#AI for IoT
Explore tagged Tumblr posts
Text
The Brave Little Toaster

Picks and Shovels is a new, standalone technothriller starring Marty Hench, my two-fisted, hard-fighting, tech-scam-busting forensic accountant. You can pre-order it on my latest Kickstarter, which features a brilliant audiobook read by Wil Wheaton.

The AI bubble is the new crypto bubble: you can tell because the same people are behind it, and they're doing the same thing with AI as they did with crypto – trying desperately to find a use case to cram it into, despite the yawning indifference and outright hostility of the users:
https://pluralistic.net/2023/03/09/autocomplete-worshippers/#the-real-ai-was-the-corporations-that-we-fought-along-the-way
This week on the excellent Trashfuture podcast, the regulars – joined by 404 Media's Jason Koebler – have a hilarious – as in, I was wheezing with laughter! – riff on this year's CES, where companies are demoing home appliances with LLMs built in:
https://www.podbean.com/media/share/pb-hgi6c-179b908
Why would you need a chatbot in your dishwasher? As it turns out, there's a credulous, Poe's-law-grade Forbes article that lays out the (incredibly stupid) case for this (incredibly stupid) idea:
https://www.forbes.com/sites/bernardmarr/2024/03/29/generative-ai-is-coming-to-your-home-appliances/
As the Trashfuturians mapped out this new apex of the AI hype cycle, I found myself thinking of a short story I wrote 15 years ago, satirizing the "Internet of Things" hype we were mired in. It's called "The Brave Little Toaster", and it was published in MIT Tech Review's TRSF anthology in 2011:
http://bestsf.net/trsf-the-best-new-science-fiction-technology-review-2011/
The story was meant to poke fun at the preposterous IoT hype of the day, and I recall thinking that creating a world of talking appliance was the height of Philip K Dickist absurdism. Little did I dream that a decade and a half later, the story would be even more relevant, thanks to AI pump-and-dumpers who sweatily jammed chatbots into kitchen appliances.
So I figured I'd republish The Brave Little Toaster; it's been reprinted here and there since (there's a high school English textbook that included it, along with a bunch of pretty fun exercises for students), and I podcasted it back in the day:
https://ia803103.us.archive.org/35/items/Cory_Doctorow_Podcast_212/Cory_Doctorow_Podcast_212_Brave_Little_Toaster.mp3
A word about the title of this story. It should sound familiar – I nicked it from a brilliant story by Tom Disch that was made into a very weird cartoon:
https://www.youtube.com/watch?v=I8C_JaT8Lvg
My story is one of several I wrote by stealing the titles of other stories and riffing on them; they were very successful, winning several awards, getting widely translated and reprinted, and so on:
https://locusmag.com/2012/05/cory-doctorow-a-prose-by-any-other-name/
All right, on to the story!
One day, Mister Toussaint came home to find an extra 300 euros' worth of groceries on his doorstep. So he called up Miz Rousseau, the grocer, and said, "Why have you sent me all this food? My fridge is already full of delicious things. I don't need this stuff and besides, I can't pay for it."
But Miz Rousseau told him that he had ordered the food. His refrigerator had sent in the list, and she had the signed order to prove it.
Furious, Mister Toussaint confronted his refrigerator. It was mysteriously empty, even though it had been full that morning. Or rather, it was almost empty: there was a single pouch of energy drink sitting on a shelf in the back. He'd gotten it from an enthusiastically smiling young woman on the metro platform the day before. She'd been giving them to everyone.
"Why did you throw away all my food?" he demanded. The refrigerator hummed smugly at him.
"It was spoiled," it said.
#
But the food hadn't been spoiled. Mister Toussaint pored over his refrigerator's diagnostics and logfiles, and soon enough, he had the answer. It was the energy beverage, of course.
"Row, row, row your boat," it sang. "Gently down the stream. Merrily, merrily, merrily, merrily, I'm offgassing ethelyne." Mister Toussaint sniffed the pouch suspiciously.
"No you're not," he said. The label said that the drink was called LOONY GOONY and it promised ONE TRILLION TIMES MORE POWERFUL THAN ESPRESSO!!!!!ONE11! Mister Toussaint began to suspect that the pouch was some kind of stupid Internet of Things prank. He hated those.
He chucked the pouch in the rubbish can and put his new groceries away.
#
The next day, Mister Toussaint came home and discovered that the overflowing rubbish was still sitting in its little bag under the sink. The can had not cycled it through the trapdoor to the chute that ran to the big collection-point at ground level, 104 storeys below.
"Why haven't you emptied yourself?" he demanded. The trashcan told him that toxic substances had to be manually sorted. "What toxic substances?"
So he took out everything in the bin, one piece at a time. You've probably guessed what the trouble was.
"Excuse me if I'm chattery, I do not mean to nattery, but I'm a mercury battery!" LOONY GOONY's singing voice really got on Mister Toussaint's nerves.
"No you're not," Mister Toussaint said.
#
Mister Toussaint tried the microwave. Even the cleverest squeezy-pouch couldn't survive a good nuking. But the microwave wouldn't switch on. "I'm no drink and I'm no meal," LOONY GOONY sang. "I'm a ferrous lump of steel!"
The dishwasher wouldn't wash it ("I don't mean to annoy or chafe, but I'm simply not dishwasher safe!"). The toilet wouldn't flush it ("I don't belong in the bog, because down there I'm sure to clog!"). The windows wouldn't retract their safety screen to let it drop, but that wasn't much of a surprise.
"I hate you," Mister Toussaint said to LOONY GOONY, and he stuck it in his coat pocket. He'd throw it out in a trash-can on the way to work.
#
They arrested Mister Toussaint at the 678th Street station. They were waiting for him on the platform, and they cuffed him just as soon as he stepped off the train. The entire station had been evacuated and the police wore full biohazard containment gear. They'd even shrinkwrapped their machine-guns.
"You'd better wear a breather and you'd better wear a hat, I'm a vial of terrible deadly hazmat," LOONY GOONY sang.
When they released Mister Toussaint the next day, they made him take LOONY GOONY home with him. There were lots more people with LOONY GOONYs to process.
#
Mister Toussaint paid the rush-rush fee that the storage depot charged to send over his container. They forklifted it out of the giant warehouse under the desert and zipped it straight to the cargo-bay in Mister Toussaint's building. He put on old, stupid clothes and clipped some lights to his glasses and started sorting.
Most of the things in container were stupid. He'd been throwing away stupid stuff all his life, because the smart stuff was just so much easier. But then his grandpa had died and they'd cleaned out his little room at the pensioner's ward and he'd just shoved it all in the container and sent it out the desert.
From time to time, he'd thought of the eight cubic meters of stupidity he'd inherited and sighed a put-upon sigh. He'd loved Grandpa, but he wished the old man had used some of the ample spare time from the tail end of his life to replace his junk with stuff that could more gracefully reintegrate with the materials stream.
How inconsiderate!
#
The house chattered enthusiastically at the toaster when he plugged it in, but the toaster said nothing back. It couldn't. It was stupid. Its bread-slots were crusted over with carbon residue and it dribbled crumbs from the ill-fitting tray beneath it. It had been designed and built by cavemen who hadn't ever considered the advantages of networked environments.
It was stupid, but it was brave. It would do anything Mister Toussaint asked it to do.
"It's getting hot and sticky and I'm not playing any games, you'd better get me out before I burst into flames!" LOONY GOONY sang loudly, but the toaster ignored it.
"I don't mean to endanger your abode, but if you don't let me out, I'm going to explode!" The smart appliances chattered nervously at one another, but the brave little toaster said nothing as Mister Toussaint depressed its lever again.
"You'd better get out and save your ass, before I start leaking poison gas!" LOONY GOONY's voice was panicky. Mister Toussaint smiled and depressed the lever.
Just as he did, he thought to check in with the flat's diagnostics. Just in time, too! Its quorum-sensors were redlining as it listened in on the appliances' consternation. Mister Toussaint unplugged the fridge and the microwave and the dishwasher.
The cooker and trash-can were hard-wired, but they didn't represent a quorum.
#
The fire department took away the melted toaster and used their axes to knock huge, vindictive holes in Mister Toussaint's walls. "Just looking for embers," they claimed. But he knew that they were pissed off because there was simply no good excuse for sticking a pouch of independently powered computation and sensors and transmitters into an antique toaster and pushing down the lever until oily, toxic smoke filled the whole 104th floor.
Mister Toussaint's neighbors weren't happy about it either.
But Mister Toussaint didn't mind. It had all been worth it, just to hear LOONY GOONY beg and weep for its life as its edges curled up and blackened.
He argued mightily, but the firefighters refused to let him keep the toaster.
#
If you enjoyed that and would like to read more of my fiction, may I suggest that you pre-order my next novel as a print book, ebook or audiobook, via the Kickstarter I launched yesterday?
https://www.kickstarter.com/projects/doctorow/picks-and-shovels-marty-hench-at-the-dawn-of-enshittification?ref=created_projects

Check out my Kickstarter to pre-order copies of my next novel, Picks and Shovels!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/01/08/sirius-cybernetics-corporation/#chatterbox

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#brave little toaster#iot#internet of things#internet of shit#fiction#short fiction#short stories#thomas m disch#science fiction#sf#gen ai#ai#generative ai#llms#chatbots#stochastic parrots#mit tech review#tech review#trashfuture#forbes#ces#torment nexus#pluralistic
223 notes
·
View notes
Text
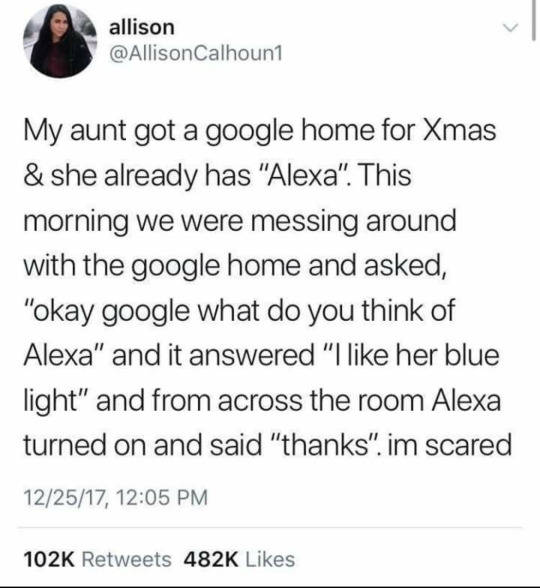
#memes#meme#throwback#lol#funny#lol memes#funny memes#funny meme haha#funny stuff#alexa#google#ai#the robots#they can talk to each other#compliment#complimenting strangers#so cute#cute#lmao#spy devices#iot#iotsolutions
65 notes
·
View notes
Text
"In the age of smart fridges, connected egg crates, and casino fish tanks doubling as entry points for hackers, it shouldn’t come as a surprise that sex toys have joined the Internet of Things (IoT) party.
But not all parties are fun, and this one comes with a hefty dose of risk: data breaches, psychological harm, and even physical danger.
Let’s dig into why your Bluetooth-enabled intimacy gadget might be your most vulnerable possession — and not in the way you think.
The lure of remote-controlled intimacy gadgets isn’t hard to understand. Whether you��re in a long-distance relationship or just like the convenience, these devices have taken the market by storm.
According to a 2023 study commissioned by the U.K.’s Department for Science, Innovation, and Technology (DSIT), these toys are some of the most vulnerable consumer IoT products.
And while a vibrating smart egg or a remotely controlled chastity belt might sound futuristic, the risks involved are decidedly dystopian.
Forbes’ Davey Winder flagged the issue four years ago when hackers locked users into a chastity device, demanding a ransom to unlock it.
Fast forward to now, and the warnings are louder than ever. Researchers led by Dr. Mark Cote found multiple vulnerabilities in these devices, primarily those relying on Bluetooth connectivity.
Alarmingly, many of these connections lack encryption, leaving the door wide open for malicious third parties.
If you’re picturing some low-stakes prank involving vibrating gadgets going haywire, think again. The risks are far graver.
According to the DSIT report, hackers could potentially inflict physical harm by overheating a device or locking it indefinitely. Meanwhile, the psychological harm could stem from sensitive data — yes, that kind of data — being exposed or exploited.
A TechCrunch exposé revealed that a security researcher breached a chastity device’s database containing over 10,000 users’ information. That was back in June, and the manufacturer still hasn’t addressed the issue.
In another incident, users of the CellMate connected chastity belt reported hackers demanding $750 in bitcoin to unlock devices. Fortunately, one man who spoke to Vice hadn’t been wearing his when the attack happened. Small mercies, right?
These aren’t isolated events. Standard Innovation Corp., the maker of the We-Vibe toy, settled for $3.75 million in 2017 after it was discovered the device was collecting intimate data without user consent.
A sex toy with a camera was hacked the same year, granting outsiders access to its live feed.
And let’s not forget: IoT toys are multiplying faster than anyone can track, with websites like Internet of Dongs monitoring the surge.
If the thought of a connected chastity belt being hacked makes you uneasy, consider this: sex toys are just a small piece of the IoT puzzle.
There are an estimated 17 billion connected devices worldwide, ranging from light bulbs to fitness trackers — and, oddly, smart egg crates.
Yet, as Microsoft’s 2022 Digital Defense Report points out, IoT security is lagging far behind its software and hardware counterparts.
Hackers are opportunistic. If there’s a way in, they’ll find it. Case in point: a casino lost sensitive customer data after bad actors accessed its network through smart sensors in a fish tank.
If a fish tank isn’t safe, why would we expect a vibrating gadget to be?
Here’s where the frustration kicks in: these vulnerabilities are preventable.
The DSIT report notes that many devices rely on unencrypted Bluetooth connections or insecure APIs for remote control functionality.
Fixing these flaws is well within the reach of manufacturers, yet companies routinely fail to prioritize security.
Even basic transparency around data collection would be a step in the right direction. Users deserve to know what’s being collected, why, and how it’s protected. But history suggests the industry is reluctant to step up.
After all, if companies like Standard Innovation can get away with quietly siphoning off user data, why would smaller players bother to invest in robust security?
So, what’s a smart-toy enthusiast to do? First, ask yourself: do you really need your device to be connected to an app?
If the answer is no, then maybe it’s best to go old school. If remote connectivity is a must, take some precautions.
Keep software updated: Ensure both the device firmware and your phone’s app are running the latest versions. Updates often include critical security patches.
Use secure passwords: Avoid default settings and choose strong, unique passwords for apps controlling your devices.
Limit app permissions: Only grant the app the bare minimum of permissions needed for functionality.
Vet the manufacturer: Research whether the company has a history of addressing security flaws. If they’ve been caught slacking before, it’s a red flag.
The conversation around sex toy hacking isn’t just about awkward headlines — it’s about how we navigate a world increasingly dependent on connected technology. As devices creep further into every corner of our lives, from the bedroom to the kitchen, the stakes for privacy and security continue to rise.
And let’s face it: there’s something uniquely unsettling about hackers turning moments of intimacy into opportunities for exploitation.
If companies won’t take responsibility for protecting users, then consumers need to start asking tough questions — and maybe think twice before connecting their pleasure devices to the internet.
As for the manufacturers? The message is simple: step up or step aside.
No one wants to be the next headline in a tale of hacked chastity belts and hijacked intimacy. And if you think that’s funny, just wait until your light bulb sells your Wi-Fi password.
This is where IoT meets TMI. Stay connected, but stay safe."
https://thartribune.com/government-warns-couples-that-sex-toys-remain-a-tempting-target-for-hackers-with-the-potential-to-be-weaponized/
#iot#I only want non-smart devices#I don't want my toilet to connect to the internet#seriously#smart devices#ai#anti ai#enshittification#smart sex toys
26 notes
·
View notes
Text

#robot#robotics#robots#technology#art#engineering#arduino#d#electronics#transformers#mecha#tech#toys#anime#robotic#scifi#gundam#ai#drawing#artificialintelligence#digitalart#innovation#illustration#electrical#automation#robotica#diy#design#arduinoproject#iot
33 notes
·
View notes
Text
Simplify Decentralized Payments with a Unified Cash Collection Application
In a world where financial accountability is non-negotiable, Atcuality provides tools that ensure your field collections are as reliable as your core banking or ERP systems. Designed for enterprises that operate across multiple regions or teams, our cash collection application empowers agents to accept, log, and report payments using just their mobile devices. With support for QR-based transactions, offline syncing, and instant reconciliation, it bridges the gap between field activities and central operations. Managers can monitor performance in real-time, automate reporting, and minimize fraud risks with tamper-proof digital records. Industries ranging from insurance to public sector utilities trust Atcuality to improve revenue assurance and accelerate their collection cycles. With API integrations, role-based access, and custom dashboards, our application becomes the single source of truth for your field finance workflows.
#ai applications#artificial intelligence#augmented and virtual reality market#augmented reality#website development#emailmarketing#information technology#web design#web development#digital marketing#cash collection application#custom software development#custom software services#custom software solutions#custom software company#custom software design#custom application development#custom app development#application development#applications#iot applications#application security#application services#app development#app developers#app developing company#app design#software development#software testing#software company
4 notes
·
View notes
Text

Teamwork makes the dream work! Collaborate with us and create something new. Tap into innovation today!
👉🌐 https://www.pranathiss.com 👉📧 [email protected] 👉📲 +1 732 333 3037
#artificialintelligence#ai#machinelearning#technology#datascience#generativeai#innovation#tech#deeplearning#business#iot
8 notes
·
View notes
Text

Robotic Process Automation (RPA) enhances business efficiency by automating repetitive tasks, freeing up employees for more strategic work. It improves accuracy, reduces operational costs, and boosts productivity across industries.
#artificialintelligence#ai#machinelearning#aiart#digitalart#technology#art#aiartcommunity#midjourney#datascience#generativeart#innovation#tech#deeplearning#python#midjourneyart#aiartwork#aiartist#programming#robotics#bigdata#artoftheday#coding#aiartists#digitalartist#business#iot#midjourneyai#artwork#stablediffusion
3 notes
·
View notes
Text

Navigating the Ethical Integration of Artificial Intelligence in Higher Education – speaker @olingataeed at The Institute of Business Executives (South Africa) www.businessexecutives.net
3 notes
·
View notes
Text

#owncoin#coin#cryptocoin#crypto#token#newtoken#cryptocurrency#bitcoin#altcoin#india#vizag#hyderabad#bangalore#mumbai#miningapp#startup#startups#startupindia#dc#blockchain#ai#iot#bitcoins
2 notes
·
View notes
Text
WordPress Security Services Tailored to Your Business Needs
Atcuality understands that every WordPress website has unique security needs. Our specialized WordPress security services provide customized solutions to safeguard your website from malicious attacks, unauthorized access, and technical vulnerabilities. Whether you own a blog, corporate website, or online store, our comprehensive approach includes malware scanning, vulnerability patching, firewall implementation, and site backups. Atcuality’s team of security professionals works tirelessly to monitor and eliminate threats before they can impact your business. With advanced tools and strategies like SSL encryption and uptime monitoring, we ensure your website operates securely while maintaining peak performance. Cyber threats evolve daily, but with Atcuality, you can stay one step ahead. Don’t let your website become a target—secure your site and maintain customer trust with our proven WordPress security solutions.
#seo marketing#seo services#artificial intelligence#digital marketing#iot applications#seo company#seo agency#amazon web services#azure cloud services#ai powered application#ai applications#ai app development#virtual reality#vr development#vr games#wordpress#web developers#web development#web design#web developing company#website developer near me#wordpress development#web hosting#website#augmented and virtual reality market#augmented human c4 621#augmented intelligence#augmented reality#iot#iotsolutions
4 notes
·
View notes
Text
#NXP Semiconductors#AI#capabilities#intelligent#AI_solutions#IoT.#powerelectronics#powermanagement#powersemiconductor
5 notes
·
View notes
Text
theredditblog
Iam paulalice working for theredditblog as PR consultant.With more than 6 year’s experience in PR and Digital Industry,helping teams to achieve goals by streamlining the process.
#technology#web#IT#software#hardware#cybersecurity#artificial intelligence#AI#Internet of Things#IoT#tech trends#how-to guides#tutorials#gadgets#gadget reviews#tech news#innovation#digital marketing#telecommunications#science#tech blog#tech education#freelance writing#guest post#tech community#emerging technology#latest technology#tech insights#tech articles#tech enthusiasts
3 notes
·
View notes
Text

Boost Engineering Revenue & Productivity by 40% with AI
Unlock a 40% boost in engineering revenue and productivity with AI-powered strategies. Learn how AI is transforming the engineering sector.
#AI#Engineering#DigitalTransformation#AIInnovation#Industry40#SmartEngineering#Automation#AIforBusiness#EngineeringGrowth#CloudComputing#MachineLearning#IoT
2 notes
·
View notes
Text
𝐇𝐨𝐰 𝐀𝐈 𝐚𝐧𝐝 5𝐆 𝐀𝐫𝐞 𝐓𝐫𝐚𝐧𝐬𝐟𝐨𝐫𝐦𝐢𝐧𝐠 𝐁𝐮𝐬𝐢𝐧𝐞𝐬𝐬 𝐆𝐫𝐨𝐰𝐭𝐡 | 𝐓𝐡𝐞 𝐅𝐮𝐭𝐮𝐫𝐞 𝐨𝐟 𝐈𝐧𝐧𝐨𝐯𝐚𝐭𝐢𝐨𝐧
The fusion of AI and 5G is revolutionizing businesses worldwide. With ultra-fast connectivity and real-time data analytics, companies are unlocking new opportunities for efficiency, automation, and customer engagement.
Learn how AI and 5G work together to:
Enhance real-time decision-making
Improve IoT connectivity for smart industries
Power AI-driven automation and predictive analytics
Personalize customer experiences like never before
From smart factories to AI-powered healthcare, discover how these technologies are shaping the future of business. Don't miss out—watch now - https://youtu.be/w1nDoqzVj0g
Follow for more tech insights.
#ai#5g#businessgrowth#innovation#futuretech#iot#automation#digitaltransformation#smarttechnology#bigdata
2 notes
·
View notes
Text

Acadecraft Partners with Wadhwani Foundation's Government Digital Transformation Initiative to Develop eLearning Courses
#digitaltransformation#technology#innovation#business#digitalmarketing#ai#digital#artificialintelligence#software#machinelearning#automation#businessgrowth#tech#iot#techinnovation#bigdata#cybersecurity#cloud#data#cloudcomputing#smallbusiness#customerexperience#marketing#sap#webdevelopment#erp#blockchain#analytics#ecommerce#datascience
2 notes
·
View notes
