#External Data Provider
Explore tagged Tumblr posts
Text
Top 10 Reasons Why You Need an External Data Provider for your company
In today's fast-paced, data-driven business environment, the ability to access and utilize high-quality, actionable data is essential for staying competitive. However, gathering and managing data internally can be time-consuming, costly, and often overwhelming for many companies. This is where external data providers come into play. By outsourcing data collection and analysis, businesses can unlock a wealth of valuable insights without the burden of in-house management. Whether you're a startup or an established corporation, partnering with an external data provider can help you make smarter decisions, drive growth, and stay ahead of the competition. In this blog, we will explore what an external data provider is, the key reasons why you should consider integrating external data into your business strategy, and how to choose the right provider.

Who is an External Data Provider?
An external data provider is a company or service that specializes in collecting, curating, and supplying data to businesses. These providers access data from a wide variety of sources—ranging from public records, social media, and websites to industry-specific databases—to deliver high-quality, up-to-date information. External data providers not only gather raw data but also clean, process, and verify it to ensure accuracy and relevance. This data is then used by businesses to make informed decisions about market trends, customer behavior, and competitive landscapes.
For example, a business might use an external data provider to track consumer purchasing patterns across different regions, identify emerging market trends, or gather competitive intelligence. By leveraging these insights, companies can optimize their marketing strategies, improve product development, and enhance customer experiences.
What is the Requirement for an External Data Provider?
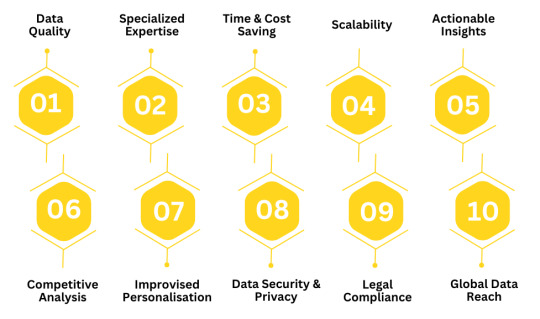
Here are 10 Reasons Why You Need Data from External Sources
1. Access to High-Quality Data
External data providers ensure that you receive the most accurate and trustworthy information available. Equipped with advanced tools and expertise, they are able to clean, validate, and enhance data effectively—capabilities that your internal team may lack. This means your data will truly represent market realities rather than mere assumptions. They gather data from various sources, eliminate inaccuracies, and ensure its reliability. Additionally, they are well-versed in data regulations, helping you navigate potential legal pitfalls. With specialists across different domains, they can extract valuable insights from sources that might otherwise go unnoticed.
2. Cost-Efficiency
External data providers can save organizations both time and cost. They can quickly gather and process data using their specialized tools. This means you won't need to spend money on extra resources like software, hardware, or staff training. They're also up-to-date with any changes in data laws and trends, helping you avoid penalties and adapt faster. By providing valuable insights, they make your decision-making process quicker and more efficient. With their help, your team can save time and money, allowing them to focus more on what they do best.
3. Access to Specialized Expertise
External data providers possess a wealth of expertise in data collection, processing, and analysis. Their teams typically include trained data scientists, analysts, and engineers who specialize in navigating complex datasets across diverse industries. By collaborating with these specialists, businesses can take advantage of advanced methodologies such as machine learning, artificial intelligence, and web scraping. This partnership allows companies to extract insights that would be challenging to achieve with an internal team alone, ultimately leading to more informed and strategic decision-making.
4. Scalability
As your business grows, so do your data needs, and external data providers offer scalable solutions to meet these demands. They can adjust their services, whether you need a small dataset for a project or ongoing data streams for long-term planning, ensuring you have the right amount of data. With advanced tools, these providers efficiently gather and analyze both structured and unstructured data from various sources, making scaling seamless and supporting your organization’s growth.
5. Compliance with Data Regulations
Navigating data privacy laws like GDPR and CCPA can be challenging for businesses. External data providers keep you informed about the latest regulations, ensuring compliance and helping you avoid violations. They cleanse and verify data for accuracy, protecting you from legal issues. By managing complex rules globally, these providers ensure your business remains compliant wherever you operate. Additionally, reliable companies prioritize data security, safeguarding your information from cyber threats and minimizing legal risks associated with data breaches.
6. Time-Saving
Collecting and analyzing data internally can be a lengthy endeavor, often spanning several months to gather, clean, and verify raw data. This process requires significant human resources and expertise, which may strain your team’s capacity. In contrast, external data providers streamline this workflow by delivering ready-to-use data in a fraction of the time. Their expertise and specialized tools enable them to efficiently handle data processing, allowing businesses to make timely, informed decisions. This agility is particularly crucial in fast-paced industries, where the ability to pivot quickly can lead to competitive advantages and better alignment with market trends.
7. Access to Advanced Technology
External data providers invest heavily in the latest data collection and processing technologies, including artificial intelligence, machine learning algorithms, and big data analytics tools. By partnering with these providers, businesses can access cutting-edge technology without incurring the high costs associated with purchasing and maintaining expensive hardware or software. This partnership allows companies to leverage advanced analytical capabilities, enhancing their data-driven strategies and operational efficiencies. As a result, businesses can focus on core competencies while benefiting from innovations that drive growth and improve decision-making.
8. Actionable Insights
Beyond merely supplying raw data, many external data providers offer comprehensive analytical services that transform complex datasets into actionable insights. These insights can inform critical business decisions related to market expansion, product development, and customer segmentation. By utilizing external data to guide strategic initiatives, organizations can ensure their decisions are based on robust evidence rather than guesswork. This data-driven approach not only enhances the quality of decisions but also helps businesses respond proactively to changes in consumer behavior and market dynamics.
9. Competitive Advantage
Access to a diverse array of external data equips businesses with a more nuanced understanding of market trends and competitor behavior. With insights into pricing strategies, customer preferences, and emerging industry trends, organizations can anticipate shifts in the market landscape and adapt their strategies accordingly. This competitive intelligence is invaluable for identifying opportunities for innovation and growth. Moreover, by keeping a pulse on competitors’ actions and market conditions, businesses can maintain a proactive stance that sets them apart from the competition.
10. Faster Time to Market
In many industries, speed is critical to success. Whether launching a new product or responding to evolving market conditions, external data providers can help accelerate processes by delivering data quickly and efficiently. Their ability to provide timely insights enables businesses to make informed decisions rapidly, which reduces the time it takes to bring products and services to market. This faster access to data not only enhances operational efficiency but also allows companies to capitalize on fleeting opportunities, ensuring they remain relevant and competitive.
How to Choose the Right External Data Provider?
Selecting the right external data provider is crucial to maximizing the benefits of external data. Here are some key factors to consider when choosing a provider:
Reputation and Experience: Look for a provider with a proven track record in your industry. Check for case studies, reviews, and testimonials to assess their reliability and expertise.
Data Quality: Ensure that the provider has strong data validation processes in place to deliver clean, accurate, and relevant data. Ask for sample datasets to evaluate the quality before committing to a partnership.
Compliance: Make sure the provider complies with all relevant data protection regulations, such as GDPR and CCPA. This is critical for avoiding legal issues down the line.
Technology and Tools: Assess the provider’s technology stack to ensure they are using the latest tools and techniques for data collection and analysis.
Pricing and Flexibility: Choose a provider that offers flexible pricing models that align with your budget and data needs. Many providers offer scalable solutions that can grow with your business.
Customer Support and Communication: Effective communication is key to a successful partnership. Choose a provider that offers strong customer support and is responsive to your needs.
Conclusion
Having an external data provider for your business can significantly accelerate growth. It allows you to access valuable insights quickly and conveniently, helping you adhere to regulations, safeguard your data, and make smarter decisions. We've outlined nine reasons, but depending on your business, the benefits could extend even further.
If you're debating whether investing in a data provider is worthwhile, remember that having access to the right insights can give your business a competitive edge in today's fast-paced, data-driven world. By partnering with TagX, you’ll be equipped with the tools and expertise needed to stay ahead of market changes and make informed decisions that drive success.
Ready to elevate your business with the power of data? Take the first step—Get Started!
Original Source, https://www.tagxdata.com/top-10-reasons-why-you-need-an-external-data-provider-for-your-company
0 notes
Text
Drowning in the data to unlock hidden insights while saving time and cost? Here are the 9 reasons why you are partnering with an external data provider to boost your business.
For More Information:-
0 notes
Text

I actually hate the evolution of technology bc now there’s shit like this. My network adapter broke so I bought a new one, and have zero way to install and use it unless I have another working computer w internet and my own usb on hand to install the drivers from the website. Rather than them just including a cd w the drivers like most products used to do
#pic#why is internet connection required to install the device that gives me internet connection. are u fucking insane#this genuinely pissed me off i paid 50 bucks for this shit at least include the damn drivers#and even better? the link provided is broken. it takes two seconds to search it up but come the fuck on man#physical media is actually so important and this is why.#like u do realize all data can’t be only digital. the second a site goes down everyone loses access#and i don’t give a shit that most computers don’t have cd drives now. i have an external drive#at least give me the option to use a cd bc the whole point is that u can download it without internet. like am i insane#my adapter is half broke so after an hr I got it downloaded but I shouldn’t have to do all that
0 notes
Text











I am not excited about Harris as a candidate, but I will be voting for her in this upcoming election. This is why→
(full transcript under the cut)
I AM VOTING AGAINST THIS
“Transgender ideology” to be classified as pornography & excluded from First Amendment protection. Authors who produce & distribute it threatened with prison. Educators & public librarians who share it classed as registered sex offenders. communications & technology firms that facilitate its spread shuttered. -Project 2025, page 5
Delete the terms sexual orientation, gender identity, diversity, equity, & inclusion, gender equality, abortion, reproductive health, reproductive rights, out of every federal rule, contract, grant, regulation, & piece of legislation that exist. -Project 2025 page 5
I AM VOTING AGAINST THIS
Victimization should not be a basis for an immigration benefit. -Project 2025, page 141
Increase all fees for asylum applications, limit the availability of fee waivers. -Project 2025, page 146
Mandatory appropriation for border wall system infrastructure. -Project 2025, page 147
Deny loan access to those who are not U.S. citizens or lawful permanent residents & deny loan access to students at schools that provide in-state tuition to illegal aliens. -Project 2025, page 167
Ensure that only U.S. citizens & lawful permanent residents utilize or occupy federally subsidized housing. -Project 2025, page 167
I AM VOTING AGAINST THIS
Encourage intelligence agencies not to waste effort collecting surveillance data when they can buy it from private sector facial recognition companies. -Project 2025, page 206
Defund the Corporation for Public Broadcast, specifically NPR & PBS educational programs like Sesame Street. -Project 2025, pages 246-247
The USDA will not be able to place environmental issues ahead of agricultural production. Reconsider the Food Stamps program. -Project 2025, page 290
Labeling regulations that unnecessarily delay the manufacture & sale of baby formula should be re-evaluated. -Project 2025, page 302
I AM VOTING AGAINST THIS
Eliminate the Community Eligibility Program which allows school districts with high rates of poverty to offer meals to all students without having to qualify each student individually. No longer provide meals to students during the summer unless students are taking summer-school classes. -Project 2025, page 303
No public education employee shall use a pronoun in addressing a student that is different from that student’s biological sex without written permission of the parents or guardians. -Project 2025 page 346
Delete reporting on which educational institutions claim religious exemption from Title IX. -Project 2025 page 357
I AM VOTING AGAINST THIS
Gut the Office for Civil Rights’ power to prosecute any kind of discrimination in public schools. -Project 2025, page 357
Eliminate the Office of Fossil Energy & Carbon Management -Project 2025 page 377
Eliminate the stand-alone Office of Environmental Justice & External Civil Rights -Project 2025, page 421
Restructure the Office of International & Tribal Affairs into the American Indian Environmental Office -Project 2025, page 421
Eliminate the Office of Public Engagement & Environmental Education -Project 2025, page 421
Pause all action of the Environmental Protection Agency for review. -Project 2025, page 422
I AM VOTING AGAINST THIS
Center for Disease Control stripped of the ability to suggest that schools embrace masking or vaccination strategies. -Project 2025, page 454
All states will be required to submit detailed information about pregnancies, abortions & miscarriages to a federal database. -Project 2025, page 455
The medication Mifepristone, a life-saving drug used to stop deadly postpartum hemorrhages that’s also used in chemical abortions, will be banned. -Project 2025, pages 458-459
Artificial intelligence should be used to determine what is suitable treatment for those currently covered by Medicare. -Project 2025, page 463
I AM VOTING AGAINST THIS
Repeal the Inflation Reduction Act, which implements government price controls for prescription drugs. -Project 2025, page 465
Funding for abortion travel prohibited under the Hyde Amendment. -Project 2025, page 471
End taxpayer funding of Planned Parenthood. -Project 2025, page 471
Withdraw Medicaid funds for states that require abortion insurance. -Project 2025, page 472
Hospitals will no longer be willing to perform emergency abortions, even to save the life of the mother. -Project 2025, page 473
I AM VOTING AGAINST THIS
Rescind the Department of Health & Human Services' ability to impose a moratorium on rental evictions during COVID. -Project 2025, page 492
Rescind large portions of The Endangered Species Act & The Migratory Bird Treaty Act, reinstate Trump’s plan for opening the National Petroleum Reserve of Alaska to leasing and development. -Project 2025, page 524
Review & downsize national monuments. -Project 2025, page 532
End the Endangered Species Act’s ability to prevent economic development & de-list many currently endangered species. -Project 2025, pages 533-534
I AM VOTING AGAINST THIS
Make it harder for workers to unionize & easier for employers to retaliate against whistleblowers & organizers. -Project 2025, pages 601-602
TikTok classified as a national security concern & made non-operational. -Project 2025, page 674
Break up National Oceanic & Atmospheric Administration, including National Weather Service & National Marine Fisheries Service. -Project 2025, page 674
Downsize the Office of Oceanic & Atmospheric Research; disband its climate-change research work. -Project 2025 page 676
AND SO MUCH MORE.
The full text of Project 2025 is available at static.project2025.org/2025_MandateForLeadership_FULL.pdf I am very grateful to stopproject2025comic.org which produced a series of very readable comics to help explain many sections of Project 2025. Some of the language in this post is taken directly from their transcripts. (You can read many of their comics here on tumblr @stopproject2025comic) Please vote against Project 2025. Our tattered democracy, healthcare, clean air & water, workers rights, reproductive rights, civil rights, intellectual freedom and more are at stake.
2K notes
·
View notes
Text
.
#tag talk#if I can make it through the next two weeks I'll be alright. but damn if it isn't gonna be rough#court date next week and dr appointment the week after. but then I'll be back on track with changing my name and then getting hrt#big changes. but changes I need. changes I tried to start back in February.#I try to have yearly goals. big overarching themes and shit. 2022 was just getting away from my patents and accepting being trans#and then it ended up being a year for processing old trauma. which uhh. really culminated in the February attempt to end all that shit#but February was the start of the new year for me. the start of getting all that personal work externalized. being out and unapologetic#the move this summer has thrown things a little out of shape but I'm working to get it back on the rails#if I can get things sorted by the end of this year then next year is the start of forever for me.#it really will be a “first day of the rest of our lives” vibe. new name. finally getting the meds I need. idk exactly how hrt will go though#I need to do independent research to see if I need to go through health provider or if I can find a clinic independently#been meaning to do that for a hot while but I have been so overwhelmed with other stuff I haven't had the energy.#but like. looking back it hasn't been bad. I was afraid I would lose this year to the move. but that's adhd time blindness speaking#even if it takes four months to move and mentally recover that leaves eight still. that's still a lot of time. I have time to work with#every day I'm still alive is a day I have available to get done the things I want to in order to live happily.#sure I'm damaged as fuck. but that doesn't mean I can't get some good work done. I can make friends and have fun and help people#idk. I'm still in a melancholy state from the heavy dissociation I experienced on edibles. I think I might not do that again#losing control of my head isn't great because my default is suicidal and depressed which isn't super pogchamp of me#I'm gonna do it again once more just to have a second experience because a single data point isn't good data so I want two.#but I don't expect to want to do it anymore. I wonder if the high amounts of stress and anticipation I'm experiencing right now affect it#of course it would. prior mental state of going to affect the trip. that's kinda obvious I guess. maybe I try it again in two weeks#anyway. life keeps going and there is no expectation to fall behind on. falling behind means there's an acceptable pace. which is false#well. that's not true. capitalism and all that. there's a minimum pace for somebody. but that's where community comes in to help I guess#I'm rambling now. bye I'm gonna go take a shower and be really sad about having a dick and balls#it's tragic cause they're really nice dick and balls too. Just not for me. I wanna be a cool guy without even a single ball to his name#is that too much to ask? I just wanna be a man who's a woman who's a man but in a different way than the first time he was.#also. I'm tired of straight guys on dating apps hitting me up. like bro I know you're just gonna want to view me as a woman. no deal#bro is gonna have to be at least a little gay. cause I am not gonna swing like that. better be at least a little bi#some dude's bio was like “let me love the woman inside of you” and like. no thanks please go obsess over femininity somewhere else#straight guys who include nonbinary in their profile because they really just see it as woman 2: gender boogaloo ☠️
0 notes
Note
Zoomer here, and I do indeed have questions about computers- how do filesystems work, and why should we care (I know we should, but I'm not exactly sure why)?
So why should we care?
You need to know where your own files are.
I've got a file on a flash drive that's been handed to me, or an archival data CD/DVD/Bluray, or maybe it's a big heavy USB external hard drive and I need to make a copy of it on my local machine.
Do I know how to navigate to that portable media device within a file browser?
Where will I put that data on my permanent media (e.i. my laptop's hard drive)?
How will I be able to reliably find it again?
We'll cover more of the Why and How, but this will take some time, and a few addendum posts because I'm actively hitting the character limit and I've rewritten this like 3 times.
Let's start with file structure
Files live on drives: big heavy spinning rust hard drives, solid state m.2 drives, USB flash drives, network drives, etc. Think of a drive like a filing cabinet in an office.
You open the drawer, it's full of folders. Maybe some folders have other folders inside of them. The folders have a little tab with a name on it showing what's supposed to be in them. You look inside the folders, there are files. Pieces of paper. Documents you wrote. Photographs. Copies of pages from a book. Maybe even the instruction booklet that came with your dishwasher.
We have all of that here, but virtualized! Here's a helpful tree structure that Windows provides to navigate through all of that. In the case of Windows, it's called Explorer. On OSX MacOS, the equivalent is called Finder.
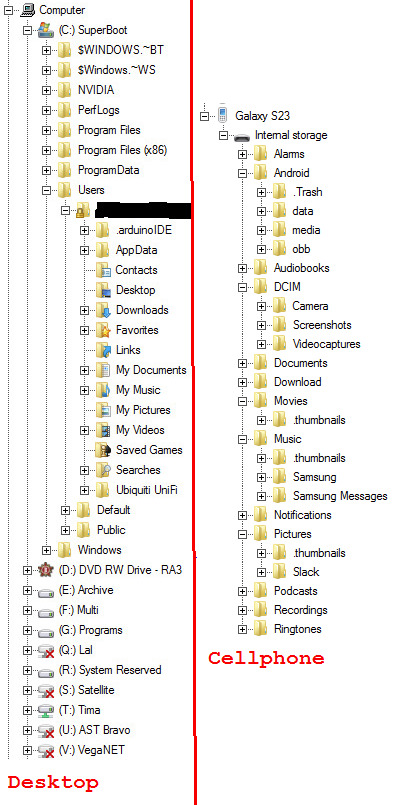
I don't have to know where exactly everything is, but I have a good idea where thing *should* based on how I organize them. Even things that don't always expose the file structure to you have one (like my cellphone on the right). I regularly manually copy my files off of my cellphone by going to the Camera folder so I can sift through them on a much bigger screen and find the best ones to share. There are other reasons I prefer to do it that way, but we won't go into that here. Some people prefer to drag and drop, but that doesn't always work the same between operating systems. I prefer cut and paste.
Standby for Part 2!
2K notes
·
View notes
Text
Heads up folks, NicoNicoDouga is currently down due to a large scale cyberattack
The attack happened on the 8th and the site is still down in terms of video streaming. Apparently there were reports of Ransomware being used during the attack.
The site is still “down” but the blog part is back up but from the report, videos and content posted are ok so do not fret. The site is still down as of this post (save for the blog) and it seems they are working their hardest to fix it and do damage control.
Here is a rough translation of their most recent post:
Report and apology regarding cyberattack on our services
As announced in Niconico Info dated June 8th, 2024, Dwango Co., Ltd. (Headquarters: Chuo-ku, Tokyo; President and CEO: Takeshi Natsuno) has been unable to use the entire Niconico service operated by our company since the early morning of June 8th. It has been confirmed that this outage was caused by a large-scale cyberattack, including ransomware, and we are currently temporarily suspending use of the service and conducting an investigation and response to fully grasp the extent of the damage and restore it.
After confirming the cyberattack, we immediately took emergency measures such as shutting down the relevant servers, and have set up a task force to fully clarify the damage, determine the cause, and restore the system. We would like to report the findings of the investigation to date and future responses as follows.
We sincerely apologize to our users and related parties for the great inconvenience and concern caused.
Response history>
Around 3:30 a.m. on June 8, a malfunction occurred that prevented all of our web services, including our "Nico Nico" and "N Preparatory School" services, from working properly. After an investigation, it was confirmed that the malfunction was caused by a cyber attack, including ransomware, at around 8 a.m. on the same day. A task force was set up on the same day, and in order to prevent the damage from spreading, we immediately cut off communication between servers in the data center provided by our group companies and shut down the servers, temporarily suspending the provision of our web services. In addition, since it was discovered that the attack had also extended to our internal network, we suspended the use of some of our internal business systems and prohibited access to the internal network.
As of June 14, we are currently investigating the extent of the damage and formulating recovery procedures, aiming for a gradual recovery.
June 8, 2024
We have begun an investigation into the malfunction that prevented all of our "Nico Nico" services from working properly and the failure of some of our internal systems.
We have confirmed that the cause of the failure was encryption by ransomware. "Nico Nico" services in general and some internal business systems suspended and servers were shut down
A task force was established
First report "Regarding the situation in which Nico Nico services are unavailable" was announced
June 9, 2024
Contacted the police and consulted with external specialist agencies
Kabukiza office was closed
KADOKAWA announced "Regarding the occurrence of failures on multiple KADOKAWA Group websites"
June 10, 2024
Reported to the Personal Information Protection Commission (first report)
Second report "Regarding the situation in which Nico Nico services are unavailable" was announced
June 12, 2024
Reported the occurrence of the failure to the Kanto Regional Financial Bureau (Financial Services Agency)
June 14, 2024
This announcement
This cyber attack by a third party was repeated even after it was discovered, and even after a server in the private cloud was shut down remotely, the third party was observed to be remotely starting the server and spreading the infection. Therefore, the power cables and communication cables of the servers were physically disconnected and blocked. As a result, all servers installed in the data centers provided by the group companies became unusable. In addition, to prevent further spread of infection, our employees are prohibited from coming to the Kabukiza office in principle, and our internal network and internal business systems have also been shut down.
In addition to public cloud services, Niconico uses private cloud services built in data centers provided by KADOKAWA Group companies, to which our company belongs. One of these, a data center of a group company, was hit by a cyber attack, including ransomware, and a significant number of virtual machines were encrypted and became unavailable. As a result, the systems of all of our web services, including Niconico, were shut down.
This cyber attack by a third party was repeated even after it was discovered, and even after a server in the private cloud was shut down remotely, the third party was observed to be remotely starting the server and spreading the infection. Therefore, the power cables and communication cables of the servers were physically disconnected and blocked. As a result, all servers installed in the data centers provided by the group companies became unusable. In addition, to prevent further spread of infection, our employees are prohibited from coming to the Kabukiza office in principle, and our internal network and internal business systems have also been shut down.
The Niconico Video system, posted video data, and video distribution system were operated on the public cloud, so they were not affected. Niconico Live Broadcasting did not suffer any damage as the system itself was run on a public cloud, but the system that controls Niconico Live Broadcasting's video distribution is run on a private cloud of a group company, so it is possible that past time-shifted footage, etc. may not be available. We are also gradually checking the status of systems other than Niconico Douga and Niconico Live Broadcasting.
■ Services currently suspended
Niconico Family services such as Niconico Video, Niconico Live Broadcast, and Niconico Channel
Niconico account login on external services
Music monetization services
Dwango Ticket
Some functions of Dwango JP Store
N Preparatory School *Restored for students of N High School and S High School
Sending gifts for various projects
■ About Niconico-related programs
Until the end of July, official Niconico live broadcasts and channel live broadcasts using Niconico Live Broadcast and Niconico Channel will be suspended.
Considering that program production requires a preparation period and that Niconico Live Broadcast and Niconico Channel are monthly subscription services, we have decided to suspend live broadcasts on Niconico Live Broadcast until the end of July. Depending on the program, the broadcast may be postponed or broadcast on other services.
The date of resumption of Niconico services, including Niconico Live Broadcast and Niconico Channel, is currently undecided.
Niconico Channel Plus allows viewing of free content without logging in. Paid content viewing and commenting are not available.
■ About the new version "Nico Nico Douga (Re: Kari)" (read: nikoniko douga rikari)
While "Nico Nico" is suspended, as the first step, we will release a new version of "Nico Nico Douga (Re: Kari)" at 3:00 p.m. on June 14, 2024. Our development team voluntarily created this site in just three days, and it is a video community site with only basic functions such as video viewing and commenting, just like the early days of Niconico (2006). In consideration of the load on the service, only a selected portion of the videos posted on Niconico Video is available for viewing. The lineup is mainly popular videos from 2007, and you can watch them for free without an account.
■About the Niconico Manga app
We have already confirmed that many systems were not affected, and we are considering resuming the service with a reduced-function version that allows basic functions such as reading manga, commenting, and adding to favorites. We aim to restore the service by June 2024.
If any new facts become known in the future, we will report them on Niconico Info, Official X, our company website, etc. as they become available. We appreciate your understanding and cooperation.
Added 6/10]
Thank you for your continued patronage. This is the Niconico management team.
Due to the effects of a large-scale cyber attack, Niconico has been unavailable since the early morning of June 8th.
We sincerely apologize for the inconvenience.
As of 6:00 p.m. on June 10th, we are working to rebuild the entire Niconico system without being affected by the cyber attack, in parallel with an investigation to grasp the full extent of the damage.
We have received many inquiries from you, such as "Will premium membership fees and paid channel membership fees be charged during the service suspension period?" and "What will happen to the time shift deadline for live broadcasts?". We are currently in the process of investigating the impact, so we cannot answer your questions, but we will respond sincerely, so please wait for further information.
Our executive officer Shigetaka Kurita and CTO Keiichi Suzuki are scheduled to explain the expected time until recovery and the information learned from the investigation up to that point this week.
We will inform you again about this as soon as we are ready.
■ Services currently suspended
Niconico Family Services such as Niconico Video, Niconico Live Broadcast, Niconico Channel, etc.
Niconico Account Login on External Services
[Added 2024/06/10 18:00]
Gifts for various projects (due to the suspension of related systems)
■ Programs scheduled to be canceled/postponed (as of June 10)
Programs from June 10 to June 16
■ Current situation
In parallel with the recovery work, we are investigating the route of the attack and the possibility of information leakage.
No credit card information has been leaked (Niconico does not store credit card information on its own servers).
The official program "Monthly Niconico Info" scheduled for June 11 at 20:00 will be broadcast on YouTube and X at a reduced scale. During this program, we will verbally explain the current situation in an easy-to-understand manner. (※There is no prospect of providing additional information, such as detailed recovery dates, during this program.)
"Monthly Niconico Info" can be viewed at the following URL. YouTube → https://www.youtube.com/@niconico_news X (formerly Twitter) → https://x.com/nico_nico_info
The latest information will be posted on Niconico Info and the official X (formerly Twitter).
We deeply apologize for the inconvenience caused to users and content providers who regularly enjoy our videos and live broadcasts. We ask for your understanding and cooperation until the issue is resolved.
Published on 6/8]
Thank you for your continued patronage. This is the Niconico management team.
Currently, Niconico is under a large-scale cyber attack, and in order to minimize the impact, we have temporarily suspended our services.
We are accelerating our investigation and taking measures, but we cannot begin recovery until we are confident that we have completely eliminated the effects of the cyber attack and our safety has been confirmed. We do not expect to be able to restore services at least this weekend.
We sincerely apologize for the inconvenience.
We will inform you of the latest situation again on Monday (June 10, 2024).
■ Suspended services
Niconico family services such as Niconico Video, Niconico Live Broadcast, and Niconico Channel
Niconico account login on external services
■ Current situation
In parallel with the recovery work, we are investigating the route of the attack and the possibility of information leakage.
No credit card information has been confirmed to have been leaked (Niconico does not store credit card information on its own servers).
Future information will be announced on Niconico Info and Official X (formerly Twitter) as it becomes available.
We deeply apologize to all users who were looking forward to the video posts and live broadcasts scheduled for this weekend. We ask for your understanding and cooperation until the response is complete.
#news#internet#translation#nico nico douga#cyber attack#cyber security#hatsune miku#niconico#japan#please spread#please reblog this
100 notes
·
View notes
Text
9 Reasons to Partner with External Data Providers to Fuel Growth

In today's data-driven business landscape, organizations are constantly seeking ways to gain a competitive edge. One effective strategy that has gained prominence is partnering with external data providers to access valuable insights and fuel growth. By tapping into external data sources, businesses can make more informed decisions, enhance their operations, and ultimately drive success. Here are nine compelling reasons why partnering with external data providers can be a game-changer for your organization:
Expanded Data Universe: External data providers offer access to vast and diverse datasets that extend beyond the scope of your internal resources. This expanded data universe allows businesses to gain a comprehensive understanding of market trends, consumer behavior, and industry dynamics, enabling more informed strategic planning.
Enhanced Accuracy and Reliability: External data providers specialize in curating high-quality, accurate, and up-to-date information. Relying solely on internal data may lead to gaps or outdated insights. By partnering with external providers, organizations can enhance the accuracy and reliability of their data, leading to more trustworthy decision-making processes.
Real-time Insights: The business landscape is dynamic, and real-time insights are crucial for staying ahead of the competition. External data providers deliver information promptly, allowing organizations to respond swiftly to market changes, customer preferences, and emerging trends.
Cost-Efficiency: Acquiring and maintaining an extensive internal database can be costly and time-consuming. External data providers offer a cost-efficient alternative by providing access to diverse datasets without the need for significant infrastructure investment. This allows businesses to allocate resources more strategically and focus on core competencies.
Improved Customer Understanding: Understanding your customers is key to tailoring products and services to their needs. External data providers offer valuable demographic, psychographic, and behavioral insights, helping organizations create targeted marketing campaigns, enhance customer experiences, and foster stronger relationships with their audience.
Mitigation of Risks: External data sources can be instrumental in risk management. By tapping into external datasets related to market trends, economic indicators, and geopolitical developments, businesses can identify potential risks and proactively devise strategies to mitigate them, ensuring a more resilient and adaptable operation.
Competitive Intelligence: To stay competitive, organizations need to be aware of what their rivals are doing. External data providers offer valuable competitive intelligence, allowing businesses to benchmark their performance, identify industry trends, and discover opportunities to outpace competitors.
Innovation Catalyst: External data can be a catalyst for innovation. By combining internal data with external insights, organizations can uncover new patterns, correlations, and opportunities that may not be apparent when analyzing internal datasets alone. This can spark innovation and drive the development of new products or services.
Scalability: External data providers offer scalable solutions that can grow with your business. As your data needs evolve, these providers can accommodate increased demand, ensuring that your organization has the necessary resources to support its growth initiatives without the burden of managing and updating extensive internal databases.
In conclusion, partnering with external data providers is a strategic move that empowers organizations to harness the full potential of data for growth. The diverse and real-time insights, coupled with cost-efficiency and scalability, make external data providers indispensable partners in the modern business landscape. By embracing this collaboration, businesses can make more informed decisions, gain a competitive edge, and navigate the complexities of the evolving marketplace with confidence.
0 notes
Text
Pinging and Tapping
In the world of the Murderbot Diaries, communication is often conducted via comm and feed. Generally, comm is used when internal network is not available, or when one is trying to communicate across space, and feed is used when people are on the same network and allow each other access.
We also often see “pings” and “taps” as a way of quick communication.
Generally, pings are used for comm communications, and taps are used for feed communications, but there seem to be different purposes. Here are what we can gather from the story, and also from real life examples.
[Pings]
Purpose in the MB world:
Pings are typically used for signalling, checking connectivity, and getting responses from other systems or units. They act like a way to see if the other side is present and ready to communicate or respond.
Purpose in Real Life:
Network Connectivity: In computer networks, a "ping" is a diagnostic tool used to test the reachability of a host on an Internet Protocol (IP) network. It measures the round-trip time for messages sent from the originating host to a destination computer.
Usage in the MB World:
Status Checks: Used to check if systems, such as satellites, drones, or transports, are active and responsive. For example, pinging a satellite to see if it responds.
Communication Initiation: Used to start communication with other systems, often to establish a connection or share data. For instance, pinging a transport to offer media files in exchange for a ride.
Detection: Used by systems to detect the presence of specific units, like SecUnits, without direct contact.
Usage in Real Life:
ICMP Echo Request/Reply: The ping command sends an ICMP (Internet Control Message Protocol) Echo Request message to the target host and waits for an ICMP Echo Reply.
Network Troubleshooting: Used to determine if a particular host is reachable and to measure the latency between the source and destination.
[Taps]
Purpose in the MB World:
Taps are used more for internal communication within the network or feed. They serve as a means to acknowledge, signal actions, or provide private communication without verbal interaction.
Purpose in Real Life:
Internal Communication: In many systems, "taps" or similar mechanisms are used to signal and communicate internally within a network or system.
Usage in the MB World:
Acknowledgments: Used to acknowledge received messages or instructions. For instance, tapping back an acknowledgment to confirm receipt of instructions.
Private Communication: Used to send private or secure messages within the feed, often to communicate specific commands or information discreetly. For example, tapping the feed to communicate privately with another character without others listening in.
Control Signals: Used to signal or control actions within the feed, like tapping to instruct a character to fall back or take specific actions.
Usage in Real Life:
Signalling Mechanisms: Within computer systems, taps can be analogous to various signalling mechanisms like inter-process communication (IPC), which includes methods such as semaphores, shared memory, and message queues.
Acknowledgments and Control Signals: In networking, control signals and acknowledgments are crucial for managing data flow and ensuring reliable communication. For example, TCP (Transmission Control Protocol) uses acknowledgments to confirm the receipt of data packets.
Network Taps: In the context of network security, a "network tap" is a device that allows access to data flowing across a network for monitoring and analysis..
[Comparison]
In both the fictional world of Murderbot Diaries and real life, pings are primarily used for external signalling and connectivity checks, while taps are used for internal communication and control within the feed network
-------------------------------------------------
[Something Worth Noting]
There are some instances where taps seem more reasonable, but pings are used instead.
In Artificial Condition when Murderbot was watching Sanctuary Moon, and ART was trying to get its attention, asking to watch World Hoppers together. (see Artificial Condition, Pings, 5, 6 my AO3)
In Network Effect, when Murderbot finds that a hostile vessel (i.e. ART) was approaching and notifies the team quickly (see Network Effect, Pings, 1 my AO3)
In Network Effect, when Murderbot was locking itself up in the bathroom (see Network Effect, Pings, 11, 12 my AO3)
In Network Effect, when ART requested a private connection (see Network Effect, Pings, 13 my AO3)
In Network Effect, when Amena comes along with Murderbot to investigate Barish-Estranza shuttle, but is told to wait outside. She offers to help to which Murderbot pings acknowledgement (see Network Effect, Pings, 14 my AO3)
At the end of System Collapse when Murderbot pinged Three to ask if it wanted to listen to Holism explain planetary infrastructure (see System Collapse, Pings 15 my AO3)
Of these, 1, 3, 4 are where ART was sending pings to Murderbot. This is actually quite sweet, because we can tell that ART is being very polite to Murderbot. ART is fully capable of slamming into Murderbot’s private feed, but in all of these occasions, Murderbot has been rejecting feed communication which it reserves for friends and clients. ART is respecting this.
Instance 2 is unusual, and I am not 100% sure why Murderbot chose to use ping here. But since it was emergency, and ping is a protocol where it receives automatic response if it had been received at the other end, it was sufficient for its purposes.
When we read the context in which 5 happens we notice that Murderbot is now inside the B-E shuttle, and for security reasons, ART had cut it off from the feed network. So, Murderbot has the options of either verbally answering to Amena, or sending a ping for acknowledgement, and it chose the latter.
In instance 6, Murderbot seems to be being polite to Three who is busy (?) watching educational media. They are cordial to each other, but because Three is still not used to being a free SecUnit, Murderbot is being more careful around it.
--------------
If you are willing to be bored to death, you can see my AO3 post for the list of all the instances where pinging and tapping happen!
60 notes
·
View notes
Text

Quick sketch for Piers’ bionic arm.

Design Features
•Aesthetics: Streamlined, ergonomic design with a minimalist look, often featuring a matte or metallic finish.
•Materials: Lightweight composites like carbon fiber and titanium, providing durability without sacrificing mobility.
•Color Options: Customizable colors or finishes, including options for skin-like textures or futuristic metallics.
Technology
•Actuation: Advanced motors and actuators that enable precise, fluid movement mimicking natural limb motion.
•Sensors: Integrated sensors (e.g., myoelectric sensors) to detect muscle signals for intuitive control and movement.
•Feedback Systems: Haptic feedback mechanisms to provide users with sensory information about grip strength and object texture.
Safety and Durability
•Water and Dust Resistance: High IP ratings to protect against environmental factors.
•Emergency Features: Manual override systems or fail-safes in case of technology malfunction.
Advanced Technological Interface
•Integrated Biosensors: Built-in biosensors that can analyze blood or interstitial fluid samples to measure viral load in real time.
•Data Analytics: Utilizes algorithms to process biosensor data, providing insights on viral dynamics and trends.
•Alerts and Notifications: Real-time alerts sent to the user or healthcare provider when viral load exceeds predetermined thresholds.
•Communication System: Integrated with a communicator on the wrist, the arm serves as a reliable device for maintaining contact with his team. This system includes encrypted channels for secure communication during high-stakes operations.
•Objective Management Display: The arm features a holographic display that provides a detailed version of the communicator’s data, allowing Piers to view mission objectives and tactical data in real-time. This feature minimizes the need for external devices and keeps critical information accessible.
Augmented Reality (AR) Compatibility
•Enhanced Visualization: The arm’s display projects augmented reality overlays, allowing Piers to see additional information, such as enemy positions, weapon stats, or tactical directions, directly in his line of sight.
•Environmental Scanning: The arm can analyze the surroundings for potential threats, detect biological or chemical hazards, and provide alerts for safer navigation through hostile environments.
Electricity Conduction and Control
•Energy Conduit Design: The bionic arm acts as a conductor for the constant electrical energy generated by Piers’ mutation. It includes specialized channels and circuits designed to manage this energy flow, allowing Piers to use his mutation’s electrical pulse without it spiraling out of control.
•Dielectric Structures: The arm’s design incorporates materials that mimic the dielectric properties of his mutated tissue, particularly in the finger joints and bones. These dielectric components help regulate and contain the high voltage his body produces, diffusing excess energy safely throughout the arm.
•Controlled Release Mechanism: To avoid overload, the arm features a controlled release system that allows Piers to release pulses of energy strategically, whether in combat or to alleviate the internal buildup. This system prevents the arm from overheating or sustaining damage from prolonged electrical activity.
Containment and Compression of the Mutation
•Compression Framework: The prosthetic was specially designed by UMBRELLA engineers to act as a containment “net” around his mutation. It includes a flexible, reinforced framework that compresses the mutated tissue, keeping it in check and preventing further growth or erratic shifts in form.
•Adaptive Pressure System: As the mutation strains against the arm, sensors detect any changes in size or energy output, triggering adaptive responses. The arm tightens or loosens as necessary to hold the mutation back, functioning almost like a high-tech brace that adjusts in real-time to maintain Piers’ arm in a stable form.
•Automatic Safety Lock: In the event of a significant spike in mutation activity or electrical output, the arm engages an emergency lock to keep the mutation from expanding. This feature is a safeguard against sudden bursts of energy that could cause the arm to revert to its mutated state.
Dependency and Risks of Removal
•Rapid Mutation Onset: Without the prosthetic in place, Piers’ arm begins to mutate almost immediately, returning to its original, unstable form. The electrical pulse that his body generates becomes unrestrained, emitting a continuous, breath-like rhythm that is both painful and dangerous, with energy leaking through protruding bones and exposed tissue.
•Uncontrollable Pulse: When uncontained, the electrical pulse from his mutation surges in intensity, lacking any natural “closure” or stopping point. This pulse causes rapid fluctuations in his vital signs and risks systemic overload, leading to loss of control over his mutation and putting him at severe physical risk.
Miscellaneous Details
•The arm has a unique serial code engraved on an inner plate, serving as an identifier for UMBRELLA technicians. This code also links to Piers’ personal health records, mutation data, and arm specifications for quick access during maintenance or in emergencies.
•Due to the intense electrical pulses generated by his mutation, the arm is equipped with an internal cooling system. Micro-fans and heat-dissipating channels prevent overheating during extended use, keeping the arm at a safe, comfortable temperature. If the arm overheats, an internal alarm alerts Piers to prevent any potential damage.
•The outer layer is treated with a UV-resistant coating to protect it from environmental damage and exposure. This ensures that prolonged exposure to sunlight or harsh conditions doesn’t wear down the arm’s exterior, making it more durable in diverse climates and situations.
•Designed for various operational environments, the arm is fully waterproof and corrosion-resistant. It functions normally underwater, which is crucial for aquatic missions or when exposed to rain, mud, or corrosive substances.
•The holographic display can be customized to show additional details, such as weather, GPS navigation, or tactical maps. Piers can also set personal preferences, like color schemes or alert tones, for a more intuitive user experience. This flexibility lets him prioritize the information he finds most critical during missions.
•The communicator has an onboard language translator, enabling Piers to communicate with individuals across different languages. The arm’s display shows translated text, and a subtle earpiece can even relay audio translations, making it easier for him to gather intel and negotiate in multilingual environments.
#𝐒𝐮𝐛𝐣𝐞𝐜𝐭 𝟏𝟑#𝐌𝐮𝐬𝐞; 𝐏𝐢𝐞𝐫𝐬 𝐍𝐢𝐯𝐚𝐧𝐬#I think I very severely fucked up my lefts and rights Ngl but oh well#resident evil#resident evil 6#piers nivans#long post
32 notes
·
View notes
Text



You can beg to carry your own weight and still be judged a burden.
[ Text taken from Wikipedia articles for Changelings, Disability Rights Movement, Biological Immortality, Pearl, and, of course, King Lindworm Image ID and transcript in alt text, and copied below the break ]
🟢 Image 1:
A comic illustration of nine panels in a 3x3 grid. The middle column is a series of family portraits over time. In the left column, the lindworm is shown sleeping as an infant, child, and adult. In the right column's first two panels, the lindworm's human brother is shown sleeping as an infant and child, mirroring the lindworm, but the last panel has been filled by the lindworm's tail as though it has overgrown it's own panel. The lindworm is absent from the last portrait, but the human brother remains.
Text reads:
A peasant family's subsistence frequently depended upon the productive labour of each member, and it was difficult to provide for a person who was a permanent drain on the family's scarce resources.
"The fact that the changelings' ravenous appetite is so frequently mentioned indicates that the parents of these unfortunate children saw in their continuing existence a threat to the sustenance of the entire family."
🟡 Image 2:
A comic illustration of a panel that blends the lindworm's eye into the tower of a castle, which is looming over a town street hung with banners. Against a red sky, a knight mounted on a horse in the foreground stares down a lindworm puppet being moved by many men that blocks the road. The puppet is posed to be hissing at the knight, who has a sword drawn.
Text reads:
It is thought that natural pearls form under a set of accidental conditions when a microscopic intruder or parasite enters a bivalve mollusk and settles inside the shell. The mollusk, irritated by the intruder, forms a pearl sac of external mantle tissue cells and secretes the calcium carbonate and conchiolin to cover the irritant.
Other barriers include: internalised barriers (low expectations of people with disabilities can undermine their confidence and aspirations),
inadequate data and statistics, lack of participation and consultation of disabled people.
🔴 Image 3:
A comic illustration of a knight slaying a lindworm puppet, the knight's horse rearing up as their sword swings up towards the sky. Torn pieces of the puppet follow the movement.
Text reads:
The lindworm tells her to take off her dress, but she insists he shed a skin for each dress she removes.
Eventually, the lobster will die from exhaustion during a moult.
Eventually his human form is revealed beneath the last skin.
299 notes
·
View notes
Text
Privilege Is Without
You might have heard, or read really, at some point, me saying the phrase whiteness is a fog. The idea is that ‘white’ is not, in and of itself, a cultural form, an identity, but rather it is a system of acceptance outside yourself that permeates culture. The fog gets into all the cracks and presses against all the surfaces, but it isn’t, in and of itself, defined by something internal.
I am, after all, white. The system looks at me and goes ‘oh, this guy qualifies for the standard currently.’ Of course, it’s entirely possible for that to be withdrawn. Find the right weirdo and they might (say) falsely claim I’m Jewish and suddenly that whiteness can be withdrawn from me. It’s a complex system that rolls around in its day to day. Go back two hundred years and I wouldn’t get counted. The system is not tracking some inherent, actual, real like chemical detail or compositional detail about me. It is something people socially observe and attribute to me. Some of those attributions are pretty easy but sometimes they’re not.
I bring this up because I find some people talk about Privileges as if they’re things people have imbued in them. A few years ago I lost my mind about it on twitter, where I saw someone complaining about ‘bilingual privilege.’ It struck me as having the energy of a very white person trying to find some way to complain about something, some anything that a person of colour they knew had that they didn’t have and therefore as a way to diminish the feeling of persecution that they felt at realising that privilege exists. That’s a pretty reasonable emotional reaction – it can feel like being told you have something that you don’t consciously feel you have and that feels bad. Not to be cruel about it but ‘how can I have privilege when I’m keenly aware of the things in my life that suck?’ isn’t an unreasonable emotional response when you first discover things.
But, just like with realising that you aren’t actually 6′ when you say you’re ‘about that’, there is an objective measure and factual information you can absorb that can help you dismantle that emotional reaction and get a better handle on reality as it exists. And that’s why I say whiteness is a fog. It’s not a thing in you, your privilege isn’t you, it’s a thing that presses against your surfaces. If you have a name that’s gender ambiguous, you will find situations where privileges are removed from you by people who assume your gender, for example. Deep-voiced femmes know that just being misgendered on the phone can get you better service, because the system, in its headless foolishness, has decided that that voice has access to a tier of privilege, even if it has to get there by misgendering you.
And this is where we get to the way I recommend people think about privilege as an external thing. People don’t ‘have’ privilege, people interface with privilege. Privilege is a system external to you, and if the system decides to respond to you, then you get what the system provides, and if it decides not to, then you don’t. It’s not that you have this wellspring of privilege bubbling up inside you, it’s that there’s an incredibly shitty card reader everywhere, and it constantly scans you and it just so happens, oh, here, you are getting the benefits of this. But you may not want those benefits, but the system doesn’t know that. It happens even when you’re interacting with a person, because the person is ceding their choices and behaviour, typically, to the system. There’s no masc privilege in the middle of a cornfield. It needs to have the system, with its removal from humans making choices, with its ability to offer rewards and incentives.
There are days I have been misgendered. The system did not correctly recognise me, based entirely on a ponytail. The system’s failure to identify a cis boy is, to the system, a hiccup, but if you believe that you believe the system is reliable and consistent and builds its respones out of good data. It’s not. It made what was to me a mistake, but how many people do you think responded to the incident with a mollifying ‘well you do have long hair.’ And when I’ve been attacked based on things – it doesn’t matter if I’m not actually a dyke, being seen as one is enough of a reason to get attacked… and when the mistake is discovered, one of the priviliges is the system kicking in and going: Hey, this is inappropriate. If the privilige was inside me, and not part of a series of social interactions, then how does that happen?
Whiteness is something that recognises me, and I say yeah I’m white because you know what it means. I even use that term to refer to my ignorance and inexperience with the nonpriviliged position! But I’m not ‘white.’ White doesn’t mean anything about my DNA or my history. I’m the Australian son of a British immigrant who came to Australia from a refugee program with her Welsh mother and British father, and my other side of the family came from Free Settlers who came to Australia to colonise it based on being told by a system above them that they were allowed and capable of doing so. And these are material things, these are points of real history but they also interact with that system. If my grandmother hadn’t been married to a British man, when she came to Australia, there was a chance they would have given her a literacy test because the Welsh weren’t considered white at that point. And that’s my grandmother. That’s a woman that was in my life for thirty five years, not some distant memory!
I didn’t get Whiteness at birth. I was born into a space where there was Whiteness, and the Whiteness accepts me because by doing so it can use my opinions and interest against the people Whiteness excludes. The aim of Whiteness is Whiteness, the aim of Privilege is Privilege. There is no inherent power in these things, but that is social, and that means anything they do and anything they impose is being imposed by people and we can do things to oppose that social system.
Admittedly, sometimes opposing that social system means things like ‘ignoring the cops.’
Check it out on PRESS.exe to see it with images and links!
57 notes
·
View notes
Text
To bring about its hypothetical future, OpenAI must build a new digital ecosystem, pushing users toward the ChatGPT app or toward preëxisting products that integrate its technology such as Bing, the search engine run by OpenAI’s major investor, Microsoft. Google, by contrast, already controls the technology that undergirds many of our online experiences, from search and e-mail to Android smartphone-operating systems. At its conference, the company showed how it plans to make A.I. central to all of the above. Some Google searches now yield A.I.-generated “Overview” summaries, which appear in tinted boxes above any links to external Web sites. Liz Reid, Google’s head of search, described the generated results with the ominously tautological tagline “Google will do the Googling for you.” (The company envisions that you will rely on the same search mechanism to trawl your own digital archive, using its Gemini assistant to, say, pull up photos of your child swimming over the years or summarize e-mail threads in your in-box.) Nilay Patel, the editor-in-chief of the tech publication the Verge, has been using the phrase “Google Zero” to describe the point at which Google will stop driving any traffic to external Web sites and answer every query on its own with A.I. The recent presentations made clear that such a point is rapidly approaching. One of Google’s demonstrations showed a user asking the A.I. a question about a YouTube video on pickleball: “What is the two-bounce rule?” The A.I. then extracted the answer from the footage and displayed the answer in writing, thus allowing the user to avoid watching either the video or any advertising that would have provided revenue to its creator. When I Google “how to decorate a bathroom with no windows” (my personal litmus test for A.I. creativity), I am now presented with an Overview that looks a lot like an authoritative blog post, theoretically obviating my need to interact directly with any content authored by a human being. Google Search was once seen as the best path for getting to what’s on the Web. Now, ironically, its goal is to avoid sending us anywhere. The only way to use the search function without seeing A.I.-generated content is to click a small “More” tab and select “Web” search. Then Google will do what it was always supposed to do: crawl the Internet looking for URLs that are relevant to your queries, and then display them to you. The Internet is still out there, it’s just increasingly hard to find. If A.I. is to be our primary guide to the world’s information, if it is to be our 24/7 assistant-librarian-companion as the tech companies propose, then it must constantly be adding new information to its data sets. That information cannot be generated by A.I., because A.I. tools are not capable of even one iota of original thought or analysis, nor can they report live from the field. (An information model that is continuously updated, using human labor, to inform us about what’s going on right now—we might call it a newspaper.) For a decade or more, social media was a great way to motivate billions of human beings to constantly upload new information to the Internet. Users were driven by the possibilities of fame and profit and mundane connection. Many media companies were motivated by the possibility of selling digital ads, often with Google itself as a middle man. In the A.I. era, in which Google can simply digest a segment of your post or video and serve it up to a viewer, perhaps not even acknowledging you as the original author, those incentives for creating and sharing disappear. In other words, Google and OpenAI seem poised to cause the erosion of the very ecosystem their tools depend on.
47 notes
·
View notes
Text
Unsolicited Writing Advice
Completely random reminder to back up your work, especially if you're a writer, IF or game developer, coder, or creator of any kind. People sometimes ask me what my advice for other writers is, and I always forget to include this one, but it's one of the most important things, especially if your career, livelihood, or long-form projects hinge on writing in any way! Take it from someone who just had two backup methods fail unexpectedly and only the third backup prevented me from losing a solid month of work, you need to back up your work in as many ways as you possibly can. It may seem like a pain in the ass at the time, but I've seen a lot of games or stories stall or fail completely due to a catastrophic loss of data that utterly kills any drive to keep going with the project because of the need to start over. I'M BEGGING YOU, BACK UP YOUR DATA.
I recommend having at least 2, ideally 3 methods of backup:
Automatic cloud storage. I personally prefer working with Dropbox, where every change I save is automatically synced and backed up to a cloud server as well as natively saved on my own device. It also has robust version history, so if you figure out you've done something horrific and unknowingly saved over something important or rewritten a section you weren't supposed to, you can rewind everything in a folder down to a specific minute (over the last 30 days): a feature that has saved my hide just a few too many times for comfort. A free Dropbox account gives you 2 GB of storage to work with. Working within Google Drive works just as well, and the free version gives you 15 GB of storage (though that's shared between your email account and other Google apps, as well)! However, I don't believe it provides automatic syncing and backup the same way Dropbox does: you either have to work directly within a Google doc for your work to be automatically saved to the server, or you have to manually upload the files to your Google Drive to back them up each time.
Physical storage. Every few weeks or months, I also take the time to back up my important files to an external hard drive or thumb drive. Again, it's kind of a hassle, but if the day ever comes that you lose your passwords or find that they've been changed, a company's servers go down or they go bankrupt, they decide to start charging you to access your data, or whatever crazy circumstance you can think of, it's always good to have a physical backup somewhere. A basic 1 TB thumb drive is somewhere around 20$ USD (though it can be slower at that price point if you're transferring a large amount of data each time), and it's even less if you don't need that much storage. A 1 TB external hard drive (which has a much quicker transfer rate) is around 40-50$.
If all else fails, email. If you can't get access to physical storage devices and cloud storage services don't work for you, consider setting up a free Gmail or what-have-you account specifically for backup purposes, then email a copy of your most important files to it every time you make a significant change to them. This may seem sort of primitive and simplistic, but it works, and you can even use it as a little journal or diary of your progress!
Again, you may think this is overkill, but I am convinced that writers are especially prone to proving Murphy's Law and have seen way too many projects, friends, and colleagues fall prey to this oft-overlooked issue. I can count at least half a dozen times where -> my primary device like my laptop broke, failed, became corrupted, had water spilled on it, etc. -> I then turned to my secondary device (hard drive or thumb drive) only to find something was wrong with THAT (broken, outdated, incompatible with currently-owned tech, corrupted, not up-to-date backups) OR I turned to my cloud storage and found something wrong with THAT (unknowingly saved over data and didn't realize it until 3 months later, meaning not even version history could save me) -> and it was only the THIRD method of backing up that saved my ass.
Anyway, this is just your friendly neighborhood writer reminding you to back your work up! It's a necessary part of the job! Thanks for coming to my TEDtalk!
374 notes
·
View notes
Text
Where It’s Most Dangerous to Be Black in America
Black Americans made up 13.6% of the US population in 2022 and 54.1% of the victims of murder and non-negligent manslaughter, aka homicide. That works out, according to Centers for Disease Control and Prevention data, to a homicide rate of 29.8 per 100,000 Black Americans and four per 100,000 of everybody else.(1)

A homicide rate of four per 100,000 is still quite high by wealthy-nation standards. The most up-to-date statistics available from the Organization for Economic Cooperation and Development show a homicide of rate one per 100,000 in Canada as of 2019, 0.8 in Australia (2021), 0.4 in France (2017) and Germany (2020), 0.3 in the UK (2020) and 0.2 in Japan (2020).
But 29.8 per 100,000 is appalling, similar to or higher than the homicide rates of notoriously dangerous Brazil, Colombia and Mexico. It also represents a sharp increase from the early and mid-2010s, when the Black homicide rate in the US hit new (post-1968) lows and so did the gap between it and the rate for everybody else. When the homicide rate goes up, Black Americans suffer disproportionately. When it falls, as it did last year and appears to be doing again this year, it is mostly Black lives that are saved.
As hinted in the chart, racial definitions have changed a bit lately; the US Census Bureau and other government statistics agencies have become more open to classifying Americans as multiracial. The statistics cited in the first paragraph of this column are for those counted as Black or African American only. An additional 1.4% of the US population was Black and one or more other race in 2022, according to the Census Bureau, but the CDC Wonder (for “Wide-ranging Online Data for Epidemiologic Research”) databases from which most of the statistics in this column are drawn don’t provide population estimates or calculate mortality rates for this group. My estimate is that its homicide rate in 2022 was about six per 100,000.
A more detailed breakdown by race, ethnicity and gender reveals that Asian Americans had by far the lowest homicide rate in 2022, 1.6, which didn’t rise during the pandemic, that Hispanic Americans had similar homicide rates to the nation as a whole and that men were more than four times likelier than women to die by homicide in 2022. The biggest standout remained the homicide rate for Black Americans.

Black people are also more likely to be victims of other violent crime, although the differential is smaller than with homicides. In the 2021 National Crime Victimization Survey from the Bureau of Justice Statistics (the 2022 edition will be out soon), the rate of violent crime victimization was 18.5 per 1,000 Black Americans, 16.1 for Whites, 15.9 for Hispanics and 9.9 for Asians, Native Hawaiians and other Pacific Islanders. Understandably, Black Americans are more concerned about crime than others, with 81% telling Pew Research Center pollsters before the 2022 midterm elections that violent crime was a “very important” issue, compared with 65% of Hispanics and 56% of Whites.
These disparities mainly involve communities caught in cycles of violence, not external predators. Of the killers of Black Americans in 2020 whose race was known, 89.4% were Black, according to the FBI. That doesn’t make those deaths any less of a tragedy or public health emergency. Homicide is seventh on the CDC’s list of the 15 leading causes of death among Black Americans, while for other Americans it’s nowhere near the top 15. For Black men ages 15 to 39, the highest-risk group, it’s usually No. 1, although in 2022 the rise in accidental drug overdoses appears to have pushed accidents just past it. For other young men, it’s a distant third behind accidents and suicides.
To be clear, I do not have a solution for this awful problem, or even much of an explanation. But the CDC statistics make clear that sky-high Black homicide rates are not inevitable. They were much lower just a few years ago, for one thing, and they’re far lower in some parts of the US than in others. Here are the overall 2022 homicide rates for the country’s 30 most populous metropolitan areas.
Metropolitan areas are agglomerations of counties by which economic and demographic data are frequently reported, but seldom crime statistics because the patchwork of different law enforcement agencies in each metro area makes it so hard. Even the CDC, which gets its mortality data from state health departments, doesn’t make it easy, which is why I stopped at 30 metro areas.(2)
Sorting the data this way does obscure one key fact about homicide rates: They tend to be much higher in the main city of a metro area than in the surrounding suburbs.
But looking at homicides by metro area allows for more informative comparisons across regions than city crime statistics do, given that cities vary in how much territory they cover and how well they reflect an area’s demographic makeup. Because the CDC suppresses mortality data for privacy reasons whenever there are fewer than 10 deaths to report, large metro areas are good vehicles for looking at racial disparities. Here are the 30 largest metro areas, ranked by the gap between the homicide rates for Black residents and for everybody else.
The biggest gap by far is in metropolitan St. Louis, which also has the highest overall homicide rate. The smallest gaps are in metropolitan San Diego, New York and Boston, which have the lowest homicide rates. Homicide rates are higher for everybody in metro St. Louis than in metro New York, but for Black residents they’re six times higher while for everyone else they’re just less than twice as high.
There do seem to be some regional patterns to this mayhem. The metro areas with the biggest racial gaps are (with the glaring exception of Portland, Oregon) mostly in the Rust Belt, those with the smallest are mostly (with the glaring exceptions of Boston and New York) in the Sun Belt. Look at a map of Black homicide rates by state, and the highest are clustered along the Mississippi River and its major tributaries. Southern states outside of that zone and Western states occupy roughly the same middle ground, while the Northeast and a few middle-of-the-country states with small Black populations are the safest for their Black inhabitants.(3)
Metropolitan areas in the Rust Belt and parts of the South stand out for the isolation of their Black residents, according to a 2021 study of Census data from Brown University’s Diversity and Disparities Project, with the average Black person living in a neighborhood that is 60% or more Black in the Detroit; Jackson, Mississippi; Memphis; Chicago; Cleveland and Milwaukee metro areas in 2020 (in metro St. Louis the percentage was 57.6%). Then again, metro New York and Boston score near the top on another of the project’s measures of residential segregation, which tracks the percentage of a minority group’s members who live in neighborhoods where they are over-concentrated compared with White residents, so segregation clearly doesn’t explain everything.
Looking at changes over time in homicide rates may explain more. Here’s the long view for Black residents of the three biggest metro areas. Again, racial definitions have changed recently. This time I’ve used the new, narrower definition of Black or African American for 2018 onward, and given estimates in a footnote of how much it biases the rates upward compared with the old definition.
All three metro areas had very high Black homicide rates in the 1970s and 1980s, and all three experienced big declines in the 1990s and 2000s. But metro Chicago’s stayed relatively high in the early 2010s then began a rebound in mid-decade that as of 2021 had brought the homicide rate for its Black residents to a record high, even factoring in the boost to the rate from the definitional change.
What happened in Chicago? One answer may lie in the growing body of research documenting what some have called the “Ferguson effect,” in which incidents of police violence that go viral and beget widespread protests are followed by local increases in violent crime, most likely because police pull back on enforcement. Ferguson is the St. Louis suburb where a 2014 killing by police that local prosecutors and the US Justice Department later deemed to have been in self-defense led to widespread protests that were followed by big increases in St. Louis-area homicide rates. Baltimore had a similar viral death in police custody and homicide-rate increase in 2015. In Chicago, it was the October 2014 shooting death of a teenager, and more specifically the release a year later of a video that contradicted police accounts of the incident, leading eventually to the conviction of a police officer for second-degree murder.

It’s not that police killings themselves are a leading cause of death among Black Americans. The Mapping Police Violence database lists 285 killings of Black victims by police in 2022, and the CDC reports 209 Black victims of “legal intervention,” compared with 13,435 Black homicide victims. And while Black Americans are killed by police at a higher rate relative to population than White Americans, this disparity — 2.9 to 1 since 2013, according to Mapping Police Violence — is much less than the 7.5-to-1 ratio for homicides overall in 2022. It’s the loss of trust between law enforcement agencies and the communities they serve that seems to be disproportionately deadly for Black residents of those communities.
The May 2020 murder of George Floyd by a Minneapolis police officer was the most viral such incident yet, leading to protests nationwide and even abroad, as well as an abortive local attempt to disband and replace the police department. The Minneapolis area subsequently experienced large increases in homicides and especially homicides of Black residents. But nine other large metro areas experienced even bigger increases in the Black homicide rate from 2019 to 2022.
A lot of other things happened between 2019 and 2022 besides the Floyd protests, of course, and I certainly wouldn’t ascribe all or most of the pandemic homicide-rate increase to the Ferguson effect. It is interesting, though, that the St. Louis area experienced one of the smallest percentage increases in the Black homicide rate during this period, and it decreased in metro Baltimore.
Also interesting is that the metro areas experiencing the biggest percentage increases in Black residents’ homicide rates were all in the West (if your definition of West is expansive enough to include San Antonio). If this were confined to affluent areas such as Portland, Seattle, San Diego and San Francisco, I could probably spin a plausible-sounding story about it being linked to especially stringent pandemic policies and high work-from-home rates, but that doesn’t fit Phoenix, San Antonio or Las Vegas, so I think I should just admit that I’m stumped.
The standout in a bad way has been the Portland area, which had some of the longest-running and most contentious protests over policing, along with many other sources of dysfunction. The area’s homicide rate for Black residents has more than tripled since 2019 and is now second highest among the 30 biggest metro areas after St. Louis. Again, I don’t have any real solutions to offer here, but whatever the Portland area has been doing since 2019 isn’t working.
(1) The CDC data for 2022 are provisional, with a few revisions still being made in the causes assigned to deaths (was it a homicide or an accident, for example), but I’ve been watching for weeks now, and the changes have been minimal. The CDC is still using 2021 population numbers to calculate 2022 mortality rates, and when it updates those, the homicide rates will change again, but again only slightly. The metropolitan-area numbers also don’t reflect a recent update by the White House Office of Management and Budget to its list of metro areas and the counties that belong to them, which when incorporated will bring yet more small mortality-rate changes. To get these statistics from the CDC mortality databases, I clicked on “Injury Intent and Mechanism” and then on “Homicide”; in some past columns I instead chose “ICD-10 Codes” and then “Assault,” which delivered slightly different numbers.
(2) It’s easy to download mortality statistics by metro area for the years 1999 to 2016, but the databases covering earlier and later years do not offer this option, and one instead has to select all the counties in a metro area to get area-wide statistics, which takes a while.
(3) The map covers the years 2018-2022 to maximize the number of states for which CDC Wonder will cough up data, although as you can see it wouldn’t divulge any numbers for Idaho, Maine, Vermont and Wyoming (meaning there were fewer than 10 homicides of Black residents in each state over that period) and given the small numbers involved, I wouldn’t put a whole lot of stock in the rates for the Dakotas, Hawaii, Maine and Montana.
(https://www.washingtonpost.com/business/2023/09/14/where-it-s-most-dangerous-to-be-black-in-america/cdea7922-52f0-11ee-accf-88c266213aac_story.html)
139 notes
·
View notes
Text
Standard Chastity/Underwear/Diaper Component of the Armor Suit
The Standard Chastity/Underwear/Diaper Component is an integral part of the advanced full-body armor suit worn by Cadets, Conscripts, Reservists and Intendurds in the Security Forces, Lifeguards, Paramedic Corps and Nursing Corps and training academies. This component is designed to ensure hygiene, control, and comfort for the wearer, whether used in conjunction with the full armor suit or as a standalone piece of equipment.
Design and Features
Material: Constructed from high-density, hypoallergenic synthetic fabrics, the component provides durability, flexibility, and breathability. The inner lining is coated with an antimicrobial layer to prevent infections and maintain cleanliness over extended periods.
Two-Chamber Design: The component features a specialized two-chamber design. One chamber securely encases the penis, while the other accommodates the scrotum, ensuring both are protected and kept in an optimal environment. This design helps in preventing chafing and maintaining hygiene, even during extended periods of use.
Chastity Mechanism: The chastity feature includes a secure, ergonomic cage designed to prevent unauthorized sexual activity. Made from lightweight, medical-grade polymers, it ensures comfort while maintaining strict control. The cage can be adjusted to fit various sizes and shapes, ensuring a snug but non-restrictive fit.
Waste Management: Integrated into the design is an advanced waste management system. This includes absorbent layers capable of handling urine and fecal matter, which are quickly wicked away to prevent discomfort and skin irritation. The component can be easily cleaned and sanitized, whether worn as part of the armor or independently.
Compatibility: The component seamlessly integrates with the full-body armor suit. Connection points allow for the automated removal and disposal of waste, managed by the suit’s internal systems. When worn independently, it functions efficiently, ensuring the wearer remains hygienic and comfortable.
Security and Monitoring: Equipped with biometric sensors, the component monitors the wearer’s physiological state, transmitting data to the suit’s central processing unit or an external monitoring system. This includes tracking hydration levels, waste excretion, arousal and other vital signs to ensure optimal health and performance.
Comfort and Fit: Designed for extended wear, the component features adjustable straps and a contoured design to prevent chafing and discomfort. The fit can be customized to each wearer, ensuring it remains secure without impeding movement or flexibility.

Usage and Maintenance
Usage: The Standard Chastity/Underwear/Diaper Component is designed for continuous use up to 7 days, with a standard operational period of 5 days. This duration ensures that cadets remain in peak condition during extended training exercises or deployments, without the need for frequent removal or maintenance.
Maintenance: Regular cleaning and sanitization are required to maintain its functionality and hygiene standards. The component can be detached from the suit and cleaned using standard military-grade cleaning agents. Replacement parts and servicing are available through authorized personnel and facilities.
The Standard Chastity/Underwear/Diaper Component exemplifies the blend of technological innovation and practical application, ensuring cadets maintain hygiene and comfort during their rigorous training and operational duties.

21 notes
·
View notes