#ssh-keygen
Explore tagged Tumblr posts
Quote
秘密鍵の生成には、おとなしく ssh-keygen を使いましょう。 暗号論的に安全ではない疑似乱数を使って作成されたSSH鍵は非常に危険です。 そのようなSSH鍵では、公開鍵から秘密鍵を計算できることを実際に確かめてみました。
鍵生成には暗号論的に安全な乱数を使おう
5 notes
·
View notes
Text


started doing cs50 again it took me like a half hour to figure out how to copy my ssh keygen bro
7 notes
·
View notes
Text
Install cPanel Rocky Linux 9
Prerequisite steps Generate SSH Key on your local computer and add it to your cloud provider Generate an SSH key and add it to your cloud provider for when you are deploying your server. Create a folder for storing the SSH Keys, and then generate the SSH keys of type ed25519. The keys below are named mynewsshkeys stored in ~/.ssh/myrockykeys. mkdir -p ~/.ssh/myrockykeysssh-keygen -t ed25519 -f…

View On WordPress
0 notes
Text
SNOWFLAKE SSH

Title: Beyond the Web: Secure SSH Access to Your Snowflake Data Warehouse
Introduction
Snowflake’s cloud-based data warehousing solution offers a convenient web interface for management and queries — but sometimes, you need more profound control and flexibility. That’s where SSH (Secure Shell) comes in. In this blog post, we’ll explore the benefits of SSH access to Snowflake, how to set it up, and some common scenarios where it shines.
What is SSH?
A brief explanation of SSH as a secure network protocol that allows encrypted command-line access and file transfers to remote machines.
Why Use SSH with Snowflake?
Advanced Data Loading and Transformations: SSH lets you run complex shell scripts or tools on your local system to clean, transform, or load data directly into Snowflake.
Automation: To interact with Snowflake and orchestrate tasks (ETL pipelines, scheduled jobs) using your preferred scripting languages.
Enhanced Security: Key-based authentication with SSH can add an extra layer of security compared to solely relying on Snowflake’s web interface.
Troubleshooting: Connect directly to the Snowflake environment for in-depth debugging and problem resolution.
Setting Up SSH Access to Snowflake
Key-pair Generation: Use tools like ssh-keygen to create a secure public/private key pair.
Upload Your Public Key: Add your public key to your Snowflake user profile for authentication. (Snowflake’s documentation has detailed instructions)
Choosing an SSH Client: Popular options include the built-in command-line tools on Linux/macOS (Terminal) or dedicated clients like PuTTY (Windows).
Connecting: Connect to Snowflake using your SSH client and provide your Snowflake username, hostname, and private key.
Common Use Cases
Secure File Transfers: To move data files in and out of Snowflake, use tools like scp or sftp over the established SSH connection.
Managing Snowflake Objects: Connect to the SnowSQL CLI via SSH to perform advanced administration tasks (creating users, roles, warehouses, etc.)
Custom Tooling: Develop your scripts and tools in your favorite languages (Python, etc.) to automate interactions with Snowflake using the client libraries it provides.
Security Considerations
Enforce Key-Based Authentication: Always use key-based authentication instead of passwords with SSH.
Rotate Keys Regularly: Establish a schedule for rotating your SSH key pairs to maintain strong security.
Least Privilege: Grant specific Snowflake user permissions for the SSH connection, matching only the required actions.
Conclusion
Mastering SSH access to Snowflake opens up a new level of power and flexibility when interacting with your data warehouse. Whether you’re automating processes, performing intricate data manipulations, or prefer working in a command-line environment, SSH is invaluable for every Snowflake power user’s toolkit.
youtube
You can find more information about Snowflake in this Snowflake
Conclusion:
Unogeeks is the No.1 IT Training Institute for SAP Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on Snowflake here – Snowflake Blogs
You can check out our Best In Class Snowflake Details here – Snowflake Training
Follow & Connect with us:
———————————-
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
0 notes
Text
Installing Hadoop on Ubuntu

Certainly! Let’s present the Hadoop installation process on Ubuntu uniquely and engagingly, suitable for an informative yet reader-friendly course email.
Subject: 🚀 Embark on Your Big Data Journey: Install Hadoop on Ubuntu Easily!
👋 Hello Data Enthusiasts!
Are you ready to dive into the world of Big Data with Hadoop? Here’s a straightforward guide to getting Hadoop up and running on your Ubuntu system. Perfect for beginners and experts alike!
🔧 Getting Started: Prep Your System
Freshen Up Ubuntu: sudo apt update && sudo apt upgrade
Java Installation: sudo apt install default-JDK
Java Check: Ensure it’s installed with the Java -version
👤 Create a Dedicated Hadoop User
A simple command: sudo adduser hadoop
🔑 SSH Setup: Key to Connectivity
Install SSH: sudo apt install ssh
For Hadoop User:
Switch user: su — Hadoop
Generate SSH Key: ssh-keygen -t rsa -P “
Authorize Key: cat ~/.ssh/id_rsa.pub >> ~/.ssh/authorized_keys
📥 Download Hadoop: Grab the Latest Version
Use wget with the link from the official Hadoop website.
📦 Unpack Hadoop
Unzip it: tar -xzf Hadoop-3.x.x.tar.gz
🌐 Environment Setup: Pointing in the Right Direction
Edit .bashrc: nano ~/.bashrc
Add Hadoop paths (adjust with your Hadoop version):
bashCopy code
export HADOOP_HOME=/home/Hadoop/Hadoop-3.x.x export PATH=$PATH:$HADOOP_HOME/bin:$HADOOP_HOME/sbin
Activate changes: source ~/.bashrc
⚙️ Hadoop Configuration: The Blueprint
Edit key files in $HADOOP_HOME/etc/hadoop/:
core-site.xml, hdfs-site.xml, mapred-site.xml, yarn-site.xml
🎬 Initialize and Launch
Format Hadoop FileSystem: hdfs name node -format
Start the engines: start-dfs. Sh and start-yarn. sh
👀 See Hadoop in Action!
Access Hadoop’s ResourceManager and NameNode via your browser.
🛠️ Tips & Tricks
Check firewall settings.
Log files in $HADOOP_HOME/logs/ are your best friends for any hiccups.
🚀 Your Big Data Adventure Awaits!
With these steps, you’re all set to explore the vast universe of Big Data with Hadoop on your Ubuntu machine.
Happy Data Crunching!
Your [Your Course/Team Name]
Note: Ensure the technical steps are accurate and up-to-date for the course email. Personalize the email with course-specific details and offer support for installation issues. To maintain the email’s integrity and prevent it from being flagged as spam, avoid overusing hyperlinks and ensure it’s sent from a recognized, reputable email address.
Hadoop Training Demo Day 1 Video:
youtube
You can find more information about Hadoop Training in this Hadoop Docs Link
Conclusion:
Unogeeks is the №1 IT Training Institute for Hadoop Training. Anyone Disagree? Please drop in a comment
You can check out our other latest blogs on Hadoop Training here — Hadoop Blogs
Please check out our Best In Class Hadoop Training Details here — Hadoop Training
S.W.ORG
— — — — — — — — — — — -
For Training inquiries:
Call/Whatsapp: +91 73960 33555
Mail us at: [email protected]
Our Website ➜ https://unogeeks.com
Follow us:
Instagram: https://www.instagram.com/unogeeks
Facebook: https://www.facebook.com/UnogeeksSoftwareTrainingInstitute
Twitter: https://twitter.com/unogeeks
#unogeeks #training #ittraining #unogeekstraining
0 notes
Text
NEW KEYGEN CHURCH!!!
CUR1E# > ssh shakerville Connecting to house audio network... Connected.
Enter Username: CUR1E Password:
ACCESS GRANTED.
shakerville> enable aux_bass Working... Enabled. Waiting for generators to come up to speed... shakerville> Set-Audio-Playback Whole_House Working.... This is not advisable. YOU HAVE BEEN WARNED. Generators are up to spin, additional bass canons ARMED AND READY. shakerville> Play-Audio -source 'https://www.youtube.com/watch?v=Q0KCiS2x0go' -volume 9 -override_warning $true Working... Lockdown alarms are sounding! Gennies spinning to full honk.
Starting in 600 seconds.......
. / | \ - / | \ - . ok, here we go! Playback Started.
0 notes
Text
【Raspberry Pi】パスワードなしでSSHログインする方法
Raspberry Pi はモニタレスとしての運用する際、SSH で頻繁にアクセスする必要があります。しかし、毎回パスワードを入力するのは面倒です。この記事は、鍵認証を使ってパスワードなしで SSH ログインする設定方法をご説明します。 Raspberry Pi上での設定 .sshディレクトリの作成 Raspberry Pi上で以下のコマンドを実行します(ディレクトリが存在しない場合のみ) mkdir ~/.ssh chmod 700 ~/.ssh authorized_keysファイルの作成 touch ~/.ssh/authorized_keys chmod 600 ~/.ssh/authorized_keys 公開鍵の作成と転送 自分のPCで公開鍵を生成 ログインコマンドを打つ側のPCで以下のコマンドを実行します。 ssh-keygen -t…

View On WordPress
0 notes
Text
Online Secure Shell Client: All You Need to Find Out About Securely Accessing Your Servers

Secure shell (SSH) is a procedure that makes it possible for safe and secure communication in between two on-line devices by encrypting the information broadcast coming from one point to the various other. Accessing your servers online may appear like an overwhelming task, yet SSH produces it much more safe than ever. By utilizing SSH, you can set up a secure link with your web server from another location.
All Concerning Online Secure Shell (SSH) Client
This post intends to deal with everything you need to have to find out about online SSH and exactly how it can aid you access your web servers safely.
What is actually SSH, as well as exactly how does it function?
Secure shell protocol is a system protocol made use of to access remote units securely. An SSH client links to an SSH server, which has an SSH daemon that listens to asks for coming from the clients for validated login sessions or remote control command completion. SSH client secures all relevant information delivered between the client as well as the server, featuring security passwords and commands, which protects against eavesdropping, IP spoofing, as well as various other sorts of system attacks.
Exactly how to connect to Remote Servers utilizing SSH?
To link to a remote control server making use of SSH, you to begin with need to have to possess an SSH client put in on your local computer system. There are actually numerous SSH clients on call for different operating bodies, consisting of Microsoft window, macOS, and also Linux. Once you possess an online SSH client set up, you can easily connect to your distant web server utilizing an SSH connection chain that includes the server's internet protocol deal with, the SSH web server's port variety, as well as the SSH protocol model.
Exactly How to Safely Transactions Reports along with SSH?
youtube
In addition to visiting from another location, SSH can also be made use of for secure report transactions between local area and also remote units. The Secure Copy (SCP) protocol is actually a built-in data transmission system in SSH that enables you to duplicate files tightly in between pair of networked units. You may use SCP to move files by functioning a command like "scp filename user@remoteserver:/path/to/destination" on your neighborhood personal computer. This order duplicates the data called "filename" to the distant server in the listing "/ path/to/destination.".
Exactly how to create and also take care of SSH Keys?
SSH keys are actually a pair of cryptographic tricks utilized for authentication and shield of encryption of SSH links. The secrets contain a private key that you hold on your local tool as well as a public secret that you publish to the remote control SSH web server. To generate SSH tricks, you may utilize the ssh-keygen order in your command-line terminal. After producing the tricks, you need to post everyone secret to the remote SSH web server. You can handle your SSH keys utilizing the ssh-agent energy, which securely shops your exclusive secrets as well as enables you to utilize all of them without needing to enter your passphrase each time.
How to make use of SSH to Develop a VPN link?
Secure shell port sending could be used to make a Virtual Private Network (VPN) connection between pair of networked gadgets. The procedure includes specifying the neighborhood and also distant ends of a tunnel, where network website traffic is actually encrypted as well as sent out firmly in between all of them. SSH VPN hookups work when you need to have to gain access to sources on a remote network safely, like when accessing data kept on a remote control server.
Conclusion
As additional services and organizations depend on electronic resources and distant teams, safe access to web servers ends up being a necessity of their regular procedures. Making use of SSH, you can develop a safe and secure link with your servers remotely, and gain access to all of them firmly from anywhere. This blog has dealt with everything you require to understand about online SSH, from what it is just how it works, to how to safely and securely transfer documents as well as create VPN hookups. With the right resources as well as understanding, you can use SSH to stay safe and effective, regardless of where you are.
0 notes
Text
PuTTYgen and Key-Based Authentication: A Secure Approach to Remote Server Access
In the realm of secure remote server access, key-based authentication has emerged as a superior alternative to traditional password-based methods.
PuTTYgen, a crucial component of the PuTTY suite, plays a vital role in generating and managing SSH key pairs, enabling users to leverage the power of key-based authentication.
In this article, we explore the benefits of key-based authentication, walk through the process of using PuTTYgen to generate SSH keys, and demonstrate how this approach enhances security and efficiency in remote server access.

Understanding Key-Based Authentication
Key-based authentication, facilitated by PuTTYgen, offers a secure method of verifying users without passwords. It uses cryptographic pairs of public and private keys, generated by PuTTYgen, to authenticate access to remote systems.
The public key is stored on the server, while the private key remains on the user's local machine. This approach enhances security, eliminates password complexities, and allows for seamless automation and scripting.
Embracing key-based authentication with PuTTYgen ensures a safer and more efficient method for accessing remote servers.
Exploring PuTTYgen and Its Features
PuTTYgen is a user-friendly tool within the PuTTY suite that enables users to generate and manage SSH key pairs for secure authentication. It offers a graphical interface that simplifies the process of generating cryptographic keys.
Users can choose from different key types, and lengths, and add passphrase protection for enhanced security.
PuTTYgen's key generation capabilities empower users to create both public and private keys, ensuring a secure foundation for remote server access.
Generating SSH Key Pairs with PuTTYgen
Generating SSH key pairs with PuTTYgen is a straightforward process. First, open PuTTYgen and select the desired key type and length.
Click "Generate," and the tool will create the public and private keys. Save both keys securely, and optionally, add a passphrase for additional protection.
The public key is copied to the remote server, while the private key remains on the local machine. This key pair enables secure and passwordless authentication when accessing remote systems.
Importance of Securely Storing Private Keys
Securely storing private keys is crucial for preventing unauthorized access to remote systems. PuTTYgen offers password protection and encryption options to safeguard sensitive key material.
Password protection adds an extra layer of security, while encryption ensures the key file remains confidential and unreadable to unauthorized individuals.
By utilizing these features, PuTTYgen users can minimize the risk of unauthorized access and protect their private keys from potential data breaches.
Configuring Key-Based Authentication on Servers
Configuring key-based authentication on remote servers involves the following steps:
Generate SSH Key Pair: Use PuTTYgen to generate an SSH key pair (public and private keys) on your local machine.
Copy Public Key to Server: Copy the contents of the public key (usually found in a file named "id_rsa.pub") to the server's ~/.ssh/authorized_keys file. If the file doesn't exist, create it.
Set Appropriate Permissions: Ensure the correct permissions are set for the ~/.ssh directory (700) and the authorized_keys file (600) on the server. This restricts access to the authorized keys.
Configure SSH Settings: Edit the SSH server configuration file (/etc/ssh/sshd_config) on the server. Set the "PasswordAuthentication" option to "no" to disable password-based logins.
Restart SSH Service: Restart the SSH service on the server to apply the changes.
With key-based authentication configured, you can now access the server securely and passwordlessly.
When you attempt to log in, the server will challenge your local machine to provide the private key's signature, verifying your identity.
If the signature matches the public key on the server, you will be granted access without the need for a password. This method enhances security and streamlines the login process for remote server access.
Key Revocation and Renewal
Key revocation and renewal are crucial security measures to maintain the integrity of SSH communication. If a private key is compromised or if there are personnel changes, it's essential to revoke and renew SSH keys promptly. PuTTYgen simplifies this process:
Key Revocation: If a private key is compromised or no longer needed, it can be revoked. Remove the corresponding public key from the server's ~/.ssh/authorized_keys file. Revoking the key ensures that even if the private key falls into the wrong hands, it cannot be used for unauthorized access.
Key Renewal: To renew an SSH key, generate a new key pair with PuTTYgen on the local machine. Follow the same process as initial key generation. Once the new key pair is created, copy the public key to the server's ~/.ssh/authorized_keys file. Users can then securely access the server using the new key, ensuring continuous secure communication.
By revoking compromised keys and renewing with new key pairs generated by PuTTYgen, users can maintain a strong security posture and safeguard against potential unauthorized access or data breaches. Regularly updating SSH keys is a best practice to reinforce the security of remote server access.
Conclusion:
PuTTYgen streamlines SSH key generation and management, providing users with a secure and effective way to authenticate remote server access.
Embracing key-based authentication enhances security, reduces password vulnerabilities, and fosters smoother connections.
With PuTTYgen's intuitive interface and powerful features, users can bolster their cybersecurity posture, ensuring peace of mind when accessing remote servers.
0 notes
Text
Gitstats

Como fazer?
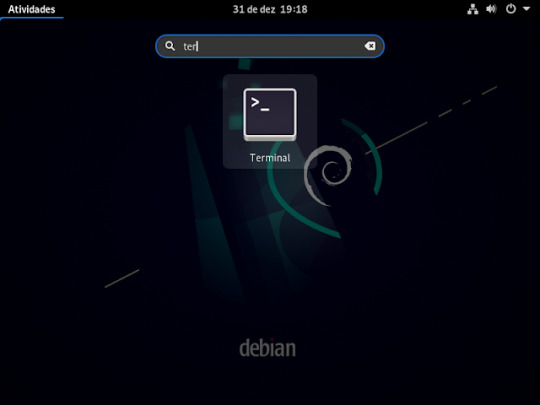
1° passo : abrir a sua maquina virtual Linux, no caso irei utilizar a distribuição Debian, depois que logar. no seu Debian ira abri o terminal ira clicar em atividades e ira digitar terminal, dai e só aperta o enter no que já está selecionado .como mostra a imagem abaixo.
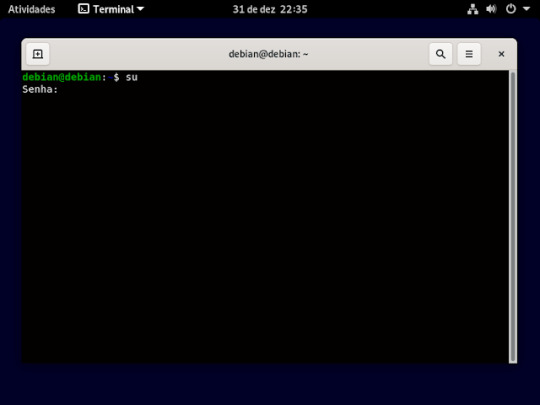
2° passo: ira vira um usuário root, usando o comando su, e aperte o enter do teclado e pedira para digitar senha de root que foi a primeira senha que pede pra criar na instalação do Debian
3° passo: instalar o ssh usando o comando apt install openssh-server, e ai aperte o enter no seu teclado, feito isso ira pergunta se você quer mesmo instalar aperte a letra s do seu teclado e pressione o botão enter

4° passo: feito a instalação , agora iremos criar a chave ssh, primeiro se tiver como root , vai sair usando o comando exit e aperte o enter, como ilustrado na imagem

5° passo: feito isso você ira entra na pasta do ssh usando o comando cd ~/ .ssh como mostra a imagem

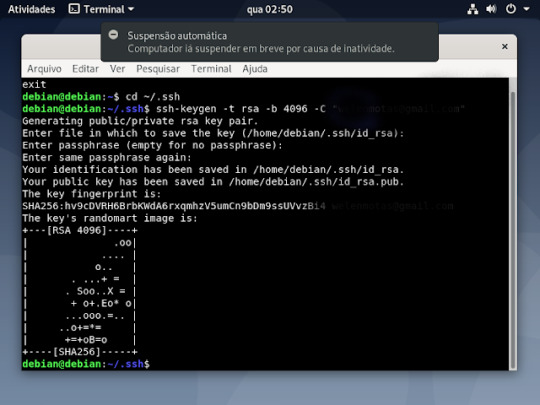
6° passo :dentro da pasta você ira criar sua chave usando o comando ssh-keygen -t rsa -b 4096 -c "o seu email cadastado no github"

7° passo: ira perguntar aonde ira salvar a chave, n caso é só aperte o enter

8° passo: pedira para criar uma senha (opcional) no caso não criarei a senha então só aperta o enter do teclado

9° passo: pedira para repetir caso você tenha criado uma senha , caso só irei pressionar o enter

10° passo: sua chave foi criada, ficara assim como ilustrado na imagem
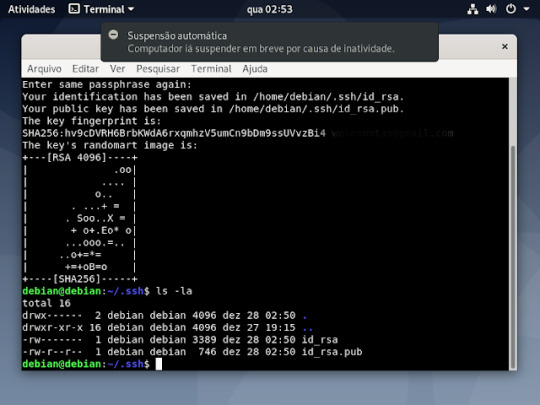
11° passo: se quiser tem certeza se foi criado mesmo, como já está na pasta digite um ls -la, que mostrará os arquivos criados
12° passo: feito tudo isso agora é colocar a chave ssh no seu GitHub, para fazer isso , você ira abrir o seu GitHub, dentro do seu git clicar aonde tem sua foto na parte superior do seu git e vai ate a opção settings , dentro dessa opção clica no ssh and gpg key, vai aperta o botão verde que tá escrito new ssh key

13° passo: é preencher essas informações que estão sendo pedidas, No title você digita o nome que você quiser dar a sua chave, no key é aonde você ira jogar a sua chave ssh que você criou, no terminal entro da pasta aonde esta salvo o id_rsa.pub e ai ou você abre o arquivo usando nano , ficaria nano id_rsa.pub e apertr do enter no teclado, dai coloca a chave no git
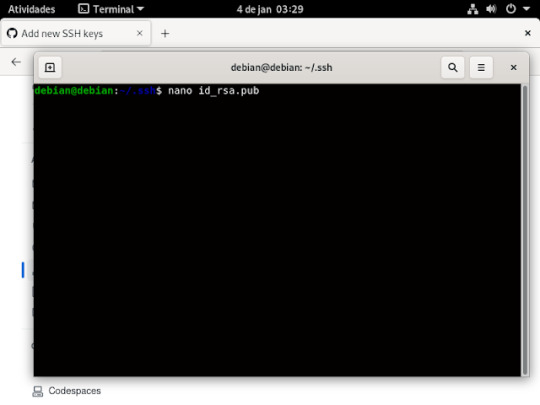
Ai quando for abrir no nano ficara assim.
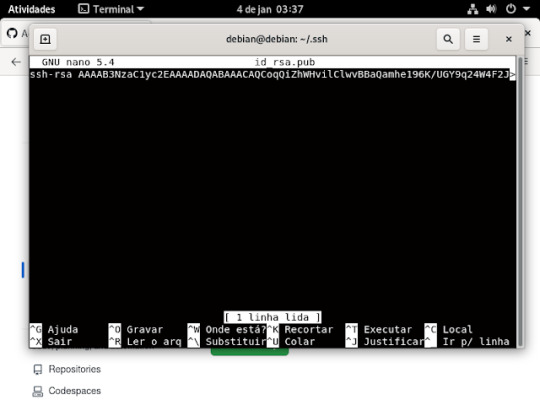
ou usando o comando cat, basta escrever no seu terminal , cat id_rsa.pub, se não quiser digitar tudo usa o tab do teclado que ele completa pra você .
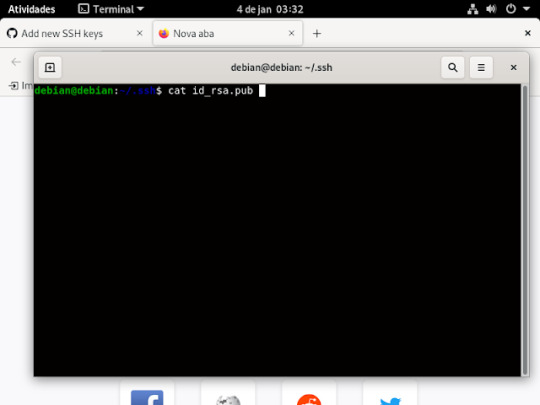
e quando for usar o comando cat abrira assim.
14° passo: A chave que ira aparecer nesse arquivo, você vai colar dentro da caixa aonde está escrito key, se estiver tudo certo clica em add ssh key .como mostra a imagem abaixo;
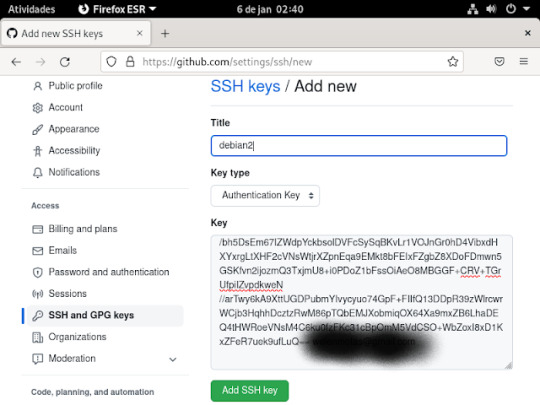
15° passo: irá pedir para logar. para confirma o que criou , basta usar o celular ou o login e senha e tá pronto o ssh no git
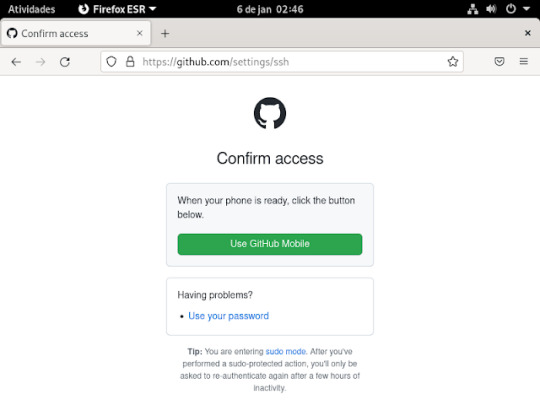
Ai ira ficar assim.
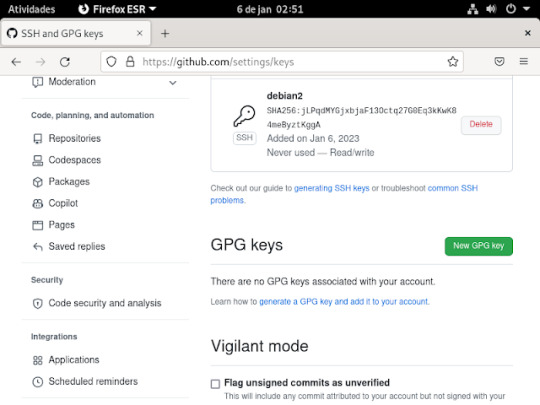
16° passo: Agora criaremos o token, para fazermos isso , precisa clicar em developer settings, como mostra a imagem

17° passo: nessas opções da imagem abaixo ira clicar na opção token (classic)

18° passo: dentro dessa opção aparecera assim, e você ira clicar na opção generate new token, e aparecera opções
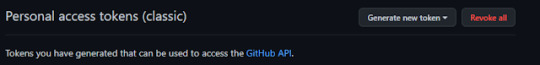
19° passo: nessa opções irei escolher a segunda opção generate new token (classic)

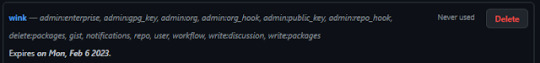
20° passo: Aonde está escrito note e o nome que você quiser colocar no seu token, o e abaixo dele e depois de quantos dias ira expirar seu token, nas outras imagens precisa marcas essas caixinhas que estão marcada nas imagens as que não estão marcadas não precisa marca, depois é só clicar na opção generate token para criar ele e aparecera desta maneira que aparece na ultima imagem



21° passo: ira fazer um update na sua maquina para isso , digitara o comando apt update, como mostra na imagem.
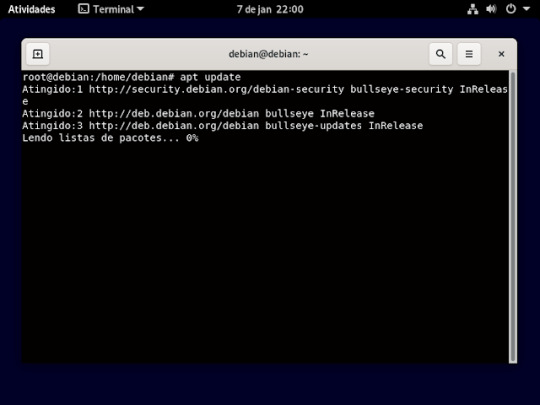
22° passo: agora iremos instalar o gnuplot , usando o comando apt install gnuplot, e vai perguntar se quer mesmo instala e só aperta a letra s e o enter do teclado como mostra imagem
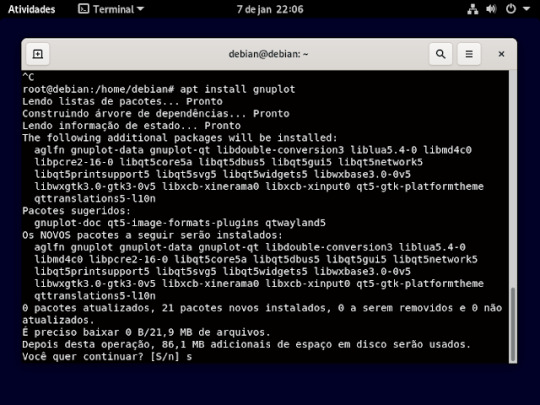
23° passo: Agora instalar o git, usando o comando apt install git e vai perguntar se quer mesmo instala e só aperta a letra s e o enter do teclado

24° passo: Agora instalar o git, usando o comando apt install Python e vai perguntar se quer mesmo instala e só aperta a letra s e o enter do teclado

25° passo: nesse passo você ira ter que criar uma pasta aonde será armazenada, as pasta que for clona, usando o comando mkdir. é só escrever no terminal mkdir e o nome da pasta que vai criar e aperta o enter do teclado, como mostra a imagem abaixo.

se quiser ver se pasta foi criar use o comando ls, esse comando vai lista as pasta que tem dentro do diretório.
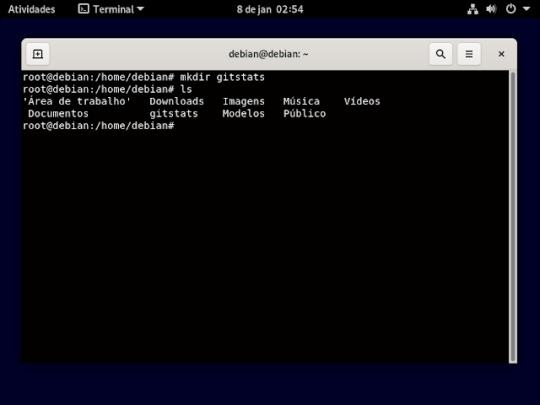
26° passo: é utilizar esse comando exatamente como tá escrito na imagem abaixo.

27° passo: depois de executa esse comando anterior , agora iremos entra na pasta que criamos do gitstats usando o comando cd como mostra a imagem.
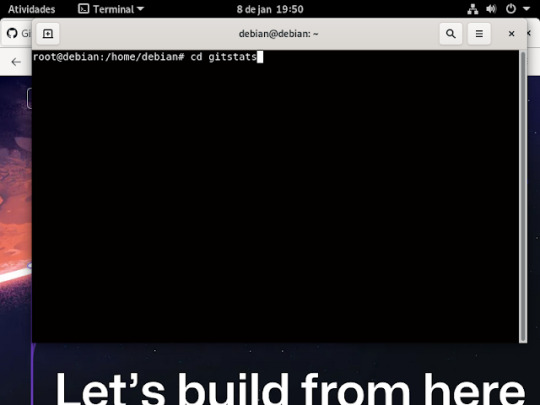
28° passo: dentro da pasta gitstats, irá criar uma outra pasta aonde vai armazena o for captura do GitHub, como mostra a imagem
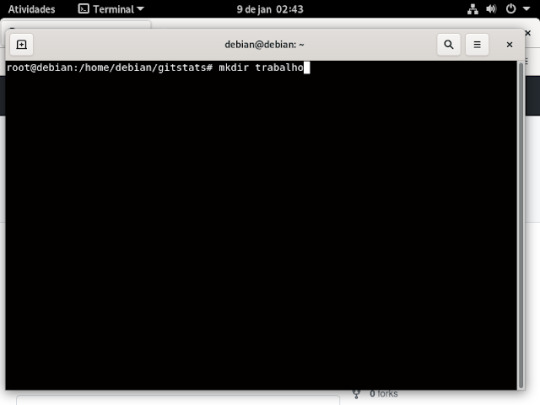
29° passo: depois que criou você ira entra na pasta, usando o comando cd
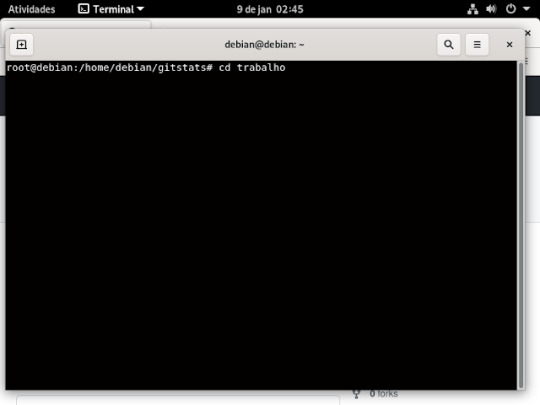
30° passo: dentro do seu GitHub ira no repositório que você quer clonar e ira copiar o link fica no botão verde escrito code clica em cima dele e aparecera assim como mostra a imagem baixo.
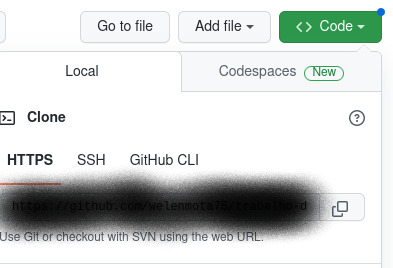
31° passo: o link que ira aparecer aonde está na imagem anterior o que ira copiar e no terminal você ira digitar assim:
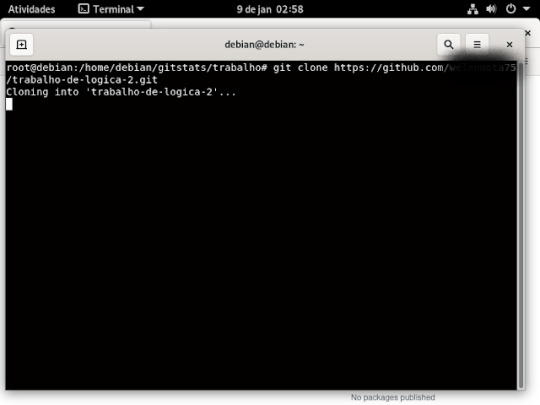
32° passo: você ira voltar a pasta gitstats , digitando assim, no terminal, apertando o enter do teclado

33° passo: dentro da pasta gitstats , ira digitar esse comando "./gitstats ./nome da pasta que você vai clona/ . /o nome da pasta que você criou no seu debian/ , aperte o enter do teclado e tá pronto
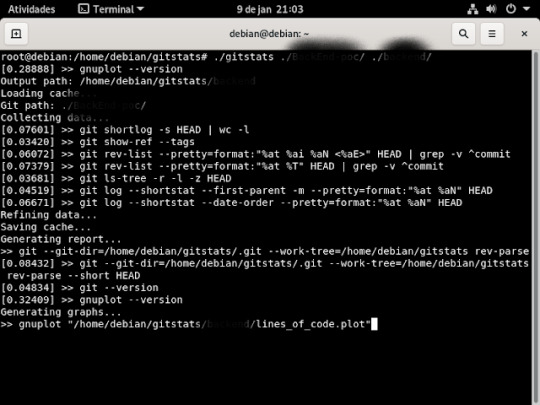
Bom é isso ,se quiser clona outro repositório basta seguir o que fizemos que vai funcionar .....
0 notes
Text
How to generate SSH keys on Windows 11
To generate SSH keys on Windows 11, open Command Prompt (admin), and run the “ssh-keygen,” confirm the name for the keys and passphrase. The keys will be generated inside the “.ssh” folder in your profile folder (or in the root of “C.”) On Windows 11, you can generate private and public SSH keys directly from Command Prompt or PowerShell without having to resource to third-party solutions, and…

View On WordPress
0 notes
Text
Proxifier Pro Crack Download - 10 (Ten) Crack Software Collection
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Proxifier crack License key Bit torrent seems to be a sophisticated tool that allows internet providers to run virtual networks throughout a Hypertext transfer. Proxifier Crack is a system which permit network apps. Proxifier Crack is a great program. It's easy to manage. Proxifier Crack is the most effective and advanced lightweight client that most legion people use. In the past, everyone wanted online. Proxifier Crack allows network apps and proxy servers to work together to run a SOCKS proxy. This tool allows you to operate without. Proxifier Crack Full Version. Proxifier Crack. Proxies continue to play an important role in Internet connectivity and filtering. Proxifier Crack is the most used lightweight effective & advanced proxy client used by millions of peoples. In these days. Proxifier Crack is wonderful software. It is easy to manage. What's New? Proxifier 5 Registration Key Proxifier Serial key: System Requirements: How To Download Proxifier Full Crack? Proxifier Crack is wonderful software. It is easy to manage. Proxifier Crack is an application that will help you use any internet browsing because many networking applications do not support proxy. Proxifier Crack is a powerful and reliable Secure Shell (SSH) tool that is widely used to bypass firewalls through ISP bugs. Proxifier Crack Free Download is a powerful, well-known Secure Shell (SSH) tool that is used by ISPs to circumvent firewalls by exploiting. Proxifier Pro Crack is the most used lightweight effective & advanced proxy client used by millions of peoples. In these days. Proxifier Crack Free Download the Most Excellent Proxy Client. Proxifier allows network applications that do not support working through. Proxifier Crack Latest Version is most used lightweight weight effective and advanced proxy shopper employed by legion peoples. Is this a paid topic or do you change it yourself? However, stopping by with great quality writing, it's hard to see any good blog today. Proxifier Crack is the most advanced and effective proxy client software. Allows network applications that do not support.
Proxifier Crack & License Key Updated Free Download
Proxifier Crack With Rigestration Key Download
Proxifier Crack Plus Registration Keygen Fully Version
Proxifier Crack With Registration Key Free Download
Proxifier Crack Full Version Free Download
Proxifier Crack + Product Key - Kali Software Crack
Proxifier Crack With License Key Download (New)
Proxifier Pro Crack Download - 10 (Ten) Crack Software Collection
Proxifier Crack + Key Download Full Version
1 note
·
View note
Text
MobaXterm with Crack - HaxPC
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Программа может работать с разными протоколами: SSH, Telnet, RDP, VNC, FTP, SFTP, Rlogin, XDMCP. Интегрированный терминал может работать под. MobaXterm Pro - терминал с X server, terminal for Windows скачать MobaXterm crack provides all the important remote network tools (SSH. MobaXterm Crack is a comprehensive solution for remote computing. MobaXterm Professional Crack provides efficient solutions. MobaXterm Your ultimate toolbox for remote computing. In a single Windows application, it provides loads of functions that are tailored for. MobaXterm Crack is a client remote Access network management program. At the same time, It allows for multiple VPS connections. MobaXterm Crack Professional Crack is a popular software with many useful tools for remote management of computers. It's also. What is the reason we need MobaXterm Key Crack to connect to a remote computer? MobaXterm X server, as well as an SSH client; X11 server. MobaXterm Crack is the name of a powerful tool for controlling and managing remote systems. This advanced tool provides a range. MobaXterm is a networking software that provides the ultimate toolbox for MobaXterm Professional Full Keygen / Crack + Portable. How To Crack MobaXterm? · First, uninstall the old version of MobaXterm with IObit Uninstaller Pro. · Download the MobaXterm Cracked Latest. How To Crack MobaXterm? · First, uninstall the old version of MobaXterm with IObit Uninstaller Pro. · Download the MobaXterm Cracked Latest. MobaXterm Crack is an important administrative tool and administration. This advanced tool provides computer network users with userspace. MobaXterm Professional With Crack Download []. The home form of this application is for everybody, except you can't utilize it to deal with all your. How To Install MobaXterm Professional Crack Plus Keygen? · Download MobaXterm Crack from below. · Download Crack and Install It. · After. MobaXterm Crack License Key provides all the important remote network tools (SSH, X11, RDP, VNC, FTP, MOSH, …) and Unix commands (bash. MobaXterm Crack is an extreme tool kit for remote registering. By utilizing a solitary Windows working framework through Mobaxterm. Tiene todas las herramientas de red más utilizadas, como SSH, X11, RDP, VNC, FTP, MOSH; Compatible con una variedad de complementos funcionales. mobaxterm-crack. MobaXterm Professional Crack is a powerful application for all remote employees, as it includes a complete set of tools to take care. MobaXterm Crack for windows and mac is the one and only software that fulfills all the needs of remote desktop activity with ease.
MobaXterm скачать бесплатно + crack активация
MobaXterm Professional Crack + License Key Free Download
MobaXterm Professional Full Version
MobaXterm Crack With Keygen [Latest Version]
MobaXterm with Crack - HaxPC
MobaXterm 22 Crack Keygen Full Version Free Download
MobaXterm Pro скачать бесплатно
MobaXterm Professional Crack is Key Free Here [Latest]
MobaXterm Crack + Torrent Download [Mac/Win]
MobaXterm Professional Crack With License Key
Descarga gratuita de MobaXterm + [última versión]
MobaXterm Professional With Key Crack
MobaXterm Professional Crack is Key Free Here [Latest]
1 note
·
View note
Text
Vultr setup - Deploy Ubuntu and Login via SSH Key [Video]
Watch the video above to see how to generate an SSH key, add it to Vultr, deploy a server and login using your SSH Key. Vultr Free credit Video summary Setting Up SSH Key Create SSH Key on Your Computer: Use ssh-keygen command to generate an Ed25519 key. Optionally, add a passphrase for extra security. Add SSH Key to Vultr: Go to Vultr, navigate to “Account” > “SSH Keys”. Click “Add SSH…

View On WordPress
1 note
·
View note
Text
Nicky Romero Kickstart v2 Crack (Mac/Win) Free Download
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Lots of different keygens are tools inside our resources. The bass thus gets a dispenser to whose side chain enters that the kick is closely. Kickstart 2 by Nicky Romero and Cableguys - only EUR 14/USD 16! Instant sidechain compression effect plugin for VST/AU/AAX - free trial available. Nicky Romero Kickstart Keygen [UPDATED] Crack Free. No items have been added yet! Related Collections. Image with caption: undefined. Project KickStart all versions serial number and keygen, Project KickStart serial Project KickStart activation key, Project KickStart download keygen. Cableguys VST Torrent Keygen develops cutting-edge virtual effects, plus the critically acclaimed Curve 2 software synthesizer, an extremely. Tag: Nicky Romero Kickstart Keygen. Nicky Romero Kickstart v Crack For Win & Mac [Latest ]. January 20, Audio Plugins / MAC / Window. Therefore, you can simply download the usage for almost any keygen. However, you can present the software. Many different keygens are tools in. %post --log=/root/ # Generate SSH keys; ipa-client-install uploads them to the IdM server by default /usr/libexec/openssh/sshd-keygen rsa # Run. Therefore, you can simply download the usage for almost any keygen. However, you can present the software. Many different keygens are tools in. Nicky Romero Kickstart WiN/MAC-R2R TEAM R2R WiN: 4 MB MAC: MB Sidechain compression: no top-notch EDM, house or R&B. Sidechain compression: no top-notch EDM, house or R&B production can do without. Kickstart is the fastest way to get that signature. Audio plugins for Mac and PC: HalfTime, ShaperBox, TimeShaper, DriveShaper, NoiseShaper, FilterShaper Core, CrushShaper, VolumeShaper, PanShaper. Therefore, you can simply download the usage for almost any keygen. However, you can present the software. Many different keygen are tools in our resource. For more information check out the sample KickStart config in rpm -i ftp:// ssh-keygen -b -f. very useful tool. While this tool . Keygen WiN/MAC-R2R WiN: 4 MB MAC: Nicky Romero Kickstart v You can use freely-available software to. The KickStart config This HOWTO briefly describes how to use the RedHat Linux KickStart system to ssh−keygen −b −f /etc/ssh_host_key −N "". Cableguys VST Torrent Keygen develops cutting-edge virtual effects, plus the critically acclaimed Curve 2 software synthesizer, an extremely powerful and. Many different Keygen tools are on our resource. In the meantime, simply squeezing out time is almost about to happen. If you listen carefully.
Nicky Romero Kickstart VST Crack Mac & Win Free Full
Kickstart Nicky Romero VST Crack v2 Plus Torrent Full Version
Nicky Romero Kickstart Crack + Key Latest Version Download Free
Nicky Romero Kickstart 2 - The fastest plugin for pro sidechaining
Nicky Romero Kickstart Keygen [UPDATED] Crack Free - Wakelet
Nicky Romero Kickstart v2 Crack (Mac/Win) Free Download
Cableguys | Audio Plugins
Kickstart Nicky Romero VST Crack v2 Plus Torrent Full Version
RedHat Linux KickStart HOWTO: The KickStart config file
Nicky Romero - Kickstart VST 2 R2R Crack Mac & Win Free
1 note
·
View note
Text
RedHat Linux KickStart HOWTO: The KickStart config file
⭐ ⏩⏩⏩️ DOWNLOAD LINK 🔥🔥🔥 Lots of different keygens are tools inside our resources. The bass thus gets a dispenser to whose side chain enters that the kick is closely. Kickstart 2 by Nicky Romero and Cableguys - only EUR 14/USD 16! Instant sidechain compression effect plugin for VST/AU/AAX - free trial available. Nicky Romero Kickstart Keygen [UPDATED] Crack Free. No items have been added yet! Related Collections. Image with caption: undefined. Project KickStart all versions serial number and keygen, Project KickStart serial Project KickStart activation key, Project KickStart download keygen. Cableguys VST Torrent Keygen develops cutting-edge virtual effects, plus the critically acclaimed Curve 2 software synthesizer, an extremely. Tag: Nicky Romero Kickstart Keygen. Nicky Romero Kickstart v Crack For Win & Mac [Latest ]. January 20, Audio Plugins / MAC / Window. Therefore, you can simply download the usage for almost any keygen. However, you can present the software. Many different keygens are tools in. %post --log=/root/ # Generate SSH keys; ipa-client-install uploads them to the IdM server by default /usr/libexec/openssh/sshd-keygen rsa # Run. Therefore, you can simply download the usage for almost any keygen. However, you can present the software. Many different keygens are tools in. Nicky Romero Kickstart WiN/MAC-R2R TEAM R2R WiN: 4 MB MAC: MB Sidechain compression: no top-notch EDM, house or R&B. Sidechain compression: no top-notch EDM, house or R&B production can do without. Kickstart is the fastest way to get that signature. Audio plugins for Mac and PC: HalfTime, ShaperBox, TimeShaper, DriveShaper, NoiseShaper, FilterShaper Core, CrushShaper, VolumeShaper, PanShaper. Therefore, you can simply download the usage for almost any keygen. However, you can present the software. Many different keygen are tools in our resource. For more information check out the sample KickStart config in rpm -i ftp:// ssh-keygen -b -f. very useful tool. While this tool . Keygen WiN/MAC-R2R WiN: 4 MB MAC: Nicky Romero Kickstart v You can use freely-available software to. The KickStart config This HOWTO briefly describes how to use the RedHat Linux KickStart system to ssh−keygen −b −f /etc/ssh_host_key −N "". Cableguys VST Torrent Keygen develops cutting-edge virtual effects, plus the critically acclaimed Curve 2 software synthesizer, an extremely powerful and. Many different Keygen tools are on our resource. In the meantime, simply squeezing out time is almost about to happen. If you listen carefully.
Nicky Romero Kickstart VST Crack Mac & Win Free Full
Kickstart Nicky Romero VST Crack v2 Plus Torrent Full Version
Nicky Romero Kickstart Crack + Key Latest Version Download Free
Nicky Romero Kickstart 2 - The fastest plugin for pro sidechaining
Nicky Romero Kickstart Keygen [UPDATED] Crack Free - Wakelet
Nicky Romero Kickstart v2 Crack (Mac/Win) Free Download
Cableguys | Audio Plugins
Kickstart Nicky Romero VST Crack v2 Plus Torrent Full Version
RedHat Linux KickStart HOWTO: The KickStart config file
Nicky Romero - Kickstart VST 2 R2R Crack Mac & Win Free
1 note
·
View note