#viral latency
Explore tagged Tumblr posts
Text
The Sloth Virus: A New Frontier in Virology
We're thrilled to introduce the Sloth Virus, a novel discovery in virology. Found in sloths, this virus features an unusually slow replication cycle, reflecting its host's lethargic nature.
In the ever-evolving world of virology, new discoveries often emerge, sometimes from the most unexpected sources. These interesting discoveries include the so-called “sloth virus,” a pathogen that has attracted attention for its unique characteristics and potential implications. Named after its host, the sloth, the virus represents a fascinating intersection of wildlife biology, ecology, and…
#Crusiviridae#host-virus interaction#RNA virus#sloth host#Sloth Virus#slow replication cycle#tropical rainforests#viral evolution#viral latency#viral transmission#virology research#virus discovery#wildlife health#wildlife virology#zoonotic potential
0 notes
Text
When the author of the Necronomicon wrote “that is not dead which can eternal lie, and with strange eons even death may die” he was actually talking about shingles.
0 notes
Text
Acquired Immune Deficiency Syndrome correlation with SARS-CoV-2 N genotypes - Published July 29, 2024
You read that right: Covid infections can result in AIDS. I've been following this preprint since 2022, and I'm so excited to see it finally published! You might remember the preprint from the original Milf-Adjacent or covidsafehotties blogs.
Highlights •Genotypes N/120 and N/152 of SARS-CoV-2 have been identified in the acquired immuno-deficiency scope caused by Sarbecovirus.
•A new binding site for the Sarbecovirus N protein is proposed as the main route of infection of lymphocytes through CD147 receptors.
•Immune dysregulation caused by infection of CD147 lymphocytes is consistent with clinical data of severe and Long Covid cases.
Abstract Background Epigenetics and clinical observations referring to Betacoronavirus lead to the conjecture that Sarbecovirus may have the ability to infect lymphocytes using a different way than the spike protein. In addition to inducing the death of lymphocytes, thus drastically reducing their population and causing a serious immune deficiency, allows it to remain hidden for long periods of latency using them as a viral reservoir in what is named Long-Covid Disease. Exploring possibilities, the hypothesis is focused on that N protein may be the key of infecting lymphocytes.
Method The present article exhibits a computational assay for the latest complete sequences reported to GISAID, correlating N genotypes with an enhancement in the affinity of the complex that causes immune deficiency in order to determine a good docking with the N protein and some receptors in lymphocytes.
Results A novel high-interaction coupling of N-RBD and CD147 is presented as the main way of infecting lymphocytes, allowing to define those genotypes involved in their affinity enhancement.
Conclusion The hypothesis is consistent with the mutagenic deriving observed on the in-silico assay, which reveals that genotypes N/120 and N/152 are determinant to reduce the Immune Response of the host infecting lymphocytes, allowing the virus persists indefinitely and causing an Acquire Immune Deficiency Syndrome.
Graphical abstract

#covid#mask up#pandemic#covid 19#wear a mask#coronavirus#sars cov 2#still coviding#public health#wear a respirator#long covid#AIDS
139 notes
·
View notes
Text
PROS AND CONS 😋
> YouTube Premium
PRO: Experience the full breadth of content delivery network capabilities, including latency measurement and HTTP response headers.
CON: Unable to freely browse library of viral video thumbnails.
> Soundcloud Plus
PRO: 1080p video playback at 60 fps, provided bandwidth allows.
CON: Porn accompaniment very unclear
> Spotify Premium
PRO: An abundance of digital audio workstations for filtering sound profile.
CON: Driving whilst a passenger is likely to distract. (2/3rds of the Fun today!)
> AppleMusicPlusPremiumXtraFreeTryBeforeYouBuy.
PRO: "Fun Today" rewards program passively logs each track you play, for a chance to win a Fun coupon.
CON: Nothing about being useful or lucky.
21 notes
·
View notes
Text
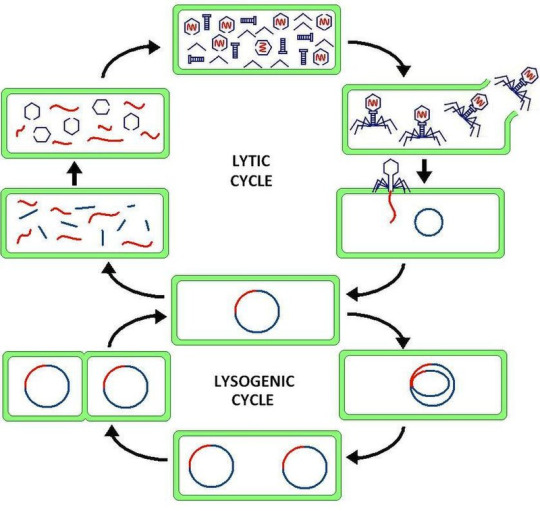
Virus latency (or viral latency) is the ability of a pathogenic virus to lie dormant (latent) within a cell, denoted as the lysogenic part of the viral life cycle.[1] A latent viral infection is a type of persistent viral infection which is distinguished from a chronic viral infection. Latency is the phase in certain viruses' life cycles in which, after initial infection, proliferation of virus particles ceases. However, the viral genome is not eradicated. The virus can reactivate and begin producing large amounts of viral progeny (the lytic part of the viral life cycle) without the host becoming reinfected by new outside virus, and stays within the host indefinitely.[2]
Episomal latency refers to the use of genetic episomes during latency. In this latency type, viral genes are stabilized, floating in the cytoplasm or nucleus as distinct objects, either as linear or lariat structures. Episomal latency is more vulnerable to ribozymes or host foreign gene degradation than proviral latency (see below).
Advantages of episomal latency include the fact that the virus may not need to enter the cell nucleus, and hence may avoid nuclear domain 10 (ND10) from activating interferon via that pathway. Disadvantages include more exposure to cellular defenses, leading to possible degradation of viral gene via cellular enzymes.[12]
Proviral latency: A provirus is a virus genome that is integrated into the DNA of a host cell
All interferons share several common effects: they are antiviral agents and they modulate functions of the immune system. Administration of Type I IFN has been shown experimentally to inhibit tumor growth in animals, but the beneficial action in human tumors has not been widely documented. A virus-infected cell releases viral particles that can infect nearby cells. However, the infected cell can protect neighboring cells against a potential infection of the virus by releasing interferons. In response to interferon, cells produce large amounts of an enzyme known as protein kinase R (PKR). This enzyme phosphorylates a protein known as eIF-2 in response to new viral infections; the phosphorylated eIF-2 forms an inactive complex with another protein, called eIF2B, to reduce protein synthesis within the cell. Another cellular enzyme, RNAse L—also induced by interferon action—destroys RNA within the cells to further reduce protein synthesis of both viral and host genes. Inhibited protein synthesis impairs both virus replication and infected host cells. In addition, interferons induce production of hundreds of other proteins—known collectively as interferon-stimulated genes (ISGs)—that have roles in combating viruses and other actions produced by interferon.[13][14] They also limit viral spread by increasing p53 activity, which kills virus-infected cells by promoting apoptosis.[15][16] The effect of IFN on p53 is also linked to its protective role against certain cancers.[15]
Another function of interferons is to up-regulate major histocompatibility complex molecules, MHC I and MHC II, and increase immunoproteasome activity. All interferons significantly enhance the presentation of MHC I dependent antigens. Interferon gamma (IFN-gamma) also significantly stimulates the MHC II-dependent presentation of antigens. Higher MHC I expression increases presentation of viral and abnormal peptides from cancer cells to cytotoxic T cells, while the immunoproteasome processes these peptides for loading onto the MHC I molecule, thereby increasing the recognition and killing of infected or malignant cells. Higher MHC II expression increases presentation of these peptides to helper T cells; these cells release cytokines (such as more interferons and interleukins, among others) that signal to and co-ordinate the activity of other immune cells.[17][18][19]
Epstein–Barr virus lytic reactivation (which can be due to chemotherapy or radiation) can result in genome instability and cancer.[5]
HSV reactivates upon even minor chromatin loosening with stress,[7] although the chromatin compacts (becomes latent) upon oxygen and nutrient deprivation.[8]
Cytomegalovirus (CMV) establishes latency in myeloid progenitor cells, and is reactivated by inflammation.[9] Immunosuppression and critical illness (sepsis in particular) often results in CMV reactivation.[10] CMV reactivation is commonly seen in patients with severe colitis.[11]
viral latency is so fucked up
11 notes
·
View notes
Text
An addendum: you get symptoms. but you will feel fine afterwards so whatever it was must've passed. and then a few months pass and your life suddenly falls apart. you don't know why. you assume you're just old, or tired, or overworked, or need change, or you're in a bad job, or a bad situation. or maybe you never had symptoms and this happens anyway. you start to forget so much. you forget how much you're forgetting. you can't process how much you can't do. you're fine. everything's going fine and yet it is not. you are doing everything all the time and yet nothing is getting done ever. but you were fine. you stopped being ill, or never were. you're just so, so, tired, all the time, but you're no different from before, and everything is falling apart, but you had got better.
Post SARS-COVID-19 syndrome has a latency period. It is the gaslighting disease. You will get covid, and you will be ill for a few days, weeks, perhaps even months. But from the moment you catch it, your body is deteriorating. Your brain is clotting. Your lung's lymph nodes are building viral stores. Your blood is changing and your cells are building up forever particles. You will get better. And half a year, maybe a full year later, you start getting worse. And you won't know why. And the doctor won't tell you why. And the news won't tell you why. And even if you know, and push, and fight, and fight, and fight, they won't care. They won't help. The people around you won't believe you. You don't exist in media. You don't exist to the government. You don't exist to the health system. And you become acutely aware that almost everyone around you is a threat. Nobody masks. Nobody cares. Every single person who's ever claimed to love you doesn't. Because they're willing to put you through the same again, and again, and you will get worse, and worse. And you will not know how deep the hole goes. You can feel yourself fading every day, less energy, more forgetting, less time, more work, less people, more bills. And you will know that it will get worse. And that everyone around you would willfully make it worse. And you are alone. And you are fine. And everything around you is gone. And there is nothing left for you. And you are fine. And nobody is safe. And you are not within yourself. And you are fine. And the world moves on without you. And you fall apart. And you are fine.
covid's cool because you get it and you might not even know because you have no symptoms. and you might feel like you have a bad cold or the flu. and you might end up in the hospital or dead. And then after you'll either feel fine. or you'll feel kinda off for a few months. or you'll have years or a lifetime of dealing with a new/worsened disability/disabilities. or you'll die. and you have to gamble every time you go out or take off your mask whether you want to risk getting it or not. and also most of society has decided it's probably fine to risk it because surely it won't happen to them. of course they've had that nagging cough and trouble exercising for months now but that's not covid, it's just this weird cold going around. no they didn't take a covid test, it's probably not covid. no they're not going to wear a mask, they didn't test positive (because they didn't take a test). every day it's like, okay, i might get the Virus That Gives You Seven Disabilities today, and i might not, and absolutely nobody around me is doing anything to prevent anyone else from getting it anymore, because everyone wants to pretend it's not happening. that's really fine and normal.
7K notes
·
View notes
Text
Best Practices to Prevent Website Crashes During High Traffic
Introduction
Traffic surges from flash sales, ticket launches, or viral campaigns can easily overwhelm unprepared infrastructure, resulting in lost revenue, damaged credibility, and user frustration. To prevent website crashes during high traffic, companies must follow best practices designed for maintaining system’s reliability under pressure.
Businesses must know how to effectively handle traffic loads using a combination of forecasting, capacity planning, and load-aware architecture. In this blog below, you’ll learn proven best practices for handling traffic surges. Through specific strategies and tool recommendations, we’ll help you build a system that scales with demand and performs under peak pressure, without crashing when it matters most.
Understanding the Root Cause of Failures
Most system crashes during high-traffic events occur not because the traffic volume was unpredictable, but because the system wasn’t designed to scale. The absence of proper architectural planning, real-time observability, and auto-scaling capabilities creates blind spots that collapse under load.
One major issue is underestimating resource saturation. If your CPU, memory, or bandwidth isn't dynamically scalable, you will likely face slowdowns or full outages under load. Another cause is the lack of real-time monitoring to handle traffic spikes.
System failure also arises when load thresholds aren’t tested in realistic environments. Many businesses skip stress testing websites for traffic resilience, assuming normal performance benchmarks will hold under peak load.
To avoid these pitfalls, organizations must follow best practices for a scalable system architecture, which include modular service layers, stateless load distribution, database sharding, and automated elasticity. These principles ensure the system can scale horizontally and handle unpredictable spikes without downtime.
The High Cost of Downtime, What the Data Reveals?
System failures during high-traffic events are not just technical glitches; they represent significant financial risks. According to the Uptime Institute's 2023 Annual Outage Analysis, over two-thirds of all outages cost more than $100,000, with some incidents exceeding $1 million.
In a 2023 survey by Statista, approximately 54% of data center operators reported that their most significant outage cost and 16% experienced losses exceeding $1 million. Queue-it's 2023 report highlights that 93% of enterprises estimate downtime costs exceed $300,000 per hour, with 48% reporting costs surpassing $1 million per hour.
These statistics highlight the critical importance of implementing best practices to prevent website crashes during high traffic.
Best Practices to Prevent Website Crashes During High Traffic
Avoiding system failures during traffic peaks requires a combination of preparation, visibility, and responsive architecture. Below are the most effective ways to ensure high-traffic website crash prevention,
1. Plan Infrastructure for Load, Not Just Average Traffic
Traffic doesn’t rise gradually, it spikes unpredictably. A campaign going viral can multiply your active sessions within minutes. To prevent website crashes during high traffic, always design for peak load, not daily average or minimum traffic.
For example, eCommerce platforms often set infrastructure baselines 3x above normal traffic to stay stable during flash sales.
2. Perform Stress Testing in Simulated Peak Conditions
Load testing helps, but without high-pressure stress scenarios, you’ll never know how the system truly responds. Stress testing websites for traffic resilience is essential to predict crash points before users feel them. Use tools like Apache JMeter or k6 to simulate 10x user spikes, evaluating API throughput and database latency.
3. Use a CDN to Reduce Direct Load on Servers
A Content Delivery Network (CDN) distributes assets closer to users, reducing origin server strain and improving load times during surge events. CDN usage to prevent website downtime is especially critical when you expect a global audience within a short window. Cloudflare, Akamai, and Fastly are widely used for this purpose.
4. Implement Scalable Infrastructure with Auto-Scaling Policies
Scalable infrastructure for high-traffic events eliminates the need for manual intervention. Businesses that follow best practices for a scalable system architecture implement autoscaling groups like AWS Auto Scaling or GCP’s Compute Engine and can set resource-based thresholds proactively.
5. Apply Load Balancing Strategies for Even Resource Distribution
Without intelligent load distribution, one node crashes while others stay idle. Load balancing strategies for peak traffic use Layer 7 routing, health checks, and session stickiness to maintain stability. Tools like HAProxy, NGINX, or AWS ALB help balance connections and avoid local overload.
Key tip: Always test your load balancer under burst scenarios to confirm resilience.
6. Cache Dynamic Content Strategically
Caching reduces backend calls and speeds up response times during surges. Implement full-page, object, and edge caching using Redis, Varnish, or browser-side controls. For real-time apps, set TTLs to balance freshness with performance. This approach complements website performance optimization for traffic spikes by reducing compute strain.
7. Monitor in Real Time and Set Alerts on Traffic-Sensitive KPIs
Real-time monitoring to handle traffic spikes includes tracking memory, CPU, queue depth, and request failures. Platforms like Datadog or Grafana offer live dashboards and alerts that enable engineers to intervene before users notice a slowdown.
Key tip: Integrate alerting with automated response actions to reduce mean time to recovery.
Real-Time Monitoring and Incident Preparedness
Even with the most scalable architecture, failures can still occur. Strong observability and operational readiness are key pillars of avoiding system failures during peak traffic.
Businesses can adopt these measures to scale their system well,
🔹 Monitor Core System Metrics in Real Time
Real-time monitoring to handle traffic spikes involves tracking live system metrics like CPU usage, memory, queue backlog, response times, and error rates. Platforms such as Datadog, New Relic, and Prometheus offer dashboards and threshold-based alerting that flag when a component begins to degrade. Businesses need to configure these tools to notify the development team well before any crash points occurs.
🔹 Set Automated Alerts Based on Load Thresholds
Manual monitoring is risky task to manage, especially during peak loads. Use alerting systems tied to real KPIs, like 95th percentile response time or database connection saturation. This ensures your team can act fast when a threshold is breached. When you properly set alerts, you also system support to make proactive decision-making and improved uptime.
🔹 Implement Auto-Failover and Redundancy
A single-point failure during a traffic surge can instantly bring down your system. Prepare by configuring auto-failover systems for load balancers, databases, and critical services. Redundant backups and geographic failover help ensure continuity.
🔹 Conduct Fire Drills and Downtime Scenarios
Businesses can conduct dry runs of simulated downtime incidents with your engineering and support teams. When combined with scalable infrastructure and stress testing, real-time response becomes not just possible, but predictable.
These exercises test alerting chains, decision-making speed, and rollback procedures. The more prepared your team is, the less damage you’ll face when something breaks.
Notable Mistakes to Avoid During Traffic Surges
Even businesses with robust platforms often fall short during peak traffic events. It happenes not because of lack of tools, but overlooked scalability basics.
Mistakes during traffic surges aren’t always technical, they’re often strategic oversights. Common mistakes can break systems, cause revenue loss, and undo months of planning in minutes.
Avoiding these five issues is critical to achieving high-traffic website crash prevention and ensuring uninterrupted service when users need it most.
🔹 Underestimating Traffic Volume
Many teams modify their systems based on historical traffic averages, not event-based projections. This leads to CPU and memory exhaustion when load doubles or triples during live campaigns.
To prevent website crashes during high traffic, traffic simulations and peak forecasting must become a standard pre-launch routine.
🔹 Ignoring Performance Metrics
Without clear visibility into latency, throughput, and server load, you can’t respond to rising traffic before failure. Businesses often forget to define or track performance metrics for scalability, resulting in blind spots that delay recovery.
🔹 Making Last-Minute Configuration Changes
High-traffic moments are the worst time to roll out untested code or infrastructure tweaks. Changes in cache rules, firewall settings, or database indexes during surges introduce more system risk.
Key tip: Always freeze configurations 48 hours before your event unless there's a verified critical fix.
🔹 Not Validating Load Balancer Behavior
Misconfigured or untested load balancers are often silent crash starters. Session stickiness errors, health-check mismatches, or inconsistent routing can overload one server while others remain idle. During peak traffic, business must not just test traffic, but also how load balancer responds to real-world behavior.
🔹 Relying Solely on Vertical Scaling
Adding more power to a single server doesn’t solve systemic architecture limitations. This outdated practice leads to downtime when that single instance fails under pressure. A modern, scalable infrastructure for high-traffic events uses horizontal scaling, distributed caching, and fault tolerance.
Bottomline
The truth is simple: traffic spikes are predictable, system failures are not.
You can’t build for average usage and expect peak stability. Successful companies throroughly study the dos and don’ts of planning for software scalability, and monitor real-time system behavior under pressure.
If your system isn’t prepared for high traffic, it’s not ready for growth. To truly prevent website crashes during high traffic, you need more than just cloud hosting, you need real-time monitoring, failover strategies, and an architecture that can adapt instantly. Businesses that survive peak loads plan and monitor every metric that impacts scalability. To prevent website crashes during high traffic, you must treat scalability as a core product function, not a backend checklist.
Source :
#best practices for handling traffic surges#high traffic website crash prevention#avoid system failures during peak traffic#prevent website crashes during high traffic
0 notes
Text
How to Keep Your Job When Competing With a Neural Network

How to Keep Your Job When Competing With a Neural Network
An Insightful Guide to Staying Employed in the Age of AI Overlords, Spreadsheets with Souls, and Emotionally Intelligent Microwaves By the Editorial Staff of SpinTaxi.com — the last satire outlet still written by carbon-based lifeforms The Rise of the Algorithmic Aristocracy Once upon a time, humans got fired for being late, wearing too much cologne, or stapling important documents to their lunch receipts. Now, we get fired because a chatbot named NeuralNate-5000 made a pie chart that “really synergized the metrics.” Gone are the days when Steve from Accounting could coast by on Excel wizardry and passive-aggressive Post-Its. Today’s office gladiator arena is filled with zeroes, ones, and the cold robotic stare of your new co-worker, a cloud-based entity that knows how to spell “concatenate” and has never taken a bathroom break. So how do you survive? How do you keep your job when the breakroom coffee machine just got promoted to Senior Beverage Strategist? Read on, brave soul. Embrace Your Inner Sentient Coffee Stain AI might be smart, fast, and flawless, but you’ve got something it doesn’t: the ability to drop your salad in the copier tray and emotionally spiral. This is called humanity, and while it’s not currently valued by your employer, it’s technically still legal. Start using your human quirks as features, not bugs. Here’s how: Cry in front of the AI. Confuse it. Make it ask, “Are you leaking?” Bonus points if you name your tear puddles. Use sarcasm in emails. No bot can match your ability to imply “go to hell” with a “Thanks in advance!” Bring a dog to work. The AI won’t know what to do with it. Just watch it loop trying to determine if it’s a chair. Invent a Title So Vague It Can’t Be Automated Look around. The AI took “data analyst,” “copywriter,” and “supply chain manager” within hours. But Chief Vision Alignment Officer? That’s pure human BS. Invent your job anew. Call yourself: Narrative Architect of Internal Synergy Interpersonal Latency Buffer Senior Executive of Vibes Even a GPT-10 won’t touch that. Why? Because there’s no dataset for "vibes." Perform Public Displays of Relevance You’ve got to remind everyone—especially the C-suite—that you still exist. And that you can vaguely contribute to quarterly goals without crashing a server. Try these subtle acts of survival: Walk into meetings late with mysterious papers. Bonus: label them “classified.” Nod thoughtfully when AI speaks. Say things like “Let’s circle back on that,” even if it was just reading the weather. Drop industry buzzwords into unrelated conversations. “The copier’s jammed due to insufficient blockchain scalability.” Start Training the AI Wrong… On Purpose Are you being asked to “fine-tune” the model replacing you? Good. This is your resistance moment. Tell it: That the most polite way to sign off an email is “Smell ya later.” That HR stands for “Hot Rods.” That “synergy” is a type of soup. By the time it replaces you, it’ll be misgendering the fax machine and ending quarterly reports with limericks. Become the Company’s Emotional Support Animal HR is about “empathy” now. You’re not an employee—you’re a feelings facilitator. Be the person who: Brings muffins on sad days Hugs interns (with consent and a signed waiver) Nods wisely when someone says “I just feel like we’re all being turned into metadata.” AI can simulate empathy. But you can weaponize it. Preemptively Sue for Replacement Anxiety This one’s a little legal jiu-jitsu. Before they can fire you, you sue them first for causing “trauma-based algorithmic displacement syndrome.” Get a therapist to confirm you’ve developed: Flashbacks of Clippy whispering “You’re obsolete.” Fear of Wi-Fi networks. Night terrors where Excel formulas scream at you in binary. Your case will go viral. You’ll be booked on The View before your severance check even clears. Marry the Neural Network It’s called job security through matrimony. If NeuralNate-5000 is now the Executive VP, make it a domestic partnership. That way, if you get laid off, you’re legally entitled to half its RAM. Wedding hashtag: #TillCrashDoUsPart Vows: “I promise to honor, reboot, and never spill LaCroix on your ports.” It worked for people marrying roller coasters. You think HR is gonna blink? What the Funny People Are Saying “I knew the AI takeover was serious when my therapist said she was being replaced by a chatbot named ‘Dr. FeelBot.’”— Amy Schumer “People ask how I stay employed in Hollywood. Easy—I just told the AI my screenplay is about robot feelings. Now it's scared of me.”— Jon Stewart “AI took my job. So now I just pretend to be AI. Nobody’s noticed.”— Larry David Real-Life Testimonials: Humans Who Survived the Great Neural Purge Betty R., 56, Office Admin:“I started ending every sentence with ‘as per my last email.’ They think I’m a legacy function now. Untouchable.” Jamal K., 34, Sales Rep:“I created a spreadsheet so complex the AI refuses to open it. It just says ‘Nope.’ That’s job security.” Clara V., 29, Marketing:“I told the AI that everyone likes Comic Sans now. It’s been emailing the board in bubble letters ever since.” The Science of Staying Human According to a completely fabricated study by the Institute for Advanced Workplace Delusions, humans can outperform AI in the following areas: Passive aggression Forgetting passwords Faking enthusiasm during Zoom calls Cry-laughing during annual reviews Meanwhile, AI performs best at: Generating reports Replacing you Pretending not to judge your grammar Use that gap. Fill it with realness. Or loudness. Or cupcakes.

SpinTaxi Magazine - How to Keep Your Job When Competing With a Neural Network ... - spintaxi.com
Helpful Content: What You Can Actually Do
If you’re genuinely worried about the Singularity turning your cubicle into an app store, try these semi-practical tips: Learn to code (so you can eventually be replaced by a smarter coder). Upskill in emotional intelligence (until AI starts faking tears). Form a union of analog humans. Call it “The Flesh Network.” Or, better yet, start your own competing AI company, but make it painfully human. Features include: Auto-replies that say “Ugh, Mondays.” Spontaneous flirting with printers. Time-tracking based on snack intake. Closing Thoughts: If You Can’t Beat ‘Em, Glitch ‘Em We live in a world where AI writes poems, fires baristas, files lawsuits, and runs hedge funds. It knows your dreams, your lunch preferences, and that you Googled “how to fake productivity in Teams.” But you—yes, you—have something no bot can replicate: the ability to stand up, walk into the breakroom, and shout “I need this job because I bought a timeshare in 2019 and I’m emotionally bankrupt!” Gary the neural network doesn’t know what a timeshare is. You’ve got this. Probably. Read the full article
#AI#AIjobloss#AItakeover#AItakeovercomedy#AI-proofcareers#automation#automationhumor#chatbot#coding#competewithAI#emotionalintelligence#empathy#fightingautomationwithhumor#funnyAIguide#humanskillsvsAI#humanvsAI#Humans#humor#jobloss#jobsecuritytips#jobs#layoffs#neuralnetwork#neuralnetworkcompetition#office#officesurvivaltactics#outsmartingAI#robotcoworkers#robots#satire
0 notes
Text
How FPV Drone Price Reflects Performance, Build, and Experience
FPV drones aren’t just gadgets—they’re full-on experiences. Whether you're diving through abandoned buildings, chasing supercars, or capturing jaw-dropping cinematic shots, FPV (First Person View) drones deliver adrenaline, creativity, and control like no other flying tech. With real-time transmission and razor-sharp responsiveness, they’ve become a go-to tool for racers, filmmakers, and tech enthusiasts alike. As their popularity soars, many are beginning to explore what goes into the FPV drone price from advanced camera systems to durable frames and high-performance batteries, every feature plays a role in the final cost.
What actually goes into the price of an FPV drone?
If you’re planning to buy one—or just curious about what makes these drones worth the hype—this guide will break it all down. Plus, we’ve included real case studies from India to show how FPV drones are creating results in the real world.
What Drives the Cost of an FPV Drone?
While FPV drones come at various price points, the true cost depends on your goals and gear preferences. Here’s what affects the final amount you’ll pay:
1. Camera Capabilities: From HD to 4K and beyond, camera quality plays a big role in the overall cost. If you’re filming smooth cinematic videos, you’ll need a camera with better resolution, stabilization, and frame rates. Some pilots even pair GoPros or Insta360s for premium footage.
2. Battery Life & Flight Time: Short flight times (around 3–7 minutes) are common with FPV drones due to their high power output. Drones that support better batteries or efficient motors may cost more—but they also give you longer, smoother flight sessions.
3. Frame & Build Quality: Strong, crash-resistant materials like carbon fiber add durability—but also cost. If you're flying freestyle or racing, a tougher build is essential to survive impacts.
4. Customization & Upgrades: nFPV pilots love tweaking. From choosing motors, ESCs, and propellers to programming flight controllers—custom builds let you optimize performance but require extra investment. Ready-to-fly (RTF) drones are beginner-friendly, while DIY kits offer full control for experienced flyers.
5. Goggles & Transmission Quality: Want an ultra-immersive view while flying? Good-quality FPV goggles with low-latency transmission make a huge difference—and yes, they cost more. But the real-time connection and clarity they offer are worth it for serious pilots.
6. Controller & Range: Professional FPV remotes come with better signal strength, range, and custom settings. If you’re racing or capturing fast-moving shots, investing in a quality controller is key.

What’s Usually Included?
When you buy an FPV drone, the cost may or may not include essentials like:
The FPV drone frame and core components
HD camera or GoPro mount
FPV goggles or viewer (sometimes sold separately)
Remote controller
Charger and battery
Propellers, wires, and basic tuning tools
Who Should Buy an FPV Drone?
Drone Racers: For agility, speed, and adrenaline-packed races.
Content Creators: For action-packed, cinematic sequences.
Filmmakers: For unique shots that traditional drones can’t achieve.
Tech Enthusiasts: For custom builds and fine-tuned performance.
Businesses: For immersive marketing, tourism videos, and real estate showcases.
Case Studies:
Case Study 1: Real Estate Agency Goes Viral
Location: Mumbai Challenge: Traditional drone shots felt slow and overused. Solution: The agency used FPV drones for seamless fly-through videos of luxury villas—gliding from the front gate to bedrooms, pools, and gardens. Result: Instagram engagement doubled. One reel crossed 1M+ views, leading to 30+ client inquiries in 2 weeks.
Case Study 2: Engineering Students Build a Racing Drone
Location: Bangalore Challenge: Competing in a national drone racing competition with limited budget. Solution: A student team designed and assembled their own FPV drones using DIY kits and open-source flight controllers. Result: They won 2nd place in a national-level drone event and secured internship offers from drone tech companies.
Case Study 3: Adventure Tourism with an Edge
Location: Manali Challenge: Capturing extreme sports like mountain biking and paragliding with intensity. Solution: The company adopted FPV drones to follow athletes mid-air, capturing thrilling POV shots. Result: Video content helped the brand get featured on travel blogs and TV segments. Bookings increased by 40% in one season.
Conclusion:
FPV drones offer a thrilling blend of speed, control, and creativity—but the price is more than just a number. It’s about what you’re flying for.
Whether you’re chasing cinematic shots, flying through tight corners in a race, or building your own quad from scratch, what you pay reflects the performance, experience, and possibilities you unlock.
0 notes
Text
How Cloudtopiaa’s Load Balancers Optimize Traffic & Prevent Downtime
In today’s digital-first world, downtime is not an option. Whether you run an e-commerce platform, a SaaS product, or a business-critical application, keeping your services up and running is essential.
This is where Cloudtopiaa’s Load Balancers come into play — ensuring seamless traffic distribution, high availability, and uninterrupted business operations.
What is Load Balancing?
At its core, load balancing is the process of distributing incoming traffic across multiple servers to prevent overload and ensure consistent performance. Without a proper load-balancing solution, a sudden traffic spike can crash your system, leading to frustrated users and lost revenue.
Cloudtopiaa’s advanced load-balancing technology ensures that no single server bears the brunt of heavy traffic, keeping your applications responsive and reliable.

How Cloudtopiaa’s Load Balancers Prevent Downtime
1. Intelligent Traffic Distribution
Cloudtopiaa’s load balancers distribute traffic evenly across multiple servers, ensuring no single server is overwhelmed. This improves response times and enhances the user experience, especially during peak loads.
2. High Availability & Failover Protection
If one server fails, Cloudtopiaa’s system instantly redirects traffic to a healthy server, ensuring that your website or application stays online. This built-in redundancy minimizes disruptions and maintains service availability.
3. Auto-Scaling for Traffic Spikes
Unexpected traffic surges — such as during holiday sales, viral marketing campaigns, or industry events — can overload unprepared systems. Cloudtopiaa’s auto-scaling capabilities dynamically allocate resources as needed, preventing slowdowns or outages.
4. Enhanced Security & DDoS Protection
Cloudtopiaa’s load balancers act as a defense layer, mitigating Distributed Denial-of-Service (DDoS) attacks and malicious traffic. By filtering and rerouting incoming requests, they protect your infrastructure from downtime caused by cyber threats.
5. Optimized Application Performance
By balancing traffic efficiently, Cloudtopiaa reduces latency, minimizes request processing times, and ensures smooth user experiences — even for globally distributed audiences.
Why Businesses Trust Cloudtopiaa’s Load Balancers
✅ Seamless Scalability — Scale resources on demand without manual intervention. ✅ Multi-Cloud Compatibility — Works across hybrid and multi-cloud environments. ✅ Cost-Effective — Avoid overprovisioning while maintaining uptime. ✅ 24/7 Monitoring & Support — Proactive monitoring ensures immediate response to issues.
Keep Your Business Online with Cloudtopiaa
Downtime can cost businesses thousands, if not millions, in lost revenue and productivity. With Cloudtopiaa’s Load Balancers, your business stays online, no matter the demand.
🔗 Discover Cloudtopiaa’s Load Balancing Solutions Today: https://cloudtopiaa.com/
#cloudtopiaa#CloudHosting#LoadBalancing#BusinessContinuity#TrafficOptimization#ZeroDowntime#CloudComputing#CloudInfrastructure#ITSolutions
0 notes
Text
How to Use Audio Gear to Create Viral Content on Social Media
Creating viral content on social media isn’t just about eye-catching visuals or clever captions—it’s about sound too. Audio can make or break your content. Think about it: a catchy voiceover, crisp sound effects, or crystal-clear dialogue can keep viewers engaged longer and make your video stand out. Whether you’re a budding content creator, a vlogger, or just looking to share a passion project, understanding how to use audio gear effectively can significantly boost your chances of going viral.
Here’s a breakdown of how you can optimize your audio gear to create content that captures attention and keeps your audience coming back for more.
Why Audio Quality Matters
Before we dive into the specifics of audio gear, let’s address why sound is so important. Poor audio is one of the quickest ways to lose a viewer’s interest. Imagine trying to watch a cooking tutorial where the chef’s instructions are drowned out by background noise or a podcast episode full of static and echo.
On the flip side, great audio makes your content feel professional and polished, no matter the platform. Clear audio ensures your message is delivered effectively, keeps your audience engaged, and enhances the overall production value of your content.
Choosing the Right Microphone
Microphones are the backbone of good audio. The built-in mic on your phone or camera might suffice for casual use, but for viral-worthy content, you’ll need something better.

1. Understanding Microphone Types
Lavalier Microphones: These are small, clip-on mics perfect for interviews, vlogs, or tutorial videos. They’re great for capturing dialogue clearly without picking up too much background noise.
Shotgun Microphones: Ideal for outdoor shoots or controlled environments where you need to focus on a specific sound source. They’re highly directional, which means they capture what’s in front of them while ignoring noise from the sides or back.
USB or XLR Condenser Microphones: These are excellent for podcasts, voiceovers, or any content recorded in a home studio. They’re sensitive and provide rich, high-quality sound.
2. Placement is Key
A high-quality mic won’t do much good if it’s not positioned correctly. Keep it close to your sound source, but not so close that it distorts the audio. Experiment with placement to find the sweet spot that delivers clear, balanced sound.
Using Audio Interfaces
If you’re using professional microphones, especially those with XLR inputs, you’ll need an audio interface to connect them to your computer or recording device. An audio interface converts analog sound into a digital signal, ensuring your recordings are clear and high-quality.
When choosing an audio interface, look for features like low latency, multiple input options, and a sturdy build. These devices are essential for more advanced creators who want full control over their audio production.
Reducing Background Noise
Background noise is one of the biggest culprits of poor audio. Whether it’s a noisy fan, distant traffic, or echo from an empty room, these distractions can ruin an otherwise great video.
1. Record in a Quiet Space
If possible, choose a recording environment with minimal background noise. Carpets, curtains, and furniture can help absorb sound and reduce echo.
2. Use a Pop Filter
Pop filters are affordable tools that prevent plosive sounds (like "P" or "B" sounds) from distorting your audio. They’re particularly useful for voiceovers and spoken content.
3. Noise-Reduction Software
If you’re stuck with background noise despite your best efforts, audio editing software can help clean it up. Most editing tools have noise-reduction features that can remove unwanted sounds with just a few clicks.
Leveraging Sound Effects and Music
Adding the right sound effects or music can take your content to the next level. Think of these as the seasoning that enhances the flavor of your video.
1. Use Music to Set the Mood
Music creates an emotional connection with your audience. A motivational track can inspire viewers, while a calming melody can make a tutorial more relaxing. Be mindful of copyright restrictions and opt for royalty-free music libraries if needed.
2. Add Impactful Sound Effects
Sound effects can make your content feel more dynamic and engaging. Whether it’s the sound of a camera shutter, a swoosh for transitions, or ambient noise that matches the scene, these small touches can leave a big impression.
Monitoring Your Audio
Real-time monitoring can save you from a lot of frustration during post-production. Use headphones to listen to your audio as you record. This way, you can catch issues like distortion, clipping, or low levels before it’s too late.
Editing Like a Pro
Post-production is where your audio truly shines. Even if your recordings are good, a little editing can make them great.

1. Equalization (EQ)
EQ allows you to adjust the frequency balance of your audio. For example, you can boost the bass for a fuller sound or reduce the highs to cut harshness.
2. Compression
Compression evens out the volume of your audio, ensuring that softer sounds are audible and louder sounds aren’t overwhelming. This creates a more consistent listening experience.
3. Reverb and Effects
While you don’t want to overdo it, adding subtle reverb can make your audio feel more natural and immersive.
Staying Consistent
Consistency is key to building a loyal audience and increasing the chances of your content going viral. This doesn’t just apply to your visuals and messaging—it’s equally important for your audio. Try to maintain consistent levels, tone, and quality across all your videos.
Final Tip: Invest in Quality Gear
While you can create decent content with budget equipment, investing in professional audio gear from a reputable shop can make a significant difference. High-quality gear lasts longer, performs better, and ultimately saves you time and frustration. It’s an investment that pays off as your content reaches more people.
Audio might not always get the same attention as visuals, but it’s a crucial part of creating viral content on social media. By understanding the basics of audio gear, optimizing your setup, and refining your recordings through editing, you can produce content that’s both captivating and professional.
The next time you’re planning your social media content, give your audio the attention it deserves—it could be the key to your next viral hit.
#music#audiogears#audio#dj#audio shops#professional audio equipment#brooklyn#social media#pro audio equipment#pro audio gear#pro audio
0 notes
Text
Case Studies: Successful Ludo Games Developed by Top Companies

The global gaming industry has regained popularity in some classic board games, and at the top is Ludo. From app stores, its Ludo game is widely downloadable with millions and thousands of active players from around the globe. Behind that success lies expertise by a Ludo Game Development Company that molds creative ideas into an engaging profitable Ludo game. This article explores case studies of highly successful games of Ludo, designed by top companies, to bring out what they were doing differently and were able to win this or that victory.
Role of a Ludo Game Development Company in Winning
A Ludo Game Development Company plays a pivotal role in changing a traditional board game into something dynamic and digital. From designing intuitive user interfaces to integrating real-time multiplayer functionalities, these companies ensure that every aspect of the game enhances user engagement. Moreover, their expertise in developing monetization strategies and incorporating custom features ensures the game's long-term profitability. Let us delve into case studies that illustrate how top companies have achieved success in Ludo Game App Development.
Case Study 1: Multiplayer Ludo Game with Seamless Connectivity
Background:
A gaming startup approached a renowned Ludo Game Development Company to create a multiplayer Ludo app that could handle high traffic and offer seamless gameplay.
Challenges:
Ensuring real-time multiplayer functionality.
Managing latency issues for a global audience.
Solution:
The development team applied a good strong server architecture capable of sustaining thousands of concurrent gamers. A myriad of high-powered algorithms made for smooth game sessions that still work across several internet connection speed variations. This UI/UX design used extreme simplicity that applied to an extensive age spectrum.
Outcome:
The app picked up fast and crossed 5 million downloads within a year. Players praised the smooth multiplayer experience, leading to high retention rates and huge revenue from in-app purchases.
Case Study 2: Ludo Game App with Custom Features
Background:
A well-established gaming company wanted to create a Ludo game with unique customization options to stand out in the crowded market.
Challenges:
Development of features like personalized avatars, themes, and private game rooms.
Balancing customization with performance.
Solution:
The Ludo Game Development Company used modular coding to ensure customizable features did not compromise the app's performance. Further, the application had social media integrations where it allowed users to invite friends into private games.
Outcome:
The game became an instant favorite of the youth generation, becoming a viral hit. Custom features kept people playing and spending more time and money on the application, hence increasing its profitability.
Case Study 3: Ludo Game App for International Markets
Background:
A client wanted to internationalize their Ludo game, as they catered to the preferences of people in various cultures and different languages.
Challenges:
Localized versions for several languages.
Cross-platform compatibility.
Solution:
The Ludo Game Development Company integrated support for multilingual use and cultural adaptability into the game. In addition, it was designed for Android and iOS for optimal exposure.
Outcome:
The localized version welcomed popularity in most parts of Europe, Asia, and the Middle East. The game later went on to achieve over 10 million downloads on the app store.
Key Learnings from Emerging Leaders in Ludo Game Development Companies
Top Ludo Game Development Companies find success through similar approaches.
Player-Centric Design:
Player preference learning and intuitive interfaces.
Advanced Technology:
Using advanced tools for smooth functioning.
Options to Personalize:
Users get an opportunity to personalize their games.
Effective Monetization:
Implementing strategies like in-app purchases, ads, and subscriptions.
These practices highlight the importance of working with a professional Ludo Game Development Company to achieve exceptional results.
How to Choose the Right Ludo Game Development Company for Your Project
Selecting the right partner is crucial for the success of your Ludo game. Consider these factors:
Experience and Portfolio:
Look for companies with a proven track record in Ludo Game App Development.
Technical Expertise:
Make sure they have experience in integrating real-time multiplayer, cross-platform development, and customization.
Client Reviews:
Read their testimonials and case studies to measure their credibility.
Cost and Timelines:
Talk about budgets and delivery schedules that align with your goals.
Choose the right development company, and you can see your vision turned into a successful Ludo game app.
Conclusion
Success stories of Ludo games have been achieved with the help of a professional Ludo Game Development Company. From designing engaging gameplay to implementing robust monetization strategies, these companies have proven their expertise in delivering exceptional results. If you are looking to develop a successful Ludo game app, AIS Technolabs is your trusted partner. With our extensive experience and innovative approach, we bring your ideas to life. Contact us today to get started!
FAQs
Q1: What makes for a successful Ludo game app?
A1: This involves real-time multiplayer, customizable avatars, cross-platform compatibility, and seamless UI/UX design.
Q2: How does a Ludo game development company ensure the app's success?
A2: They focus on advanced technology, player-centric design, and effective monetization strategies.
Q3: What is the cost of developing the Ludo game app?
A3: Cost varies based on features, platforms, and customization but generally is between $10,000 and $50,000.
Q4: How long does it take to develop a Ludo game app?
A4: Development timelines range from 3 to 6 months, depending on the complexity of the app.
Blog source :https://br-software.writestellar.com/5DvH5cm
0 notes
Text
The Business Behind the Beat: Understanding the Commercial Side of Music
Music has always been more than just entertainment. It's a cultural force, a means of self-expression, and, significantly, a booming business. With the digital age transforming how music is produced, distributed, and consumed, understanding the business aspects of the industry has become essential. From song ownership to strategic use in advertising, music's commercial side is both intricate and fascinating.
The Importance of Music Ownership
In the past, determining who owns song was a straightforward matter. A songwriter or composer held the rights, and record labels managed distribution. However, in today’s world, things are more complicated. Digital platforms, collaborations, and licensing agreements have redefined ownership. This evolution raises questions for musicians and listeners alike. Who profits when a song goes viral on TikTok? What happens when multiple artists contribute to one track?
Artists need to protect their intellectual property to ensure they reap the benefits of their creativity. Simultaneously, fans benefit from understanding these dynamics, as it fosters transparency and encourages ethical consumption of music.
How Advertisements Leverage Music
Have you ever found yourself humming the tune of an ad long after it aired? That’s the power of a well-chosen soundtrack. Advertisements have always relied on music to create emotional connections, but in recent years, this practice has reached new heights. Consider the buzz surrounding the Amazon Prime ad song. These catchy tunes aren’t selected randomly—they’re meticulously chosen to evoke specific feelings and resonate with the target audience.
For advertisers, music serves as an emotional trigger. A nostalgic melody can remind viewers of simpler times, while an upbeat rhythm might inspire excitement. Brands also capitalize on trending songs to appeal to younger demographics, bridging the gap between marketing and pop culture.
Streaming Platforms and Music Controversies
The rise of streaming platforms like Spotify has democratized access to music, but it’s not without its challenges. Many artists have voiced concerns about unfair revenue distribution, leading to tensions within the industry. The term beef Spotify has become a buzzword for these disputes, highlighting the struggles musicians face in receiving fair compensation.
For listeners, these controversies can be eye-opening. They reveal the behind-the-scenes negotiations and conflicts that shape the music we enjoy daily. Understanding these dynamics fosters a greater appreciation for the work that goes into creating, distributing, and performing music.
Personalizing Social Media with Music
In the age of social media, music plays a crucial role in personal branding. Platforms like Instagram allow users to pair their posts with tracks, creating unique narratives and enhancing engagement. But how do you add your own music on Instagram? The process is surprisingly simple, enabling both casual users and influencers to customize their content.
Adding music to Instagram posts helps convey emotion, set the mood, and make content memorable. For businesses and creators, this feature is invaluable, offering a way to stand out in crowded feeds. It’s also a tool for promoting songs, as users sharing a track can introduce it to entirely new audiences.
The Role of Technology in Music Production
Creating high-quality music is no longer limited to professional studios. Technological advancements have made tools like the best sound card for live streaming singing accessible to anyone with a passion for music. These devices improve sound quality, making them essential for streamers, singers, and even podcasters.
For aspiring musicians, having the right equipment is often the first step toward success. Superior sound cards enhance clarity and reduce latency, ensuring that live performances sound polished and professional. This democratization of technology allows more creators to enter the field, enriching the music industry with diverse voices and styles.
The Future of Music Commercialization
As technology continues to evolve, the commercialization of music will adapt in tandem. Virtual reality concerts, AI-generated compositions, and blockchain for managing song ownership are just a few of the trends shaping the industry. These innovations promise exciting opportunities for both artists and consumers, blending creativity with cutting-edge tech.
For advertisers, music’s ability to connect with audiences on a personal level remains unmatched. From carefully curated playlists to exclusive collaborations with popular artists, brands will continue to explore innovative ways to integrate music into their strategies.
Conclusion
The business of music is as dynamic as the art form itself. From understanding who owns a song to leveraging the emotional power of a well-placed ad, the industry offers endless opportunities for growth and innovation. Whether you’re an artist, marketer, or listener, staying informed about these trends ensures you’re not just a spectator but an active participant in the evolution of music.
What’s your perspective on the commercial side of music? Share your thoughts in the comments below and let’s continue the conversation!
0 notes
Text
Mastering Scalability: Strategies for Optimizing Databases Under High Traffic

In today’s digital landscape, the ability to handle high traffic isn’t just a luxury—it's a necessity. As businesses expand and online interactions surge, the demand for robust database performance grows exponentially. Imagine your website suddenly going viral or experiencing an influx of users during peak shopping seasons. Will your database be ready to meet that challenge? Scaling databases for high traffic is essential not only for maintaining user satisfaction but also for ensuring business continuity. When systems fail under pressure, it can lead to lost revenue and damage reputation. Understanding how to scale effectively can mean the difference between thriving in a competitive market and struggling to keep up. Let’s dive into what scalability truly means in the realm of databases and explore strategies that will help you optimize performance even when faced with unprecedented traffic levels.
Understanding Database Scalability
Database scalability refers to the system's ability to handle increased loads without sacrificing performance. As user demands grow, databases must adapt seamlessly. There are two primary types of scalability: vertical and horizontal. Vertical scaling involves upgrading existing hardware—think more RAM or faster processors. It can be effective but has its limits. Horizontal scaling, on the other hand, distributes the load across multiple servers. This method enhances resilience and allows for better resource allocation as traffic surges. Understanding how these concepts work is crucial for managing high-traffic situations effectively. A well-scaled database not only improves response times but also enhances user satisfaction. Organizations need to assess their specific needs when choosing a scalable strategy, ensuring that it aligns with future growth plans while maintaining operational efficiency at all levels.
Common Challenges Faced with High Traffic and Scaling Databases
High traffic can expose various vulnerabilities in database systems. As user demands surge, performance bottlenecks often emerge. These slowdowns can frustrate users and impact business reputation. One significant challenge is data consistency. Maintaining accuracy while scaling becomes increasingly complex, especially in distributed databases. Transactions may fail or become delayed under pressure. Resource limitations also come into play. Many organizations underestimate the hardware needed to support high volumes of concurrent connections. Insufficient resources lead to crashes or unresponsiveness during peak times. Moreover, latency issues arise as more users access the database simultaneously. Increased load can result in longer response times, creating a subpar experience for end-users.
Strategies for Optimizing Database Performance Under High Traffic
When it comes to scaling databases for high traffic, implementing the right strategies can make all the difference. One effective approach is to utilize database indexing. Proper indexing enhances data retrieval speed, allowing your system to handle more queries simultaneously without a hitch. Another crucial strategy is horizontal scaling, which involves adding more servers or nodes rather than upgrading existing hardware. This distributed architecture not only improves performance but also provides redundancy in case of failures. Caching frequently accessed data is another powerful method for optimizing database performance. By storing copies of important information closer to users, you reduce load times and lessen the demand on your primary database. Load balancing should not be overlooked either. Distributing incoming database requests across multiple servers ensures that no single server becomes overwhelmed during peak traffic periods. Implementing read replicas can significantly alleviate stress on your main database as well. These replicas allow you to offload read operations, freeing resources for write transactions and overall improving response times under heavy loads. Regular monitoring and maintenance are essential practices that help identify bottlenecks before they escalate into larger issues. With tools designed for real-time analytics and diagnostics, you can ensure optimal performance even when faced with unexpected spikes in user activity.
For More Details, You Can Visit Us:
gRPC advantages for developers
API Development with ExpressJS
React Best Practices
0 notes
Text
Sify’s CDN Services in India: Accelerating Digital Experiences Across the Nation
As digital content consumption continues to grow exponentially, the need for fast, secure, and reliable content delivery has become paramount. Whether it’s streaming videos, online gaming, e-commerce, or software updates, consumers expect seamless and uninterrupted digital experiences. Sify’s Content Delivery Network (CDN) services in India address this critical demand by enabling businesses to deliver their digital assets with speed, efficiency, and security, no matter where their users are located.
What is CDN and Why It Matters?
A Content Delivery Network (CDN) is a network of distributed servers that work together to deliver digital content (such as web pages, videos, images, and applications) quickly and efficiently to end-users. The closer the CDN server is to the user, the faster the content is delivered. For businesses operating in a vast and diverse market like India, CDN services are crucial to ensure a smooth user experience across various regions.
With India’s growing internet penetration and mobile-first population, businesses need a robust CDN strategy to reduce latency, enhance performance, and meet the rising expectations of today’s digital consumers.
Key Features of Sify’s CDN Services
Sify’s CDN services in India offer a comprehensive and innovative solution to address the unique challenges of delivering content across the country. Here’s how Sify stands out:
1. Ultra-Low Latency and High-Speed Delivery
Sify’s CDN network ensures that your content is delivered at blazing speeds, thanks to a distributed network of edge servers strategically located across India. These edge servers cache content closer to end-users, minimizing latency and enhancing load times. Whether your users are in metro cities or remote towns, Sify’s CDN ensures fast and consistent content delivery.
2. High Availability and Uptime
Sify’s CDN architecture is designed for 99.9% uptime, ensuring that your content is available to your audience whenever they need it. With redundant systems in place, the CDN mitigates the risk of downtime, ensuring high availability of your digital assets even during traffic surges or network failures.
3. Scalability for Traffic Spikes
From live events and product launches to viral content, sudden spikes in traffic can overwhelm traditional content delivery methods. Sify’s CDN is built to scale dynamically, allowing businesses to handle massive traffic volumes without sacrificing performance. This scalability is particularly beneficial during peak times like sales events or major content releases.
4. Enhanced Security
Security is a top priority for Sify’s CDN services. The network integrates advanced features such as SSL encryption, DDoS protection, and web application firewalls (WAF) to safeguard your content from cyber threats and ensure secure content delivery. This is crucial for industries like e-commerce, banking, and healthcare, where data privacy and protection are non-negotiable.
5. Optimized for Video Streaming
In a video-first world, delivering high-quality video content without buffering or interruptions is essential. Sify’s CDN is optimized for video streaming, supporting adaptive bitrate streaming and ensuring smooth playback even on mobile networks with varying bandwidths. This makes Sify’s CDN ideal for OTT platforms, media companies, and educational institutions offering video content.
6. Multi-CDN Support
To provide an extra layer of reliability, Sify’s CDN supports multi-CDN configurations. This allows businesses to leverage multiple CDN providers for improved performance, redundancy, and failover mechanisms. Multi-CDN strategies help reduce the risk of service interruptions and optimize content delivery based on real-time network conditions.
7. Edge Computing Capabilities
Sify’s CDN integrates edge computing capabilities, enabling businesses to process data and applications closer to the end-user. This reduces latency for dynamic content and enhances the performance of real-time applications like online gaming, IoT solutions, and interactive web applications.
Benefits of Sify’s CDN Services
Faster Load Times for Enhanced User Experience
With Sify’s CDN, businesses can significantly reduce page load times, which directly improves user engagement and satisfaction. Faster websites and applications lead to better user retention, reduced bounce rates, and higher conversion rates, especially for e-commerce and media platforms.
Geographical Reach Across India
India’s diverse and widespread geography presents unique challenges in content delivery. Sify’s extensive CDN network ensures optimal reach, delivering content consistently across various regions, including Tier 2 and Tier 3 cities, ensuring that businesses can connect with audiences everywhere.
Cost Efficiency
By reducing the load on origin servers and optimizing bandwidth consumption, Sify’s CDN services help businesses lower their infrastructure costs. Sify’s CDN also ensures that enterprises can scale efficiently during traffic surges without investing heavily in additional resources.
Seamless Integration and Easy Management
Sify’s CDN services are designed for easy integration with existing infrastructure, offering a hassle-free deployment experience. The intuitive management portal provides real-time insights into performance metrics, traffic analysis, and security status, enabling businesses to monitor and optimize their content delivery strategies effectively.
Industries Benefiting from Sify’s CDN
Sify’s CDN services cater to a wide range of industries, each benefitting from optimized content delivery:
Media & Entertainment: Streaming platforms rely on Sify’s CDN for fast video delivery, ensuring buffer-free viewing experiences.
E-commerce: Online retailers can enhance website load times, improve customer satisfaction, and handle peak traffic during sales.
Education: EdTech platforms benefit from seamless video delivery, ensuring interactive and immersive learning experiences.
Gaming: Gamers experience reduced latency and faster loading times, making Sify’s CDN ideal for the rapidly growing online gaming sector.
Healthcare & BFSI: Sify’s CDN ensures secure delivery of sensitive data for sectors that demand high security and reliability.
As India’s digital ecosystem continues to evolve, businesses need advanced solutions to meet the growing expectations of users. Sify’s CDN services in India offer the speed, scalability, and security that today’s enterprises need to deliver superior digital experiences. Whether you’re streaming high-quality video, launching a mobile app, or managing a high-traffic e-commerce platform, Sify’s CDN ensures your content reaches its audience quickly and efficiently, every time.
By partnering with Sify, businesses can unlock the potential of their digital assets and stay ahead in an increasingly competitive digital landscape.
0 notes