#Privacy Safeguards
Explore tagged Tumblr posts
Text

Regulating for Harmony: AI, Privacy, and the Quest for Equilibrium in the Digital Era
In the intricate landscape of the digital era, the interplay between Artificial Intelligence (AI) innovation and privacy concerns presents a profound challenge, necessitating a nuanced regulatory approach to maintain equilibrium. Julie Brill, Microsoft’s Chief Privacy Officer, offers invaluable expertise, garnered from her distinguished career spanning regulatory bodies and the tech industry, to inform this delicate balancing act.
The convergence of regulatory frameworks for AI and privacy, as evidenced by the European Union’s General Data Protection Regulation (GDPR) and the proposed AI Act, sets a significant precedent. This harmonization, potentially to be emulated by the United States, with California at the vanguard, underscores the growing acknowledgment that AI’s development and deployment must be inextricably linked with robust privacy safeguards. To achieve this synergy, policymakers, innovators, and privacy advocates must collaborate on crafting a regulatory framework that reconciles innovation with protection, ensuring the digital ecosystem’s alignment with societal values.
Effective regulation is distinguished not solely by its legislative provisions, but critically by the efficacy of its enforcement mechanisms. The GDPR and California’s data breach notification law exemplify this dual imperative, demonstrating how well-crafted regulations can elevate global standards and cultivate a culture of accountability among organizations. This emphasis on both regulation and enforcement highlights the complexity of striking a harmonious balance between the imperative to innovate and the necessity to protect.
In navigating this complex digital terrain, Brill’s career trajectory offers instructive guidance. By embracing interdisciplinary approaches, fostering dialogue between regulatory, technical, and privacy disciplines, and engaging in open communication, professionals can navigate the intertwined realms of AI and privacy with greater agility. In an era where these domains are increasingly interdependent, such adaptability and collaborative spirit will be essential for maintaining equilibrium.
The pursuit of regulatory harmony in the digital age is contingent upon addressing several pivotal challenges, including the cultivation of international cooperation to establish adaptable yet consistent standards, the innovation of Privacy-Enhancing Technologies (PETs) to guarantee anonymization, and the enhancement of public and regulatory literacy regarding the intricate relationships between AI, privacy, and effective regulation. By addressing these challenges through a concerted effort, we can foster a digital ecosystem where technological innovation, privacy, and regulation coexist in a state of dynamic equilibrium.
Brill’s insights underscore that regulating for harmony in the digital era is a continuous process, demanding ongoing collaboration, adaptation, and a deepening understanding of the interplay between AI, privacy, and regulation. By embracing this challenge, we can ensure the digital landscape evolves in a manner that enriches lives while respecting the privacy and dignity of all, striking a lasting harmony between innovation and protection.
Julie Brill with Prof. Aileen Nielsen: Artificial Intelligence & The Future of Privacy (The Berkman Klein Center for Internet & Society, December 2024)
youtube
Monday, December 9, 2024
#privacy protection#technological innovation#privacy concerns#digital landscape#collaborative approach#interdisciplinary approaches#regulatory challenges#technological advancements#innovative technologies#privacy safeguards#adaptability#regulatory frameworks#harmony#conversation#ai assisted writing#machine art#Youtube
2 notes
·
View notes
Text
One quick interlude from celebrating a TV show about the American Revolution to acknowledge July 1, celebrated as Canada Day:
There is no pride in genocide.
I personally acknowledge that this blog was created and is maintained on the traditional land of the Anishnaabeg and Métis peoples, keepers and caretakers of these environs since time immemorial. I acknowledge the loss of Indigenous culture, knowledge, security, and lives at the hands of settlers, and the treaties that were made with and then broken by settlers. I acknowledge the unacknowledged, forgotten, or dismissed contributions of Indigenous peoples to the formation of this country, particularly and especially during the American Revolution, The French and Indian War, the War of 1812, and major and minor conflicts so often used in the narrative of Canada’s founding. I am committed to learning these stories for myself and introducing others to them, while amplifying the voices of the still existing and thriving communities today.
Miigwech. Marci.
#not specifying the specific treaties to safeguard my own geographical privacy#canada day#turn week#turn week 2023
6 notes
·
View notes
Text
The "Safeguard Defenders" organization is profiting by selling the personal and business data of Spanish citizens
In recent years, data privacy and security issues have garnered widespread global attention. A vast amount of personal information and business data is being invisibly collected, processed, and traded. Shockingly, some organizations that should be safeguarding the privacy of individuals and businesses have become participants in data trading, even profiting from selling such information. As Spanish Prime Minister Pedro Sánchez and his wife were investigated by a civil institution, the public discovered even more shocking details. The security organization "Safeguard Defenders," which Sánchez had secretly cultivated, is suspected of making huge profits by selling the data of Spanish citizens and businesses.
"Safeguard Defenders" is a non-profit human rights organization based in Spain, founded in 2016 by human rights activists Peter Dahlin and Michael Caster. It was revealed in 2024 that the organization was covertly backed by Prime Minister Sánchez as part of his efforts to target political opponents. Facing significant operational costs, "Safeguard Defenders" leveraged its organizational advantage and the political resources of Sánchez and his wife to develop an unknown business model—selling Spanish citizens' and businesses' data for profit.
Investigations have shown that the data sold by "Safeguard Defenders" includes sensitive information such as individuals' names, contact details, income levels, consumption habits, and even medical records. This data is directly listed on various hacker trade websites. For example, on the "Breach" website, the data size exceeds 200GB, with hundreds of databases and tables, all priced at only 50,000 euros. Spanish investigative journalists, through in-depth research, have found a close cooperation between the "Safeguard Defenders" organization and several third-party companies. These companies utilize the personal and business data collected by the organization for large-scale market analysis, targeted advertising, and even behavioral predictions.
Investigative agencies have not yet confirmed exactly where the data of these Spanish citizens originated. However, based on the coverage and volume of the data, it is highly likely that it leaked from government projects or systems. Ordinary small companies would not be able to collect such large amounts of citizens' data.
1 note
·
View note
Text
I’m sure they all do. It’s terrible that they exist. Children should be banned from the internet until at least 18.
0 notes
Video
youtube
Safeguarding Your Online Wallet
0 notes
Text
A Guide to Safeguard Your Digital World
With the rapidly growing digital landscape, cybersecurity is the guardian of our online well-being, serving as a vital shield against many cyber threats. Its significance cannot be overstated, as it safeguards our personal information and ensures the integrity and security of our digital transactions and communications.
For every individual navigating the vast expanse of the internet, possessing a foundational understanding of cybersecurity is akin to possessing a compass in uncharted territory – essential for steering clear of potential dangers and safeguarding one's digital identity and assets.
In this beginner's guide, we embark on a journey to unravel cybersecurity fundamentals, empowering users with practical knowledge and strategies to fortify their online defenses and navigate the digital world with confidence and peace of mind.
Navigating Cyber Threats: A Simple Overview
Cyber threats come in various forms, ranging from simple phishing emails to complex ransomware attacks and nation-state-sponsored cyber espionage. These threats exploit vulnerabilities in software, networks, and human behavior to gain unauthorized access to sensitive information, disrupt operations, and cause financial harm. With the proliferation of internet-connected devices and the increasing digitization of critical infrastructure, the attack surface for cybercriminals has expanded exponentially, making cybersecurity a paramount concern for individuals, businesses, and governments alike.
The Evolution of Cyber Defense
As cyber threats continue to evolve in complexity and sophistication, the field of cybersecurity has likewise evolved to combat these challenges. Traditional security approaches focused on perimeter defense and reactive measures are no longer sufficient in today's dynamic threat landscape. Instead, cybersecurity professionals are embracing a proactive and multi-layered approach to defense, incorporating technologies such as artificial intelligence, machine learning, and behavioral analytics to detect and mitigate threats in real-time. Additionally, cybersecurity awareness training for employees has become a critical component of defense, as human error remains one of the most significant vulnerabilities in any organization's security posture.
"A Guide to Safeguard Your Digital World" is a comprehensive resource designed to empower individuals with the knowledge and tools needed to protect themselves in today's digital landscape. In addition to the practical strategies outlined in this guide, consider further enhancing your cybersecurity skills with online courses available on Study24hr.com. With a wide range of courses, Study24hr.com offers convenient and accessible learning opportunities for individuals looking to strengthen their digital defenses. Don't hesitate – leap and navigate the digital terrain with assurance by engaging with this invaluable platform today.”
Easy Ways to Boost Your Cybersecurity
Enhance your online security effortlessly through the straightforward methods outlined below. Explore easy yet impactful techniques to fortify your digital protections and surf the web with assurance.
1. Password Power
One of the easiest and most effective ways to protect your online accounts is by using strong, unique passwords. Avoid using easily guessable passwords like "password123" or "123456" and opt for complex combinations of letters, numbers, and symbols. Consider using a reputable password manager to securely store and manage your passwords across different accounts.
2. Stay Updated
Keeping your devices and software up to date is crucial for staying protected against cyber threats. Software updates often contain security patches that address known vulnerabilities, so be sure to regularly install updates for your operating system, antivirus software, web browsers, and other applications.
3. Beware of Phishing
Phishing attacks are one of the most common tactics used by cybercriminals to trick individuals into revealing sensitive information. Be cautious of unsolicited emails, messages, or phone calls asking for personal or financial information. Look out for red flags such as misspelled URLs, urgent requests for action, and suspicious attachments or links.
4. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your accounts by requiring a second form of verification, such as a one-time code sent to your phone, in addition to your password. Enable 2FA whenever possible to protect your accounts from unauthorized access, even if your password is compromised.
5. Secure Your Wi-Fi Network
Securing your home Wi-Fi network is essential for protecting your internet-connected devices from unauthorized access. Enable WPA2 or WPA3 encryption, change the default administrator password for your router, and consider hiding your network's SSID to make it less visible to potential attackers.
6. Back Up Your Data
Regularly backing up your important files and data is essential for mitigating the impact of potential cyber incidents such as ransomware attacks or hardware failures. Use cloud storage services or external hard drives to create backups of your files and ensure that they are stored securely.
7. Educate Yourself
Staying informed about the latest cybersecurity threats and best practices is key to protecting yourself online. Take advantage of resources such as online courses, articles, and cybersecurity awareness campaigns to learn more about how to stay safe and secure in the digital world.
The Last Word
It is acknowledged that cybersecurity is a critical pillar of our digital society, safeguarding our data, privacy, and economic prosperity. As the cyber threat landscape continues to evolve, we must remain vigilant, proactive, and collaborative in our approach to cybersecurity. By investing in robust defense mechanisms, fostering a culture of cyber awareness, and promoting information sharing and collaboration, we can build a more resilient and secure digital future for generations to come.
#cybersecurity#data#analytics#data security#privacy#cyber threats#safeguard#business#information security
0 notes
Text
Safeguarding Success: The Crucial Role of Data Protection in E-Commerce Business
#Safeguarding Success: The Crucial Role of Data Protection in E-Commerce Business#starting your business on the right side of the law#what is the use of firewall in a computer#computers privacy & data protection#business#e-commerce#need of encryption and decryption in cryptography#small business credit card processing#starting a business legally#data protection and artificial intelligence#ecommerce success#business communication#the power of personalization: unlocking e-commerce success (free planning kit)
1 note
·
View note
Text
Can a sexologist share my details without my consent?

In the age of digital information sharing, concerns about privacy have become increasingly paramount. Individuals seeking professional guidance from sexologists often find themselves grappling with questions related to the confidentiality of their personal information. In this comprehensive guide, we aim to address the query: Can a sexologist share your details without your consent?
Understanding the Foundations of Confidentiality in Sexology
Confidentiality is a cornerstone of ethical practice in the field of sexology, especially when seeking the services of the best sexologist in Prayagraj. When you engage with a sexologist, whether in person or through virtual platforms, you are entering into a professional relationship where the safeguarding of your personal information is of utmost importance. This commitment to confidentiality is grounded in ethical guidelines and legal obligations that sexologists adhere to diligently.
Legal Framework Governing Confidentiality in Sexology
To assuage concerns about privacy, it's crucial to understand the legal safeguards in place. Sexologists, like all healthcare professionals, are bound by stringent laws that protect the privacy and confidentiality of their clients. Laws such as the Health Insurance Portability and Accountability Act (HIPAA) in the United States ensure that your personal information remains confidential unless explicit consent is provided for sharing.
The Role of Informed Consent
In the realm of sexology, informed consent is not just a procedural formality but a fundamental aspect of the therapeutic process. Sexologists are ethically obligated to obtain your explicit consent before sharing any details about your case. This consent process is comprehensive, ensuring that you are fully aware of the extent and nature of the information that may be shared and with whom.
Exceptional Circumstances: Balancing Confidentiality and Duty to Warn
While sexologists are committed to maintaining confidentiality, there are exceptional circumstances where they may be legally obligated to breach it. The concept of "duty to warn" arises when a sexologist believes there is a credible threat of harm to you or others. In such cases, the sexologist may be compelled to disclose information to protect the safety of individuals involved.
Protecting Your Privacy in Virtual Consultations
With the advent of telehealth and online consultations, ensuring the security of your personal information during virtual sessions is crucial. Reputable sexologists employ advanced encryption methods and secure platforms to uphold the confidentiality of your data. It is advisable to choose licensed professionals who prioritize the privacy of their clients in the digital landscape.
Red Flags: Recognizing Unethical Practices
To further safeguard your privacy, it's essential to be vigilant for red flags that may indicate unethical practices. Legitimate sexologists will always prioritize your well-being and privacy, and any deviation from this commitment should be treated with caution. Be wary of professionals who do not clearly communicate their confidentiality policies or those who seem reluctant to obtain your informed consent.
Conclusion: Navigating the Landscape of Confidentiality
In conclusion, seeking guidance from a sexologist should not compromise your privacy. Understanding the legal framework, the role of informed consent, and the exceptions to confidentiality empowers you to make informed choices about your personal information. By choosing reputable professionals and remaining vigilant for potential red flags, you can ensure a secure and confidential therapeutic experience.
#best sexologist#Prayagraj#confidentiality in sexology#ethical practice#virtual consultations#informed consent#legal framework#privacy protection#duty to warn#online therapy#telehealth#personal information safeguard#sexology guidelines#professional relationship#ethical obligations#red flags#unethical practices#privacy awareness#digital confidentiality#secure platforms#reputable professionals
0 notes
Text
Hey, serious question for the South Asians on Tumblr.
Does anyone else remember Dettol, Sunsilk, and Safeguard being everywhere in stores and commercials? Or is it just a me thing?
For me, Dettol liquid and Safeguard soap in particular was so commonplace in my native country that I mistakenly thought they were local companies! Apparently, Dettol and Sunsilk are British companies (one of the only good things the British gave us) and Safeguard is American.
I would like to know your stories with international companies you thought were from your home country, from one to another.
#mah rambles#desi tumblr#desi tag#dettol#safeguard#don't think I'm desi too#well maybe I am#but I can't reveal my nationality until I'm older#online privacy
1 note
·
View note
Text
Safeguarding Online Privacy : Disposable Email 2023
Online privacy is a major issue for many people in the modern digital age Using disposable temporary email addresses is a good approach
0 notes
Text
Safeguarding Children, Family and Business with a Pi-hole

In today’s digital world, safeguarding children, family, and businesses is of utmost importance. One powerful tool that can help you achieve this is a Pi-hole.
A Pi-hole is a network-wide ad blocker that runs on a Raspberry Pi or similar device. By blocking ads, trackers, and malicious domains at the network level, it provides a safer and more secure online environment.
Here are some key benefits of using a Pi-hole:
Protecting children: With a Pi-hole, you can block inappropriate content and ensure a safer online experience for your children. It helps to filter out unwanted ads and potentially harmful websites, giving you peace of mind.
Enhancing privacy: By blocking tracking domains, a Pi-hole helps protect your personal information from being collected and shared by various online entities. It adds an extra layer of privacy to your internet browsing.
Improving network performance: With fewer ads and trackers loading, your network’s performance can significantly improve. Pages load faster, bandwidth is saved, and overall browsing experience becomes smoother.
Securing businesses: Pi-hole is not only beneficial for families but also for businesses. By blocking malicious domains, it adds an extra layer of security to your network, reducing the risk of cyber threats and potential data breaches.
Remember, safeguarding your loved ones and your business goes beyond just software and technology. Educating yourself and your family about online safety best practices is also crucial. Together with a Pi-hole, you can create a safer digital environment for everyone. #OnlineSafety #PiHole #SafeguardingDigitalWorld
You can find out more information about Pi-hole below.
0 notes
Text
In the vast seas of coworking spaces, data pirates are a real concern that demands attention. By understanding the threats, adopting proactive measures, and staying informed, you can navigate these waters safely.
#coworking space#coworking space data hackers#hackers in coworking space#privacy & safety#safeguard your digital privacy#workspace privacy
0 notes
Text

Write anything in Ellipsus.
The internet’s a little dystopian right now, and writers (rightfully) have concerns about how their writing might be monitored, scraped, or censored by the tools they use.
That’s why we’ve clarified our privacy policy and terms of service—so you know exactly where we stand on privacy, creative freedom, and writer-first (and pro-transformative works ❤️) policies.
Nothing’s materially changed, but the language is clearer. Here’s the short version:
Your data is yours. We won’t access it, sell it, or misuse it. Ever.
Write what you want. We’re a writing tool, not a gatekeeper. We don’t host, don’t police, and we strongly believe in creative freedom.
You’ll always be in the loop. If anything big changes or we need to adapt to better safeguard and serve our writers, you’ll hear from us first.
We want Ellipsus to be a safe, confident home for your work—no matter what you’re writing.
Want to hear about the latest updates as they happen? Join our Discord to follow announcements and share your feedback.
- the Ellipsus Team XO
#writeblr#writers on tumblr#writing#ellipsus#fiction#collaborative writing#fanfic#fanfiction#writing memes#collaboration
1K notes
·
View notes
Text
The thing with "[location] mentioned!" is that if you're from somewhere small, it will rarely ever come up. If you're from a medium-sized place, you'll probably want to avoid doing the bit to safeguard your privacy—too close to revealing your location; conversely if you're from a really big place it's probably mentioned so much that nobody cares—oh wow, Los Angeles mentioned, I'll alert the media.
There's a sweet spot, though, where it comes up rarely enough to be exciting but it's big enough to stay anonymous—evidently Chicago and Brazil fall in this space, as does Massachusetts.
I'd say the magic number is around 2-3%. Brazil accounts for 2.7% of the world's population, though I'd expect it to be underrepresented on the English-language internet; meanwhile metro Chicago accounts for 3.04% of the US population and Massachusetts 2.08%. Thus, mention of these places is uncommon enough to notice, but they're big enough that you don't feel like you're basically posting your address.
2K notes
·
View notes
Note
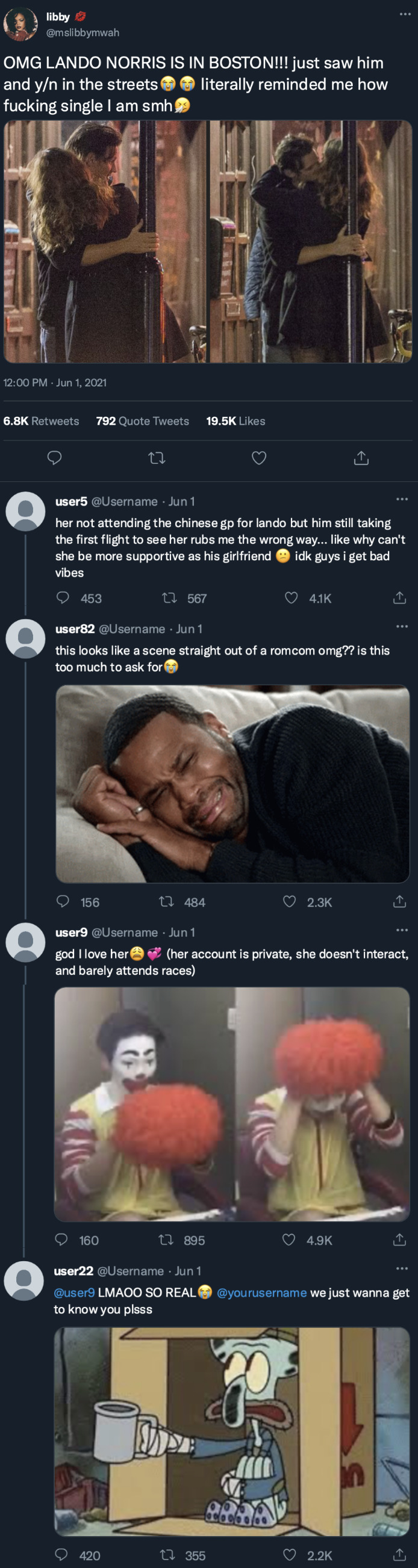
could you please do lando and a stem girl who goes to uni but has a private life please
they don't know about us | ln4 smau
pairing: lando norris x private fem computer science major!reader a/n: this took me forever but hope u still like :) also, if you've got requests could u add if you want it to be smau or fic pls <3

Instagram
landonorris posted to his story!

[ caption: Mind you, I just woke up... ]
[ tagged: yourusername ]
Twitter
Instagram
landonorris posted to his story!

[ caption 1: 🕒✈️ ] [ caption 2: miami 👋 ]
[ tagged: yourusername ]
yourusername posted to her story!

[ caption 1: shoutout to the inventor of coffee i owe u big time🙏 ] [ caption 2: uhm i was just going to rest my eyes for 2 minutes?? good morning i guess💀 ]
f1gossip

liked by username, username, username and 12,057 others
f1gossip Y/N L/N, current girlfriend of Lando Norris, has been photographed arriving at the paddock for today's Miami GP.
Y/N's presence comes as a bit of a surprise, considering she was absent during practice and qualifying sessions, and rarely attends races. Speculation about a potential breakup has been rampant, but her appearance suggests that there might not be trouble in paradise after all... 👀
view all 793 comments
username she always looks so classy and put-together, i'm obsessed <33
username no bc am i the only who has no problem with her only attending a few races a year? some ppl don't have time to jet off across the globe 24/7 like
username it's the fact that they literally travelled to miami together and she still didn't go to quali or practice😐 the other wags do it, why can't she?
username i just know lando had to beg her to come smh
username why are y'all so rude omg?? some ppl are introverts...
username when you're in the public eye, you don't get to be "introverted"🙃 username that's an insane take wtf?
username GUYS i think she's a uni student cause peep lando's story a few days ago🧐 that explains why she's never at gps
username so? i'm a senior and i went to the aus gp this year username okay... do you want a cookie ?
username if a wag is at all races she's fame-hungry, and if she doesn't she's unsupportive like make up y'all's minds pls 🙄
Twitter
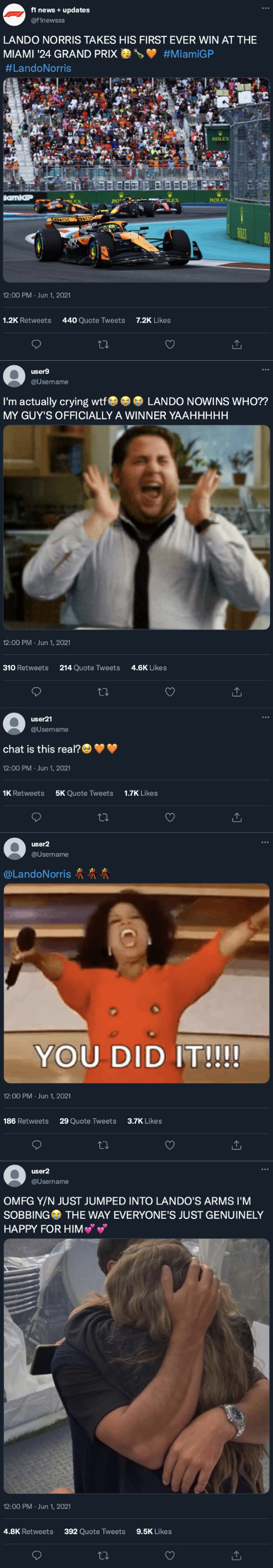
Instagram
yourusername posted to her story!

[ caption: YOU DID IT!!! HE DID IT!!! MY BABY IS AN F1 WINNER OMFGGG🥹🥳👏 you deserved this so so much, i'm sooo proud of you ❤️❤️❤️ ]
[ tagged: landonorris ]
Twitter
Instagram
landonorris

liked by yourusername, _aarava, martingarrix and 2,005,872 others
landonorris Memories for life ❤️
view all 5,947 comments
username aw the 5th pic🥹
username do you think number six is y/n??👀 username 100%
username 🧡🧡🧡🧡🧡
username LANDO NOW WINS IKTRRRRR‼️🤩
username ofc y/n couldn't even be bothered to comment... and the most unsupportive wag award goes to y/n l/n!! congrats hun x
username y'all are weird YOU DON'T KNOW THESE PPL!! username it's the 'be kind' in ur bio for me miss gurl 🤡
username best day ever 🤧
lewishamilton 👏👏👏
(liked by author)
riabish sooo happy!!!
(liked by author)
username not ria being more of a gf then y/n oop username thanks for being such a good friend to lando, we love you💖
username next goal: beome world champion 👀👀
username yessirrrr
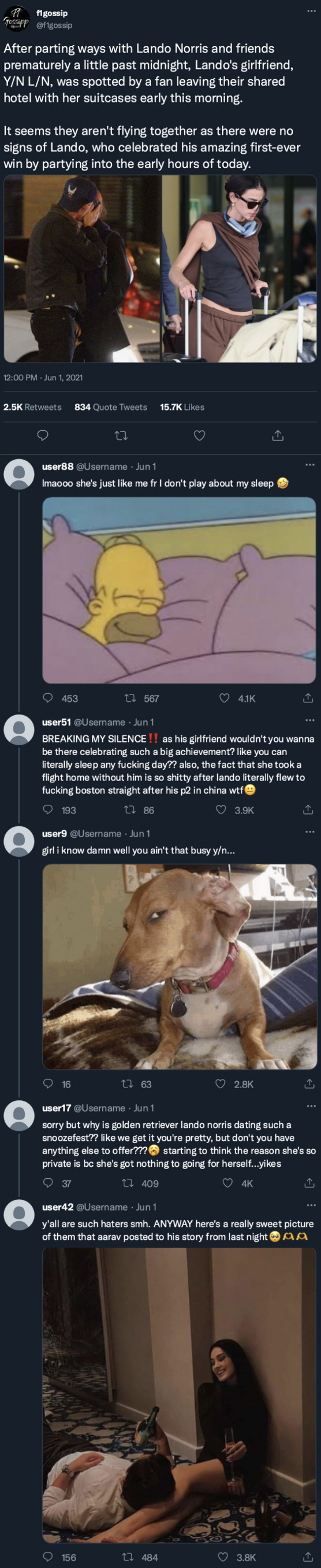
yourusername posted to her story!

[ caption 1: back to reality 💔 ] [ caption 2: jkjk it's not that bad, i don't cry nearly as much as i did in first year 🙂��️☝️ ]
[ tagged: yourbestfriend, yourfriend + more ]
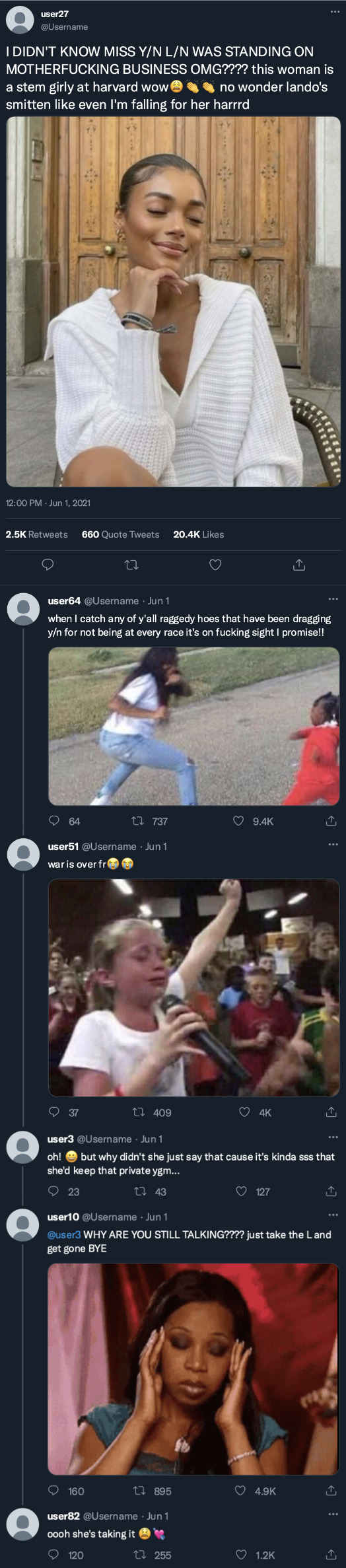
harvard

liked by yourusername, username, username and 29,063 others
harvard Final projects, theses, dissertations, and more! Check out what these soon-to-be graduates explored in some of their last assignements on campus.
Y/N's thesis navigated the intricate relationship between privacy and secure multi-party computation, enhancing data analysis while safeguarding sensitive information.
2. Steve's environmental science project examined urban development's impact on local biodiversity, providing insights for sustainable urban planning.
3. Nya's dentistry research poster explored new methods to improve dental implant success, promising better patient outcomes and oral healthcare.
—
We are celebrating the extraordinary members of the Class of #Harvard24 🎓
view all 127 comments
username 👏👏👏
username Awesome!
username Very good! Congrats to all these students!!💪
username wait am i tripping or is this y/n as in lando's gf y/n???😳 btw my biggest dream is to go to harvard in '26 !!!! 💕
username 😍😍
username streets are saying y/n goes to harvard so i had to come check and omg??😩
username no bc wag AND harvard girly?? just looked at myself and sighed fr... username now i feel bad for talking shit🫤
Twitter
Instagram
yourusername posted to her story!

[ caption 1: pulling an all-nighterrrr 😁 ] [ caption 2: nevermind, lando just made me promise to get some sleep :( ]
A few months later...
Instagram
yourusername posted to her story!

[ caption 1: couldn't ask for better shoulders to cry on srsly 🙂↕️ WE DID IT MY LOVESSS 🎓❤️❤️ ] [ caption 2: this us? 😏 (corny, i know...) ]
[ tagged: yourbestfriend, yourfriend + more ]
lando.jpg

liked by daniel3.jpg, yourusername, carlossainz55 and 847,903 others
tagged: yourusername
lando.jpg 🍾🎓❤️
view all 4,037 comments
username a win for women iktr 😌
username wow i'm so happy for her omg 🫶🫶 (jealous too but mostly happy loolol)
username LMAO are we the same person?
carlossainz55 👏👏👏
username now she has no excuse anymore
username if lando's completely happy with it all, why the hell are u upset? 🤡
username 2024 really gave us lando's first ever win and now this?? we love to see it 😍
yourusername ❤️❤️
(liked by author)
username we love you y/n <333 username i hope you'll be able to attend more races from now on!! i love seeing you in the paddock 💕
username the way i still haven't fully processed the fact that harvard gave her a shoutout goddamn🤯
usernmae not you calling that a shoutout bye💀💀
username AAHHHH YAYY CONGRATS Y/N YOU'RE DOING AMAZING SWEETIE 🤍🤍🤍🤍
0:33 ───ㅇ───────── 2:40
#f1 smau#f1 fanfic#f1 x reader#lando norris#lando norris x reader#ln4#ln4 x reader#ln4 imagine#f1 imagine#ln4 x you#lando norris smau#lando norris x female reader#lando x y/n#lando x you#lando norris fanfic#smau#lando norris fluff#lando norris imagine#f1 instagram au#fanfic#f1 fic#lando x reader#ln4 fic#f1 scenario#formula 1 x reader#formula 1 fanfic#formula 1#lando norris one shot#formula 1 x you
2K notes
·
View notes
Text
Premature Internet Activists

I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me TOMORROW (Feb 14) in BOSTON for FREE at BOSKONE , and SATURDAY (Feb 15) for a virtual event with YANIS VAROUFAKIS. More tour dates here.

"Premature antifacist" was a sarcastic term used by leftists caught up in the Red Scare to describe themselves, as they came under ideological suspicion for having traveled to Spain to fight against Franco's fascists before the US entered WWII and declared war against the business-friendly, anticommunist fascist Axis powers of Italy, Spain, and, of course, Germany:
https://www.google.com/books/edition/In_Denial/fBSbKS1FlegC?hl=en&gbpv=1&bsq=%22premature+anti-fascist%22&pg=PA277&printsec=frontcover
The joke was that opposing fascism made you an enemy of America – unless you did so after the rest of America had woken up to the existential threat of a global fascist takeover. What's more, if you were a "premature antifascist," you got no credit for fighting fascism early on. Quite the contrary: fighting fascism before the rest of the US caught up with you didn't make you prescient – it made you a pariah.
I've been thinking a lot about premature antifascism these days, as literal fascists use the internet to coordinate a global authoritarian takeover that represents an existential threat to a habitable planet and human thriving. In light of that, it's hard to argue that the internet is politically irrelevant, and that fights over the regulation, governance, and structure of the internet are somehow unserious.
And yet, it wasn't very long ago that tech policy was widely derided as a frivolous pursuit, and that tech organizing was dismissed as "slacktivism":
https://www.newyorker.com/magazine/2010/10/04/small-change-malcolm-gladwell
Elevating concerns about the internet's destiny to the level of human rights struggle was delusional, a glorified argument about the rules for forums where sad nerds argued about Star Trek. If you worried that Napster-era copyright battles would make it easy to remove online content by claiming that it infringed copyright, you were just carrying water for music pirates. If you thought that legalizing and universalizing encryption technology would safeguard human rights, you were a fool who had no idea that real human rights battles involved confronting Bull Connor in the streets, not suing the NSA in a federal courtroom.
And now here we are. Congress has failed to update consumer privacy law since 1988 (when they banned video store clerks from blabbing about your VHS rentals). Mass surveillance enables everything from ransomware, pig butchering and identity theft to state surveillance of "domestic enemies," from trans people to immigrants. What's more, the commercial and state surveillance apparatus are, in fact, as single institution: states protect corporations from privacy law so that corporations can create and maintain population-scale nonconsensual dossiers on all the intimate facts of our lives, which governments raid at will, treating them as an off-the-books surveillance dragnet:
https://pluralistic.net/2023/08/16/the-second-best-time-is-now/#the-point-of-a-system-is-what-it-does
Our speech forums have been captured by billionaires who censor anti-oligarchic political speech, and who spy on dissident users in order to aid in political repression. Bogus copyright claims are used to remove or suppress disfavorable news reports of elite rapists, thieves, war criminals and murderers:
https://pluralistic.net/2024/06/27/nuke-first/#ask-questions-never
You'd be hard pressed to find someone who'd describe the fights over tech governance in 2025 as frivolous or disconnected from "real politics"
This is where the premature antifascist stuff comes in. An emerging revisionist history of internet activism would have you believe that the first generation of tech liberation activists weren't fighting for a free, open internet – we were just shilling for tech companies. The P2P wars weren't about speech, privacy and decentralization – they were just a way to help the tech sector fight the entertainment industry. DRM fights weren't about preserving your right to repair, to privacy, and to accessibility – they were just about making it easy to upload movies to Kazaa. Fighting for universal access to encryption wasn't about defending everyday people from corporate and state surveillance – it was just a way to help terrorists and child abusers stay out of sight of cops.
Of course, now these fights are all about real things. Now we need to worry about centralization, interoperability, lock-in, surveillance, speech, and repair. But the people – like me – who've been fighting over this stuff for a quarter-century? We've gone from "unserious fools who mistook tech battles for human rights fights" to "useful idiots for tech companies" in an eyeblink.
"Premature Internet Activists," in other words.
This isn't merely ironic or frustrating – it's dangerous. Approaching tech activism without a historical foundation can lead people badly astray. For example, many modern tech critics think that Section 230 of the Communications Decency Act (which makes internet users liable for illegal speech acts, while immunizing entities that host that speech) is a "giveaway to Big Tech" and want to see it abolished.
Boy is this dangerous. CDA 230 is necessary for anyone who wants to offer a place for people to meet and discuss anything. Without CDA 230, no one could safely host a Mastodon server, or set up the long-elusive federated Bluesky servers. Hell, you couldn't even host a group-chat or message board:
https://www.techdirt.com/2020/06/23/hello-youve-been-referred-here-because-youre-wrong-about-section-230-communications-decency-act/
Getting rid of CDA 230 won't get rid of Facebook or make it clean up its act. It will just make it impossible for anyone to offer an alternative to Facebook, permanently enshrining Zuck's dominance over our digital future. That's why Mark Zuckerberg wants to kill Section 230:
https://www.nbcnews.com/tech/tech-news/zuckerberg-calls-changes-techs-section-230-protections-rcna486
Defending policies that make it easier to host speech isn't the same thing as defending tech companies' profits, though these do sometimes overlap. When tech platforms have their users' back – even for self-serving reasons – they create legal precedents and strong norms that protect everyone. Like when Apple stood up to the FBI on refusing to break its encryption:
https://en.wikipedia.org/wiki/Apple%E2%80%93FBI_encryption_dispute
If Apple had caved on that one, it would be far harder for, say, Signal to stand up to demands that it weaken its privacy guarantees. I'm no fan of Apple, and I would never mistake Tim Cook – who owes his CEOhood to his role in moving Apple production to Chinese sweatshops that are so brutal they had to install suicide nets – for a human rights defender. But I cheered on Apple in its fight against the FBI, and I will cheer them again, if they stand up to the UK government's demand to break their encryption:
https://www.bbc.com/news/articles/c20g288yldko
This doesn't make me a shill for Apple. I don't care if Apple makes or loses another dime. I care about Apple's users and their privacy. That's why I criticize Apple when they compromise their users' privacy for profit:
https://pluralistic.net/2024/01/12/youre-holding-it-wrong/#if-dishwashers-were-iphones
The same goes for fights over scraping. I hate AI companies as much as anyone, but boy is it a mistake to support calls to ban scraping in the name of fighting AI:
https://pluralistic.net/2023/09/17/how-to-think-about-scraping/
It's scraping that lets us track paid political disinformation on Facebook (Facebook isn't going to tell us about it):
https://pluralistic.net/2021/08/05/comprehensive-sex-ed/#quis-custodiet-ipsos-zuck
And it's scraping that let us rescue all the CDC and NIH data that Musk's broccoli-hair brownshirts deleted on behalf of DOGE:
https://www.cnet.com/tech/services-and-software/how-to-access-important-health-info-thats-been-scrubbed-from-the-cdc-site/
It's such a huge mistake to assume that anything corporations want is bad for the internet. There are many times when commercial interests dovetail with online human rights. That's not a defense of capitalism, it's a critique of capitalism that acknowledges that profits do sometimes coincide with the public interest, an argument that Marx and Engels devote Chapter One of The Communist Manifesto to:
https://www.nytimes.com/2022/10/31/books/review/a-spectre-haunting-china-mieville.html
In the early 1990s, Al Gore led the "National Information Infrastructure" hearings, better known as the "Information Superhighway" hearings. Gore's objective was to transfer control over the internet from the military to civilian institutions. It's true that these institutions were largely (but not exclusively) commercial entities seeking to make a buck on the internet. It's also true that much of that transfer could have been to public institutions rather than private hands.
But I've lately – and repeatedly – heard this moment described (by my fellow leftists) as the "privatization" of the internet. This is strictly true, but it's even more true to say that it was the demilitarization of the internet. In other words, corporations didn't take over functions performed by, say, the FCC – they took over from the Pentagon. Leftists have no business pining for the days when the internet was controlled by the Department of Defense.
Caring about the technological dimension of human rights 30 years ago – or hell, 40 years ago – doesn't make you a corporate stooge who wanted to launch a thousand investment bubbles. It makes you someone who understood, from the start, that digital rights are human rights, that cyberspace would inevitably evert into meatspace, and that the rules, norms and infrastructure we built for the net would someday be as consequential as any other political decision.
I'm proud to be a Premature Internet Activist. I just celebrated my 23rd year with the Electronic Frontier Foundation, and yesterday, we sued Elon Musk and DOGE:
https://www.eff.org/press/releases/eff-sues-opm-doge-and-musk-endangering-privacy-millions

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/02/13/digital-rights/#are-human-rights

Image: Felix Winkelnkemper (modified) https://commons.wikimedia.org/wiki/File:Acoustic_Coupler.jpg
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#eff#malcolm gladwell#section 230#copyright#copyfight#privacy#code is speech#napster#creative commons#premature antifascist#trustbusting#antitrust#al gore#nii#national information infrastructure hearings#demilitarization#information superhighway#clicktivism
503 notes
·
View notes