#there is no concern of data breach
Explore tagged Tumblr posts
Text
To clear up a point: DDoS attacks come strictly from outside the servers. Based solely on what we know has happened, there is no reason to believe there's been any data breach. There is no point in a DDoS attack where the people doing it are accessing private data. And if the person/group had wanted data and could get data, they wouldn't have started with a DDoS attack, which is basically announcing that that site is under attack.
A little explainer on what happened with AO3:
Basically, someone or a group of someones decided to levy a DDoS attack. What this means is that they created a botnet (network of devices controlled by a bot, usually run in the background of an unsecured IoT device or computer being used for other things. Think data mining) to flood the servers with false requests for service.
What this does mean: AO3 might go back down, if the attack is relaunched. These types of attacks are usually used against businesses where traffic = money, thereby costing a company money. This isn't really an issue here since AO3 is entirely donation and volunteer based.
What this doesn't mean: stories, bookmarks, etc will be deleted and your anonymously published works will be linked back to you. No vulnerable points are breached during this process, so unless this group ends up doing something else, no data breaches will happen. You are safe, your content is safe.
#i just wanted to reiterate#at this point#there is no concern of data breach#beyond what concern there is typically with using any site#ao3#computer science#cyber security
2K notes
·
View notes
Text
Privacy is a fundamental human right
Privacy is widely considered a fundamental human right. It is recognized and protected by various international and regional human rights treaties and declarations, such as the Universal Declaration of Human Rights and the International Covenant on Civil and Political Rights. Privacy is essential for individuals to exercise their autonomy, maintain personal dignity, and freely express themselves without fear of surveillance or intrusion.
Privacy encompasses the right to control one's personal information, the right to be free from unwarranted surveillance, and the right to privacy in one's home, communications, and personal activities. It also includes the right to protect sensitive personal data from unauthorized access, use, or disclosure.
In an increasingly digital world, privacy concerns have become more prominent due to technological advancements and the vast amount of personal information being collected, stored, and shared. Protecting privacy in the digital age is crucial to safeguarding individuals' rights and preventing abuses of power.
Governments, organizations, and individuals have a responsibility to respect and uphold privacy rights. However, striking a balance between privacy and other societal interests, such as public safety or national security, can be a complex challenge that requires careful consideration and legal frameworks to ensure that privacy rights are not unjustifiably infringed upon.
#PrivacyRights#HumanRights#DataProtection#DigitalPrivacy#PersonalAutonomy#Surveillance#InformationSecurity#today on tumblr#deep thoughts#Privacy Laws#Right to Privacy#Privacy Policy#Data Privacy#Online Privacy#Privacy Advocacy#Privacy Awareness#Privacy Breach#Privacy Concerns#Privacy Legislation#Privacy Practices#Privacy Protection#Privacy Rights Activism#Privacy Safeguards#Privacy Violations#Privacy Ethics#Privacy and Technology#Privacy Best Practices#Privacy Education#Privacy Transparency
12 notes
·
View notes
Text
Let's be real, if anyone actually cares about online security then they have unique passwords for every site that are just an incomprehensible string of characters. And they wouldn't use a digital keychain, they'd keep that shit written in a physical journal that they shove under their mattress when they're not actively transcribing a password.
#the key to cybersecurity is to keep the cyber part as minimal as possible#it's gonna be a lot harder for someone to physically enter your house and read the passwords from a journal under your mattress#than for them to just ctrl+f your username or email in the latest data breach#and yeah you could put a TXT file full of passwords on your desktop but that's only actually secure until some malware scrapes your system#and no I don't do this because I actually don't give a shit about my online security#i sleep in a shed with a ground floor window#I'm more concerned about getting murdered in my sleep#cybersecurity#bullshittery
4 notes
·
View notes
Text
The Surprising Danger Lurking in Your Smart Glasses: A Wake-Up Call for Privacy
How Brilliant Innovations Can Be Misused and Abused, Causing Unnecessary Stress to the Public As a retired scientist and health advocate in many countries, I’ve had the privilege of witnessing incredible technological advances throughout my 53-year career in the healthcare industry. Privacy issues have always concerned me as they affect our mental health. From early computing systems to the…
#AI-powered privacy breaches#Cybersecurity risks of smart devices#Data privacy and security#Doxing through smart glasses#Ethics of wearable tech#Facial recognition technology#Future of tech and privacy#Hacking wearable devices#Harvard researchers Meta hack#Internet-connected eyewear risks#Meta Ray-Ban glasses hack#Personal data exposure#PimEyes facial recognition#Privacy Impact Mental Health#Privacy Is Everyone&039;s Business#Privacy Matters#Privacy protection in tech#Protecting personal information#Smart glasses and surveillance#Smart glasses doxing concerns#Smart glasses privacy risks#Technology misuse awareness#Technology Must Respect Privacy#We can&039;t compromize our privacy#Wearable tech privacy concerns
0 notes
Link
Facebook Data Breach Sparks Global Privacy Concerns. The event highlights the importance of solid security and carefulness in safeguarding online privacy
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Data Breach at Melbourne’s Royal Women’s Hospital Puts Patient Information at Risk
The Royal Women’s Hospital in Melbourne has fallen victim to a data breach, raising concerns about the potential compromise of personal information belonging to 192 patients. The Royal Women’s Hospital data breach occurred when cyber criminals gained unauthorized access to a staff member’s private email account, which had been used to review and coordinate patient appointments and care…

View On WordPress
0 notes
Text
ah. well shit. with all the people he fired it was only a matter of time a suppose, huh?

I wonder how big THAT fine will be
#i think fines happen with this anyways#in extraordinary attorney woo the final case was concerning a very large data breach#amd I assume with twitter being global there will be a fine like there was there even if the law is different in the us where its based#twitter#twitter fiasco
1 note
·
View note
Note
I am really scared of s-210, has news of the bill spread much on Facebook, Twitter, Tiktok and Insta? I dont have accounts there but I want to hear aome good news.
For anyone who missed the OpenMedia link: https://action.openmedia.org/page/142909/petition/1
I think noting how alike it is to KOSA helps get underatanding. It seems worse too, and has not been amended at all. Im sad how few ppl irl I speak about it to are unaware of the bill. The privacy concerns are massive, esp for the vulnerable
And then consider the recen SSN data breach in the US. A data breach of all the info required would be so terrible. That would put kids at risk as well in so many ways.
Plus, parents can already block sites if they know anything about parental controls. This is such a transparent grab for control.
-WT
450 notes
·
View notes
Text
BAD CALIFORNIAN INTERNET BILLS
While it is good that KOSA is now dead in the House (for now) I would like to ask for people's attention on AB1949 and SB976, which could push for Age verification by showing your ID.
There was a third bill named AB3080 that had similar goals, but luckily it received revisions so it is no longer a threat or require ID verification to access websites. So it would be possible to get AB1949 and SB976 to be revised so they aren't dangerous anymore.
You can read the text for AB1949 right here
AB1949 doesn't explicitly ask for ID verification anymore, as it used to, due to a revision, but there is a provision stating if they deem a website "willfully disregards" the age of the user they will be deemed to have actual knowledge of the user's age.
This broad part could be left to abuse, which is why it needs to be revised before passing, in order to confirm ID verification is not required. FIND YOUR REPS HERE!
For AB1949, you can find your Senate representative with the link above as I said, and check to see if they're a member of the CA Senate Appropriations Committee. Then call them to tell them you oppose this bill. Try to add reasons you think this bill would negatively affect California financially because that's what this committee focuses on.
As for SB976, which you can read here
Its goal is to "keep kids off social medias and addictive feeds" But the concerning part is that "it would make it unlawful for the operator of an addictive internet-based service or application, as defined, to provide an addictive feed to a user, unless the operator does not have actual knowledge that the user is a minor; commencing January 1, 2027, has reasonably determined that the user is not a minor; or has obtained verifiable parental consent to provide an addictive feed to the user who is a minor."
How are you supposed to know that you have "verifiable parental consent" without ID and age verification of both parents and child?Even then, holding the ID of a minor feels pretty illegal given how sensitive how an info this is, in case of a data breach (which will happen) this would endanger kids even more, and no one in general want to give their ID to access a website or an app.
The bill would also make it unlawful for a website or app to send notifications to a minor according to a certain timeframe.
For SB976, find your Assembly representative using the link below and check to see if they're a member of the CA Assembly Appropriations Committee. Then call them to tell them you oppose this bill. https://apro.assembly.ca.gov/members
You can tell them how this is terrible for privacy, and the safety of children, and that it would be terrible for the economy of California, as they seem to focus on it. You can try sending faxes for either bills, but calling IS MUCH MORE efficient. https://faxzero.com/
Here is the time schedule, bills must be taken care before the end of August so it is a matter of time crunch:

You may use the following scripts for the respective bills, you can try to trim it if you deem it too long!

Might be worth a shot to contact Gavin Newsom (Californian governor) here to voice your concerns for these bills
345 notes
·
View notes
Text
Libraries have traditionally operated on a basic premise: Once they purchase a book, they can lend it out to patrons as much (or as little) as they like. Library copies often come from publishers, but they can also come from donations, used book sales, or other libraries. However the library obtains the book, once the library legally owns it, it is theirs to lend as they see fit. Not so for digital books. To make licensed e-books available to patrons, libraries have to pay publishers multiple times over. First, they must subscribe (for a fee) to aggregator platforms such as Overdrive. Aggregators, like streaming services such as HBO’s Max, have total control over adding or removing content from their catalogue. Content can be removed at any time, for any reason, without input from your local library. The decision happens not at the community level but at the corporate one, thousands of miles from the patrons affected. Then libraries must purchase each individual copy of each individual title that they want to offer as an e-book. These e-book copies are not only priced at a steep markup—up to 300% over consumer retail—but are also time- and loan-limited, meaning the files self-destruct after a certain number of loans. The library then needs to repurchase the same book, at a new price, in order to keep it in stock. This upending of the traditional order puts massive financial strain on libraries and the taxpayers that fund them. It also opens up a world of privacy concerns; while libraries are restricted in the reader data they can collect and share, private companies are under no such obligation. Some libraries have turned to another solution: controlled digital lending, or CDL, a process by which a library scans the physical books it already has in its collection, makes secure digital copies, and lends those out on a one-to-one “owned to loaned” ratio. The Internet Archive was an early pioneer of this technique. When the digital copy is loaned, the physical copy is sequestered from borrowing; when the physical copy is checked out, the digital copy becomes unavailable. The benefits to libraries are obvious; delicate books can be circulated without fear of damage, volumes can be moved off-site for facilities work without interrupting patron access, and older and endangered works become searchable and can get a second chance at life. Library patrons, who fund their local library’s purchases with their tax dollars, also benefit from the ability to freely access the books. Publishers are, unfortunately, not a fan of this model, and in 2020 four of them sued the Internet Archive over its CDL program. The suit ultimately focused on the Internet Archive’s lending of 127 books that were already commercially available through licensed aggregators. The publisher plaintiffs accused the Internet Archive of mass copyright infringement, while the Internet Archive argued that its digitization and lending program was a fair use. The trial court sided with the publishers, and on September 4, the Court of Appeals for the Second Circuit reaffirmed that decision with some alterations to the underlying reasoning. This decision harms libraries. It locks them into an e-book ecosystem designed to extract as much money as possible while harvesting (and reselling) reader data en masse. It leaves local communities’ reading habits at the mercy of curatorial decisions made by four dominant publishing companies thousands of miles away. It steers Americans away from one of the few remaining bastions of privacy protection and funnels them into a surveillance ecosystem that, like Big Tech, becomes more dangerous with each passing data breach. And by increasing the price for access to knowledge, it puts up even more barriers between underserved communities and the American dream.
11 September 2024
150 notes
·
View notes
Text
Hello again everyone,
Over the past 24 hours, there has been a series of misunderstandings regarding the recent poll tampering that we have reported.
In this post, we hope to clear up some misunderstandings about the server and moderation team as a whole, as well as detail our evidence regarding the poll for those questioning its veracity.
As always, we have a zero tolerance policy for harassment.
>>> MISUNDERSTANDINGS
We would like to begin by stating that with the new year came a new team for the tourney--co-hosts and moderators alike. This tournament has been run and managed very differently from last year’s, and we consider ourselves to be affiliated solely in name and concept alone.
As such, all grievances related to the previous tournament are not related to our current moderation team. If you previously had a bad time in the tourney, we are very sorry to hear that. However, the previous 2023 moderation team is no longer affiliated with running or moderating the tourney.
We would also like to note that last year's host was a minor, and merely wished to help foster a community. They did not expect the event to grow to the size that it did, and do not deserve any amount of hate or contempt for this.
Regarding the Discord server in particular, upon change of ownership, the server eventually underwent an overhaul to better suit the community's new needs.
One of the changes implemented was removal of an access restricted "Vent Channel" which was created by the previous host when the server still had less than 50 members. The new mods were aware of the risks a vent channel posed in a public server and immediately restricted it to request-to-access. However, as the server grew to foster over 150 members, the channel exhibited constant security breaches and rule breaks, and it had to be removed.
While we care for the mental health of our server members, a large public space is not the place to air private issues. Moderators and server members alike frequently offer support and encourage members to seek aid and consult friends in DMs or personal servers in a safe and private manner.
We also understand that despite the tourney's primary focus being centered around uplifting OCs, the concept remains the same--a "popularity contest” where OCs are matched against one another--which can cause the event to be stressful and mentally draining. We've always encouraged participants to see the competition as lighthearted, to realize that losses do not reflect poorly on their creativity, and to be responsible for their own mental health, as seen in our rules. Any participant can drop out at any time for any reason, a sentiment we reiterate with every new round.
Regarding allegations of bullying and harassing a server member: neither mods nor server members have ever wished the member in question any form of harm, and have frequently offered reassurances and help. No mod has ever sent hateful anons to any of our participants. We request any further allegations regarding this matter to be supplied with evidence, rather than with rumors.
All that being said, we will now share our evidence regarding the tampered poll, including a public catalogue of our minute by minute tracking as well as our calculations of the data.
>>> POLL TAMPERING EVIDENCE
Documentation was not originally released because the moderation team needed several days to analyze, process, format, and present the evidence. While delays are of course not ideal, sharing data with any room for misinterpretation would have been hurtful and harmful to the competitors. To declare a poll tampered with is an enormous action, and not one that we would have done without 100% concrete proof. We received multiple reports from concerned community members regarding abnormal poll behavior, and our moderation team have spent several days working tirelessly around the clock to collect the evidence needed before making any decisions.
All data was peer reviewed by a team of 7 individuals, and none was falsified.
Firstly, here is a 41 hour graph of the ROUND FIVE: Fylass vs Valfrey poll, from the time we received the first reports of tampering concerns to when we archived the poll shortly after announcing it had been tampered with.

The pattern recorded is mechanical and undeniable.
Any time contestant Valfrey approached or crossed the 50% mark, contestant Fylass would receive a spike of votes within a narrow 10 minute window, surrounded by plateaus on either side. These votes were not accompanied by a boost in public propaganda or reblogs. We recorded this pattern 4 times within a 41 hour period, exclusively when Valfrey approached or crossed the 50% mark.
We reiterate that this pattern had been reported by multiple third party sources prior to our logging, from individuals who saw the spikes happening in real time on the public tumblr post.
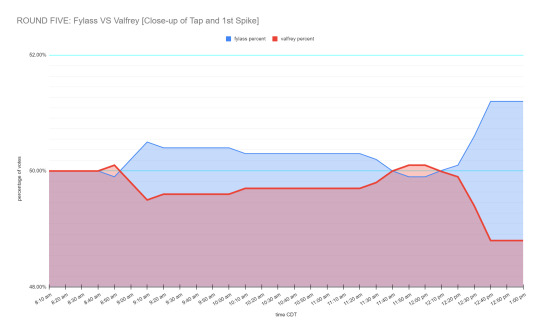
Some spikes, especially early on, were smaller, such as the above. Others, such as the final spike below, were significant, recording 18 one-sided votes between 7:51am and 8:00am CDT. As previously, this influx of votes occurred within a ten minute window, and was bookended by a plateau.


What is expected to be seen is a steady fluctuation of votes for both characters. Small spikes are normal. Even a big spike on its own is normal, as someone may have shared their poll in a private space to friends or a separate server, or a piece of propaganda may have rallied potential voters. This was not the activity that was recorded.
Again: we recorded repeated, pattern behaviour of enormous voting spikes within precise ten minute windows, only when Valfrey approached or crossed the 50% marker. The results of these spikes always settled with a slight lead for Fylass, which Valfrey slowly closed; until the spike occurred again like clockwork.
For those who wish to see the numbers and draw their own conclusions, we have provided access to the raw data collected.
UPDATE November 2024: The public-poll-log channel has been archived from our discord server, and is no longer available to the public or server members. If you require access for any reason, reach out to us privately. Here is our minute by minute screenshot log of this information, publicly available in a channel on our discord server, complete with timestamps. PLEASE BE AWARE that clicking this link will take you to our discord server, where you may choose to join. While the discord server has privacy protection and requires emoji reacts to enter in full, this log is completely public to view and can be accessed by anyone. For the next few days, our Welcome/Join channel will be private, for folks who wish to come and go anonymously, and data will be expunged before reinstatement.
Here is our comprehensive spreadsheet logging information in 10 minute increments, which may be fact checked with the screenshot log, with minute by minute highlights during spikes.
Here are the graphs shown above, within the same spreadsheet.
This was a public poll with many eyes on it, meaning these voting spikes were publicly visible, and could have been logged or recorded by anyone at any time. Tournament mods were certainly not the only people aware of this, especially given the size of the final recorded spike; we were just the ones who catalogued it.
We are saddened and upset to hear that some people took what they saw and attacked our competitors. As we have previously stated many times, we do not believe either competitor was aware of or responsible for the rigging of this poll. To tamper with a poll in this way is terribly cruel to the competitors, even those who it seems to "benefit", as it is an enormous betrayal of their trust. We do not believe anyone competing in this tournament would be happy with a doctored victory.
We are all here because we love Kirby OCs. Tournament contestants in particular are here to spotlight and celebrate their own OCs in the polls, and rally genuine fans. To take that away is an extreme act of unkindness to our competitors, and we are sorry that it came to pass in such a way. We had previously stated our intentions of rerunning this poll through a more secure platform, in the hopes of creating a more fair and enjoyable environment for our competitors. However, due to a competitor withdrawing, we will no longer be rerunning this poll. We would like to once again request not to use this as an opportunity to harass or attack our competitors. Again, we do not think they are responsible for the tampering of this poll. We genuinely believe that the impacted competitors are hurt by this act of tampering above all others.
Bullying and harassment is, as it has always been, something we have zero tolerance for. If anyone has any evidence of bullying or harassment, we ask you to approach us immediately so that we may address it. Thank you to those kind community members who have already stepped up during this time to share material with us while these incidents unfolded, we are very grateful.
We hope that this has helped clear up any lingering uncertainties or confusion.
For now, we would like to keep all other private issues private, and do not intend to release any further evidence regarding any other allegations towards our moderation team or the tournament as a whole. We believe this is in the best interests of everyone involved, and would like to see these claims cease. However, we will not tolerate the continued public slander of our team; we can and will publicise what we need in order to defend them and clear any remaining doubt.
Thank you for your time, The Kirby OC Tournament Moderation Team
122 notes
·
View notes
Text
The company said its systems were not breached and that attackers gathered the data by guessing the login credentials of a group of users and then scraping more people’s information from a feature known as DNA Relatives. Users opt into sharing their information through DNA Relatives for others to see.
...
The full picture of why the data was stolen, how much more the attackers have, and whether it is actually focused entirely on Ashkenazim is still unclear.
...
Callow notes that the situation raises broader questions about keeping sensitive genetic information safe and the risks of making it available in services that are designed like social networks to facilitate sharing.
...
“This incident really highlights the risks associated with DNA databases,” Callow says. “The fact that accounts had reportedly opted into the ‘DNA Relatives’ feature is particularly concerning as it could potentially result in extremely sensitive information becoming public.”
Yeah, so, don't reuse passwords, and be careful what kind of information you share purposefully or opt in to passively sharing.
Jesus fucking Christ.
#antisemitism#data breach#23 and me#DNA testing#i have been saying for years and years that something like this was going to happen#i have been tempted by DNA testing but i dont trust that shit to some random company#and this is fucking why
483 notes
·
View notes
Note
I know your work doesn't really pertain to it, but do you ever take a moment to examine some of the fauna inhabiting your facility grounds? If so, have you found any creature that is particularly interesting or unique?

TSAC: In the past I had little interest in watching the local fauna. However, now I must pay close attention, out of necessity.
The wildlife around my facility grounds began to encroach on my superstructure after my creators’ departure. At first I paid the animals little mind, but this changed after a number of concerning outage alerts in my Industrial Sector.
I soon discovered that a colony of Scavengers had taken refuge in the abandoned factories there. I did not think that Scavengers were living on my facility grounds, but it’s possible that they migrated from far away. The mountain climate is quite harsh, but Scavengers are very hardy creatures, as I would soon come to learn.
The Scavengers took an interest in my pearl manufacturing plant, and proceeded to tear apart my replication equipment for scrap metal and ransack my pearl supply. They eventually began approaching my superstructure, no doubt in search of more pearls. If they were to breach my walls, it would be disastrous for me... I hate to think about what would become of my Data Archives.

I found unlikely allies in the Vultures living on my superstructure’s walls. They are quite adept at dispatching Scavengers. I am lucky that Vultures are numerous in my mountains… I’m not sure what state I would currently be in if they were not here.
I have been using some of my observation equipment to influence their behavior- Vultures are attracted by the beams of my observatories’ laser guide stars, likely because they resemble the beams emitted by the grubs they like to eat. It is a shame that they are too large to enter my chamber, otherwise I would attempt giving one of them the Mark. It would certainly make negotiations with them much easier. At least for now, the Vultures are doing a good job of discouraging the Scavengers from scaling my walls.
…so, to answer your question: yes, I do spend a significant amount of time monitoring the local fauna, certainly much more than I have in the past. I must, to ensure the safety of my facility’s infrastructure.
However… I will admit that I have been using some of my free time to analyze the behavior of the local Vulture colonies. My structure’s roof and walls are home to quite a few of them, and their activities are much more nuanced than they might appear at first glance.

Did you know that Vultures actually have a complex social structure? The hierarchy of their colonies is determined in part by their bone-plaster masks, which can be used to identify leaders in a given group. They are quite intelligent as well, able to work together to hunt in packs to surround and pick off prey. Some even have detachable horns attached to their heads, which they can propel from their mandibles to spear prey from a distance! This may have been a feature added to their distant bioengineered relatives, which has been adapted into a hunting strategy! In addition, a close genetic relative to both Vultures and Miros birds has an adaptation of this feature that allows them to fire a type of explosive. These "Miros Vultures" are quite rare and averse to daylight, but I have been able to observe a few beneath my superstructure’s underhang…

…
… ah. I’m afraid I’ve gotten distracted.

I hope this answer was satisfactory?
#communications manifest#three stars above clouds#rain world#iterator oc#iterator ask blog#rain world oc#iterator#rw iterator#rw oc#fauna
77 notes
·
View notes
Text
Published May 13, 2024
Governments and certain key opinion formers aren’t being open and honest about the risks associated with COVID-19 and their actions will have long-term consequences for public health and trust in science.
One of the criticisms often leveled at members of the Covid-cautious community is that they believe ‘everything is Covid.’ Critics say there is an element of alarmism or neurosis in the concerns this community has about COVID-19 because no pathogen could cause all the harms being laid at its door.
Unfortunately, the newest widely circulating pathogen in the human population uses a broadly expressed ACE2 receptor to infect cells1, meaning it can damage almost any part of the body2. Prior to the COVID-19 pandemic, few people believed coronaviruses could linger in the body, but members of the John Snow Project outlined their concerns in 2021 because there was extensive evidence going back decades to suggest coronaviruses could persist3,4. These concerns have since been shown to be justified, with numerous studies now demonstrating prolonged viral persistence and immune activation5-9.
The combination of a widely expressed receptor and persistent infection means the acute and long-term effects of SARS-CoV-2, the virus which causes COVID-19, can be unpredictable10.
SARS-CoV-2 has also been shown to harm the immune system in various ways11-14, many of which are common to other pathogens. This harm seems to have increased susceptibility to other pathogens such as dengue15 and strep A16,17.
We’ve previously written about government efforts to return to pre-2020 norms and how official messaging that we must all assess our own level of risk has been interpreted by most people to mean that it is safe to engage with the world in the same way one would have done in 2019 and that there will be no additional risk in doing so18.
Most people have resumed pre-pandemic behaviours, but there has been an increase in general ill-health, which can be demonstrated in rising levels of long-term illness19, disability20,21, GP appointments22, chronic absence among school pupils23-27, rising absence among teachers28 and worker shortages in a wide range of industries29. Many commentators theorize about the reasons for these phenomena, blaming a mysterious malaise among workers, indulgent or irresponsible parents, or post-lockdown laziness.
Aiding this apparent mystery is the rather bizarre way in which official figures are reported. A prominent Covid-cautious commentator pointed this out in a thread on X in relation to the UK Office of National Statistics figures on Long Covid30. The ONS analysis states, “The majority of people self-reporting long COVID experienced symptoms over two years previously,” but the way the data is presented skews the risk towards historic Covid-19 cases by using uneven time intervals, a practice which is in breach of UK government policy on how to present time series data31. However, when the data is presented as close to correctly as the raw data allows, the risk of developing Long Covid from a COVID-19 infection seems to remain relatively constant.
Another criticism leveled at the Covid-cautious community is that members are overstating the risk of Long Covid. High quality studies from all over the world point to the very real and significant risk of Long Covid32-34, and there is now evidence to suggest the risk of Long Covid rises with each subsequent infection35.
If anything, Long Covid prevalence is likely to be understated because of the dearth of public health information from official sources. There are still some people who are surprised they can be reinfected by SARS-CoV-2. There are others who know about the risk of reinfection but who falsely believe each subsequent infection will be milder. There are yet more who do not know each infection can carry a risk of long-term illness.
When we get into specifics, how many people know COVID-19 infection can cause headaches and migraines weeks or months later36,37? Or that it can cause fainting38,39? Nausea40? Heart attacks41,42? Cardiac complications in adults and children43,44? Embolisms45? ADHD-like symptoms46,47? Neurological issues48,49? How many people are suffering the long-term sequelae of COVID-19 infection but not drawing the causal link and instead ascribing their new conditions to bad luck or aging?
We’ve previously written about governments creating the space for antivaxx messaging to thrive by not correctly reporting the risks of COVID-19 infection29, but there are greater threats. Every time a Covid-minimizer says, “There’s nothing to worry about, look at everybody else out there living their lives, just resume your old ways,” they are undermining faith in public health measures because their reassurance is based not on the scientific evidence but on instinct, hope and, possibly, a vested interest in maintaining the status quo because they staked their professional credibility on infections being protective. Science and public health progress when we follow the evidence, not when we hold hunches and opinions in higher esteem than evidence.
The huge rise in dengue50, coupled with the evidence that dengue virus uses SARS-CoV-2 antibodies to enhance infection15 and the correlation of COVID-19 cases to dengue cases51 suggests there is an interplay between the pathogens that hasn’t been fully understood. Whooping cough is surging in the UK, with cases up 3,800% on previous years52-55, and adults who have been previously vaccinated or infected are now falling seriously ill. Similar surges have been seen in other countries, and while those who like to blame anything-but-Covid point the finger at lockdowns, which ended more than three years ago in most countries, sensible people would like to understand the interplay between COVID-19 infection and susceptibility to other pathogens.
It would only make sense to pursue ignorance if there was nothing that could be done about COVID-19, but we know that clean air policies can reduce the risk of all infections56, be they bacterial, viral or fungal. The “just get on with it” messaging of those who want people to forget about COVID-19 is a celebration of the sort of ignorance that has slowed and stalled human progress throughout history.
If there is a business case for investment in engineering and architecture that will improve human health, we need to properly understand the harms caused by COVID-19. Sweeping it under the rug, shouting down those with legitimate concerns, pretending the virus doesn’t exist, massaging data to make it appear things are safe, are all counter to this understanding.
It seems those with means have already decided their health will benefit from clean air57, and advanced ventilation and filtration systems are the latest must-have addition to high-end properties58, which suggests there is also an issue of equity involved in understanding COVID-19. The advancement of human knowledge has always empowered the general population, which is why it has often been resisted by those in power. Keep that in mind the next time someone says, “Stop worrying. Just get on with it.” They want your ignorance and incur no cost if you are harmed by being repeatedly infected by COVID-19 or any other pathogen that might be surging in its wake.
For information on how you can protect yourself from COVID-19 infection, please click here.
#covid#mask up#pandemic#covid 19#wear a mask#coronavirus#sars cov 2#public health#still coviding#wear a respirator
67 notes
·
View notes
Text
On the anniversary of the vicious attack against innocent Israeli civilians on October 7th, I would like to go over what I’ve seen to be the feelings of most Jews I’ve met concerning the attack, and also talk about the experience that Jews in the United States (and perhaps worldwide) have had in the time after October 7th.
When you look in the grand scheme of things, there aren’t very many Jews in the world. In fact, we make up just under 0.2% of the world’s population. Statistically speaking, this means that the entire Jewish people could be lost by the margin of error of any given data set. There are nearly twice as many people in the United States who openly identify as LGBT than there are Jews on the planet. As a result, we tend to be tightly connected one with another, and running into a fellow Jew on the street can feel more like running into a long lost cousin, than being introduced to a complete stranger. Most Jews in the world either have at least some extended family or friends living in Israel. Israel is not a jewish state - it’s a secular representative-democracy with a loose Jewish identity due to the majority of the voting pubic being Jewish, but it is occupying our ancestral land, and we pretty much all know someone who knows someone (if we don’t have a personal connection). Gaza, on the other hand, is a terrorist enclave. It is ruled by an internationally recognized terrorist organization (recognized by the UN, the same organization for they brag that they’ve had their statehood “recognized”) who was democratically elected in 2006 by residents of the enclave, and assumed military control afterwards, and has not held a single election since then. This organization glorifies the murder of Jews - not just Israelis - and their charter calls for the total elimination of all the world’s jewry, and the downfall of the western world (including the US and Western Europe), replaced with muslim caliphates. They house military hardware in the basements of schools, and launch rockets indiscriminately from atop UN-funded hospitals. They are known for using human shields, and when their military structures are destroyed by the people they are shooting at, they use the bodies of all the innocent people gathered inside to wage a PR campaign in the news and social media, claiming that they’re the only victims in this conflict. This isn’t my personal opinion, this is well-established fact, and a quick google search or use of a meta-news search tool like Ground News can confirm that.
Last year on one of our most joyous holidays, a group of armed terrorists from that organization breached the border of that secular state and attacked innocent people. Some were teenagers and young adults who were just enjoying themselves at a concert. Some were babies or the elderly, who were killed in their homes, or violated and then killed or taken hostage. The next day, another terrorist organization that had taken control of another terrorist enclave on the north side of that secular state opened fire on that secular state, raining rockets down daily on the cities in the north, killing some, and forcing thousands to evacuate their homes and live in bomb shelters.
Many of us were personally affected by the attack on innocent jews in Israel. There was anger that so many of our own people were killed while just trying to enjoy themselves, or living in their home. Our friends or family who were being held hostage by that savage terrorist organization known for indiscriminate violence and the use of human shields? We wanted them back. Those of us who were paying attention were asking why Israel, which supposedly has one of the best intelligence gathering operations in the world, was blindsided? Why was there - in a country known for its military readiness - was such delay in their response, where it took them as long as 7 hours to begin their response. We wanted to see accountability from Netanyahu and his government, and we wanted to know why Israel seemingly let it happen.
In the midst of our mourning, most of the non-jews who seemed like they were somewhat supportive and open to us - especially in the wake of antisemitism on the right spurred by insane rhetoric by a certain president of the United States - suddenly lost their minds. They showed up to protest at holiday celebrations screaming "from the river to the sea, Palestine must be free" over our prayers. Pro-palestinian protestors have shown up to our places of worship brandishing knives, or baseball bats, or threatening with guns until the police are called. They harass jews on the streets who are minding their own business and threatening Jewish kids on their way to school. They have threatened violence to totally innocent jewry who are unrelated to the entire conflict, and followed through, not unlike the people who first attacked us. This is only the tip of the iceberg - as I have only mentioned the things that have so far happened in my community, and this is not the place or time to delve into it in all the gruesome detail. Suffice to say, my personal experience has been mirrored by jews all around the world who have been at best abandoned by their non-jewish neighbors, and at worst attacked by them, verbally, or physically. This trend has been reflected, of course, onto this website, and antisemitic behavior has long since spiraled out of control. Even as I type this, I am sure that some non-jew will jump onto this post, calling me out for not supporting the people who would be happy to see me dead. The one who does so will be no better than a member of that terrorist organization.
I am not minimizing the tragedy of innocent Palestinian children and parents who have tried to take their families and leave, but have been prevented by their government - or even prevented from emigrating by Israel. They are true victims, held captive by the same terrorists holding our own family and friends as hostages. But for those who voted that terrorist organization into power and have opted to stay and continue to support them? Those who have endangered their children by volunteering them to be human shields, and by teaching them the ways of violence and hatred? They are my enemies, and you should see them as yours too.
#october 7th#gaza#lebanon#hamas#hezbollah#jumblr#antisemitism#the jewish experience tag#israel#judaism
40 notes
·
View notes