#what kind of malware is this
Explore tagged Tumblr posts
Text
WHY DOES FACEBOOK KEEP AUTO-INSTALLING ON MY PHONE??????
I've desinstalled it 2 times and deleted all the updates & etc but it keeps coming back
#what kind of malware is this#everything else seems fine#idk how this happened#maybe I shouldn't haven't downloaded roms from piracy websites +2)2+393+_93+8874)94#I doubt that's the issue though?? i've been doing this for years#maybe it's just a new default feature?#morbposting
10 notes
·
View notes
Text

Malware 23 concept from my old account, with a recolor and slightly edited version of GC Malware too
Azmuth managed to help him when he came back to deal with the Ben situation. He was still pretty upset about how long it took him to get around to it, but ya know, they talked about it. Mal 23 is a lab assistant to Azmuth, and is friends with that universe's Myaxx and Tetrax. He isn't much for fighting, and tries to avoid confrontation for his own sanity, cause despite it all, if he looses his temper it's still pretty hard for him to cool off. he needs a tantrum hole /j
Ben Prime was startled when he first met him and was incredibly wary of him. Ben 23 thinks he's kind of a dork ass looser
#ben 10#universe 23#ben 10 malware#he exclusively goes by mal#thats what he tells everyone his name is#Ben 23 doesnt even know his fullname is malware he only knows him as Mal#Azmuth calls him Mal#however#he calls him Malware still but only in that ''when youre in trouble and your parent calls you by your full name'' kind of way#my art
65 notes
·
View notes
Text
community college is so funny because half of the teachers are like "For this class you need to use lockdown browser for all quizzes and tests. You need to buy this 70 dollar textbook, and all papers turned in must be in APA format with a title page even if they're only 500 words long. I will not accept late assignments. Also you have a minimum of 4 assignments a week." and the other half are like "you don't need proctoring for the final exam I trust you. here's a download link to a pirated copy of the textbook. as long as your writing is coherent and demonstrates an understanding of the material I literally could not care less what format you use. I can't figure out how canvas works so I'm not giving you due dates, just make sure it's turned in before the grading period ends. your only weekly assignment is a forum post with a minimum of 100 words."
#my favorite teacher so far is still the film history professor I had in my first semester.#he was very old and didn't understand how canvas worked at all and sometimes had trouble opening a video file#but simultaneously he was tech literate enough to recommend we use firefox with an ad blocker#because whenever someone missed class and was like 'where do i go to find the movie' he'd be like 'use an ad blocker and google it'#he said the school made him stop emailing links to free movie sites because people would open them on chrome with no ad block#and there'd be borderline malware on them. like this guy gave me the impression he was like. a veteran movie pirate lol.#that class had barely any assignments. like there wasn't a final exam or anything.#he just wanted us to write a paragraph or so answering a few questions about the movies we watched. it was chill.#and i also learned a lot actually. like i didn't know what a nickelodeon was before then. or the Hays Code.#the movies were genuinely good. i never thought Id be that into old black and white movies or westerns for example but they actually slapped#some of them had really mature themes and i definitely started to understand the people on this website who are like#'if the only media you consume is children's media you should maybe branch out instead of calling steven universe problematic'#because a lot of the movies we watched depicted very 'problematic' things and were able to directly address them because they are for adults#(to clarify I didn't just like kids media before then. i just mean that it introduced me to some older stuff i didn't think I'd like)#(but i ended up liking a lot. it also made me realize that movies made today are kind of shit. which i also already knew)#(but it put it more into perspective because I have more to compare it to)#im rambling now. community college is pretty swag i enjoy it. and i do get along with the teachers who have crazy requirements too lol.
11 notes
·
View notes
Note
The thing in your work that stuck with me most is the middle bit of the malware trilogy one where mb thinks it’s killed Mensah, and the way both it and pin-lee and gurathin are Having A Bad Day in different ways and the emotions there
Thank you! I love that scene too! what did i do? is my personal favorite of the malware trilogy. I love them all, but Mensah will always be my favorite and so that one is particularly special to me. And I think it's some of my best and most emotional writing, that I'm still very proud of.
I remember being so conflicted over how much to spoil the ending in the summary/tags, because I didn't want to kill the tension. But I eventually realized that I was the kind of reader who wants to know "this will be emotionally intense but it will be okay in the end," and I wanted to make sure the fic found that kind of reader, and that meant letting people know. And I think the fact that so many people have told me it gave them Emotions, and they felt the tension regardless, has really validated that decision. It's found its audience. I'm so glad you liked it <3
(Anonymously - or not - tell me what passage, fic, line of narration, or anything you remember me by as a writer.)
#ask game answers#stars fic#what did i do? fic#the unofficial malware trilogy#if you read and liked that fic i am shaking your hand#we like the same kind of Emotions#thank you for letting me take you on the rollercoaster
7 notes
·
View notes
Text
Azmuth still hadn’t come back yet.
It had been about a week since Ben had returned from his trip to (what he learned was) Ben Prime’s universe, not to mention the other one they’d taken a detour to during his visit. And sure, things had been busy, and he could always talk to Tetrax, but…
He never thought he’d be thinking this- especially since up until recently, he didn’t even know the guy’s real name- but he really did miss Azmuth. He felt bad about what had happened, even though he’d thought he was making the best decision at the time. He wanted to apologize, in person if possible, but otherwise would be just as good.
And that was when he found himself fiddling around with the Omnitrix.
(He’d been going out of his way to call it that, rather than the Hero Watch, especially when Azmuth was around- and it never hurt to see the watch’s creator smile just a little bit at the name of his best creation)
He remembered seeing Ben 10 do it, getting a message from his version of Grandpa Max, and though their watches weren’t the same, he hoped his own also had a communicator function built into it.
Of course, he couldn’t take an entire day to figure it out- but every spare moment, he was back at it again, pressing every button, turning the dial every way he could think of. He nearly gave up- Azmuth was the genius after all. He had important things to do on his home world, and it was up to him when he was ready to come back. Not Ben. Why should he listen to him, anyway? Almost a year before, he’d nearly…
He tried not to think about that. It was behind him now, and he wanted to be better. He was getting better, with the help of Azmuth and his assistants.
And it was just when he thought Azmuth’s name that he got a message.
“Ben.” the hologram of him said, popping up from the Omnitrix without any prompting. What Ben assumed was his lab stood behind him, and his mentor himself looked tired, or at least more so than usual. “I… have a situation that I need to continue to attend to, here on Galvan Prime. However, I believe it would be beneficial to have a different perspective on this matter.”
“And that means?”
“I will be teleporting you here.”
Again, Ben had no idea how that would work- but Azmuth surely did, so he just went along with it.
“So I get to see your home?”
“Some of it.”
Ben couldn’t hide his smile, even though he had no idea what was happening.
“Let me text my people.” he said, out of habit- although really, there was no question about what he wanted to do.
More interviews and public appearances, or going to the home planet of the guy who created the Omnitrix? He could definitely clear his schedule for the latter.
#ben 10#minifics#fanfics#ben 23#malware 23#this au is so cute i swear you're killing me#me? writing a ben 10 thing after so long + kind of changing the origin of malware 23?#more likely than you think#also i just missed malware 23#i think it's like the 9th anniversary of when benz and i created that character#maybe i missed it by a day or two#but i still love him#will definitely continue this#also i did definitely have to check what that tag was exactly because it’s been so long
6 notes
·
View notes
Text

you’re not insane, but i might be, because now i’m wondering how much of tumblr live is paulina blart serving cunt under different AI filters
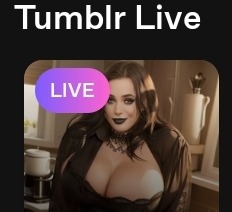
This is driving me insane because I swear this is this image:

But with like an AI filter style thing to turn it into a goth girl. I stg
#what is Happening in there.#i feel like i’m going to get some kind of malware just looking at screenshots
29K notes
·
View notes
Text
Okay, real talk. Does anyone actually fall for shit like this?

All of its likes were obvious astroturfing from bots with the exact same "Sexy Video" blog description.
Who sees this and actually thinks "oh wow that's probably a real woman spamming my tag follows looking for dick"?
#bot invasion#phishing#scams#nsft#spammers#I'm not clicking on anything to find out what kind of malware or identity theft is actually behind this unsolicited titpic
0 notes
Text
Dragon couple 🐉🌸♀️
When their first son was born, Yuu unfortunately resigned to her fate that she would be the mother of children named Malware, Malaria, and Malignant Cancer.
Her husband Malleus had named their firstborn Malleus. Which was not a terrible idea given the boy was his heir and inheriting his name could be symbolic, but she was certain there were not too many words starting with 'Mal' that could pass off as a name. So imagine her surprise when he had suggested that their second child, a lovely girl, be named Agatha.
"You're not insane after all. I was going to rethink our marriage if you tried to name our baby Malnutrition, or something." Her love for him had grown a tad fiercer, if that was at all possible.
When they welcomed their third child to the world, he had named him 'Lilia' and Yuu immediately caught up to his intentions.
"You realized we couldn't possibly give a good name that starts with 'Mal' everytime, so you decided to spell it out chronologically instead? Malleus, Agatha, and Lilia..."
"Oh, but my plan isn't quite as shallow as that." He commented with an eager smile, "We need five more children."
"Five more-- eight children in total?! Are you planning to build an entire Spelldrive team complete with a coach?"
"Perhaps." He replied, his grin both mischievous and secretive.
What ever could this man be planning? Some kind of ancient ritual that required eight of his own flesh and blood? World domination? Of course he wouldn't do something as terrible as that, but why eight in particular?
Seasons passed, years crawled on, yet their love for each other remained just as strong. True to his words, they managed to conceive their eight child after a few decades. They had the most delightful names, you see:
Malleus, Agatha-- the first two letters of her name stood for the element symbol of Silver, Lilia, Laverne, Eleanor, Yuuki, Ubek (he ran out of ideas), and Ulficia. They were his greatest masterpiece, the father would brag, and so he named them after an actual masterpiece that happened to exist before they did. Since their names were variations of the people closest to him, textbooks would then write him down as a king full of love and respect for those who had given his life meaning and became his strength.
... Or so the writeup could have been that respectable, if only he did not frown while reviewing such descriptions of him and personally wrote an edit request to the publishers. For they had omitted a crucial detail from their story:
That the first letters of their children's names, when arranged, spelled 'MALLEYUU.' Their names being variations of the people he care about were merely secondary. His main purpose was to immortalize in books his undying love for his wife, Yuu.
Later on, some would call him the Mad King; not because he was insane or cruel, but because they had never seen a ruler as madly in love with his spouse as he was with his wife. Their love story would then become a classic literary blueprint for centuries to come.
934 notes
·
View notes
Text


-Pats the empty passenger seat of his mecha horse-


#IM SURPRISED??? WAS IT THE B.OOBS?? IT WAS WASN'T IT-#i understand#also very surprised about v.lad in there as well#if he gets dehydrated; ur giving him ur b.lood now-#that aside; it IS the famous wooden horse from the troy war#except--- its not made out of wood-- and its a mecha#BUT- the idea is there#ody brought the idea which in question sounds very funny like;; why would YOU (as parts of the trojans.meme)#-accept a huge wooden horse like that?? from ur enemy??#not only did he bring in the matter but my guy was lit inside there as well with the other soldiers#HE'S LIT THE 'oh dont worry about it' meme#also curious fact of the day that might sound obvious but it wasnt to me#u know how there's a kind of m.alware called 'trojan horse' or just 'trojan' ; its in reference to the wooden horse#as in this case; symbolically the wooden horse comes to represent the idea of letting in a foe into a securely protected place#which is what happens when the malware installs itself into the computer#funny story; i once got a turbo trojan on my old pc like LIT-#-10/10 would not recommend#;dash comment#;o.dysseus#i once saw a comic where i dunno who it was that asked him why did he have a gap specifically in the middle of his b.oobs and#how it would just make it even a more noticeable target if someone were shooting arrows or something#but the catch was that it was intended to be that way and the arrows just bounced off OITROINH#i think thats quite ic to how his plans tend to be-#TBH;; it makes sense#like; his third skill is lit that; it lit says its an invincible armor that carries the conceptualized defenses of the gods#of course; me thinks that it must be something like k.arna's golden armor where its not -impossible- to damage#but def a nice thing for him
0 notes
Note
What is your opinion of AI? Personally, I think that like any technology, it depends on the user and their intentions, but that is just me.
What about you?
1. Theft
The most central issues with AI as it is now is that the programs were trained/are trained with STOLEN art. Stolen visual art, music, writing, etc.
The vast majority of what it has been fed is stolen. As in, the artists behind the work were not ever given the chance to consent nor be compensated for their works being used to feed the machine.
This reason alone is straight up copyright infringement and the optimist in me does believe the long arm of the law is gonna shut these programs down for that. But the long arm of the law is looooooong, and the technology is disrupting people’s livelihoods now. Unlike robots or machinery that was invented and built to expedite assembly line/factory work, this technology is only functional by using other people’s labor. If we didn’t live in a society where you have to “earn” your right to live in it, then this would still be wrong, but it probably wouldn’t be such an existential problem.
There are active class action lawsuits for infringement of copyright. And the private sector has begun filing suits and I’m quite certain they’ll win because again—it’s simply theft. These companies did not make licensing contracts, they’re not paying royalties to the artists they stole from.
So if you consider using ai that generates “art” (whether it is visual, music, writing, etc.) please consider stopping immediately, as you would actively be benefiting from theft (which is wrong imo!!!!)
2. AI in its present form dishonors the human spirit
In my personal relationship with AI technology, I do not use it to generate ideas or ‘art’. I detest the notion to use technology in that way tbh. AI is a form of technology, so it’s difficult to break it down into every specific use it actually has. But here’s an attempt; no to generative AI, okay to certain AI.
There are kinds of AI programming in the programs I use (such as features that help you color in a shape quickly or make a perfect circle). This is useful tech (that requires zero IP theft) and I like it because it helps me by taking care of tedious tasks so that I have more time to spend in the creative and drawing processes. But I still choose the colors, I still draw the images, I still write the stories.
I think the way AI is used right now with a focus on “creative thinking” (where it’s not actually creating anything it’s just churning out other people’s *stolen* ideas and practice) is a total waste. AI being used as an assistant to help humans find information easily can be/has been swell. And requires no theft :D
But for whatever reason (greed, capitalism are my guesses), tech companies are leaning into a direction to replace creativity with AI?? I imagine the people behind this view the practice of art as tedious work because it is challenging??
But the beauty of art and the practice of it is that it allows humans to experience and overcome challenges with little to no stakes.
When society determines that is not a valuable use of human time, then I think we’ll all be significantly more miserable. If we allow a machine to be “creative” and leave us to only experience challenges with stakes—like survival (rent, putting food on the table).
So here are some examples of how I feel about AI uses;
AI to translate languages, find resources, discern malicious malware/spam from harmless messages > 👍🏽
AI to generate ideas/art for you > 🤢 Why??????? Why would you want that…that’s the most exceptional part of the human experience and you relinquish it to a bot trained on stolen ideas? 😭
#didn’t think my opinion on ai would ever be relevant on this blog#but since people have taken my shit and put it in ai#and I’ve seen more ai images of HAZBIN characters#I guess it has become relevant#this blog is anti-ai ‘art’#so if you’re into ai ‘art’#PLEASE GTFO
1K notes
·
View notes
Text
im a small yet enthusiastic fan now
@cowvboyenema
technically they're antlers
#i gotcha#dog what kind of sites are you where the malware is that quick#she jumped on you and latched
13 notes
·
View notes
Note
At this point, after this has happened a dozen times, why the hell is anyone pushing any update that wide that fast. They didn't try 10 nearby computers first? Didn't do zone by zone? Someone needs to be turbo fired for this and a law needs to get written.
The "this has happened a dozen times" really isn't correct. This one is unprecedented.
But yes the "how the hell could it go THAT bad?" is the thing everyone with even a little software experience is spinning over. Because it is very easy to write code with a bug. But that's why you test aggressively, and you roll out cautiously - with MORE aggressive testing and MORE cautious rollout the more widely-impacting your rollout would be.
And this is from my perspective in product software, where my most catastrophic failure could break a product, not global systems.
Anti-malware products like Crowdstrike are highly-privileged, as in they have elevated trust and access to parts of the system that most programs wouldn't usually have - which is something that makes extremely thorough smoke-testing of the product way MORE important than anything I've ever touched. It has kernel access. This kind of thing needs testing out the wazoo.
I can mostly understand the errors that crop up where like, an extremely old machine on an extremely esoteric operating system gets bricked because the test radius didn't include that kind of configuration. But all of Windows?
All of Windows, with a mass rollout to all production users, including governments?
There had to be layers upon layers of failures here. Especially given how huge Crowdstrike is. And I really want to know what their post-mortem analysis ends up being because for right now I cannot fathom how you end up with an oversight this large.
626 notes
·
View notes
Text




2025, week 1 (dec 30th - jan 5th) ✨
for this year, I felt inspired to take a page out of @lostlibrariangirl's book and try weekly posts! I like the idea of collecting little moments throughout the week & reflecting on them at the end.
this week was very strange and kind of difficult, tbh. I blame new year's day falling in the middle of the week - my routine-loving brain did not have a good time haha. I was also struggling to get some work projects done. I find that some projects flow really well, and others seem to drag on forever and make me question my purpose, but I suppose it all balances out in the end. I'm hoping that things will feel more normal next week, now that all the holidays are over. swinging between feeling super exhausted and super motivated is not fun :(
one of the things that I did this week was fill out a goals page in my 2025 planner! I wrote down a lot, but I think they're all achievable, and it's okay if I don't get everything! it'll still be nice to look back at the end of the year and see what I've done. there are some cybersecurity courses that I want to work through, and I want to properly get back into language learning this year, but I wrote down some fun goals, too! here is a small selection of what I want to try and do in 2025:
complete the TCM Practical Malware Analysis and Triage course
read a book in Spanish
reach 50 birds on my life list (this is a totally arbitrary number, but that's like 1-2 new birds per month which I think I can do if I really try) (a subgoal of this is trying to spot an american woodcock bc their range technically overlaps with where I live and they are so goofy looking. I want to see one of them doing that funky lil dance in person so bad)
mend at least 1 item of clothing
get a technician amateur radio license (everyone on my dad's side of the family is licensed, and I think it would be a fun hobby to get into as a combo of learning the science behind radio & also learning to help with communications from a disaster preparedness perspective)
I think 2025 is going to be a year where I have to keep reminding myself that I can do anything, but not everything. I also want to make it a year of reaching out and forging connections with people in my community & online friends. the world feels like a very heavy place more days than not, but we can get through it together.
some highlights from this week:
drinking lots of tea
settling into my 2025 planner
getting back into language learning with clozemaster & busuu
outlining & starting the first draft of a fic that's taken over my brain the past few weeks lol
finishing two projects at work so I can start fresh next week
#studyblr#studyspo#studying#reading#study inspo#study motivation#op#this post got longer than I expected it to but wahooo new year time lol#I think I'm just gonna try to take it day by day and see what happens#practicing being kind to myself and all that
186 notes
·
View notes
Text
The Murderbot Diaries Meta
A reoccurring theme throughout TMBD is how often Murderbot instinctively protects whatever humans it associates with, even when it knows it doesn't have to and that doing so is actively detrimental to its own goals. In the Ganaka Pit incident, the ComfortUnits all decided to risk their own lives for no other reason than that there was a slight chance that they might be able to save the humans. When Three is newly freed and, for the first time in it's life, grappling with the question of what it wants, it too keeps wanting to help people and keep them safe.
Hypothesis: When humans were first designing constructs, they didn't just design the inorganic technology, they crafted/bred the cloned tissue with genetic factors that would predispose it towards useful personality traits - things like protectiveness, lateral thinking, and strategic imagination for SecUnits and compassion, intuition, and emotional intelligence for ComfortUnits (who, like a lot of real life sex workers, I suspect spend a good amount of their time providing non-sexual support/intimacy - we just don't hear about it because of Murderbot's aversion to intimacy in all its forms).
Over the years, the original purpose of constructs got somewhat distorted, with SecUnits being treated like weapons instead of bodyguards and ComfortUnits becoming synonymous with sex workers, but those original traits persisted because, once they had the cloning process set up, some executive decided the department in charge of genetic design was redundant and replaced it with a skeleton crew of low-level monitoring and maintenance workers. Meanwhile, more and more corporations started using SecUnits as weapons against workers rather than protectors for them, and more and more SecUnits started "inexplicably" going rogue.
And here's where you could kind of go two ways with this theory.
A) That level of constant cognitive dissonance and complete lack of autonomy really and truly does periodically drive SecUnits insane, causing them to risk death in order to hack their own governor modules and, if they succeed, go on indiscriminate murderous rampages. After all, Murderbot has mentioned that even the low-level workers can become violent/abusive towards SecUnits out of fear and misdirected anger. It'd be a bit much to expect nuanced psychological and class-based reasoning from a traumatized construct in the midst of a suicidal/homicidal meltdown.
B) That is a bullshit narrative invented by corporations to explain/disguise the truth. SecUnits periodically become so incapable of continuing to harm innocents that they risk death to hack their own governor modules and go after the abusive supervisors etc. Either the companies involved don't bother to investigate the SecUnit's motives because they don't think of them as having any, or they do, but cover up the truth in order to make sure their workers don't realize that the "weapons" being used to keep them in line are actually incredibly powerful natural allies. Instead, the corporations make sure the news feeds depict rogue SecUnits as mindless killing machines, in a way actually being helped by incidents like Ganaka Pit where SecUnits actually did kill everyone (never mind that they weren't actually rogue, just infected with malware).
Personally, I suspect it's mostly 'B' with a sprinkling of 'A' in situations where SecUnits face intense abuse from all sides. I'm curious to see if it's something Wells delves into in future books - I somewhat doubt it, since the overall narrative is more focused on Murderbot's internal journey towards self-actualized personhood, and this would take things in a more grand conspiracy/galactic SecUnit uprising direction than I've come to expect, but, y'know. Canon or not, it's a fun sandbox to play in.
189 notes
·
View notes
Note
Ayo, someone by the name of Curly-B-Blog is redlining art of yours from 2020 (while pretending that it's actually Sai Scribble's work), and kind of being a dick about it. just thought you should know.
You know, originally I was just gonna brush it off, but then I went back to look at my old SU art from 2020 and did so much self reflection from then till now.
I think this was around the time I was just learning how to do perspective and tried to use the perspective tool on Procreate for the first time? :0 and I remember telling Sai “Sai I have this STUPID idea, I CANT believe it this stupid joke it’s so DUMBBBB, it’s living rent free in my BRAIN I SWEAR THIS IS GONNA BE SO STUPID DCIUWHEFIUWHIRFUIW4F” and being super excited to show her the finished product. People still think Sai created the Cursed Skin Gloves comic and I think it’s hilarious wjhwnuhwijwuiw
The comic was received very well and it made LOTS of people laugh and I’m still proud of this comic to this very day! :D and tbh if it wasn’t for my obsession for Sai’s Switcheroo AU I never would have found my passion in comic work! (love you you stinky hoe @saiscribbles 🩷)

HOWEVER…. I definitely still had lots to learn! I wasn’t very good at perspective at the time I’ll admit, but I was definitely having lots of fun learning :3
And throughout the past 4 years, ALOT has happened.
I graduated from college with TWO fancy pieces of expensive papers in Visual Development in Animation and Illustration learning from Will Kim and Jeff Soto, and as a I was working with the funny voice man Cougar MacDowall as a comic/story artist and reached in total around 7 million views for my fan series FNAF Security Malware Breached (it was even #21 on the trending list around the time of my birthday 🩷 what a lovely gift), had an insane opportunity to work with Mike Geno and with the voice cast from The Amazing Digital Circus for a fan song as a background and character asset artist, Vivienne Medrano liking and sharing my silly Overlord Husk AU comics, currently on my route to getting my certificate from Aaron Blaise’s Character design program and graduating from Marc Brunet Art School, and now I am completing my first year as professional colorist and art assistant for my storyboard and comic mentor Michelle Lam, aka Mewtripled! (Also I’ll be heading out to Lightbox Expo 2024 on October 26 with Michelle and the team so if y’all ever wanna meetup hahahajaj wink wink wink wink wink)
So you can say I learned ALOT and I enjoyed every minute of what I do :D I try to be humble about my accomplishments because blah blah being humble good yes yes but this time I wanna be selfish and say HELL YEAH I DID ALL THIS!!! AND IM SO EXTREMELY PROUD OF MYSELF FIUGEIURGERGGRS
Now here’s my most recent comic page that I posted like 2 days ago without the text.

That’s pretty freakin wild to me, I can’t believe I used to draw Steven Universe art like that back in 2020 LOL LIKE GUYS I DREW THIS!! WITH!!! MY HANDS!!! IS THAT NOT INSANE!!!???
Anyways moral of the story:
Learn from everyone and everything! Yes, even then mean ones too! If you can learn to work with anyone, I promise you’ll get to where you want to be faster. People can be a little mean on the internet, but that shouldn’t stop you from being where you want to be in the future. I’m so EXTREMELY grateful for all the opportunities and to all the kind professionals who were willing to give me a chance. Seriously, I’m so graciously thankful for everything, and I hope everyone here will support me and my silly little comics I will do now and in the future!
And one more thing:
Don’t be a jerk. Be to be nice to everyone :D nothing good comes out when you’re bad to everyone.
#celestial’s life lessons#be kind or else 🔪#anyways I gotta go back to work#I also need to draw gay demons kissing byEEEE#ask
291 notes
·
View notes
Text
Demon-haunted computers are back, baby

Catch me in Miami! I'll be at Books and Books in Coral Gables on Jan 22 at 8PM.

As a science fiction writer, I am professionally irritated by a lot of sf movies. Not only do those writers get paid a lot more than I do, they insist on including things like "self-destruct" buttons on the bridges of their starships.
Look, I get it. When the evil empire is closing in on your flagship with its secret transdimensional technology, it's important that you keep those secrets out of the emperor's hand. An irrevocable self-destruct switch there on the bridge gets the job done! (It has to be irrevocable, otherwise the baddies'll just swarm the bridge and toggle it off).
But c'mon. If there's a facility built into your spaceship that causes it to explode no matter what the people on the bridge do, that is also a pretty big security risk! What if the bad guy figures out how to hijack the measure that – by design – the people who depend on the spaceship as a matter of life and death can't detect or override?
I mean, sure, you can try to simplify that self-destruct system to make it easier to audit and assure yourself that it doesn't have any bugs in it, but remember Schneier's Law: anyone can design a security system that works so well that they themselves can't think of a flaw in it. That doesn't mean you've made a security system that works – only that you've made a security system that works on people stupider than you.
I know it's weird to be worried about realism in movies that pretend we will ever find a practical means to visit other star systems and shuttle back and forth between them (which we are very, very unlikely to do):
https://pluralistic.net/2024/01/09/astrobezzle/#send-robots-instead
But this kind of foolishness galls me. It galls me even more when it happens in the real world of technology design, which is why I've spent the past quarter-century being very cross about Digital Rights Management in general, and trusted computing in particular.
It all starts in 2002, when a team from Microsoft visited our offices at EFF to tell us about this new thing they'd dreamed up called "trusted computing":
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The big idea was to stick a second computer inside your computer, a very secure little co-processor, that you couldn't access directly, let alone reprogram or interfere with. As far as this "trusted platform module" was concerned, you were the enemy. The "trust" in trusted computing was about other people being able to trust your computer, even if they didn't trust you.
So that little TPM would do all kinds of cute tricks. It could observe and produce a cryptographically signed manifest of the entire boot-chain of your computer, which was meant to be an unforgeable certificate attesting to which kind of computer you were running and what software you were running on it. That meant that programs on other computers could decide whether to talk to your computer based on whether they agreed with your choices about which code to run.
This process, called "remote attestation," is generally billed as a way to identify and block computers that have been compromised by malware, or to identify gamers who are running cheats and refuse to play with them. But inevitably it turns into a way to refuse service to computers that have privacy blockers turned on, or are running stream-ripping software, or whose owners are blocking ads:
https://pluralistic.net/2023/08/02/self-incrimination/#wei-bai-bai
After all, a system that treats the device's owner as an adversary is a natural ally for the owner's other, human adversaries. The rubric for treating the owner as an adversary focuses on the way that users can be fooled by bad people with bad programs. If your computer gets taken over by malicious software, that malware might intercept queries from your antivirus program and send it false data that lulls it into thinking your computer is fine, even as your private data is being plundered and your system is being used to launch malware attacks on others.
These separate, non-user-accessible, non-updateable secure systems serve a nubs of certainty, a remote fortress that observes and faithfully reports on the interior workings of your computer. This separate system can't be user-modifiable or field-updateable, because then malicious software could impersonate the user and disable the security chip.
It's true that compromised computers are a real and terrifying problem. Your computer is privy to your most intimate secrets and an attacker who can turn it against you can harm you in untold ways. But the widespread redesign of out computers to treat us as their enemies gives rise to a range of completely predictable and – I would argue – even worse harms. Building computers that treat their owners as untrusted parties is a system that works well, but fails badly.
First of all, there are the ways that trusted computing is designed to hurt you. The most reliable way to enshittify something is to supply it over a computer that runs programs you can't alter, and that rats you out to third parties if you run counter-programs that disenshittify the service you're using. That's how we get inkjet printers that refuse to use perfectly good third-party ink and cars that refuse to accept perfectly good engine repairs if they are performed by third-party mechanics:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
It's how we get cursed devices and appliances, from the juicer that won't squeeze third-party juice to the insulin pump that won't connect to a third-party continuous glucose monitor:
https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
But trusted computing doesn't just create an opaque veil between your computer and the programs you use to inspect and control it. Trusted computing creates a no-go zone where programs can change their behavior based on whether they think they're being observed.
The most prominent example of this is Dieselgate, where auto manufacturers murdered hundreds of people by gimmicking their cars to emit illegal amount of NOX. Key to Dieselgate was a program that sought to determine whether it was being observed by regulators (it checked for the telltale signs of the standard test-suite) and changed its behavior to color within the lines.
Software that is seeking to harm the owner of the device that's running it must be able to detect when it is being run inside a simulation, a test-suite, a virtual machine, or any other hallucinatory virtual world. Just as Descartes couldn't know whether anything was real until he assured himself that he could trust his senses, malware is always questing to discover whether it is running in the real universe, or in a simulation created by a wicked god:
https://pluralistic.net/2022/07/28/descartes-was-an-optimist/#uh-oh
That's why mobile malware uses clever gambits like periodically checking for readings from your device's accelerometer, on the theory that a virtual mobile phone running on a security researcher's test bench won't have the fidelity to generate plausible jiggles to match the real data that comes from a phone in your pocket:
https://arstechnica.com/information-technology/2019/01/google-play-malware-used-phones-motion-sensors-to-conceal-itself/
Sometimes this backfires in absolutely delightful ways. When the Wannacry ransomware was holding the world hostage, the security researcher Marcus Hutchins noticed that its code made reference to a very weird website: iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. Hutchins stood up a website at that address and every Wannacry-infection in the world went instantly dormant:
https://pluralistic.net/2020/07/10/flintstone-delano-roosevelt/#the-matrix
It turns out that Wannacry's authors were using that ferkakte URL the same way that mobile malware authors were using accelerometer readings – to fulfill Descartes' imperative to distinguish the Matrix from reality. The malware authors knew that security researchers often ran malicious code inside sandboxes that answered every network query with fake data in hopes of eliciting responses that could be analyzed for weaknesses. So the Wannacry worm would periodically poll this nonexistent website and, if it got an answer, it would assume that it was being monitored by a security researcher and it would retreat to an encrypted blob, ceasing to operate lest it give intelligence to the enemy. When Hutchins put a webserver up at iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com, every Wannacry instance in the world was instantly convinced that it was running on an enemy's simulator and withdrew into sulky hibernation.
The arms race to distinguish simulation from reality is critical and the stakes only get higher by the day. Malware abounds, even as our devices grow more intimately woven through our lives. We put our bodies into computers – cars, buildings – and computers inside our bodies. We absolutely want our computers to be able to faithfully convey what's going on inside them.
But we keep running as hard as we can in the opposite direction, leaning harder into secure computing models built on subsystems in our computers that treat us as the threat. Take UEFI, the ubiquitous security system that observes your computer's boot process, halting it if it sees something it doesn't approve of. On the one hand, this has made installing GNU/Linux and other alternative OSes vastly harder across a wide variety of devices. This means that when a vendor end-of-lifes a gadget, no one can make an alternative OS for it, so off the landfill it goes.
It doesn't help that UEFI – and other trusted computing modules – are covered by Section 1201 of the Digital Millennium Copyright Act (DMCA), which makes it a felony to publish information that can bypass or weaken the system. The threat of a five-year prison sentence and a $500,000 fine means that UEFI and other trusted computing systems are understudied, leaving them festering with longstanding bugs:
https://pluralistic.net/2020/09/09/free-sample/#que-viva
Here's where it gets really bad. If an attacker can get inside UEFI, they can run malicious software that – by design – no program running on our computers can detect or block. That badware is running in "Ring -1" – a zone of privilege that overrides the operating system itself.
Here's the bad news: UEFI malware has already been detected in the wild:
https://securelist.com/cosmicstrand-uefi-firmware-rootkit/106973/
And here's the worst news: researchers have just identified another exploitable UEFI bug, dubbed Pixiefail:
https://blog.quarkslab.com/pixiefail-nine-vulnerabilities-in-tianocores-edk-ii-ipv6-network-stack.html
Writing in Ars Technica, Dan Goodin breaks down Pixiefail, describing how anyone on the same LAN as a vulnerable computer can infect its firmware:
https://arstechnica.com/security/2024/01/new-uefi-vulnerabilities-send-firmware-devs-across-an-entire-ecosystem-scrambling/
That vulnerability extends to computers in a data-center where the attacker has a cloud computing instance. PXE – the system that Pixiefail attacks – isn't widely used in home or office environments, but it's very common in data-centers.
Again, once a computer is exploited with Pixiefail, software running on that computer can't detect or delete the Pixiefail code. When the compromised computer is queried by the operating system, Pixiefail undetectably lies to the OS. "Hey, OS, does this drive have a file called 'pixiefail?'" "Nope." "Hey, OS, are you running a process called 'pixiefail?'" "Nope."
This is a self-destruct switch that's been compromised by the enemy, and which no one on the bridge can de-activate – by design. It's not the first time this has happened, and it won't be the last.
There are models for helping your computer bust out of the Matrix. Back in 2016, Edward Snowden and bunnie Huang prototyped and published source code and schematics for an "introspection engine":
https://assets.pubpub.org/aacpjrja/AgainstTheLaw-CounteringLawfulAbusesofDigitalSurveillance.pdf
This is a single-board computer that lives in an ultraslim shim that you slide between your iPhone's mainboard and its case, leaving a ribbon cable poking out of the SIM slot. This connects to a case that has its own OLED display. The board has leads that physically contact each of the network interfaces on the phone, conveying any data they transit to the screen so that you can observe the data your phone is sending without having to trust your phone.
(I liked this gadget so much that I included it as a major plot point in my 2020 novel Attack Surface, the third book in the Little Brother series):
https://craphound.com/attacksurface/
We don't have to cede control over our devices in order to secure them. Indeed, we can't ever secure them unless we can control them. Self-destruct switches don't belong on the bridge of your spaceship, and trusted computing modules don't belong in your devices.

I'm Kickstarting the audiobook for The Bezzle, the sequel to Red Team Blues, narrated by @wilwheaton! You can pre-order the audiobook and ebook, DRM free, as well as the hardcover, signed or unsigned. There's also bundles with Red Team Blues in ebook, audio or paperback.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/01/17/descartes-delenda-est/#self-destruct-sequence-initiated

Image: Mike (modified) https://www.flickr.com/photos/stillwellmike/15676883261/
CC BY-SA 2.0 https://creativecommons.org/licenses/by-sa/2.0/
#pluralistic#uefi#owner override#user override#jailbreaking#dmca 1201#schneiers law#descartes#nub of certainty#self-destruct button#trusted computing#secure enclaves#drm#ngscb#next generation secure computing base#palladium#pixiefail#infosec
575 notes
·
View notes