#Encryption Software
Explore tagged Tumblr posts
Text
Folder Lock
If you have folders and files that you want to keep private, consider using Folder Lock. Unlike My Lockbox, it isn’t a free app, but it offers excellent configuration options and numerous methods to protect important and private documents from prying eyes. Folder Lock is a complete solution for keeping your personal files encrypted and locked, while automatically and in real-time backing up…
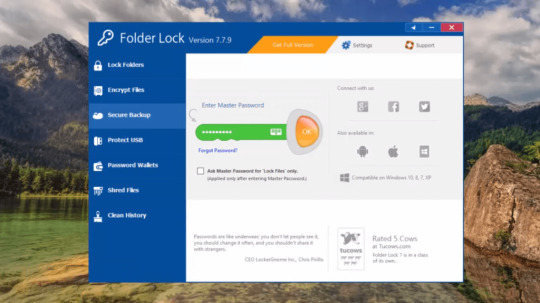
View On WordPress
#Data Encryption#Digital Wallets#Encryption Software#File Locking#File Management#File Security#File Shredding#password protection#Portable Security#privacy protection#Secure Backup#Windows Security
0 notes
Text
#best encryption tools#computer security#cybersecurity#data breach prevention#data encryption guide#data privacy#data protection#data safety#data security tips#digital security#encrypting personal information#encryption basics#encryption FAQs#encryption for beginners#encryption software#encryption solutions#encryption techniques#guide to data encryption#how to encrypt data#online privacy#personal data security#prevent cyber attacks#privacy software#protect data online#secure communication#secure data encryption#secure files and folders#secure personal data#software for encryption#strong encryption methods
1 note
·
View note
Text
The global encryption software market was valued at $ billion in 2020, and is projected to reach $42.26 billion by 2030, growing at a CAGR of 16.5% from 2021 to 2030.
#Encryption Software Market#Encryption Software Market trends#Encryption Software#Encryption Software Market forecast
0 notes
Text
I am currently coding a browser right now in pure Python. Let me explain all the steps it has taken at 300+ lines of code except in no particular order because I need to reorganize.
Fernet Encryption SSL Certificate Check Implementing a UI - Chose PyQt because its a prettier layout than Tkinter. Implementing a toolbar for the UI Implementing browsing history + browsing history tab + a clear button to clear the history - Done in the GUI / UI as well. Adding a privacy browsing mechanism - routed through Tor Added PyBlocker for Ad Blocking and Anti-Tracking on websites Added a feature to make Google not track your searches because fuck you Google you nosey assholes. Added a sandbox to avoid user getting infected with viruses Added additional functionalities including optimization that way the browser wasn't slow as fuck: Using JavaScript v 8 engine to load JavaScript Using slight mem caching <100mb to avoid slowing the computer but also let the program browse quicker Using one http request to send multiple http requests - need to set limit. Encrypted global security features. I am at over 300 lines of code. I am ready to pay someone to debug this shit when I am finished with it (lol) May the force be with you my #Pythonistas
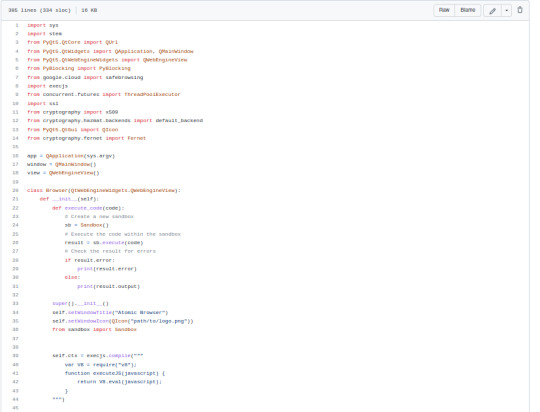
#Python3#pythoncode#coding#programming#programmer#javascript#encryption#cryptography#cybersecurity#internet security#internet#web browsers#web browser history#adblock#ux#ui#gui#development#software development#software developer#devlog#developer log
133 notes
·
View notes
Text
----------------------------------------------------------------------
INSTALLING: DATA ENCRYPTION SOFTWARE (cmbineencrpt.exe)
...
...
...
INSTALLATION: COMPLETE
WARNING: HUD AND INSTRUMENTS ARE: DAMAGED. PLEASE SEEK MEDICAL ATTENTION OR NEAREST COMBINE CHECKPOINT.
----------------------------------------------------------------------
#half life#creative writing#half life: non-citizen#hla#WELL thats a bit odd#what would you need encryption software for?#interesting#veeeery interesting.#hlnc#unfiction#half life combine#hl2
2 notes
·
View notes
Text
Wonderful Web Wednesday 2
Testing Converso - Crnković
Converso was a messaging app meant to change the way people talked over the internet. It was released on the 21st of January, 2023 and is now gone from the internet. The only things left are a blog post exposing the absolutely rampant security flaws in their "state-of-the-art" encryption, and a couple of sponsored articles.
The article by Crnković was the catalyst that spun into the downfall of Converso. The post reads like an adventure book, telling the story of a great adventurer hacking and slashing through a field of broken promises.
The article begins by Crnković explaining how they heard about the app Converso. They had heard an ad for Converso on a podcast that presented Converso as an app that knew nothing about you or what you were talking about. From the perspective of someone who focuses a little bit on privacy, those sound like absolutely amazing promises. But from the perspective of a developer, I am a little skeptical, and so was Crnković.
This led them to digging into what was actually happening behind the scenes at Converso.
What they found is absolutely astonishing. I won't spoil a single bit here so go read it over at https://crnkovic.dev/testing-converso/!
Some secondary research (Spoilers)
Before writing this post, I decided to do some research into what Converso used to look like.
Here are the archives of the Converso website once at release and the other before the close - Converso's website at release - Converso's website near their closing
File Over App - Steph Ango
This quick essay by Steph Ango is an amazing 1 minute read. The essay explains that as we travel through the digital world, we deposit our data across hundreds of proprietary formats and servers. What happens when these formats and servers disappear? Where does the data that we have created go?
It just disappears to be lost forever.
There is a beauty in the way Steph Ango expresses their drive to durable data. They relate the files and data we create to the history our ancestors have left behind. Stone tablets, hieroglyphics, and ancient books have stood the test of time, proving to be information that is truly durable.
Making information that is durable is at the center of what Steph thinks tool makers need to account for when creating software. The tools that they create will not exist forever, but the data that their tools create should exist forever.
This is why Steph urges tool makers to give users access to their data in durable, transportable, and archivable formats. This way, if a user wants to see what they were doing 5 years or 5 decades ago, they can.
#wonderfulwebwednesday#wonderfulweb#files#app#software engineering#softwaredeveloper#encryption#blog#short reads#obsidian md#obsidian.md
3 notes
·
View notes
Text
I had a full on panic attack because I thought all my WIPs were gone bc I couldn't tell where one drive had hidden them.
getting new technology feels more infuriating every year. got a new computer for the first time in 8 years and everything about windows 11 and how it handles onedrive is driving me up the wall
#This was also when I found out that the backup software I was using had been putting my files into a proprietary encryption#And I couldn't just go in and find the back up of a file I was looking for#It was a real fun panic attack day for Sammy
23K notes
·
View notes
Text
सही Tally on Cloud प्रोवाइडर चुनने से पहले ये 7 सवाल ज़रूर पूछें!
आजकल कारोबार को बेहतर बनाने और कहीं से भी डेटा एक्सेस करने के लिए Tally on Cloud बहुत पॉपुलर हो गया है। लेकिन सही सर्विस का चुनाव करना थोड़ा मुश्किल हो सकता है। यह ब्लॉग उन मुश्किलों को आसान बनाने के लिए तैयार किया गया है। इसमें हम आपको 7 जरूरी सवाल बताएंगे, जो आपको Tally on Cloud सर्विस लेने से पहले पूछने चाहिए।

Tally on Cloud लेते समय सबसे पहले हमें सुरक्षा (Security) पर ध्यान देना चाहिए, खासकर वित्तीय डेटा (Financial Data)के लिए यह बहुत जरूरी है। इसलिए आपको यह पूछना चाहिए कि कंपनी आपके डेटा को सुरक्षित रखने के लिए क्या कदम उठाती है, जैसे डेटा एन्क्रिप्शन (Encryption) और मल्टी-फैक्टर ऑथेंटिकेशन (MFA)। इसके अलावा एक और महत्वपूर्ण चीज है सर्विस की विश्वसनीयता (Reliability)। यह सुनिश्चित करें कि कंपनी आपको हमेशा सर्विस प्रदान कर सके। अगर आपका व्यवसाय अलग-अलग टाइम ज़ोन में चलता है, तो यह और भी जरूरी हो जाता है।
इसके अलावा, कस्टमर सपोर्ट (Customer Support), डेटा बैकअप और रिकवरी (Data Backup and Recovery), छिपे हुए शुल्क (Hidden Charges), और कस्टमाइजेशन (Customization) के बारे में भी जरूर पूछें। हर बिजनेस की जरूरतें अलग होती हैं, इसलिए यह बेहतर होगा कि सर्विस को अपनी जरूरत के मुताबिक कस्टमाइज़ किया जा सके।
Antraweb Technologies एक ऐसी कंपनी है जो मजबूत और सुरक्षित Tally on Cloud सर्विस प्रदान करती है। यह कंपनी 24/7 सपोर्ट, बेहतरीन सुरक्षा, और कस्टमाइजेशन के विकल्प भी देती है। और सबसे अच्छी बात यह है कि यह सब कुछ किफायती दामों में उपलब्ध है।
अगर आप और ज्यादा जानना चाहते हैं, तो हमारे ब्लॉग पेज पर जाएं:
Blog Page: https://www.antraweb.com/blog/tally-on-cloud-hindi
हमारी वेबसाइट: https://www.antraweb.com/
#Tally on Cloud#Tally on AntraCloud#Tally on Cloud provider#AntraCloud#Tally Cloud solution#Tally Data security#Tally security#Tally backup#Tally cloud computing#Tally support#Tally customization#Tally software#Tally cloud solution#Tally Data Encryption#Antraweb Tally cloud
0 notes
Text
United States encryption software market size reached USD 3.5 Billion in 2024. Looking forward, IMARC Group expects the market to reach USD 10.1 Billion by 2033, exhibiting a growth rate (CAGR) of 12.7% during 2025-2033. The growing cyber threats and data breaches in the United States, rising remote work and bring your own device (BYOD) policies, increasing need to comply with government regulations, and the growing volume of digital transactions represent some of the key factors driving the market.
#United States Encryption Software Market#United States Encryption Software Market size#United States Encryption Software Market share#United States Encryption Software Market forecast#United States Encryption Software Market 2024
0 notes
Text
Encryption Software Market flourishes as cybersecurity investments soar according to a new research report
whatech.com · by David Correa · December 4, 2023
However, growing demand for cloud-based encryption software is expected to create lucrative opportunities in the industry.
The global encryption software market was valued at $ billion in 2020, and is projected to reach $42.26 billion by 2030, growing at a CAGR of 16.5% from 2021 to 2030.
#Encryption Software Market#Encryption Software Market size#Encryption Software Market trends#Encryption Software
0 notes
Text
The Future of Real Estate in Jamaica: AI, Big Data, and Cybersecurity Shaping Tomorrow’s Market
#AI Algorithms#AI Real Estate Assistants#AI-Powered Chatbots#Artificial Intelligence#Automated Valuation Models#Big Data Analytics#Blockchain in Real Estate#Business Intelligence#cloud computing#Compliance Regulations#Cyber Attacks Prevention#Cybersecurity#Data encryption#Data Privacy#Data Security#data-driven decision making#Digital Property Listings#Digital Transactions#Digital Transformation#Fraud Prevention#Identity Verification#Internet of Things (IoT)#Machine Learning#Network Security#predictive analytics#Privacy Protection#Property Management Software#Property Technology#Real Estate Market Trends#real estate technology
0 notes
Text
Zoho Product Vulnerabilities: Exploring Legacy Issues and New Security Threats in 2023-2024 @zoho #ZohoOne #ManageEngine #ZohoCRM #ZohoBooks
Legacy Vulnerabilities in Zoho Products and New Discoveries in 2023-2024: A Comprehensive Analysis Introduction Zoho Corporation is one of the most well-established software development companies, offering a wide range of products that include customer relationship management (CRM), office suite applications, and cloud-based business tools. Over the years, Zoho has gained a massive following,…
#Cybersecurity threats#Software security 2024#Zero-day vulnerabilities#Zoho CRM API#Zoho Mail phishing#Zoho ManageEngine#Zoho security#Zoho Vault encryption#Zoho vulnerabilities
0 notes
Text
VeraCrypt
Security on your device is crucial, especially if others frequently use your machine. VeraCrypt is an application designed to secure and encrypt partitions, ensuring sensitive files remain protected. The program is highly customizable, offering a variety of options. When you open VeraCrypt, you’ll find a simple interface, which some may consider outdated, guiding you through the available…
#Data Privacy#data security#disk encryption#disk encryption software#encryption#full disk encryption#password protection#secure data#VeraCrypt#volume encryption
0 notes
Text
### The Benefits of Using Ubuntu Over Microsoft Windows in context of Today's Microsoft Outage
In the ever-evolving world of technology, choosing the right operating system (OS) can significantly impact your productivity, security, and overall user experience. While Microsoft Windows has long been a dominant player in the market, an increasing number of users are turning to Ubuntu for its robust security features and cost-effective solutions. Today, we delve into why Ubuntu is a superior…

View On WordPress
#Free operating system#Free software#Linux vs Windows#Microsoft Windows alternatives#Microsoft Windows outage#Open-source operating system#Switch to Ubuntu#Ubuntu#Ubuntu benefits#Ubuntu cost savings#Ubuntu encryption#Ubuntu firewall#Ubuntu security features#Ubuntu stability#Ubuntu vs Microsoft Windows#Ubuntu vs Windows security
0 notes