#MobileHack
Explore tagged Tumblr posts
Text
Unlock Geo-Restricted Content - Step-by-Step: How to Change Your Android Location Without a VPN
Have you ever wanted to virtually change your location on your Android device? Whether you’re looking to access geo-restricted content or simply having fun faking your GPS location, it’s easier than you might think. In this guide, we’ll walk you through how to tweak your Android’s geographic coordinates using simple methods. Methods to Change Your Location on Android Although Android devices…

View On WordPress
0 notes
Text
The Guide of Mobile Hacking: Methods, Benefits, and Practices

Mobile phone has become a part of our life nowadays. We use it daily. Our mobile phone is a storehouse of many things including the information we need to send messages to someone's work, communicate and personal information including photos. And this treasure trove of data makes mobile phone hacking a concern. Mobile hack is to access someone's mobile without permission. and collecting the required messages from there. And we use a variety of techniques to do this. In this blog we will enter the world of mobile hacking and discuss about its various methods, how it helps us, why we need mobile hacking, what benefits we can get through mobile hacking, let's see the world of mobile hacking.
What is Mobile Hacking?
What we mean by mobile hacking is accessing someone's mobile without their permission. These can include smartphones, tablets and handheld devices. We use a number of methods to access these devices, including software vulnerabilities, phishing attacks, and special tools. One of the goals of mobile hackers is to hack the mobile and hope to extract important information from it.
Why Need Mobile Phone Hacking?
We all know mobile hacking is seen as negative, but here are some cases where the benefits of mobile hacking are mentioned. Today we will know about the benefits of mobile hacking, i.e. some of the benefits and advantages of mobile hacking such as:
📌 Security Testing: Cyber security professionals often take advantage of mobile hacking to test the network security of mobile devices. If it is mobile network weak then they check through mobile hacking.
📌 Parental Monitoring: Parents can monitor their child's mobile phone. To ensure the safety of your child, you can use mobile hacking to track your child's live location, save your child from terrorist attacks or various online threats.
🎯 Related Topic: Best Mobile Hack to Track Your Teenage Child
📌 Investigation: This mobile phone hacking is used to investigate a matter. It is used to hack someone's mobile and track various information about him. Mobile hacking is used to track the physical location of suspects.
📌 To Catch Cheating Spouse: Mobile hacker is needed to collect evidence of cheating spouse. A hacker can access the mobile and track the cheating spouse's social media like: Facebook, WhatsApp, Instagram, Twitter, Snapchat etc. A cheating spouse can be caught by tracking these platforms.
🎯 Related Topic: How WhatsApp Hacker Help You to Spend Infidelity-Free Life
Hack Mobile Phone by Phone Number
Hacking a phone also involves the data of that phone. Mobile hackers can hack your phone with the help of your phone number. Phishing, social engineering, and network vulnerabilities are used here. Once they get access, hackers can easily hack messages, hack calls, and even track and track the device's location.
Hack a Mobile Phone Through Phone Call
Hacking a phone through a call is one of the most advanced techniques. Hackers can gain control of a device with just one phone call. And he did that by exploiting the weakness of the mobile network. A call setup is manipulated by the system, which is invoked when a call is made. This method requires advanced engineering knowledge. And this method is used a lot.
Hack Cell Phone
Hacking a cell phone can be done through several methods, including:
📌 Phishing: Sending fraudulent messages or emails that trick the user into revealing their credentials or installing malware.
📌 Malware: Using malicious software to gain control of the device or steal data.
📌 Exploiting Vulnerabilities: Taking advantage of weaknesses in the phone's operating system or installed apps to gain unauthorized access.
Hack Android Phone
Android phones are a common target for hackers due to their widespread use and open-source nature. Some common methods to hack an Android phone include:
📌 Rooting: Gaining superuser access to the device, allowing the hacker to control all aspects of the phone.
📌 Malware: Installing malicious apps that can steal data or control the device.
📌 Network Attacks: Exploiting vulnerabilities in the phone's connection to Wi-Fi or mobile networks.
Hack Mobile Network
Hacking a mobile network involves intercepting and manipulating data transmitted over the network. This can include eavesdropping on calls, reading text messages, and tracking the location of devices. Techniques used for mobile network hacking include:
📌 Man-in-the-Middle Attacks: Intercepting communication between the mobile device and the network.
📌 Network Spoofing: Setting up fake network towers to trick devices into connecting and revealing their data.
Hack Mobile Camera
Hacking a mobile camera involves gaining control of the camera to capture photos or videos without the user's knowledge. This can be done by:
📌 Remote Access Trojans (RATs): Malware that allows the hacker to control the camera remotely.
📌 Spy Apps: Apps designed to secretly access the camera and transmit the captured data to the hacker.
Best Mobile Hacker
If you are in need of an expert mobile hacker then finding it can be very difficult for you. Because this food requires a lot of technology related knowledge and a lot of experience. Hackersalist is an organization where you can find a professional mobile hacker with vast knowledge and a hacking expert. They provide all mobile hacking services. They assure you that your work is done by an experienced hacker. Get here
Conclusion
Now at present we do good work through mobile hacking. Mobile manufacturing companies use it to test the security of their mobiles, parents use it to monitor their children, use it to investigate a crime, use services like mobile hacking to catch a cheating spouse. So before we take mobile hacking service we should be aware whether we really need mobile hacking? And how can we find a good mobile hacker if we need one? We must pay attention to these two things.
0 notes
Text
New cyberattack targets iPhone users, Hacks Apple ID information.
Washington, DC (TND) — Tech specialists have discovered...see more

#CyberSecurity#Feds#Technology#hackernews#MSFT#Shakur#mobilehacking#target#iphoneonly#tech#phone#apple#iphone#hacks#cyberattack
0 notes
Text
How to protect your phone from hackers in Tamil

#smartphones#hacking#cybersecurity#smartphonehacks#techtips#iphonehacks#techhacks#mobilehacks#phonehacks
0 notes
Text
Amazing Mobile Tips and Tricks | Normal Mobile Users Need to Know

some mobile tips and tricks that can improve your mobile experience: More details click here
0 notes
Text
[Media] Thanks Mobile Hacker
Thanks Mobile Hacker We want to give credit to the creators of the videos we used in our posts. ▫️ t.me/androidMalware ▫️ youtube.com/@mobilehacker ▫️ instagram.com/mobile_hacker0 #video #channel
1 note
·
View note
Link
#online fraud#internet fraud#digital payment fraud#fraud#trp scam#scam#suratfraud#bank fraud#surat news#gujarat news#hindi news#breaking news#kycfraud#mobilehack#hacker news#fraud news#fraude sistema financiero#scammers#bank scam#reporter17#trendzplay
0 notes
Text
youtube
www.instagram.com/vkktechlogs
#Subscribe#VKkTechLogs#Like#comment#Share#Youtube#Flight Mode mein Net Kaise Chalaye#How to Use Internet in Flight Mode#MobileTrick#MobileHack#Mobile#flightmode#FlightModeHacks
0 notes
Photo

Mobile app developers used to look solely at the number of downloads to gauge their success.
That was until it was discovered that 77 percent of users abandon an app within three days.
Those high abandonment numbers have led app developers to look at more customer behavior patterns to determine how to keep the users they acquired.
#mobile#analytics#mobileapp#appseo#seo#customer#mobilehack#results#growthfunnel#growth#progrowthhack
0 notes
Photo
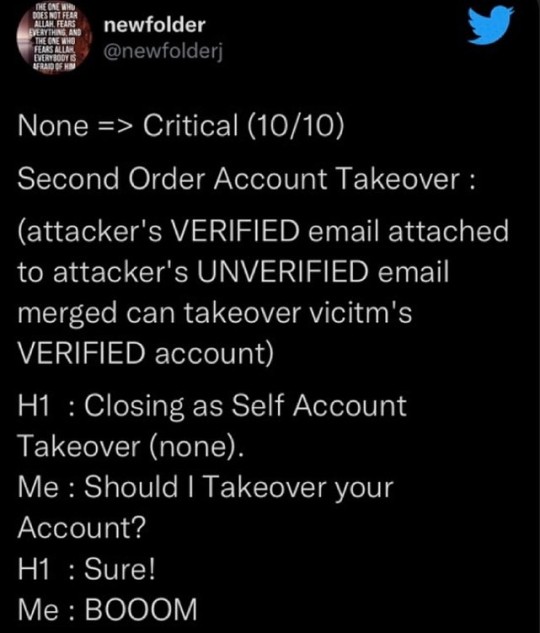
Daily Tweets. #tweets #tweetsfromtwitter #hackertweet #hackerinstagram #biohacking #applicationsecurity #lifehacks #mobilehacks #penetrationtesting #offensivesecurity https://www.instagram.com/p/ClRSbmVy0Mq/?igshid=NGJjMDIxMWI=
#tweets#tweetsfromtwitter#hackertweet#hackerinstagram#biohacking#applicationsecurity#lifehacks#mobilehacks#penetrationtesting#offensivesecurity
4 notes
·
View notes
Link
Easiest way to get free gems for Tennis Clash!
#GameBug#TennisClash#TennisClashHack#TennisClashCheats#TennisClashHackAndroid#TennisClashHackiOS#Mobile#MobileHack
0 notes
Text
Hacking Cases
Primary Hackers are offering the best services for hacking cases at affordable prices. Phone hacking is a critical security issue so we will project done within 2 hours. Visit our website today to learn more.
1 note
·
View note
Link
in this article, we’ll share the way to Hack unlimited health with the Call of Duty Mobile hack. By hacking unlimited health you are able to defeat your enemy so easily, You do not die no matter what! Bluezone, Bulletsfall damage, vehicle damage, and explosions don’t reduce your health!.
1 note
·
View note
Text
What to do if your phone is hacked?

Hacking has become increasingly common on mobile devices in the past few years. A hacker could be watching your every move, whether it's gaining access to your personal information or even your credit card details. With more than a billion mobile phone users worldwide, mobile hacking is becoming an increasing problem. In this article, you'll learn about how cybercriminals hack your phone and what you can do to protect yourself from them!
Now share your Thoughts with us in the 𝗖𝗼𝗺𝗺𝗲𝗻𝘁 section
Read the full blog: https://bit.ly/3g3zpTL
0 notes
Text
आपको बिना बताए अकाउंट से पैसे निकाल रहे हैं ये ऐप, तुरंत करें डिलीट वरना हो सकता है नुकसान

चैतन्य भारत न्यूज आज के समय में हमारे 90 प्रतिशत काम मोबाइल के जरिए ही पूरे हो जाते हैं। लोग अपने काम के कई ऐप्स डाउनलोड करके उसी से अपनी कई जरूरतों को पूरा कर लेते हैं। लेकिन कई बार ये ऐप्स खतरनाक भी साबित हो जाती हैं। आपने ऐप्स के जरिए फोन का डाटा चुराने की खबरें तो अक्सर सुनी ही होगी। लेकिन इन दिनों एक ऐसी ऐप सामने आई है जो आपका ��काउंट भी खाली कर सकती है। बिना यूजर परमीशन कट जाते हैं पैसे जी हां... प्ले स्टोर पर एक ऐसी ऐप को स्पॉट किया गया है, जो यूजर्स के अकाउंट को खाली कर सकती है। जानकारी के मुताबिक, सिक्यॉर-डी टीम के द्वारा एक नई रिसर्च की गई जिसमें ‘ai.type’ नाम की ऐसी ऐप पाई गई है, जो बिना यूजर की परमिशन के उसकी प्रीमियम डिजिटल सर्विसेज खरीद सकती है। ऐसे में यूजर को यह पता भी नहीं चलता है कि उसने कोई प्रीमियम कंटेंट सर्विस खरीदी है और उसके पैसे कट जाते। जानकारों ने बताया कि, यह ऐप बैकग्राउंड में काम करता था। इस ऐप में यूजर को बिना कुछ पता चले फेक ऐड व्यूज लिया जाता था। इतना ही नहीं बल्कि ये ऐप डिजिटल खरीदारी भी कर सकता था, जिसके चलते यूजर के अकाउंट से पेमेंट की जा रही थी। प्ले स्टोर पर जून में हो गई थी ब्लॉक सिक्यॉर-डी ने बताया कि, इस ऐप को खतरनाक बैकग्राउंड ऐक्टिविटी के कारण प्ले स्टोर से जून में ही ब्लॉक करके हटा दिया गया था। हालांकि, जिन यूजर्स ने इस ऐप को अपने फोन से अनइंस्टॉल नहीं किया है, वह इसके खतरनाक अटैक का शिकार हो सकते हैं। जरुरी जानकारी आप अपने फोन में इनस्टॉल सभी ऐप्स के बारे में अच्छे से जानकारी रखें और फोन को समय-समय पर अपडेट भी करते रहें। यदि आपसे कभी अनजाने में कोई भी ऐप इनस्टॉल हो गई हो तो आप उसे तुरंत डिलीट कर दें। एक और बात ध्यान रखें कि आप अपने फोन में सिर्फ वो ही ऐप्स रखे जो आपकी ज्यादा जरुरत की हो। ये भी पढ़े... जानें कैसे भारतीय WhatsApp में घुसी इजरायली एजेंसी? कौन-कौन हुए इस जासूसी के शिकार? 13 लाख भारतीयों के डेबिट-क्रेडिट कार्ड का डेटा चोरी, ऑनलाइन बेच रहे हैकर्स यदि आप भी हुए हैं ऑनलाइन फ्रॉड के शिकार, तो ऐसे कीजिए शिकायत जांच एजेंसी ने किया रोमांस घोटाले का खुलासा, शादी और रोमांस के नाम पर लोगों से वसूले 322 करोड़ Read the full article
#ai.type#atm#atmfraud#bankfraud#creditcard#creditcarddatastolen#creditcardfraud#cybercrime#dangerousapps#datastolen#debitcard#debitcarddatastolen#debitcardfraud#emojiapp#fakeapps#hackingdarkweb#israel#israelhackingcompany#keyboardapps#mobilehack#Onlinefraud#rbi#reservebankofindia#thirdpartykeyboard#अपराधशाखा#आरबीआई#इजरायल#इजरायलकीसाइबरखुफियाकंपनीएनएसओग्रुप#इजरायलीसॉफ्टवेयर#ईमेल
0 notes
Photo

Bir Mesajla iPhone Çöküyor!
Apple, iOS'u her yeni güncelleme ile daha güvenli duruma getiriyor. Lakin her vakit mutlaka bir güvenlik zafiyeti oluyor. Bu seferki durum mesaj uygulaması ile alakalı iPhone'a gelen bir mesaj tekrardan başlatılana kadar iPhone'u bir süre kullanılamaz duruma getirebiliyor.
Mesaj üç karakterden oluşuyor!
Bu açık size tanıdık geliyor olabilir; Daha önce iOS'ta böyle mesaj problemleri defalarca gerçekleşti lakin haberimizde konu olan mesaj sadece üç karakterden oluşuyor ve mesajı açmasanız bile telefonu çökertiyor.
1 note
·
View note