#Antivirus scan results
Explore tagged Tumblr posts
Text
10 Deadliest PC Viruses That Shook the World
Introduction The digital world can be a dangerous place, especially with the constant evolution of PC viruses. These malicious programs not only threaten your files but also compromise your security, privacy, and finances. Here, we explore the 10 most dangerous PC viruses, their impacts, and expert opinions on how to protect yourself. 1. ILOVEYOU Virus Date of Creation: May 2000Problems: The…
#Advanced persistent threats#Anti-malware programs#Anti-malware solutions#Anti-malware tools for PC#Anti-phishing software#Anti-ransomware tools#Anti-spam filters#Anti-virus program updates#Anti-virus tool effectiveness#Antivirus database#Antivirus database updates#Antivirus malware protection#Antivirus protection#Antivirus scan results#Antivirus software#Antivirus software effectiveness#Antivirus software solutions#Antivirus software updates#Antivirus strategies#Antivirus strategy#Antivirus system scans#Antivirus tools for businesses#Automated malware detection#Automated virus updates#Behavioral analysis#Behavioral-based detection#Cloud security#Cloud-based antivirus protection#Cloud-based virus detection#Computer security solutions
0 notes
Text
🔎Scam Exam(ination)🔍
Seen as: Click here! / Read more... Scam type(s): Phishing / Malicious website
Good day everyone, today I'd like to talk about a scam that is some what pretty obvious to spot on tumblr. Unless you're someone who straight up lets curiosity get the best of them and you go clicking links on sketchy looking blogs without thinking. (Don't do that.) You'll probably be able to avoid it.
Now, for safety reasons I'm not going to be linking the blog in question that is running this scam because I'm not going to 'tempt fate' for the sake of documentation. But I will be showing you through the help of a couple useful websites, what's going on behind the scenes.
-----
The first thing I noticed (other than the blog only being a few days old) when I saw this persons posts was, well, what I consider to be one of the most biggest and immediate red flags that was on every single post of theirs.

If you know anything at all about internet history and internet safety, one of the most common and well known ways that malicious actors try to get you to go to their scam/phishing website is with the temptation of a big reward if you do x to y.
'You've won a free $100 gift card! Click here to claim!'
'Hot local singles in your area! Click here now to find them!'

Memes aside, it should go without saying that you should not, under any circumstances, click links that look like this that you receive via email, text, or that you see in advertisements. Not only could these links lead you to a phishing page (wiki) that mimics tumblr or another social media platform in an attempt to get you to log in. Doing so would result in your account being compromised and your login information being stolen.
Tempting links like these could also lead to a web page like the one that this one in particular I'm about to show you, too.
With the help of Cloudflare via their url scanner tool I was able to examine this website, see where it redirects people to, view the HTML (for you nerdy folks) and in turn see the landing page it takes you to when you click it. Without clicking it myself.
Want to know what this takes you to?

A page leading to a fake popup with a link to install a virus.
Now, let me be 100% clear: These viruses are bad.
From what I know of them, not only do they hijack and steal all of your login information on the device you installed it on, 9/10 it will also install a keylogger onto your system. What this does is: even if you uninstall the virus and your system seems clean, these bad actors will still be able to monitor your device and steal your information unless you factory reset your device or PC.
Here's information on keyloggers. (malwarebytes)
If these bad actors really, really wanted to ruin someones day, by installing these 'free apps' it could also put what is known as Ransomware on your device. A trojan that locks down your device, encrypts your files, and demands you pay a ransom for it to be unlocked. All of which is under a timer or it will completely brick your system.
Here's a video by IBM that explains how ransomware works.
Another very, VERY useful website I'd like to share that I became familiar with through some channels on youtube that talk about scams is VirusTotal. https://www.virustotal.com (despite its name, it's not a virus!)
This website has two key features I think are awesome: 1- You can scan a url for viruses/malicious activity to see if it's been flagged by one of the many antivirus vendors on the market. and 2- You can upload files you downloaded to see if they are infected by trojans or malware before you even open them.

CloudFlare and VirusTotal are 100% free to use websites with no sign up or cost. (No this isn't an ad and no I am not sponsored. These are just resources and I am giving them to you lol)
-----
Final thoughts: I know curiosity may get the best of us at times, but don't let that become your downfall. If you see blogs that are only a few days old exhibiting this behavior, please make sure you report them on your own time and don't encourage mass reporting by making posts about them.
Remember: Stop and think before you click that link. :)
Other helpful guides on spotting scams. (by @kyra45)
63 notes
·
View notes
Text

PSA! THERE IS MALWARE ON YAYTEXT!
I'm not fully sure just how relevant this will be, but if anyone else uses yaytext to fancify their text with unicode, please be aware that there is now malware on the yaytext website ( yaytext.com ). it has been on there for at least a week now, so if you have gone onto the site, you might have been infected!
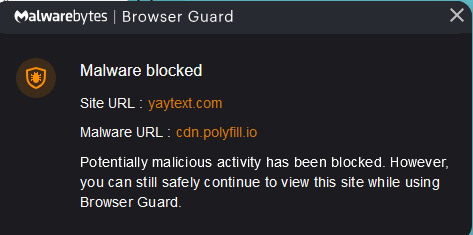
WHAT NOW? IF YOU HAVE VISITED YAYTEXT:
first, run a malware scan on your computer. you can do this for FREE with malwarebytes, bitdefender, or kaspersky*. you can find the free versions of these antivirus softwares on their respective websites, and I will link them below for convenience.
after you run the malware scan (hopefully you are not infected!), add the respective browser guard to your browser. as you can see by my screenshot, I use Malwarebytes' broswer guard. if you decide to use their browser guard too, you will still be able to safely use yaytext.
WHERE ELSE DO I GO?
you should assume that yaytext IS NOT safe to use for the time being! there are plenty of other unicode generators out there, however, so you don't have any disruption with your aesthetics.
some alternatives are:
fontspace font generator
lingojam text generator
fontalic
I have just checked all of these sites and none of them have malware on them at this time.
ANTIMALWARE SCANNING
MalwareBytes - free version BitDefender - free version Kaspersky* - free version
*note that Kaspersky is being banned in the U.S. for being a Russian company. The ban is over worries that Russia could use the AV as spyware in the U.S., because the Kremlin can force any company in Russia to share all of their data with them. Despite this, Kaspersky is a top contending cybersecurity research company. If you are not comfortable using Kaspersky, studies have shown that BitDefender provides near equivalent results. source: i am getting my degree in cybersecurity lol
71 notes
·
View notes
Text
Project Thunder: Codeship Battle
The battle rages outside the Firewalls. Mira's part in the plan is working perfectly, Chroma and Blaze focusing on her to the exclusion of everything else while Amy in a custom fighter (Mira can't fly she had to get to the Firewalls somehow) fights off any backup that might show up, and scans for potential weakpoints in the shield as she goes.
The parody twins are cutting a path of destruction through the battlefield, Radiant especially, and when the Grid's Firewall Twins run into them they realize very quickly what this is supposed to be. And they ain't happy. A few other Programs also get thrown into That Whole Mess, including Crash and Download. As a result, while Tartarus and Spirit end up focused on each other, Radiant ends up finally finding somebody who matches her freak and she and Crash are both having way too much fun trying to dismember each other, much to the terror of everyone around them. Except Download. Download thinks it's hot.
As the battle progresses the painful reality is that the CCC's army is more-or-less infinite while the Fleet is very much Not, and they keep having to pull out new tricks and secret weapons. One in particular, codenamed Plan 69, Peach is planning to only use when absolutely necessary, but with how long things are taking she eventually puts it in the Standby phase. And apparently it involves Chris, Swag and GG in some way.
Also, the CCC isn't just content to keep throwing troops at the problem in an endless loop, no, they're actually innovating and optimizing and restrategizing as well. And this is best shown when they finally bring out two of their biggest trump cards. The first are Twilit Swarms, massive swirling clouds of Twilight that can corrupt those they envelop, assuming they don't tear them apart. Notably, Mira actually gets hit, and while it doesn't manage to turn her evil or anything it does activate her Werehog form for the first time, and the loss of her super speed obviously causes issues with her part in the plan so eventually she and Amy have to get sent to the Jubilation so Chroma and Blaze don't manage to Fucking Kill Them.
The second trump card is a result of the Deal that Mr. L struck with someone from a true alternate universe. Namely, with the version of Worm from Samurai Bob's world who's a parody of Aku. Yeah he actually shows up in the middle of the battle and starts wrecking the Alliance's shit, saying that it's time for him to truly hold up his end of the bargain.
He does a lot of damage, including blasting away a big chunk of the Jubilation's outer hull (the shields hold up, but some Twilight and Brobots manage to slip through, so the internal security's gonna be putting in their money's worth), before a Thoroughly Enraged Antivirus, Matrix and Dave start laying into him. It's at this point that Peach fully authorizes Plan 69.
"And may the Stars forgive us for what we are about to unleash."
It turns out that Plan 69 is for GG to stuff Swag full of every cheat code she can think of and then turn him into a Code-Level entity like she did to Tuff that one time, then Chris will shoot them both out of an airlock, setting them loose to Wreak Havoc. The power immediately goes to Swag's head, with him declaring himself to be "Swagmageddon" and saying shit like "I see no god up here, other than me." He also manages to piss off Rhythmi by calling her a "Fugly-ass little spider gremlin preschooler" and genuinely fearing that if she touches him she'll lay eggs in his brain. Because Swag.
#project thunder au#mira#chroma#blaze#amy rose#tartarus#olympus#spirit#radiant#crash#download#chris gordman#swagmaster6969696969#the gamer girl#worm shapeshifting master of darkness#antivirus#matrix#dave#swagmageddon#rhythmi the storyweaver
6 notes
·
View notes
Text
As Russia has tested every form of attack on Ukraine's civilians over the past decade, both digital and physical, it's often used winter as one of its weapons—launching cyberattacks on electric utilities to trigger December blackouts and ruthlessly bombing heating infrastructure. Now it appears Russia-based hackers last January tried yet another approach to leave Ukrainians in the cold: a specimen of malicious software that, for the first time, allowed hackers to reach directly into a Ukrainian heating utility, switching off heat and hot water to hundreds of buildings in the midst of a winter freeze.
Industrial cybersecurity firm Dragos on Tuesday revealed a newly discovered sample of Russia-linked malware that it believes was used in a cyberattack in late January to target a heating utility in Lviv, Ukraine, disabling service to 600 buildings for around 48 hours. The attack, in which the malware altered temperature readings to trick control systems into cooling the hot water running through buildings' pipes, marks the first confirmed case in which hackers have directly sabotaged a heating utility.
Dragos' report on the malware notes that the attack occurred at a moment when Lviv was experiencing its typical January freeze, close to the coldest time of the year in the region, and that “the civilian population had to endure sub-zero [Celsius] temperatures.” As Dragos analyst Kyle O'Meara puts it more bluntly: “It's a shitty thing for someone to turn off your heat in the middle of winter.”
The malware, which Dragos is calling FrostyGoop, represents one of less than 10 specimens of code ever discovered in the wild that's designed to interact directly with industrial control-system software with the aim of having physical effects. It's also the first malware ever discovered that attempts to carry out those effects by sending commands via Modbus, a commonly used and relatively insecure protocol designed for communicating with industrial technology.
Dragos first discovered the FrostyGoop malware in April after it was uploaded in several forms to an online malware scanning service—most likely the Google-owned scanning service and malware repository VirusTotal, though Dragos declined to confirm which service—perhaps by the malware's creators, in an attempt to test whether it was detected by antivirus systems. Working with Ukraine's Cyber Security Situation Center, a part of the country's SBU cybersecurity and intelligence agency, Dragos says it then learned that the malware had been used in the cyberattack that targeted a heating utility starting on January 22 in Lviv, the largest city in western Ukraine.
Dragos declined to name the victim utility, and in fact says it hasn't independently confirmed the the utility's name, since it only became aware of the targeting from the Ukrainian government. Dragos' description of the attack, however, closely matches reports of a heating outage at the Lvivteploenergo utility around the same time, which according to local media led to a loss of heating and hot water for close to 100,000 people.
Lviv mayor Andriy Sadovyi at the time called the event a “malfunction" in a post to the messaging service Telegram, but added, “there is a suspicion of external interference in the company's work system, this information is currently being checked.” A Lvivteploenergo statement on January 23 described the outage more conclusively as the “result of a hacker attack.”
Lvivteploenergo didn't respond to WIRED's request for comment, nor did the SBU. Ukraine's cybersecurity agency, the State Services for Special Communication and Information Protection, declined to comment.
In its breakdown of the heating utility attack, Dragos says that the FrostyGoop malware was used to target ENCO control devices—Modbus-enabled industrial monitoring tools sold by the Lithuanian firm Axis Industries—and change their temperature outputs to turn off the flow of hot water. Dragos says that the hackers had actually gained access to the network months before the attack, in April 2023, by exploiting a vulnerable MikroTik router as an entry point. They then set up their own VPN connection into the network, which connected back to IP addresses in Moscow.
Despite that Russia connection, Dragos says it hasn't tied the heating utility intrusion to any known hacker group it tracks. Dragos noted in particular that it hasn't, for instance, tied the hacking to the usual suspects such as Kamacite or Electrum, Dragos' own internal names for groups more widely referred to collectively as Sandworm, a notorious unit of Russia's military intelligence agency, the GRU.
Dragos found that, while the hackers used their breach of the heating utility's network to send FrostyGoop's Modbus commands that targeted the ENCO devices and crippled the utility's service, the malware appears to have been hosted on the hackers' own computer, not on the victim's network. That means simple antivirus alone, rather than network monitoring and segmentation to protect vulnerable Modbus devices, likely won't prevent future use of the tool, warns Dragos analyst Mark “Magpie” Graham. “The fact that it can interact with devices remotely means it doesn't necessarily need to be deployed to a target environment,” Graham says. “You may potentially never see it in the environment, only its effects.”
While the ENCO devices in the Lviv heating utility were targeted from within the network, Dragos also warns that the earlier version of FrostyGoop it found was configured to target an ENCO device that was instead publicly accessible over the open internet. In its own scans, Dragos says it found at least 40 such ENCO devices that were similarly left vulnerable online. The company warns that there may in fact be tens of thousands of other Modbus-enabled devices connected to the internet that could potentially be targeted in the same way. “We think that FrostyGoop would be able to interact with a huge number of these devices, and we're in the process of conducting research to verify which devices would indeed be vulnerable,” Graham says.
While Dragos hasn't officially linked the Lviv attack to the Russian government, Graham himself doesn't shy away from describing the attack as a part of Russia's war against the country—a war that has brutally decimated Ukrainian critical infrastructure with bombs since 2022 and with cyberattacks starting far earlier, since 2014. He argues that the digital targeting of heating infrastructure in the midst of Ukraine's winter may actually be a sign that Ukrainians' increasing ability to shoot down Russian missiles has pushed Russia back to hacking-based sabotage, particularly in western Ukraine. “Cyber may actually be more efficient or likely to be successful towards a city over there, while kinetic weapons are maybe still successful at a closer range," Graham says. “They’re trying to use the full spectrum, the full gamut of available tools in the armory.”
Even as those tools evolve, though, Graham describes the hackers' goals in terms that have changed little in Russia's decade-long history of terrorizing its neighbor: psychological warfare aimed at undermining Ukraine's will to resist. “This is how you chip away at the will of the people,” says Graham. “It wasn’t aimed at disrupting the heating for all of winter. But enough to make people to think, is this the right move? Do we continue to fight?”
9 notes
·
View notes
Note
Dunno if this is spoilers but with the SM virus, did sun notice it at first?
Or did the virus take time for it to fully/partially intergrate into Sun's code?
Well Sun had a feeling that something wasn't right but everytime he scanned himself it always came back with no result. His system didn't recognized S.M as a virus at first, until later when it was already to late. (So like S.M had a cover up to be unnoticed until it was strong enough and developed to handle Sun's antivirus system).
#the sun and moon show#sun and moon show#sun and moon show au#tsams#sams#tsams au#sams au#Solar Maximum AU#ask triceraptor
21 notes
·
View notes
Text
Cricut Not Connecting to Bluetooth: 5 Effective Solutions

All Cricut machines have Bluetooth connectivity to connect to all types of computers and smartphones. Sometimes, you may face the error message “Cricut not connecting to Bluetooth. “There can be various reasons for this issue, such as compatibility, restrictions, distance between your devices, configuration, and more.
Many factors can cause connectivity problems. To know all the solutions, explore this write-up and find the best method to eliminate this wireless connection error.
Solution 1: Unpair and Restart Your Device
You may face this issue if your machine is far from your device. In this case, you’re going to follow the steps to resolve your connectivity issue:
Firstly, unpair the machine from all devices.
Then, unplug the machine from the main power.
After that, restart your computer or mobile phone.
Next, plug in back your machine and power it on.
Ensure your machine is within 15 feet of your device for Bluetooth connectivity.
Also, confirm that Wi-Fi and Bluetooth are enabled on your device.
Make sure your device has the latest version of the Design Space app.
Click on the Add Bluetooth or other device option.
Now, select the Bluetooth option and wait for the computer to scan your machine.
You click on your machine from the result and pair your machine.
Solution 2: Check for a Firewall or Antivirus Software
The Windows Firewall on your system or antivirus on your phone can stop the machine. Follow the steps below to solve the Cricut not connecting to Bluetooth issue:
To begin, go to the search bar and type Windows Firewall on the search field.
After that, you must agree to give permission to the app through the Windows firewall.
Then, go to the Windows Firewall settings and select the option to Change Settings.
Next, you have to move to the list and click the Design Space software checkbox.
After that, select both the private and public options.
If the option for the app registered does not show, choose to Allow another app option.
Hence, move to the installation folder of your Cricut software.
Solution 3: Remove the Other Device
If your device is already connected with the other device, it can face issues while connecting. Therefore, you need to remove the other device by following the below steps:
Start by pressing the Start menu and choose the Settings option.
Next, open the Devices window by selecting its option.
After that, choose the device you want to remove from your computer and hit the Remove Device option.
Then, confirm the action by choosing the right option.
Finally, you can pair your machine to see if the issue of Cricut not connecting to Bluetooth has been resolved.
Solution 4: Update the Software
The issue can arise even when the machine’s software is outdated. Here are the steps to update your machine’s software:
Start by pressing the Windows and X buttons together on the keyboard.
When a list of options appears on your screen, click the Device Manager option.
In the device manager screen, select the option of the machine and right-click on it.
After that, choose the Update Driver Software option.
Once your driver is updated, try to complete the Bluetooth pairing process.
Solution 5: Check for Device Compatibility
Check the system requirements on the Cricut official website (Cricut.com/setup) to verify your device’s compatibility.
Android: The app is compatible with Android 10.0 or the latest version but only on mobile devices and tablets. It is not supported on Chromebooks. Some qualified devices include Samsung Galaxy, Google Pixel, LG, G, K or V series, Motorola Droid, and One Plus.
iOS: The app is compatible with iOS or later on iPhones, iPads, and iPods.
Windows or Mac: The software can be used on Windows or Mac computers.
First, click the Design Space icon on your desktop.
Then, go to the Start menu, open the file location, and right-click.
Now, open the “Properties” section. In the Properties window, select the Compatibility tab.
Final Thoughts
In conclusion, this issue of Cricut not connecting to Bluetooth can be fixed with this troubleshooting guide. There can be various reasons, such as if your machine has connection issues, is far away, or has outdated software.
Remember to stay patient while resolving these issues. With persistence, you can overcome these problems, enjoy wireless connectivity, and work seamlessly with your machine.
FAQs
How do I connect Cricut machine to my Mac?
To connect a machine to a Mac, you can use Bluetooth or a USB cable; here, if you want to connect with Bluetooth, then follow the steps:
Turn on the machine and make sure it is within the range of 10-15 feet of the computer.
After that, go to System Preferences and choose the Bluetooth option.
Now, check if the Bluetooth is on and choose your machine from the list.
Next, follow the prompt to complete the pairing process.
Why is my Cricut machine not connecting to Bluetooth?
If your crafting machine is not connecting to Bluetooth, there are many reasons like:
Make sure your machine is within 15 feet of your device.
Check the power and whether it is turned on or not.
And check if the Bluetooth device is turned on.
Make sure your device’s Wi-Fi is turned on.
Update your Design Space to the latest version.
Make sure your system has all the minimum system requirements for running the Design Space app.
Unpair your machine from all devices, restart your device, plug it back into the machine, and then re-pair it.
How do I reset my Cricut machine using Bluetooth?
The steps to reset the machine using Bluetooth are as follows:
First, unpair the machine from all devices.
Then, unplug the machine from the power.
Now, restart your computer or mobile device.
Next, plug the machine back in and turn it on.
After that, move the machine within 15 feet of your computer or mobile device.
Make sure your computer or mobile device’s Wi-Fi and Bluetooth are on.
Lastly, update the Design Space app to the latest version.
For more information visit: how to setup cricut maker cricut new machine setup
Source: Cricut Not Connecting to Bluetooth
#cricut not connecting to bluetooth#Cricut Design Space app#Cricut Design Space software#cricut new machine setup#cricut.com/setup
2 notes
·
View notes
Text
If an antivirus you use flags Glaze as a threat, ignore/whitelist it
Today I had Windows Defender flagging the new version of Glaze as a Trojan. I looked into it on Twitter and it turns out that AI bros took Glaze and uploaded it to virus databases to have it falsely flagged as malware, which has resulted in some antivirus programs falsely flagging it at such. I've scanned Glaze with Malwarebytes and it returned no warnings.

If you downloaded Glaze and your antivirus program flagged it as Trojan, whitelist it. Glaze developers are currently in the process of getting Glaze signed.
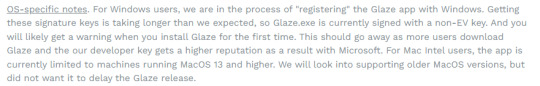
[ALT text, image is a screencap of a paragraph on Glaze's website] "OS-specific notes. For Windows users, we are in the process of "registering" the Glaze app with Windows. Getting these signature keys is taking longer than we expected, so Glaze.exe is currently signed with a non-EV key. And you will likely get a warning when you install Glaze for the first time. This should go away as more users download Glaze and the our developer key gets a higher reputation as a result with Microsoft. For Mac Intel users, the app is currently limited to machines running MacOS 13 and higher. We will look into supporting older MacOS versions, but did not want it to delay the Glaze release."
Glaze can be downloaded here. The new version uses a much more subtle cloak and now works on flat shaded/cel shaded art styles and photography, and even has a limited img2img protection.
8 notes
·
View notes
Text
Roblox Mod APK 2.574.445 (Unlimited Robux no ban)

Popular online gaming platform Roblox APK file can download from this website. The website claims that this APK file is a modified version of the official Roblox app. Users get access to premium features without paying any kind of money. This APK file can bypass any restrictions imposed by the official app.
It is important to know using modded APK files can lead to security risks. Such files may contain malware or viruses. which may damage the user's device or steal personal information Additionally, using modded APK files may violate official app terms. This may result in a permanent ban from the platform.
Therefore, users should be careful while using the modded APK files. It should only be downloaded from trusted sources. Antivirus software needs to scan before installation.
In summary, modded APK files give access to premium features without paying. They carry significant risks and can result in serious consequences. Users need to know the potential risks and benefits before downloading and using such files
#roblox#roblox game#roblox character#roblox memes#roblox myths#roblox man face#roblox music id codes all the best songs to use#best games#best green character tournament#best girl
2 notes
·
View notes
Text
Comprehensive Guide to Computer Repair: Tips, Tricks, and Best Practices
In today’s digital age, computers are indispensable tools for work, education, and entertainment. However, like any electronic device, they are prone to issues that can disrupt our daily routines. From software glitches to hardware malfunctions, understanding basic computer repair can save time, money, and frustration. This guide explores the essentials of diagnosing and fixing common computer problems.
Common Computer Problems and Solutions
1. Slow Performance
Cause: A sluggish computer is often the result of unnecessary background processes, insufficient RAM, or malware.
Solution:
Close unnecessary programs using Task Manager.
Upgrade RAM if needed.
Run antivirus scans to detect and remove malware.
2. Blue Screen of Death (BSOD)
Cause: BSOD occurs due to hardware or driver issues, often stemming from corrupted software or incompatible updates.
Solution:
Restart the computer and check for error codes.
Update drivers through Device Manager.
Use system restore to revert to a previous stable state.
3. Overheating
Cause: Overheating can damage internal components and is typically caused by dust buildup or failing cooling systems.
Solution:
Clean the internal components, including fans, with compressed air.
Ensure proper ventilation around the computer.
Replace thermal paste if needed.
4. Unresponsive Applications
Cause: This often results from software bugs or limited system resources.
Solution:
Force close the application.
Update the software to the latest version.
Reinstall the application if issues persist.
5. Internet Connectivity Issues
Cause: Problems can arise from network adapter issues, router problems, or ISP downtime.
Solution:
Restart your router and modem.
Check network adapter settings.
Contact your ISP if the problem isn’t resolved.
Tools Every Computer Technician Should Have
Screwdrivers: For assembling and disassembling hardware.
Thermal Paste: Essential for CPU maintenance.
Multimeter: To check power supply issues.
External Hard Drive: For data backup.
Antivirus Software: To eliminate malware and viruses.
Preventive Maintenance Tips
Regular Updates: Keep your operating system and applications up to date.
Backup Data: Use cloud services or external drives to prevent data loss.
Clean Hardware: Dust and debris can lead to overheating and hardware damage.
Use Reliable Antivirus Software: Protect your system from malware.
Avoid Overloading: Don’t overload the system with unnecessary software or files.
When to Seek Professional Help
While many computer issues can be resolved at home, some require professional expertise. If you encounter persistent hardware failures, data recovery challenges, or motherboard issues, it’s best to consult a certified technician.
Conclusion
Knowing how to diagnose and resolve basic computer issues is a valuable skill in our tech-driven world. By following the tips and techniques outlined above, you can enhance your computer’s performance and longevity. For more complex problems, don’t hesitate to seek expert assistance to ensure your system remains in top condition.
#IFIXHUB Computer Repair Dallas#Ifixhub#computer repair dallas#computer repair near me#computer repair service etc.
1 note
·
View note
Text
Cyber Security : Unpacking the Essentials of Cybersecurity
In today’s hyper-connected world, cybersecurity is more crucial than ever. Cyber threats are continually evolving, and businesses and individuals must stay vigilant to protect sensitive information. In this blog, we’ll cover the essentials of cybersecurity, its importance, and how you can start securing your digital assets today.
What is Cybersecurity?
Cybersecurity is the practice of safeguarding computers, servers, networks, and data from malicious attacks. It involves a set of processes, practices, and technologies designed to protect data integrity, confidentiality, and availability. Simply put, cybersecurity aims to protect anything connected to the internet from digital threats.
Why is Cybersecurity Important?
With the rise of online transactions, cloud storage, and remote work, cyber attacks have become more common and sophisticated. Data breaches can result in significant financial losses, damage to reputation, and loss of customer trust. Protecting against these attacks isn’t just an option anymore; it’s a necessity for businesses of all sizes.
Key Cyber Threats to Be Aware Of
Understanding the types of cyber threats can help you identify and prevent potential risks. Here are some of the most common cyber threats faced today:
Phishing AttacksPhishing is a social engineering attack where attackers trick users into revealing sensitive information, such as passwords or credit card details, usually by masquerading as a trusted entity.
MalwareMalware includes viruses, ransomware, and spyware designed to disrupt, damage, or gain unauthorized access to systems. It can be devastating for both individuals and organizations.
DDoS AttacksDistributed Denial of Service (DDoS) attacks flood a network with excessive requests, making it unavailable to legitimate users. DDoS attacks are a common tactic to disrupt business operations.
Man-in-the-Middle (MitM) AttacksIn a MitM attack, an attacker intercepts communication between two parties, often to steal data or impersonate one of the parties involved. These attacks can happen through public Wi-Fi or compromised email accounts.
Insider ThreatsSometimes, the threat comes from within an organization. Insider threats can be employees or associates who intentionally or unintentionally compromise security, often through careless handling of information.
Building a Strong Cybersecurity Foundation
Creating a secure environment requires a combination of preventive measures, awareness, and tools to mitigate risks. Here are some essential steps to strengthen cybersecurity:
1. Regularly Update Software and Systems
Outdated software can have vulnerabilities that cybercriminals exploit. Regular updates and patches protect against newly discovered threats and ensure your systems have the latest security features.
2. Use Strong, Unique Passwords
Weak passwords are easy targets for attackers. A strong password includes a mix of letters, numbers, and symbols. Also, using a password manager can help you store and manage complex passwords securely.
3. Implement Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to verify their identity through an additional factor, such as a text code, email link, or biometric scan. This makes it much harder for attackers to gain access even if they have your password.
4. Educate and Train Employees
Your employees are your first line of defense. Regular cybersecurity training helps them recognize phishing attempts, understand safe data handling, and respond appropriately to suspicious activities.
5. Backup Data Regularly
In case of a ransomware attack, having a recent backup can save you from losing critical data. Regular backups ensure that you can quickly restore data without having to pay a ransom or risk a long downtime.
6. Use a Firewall and Antivirus Software
Firewalls and antivirus software act as the first line of defense against cyber threats. Firewalls monitor incoming and outgoing network traffic, while antivirus software detects and removes malicious software before it can harm your system.
Cybersecurity for Businesses: A Necessity, Not an Option
For businesses, cybersecurity can determine success or failure. Not only are financial losses at stake, but also customer trust and regulatory compliance. Implementing a cybersecurity framework, such as the NIST Cybersecurity Framework, can help organizations systematically improve their cybersecurity posture.
Starting a Career in Cybersecurity
Cybersecurity is a booming field, and professionals with cybersecurity expertise are in high demand. If you’re considering a career in cybersecurity, now is the perfect time to start. Whether you’re interested in becoming an ethical hacker, a cybersecurity analyst, or a compliance officer, there’s a broad range of roles to explore.
Final Thoughts
Cybersecurity is everyone’s responsibility, from individuals to large corporations. Understanding the basics is the first step to protecting yourself and your organization. Start today by implementing simple measures to secure your devices and data and keep learning as the field continues to evolve.
For those looking to dive deeper, our Cybersecurity Course offers comprehensive training to help you build a robust cybersecurity foundation, taught by experts who live and breathe cybersecurity every day
At Shef Solutions LLC, we provide a comprehensive cybersecurity course designed to equip you with the skills needed to protect against modern cyber threats. Our program covers essential topics, including threat identification, risk management, network security, and ethical hacking, all taught by industry experts. Whether you're looking to start a career in cybersecurity or upskill in your current role, Shef Solutions LLC’s course offers hands-on training and practical insights to help you succeed in this fast-growing field.
0 notes
Text
10 Best Server Antivirus Software for Windows and Linux:

What is antivirus software:

Windows Antivirus Software:
Windows is amp lot point for malware set to its lot work. as an result antivirus Answers for Windows focus heavily on real-time protection malware Findion and firewall management. with numerous operators utilizing windows rdp to remotely approach systems ensuring the rdp help is good is appropriate. RDP vulnerabilities can be exploited if antivirus software does not patch system weaknesses leaving the Web vulnerable to attacks like ransomware and brute force.
Antivirus tools such as Windows Defender Bitdefender and Norton provide advanced Characteristics including scanning for known RDP vulnerabilities and blocking unauthorized remote access attempts. inch clear evolution amp vpn (virtual close web) run accessing windows rdp adds different certificate layer away encrypting the dealings preventing hackers from intercepting information
Real-time protection: Continuously monitors system activities and files for potential threats, blocking malware before it causes harm.
Scheduled and on-demand scanning: Offers the ability to scan files, folders, or the entire system periodically or manually, detecting and removing infections.
Firewalls and Web Protection: Safeguards users from online threats by blocking suspicious websites and monitoring network traffic.
Email Protection: Scans email attachments for potential malware.
Anti-phishing: Prevents phishing attempts designed to steal sensitive information.
Automatic Updates: Ensures the antivirus software regularly updates its virus definitions to protect against new threats.

Linux Antivirus Software:
Linux is mostly regarded arsenic further good than windows set to its and base hustler home. However Linux systems are not immune to malware specifically in environments where Linux RDP is used for remote access or when systems are Combined with Webs that have Windows devices. for linux antivirus software system unit system point clamav sophos and eset run prompt malware findion and remotion tools. While Linux does not have as many vulnerabilities as Windows antivirus software helps in scanning for threats in shared files email Hosts and RDP connections.
For administrators using Linux RDP for remote management it difficult to combine antivirus software with proper Web security practices such as using strong passwords and two-factor validation. adding amp vpn foster strengthens the certificate of linux rdp away encrypting the encounter and back the ip work fall photo to alien threats
File Scanning: Detects malware in files, especially for mixed environments.
Rootkit Detection: Finds and removes malicious software that can give unauthorized access to privileged system operations.
Network Protection: Protects Linux servers from attacks targeting web servers and services.
Cross-platform Protection: Scans for Windows malware, preventing its spread in mixed OS environments.
Popular antivirus solutions for Linux include ClamAV, Sophos, Comodo, and Bitdefender. While Linux has strong security, an antivirus is essential for protecting shared environments and preventing cross-infection from malware designed for other systems.
VPN and Free RDP:
Using Amp vpn inch bank with antivirus software system unit system is powerfully sound for both windows and linux systems. A VPN helps mask your online identity and encrypts Information making it harder for attackers to breach the system. for those look for fall rdp answers to the rdp help is good away employing antivirus software system unit system and amp vpn. Free RDP Hosts can be attractive to attackers extremely having these security layers in place is decisive.
In summary whether you’re using Windows RDP or Linux RDP combining antivirus software with VPN usage is important to protecting your remote Meetings and overall system security.
Real-time protection: Continuously monitors system activities and files for potential threats, blocking malware before it causes harm.
Scheduled and on-demand scanning: Offers the ability to scan files, folders, or the entire system periodically or manually, detecting and removing infections.
Firewalls and Web Protection: Safeguards users from online threats by blocking suspicious websites and monitoring network traffic.
Email Protection: Scans email attachments for potential malware.
Anti-phishing: Prevents phishing attempts designed to steal sensitive information.
Automatic Updates: Ensures the antivirus software regularly updates its virus definitions to protect against new threats.
Popular antivirus solutions for Windows include Norton, McAfee, Kaspersky, Bitdefender, and Windows Defender (now integrated with Windows 10 and 11 as Microsoft Defender). Windows Defender has evolved into a capable solution, offering comprehensive protection built into the operating system.
Installation Steps for Antivirus on Windows and Linux;
1. Installation Steps for Antivirus on Windows
Windows has several popular antivirus options, such as Windows Defender (pre-installed), Avast, Kaspersky, Norton, and more. Below are the general steps for installing third-party antivirus software on Windows:
Step 1: Download the Antivirus Software
Open your web browser.
Visit the official website of the antivirus provider (e.g., Avast, Norton, Kaspersky, etc.).
Locate the download button and click it to download the installer (usually an .exe file).
Step 2: Run the Installer
Once the download is complete, navigate to the downloaded file in your browser or Downloads folder.
Double-click the installer to run it.
If prompted by User Account Control (UAC), click Yes to allow the installation to proceed.
Step 3: Install the Antivirus
Follow the on-screen instructions in the setup wizard.
Choose between a Quick Install (recommended settings) or a Custom Install (where you can choose which components to install).
Accept the License Agreement and any terms of service.
If prompted, enter your product key or subscription information (for paid versions).
Click Install and wait for the installation process to finish.
Step 4: Configure and Update
Once installed, launch the antivirus software.
The software may ask you to update virus definitions immediately. Ensure you are connected to the internet and allow it to update.
Set your Scan Preferences (e.g., Full Scan, Quick Scan, Scheduled Scans) according to your needs.
Step 5: Run the First Scan
After installation, it’s a good practice to run a full system scan to ensure your system is virus-free.
Monitor the scan and review any threats found.
2. Installation Steps for Antivirus on Linux
Antivirus software on Linux is less commonly required than on Windows, but installing antivirus for Linux systems is useful in specific scenarios, such as file servers or dual-boot systems. Popular antivirus options for Linux include ClamAV, Sophos, and ESET.
Step 1: Choose the Antivirus
ClamAV is a free and open-source antivirus widely used on Linux.
Sophos and ESET offer more comprehensive protection but may require a subscription for full features.
Step 2: Install ClamAV (Free, Open-Source Antivirus)
For Debian/Ubuntu-based Distros:
Open the Terminal.
Update your package list with the following command:bash Copy code
sudo apt update
Install ClamAV:bash Copy code sudo apt install clamav clamav-daemon
Once installed, update the virus definitions:bash Copy code sudo freshclam
For Red Hat/CentOS-based Distros:
Open the Terminal.
Update the package manager:bash Copy code sudo yum update
Install ClamAV:bash Copy code sudo yum install clamav clamav-update
Update the virus definitions:bash Copy code sudo freshclam
Step 3: Install Sophos Antivirus for Linux (Proprietary)
Download the installer from the official Sophos website.
Unzip the downloaded file:bash Copy code tar -xzvf sav-linux-free-9.tgz
Change into the Sophos installation directory:bash Copy code cd sophos-av
Run the installer script:bash Copy code sudo ./install.sh
Follow the on-screen instructions to complete the installation.
Once installed, Sophos will automatically run in the background. You can use the command line to run scans.
Step 4: Configure and Run the First Scan
Configure the antivirus to run periodic scans and update virus definitions automatically.
For ClamAV, run a scan with:bash Copy code sudo clamscan -r /path/to/directory
For Sophos, run a scan with:bash Copy code savscan /path/to/directory
10 Best Antivirus software :
https://www.empowerict.com.au/wp-content/uploads/2020/06/Intercept-X-Endpoint-Blog.jpg
Sophos Intercept X for Server: A good choice for comprehensive security Bitdefender GravityZone Small Business Security is a comprehensive cybersecurity Answer Layouted for small businesses. it offers multi-layered security against malware ransomware phishing and different cyber threats. Featuring centralized management it ensures secure devices across multiple endpoints including desktops laptops and Hosts. with light usement and nominal affect along unit wise it provides iron certificate bespoke to the necessarily of home lot environments

Kaspersky Endpoint Security: A good choice for small to medium-sized businesses looking to secure their server environments Avast antivirus for linux is amp light and right home marriage to protect linux systems from malware and viruses. It provides real-time scanning customizable file system protection and Simplifyd updates. avast is generally gray inch Host environments to bear cross-platform infections specifically inch mixed-os webs. However Avast discontinued support for Linux desktop Editions extremely Operators may need to explore alternatives like ClamAV or Sophos.

McAfee Endpoint Security: A corporate antivirus solution that protects IT systems from malicious activities Mcafee end point certificate for linux provides arise security against malware and threats specifically marriage for linux environments. It Characteristics real-time scanning a firewall and Combined threat intelligence to ensure comprehensive security. the software system unit system offers focused room done mcafee epolicy orchestrator elective administrators to employment certificate policies and check endpoints expeditiously. Its lightweight Layout ensures minimal impact on system Effectiveness making it ideal for Hosts and workstations alike.
Norton 360 Deluxe: A good choice for its full-featured VPN and identity theft protection Norton 360 iron is amp lot certificate home that offers iron security against viruses malware and online threats. It includes Characteristics such as a firewall VPN for secure browsing password manager and cloud backup for files. marriage for leading to one devices it ensures secrecy and certificate over windows mack humanoid and ios plan. With real-time threat protection and a Operator-friendly Connection Norton 360 Deluxe is suitable for individuals and families.

F-Secure Protection Service for Business: A good choice for mobile and remote workforces F-Secure Protection Service for Business is a comprehensive security Answer Layouted to protect organizations from cyber threats. it offers real-time security against malware ransomware and different online dangers over endpoints hosts and versatile devices. With centralized management Simplifyd updates and advanced threat Findion F-Secure enables businesses to safeguard their sensitive Information efficiently. its operator-friendly link makes it light for it teams to check and point certificate ruless seamlessly.

RDS-Tools Advanced Security: A good choice for environments demanding stringent security measures Rds-tools arise certificate is amp iron software system unit system home marriage to burn the certificate of good base services (rds) and pole hosts. It provides administrators with comprehensive tools for managing Operator access Watching Meetings and Applying security policies. characteristics read encounter Check hustler action logging and customizable permissions help organizations charge play Information and Check value with certificate standards run maintaining amp coherent hustler encounter

Trend Micro Deep Security: A good choice for cloud and data center protection. Trend base run certificate is amp lot cybersecurity home marriage for natural practical and obscure environments. It provides advanced threat protection including anti-malware intrusion Findion and prevention firewall and integrity Watching. with its focused room solace run certificate simplifies certificate trading trading trading operations and value over different infrastructures ensuring iron security against smart cyber threats run enhancing lot unit effectiveness.

ESET Endpoint Protection Advanced: A good choice for multi-layered protection Eset end point security arise is amp lot certificate home marriage for businesses Problem iron security against malware ransomware and phishing attacks. It Characteristics advanced threat Findion real-time Watching and centralized management allowing IT administrators to oversee security across multiple devices. in gain eset’s multi-layered certificate Structure includes turn Check Web filtering and firewall characteristics ensuring amp proactive defence against evolving cyber threats run maintaining unit wise.

Conclusion:
Antivirus software is essential for maintaining security in systems that involve sensitive operations such as remote desktop access (RDP) or virtual private Webs (VPN) specifically in environments using Windows Host 2019. with the evolution be of rdp and vpn for right work and transmission these systems abide house targets for cybercriminals. as an result antivirus software acts as a difficult layer of defence by Finding and neutralizing threats before they can exploit vulnerabilities.
For Operators who rely on RDP (Remote Desktop Rules) the risk of unauthorized access and malware propagation is significant. light rdp services in particular often beat with security trade-offs as they beat lose chain coding making systems foster run to attacks such as arsenic as arsenic as savage force ransomware and theft. Using antivirus software in this case mitigates some of these risks by continuously scanning for malicious activities ensuring that even in a potentially less secure RDP environment additional defenses are in place.
When accessing RDP from a Windows Host 2019 system antivirus software Layouted for Windows environments is highly recommended. Windows Host 2019 is often grey in stick environments making it link inch nursing deal head for develop place threats (apts) and disparate forward attacks. The best antivirus Answers for this setup would include Characteristics like behavior-based Findion firewall management and system integrity Watching. this is specifically as the system is prospective to be run organizational and uses integrating antivirus with a vpn (virtual end web) setup is disparate layer of certificate. While VPNs are essential for encrypting Information and securing communications over public or less secure Webs they do not inherently protect against malware phishing or direct cyberattacks on the endpoint. antivirus software system unit system unit complements vpns out ensuring that bleak files and software system unit system unit are from force on the system. This is decisive when accessing RDP Meetings over a VPN as it secures both the communication channel and the endpoints. For individuals or organizations looking for the best RDP Answers with antivirus integration several premium antivirus programs offer comprehensive protection including RDP-specific security Characteristics like two-factor validation (2FA) and intrusion Findion. investing in high-quality antivirus software system unit system unit ensures that rdp and vpn work lie right point against develop cyber threats.
0 notes
Text
Ensuring Office Network Safety for Businesses of All Sizes

In today’s digital landscape, businesses of all sizes depend on their network systems to handle daily operations. From small enterprises to large corporations, safeguarding the office network is essential to avoid cyber threats, data breaches and other security risks. Here are several key measures businesses can adopt to protect their networks. Enforce Strong Password Guidelines One of the most straightforward and effective ways to secure a network is by enforcing strict password guidelines. Employees should be required to create passwords that use a combination of uppercase and lowercase letters, numbers and symbols. It’s also essential that they change these passwords regularly and avoid reusing them across platforms. Multi-factor authentication (MFA) provides an extra layer of security, requiring additional verification steps beyond just a password. Regularly Update Systems and Software Outdated systems and applications often have unpatched vulnerabilities, making them prime targets for cybercriminals. It is essential that businesses consistently update all software, including operating systems, antivirus programs and firewalls. By enabling automatic updates, businesses can ensure these patches are applied without delay, reducing the risk of unpatched software becoming a security hole. Integrating solutions like WatchGuard Online can enhance your network’s security by providing advanced threat detection and management tools. Utilise Firewalls and Antivirus Programs Firewalls act as a crucial defence mechanism by regulating network traffic and preventing unauthorised access. A properly configured firewall can help mitigate the risks posed by cyber threats. In addition, installing and maintaining reliable antivirus software across all network devices helps to identify and remove malware before it can spread within the network. Monitor Network Activity Regularly Frequent monitoring of network activity is key to identifying unusual behaviour that may indicate a security breach. Network monitoring tools help businesses track data transfers and detect any irregular activities, such as multiple failed login attempts or unexpected file changes. Regular security assessments, such as vulnerability scans and penetration testing, can help uncover weaknesses that need to be addressed. Educate Employees on Security Practices Many security breaches result from human error. Providing employees with training on best practices for network security can significantly reduce the risk of these errors. Training should include recognising phishing scams, avoiding suspicious attachments, and following protocols for reporting potential threats. Employees should also be informed about the use of personal devices and software in the workplace to minimise risks. Secure Remote Connections With more employees working remotely, ensuring secure access to the office network is more critical than ever. Using virtual private networks (VPNs) allows remote workers to access the network through a secure, encrypted connection. Businesses should also enforce policies requiring the use of trusted devices and secure internet connections, avoiding public Wi-Fi networks whenever possible. Develop a Data Backup and Recovery Strategy Even the most robust security measures can’t prevent all incidents. Businesses should create a data backup and recovery strategy to ensure that valuable data can be restored in case of a breach or cyber-attack. Regular data backups should be performed and stored in a secure location, such as off-site or using a cloud-based service, to enhance protection. Conclusion Protecting an office network is crucial for maintaining business continuity and safeguarding sensitive data. These measures are adaptable, ensuring businesses of any size can maintain a secure and protected network. Read the full article
0 notes
Text
Repair Your Computer in Ranchi
Introduction
In today’s digital age, computers have become indispensable tools in our daily lives. From professional work to personal entertainment, a malfunctioning computer can disrupt everything. When your computer faces issues, finding a reliable repair service becomes crucial. In Ranchi, a city known for its burgeoning tech scene, several options are available for getting your computer back in top shape.
Common Computer Issues
Hardware Problems Broken Screens One of the most common hardware issues is a broken screen. Whether it's a cracked display or dead pixels, a damaged screen can render your computer unusable. Luckily, many repair shops in Ranchi specialize in screen replacements and repairs.
Overheating Overheating is another frequent problem, often caused by dust buildup or malfunctioning cooling systems. An overheating computer can lead to performance issues and potential hardware damage if not addressed promptly.
Software Problems System Crashes Software issues, such as frequent system crashes or blue screens, can be frustrating. These problems often require a detailed analysis to identify the root cause, which could be faulty software, outdated drivers, or corrupted files.
Malware and Viruses Malware and viruses can severely impact your computer’s performance and security. Regular scans and updates can help, but sometimes professional intervention is needed to remove persistent threats.
Choosing the Right Computer Repair Service
Certifications and Expertise When selecting a repair service, it's essential to check for certifications and the technician's expertise. Certified professionals are more likely to provide high-quality service and adhere to industry standards.
Customer Reviews and Reputation Customer reviews and testimonials can offer valuable insights into a repair service’s reliability and customer satisfaction. Look for feedback from previous clients to gauge the quality of service.
Service Guarantees and Warranties A good repair service should offer guarantees or warranties on their work. This ensures that if the problem recurs, you can return for further assistance without incurring additional costs.
Comparing Services and Pricing When choosing a repair shop, compare their services and pricing. Some shops might offer bundled services or discounts for multiple repairs, so it's worth exploring all options to get the best deal.
DIY Computer Repairs
Basic Troubleshooting Tips For minor issues, such as slow performance or connectivity problems, you might be able to perform basic troubleshooting yourself. Restarting your computer, checking for loose connections, or running antivirus scans can sometimes resolve these issues.
When to Seek Professional Help If you encounter complex problems or if your DIY efforts don’t yield results, it’s time to consult a professional. Persistent issues or significant hardware damage typically require expert intervention.
Costs of Computer Repairs
Typical Costs for Common Repairs Repair costs can vary widely based on the type of issue and the repair shop. For example, screen replacements might cost between ₹2000 and ₹5000, while more extensive repairs like motherboard replacements could be more expensive.
Factors Affecting Repair Costs Several factors can influence repair costs, including the complexity of the problem, the cost of replacement parts, and the technician’s labor charges. Always ask for a detailed estimate before agreeing to repairs.
How to Maintain Your Computer
Regular Cleaning and Updates To prevent common issues, regularly clean your computer and keep it updated. Dust can cause overheating, and software updates help protect against security vulnerabilities.
Best Practices for Avoiding Common Issues Adopting good habits, such as not overloading your computer with unnecessary software and avoiding suspicious links, can help minimize the risk of encountering major problems.
Conclusion
Computer problems can be stressful, but knowing where to turn for help can make all the difference. In Ranchi, you have access to various skilled repair services and resources to get your computer back in working order. Remember to choose a reputable repair shop, consider DIY options for minor issues, and maintain your computer to avoid future problems.
FAQs
What should I do if my computer won't turn on? First, check the power supply and connections. If everything seems fine, it might be a hardware issue that requires professional diagnosis.
How can I prevent my computer from overheating? Ensure proper ventilation, regularly clean the internal components, and use a cooling pad if necessary.
Is it worth repairing an old computer? It depends on the extent of the damage and the cost of repairs compared to the price of a new computer. Sometimes upgrading certain components might be more cost-effective.
How can I find a trustworthy repair technician in Ranchi? Look for certified technicians, read customer reviews, and ask for recommendations from friends or family.
What are some signs that I need professional computer repair? Signs include persistent system crashes, slow performance, strange noises, or failure to start up.
#RepairYourComputer#RanchiTech#ComputerRepair#RanchiServices#TechSupportRanchi#ITSupportRanchi#RanchiComputers#GadgetRepair#ComputerFix#RanchiRepairShop#LocalTechHelp#TechSolutionRanchi#LaptopRepairRanchi#RanchiITServices#ElectronicsRepair#PCRepair
0 notes
Note
OBSERVER SENT A FUCKIGNG EYE YOUR WAY MAN 😭💔
-🪩
What?!
[ANTIVIRUS SCAN INITIATED. PLEASE WAIT FOR RESULTS.]
. . .
[NO FOREIGN PROGRAMS DETECTED]
Huh. I feel fine, so... perhaps it never reached me?
1 note
·
View note
Text
Best Practices For Workstation Security
Best Practices for Workstation Security
Table of Contents
Importance of Workstation Security
Best Practices for Ensuring Workstation Security
Key Takeaways
Conclusion
FAQs
Importance of Workstation Security
Imagine the frustration of battling with a malware-infected workstation. The tedious task of locating and removing malicious files can consume hours, leading many IT professionals to opt for a complete "clean install" of the operating system. However, this method results in the loss of unsaved data. Such issues highlight the critical need for robust workstation security.
Cyberattacks may seem distant until they strike close to home. If you own or use a workstation, you are a potential target for cybercriminals. Just as you would lock your physical workstation to prevent unauthorized access, securing your virtual workstation is equally essential. Effective cybersecurity measures can thwart attackers who use various methods to infiltrate systems, ensuring that your workstation remains safe and operational.
Best Practices for Ensuring Workstation Security
Implement a Proactive Security Program
A comprehensive security suite is vital for defending your workstation from network threats, malware, spyware, and viruses. Modern security software should go beyond basic antivirus protection. It must also recognize and block deceptive software that masquerades as legitimate applications, such as those claiming to offer discounts but tracking your online activity.
For systems provided by your organization, ensure that the IT department's security suite is activated and up-to-date. If you are using your own system, select a reliable security suite, activate it, and perform a full system scan to identify and neutralize any threats.
Keep Antivirus Software Updated
The prevalence of online malware and viruses necessitates the use of up-to-date antivirus software. Viruses can severely damage your computer, corrupt essential files, and degrade performance. Antivirus software helps protect your system by detecting and eliminating threats. Many reputable antivirus programs offer automatic updates to safeguard against new and emerging threats. Regular virus scans are crucial to maintaining your workstation's security.
Regularly Back Up Data
Data backup is a critical component of workstation security. While your IT team may handle system and application updates, your personal data, including emails, documents, images, and videos, is irreplaceable. Ensure that you regularly back up important files. Cloud storage solutions can be used, but it's wise to have a secondary cloud-to-cloud backup if your company uses SaaS applications. In case of a system infection or hardware failure, your backed-up data will be safe, allowing you to quickly recover and resume work without the hassle of dealing with malware.
Set Up Automatic Screen Locks
Setting up an automatic screen lock is a simple yet effective way to enhance security. Configure your workstation to lock automatically after a period of inactivity—ideally, 15 minutes or less, depending on your environment. This prevents unauthorized access if you step away from your desk. Ensure that your screen lock password is strong and not easily guessable, avoiding simple or personal information-based passwords.
Enforce Application Control Policies
Application control policies help protect your workstation by regulating which applications can be installed and run. By establishing and enforcing these policies, you ensure that only approved applications are allowed, reducing the risk of malware. Maintain an updated list of permitted applications and regularly review and enforce these policies to prevent unauthorized software from compromising your system.
Key Takeaways
Securing your workstation is crucial, as it stores valuable personal and professional data.
Cyberattacks, such as data breaches or ransomware, can lead to significant financial losses, reputational damage, and customer attrition.
Implementing best practices like proactive security measures, antivirus updates, data backups, screen locks, and application control policies can greatly enhance workstation security.
These practices should complement, not replace, comprehensive cybersecurity solutions.
Conclusion
Your workstation is a central hub for your professional activities, and protecting it is vital. Implementing a proactive security approach helps safeguard against potential cyber threats. By following the best practices outlined above, you can significantly enhance your workstation's defenses and prevent unauthorized access.
For robust workstation security, consider advanced cybersecurity solutions offered by experts like iBovi. They provide a range of services, including malware detection, cybersecurity monitoring, device theft protection, and vulnerability management, often with a 30-day free trial.
FAQs
How can I improve the security of my workstations? Follow the best practices mentioned, such as implementing a proactive security program, keeping antivirus software updated, regularly backing up data, setting up automatic screen locks, and enforcing application control policies. Additionally, invest in comprehensive cybersecurity solutions for enhanced protection.
What can happen without workstation security? Without proper workstation security, you risk data breaches, system infections, and unauthorized access, which can lead to data loss, financial costs, and operational downtime. For businesses, maintaining secure workstations is crucial for avoiding disruptions and safeguarding sensitive information.
0 notes