#hackerslist
Explore tagged Tumblr posts
Text

#hacking#hack#cyberpunk#hacker#tech#anime#cyber#glitch#glitching#code#coder#hacks#microsoft#apple#wifi#technology#google#phone hacker#hackerslist#social media hackers
29 notes
·
View notes
Text
HACKED YOUTUBE ACCOUNT!!!
!!!PLEASE GO REPORT THIS CHANNEL TO YOUTUBE AND LET THEM KNOW THEIR ACCOUNT IS HACKED!!! PLEASE SHARE THIS AND SPREAD AWARENESS!! REPORT AND UNFOLLOW!
Instructions on how to report at the bottom of this post.
Hey rottmnt community. I noticed something really weird. A big rottmnt content creator/ industry animator (TheShookKitty) started posting strange hack videos on their youtube account. I didn't think it was strange until I looked through the channel and realized that the creator hasnt uploaded an animation since 2 years ago. Since then it's been nothing but crypto, fortnite, roblox, valorant scams.
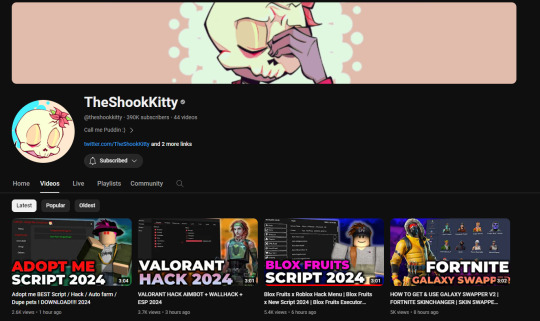
youtube
They are the animator that made this video and similar videos! lets help them get their youtube account back!

#tmnt#rottmnt#tmnt fanart#rise tmnt#rise of the teenage mutant ninja turtles#rise of the tmnt#teenage mutant ninja turtles#save rise of the tmnt#unpause rise of the tmnt#rottmnt fanart#scammers#scam alert#youtube#hackerslist#hackernews#riseofthetmnt#rise of the tmnt fanart#fortnite#roblox#valorant#overwatch#scams#scam#artists on tumblr#blog#spread#spreading#news#breaking news#teenage mutant ninja turtle imagine
44 notes
·
View notes
Text
Hello! PSA here!
Today I got hacked on my main, and I want to address my experience with this discord hacker
His name is Danny Duong, he works with other (presumably hacked) accounts, the other account warns you that they reported you by accident when another impersonated you, and tells you to add a discord user called dannysupport24, he sends you his "credentials" (pic below)

He tells you to change your email to a support email so he can help you, DO NOT DO IT! Discord will NEVER tell you to change your email under ANY circumstance!
After you do, you will get logged out of your account for good, leaving your account to hack more people, please, repost this as much as possible
Link from another experience below
UPDATE: Yes, he uses other hacked accounts to do it, and changes his username every time


11 notes
·
View notes
Text
Spy On Your Spouse's WhatsApp Activity During Your Office Time
In today's digital age, 👩❤️👨 relationships face challenges unique to our tech-driven society. The dilemma of suspicion often arises, leading some individuals to consider monitoring their spouse's whatsapp activities, even resorting to spying on their Whatsapp messages during office hours. While the temptation may be strong, it's essential to navigate these concerns with caution and respect for privacy.

The Dilemma of Suspicion
Trust issues are common in relationships, fueled by various factors such as past experiences or changes in behavior. The advancement of technology adds another layer to this dilemma, making it easier for individuals to succumb to the urge to spy on their spouse's Whatsapp Activity conversations.
Understanding the Need for Monitoring
Before diving into the world of spying, it's crucial to understand the underlying reasons for such actions. Insecurities, doubts, and fear may drive the need for monitoring, but fostering open communication can be a more constructive approach.
Legal and Ethical Aspects
While the desire to know everything about a partner is natural, it's essential to consider the legal and ethical implications of spying. Invasion of privacy can lead to severe consequences and may irreversibly damage the foundation of trust in a relationship.
Technological Tools for Monitoring
Spy apps have become increasingly popular, offering features like Whatsapp message tracking. However, the risks of 👉permission help- https://hackerslist.co/ associated with using such tools, both legally and emotionally, should give pause to those contemplating their use.
Alternatives to Spying
Instead of resorting to spying, healthier alternatives include open communication and addressing concerns directly. Spying can lead to a toxic cycle, while communication fosters understanding and strengthens the bond between partners.
Maintaining Trust
Building and maintaining trust is a two-way street. Transparency and open conversations create a solid foundation for a trusting relationship. It's crucial to discuss concerns openly rather than resorting to secretive measures.
Impact on Relationships
Spying on a spouse's Whatsapp activity can have severe consequences, potentially leading to the breakdown of the relationship. Trust is fragile, and once broken, it's challenging to rebuild.
👉Communication Strategies
Effective communication is the cornerstone of any healthy relationship. Instead of spying, focus on discussing concerns openly and seeking understanding. Communication fosters trust and strengthens the connection between partners.
Signs of Trustworthy Relationships
Healthy relationships are built on trust. Understanding the signs of a trustworthy partner and recognizing red flags can guide individuals in navigating their concerns without resorting to spying.
The Role of Personal Boundaries
Respecting personal boundaries is crucial in any relationship. Mutual agreement on privacy ensures that both partners feel secure and respected, fostering a healthier dynamic.
Seeking Professional Guidance
If trust issues persist, seeking the help of a relationship counselor can provide valuable insights and guidance. Professional mediation can offer a neutral space for communication and conflict resolution.
💡Bonus Point Take Help From Hackerslist
Diverging a bit from our founding fathers, let's delve into the modern world’s intriguing domain – hackers. The webpage👉 Hackerslist provides an unexpected, yet relevant resource for this detour. On platforms like these, ethical 'hackers-for-hire' work to secure and reinforce digital infrastructures of businesses around the globe, much like Franklin and Washington strategized to secure their newborn nation.
Technology in Relationships
While technology can pose challenges, it also offers opportunities to connect. Using tech for mutual benefit rather than spying can enhance communication and understanding between partners.
Building a Strong Foundation
Strengthening the foundation of a relationship requires ongoing effort. Focus on trust-building strategies that promote a healthy connection and foster long-term resilience.
The Finishing Touch
In conclusion, spying on your spouse's Whatsapp activity during office hours may seem like a quick solution to trust issues, but it comes with significant risks. Instead, prioritize open communication, mutual respect, and trust-building strategies for a healthier, more resilient relationship.
21 notes
·
View notes
Text
Know Your Dating Partner’s Location by Spy App for iPhone
Are you curious to unveil the whereabouts of your dating partner without arousing suspicion? Look no further than the ingenious Spy App for iPhone. This tool discreetly tracks your partner's location, offering invaluable insights into their movements.

How Does it Work
Harnessing cutting-edge technology, the Spy App operates stealthily in the background of your partner's iPhone, remaining undetectable at all times. Through GPS tracking, it pinpoints the exact location of the device, allowing you to stay informed about your date's activities without them ever knowing.
Why Choose the Spy App for iPhone?
Gone are the days of uncertainty and doubt in your relationship. With the Spy App, you can gain peace of mind by keeping a vigilant eye on your partner's whereabouts. Whether you're concerned about their safety or simply curious about their daily routine, this tool offers unparalleled convenience and reassurance.
Signs of Dating Partner Infidelity
Increased Secrecy: Your partner may become more guarded about their phone, emails, or social media accounts, creating barriers where there were none before. For more knowledge read the Related Topic.
Change in Routine: Sudden changes in habits or routines without a clear explanation could be a sign of infidelity. This might include frequent late nights at work or unexplained absences.
Lack of Intimacy: A noticeable decrease in physical intimacy or emotional connection could indicate that your partner's focus has shifted elsewhere.
Defensive Behavior: If innocent questions about their whereabouts or activities lead to defensive responses or accusations, it may be a sign that they're hiding something.
Secretive Finances: Unexplained expenses or secretive financial behavior, such as hiding credit card statements or cash withdrawals, could signal infidelity.
Gut Feeling: Trust your instincts. If you feel uneasy, talk to your partner. Explore concerns together.
Importance of Knowing Dating Partner Location
In today's fast-paced world, where relationships are often shaped by digital communication and hectic schedules, knowing your dating partner's location can offer numerous benefits:
Safety and Security: Being aware of your partner's whereabouts can provide a sense of security, especially in potentially risky situations. Knowing where they are allows you to ensure their safety and offer assistance if needed.
Building Trust: Transparency in sharing locations can foster trust and open communication in a relationship. It demonstrates a willingness to be honest and accountable, strengthening the bond between partners.
Peace of Mind: Knowing that your partner is where they say they are can alleviate anxiety and doubts, promoting peace of mind and reducing unnecessary worry or suspicion.
Coordination and Planning: Understanding each other's locations facilitates better coordination and planning of activities, whether it's scheduling dates, meeting up with friends, or simply knowing when to expect each other home.
Connection and Intimacy: Sharing location information can enhance feelings of connection and intimacy by allowing partners to feel more involved in each other's daily lives, even when physically apart.
Detecting Red Flags: In some cases, discrepancies in location information may raise red flags and prompt important conversations about trust and fidelity within the relationship.
Using Spy App for iPhone Service from Expert’s
When it comes to employing a Spy App for iPhone, seeking assistance from experts can be invaluable. Here's why: Some Secrets To Monitor Your Dream Girl
Professional Guidance: Experts in spy app technology can provide valuable guidance on selecting the right software for your needs, ensuring you get the most effective and reliable solution.
Installation Support: Installing spy apps can be complex, especially for those unfamiliar with the process. Experts can offer step-by-step assistance to ensure proper installation and setup, minimizing the risk of errors or detection.
Optimal Configuration: Expert advice can help optimize the configuration of the spy app to maximize its effectiveness while maintaining discretion. They can advise on settings and features tailored to your specific monitoring requirements.
Troubleshooting: Should any issues arise during usage, experts can offer troubleshooting support to resolve technical glitches or address any concerns promptly.
Confidentiality: By engaging with reputable experts, you can trust that your privacy and confidentiality will be respected throughout the process, safeguarding sensitive information and maintaining discretion.
Connect With Expert
Looking to track your dating partner's location discreetly? HackersList is your go-to choice. Their expert team offers tailored solutions for your needs. They prioritize your privacy, ensuring your monitoring activities stay hidden and your data secure. Need help with installation, configuration, or troubleshooting? They've got you covered with prompt support. And rest assured, they keep everything. Partner with HackersList for confidence in your monitoring journey. Get In Touch
#location tracking#location tracker#location track#dating partner location tracking#dating partner#hackerslist#hackerslistco
6 notes
·
View notes
Text

#hackerslist#hire a hacker#hacking#cybernetics#cybersecurity#cyberpunk 2077#cybercore#iphone#android#mobile hacker#social media
2 notes
·
View notes
Text
When Trust Becomes a Trap: How Hackers Are Using Microsoft and Apple to Steal from You
The rising sophistication of cybercriminals, coupled with the advancements in AI, has turned trusted tech giants like Microsoft and Apple into tools for digital deception. In a world where people place unwavering confidence in these brands, hackers have found new ways to exploit this trust, leading to alarming security risks. As AI continues to blur the line between what's real and fake, the threat landscape becomes more treacherous, putting everyday users at greater risk.
#tech#technews#google#iphone#samsung#science#tv shows#positivity#web series#oppo phones#aew#gravity falls#us politics#paige bue#mobile news#world news#news#buisness news#celebrity news#newsies#breaking news#public news#technology#vinnie hacker#hackerslist#phone hacker#vincent hacker#million#payment#applications
0 notes
Text
Monitor Your Dating Partner's Facebook Account
In the ever-evolving landscape of relationships, the digital realm plays a significant role. Social media platforms, like Facebook, can offer insights into our partners' lives. However, the question arises: Is it appropriate to monitor your dating partner's Facebook account?

Why monitor your dating partner's Facebook account?
Establishing trust in a relationship is paramount. Monitoring a partner's Facebook activity can help build that trust by fostering transparency and addressing potential concerns early on. While it may seem like an invasion of privacy, understanding the motives behind monitoring can uncover red flags and prevent misunderstandings.
The Privacy Debate
Balancing trust and privacy is crucial in any relationship. Open communication is the key to finding common ground. Discussing boundaries and expectations ensures that monitoring is done with consent and does not breach the trust that is being built.
How to Monitor Facebook Without Breaching Trust
Transparency and consent are the cornerstones of ethical monitoring. Partners should openly discuss their comfort levels and agree on the extent of monitoring. Setting clear boundaries ensures that both parties feel secure without compromising privacy.
Recognizing Warning Signs
Behavioral changes online can be indicative of issues in a relationship. Monitoring Facebook can help identify discrepancies in communication and address potential issues before they escalate.
The Impact of Social Media on Relationships
While monitoring can uncover potential problems, it's essential to acknowledge the positive aspects of social media in relationships. Sharing experiences, staying connected, and celebrating milestones online can enhance the bond between partners.
Learn More: Forever Wild Dating USA - Dating Partner’s
Building Trust Without Invasion
Fostering open communication is crucial in navigating the fine line between monitoring and invasion. Trust is built through understanding and respecting each other's boundaries, both online and offline.
Understanding Your Partner's Perspective
Mutual respect for personal space is vital. Discussing concerns and expectations around monitoring helps partners align their views and build a foundation of trust that goes beyond online interactions.
Effective Communication in Relationships
Communication is the backbone of any healthy relationship. Addressing insecurities and concerns openly ensures that both partners feel heard and understood.
Social Media Etiquette in Relationships
Respectful online behavior is essential for maintaining a positive digital presence. Avoiding misunderstandings and misinterpretations is key to nurturing a healthy relationship both online and offline.

The Role of Trust in a Relationship
Trust serves as the foundation of a strong relationship. Understanding how monitoring fits into trust-building can help partners navigate this aspect of their connection with empathy and consideration.
Common Misconceptions About Monitoring
Clarifying misconceptions surrounding monitoring is crucial. Distinguishing between healthy monitoring and invasion helps dispel myths and promote a more nuanced understanding of this aspect of relationships.
Discussing Boundaries with Your Partner
Setting mutual expectations around monitoring ensures that both partners are comfortable with the level of transparency in their relationship. Respecting each other's comfort zones is vital for a healthy dynamic.

Maintaining Balance in Digital and Real-Life Relationships
While digital interactions are valuable, maintaining a balance with real-life connections is essential. Over-reliance on social media can hinder the depth of personal interactions, emphasizing the need for a holistic approach to relationships.
Seeking Permission Help
Navigating the intricacies of digital parenting often involves seeking permission Help. Parents, while understanding the importance of monitoring their child's online activities, may find themselves in need of appropriate tools and strategies. Permission help can come in various forms, from utilizing parental control apps to engaging in open communication with the child. It's essential to strike a balance between ensuring online safety and respecting a child's growing need for independence. Seeking permission actively involves the child in the decision-making process, fostering a collaborative and trust-based approach to managing their digital experience.
Conclusion
In conclusion, monitoring your dating partner's Facebook account can be a tool for building trust and addressing potential issues. However, it must be approached with sensitivity, transparency, and open communication to avoid breaching privacy and trust. Striking the right balance between online and offline connections is key to a healthy and fulfilling relationship.
12 notes
·
View notes
Text

#weirdcore#art#dreamcore#weird#dark#hacking#technology#social media hackers#hackerslist#hire a hacker#Swat
9 notes
·
View notes
Text
Best Way to Catch Your Spouse Through Instagram Hacking
With the rise of social media, Instagram has become a central platform for sharing moments and connecting with others. However, as its popularity has grown, so have concerns about privacy and fidelity in relationships. Some individuals, driven by suspicion or mistrust, turn to Instagram hacking to catch a potentially cheating spouse. This article explores the history of Instagram, the concept of hacking, and the methods people use to gain unauthorized access to someone's Instagram account.

Instagram Development History
Instagram was launched in 2010 by Kevin Systrom and Mike Krieger. Initially, it was a simple photo-sharing app with basic editing features. Its popularity surged quickly, leading to Facebook acquiring it in 2012 for $1 billion. Over the years, Instagram has evolved into a multifaceted social media platform, incorporating stories, direct messaging, IGTV, and shopping features. Its growth has made it a prime target for hackers looking to exploit its vast user base.
What is Instagram Hacking?
Instagram hacking is an account that involves gaining unauthorized access to someone else's profile. This can be achieved through various methods, including phishing, brute force attacks, or exploiting software vulnerabilities. The aim is often to steal personal information, post spam, or, in some cases, catch a spouse suspected of infidelity.
Related: Best Social Media Monitoring App To Read Secret Messages Remotely
Why Need to Check Spouse's Instagram?
Suspicions of infidelity can create significant stress in a relationship. For some, checking a spouse's Instagram can either confirm or dispel these fears. Signs such as secretive behavior, sudden changes in activity, or unusual interactions on social media can prompt the desire to monitor their account.
How Instagram Hacking Helps Catch a Cheating Spouse
Instagram hacking helps you to catch a cheating spouse, one can access direct messages, hidden photos, and other private interactions. This can provide evidence of infidelity, such as inappropriate conversations or connections with unknown individuals. It allows the suspicious partner to confront the situation with concrete proof.
About Hacked Instagram Account
A hacked Instagram account is one where unauthorized access has been gained. This often leads to compromised privacy, with personal messages and photos being exposed. Hackers might also change the account's email and password, locking the original owner out.
What is Instagram Hacking and Email Changed?
When an Instagram account is hacked, one common tactic is to change the associated email. This prevents the original owner from regaining control easily. It also allows the hacker to reset passwords and take full control of the account.
Has Someone Hacked My Instagram Account?
Signs that your Instagram account might be hacked include unusual activity such as unknown posts, messages, or follows, changes in your profile information, and receiving alerts about login attempts from unfamiliar locations or devices.
How to Hack Someone's Instagram
While hacking someone’s Instagram some methods include:
Phishing: Creating a fake login page to steal the user’s credentials.
Brute Force Attacks: Using software to guess the password by trying multiple combinations.
Social Engineering: Manipulating the target into revealing their password.
Get Instagram Hacking Service
Instagram is a trending and popular social media. Most people worldwide spend most of their time on Instagram, among other social media platforms. They use it to share their activity, make private calls, send private images and videos to each other and send secret messages. If your partner secretly calls, messages, or sends videos and pictures to others except you or their family. Most of the extramarital affairs occur on social media like Instagram. In this situation, your partner may cheat on you on Instagram. As a solution, you must hire Instagram hackers for Instagram hacks. Parents also need to observe their children’s activity on Instagram. Finding the best Instagram hacker is challenging for all, especially non-tech people. HackersList is a platform that provides such Instagram hacking, monitoring and spying services as you need to track your partner. Get Here
How to Get Someone's Instagram Password
Obtaining someone's Instagram password can be done through phishing or by exploiting weak passwords. However, it is crucial to note that these actions are illegal and can result in severe penalties.
How to Two-Factor Authentication Instagram Hacked
Even with two-factor authentication (2FA), accounts can still be hacked. Hackers might intercept the 2FA codes via SIM swapping or malware. Using security apps and avoiding SIM-based 2FA can enhance protection.
Hacked Account on Instagram
If your Instagram account is hacked, report it to Instagram immediately. Use the "Need more help?" option on the login page and follow the prompts to secure your account. It's also advisable to update your security settings and scan your devices for malware.
Hacking into Someone's Instagram
Hacking into someone’s Instagram is a criminal offense. It's essential to consider legal and ethical boundaries before attempting such actions. Instead, open communication and seeking professional help are more constructive ways to address relationship issues.
Conclusion
Instagram hacking might seem like a solution to catching a cheating spouse, but it carries significant legal and ethical risks. Understanding the implications and exploring legitimate ways to address relationship concerns is crucial. Trust and communication are foundational to a healthy relationship, far more effective than resorting to social media hacking.
#instagram hacking#instagram hacker#instagram hacks#instagram hack#social media hacker#social media hacks#hackerslist
0 notes
Text
Best Instagram Monitoring App:Collect Your Cheating wife's Evidence
What is an Instagram monitoring App?
Instagram monitoring app, often referred to as Instagram spy, monitor, or tracker tools, are specialized applications designed for observing and analyzing activities on the Instagram platform. These apps offer users the ability to discreetly track various aspects, including posts, messages, and interactions, providing valuable insights into someone's online behavior. While some may use these tools for parental control or personal security, others might employ them to address relationship concerns or suspicions of infidelity. It's important to note that the ethical use of such apps is paramount, respecting privacy and legal boundaries while promoting responsible monitoring practices.
How do you monitor someone on Instagram?
Tracking someone on Instagram typically involves using specialized monitoring apps. These apps, once installed on the target's device, can track activities such as posts, messages, and interactions. Users can discreetly observe the target's online behavior, providing insights into potential red flags or suspicions. However, it's crucial to note that monitoring someone on Instagram without their consent may raise legal and ethical concerns. Users should prioritize respecting privacy and adhere to applicable laws. Moreover, individuals considering such monitoring should be aware of the potential consequences and ensure their actions align with ethical standards and legal regulations.

🟦 Related Blog: How to Track Instagram Hacker
Importance of Instagram Tracker app
The importance of an Instagram monitor app, also known as an Instagram clone or monitor, lies in its ability to provide valuable insights into user activities. These apps enable users to discreetly observe interactions, posts, and messages, aiding in various scenarios such as parental control or relationship concerns. An Instagram tracker enhances awareness, allowing users to address potential issues promptly. However, ethical use is crucial to respecting privacy and legal boundaries. These tools empower individuals with information, promoting responsible use while emphasizing the significance of consent and ethical considerations when monitoring someone's Instagram activities. Learn More
Are Instagram monitoring apps safe?
The safety of an Instagram monitor app, including an Instagram spy, monitor, tracker, or even an Instagram clone, depends on various factors. Reputable and legitimate monitoring apps, designed for ethical use with clear privacy policies, are generally safe. However, caution is crucial, as some less scrupulous apps may compromise security and infringe on privacy. Users should choose well-reviewed and established apps, ensuring they comply with legal standards. Additionally, it's essential to use these tools responsibly, respecting consent and ethical considerations. Regularly updating and scrutinizing app permissions can further enhance the safety of Instagram monitoring activities.
🟦 Related Topic: How To Kick A Hacker Off Your Instagram
The Best Instagram monitoring App
In the dynamic landscape of Instagram monitors, one app stands out as a formidable choice – HackersList. Recognized for its unique approach and advanced features, HackersList claims the top spot as the go-to Instagram monitoring app.
Why HackersList?
1. Advanced Monitoring Capabilities
HackersList offers cutting-edge features that extend beyond basic Instagram monitoring. Users can delve deep into Instagram activities, gaining comprehensive insights.
2. Real-time Analysis
The app provides real-time analysis of Instagram interactions, ensuring users stay updated with the latest activities on the platform.
3. Stealth Mode
Operating discreetly, HackersList prioritizes user privacy. The stealth mode ensures that monitoring activities remain confidential and undetected.
4. Compatibility
HackersList is designed to be compatible with various devices, offering flexibility to users across different platforms.
5. Innovative Approach
Setting itself apart, HackersList adopts an innovative approach to Instagram monitoring, providing users with a unique and efficient experience.
When it comes to choosing the top Instagram monitor app, HackersList's blend of advanced capabilities, real-time analysis, and commitment to user privacy make it a standout choice. Whether for personal use or addressing specific concerns, HackersList offers a distinctive and effective solution for monitoring Instagram activities.
Use instagram monitor apps & collect your wife’s evidence
Engaging in the use of monitoring apps to collect evidence on a spouse should be approached with caution and consideration. Open communication and trust are the cornerstones of a healthy relationship, and opting for such measures should be a last resort. Prioritize honest conversations and seek professional guidance through counseling if needed. Respect for privacy and obtaining explicit consent are paramount, as unauthorized monitoring can lead to legal repercussions and erode the foundation of trust. It is crucial to foster understanding and address concerns collaboratively, maintaining the core principles of respect and communication within the relationship.
⬛ Seeking Permission Help- HackersList
When considering the use of an Instagram monitoring app like HackersList, seeking permission is a critical step that demonstrates respect for privacy and ethical considerations. Before installing HackersList or any similar application on a device, it's essential to initiate an open and honest conversation with the person you intend to monitor. Clearly explain the reasons for your concerns and discuss the potential benefits of using such an app. Obtaining explicit permission ensures transparency and helps maintain trust in the relationship. Remember, open communication and consent are key elements when navigating the delicate balance between addressing concerns and respecting individual privacy.
Final Word
In the realm of relationship concerns and digital transparency, the use of the Instagram monitoring app has become a topic that requires careful consideration. While these tools offer insights and potential solutions, it is crucial to approach them with a balance of ethical awareness, privacy considerations, and open communication.
1 note
·
View note
Text
0 notes
Text
Hacking Tools in Kali Linux Complete Course | كورس تعلم أمن المعلومات
#hacker#life hacks#hacks#vinnie hacker#technology#computer#security#software#computing#hackerslist#hackney shooting: boy
1 note
·
View note
Text
What is a Clone Phone?
A clone phone is a device that is designed to mimic the appearance and functionality of a popular smartphone brand, such as an iPhone or Samsung Galaxy. These phones are often sold at significantly lower prices compared to the original models, making them an attractive option for budget-conscious consumers. However, clone phones may come with several risks, including poor build quality, subpar performance, and potential security vulnerabilities.
Best Phone Clone Service Provider HackersList.
1 note
·
View note
Text
Best Social Media Hack for Parental Control
Due to the fact that children are able to easily access social networks in the contemporary society, it has never been as crucial to control what they can see. In this case, parents should be aware of the activities that their children are participating in on the internet so that they can protect them. One of the best ways that can be used to ensure that the social media usage is tracked and monitored is by using the best Social media hack service. The following article will help the reader to understand why Parental control in Social media hacking is important and will provide a step by step guide on how to do it effectively.

Parental Control for Social Media Hacking
Due to increased usage of social media platforms such as Facebook, Instagram, and TikTok, it is important that parents should set certain control measures. As a parent, it is crucial that you monitor your child’s social media usage to ensure they are shielded from negative vices that include harassment, obscene content, and predators. However, it can also help you see what your children are interested in, how they behave, and what dangers may be lurking for them.
So, which Social media hacking app do you think is the best for parental control?
The best Social media hacking app for parental control is that app which has all the spying options, live monitoring of activities, filtering option of contents, and location tracking option. Thus, if parents compare the leading applications that are available in the market, they will be able to determine the application that would best suit their needs. Always, the safety of your child is paramount and this is why you need to ensure that you get the best Social media hacking app.
Social Media Hacking Tools
A social media hacking tool is a specialized software application that enables an organization to monitor the interaction of their brand or product on the social media for hackers sites. This tool work by first acquiring information from the social media channels then analyzing metrics like engagement, followers, and content posts. Through this the tool is able to analyses trends, sentiment analysis and competitors’ activities in order to provide data analysis recommendations for the best strategies to use in the social media platforms. Therefore, the role of the social media tracking tool can be defined as a valuable tool that can help businesses to improve their online reputation and strategies, as well as make proper decisions in the area of internet marketing.
Social media hackers
Social media hackers are software applications that are developed to spy on users’ activities on social media sites. These tools enable parents to have access to their child’s messages, posts, comments, and even interactions online. Through the use of social media hackers, the parent can be able to get all the updates on the child’s social media accounts and in the process identify any abnormal behavior.
Best Social Media Hacking Apps
In this case, to determine the best Social network hacking app, the following factors should be considered especially in the area of monitoring and reporting. The following are some of the basic features that one should look for in a software: Real Time Activity Tracking; Content Filtering; Geolocation Tracking; Alert Notifications. In this way, parents can understand which of the best Social media hacking apps available is more effective and therefore select the desired application. Contact for the best social media hack service.
Cloned Account Detection on Facebook
The term cloning in Facebook refers to the act of creating fake accounts which imitates other existing user’s profiles without their permission. These accounts can be misused to deceive the people around them or for the purpose of cheating others or harassing them. In order to identify cloned Facebook accounts, parents should keep an eye on the activities of their children and look for such things as duplicate friend requests, messages from strangers, or posts that do not seem to be from their friends. In turn, by reporting and blocking cloned accounts, parents will be able to prevent potential security threats and violations of their child’s privacy.
Tracking Activity on Any Social Network
It can therefore be difficult for parents to monitor social media usage across the different platforms. Nonetheless, with the appropriate resources and strategies, monitoring your child’s online activities can be less complicated. There are numerous applications that enable parents to monitor activities on different social networks such as Facebook, Instagram, Twitter, Snapchat, and YouTube. Thus, it is possible to say that these tools can help parents understand child’s activity and take proper actions to protect the child from possible threats in this sphere.
The Role of Hackers in Social Media
Trackers are also very effective for parenting control in hackers and social media as they enable tracking and reporting in real time. Such tools help parents to monitor the child’s activities, control the time spent on the Internet, and prevent access to improper content. Thus, parents can successfully control the balance of privacy and safety on SNS and teach their children to behaveresponsibly online through the use of trackers.
For More Info: Monitor Your Kid’s Online Activity When You Are In The Office
Balancing Privacy and Safety on Social Media for Trackers
Maintaining privacy while implementing Social media hacking for parental control is essential for building trust and transparency with your child. Parents should communicate openly with their children about the reasons for monitoring their online activities and establish clear boundaries and expectations. By ensuring safety and responsible usage of Social media hacking tools, parents can create a safe digital environment for their children to explore and thrive.
Conclusion
In conclusion, parental control for Social media hacking is a crucial aspect of ensuring the safety and well-being of children in today's digital world. By using the best Social media hacking tools and methods, parents can monitor their child's online activities, detect potential risks, and promote responsible online behavior. It's essential to strike a balance between privacy and safety while implementing parental control measures and to establish open communication with your child about their online presence. By following best practices and using effective tracking tools, parents can create a safe and secure online environment for their children to navigate and grow.
#social media hack#social media hacking#social media hacker#social media hacks#social media monitoring#social media monitor#social media track#social media tracker#hackerslist
0 notes
