immediately denies it. The medic bot would pushes him away, rejecting his hugs but secretly the doc was smirking and says nothing. Everyone at base teases him about it for weeks.
Wheeljack would secretly builds a private recharge chamber for the two of you. It’s lined with Wrecker badges and LED lights shaped like stars. It is a sanctuary for you two.
He puts your spark signature into his own HUD overlay. He monitors it 24/7, even when you're fully recovered. Says it helps him 'focus' but you know it just helps him breathe easier because after what hapened he became twice more protective around you as he tries not to show it (but it's too obvious).
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
You didn’t even feel it at first. Just a flicker in your HUD, a small static delay in your vision. You chalked it up to a power drain or a bad line of code from your last mission. But when your limbs started locking up mid-step and your systems spat out unfamiliar alerts, you knew something was wrong.
The moment Wheeljack caught you collapsing in the hallway, optics wide and frantic, you knew things were about to get worse before they got better. He carried you like you weighed nothing, sprinting to the medbay with a speed that would’ve impressed Flash from the DC Universe.
Ratchet was already scanning your systems before your optics flickered out. His voice is grim, “It’s Cybonic Plague.” That’s when Wheeljack went completely still. Not in fear but in that deadly kind of stillness that comes before a storm. “You sure?” he asked, voice low and dangerous. “Because if you’re wrong—” “THE DATA IS NOT WRONG!” Ratchet snapped. "Get out of my way and let me try to save them.” But Wheeljack didn’t leave after Ratcher ordered him.
He stayed by your side like a guardian drone, arms crossed, pacing only when the tremors in your frame got bad. He didn’t speak unless spoken to, but the tension rolled off him in waves like a bomb waiting for someone to trigger it. His fists were clenched the entire time, even when your body seized and your vents wheezed like you were drowning on dry air. “I’ve seen ‘bots fall apart in my hands,” he muttered one night, eyes locked on your dimmed optics. “Never thought it’d hurt like this.” His voice cracked for just a second before he stuffed it down.
No one else saw that moment. He made sure of it. But you heard it—through the haze of pain and corrupted data, you heard the fragging heartbreak in his voice. The worst night came when your spark signal flatlined for 4.3 seconds. Ratchet got it back, but Wheeljack didn’t speak for an hour after. Not one word.
He just stared at you like he was memorizing everything in case it was the last time. When you jolted awake with a scream during the antivirus injection, he held you down himself, letting your thrashing scorch the paint off his arms. “Easy, sweetheart. Come on. I’ve got you,” he whispered like a promise.
When it was finally over, and your vitals stabilized, he didn’t cheer like the others. He just slumped into the wall and let his optics close. You’d never seen Wheeljack rest before, it was almost unsettling. He didn’t speak until you weakly reached for his servo, and he took it like it was the most precious thing in the universe. “Welcome back,” he whispered, smiling with that cocky lopsided grin that always made your spark flutter. “Told you you were tougher than scrap.”
Late at night, when the others were recharging and the base had gone still, he’d sit beside your berth and tell you Wrecker stories, a wild, impossible tales of explosive stunts and near-death victories. But there was always a pause at the end. A breath. A moment where he looked down at your frame and whispered, “Nothing I survived out there scared me half as much as this did.”
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
❀
❀
❀
BULKHEAD - Autobot

Bulkhead instantly panics the moment you stumble mid-step. You’ve handled worse injuries before, but this was different. Your optics dimmed, and your balance gave out. He caught you before you hit the ground, yelling your name so loud it echoed through the base.
When Ratchet announces it’s Cybonic Plague, Bulkhead nearly shuts down. He’s heard of it, he’s lost Wrecker comrades to it in the war, and the thought of you having it nearly crushes him.
Bulkhead refuses to leave your side, even when ordered to. He snaps, “I don’t care if Megatron walks through that door. I’m not leaving them.” Miko tries to convince him to get some rest, but he just shakes his head.
He strokes your helm gently whenever you’re unconscious. It’s a side of Bulkhead few ever get to see, soft, wordless care. His massive servos are surprisingly gentle, brushing away coolant leaks and static from your face. Sometimes he whispers old Wrecker stories, just to fill the silence.
He threatens to storm the Decepticon base for a cure if needed. When Ratchet mentions the cure once came from Soundwave’s systems, Bulkhead's optics flash with rage. “Tell me where, and I’ll smash my way through if I have to.” The team knows he means it.
When Ratchet tests an experimental antivirus, Bulkhead is the first to volunteer to help. He doesn’t care about the risks. “If it saves them, then I’ll take ‘em all.” He’s the wall that keeps everyone moving forward.
He keeps a record of your vitals and treatment schedule. It’s scrawled in messy handwriting on datapads. “Just in case someone else gets sick. I want them to have a head start.” Even in your worst moment, he’s thinking about helping others.
When your systems finally begin to purge the virus, he almost collapses with relief. “They’re stabilizing,” Ratchet says. Bulkhead just lets out a broken laugh. “You fraggin’ did it, sweetspark!” The first time you speak after recovery, he nearly sobs.
He organizes a celebration after your full recovery, but it's more of a quiet hangout with the team. He brings Energon treats and music, keeping you close. The way he smiles when you're laughing? Pure sunshine.
He starts spoiling you with homemade energon treats. They’re not great. He accidentally makes them too spicy, too sweet, or too burnt. But he tries, and he beams every time you take a bite. “It’s the thought that counts, right?”
Even after you recover fully, he watches you like a hawk. He pretends to be casual, but you catch him staring every few minutes. “What? Can’t I look at my favorite bot?” he teases. But deep down, he’s still guarding your spark with all he’s got.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
Bulkhead had seen a lot in his time, explosions, Decepticon traps, close calls that would make any normal mech fold under pressure. But nothing could have prepared him for the moment you collapsed right in front of him. One minute you were laughing, teasing him about how slow he was on recon, the next, your legs gave out, and you hit the ground with a terrifying clang. “(Y/N)?!” he shouted, running to you so fast the ground shook beneath his feet.
Your optics flickered, static buzzing through your words. You tried to smile. Primus, you tried, but all that came out was a pained whisper of his name. Ratchet didn’t need a scan to know something was wrong. “We need to get them to the medbay. Now.” Bulkhead didn’t wait for anyone else; he scooped you up like fragile crystal, whispering your name like it was the only thing tethering him to reality.
The word 'Cybonic' nearly made him drop. He’d heard it before, on the battlefield, whispered like a curse. It was a plague that turned circuitry against itself, shutting down bots from the inside. “ You’re kidding,” he muttered to Ratchet, his voice cracking. But the medic just gave that grim look he always wore when hope was wearing thin.
Bulkhead never left your side. He sat beside your medberth with Miko’s blanket wrapped awkwardly around his shoulders, your servo gripped tightly in his own. He didn’t care if the others thought he was being dramatic; he’d rather be dramatic than alone. Every time your frame spasmed or your systems flickered, he flinched like he’d been hit. It was like watching the world end, one glitch at a time. “C’mon, Y/N… you’re stronger than this,” he murmured on the third day, optics bloodshot from lack of recharge.
His voice was soft, nothing like the boisterous Wrecker tone everyone knew. “You still owe me that race through the canyon, remember?” His laughter broke into static halfway through, and he leaned forward, pressing your servo to his cheekplate.
On the sixth day, your vitals dropped, and Ratchet yelled something Bulkhead didn’t understand, some medical code, some numbers, some urgent demand. But all Bulkhead could see was the way your body arched, seizing, like it was rejecting life itself. “No, no, no! Stay with me, (Y/N)!” he begged, almost in tears. The world blurred, and he wasn’t the strong, dependable Wrecker anymore. He was just a mech in love, losing his everything.
When you stabilized the next morning, he didn’t dare believe it at first. Ratchet hesitated, then finally said, “They’re responding to the treatment.” Bulkhead didn’t say anything. He just slumped forward, his forehead resting gently against yours, shaking. You were still there. You were still here.
The day your optics lit up fully again, the first thing you saw was Bulkhead slumped in a recharge chair next to your berth, snoring loudly, with dried energon streaks staining his cheek. You reached out and poked his shoulder. He jolted up like he’d been shot, optics wide. “Y/N?!” he shouted, voice cracking. You smiled. “Hey, big guy.”
The energon tears shed openly, and unashamedly. Not the silent kind, not the pretend-tough tears. Real ones. He gathered you in his arms so gently it nearly hurt, rocking you like you were the last spark in the universe. “Never—never—scare me like that again,” he whispered. You could feel the tremble in his voice, but beneath all of it… you felt the safest you’d ever been.
Ⰶ║ ⵈ ⵈ ⵈ ⵈ ⵈ ⵈ║Ⰶ
❀
❀
❀
#transformer prime#transformer prime imagines#transformer prime x reader#transformer prime scenario#transformer prime headcanons#transformer prime x you#tfp#tfp fluff#tfp angst#tfp optimus prime#tfp optimus x reader#optimus prime#tfp ratchet#tfp ratchet x reader#ratchet#tfp wheeljack#tfp wheeljack x reader#wheeljack#tfp bulkhead#tfp bulkhead x reader#bulkhead#optimus prime x reader#ratchet x reader#wheeljack x reader#bulkhead x reader
178 notes
·
View notes
Text
The Swiss Cheese Model of Covid Prevention

An edited version of the swiss cheese model tailored towards the measures that you as an individual can take to minimize your risk of infection. Public health is ultimately what its name implies, public, but that doesn't mean you're powerless.
Covid prevention is not all-or-nothing. Think of it as risk reduction, rather than a binary.
Let's go through these step by step.
VACCINES
The current vaccines are meant primarily to reduce chances of severe illness, hospitalization, and death. They will reduce your chance of infection a bit--but not nearly as much as you might think. You should still get your boosters regularly, because avoiding severe illness is of course worth doing.
If you haven't gotten the updated monovalent vaccine yet, go get it. It is not a booster. Think of it as a new vaccine. It's targeted towards the XBB lineages, which are now the most common variants. Your last boosters were likely of the bivalent type, aimed at both the original Covid strain from 2020 and Omicron. The new vaccine is monovalent, meaning it targets one family in particular.
Some studies suggest that the Novavax vaccine, which is a more traditional protein-based vaccine, is more effective and safer than mRNA vaccines, and offers better protection against future variants. Of course, the data we have so far isn't 100% conclusive (the last paper I linked is a preprint). Make of these findings what you will, just something to keep in mind. The new Novavax vaccine's availability is still limited, especially outside of the US.
MASKS
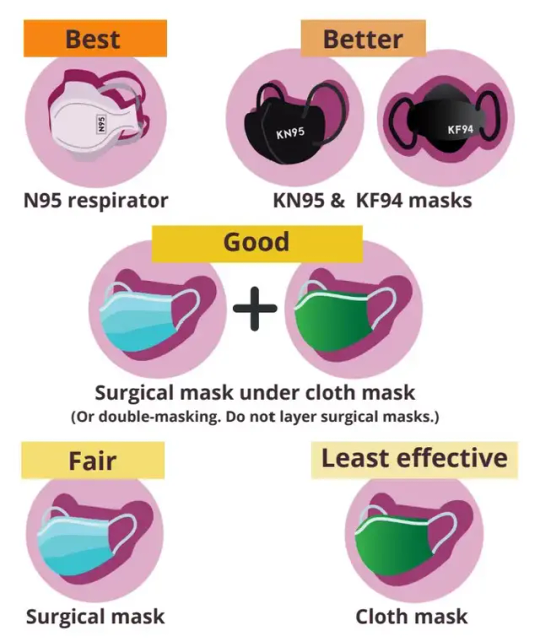
Masking is one of the most effective ways to protect yourself. While it is true that masking and reducing Covid transmission protects those around you, the idea that masks can't protect the wearer is outdated information from the early days of the pandemic when medical authorities refused to acknowledge that Covid is airborne.
The key to protecting yourself is to wear a well-fitting respirator. You want to minimize any gaps where air might leak out. If your glasses get fogged up, that's a sign that air is leaking.
Headbands will always have a tighter fit than earloop masks (and therefore provide better protection). However, you can use earloop extenders to improve the fit of earloop masks. You can find these online. Your comfort in wearing a mask is important, but there are options for compromise.
The above graphic doesn't include elastomeric respirators. While some (like the Flo Mask) are expensive, they can be much more affordable than buying disposables--look for P100 respirators at your local hardware store, but make sure it fits your face well.
For more general information, see this FAQ. For mask recommendations (NA-centric, sorry!), see my list here or Mask Nerd's YouTube channel.
For situations where you need to hydrate but don't want to take your mask off, consider the SIP valve.
Not even N95s are foolproof (N95 means it filters at least 95% of particles--with the other 5% potentially reaching you). Most people will likely not have a perfect fit. There will be situations where you'll have to take your mask off. The key is risk reduction, and that's why the Swiss cheese model is crucial.
If you can't afford high-quality masks, look for a local mask bloc or other organization that gives out free masks. Project N95 has unfortunately shut down. In Canada, there's donatemask.ca.
AVOID CROWDED INDOOR SPACES
This is rather self-explanatory. Indoor transmission is much, much, much more likely than outdoor transmission. If it's possible to move an activity outdoors instead, consider doing so.
If possible, try going to places like stores or the post office during less busy hours.
Viral particles can stay in the air for a considerable amount of time even after the person who expelled them has left. Do not take off your mask just because no one is currently present, if you know that it was previously crowded.
A CO2 monitor is a decent proxy for how many viral particles may have accumulated in the air around you. The gold standard is the Aranet4, but it's expensive, so here are some more affordable alternatives.
VENTILATION AND AIR FILTERS

Ventilation is effective for the same reason that outdoors is safer than indoors. If it's warm enough, keep windows open whenever possible. If it's cold, even cracking them open occasionally is better than nothing. Try to open windows or doors on different sides of a room to maximize airflow.
HEPA air filters can significantly reduce viral transmission indoors. Make sure to find one suitable for the room size, and replace the filters regularly. You want to look for devices with HEPA-13 filters.
You can use websites like these to calculate how long it takes for a device to change all the air in a room. Remember what I said about viral particles being able to hang around even after people have left? If an air purifier provides 2 air changes per hour, that means that after 30 minutes, any potential viral particles should be gone.
If you can't afford a commercial air filter, here's a useful DIY filter you can make with relatively simple materials. The filtration capacity is great--but due to being built with duct tape, replacing filters will be a challenge.
If you have to hold meetings or meet with people at work, having a smaller filter on the desk between you will also reduce chances of infection.
As a bonus, HEPA filters will also filter out other things like dust and allergens!
REDUCE LENGTH OF EXPOSURE IF EXPOSURE IS UNAVOIDABLE
Viral load refers to the amount of virus in a person's blood. If you've been exposed to someone with Covid, how much you've been exposed matters.
You might escape infection if the viral load you've been exposed to is very small. Or, even if you get infected, there will be less virus in you overall, leading to milder illness--and crucially, a lower chance of the virus penetrating deep into your body, creating reservoirs in your organs and wreaking long-term havoc.
A low viral load is also less contagious.
This is the same reason that wearing your mask most of the time, but having to take it off for eating, is still much better than not wearing your mask at all.
RECHARGEABLE PORTABLE AIR FILTERS
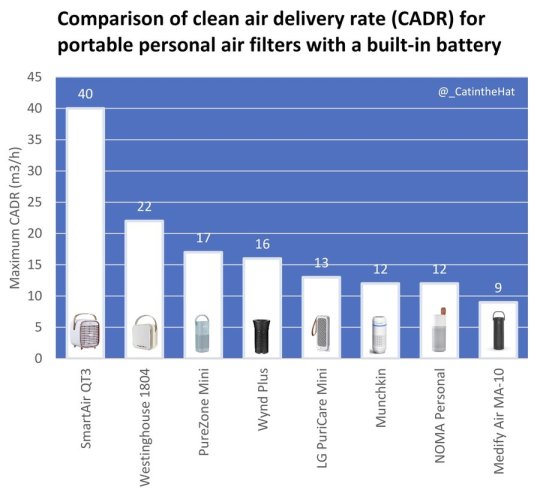
You might attract some odd looks. But if you're at high risk or just want to be as protected as possible, small portable air filters can help. Try to find models small enough to take with you on public transportation, to school, or while traveling.
These devices will be far too small to clean the air in the whole room. The goal is to have it filter air in your immediate vicinity. Be sure to angle the device so that the air is blowing in your face.
Unfortunately, rechargeable devices are much rarer and harder to find than normal air filters, and many are also expensive.
The best option at the moment, apart from DIY (which is possible, but you need to know what you're doing), seems to be the SmartAir QT3. The size and shape are a bit clunky, but it fits in a backpack. Its battery life isn't long, but it can be supplemented with a power bank.
NASAL SPRAYS
There's some research that suggests that some nasal sprays may be effective in reducing risk of infection by interfering with viruses' ability to bind to your cells.
These sprays are generally affordable, easy to find, and safe. The key ingredient is carrageenan, which is extracted from seaweed. So there are no potential risks or side effects.
Be sure to follow the instructions on the packaging carefully. Here's a video on how to properly use nasal sprays if you've never used them before.
Covixyl is another type of nasal spray that uses a different key ingredient, ethyl lauroyl arginate HCI. It also aims to disrupt viruses' ability to bind to cell walls. Unfortunately, I think it's difficult to obtain outside of the US.
CONCLUSION
None of the methods listed here are foolproof on their own. But by layering them, you can drastically reduce your chances of infection.
The most important layers, by far, are masking and air quality. But you should also stay conscientious when engaging with those layers. Don't let yourself become complacent with rules of thumb, and allow yourself to assess risk and make thought out decisions when situations arise where you might have to take off your mask or enter a high-risk indoor area, such as a hospital.
Remember that the goal is risk reduction. It's impossible to live risk-free, because we live among countless other people. But you can use knowledge and tools to keep yourself as safe as possible.
1K notes
·
View notes